COEN 350 Mobile Security Wireless Security n Wireless

COEN 350 Mobile Security

Wireless Security n Wireless offers additional challenges: n n Physical media can easily be sniffed. War Driving n Legal? n U. S. federal computer crime statute, Title 18 U. S. C. 1030, n Crime to knowingly access a computer used in interstate or foreign communication "without authorization" and obtain any information from the computer. n Crime to access a computer without authorization with "intent to defraud" to obtain "anything of value. " n But not if "the object of the fraud and the thing obtained consists only of the use of the computer and the value of such use is not more than $ 5, 000 in any 1 -year period. "

Wireless Security n Wireless offers additional challenges: n n Physical media can easily be sniffed. Mobile computing needs to preserve battery power. n n Calculations cost more on a mobile platform. Especially important for sensor networks

Wireless Security: Attackers Perspective n Knowing the Threat n Targets of opportunity n Goal is n n n Targeted attacks n n Internet access. Easy pickings. Targets assets valuable enough. Internal attackers n n Most Dangerous Can open an unintentional security hole

IEEE 802. 11 n Wired Equivalent Privacy (WEP) Protocol n Based on a shared secret k. n n n Distributed out of band. Uses CRC for internal integrity protection. Uses RC 4 to encrypt network traffic.

WEP Protocol
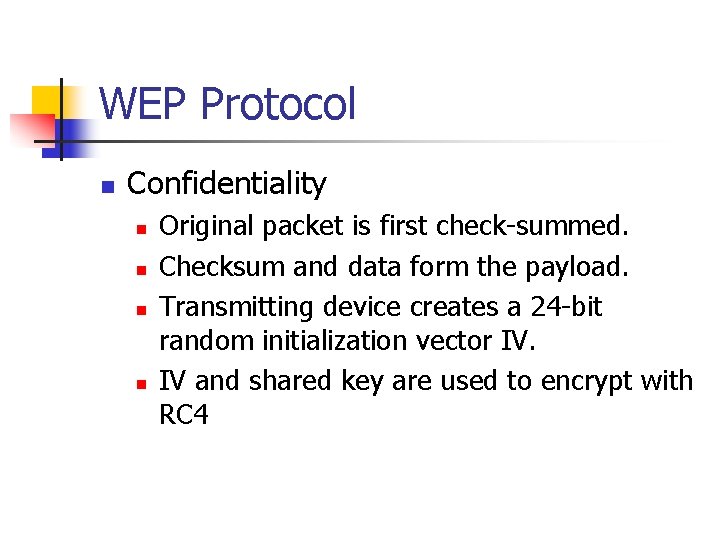
WEP Protocol n Confidentiality n n Original packet is first check-summed. Checksum and data form the payload. Transmitting device creates a 24 -bit random initialization vector IV. IV and shared key are used to encrypt with RC 4
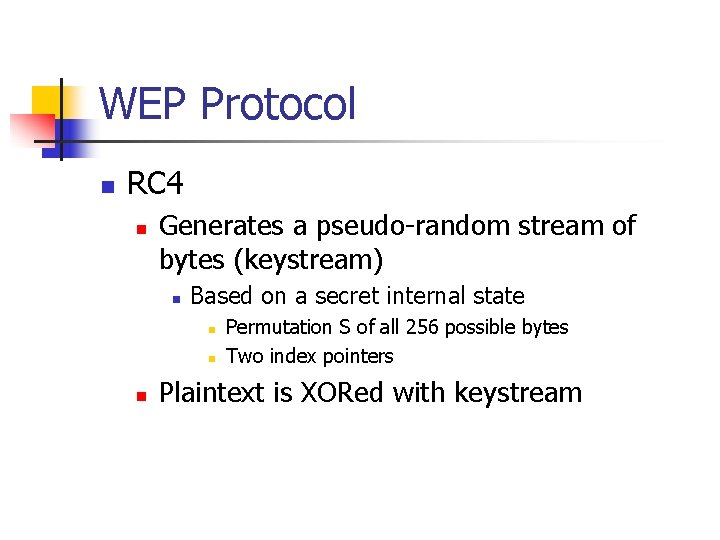
WEP Protocol n RC 4 n Generates a pseudo-random stream of bytes (keystream) n Based on a secret internal state n n n Permutation S of all 256 possible bytes Two index pointers Plaintext is XORed with keystream

