COEN 350 Network Security ECommerce Issues ECommerce Issues













![Cookies n Version 0 cookies n Set-Cookie: name=value [; expires=date] [; path=path] [; domain=domain] Cookies n Version 0 cookies n Set-Cookie: name=value [; expires=date] [; path=path] [; domain=domain]](https://slidetodoc.com/presentation_image/ba20092b6211fe5831a30f2211b67a3f/image-18.jpg)


- Slides: 21

COEN 350: Network Security E-Commerce Issues

E-Commerce Issues n Table of Content n n HTTP Authentication Cookies

HTTP Authentication n HTTP n Basically very simple. n n n GET: Used to read a website. POST: Sends data to a website. Some data has security implications n FROM field contains email. n n But not by default, only if browser is configured that way. Used for spiders (crawlers) so that admins can complain about spider behavior.

HTTP Authentication n HTTP n Some data has security implications n AUTHORIZATION field: n n COOKIE field: n n Contains authentication data. See below REFERRER (REFERER) field: n Contains the URL of the page from which the client came.

HTTP Authentication n n n URL allow username / password data. HTTP 1. 1 has two authentication mechanisms. Can use SSL, integrated as HTTPS.

HTTP Authentication n URL Authentication

HTTP Authentication n URL authentication n Can be abused in phishing expeditions.

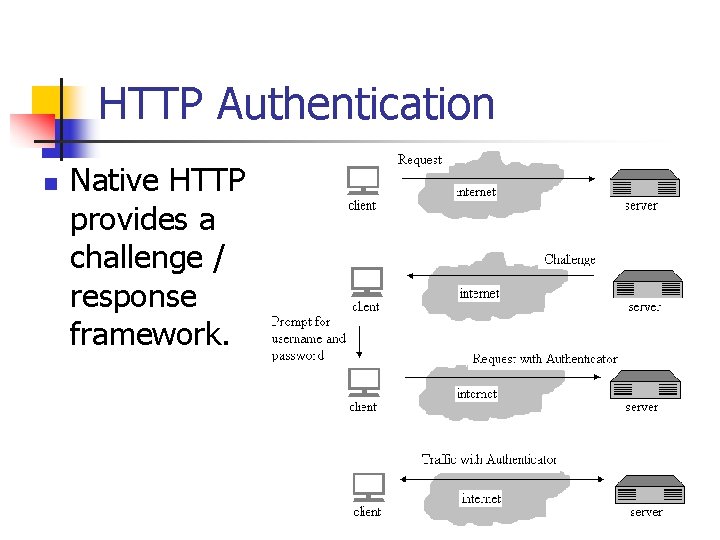
HTTP Authentication n Native HTTP provides a challenge / response framework.

HTTP Authentication n HTTP authenticator: n A base 64 username / password encoding: n n The username and the password in the base 64 encoding Completely insecure. n n n Data is not humanly readable It is easy to decode. Even easier to replay authorization

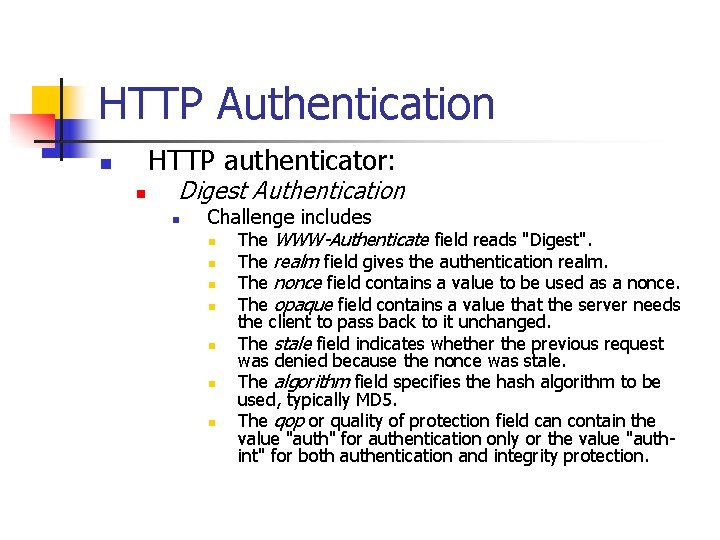
HTTP Authentication HTTP authenticator: n n Digest Authentication n Challenge includes n The WWW-Authenticate field reads "Digest". n The realm field gives the authentication realm. n The nonce field contains a value to be used as a nonce. n The opaque field contains a value that the server needs n n n the client to pass back to it unchanged. The stale field indicates whether the previous request was denied because the nonce was stale. The algorithm field specifies the hash algorithm to be used, typically MD 5. The qop or quality of protection field can contain the value "auth" for authentication only or the value "authint" for both authentication and integrity protection.

