COEN 350 Network Security Overview of Cryptography Overview























































- Slides: 71

COEN 350: Network Security Overview of Cryptography

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

Cryptography n Traditional use of cryptography n n n Secret Key (Symmetric) Cryptography n n Encrypt a plain text into cypher Only people with the right knowledge can recover plain text. Encryption and decryption use secret key c. Public Key (Asymmetric) Cryptography n Encryption and decryption use two different keys.

Cryptography n Other uses of cryptography n n Secure data while stored. Authenticate entities. Ensure integrity of data. Sign statements so that signature cannot be repudiated.

Hash Functions n n Given an object, create a hash (short bit -string) of the object. Hashs differ Objects differ with overwhelming prob. Hashes differ Cryptographically secure hash: n Given a hash, cannot find object with that hash.

Hash Functions n Tripwire n n n Protect OS against trojans. Maintain hashes of all system libraries in a secure area. Check hash against known hash periodically.

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

Cryptographic Security n n Leverage in cryptography comes from functions that are hard to computer without special knowledge. “Hard to compute” difficult to substantiate

Cryptographic Security n “Hard to compute” = NP complete n n n n Problem is P: can be solved deterministically in polynomial time. Problem is NP: solution can be verified in polynomial time. Central Conjecture: NP P. NP-complete: If this problem can be solved in polynomial time then all NP problems can be solved in polynomial time. NP-complete problems: Intrinsically difficult problems to solve on a computer. But: NP completeness is tendency. Instances of NP-complete problems can be easy to solve. n Knapsack problem.

Cryptographic Security n n “Computationally hard” = “Takes n years to solve on best machine. ” Breaking codes is usually parallelizable. Use distributed attack. n n SETI@home Moore’s law: Computers double in speed every 16 months.

Cryptographic Security n UNIX password cracking n UNIX passwords are 8 characters long. n n n Assume 102 printable characters in a password. 1016 possible passwords. 10000 password attempts a second takes 1012/2 seconds to find random password. 16, 000 years to find password Dictionary attacks take much less.

Cryptographic Security n n n DES Data encryption standard Published in 1977 by National Bureau of Standards. Uses 56 bit key Brute-Force attack succeeds after ~1016 tries. 1977: Diffie Hellman: n n Spend $20, 000. - to build parallel machine that can find key in 12 hours. 1998: Electronic Frontier Association n n Build DES cracker for $250, 000. - that could break a key in 4 days. $150, 000. - for second cracker

Cryptographic Security n Security of Algorithms n Fundamental Security Paradigm "If a lot of smart people have tried to crack a paradigm for a long time, then it is impossible to crack the paradigm. " n

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

One-Way Functions n One way function n n Easy to compute Hard to invert. n “Hard” means computationally infeasible.

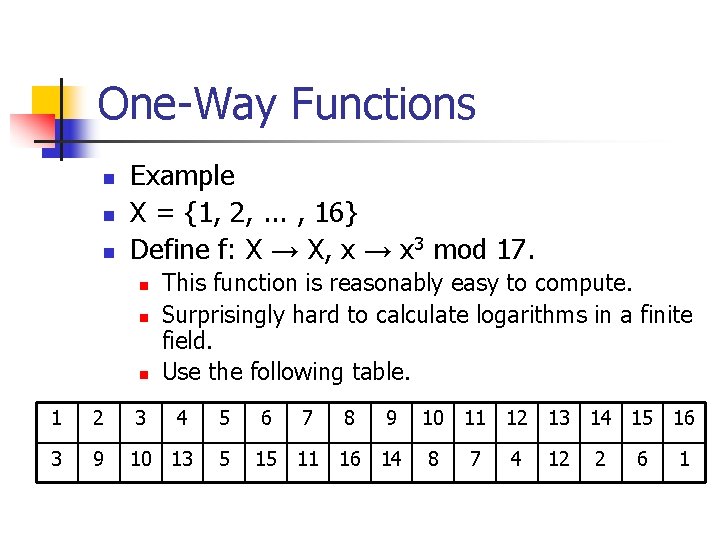
One-Way Functions n n n Example X = {1, 2, . . . , 16} Define f: X → X, x → x 3 mod 17. n n n This function is reasonably easy to compute. Surprisingly hard to calculate logarithms in a finite field. Use the following table. 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 3 9 10 13 5 15 11 16 14 8 7 4 12 2 6 1

One-Way Functions n Preimage resistance: n n Given a possible image y, it is computationally impossible to find any preimage x such that f (x) = y. Second preimage resistance: n Given a pre-image x, it is computationally infeasible to find another preimage z, z x, such that f (x) = f (y).

