COEN 350 Network Security Authorization Fundamental Mechanisms Access





- Slides: 15

COEN 350: Network Security Authorization

Fundamental Mechanisms: Access Matrix n Subjects Objects (Subjects can be objects, too. ) Access Rights n Example: n n n OS n n n Subjects = Processes Objects = System Resources Access Rights: read, write, execute

Fundamental Mechanisms: Access Matrix n Example: n DBMS n n n Subjects = Users Objects = Relations Access Rights: retrieve, update, insert, delete

Fundamental Mechanisms: Access Matrix n Access Matrix: n n Row for each object Column for each subject Entry is a set of access rights. Later Security Models: n Allow for administrative operations that change the access matrix. n Example: Owner of file can give permissions to others.

Fundamental Mechanisms: Access Matrix n Access Control Lists n n n ACL for each object. Lists all the subjects and their rights. Capabilities n n Capability list for each subject. Contains all the objects and the rights of the subject.

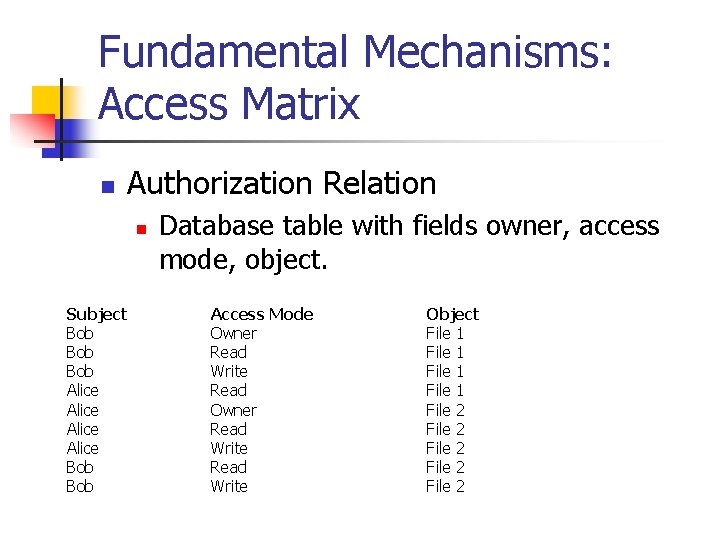
Fundamental Mechanisms: Access Matrix n Authorization Relation n Subject Bob Bob Alice Bob Database table with fields owner, access mode, object. Access Mode Owner Read Write Object File 1 File 2 File 2

Fundamental Mechanisms: Intermediate Controls n n n Access matrix too storage intensive Access matrices make it hard to change policies. Mechanism 1: Groups n n Ideally, all access privileges mediated through group membership. Negative permissions implement exceptions

Fundamental Mechanisms: Intermediate Control n n Protection Rings Example: n Group processes and system resources into four categories n n n n Operating System Kernel Operating System Utilities User Processes Access to an object is only granted to a subject of lower level. Unix only has two levels. Sometimes protection rings have hardware support.

Fundamental Mechanisms: Security Classes n n Each object has a Security class (Security Label) Denning: n Information Control Policy consists of n n n Security Classes “Can flow” relationship Join operation n n Join A B combines rights and restrictions of both. US Do. D Security Levels n n Top Secret Confidential Unclassified

Fundamental Mechanisms Access Control Policies n Discretionary Access Control (DAC) n n Specifies authorization solely based on object and subject identity. Flexible and simple. Difficult to control information flow. (Classical) Mandatory Access Control (MAC) n n n Each user and object has a security level. Security level reflects trust that user will not pass information to users with lower level clearance. Access to an object based on security level.

Fundamental Mechanisms Access Control Policies n (Refined) Mandatory Access Control (MAC) n n Security Levels and Compartments. Example: n n n CRYPTO for cryptographic algorithms. COMSEC for communication security. Possible to have top secret clearance in CRYPTO and unclassified clearance in COMSEC Discretionary policies typical in low security (academic) environments. Mandatory policies typical in high security (military) environments. Neither policy adequate for commercial systems.

Fundamental Mechanisms Access Control Policies n Role Based Access Control (RBAC) n n n Regulate user’s access to information based on the activities the users execute in the system. “Role” is a set of actions and responsibilities associated with a particular working activity. Access based on role, not identity of user.

Fundamental Mechanisms Access Control Policies n Role Based Access Control (RBAC) n User authorization is broken into two tasks: n n n Roles can be hierarchical n n n Granting roles to users Granting rights to roles Engineers inherent employee rights. User can login with the least privilege for a set of particular tasks. Roles make it easier to enforce separation of duties: “No single user can subvert the system by herself/himself. ”

Covert Channels n n A mechanism to circumvent automatic confinement within a security perimeter. Example: n n Person with TOP SECRET clearance runs (inadvertently) Trojan horse has free access to files in the compartment. Trojan horse cannot write down to an unclassified file. But: Trojan horse can do things that are visible from the outside and thus send contents of TOP SECRET files through a covert channel. n n T. H. either runs or waits. System load will vary. Small bandwidth channel. T. H. can or cannot use shared resources. To send a bit, T. H. fills up the printer line to send 1 bit, or empties it for a 0 bit.

UNIX Woes: SUID programs n n n Programs can execute the setuid system call. Executable runs as if executed by user. Sendmail uses setuid to implement email. User can cause programs to run as root with input they provide. Favorite targets of buffer overflow attacks.