COEN 350 Network Security Authentication Authentication n n
































- Slides: 35

COEN 350: Network Security Authentication

Authentication n n Between human and machine Between machine and machine

Human Machine Authentication n Authentication protocols are based on n What you know. n n What you have. n n Physical key, smart card. What you are. n n E. g. password, pass-phrase, (secret key, private key). Biometrics. Where you are. n E. g. trusted machine, access to room, …

Authentication n Passwords n n Predate computers. As do some attacks (stealing, guessing) n n Older cell phone technology transmits originating number with a password. Password good, call goes through. Eavesdropper receives phone number – password combination. Eavesdropper can now clone the phone.

Authentication n Password Attacks n Guessing n On-line n n n Off-line n n n Time consuming. Authentication attempts are usually logged. Can detect attack long before it is likely to succeed. Can disrupt the attack. Attacker needs to steal relevant data from which password(s) can be determined. Attacker can use arbitrary amount of computing power. Capturing Passwords n n Eavesdropping Login Trojan Horse

Authentication n Passwords are stored n n On each server Alice uses. Centrally: Authentication Storage Node: n n Each server retrieves the information when it wants to authenticate Alice. Centrally: Authentication Facilitator Node: n Each server takes Alice’s data and password and goes to the AFN.

Authentication n Password can be stored n Unencrypted n n n Implicitly as hashes of passwords n n n Simple Dangerous As in UNIX, VMS Encrypted Hashed and Encrypted

Authentication n Example: Network Information Service n n Directory service is the authentication storage node. Stores hashed passwords of users. Typically, hashed passwords list is world readable (by claiming to be a server). NIS authentication storage node is

Authentication n Passwords for machine – machine communication can be made difficult to guess. n n n Arbitrary length Truly random choice of characters. Human-machine passwords n n Guessable Subject to dictionary attack.

Authentication n Dictionary attack n n n Most passwords are natural language words. Or derived from natural language words. Guess the language. Use a dictionary to try out all words in the language. Start with common passwords first. Replace a single character in a word, attach a random character, etc.

Authentication n n Brute-Force Attack Generate all possible password. n Sometimes make assumptions on the alphabet n n only printable characters on a key-board

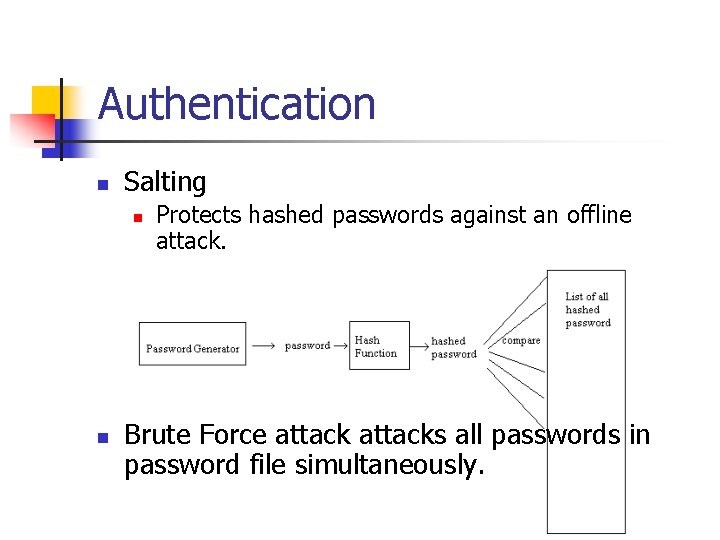
Authentication n Salting n n Protects hashed passwords against an offline attack. Brute Force attacks all passwords in password file simultaneously.

Authentication n n Salting Store a salt with each password Hash depends on salt and password. Use different salts for different passwords. Store salt with password.

Authentication n Salting n Brute force attack, dictionary attack can only attack a single password.

Authentication n Passwords are compromised: n By obtaining password file. n Safeguard by n n n Hashing and Salting Encryption By eavesdropping on an exchange n Use one-way passwords: n Lamport Hash

Authentication n Address Based n Common in early UNIX n Rtools: n n . rhosts n In user home directory n (Computer, Account) pairs n These pairs are allowed access to the user’s account /etc/hosts. equiv n n List of network addresses of “equivalent” machines Account name on A is equivalent to account name on B. n Users have to have identical account names.

Authentication n Addressed based authentication threatened by n Access escalation n Attacker gains access to one hosts. Access cascades to equivalent hosts / rhosts. Spoofing addresses n n Very easy to spoof source address. Harder to intercept traffic back.

Authentication n Ethernet network address impersonation n n Easy on the same link. Hubs do not protect. Switches can be spoofed through the ARP protocol. Routers are harder to fool, but can be attacked and provided with misleading routing data.

Authentication n Cryptographic authentication n Alice proves her identity to Bob by proving to Bob that she knows a secret. n n n Hashes Secret key cryptography Public key cryptography.

Human Machine Authentication n Initial password distribution to humans n Pre-expired, strong passwords n n Through mail Derivable from common knowledge n Student ID

Human Machine Authentication n Authentication Token n Possession of the token proves right to access. n Magnetic stripe as on credit cards. n n Demand special hardware Can be lost or stolen n n Harder to reproduce “Impossible” to guess Add pin or password protection Are not safe against communication eavesdropping and forging

Human Machine Authentication n Authentication Token n Smart Card. n n Needs to be inserted in a smart card reader. Card authenticates to the smart card reader. n n PIN protected smart cards. n Stops working after a number of false PINs. Cryptographic challenge / response cards n Card contains a cryptographic key. n Authenticating computer issues a challenge. n Card solves the challenge after PIN is entered. n Harder to crack than PIN protected smart cards because key is never revealed.