One-Way Functions n Collision resistant: n It is computationally infeasible to find any two distincts inputs x, x' x such that f(x) = f(x').

One-Way Functions Definition: A function f is a strong oneway hash function (also known as a collision resistant (one-way) hash function) if and only if n f is easily computable, that is, given x, it is easy to calculate f(x). n f is preimage resistant. n f is second preimage resistant. n f is collision resistant.

One-Way Functions n One-Way function with trapdoors n n Much in cryptography is based on being able to do a difficult thing when possessing a secret. There are one-way functions that are easy to invert if one knows a secret.

One-Way Functions n Choose n n p = 48611 (a prime) q = 53993 (a prime) n = p·q. Define f n n n f (x) = x 3 mod n. f is one way, if we only know n. If we know the secret that n = pq, then there is an algorithm that solves x 3 = y mod n for given y and unknown x.

One-Way Functions n One-way function with trapdoor n n n Family of functions fi where i I, an index set. Each fi is one-way. There exists functions hi and a secret s such that n n hi (s, . ) is easy to compute fi (hi (s, y)) = y. n That is, hi (s, . ) is the inverse function of fi

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

Secret Key Cryptography n Conventional encryption uses a secret to convert plaintext to cipher and the same secret to convert cipher to plaintext. n A Greek general tattoos the message into the crown of the head of a slave who then lets his hair grow again. When the slave reaches the destination, the recipient reads the message after the slave has shaven his head again. n One-time pad n Caesar’s cypher

Secret Key Cryptography n n Encryption uses an algorithm publicly known. Sender and receiver use a key.

Secret Key Cryptography n Generic recipe: n n Take the plain text. Apply a transformation (based on secret, reversible with secret). Repeat until result is sufficiently disguised Product cipher n Use first one transformation, then another one.

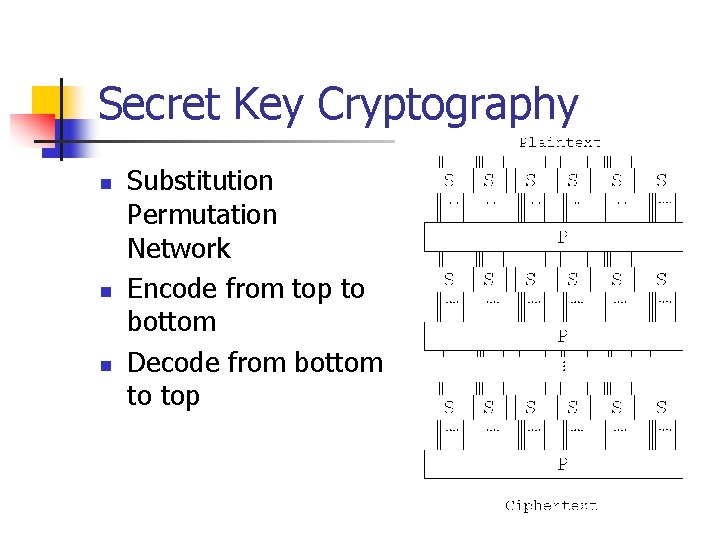
Secret Key Cryptography n n n Substitution Permutation Network Each state involves substitutions and permutations. Substitutions: n n Take an input, replace it by an output. Often implemented as a table. n Input needs to be small.