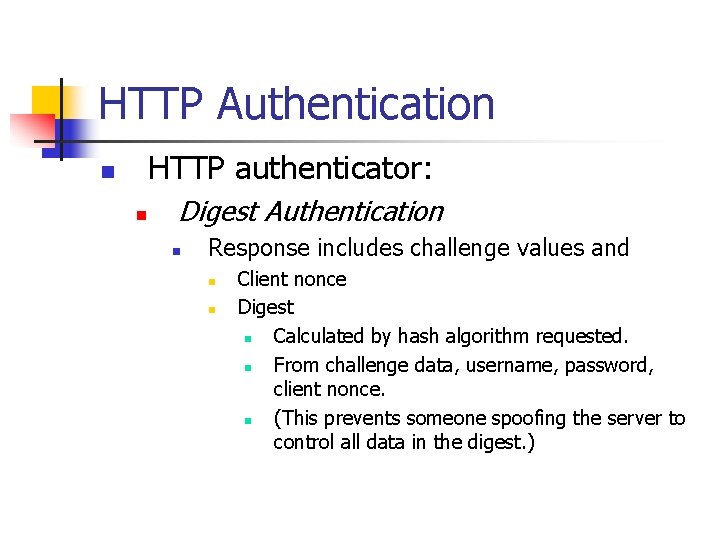
HTTP Authentication HTTP authenticator: n n Digest Authentication n Response includes challenge values and n n Client nonce Digest n Calculated by hash algorithm requested. n From challenge data, username, password, client nonce. n (This prevents someone spoofing the server to control all data in the digest. )

Cookies n HTTP is stateless. n n Good for requesting resources. Bad if server needs to update state based on clients actions. n n n Fat URLs change server state. Cookies maintain state at client site. E-commerce integrates both.

Cookies n How cookies work: n n Client contacts server. Server includes cookie in answer. n n n “Slapping a cookie”. Client stores cookie in cookie jar. Client goes to the same website: n Browser passes unexpired cookies along.

Cookies n Cookies: n Permanent cookies n n Valid for more than a single transaction. Session cookies n Deleted when browser is closed.

Cookies n n Contain domain field. Example: n n Alice visits www. scu. edu slams her with n n Set-cookie: user="Alice"; domain="scu. edu“ Alice visits cse. scu. edu n Browser includes the cookie in header of request because it matches the domain.

Cookies n Domain field n n Specifies to whom cookies will be sent. Limited to specific sites. n n E. g. . com. ft or. edu is not allowed. Path field n Limits cookie sending to a given path = “www. cse. scu. edu/~tschwarz/coen 350_04”

Cookies n Cookie Versions n n Netscape Cookies= Version 0 Cookies RFC 2965 Cookies = Version 1 Cookies n RFC 2965 : HTTP State Management Mechanism.
![Cookies n Version 0 cookies n SetCookie namevalue expiresdate pathpath domaindomain Cookies n Version 0 cookies n Set-Cookie: name=value [; expires=date] [; path=path] [; domain=domain]](https://slidetodoc.com/presentation_image/ba20092b6211fe5831a30f2211b67a3f/image-18.jpg)
Cookies n Version 0 cookies n Set-Cookie: name=value [; expires=date] [; path=path] [; domain=domain] [; secure]. n Secure: only include this cookie with HTTPS (i. e. with SSL) requests.

Cookies n Web Bugs n n Web page can contain URL addressed resources. Web bug: n Typically 1 by 1 image. n n n Hence invisible. Ad from Ad server. Browser goes to the URL specified. Sends along cookies belonging to that URL Referrer field contains the referring URL.

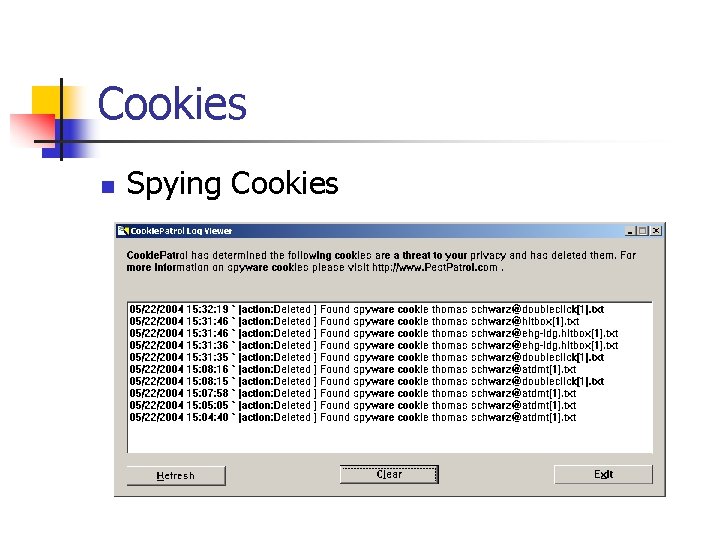
Cookies n Spying Cookies

Cookies n Unprotected Cookies n n Servers need to protect themselves against users altering cookies. Plain text cookies are simple to forge. n n n Change state information such as prices of items in a shopping cart. Gain unauthorized access by changing the userid. Encryption of cookies needs to be understood and strong.