Human Machine Authentication n Authentication Token n Smart Card. n Readerless smart card (Cryptographic calculator) n n n Communicates with owner through mini-keyboard and display. Authenticating computer issues a challenge to Alice types in challenge into readerless smart card. Readerless smart card solves the challenge. n After Alice puts in her password. Alice transfers the answer to the computer.

Human Machine Authentication n Biometrics n n n n Retinal scanner Fingerprint reader Face recognition Iris scanner Handprint readers Voiceprints Keystroke timing Signatures

Strong Passwords n Goal: n Eavesdropper does not obtain enough information to do an off-line verification of password guesses.

Strong Passwords n Bob (Machine) and Alice (Human) share a “weak” secret W. n n W is a hash of Alice’s password. Bob knows W because he stores it.

Strong Passwords: EKE Alice Bob Alice and Bob share a weak secret W = f (password) Alice chooses a random Bob chooses a random b and number a. challenge C 1. Shea sends: Bob encrypts this message and finds. He that Alice has solved his challenge C 1. sends Both Bob and Alice use their knowledge ofa}W to encrypt their Alice, W { g Finally, authenticates himself proves his knowledge of W by Alice then. Bob proves her knowledge of to W Alice. by her. He ability ab. to calculate K. She b mutual messages. They both calculate K = g , C}1}able his picks knowledge of K, which proves to correctly encrypt Alice’s also a challenge C 2 andhesends KW {by C{1 gbeing , C to Bob. 2 challenge C 2. He sends K {C 2 } to Alice.

Strong Passwords: EKE n A bad implementation of EKE allows an eavesdropper to exclude passwords. n Assume that we calculate in the field of number modulo p, p Nr of Exchanges Chance of false password surviving 1 2 n n 5 10 n 20 n 50 n a prime. Then ga and gb are both 80% m bit numbers smaller than p. 64% Attacker maintains a dictionary of possible passwords and observes many authentication 33% rounds. If W is in the dictionary, he encrypts Alice’s round 1 message M. If W -1{M } > p, then 10% attacker excludes W. 1. 2% Chance of excluding a false password W is 2 m – p / p. If this chance is about 80%, then 50 rounds determine the 0. 0014% password out of a normal dictionary.

Strong Passwords n Simple Password Exponential Key Exchange: SPEKE n Like EKE, but n n Transmit W a and W b and agree on key K. Has a related vulnerability: n W shares algebraic properties with W a. n Generator, perfect square

Strong Passwords n PDM: Password Derived Moduli n n Key Idea: Pick the field based on the password. Diffie Hellman exchange based on p = f (password) with base 2: n n n Alice to Bob: Alice, 2 a mod p. Bob to Alice: 2 b mod p. Prove knowledge of K = 2 ab mod p.

Strong Passwords n n Augmented Strong Password Protocols Prevent someone who has stolen the server data Strong base. Passwords to impersonate a user. n Server does not store the password, but a quantity sufficient to evaluate it. n Augmented EKE: n http: //citeseer. ist. psu. edu/bellovin 93 augmented. html

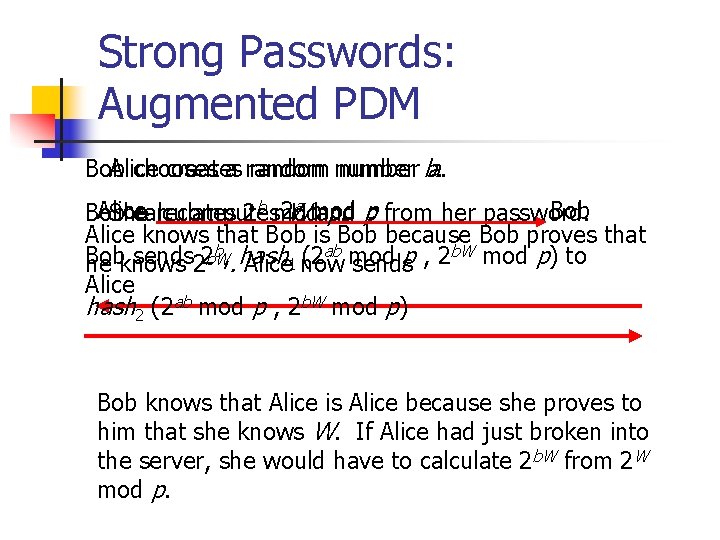
Strong Passwords n Augmented PDM n Server Information Creation n Alice has password pssw Alice sends to Bob n p = f (pssw) [this is a prime] n W = hash (pssw) [one-way hash] Bob stores: n Alice, p, W,

Strong Passwords: Augmented PDM Bob Alice chooses creates a random number ba. . a mod p Alice 2 W Bob She calculates recomputes 2 b mod and p. from her password. Alice knows that Bob is Bob because Bob proves that b, hash (2 ab mod p , 2 b. W mod p) to Bob sends 2 b. W he knows 2. Alice 1 now sends Alice hash 2 (2 ab mod p , 2 b. W mod p) Bob knows that Alice is Alice because she proves to him that she knows W. If Alice had just broken into the server, she would have to calculate 2 b. W from 2 W mod p.

Strong Passwords n Secure Remote Password n n RFC 2945 Bob stores {Alice, g. W mod p}, where W = f (passwd).

Strong Passwords SRP Alice creates random a and sends ga to Bob creates random b, challenge CBOB and 32 b number u. Bob sends gb + g. W mod p, u, CBOB to Alice. Both calculate K = g b(a+u. W) mod p Alice sends K {CBob}, CAlice to Bob sends K {CAlice} to Bob.