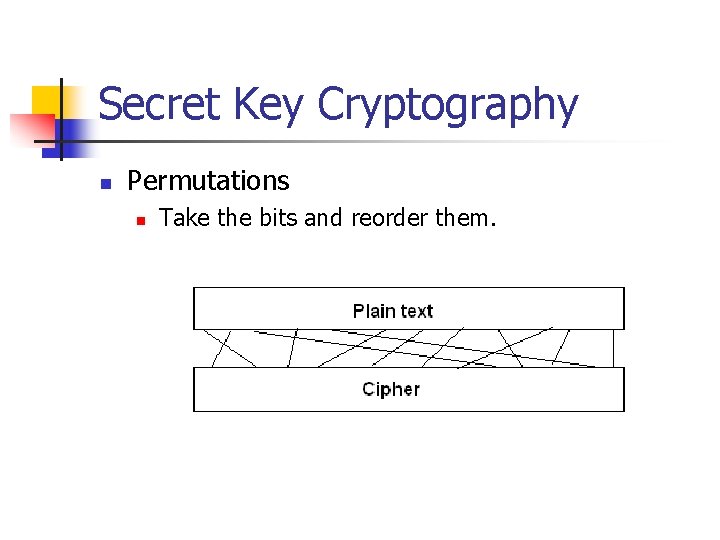
Secret Key Cryptography n Permutations n Take the bits and reorder them.

Secret Key Cryptography n n n Substitution Permutation Network Encode from top to bottom Decode from bottom to top

Secret Key Cryptography n Iterated block cipher n n n Made up of rounds. In each round, apply an transformation with a separate key (the round key). Feistel Cipher

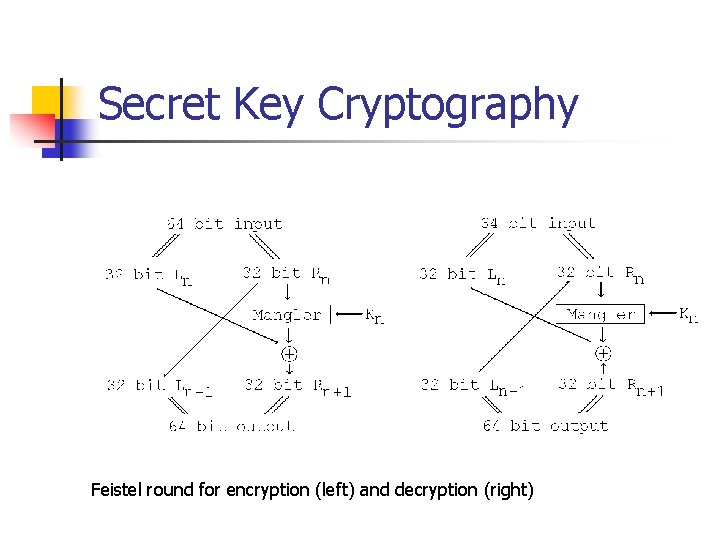
Secret Key Cryptography n Feistel Cipher n n n Iterated Block cipher Block size is 2 t. Each round: n Breaks input into left half L(n) and right half R(n) n L(n+1) = R(n). n R(n+1) = Mangler(R(n), Kn) L(n) n Kn is round key.

Secret Key Cryptography Feistel round for encryption (left) and decryption (right)

Secret Key Cryptography n DES (1977) n n n uses a 64 b key with a parity check, so that effective key size is 56 b. Derives 16 round keys of 48 b each. Works on input of size 64. Uses 16 round Feistel algorithm IDEA (1991) n n n Uses a 128 b key Uses 8 computationally identical rounds based on generalized Feistel algorithm Additional beginning and ending transformation.

Secret Key Cryptography n n Typical block code takes 64 b plaintext and changes it to 64 b cipher text. Electronic Code Book: n n n Break plain text into 64 b-blocks. Encrypt all blocks. Vulnerable to attacks n Two identical text blocks are encrypted the same way. n n Allows guessing contents. Reordering of plain text = Reordering of cipher text. n Change meaning of cipher text.

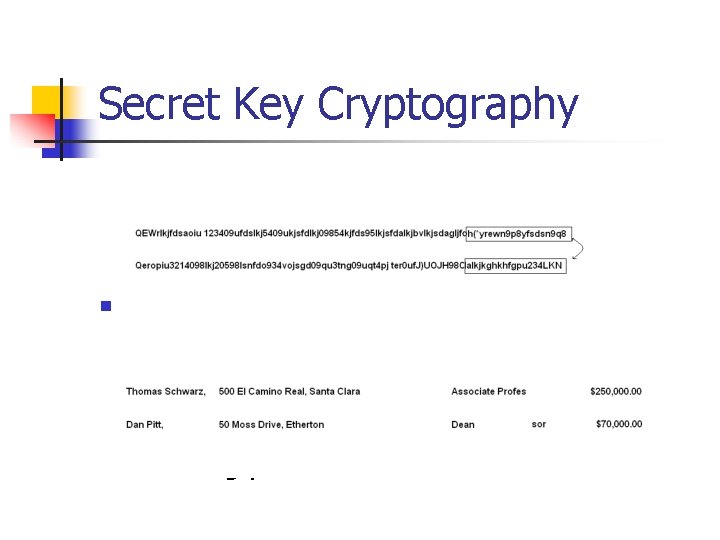
Example: Secret Key Cryptography Database contains employee and salary n n information. n Encrypted:

Secret Key Cryptography n Switch portion of cipher text n Resulting plaintext

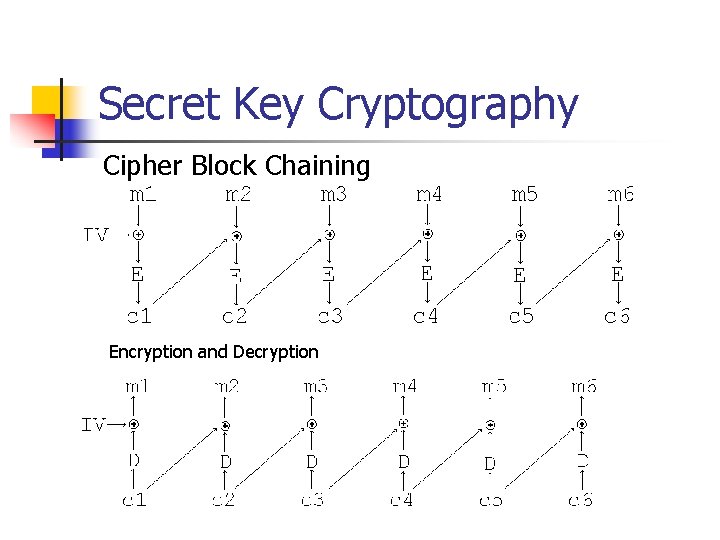
Secret Key Cryptography Cipher Block Chaining Encryption and Decryption

Secret Key Cryptography n n n Cipher Block Chaining If we do not mind to mangle some preceding data, we can switch bits. How? Your turn.

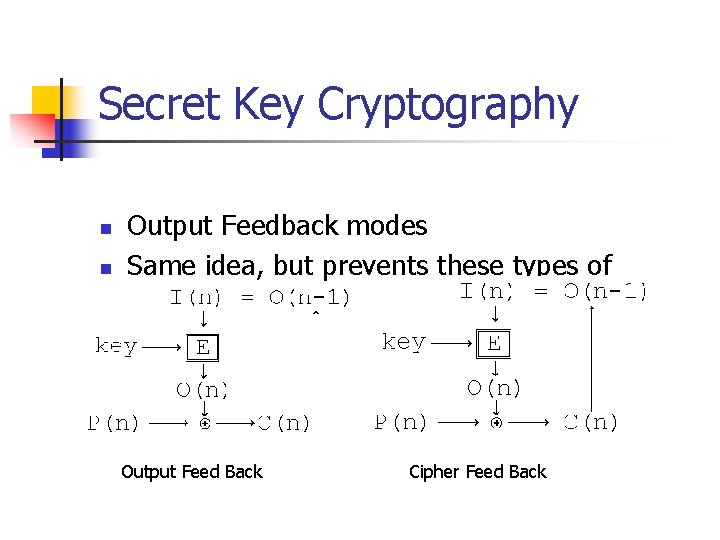
Secret Key Cryptography n n Output Feedback modes Same idea, but prevents these types of attacks. Output Feed Back Cipher Feed Back

Secret Key Cryptography n One-Time Pad n n n Only proven secure cryptographic method But the pad needs to be transmitted between sender and receiver. XORing with a short string is not secure. n See projects

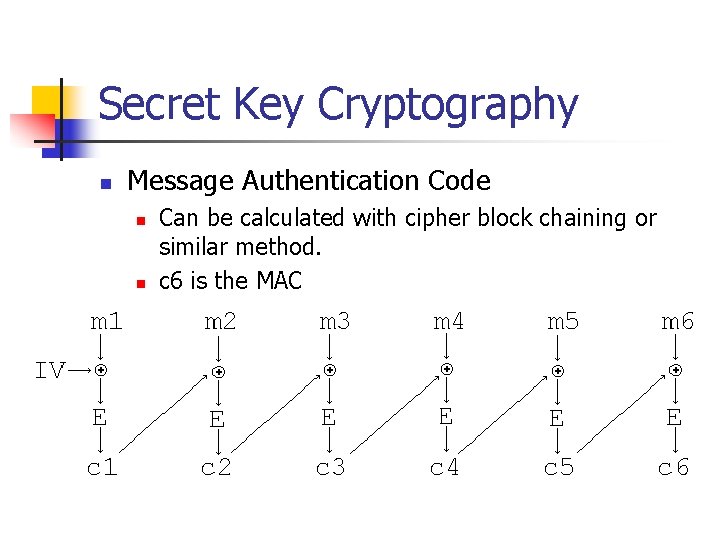
Secret Key Cryptography n Message Authentication Code n n Can be calculated with cipher block chaining or similar method. c 6 is the MAC

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

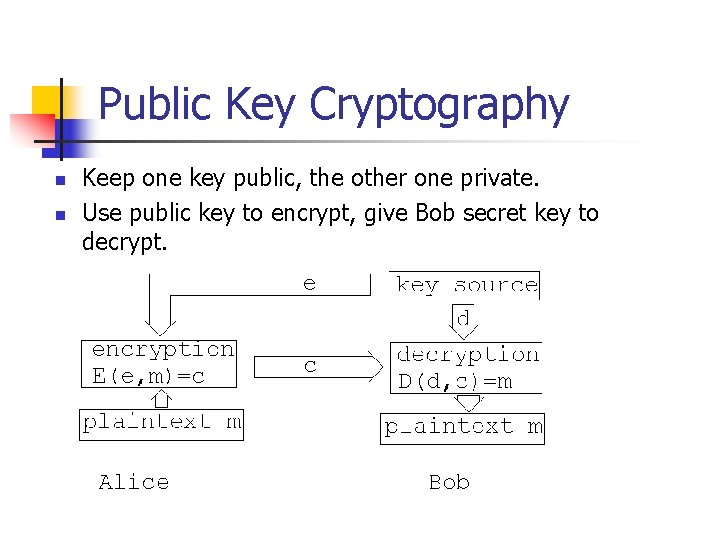
Public Key Cryptography n Asymmetric Key Cryptograpy. n n Use one key for encryption, another for decryption. E(e, . ) encryption with key e D(d, . ) is decryption with key d D(d, E(e, m)) = E(e, D(d, m)) = m for all messages m.

Public Key Cryptography n n Keep one key public, the other one private. Use public key to encrypt, give Bob secret key to decrypt.

Public Key Cryptography n Signing Messages. n n Alice creates a public key pair (e, d) and gives or publishes e. Alice uses private key to calculate s = D(d, m) n n n Pad with zeroes if necessary. Bob uses Alice's public key to decrypt E(e, s) = E(e, D(d, m')) = m. If m is in the format that a signed message has, then Bob accepts the message as truly Alice's.

Public Key Cryptography RSA n n RSA: Rivest Shamir Adleman Choose n = pq, p, q large primes Select e that is coprime to (n)=(p-1)(q-1) Find d such that e d = 1 mod (n). n n n Only computationally feasible if n = pq is known. Public key: (e, n) Private key: (d, n)

Public Key Cryptography RSA n n Encryption with private key. Divide messages into chunks < n Encrypt chunk c as c 1 = ce mod n. Decryption n Calculate c = c 1 d mod n. c 1 d = (ce)d = ced = cx (n)+1 = c Using Euler’s theorem n a (n) = 1 mod n.

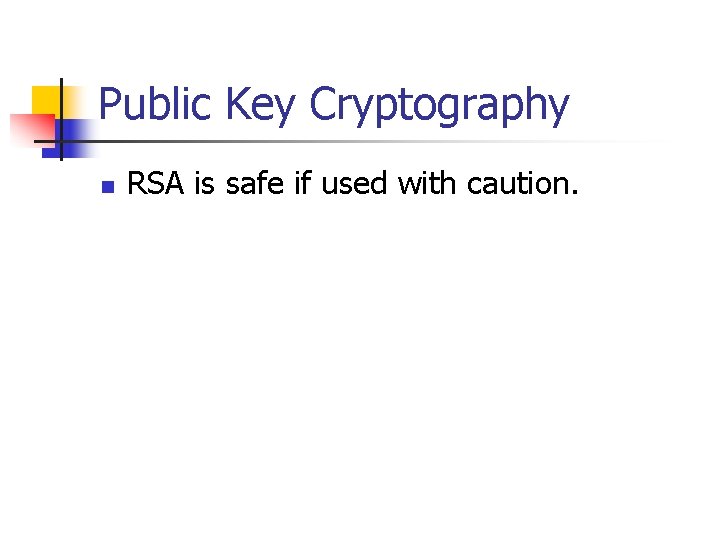
Public Key Cryptography n RSA is safe if used with caution.

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

Message Authentication Code n n Also known as MIC (Message Integrity Code). Append MAC to message. Nobody can change message without changing MAC. Easy to check whether MAC belongs to the message.

Message Authentication Code n Symmetric key MACs using a hash function n n Message Calculate hash value Protect hash value by encrypting it with a secret key. Sender and receiver share the secret key.

Message Authentication Code n ISO 8732 -2: (Banking - Approved Algorithm for Message Authentication) MAC(Message M) { for(i=0; i <= Length. Of. Message; i++) { v = v << 1 e = v XOR w x = [ ((e + y mod 2**32) or A and C) * (x XOR M(i) ] mod 2**32 -1 y = [ ((e + x mod 2**32) or B and D) * (y XOR M(i) ] mod 2**32 -2 } return x XOR y; } where A, B, C, and D are constants, and v and w are determined by the key.

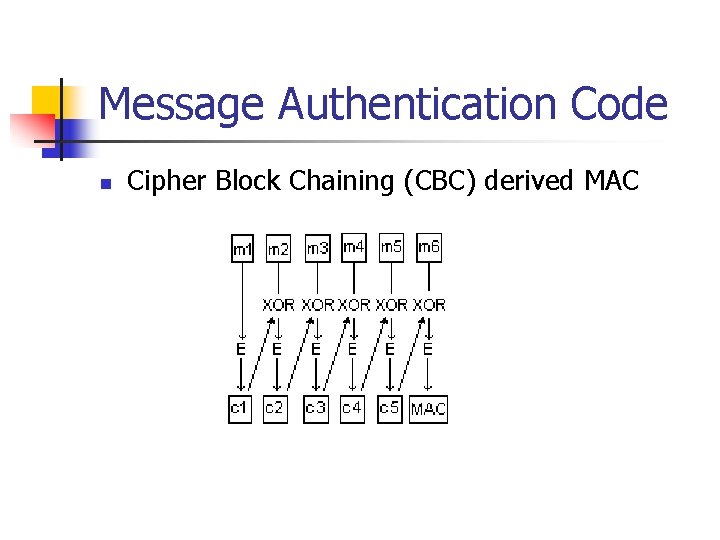
Message Authentication Code n Cipher Block Chaining (CBC) derived MAC

Message Authentication Code n Public Key Message Authentication n If message is small n n Alice encrypts with private key. Bob decrypts with public key. n n If message looks right, it comes from someone who knows Alice’s key. If message is large n n Calculate a digest (hash) of the message Alice encrypts digest with private key. Bob decrypts digest with public key. If digest matches, it comes from Alice.

Message Authentication Code n MD 5 n n n MD 5 was developed by Rivest in 1994. Its 128 bit (16 byte) message digest SHA 1 n n Secure Hash Algorithm developed by NIST published in 1994 produces a 160 -bit (20 byte) message digest

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

Zero Knowledge Proof n n A potentially new way for identification. Challenge-Response n Claimant proves identity to verifier by demonstrating knowledge of a secret. n n E. g. Verifier gives Claimant random number. n Claimant can encode it, thus proving knowledge of a secret key. Password: Forces claimant to give out password.

Zero-Knowledge Proofs n n Interactive proof system that claimant knows secret. But secret is not revealed to verifier or an observer.

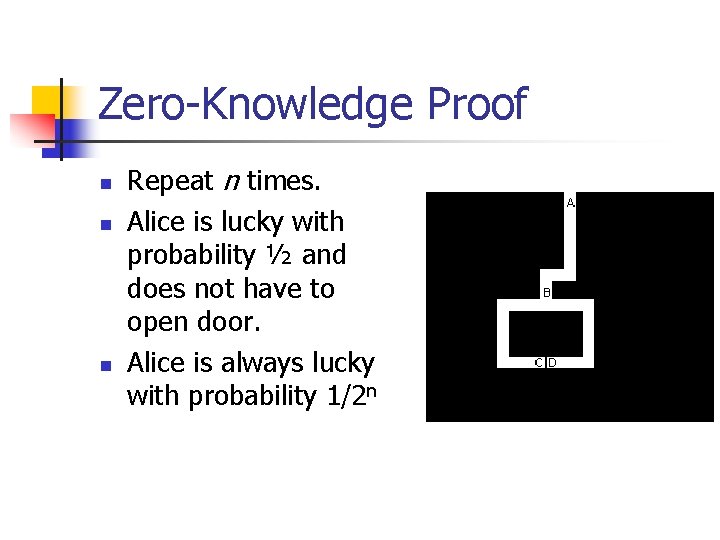
Zero-Knowledge Proof n n Alice wants to convince Bob that she knows the secret word to the door in this cave. But Alice doesn’t want to show Bob how she does it.

Zero-Knowledge Proof n n Bob and Alice walk to A. Alice walks to either C or D. Bob goes to B and cries out “left” or “right” Alice can satisfy the request.

Zero-Knowledge Proof n n n Repeat n times. Alice is lucky with probability ½ and does not have to open door. Alice is always lucky with probability 1/2 n

Zero-Knowledge Proof n Hostile observer cannot distinguish between Alice and Bob playing a charade or Alice knowing how to get through the door.

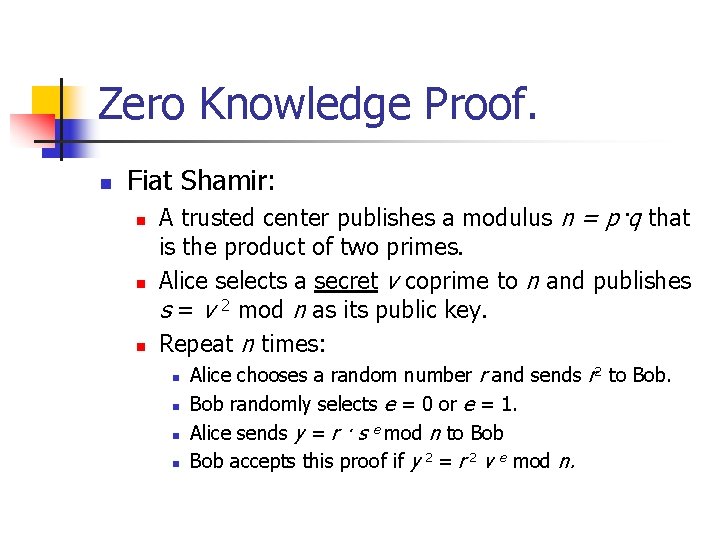
Zero Knowledge Proof. n Fiat Shamir: n n n A trusted center publishes a modulus n = p·q that is the product of two primes. Alice selects a secret v coprime to n and publishes s = v 2 mod n as its public key. Repeat n times: n n Alice chooses a random number r and sends r 2 to Bob randomly selects e = 0 or e = 1. Alice sends y = r · s e mod n to Bob accepts this proof if y 2 = r 2 v e mod n.

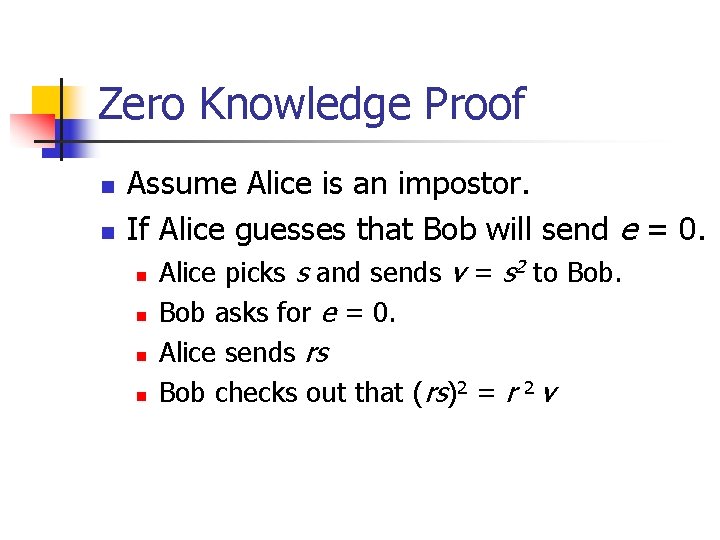
Zero Knowledge Proof n n Assume Alice is an impostor. If Alice guesses that Bob will send e = 0. n n Alice picks s and sends v = s 2 to Bob asks for e = 0. Alice sends rs Bob checks out that (rs)2 = r 2 v

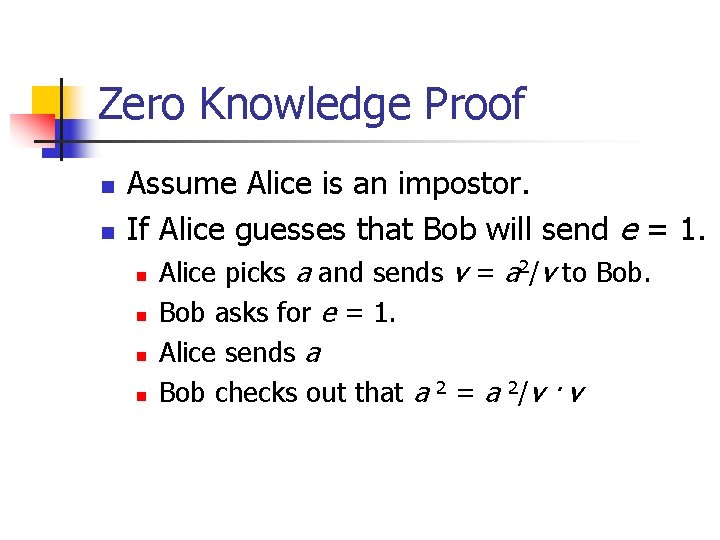
Zero Knowledge Proof n n Assume Alice is an impostor. If Alice guesses that Bob will send e = 1. n n Alice picks a and sends v = a 2/v to Bob asks for e = 1. Alice sends a Bob checks out that a 2 = a 2/v · v

Overview of Cryptography Table of contents n Introduction n Cryptographic Security n One Way Functions n Secret Key Cryptography n Public Key Cryptography n Message Authentication Codes n Zero Knowledge Proofs n Diffie Hellman Key Exchange

Diffie Hellmann n First public key system. Two partners share secret number. No eavesdropper can deduce secret number.

Diffie Hellman n n p large prime g<p n Best choice is a generator modulo p: n n n n n i : n = gi. (p, g) are public. Alice picks secret r. Bob picks secret s. Alice sends gr mod p to Bob sends gs mod p to Alice. Common key is t = (gr)s = (gs)r mod t.

Diffie Hellman n n Snooper needs to derive t from gr and g s. This is computationally equivalent to calculate r from gr mod p.

Diffie Hellman n Man-in-the-middle-attack: n n n n Mallory intercepts communications between Alice and Bob. Alice sends gr to Mallory sends gr’ to Bob sends gs to Mallory sends gs’ to Alice establishes common key grs’ with Mallory. Bob establishes common key gr’s with Mallory. Alice and Bob communicate via Mallory, who reads the traffic (or changes it).

Diffie Hellman n Social defense against this attack: n Alice publicly distributes gr mod p.