WEP Protocol n RC 4 n Key Scheduling Algorithm (KSA) n Initializes S based on a key for i from 0 to 255 S[i] : = i j : = 0 for i from 0 to 255 j : = (j + S[i] + key[i mod keylength]) mod 256 swap(S[i], S[j])
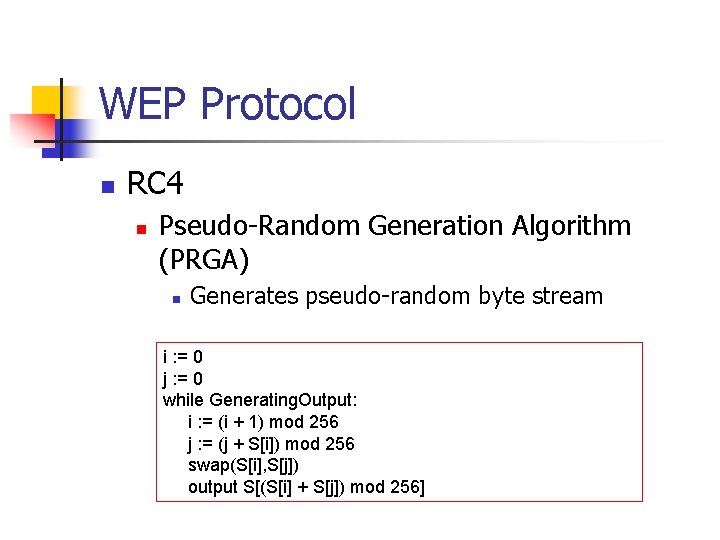
WEP Protocol n RC 4 n Pseudo-Random Generation Algorithm (PRGA) n Generates pseudo-random byte stream i : = 0 j : = 0 while Generating. Output: i : = (i + 1) mod 256 j : = (j + S[i]) mod 256 swap(S[i], S[j]) output S[(S[i] + S[j]) mod 256]

WEP Protocol n RC 4 n Known weaknesses n Keystream slightly biased n n Fluhrer & Mc. Grew attack can distinguish keystream from random stream given a GB of input. Fluhrer, Mantin, Shamir: statistics for output of the first few bytes of output keystream are non-random, leaking information about key.

WEP Protocol n Authentication n n Station associating with access point needs to authenticate itself. Both exchange the type of authentication that is accepted. n n Open: Just identification between station and AP Shared Secret: Participants send nonces to each other, encrypt the nonce using WEP (and the shared secret key), and verify the other’s response.

WEP has no key management n n Everyone allowed to have access to a wireless network has the same key. Anyone with the key can read ALL traffic.

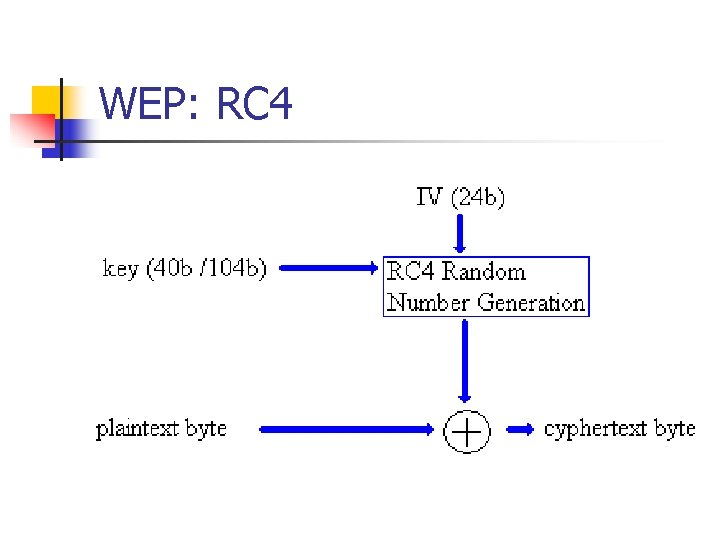
WEP: RC 4 n n RC 4 uses the key and the IV to produce a stream of pseudo-random bytes. Calculates cipher text from plaintext by XORing the pseudo-random stream with the plain-text.
WEP: RC 4

WEP: Attacks on RC 4 n Dictionary Attack n n n Build database: 224 different IVs Build a database of 224 streams of MTU bytes (2, 312 B) for each different IV. Takes < 40 GB storage. XOR two entries with the same IV. n n Result are the two plaintexts XORed. Natural language text has enough redundancy to decrypt the XOR of two text streams.

WEP: Attacks on RC 4 n Dictionary Attack n n n Many packages can be completely or partially guessed. XORing guessed plaintext and captured cipher gives pseudo-random byte stream for a given IV. Some implementations reset IVs poorly. n This simplifies dictionary attacks.

WEP: Attacks on RC 4 n Injection Attack n n Attacker creates packets on the wireless connection. Attacker XORs plaintext and cipher. n Builds Pseudo-Random Stream database indexed by IV.

RC 4 Fluhrer, Mantin, Shamir Attack n First few bits of several thousand messages reveals key. n Based on an analysis of the RC 4 code. n Originally kept secret, but later leaked on the internet.
RC 4 Fluhrer, Mantin, Shamir Attack n Key Scheduling Algorithm n n Sets up RC 4 state array S S is a permutation of 0, 1, … 255 Output generator uses S to create a pseudo-random sequence. First byte of output is given by S[S[1]+S[S[1]]]. n First byte depends on n {S[1], S[S[1]+S[S[1]]}
RC 4 Fluhrer, Mantin, Shamir Attack n Key Scheduling Algorithm n First byte of plain text package is part of the SNAP header n n 0 x. AA for IP and ARP packages 0 x. FF or 0 x. E 0 for IPX Guessing the first byte is trivial Some IVs are vulnerable: “resolved” n n n n (Key. Byte+3, 0 x. FF, *) Plus some more Easy to test whether an IV is vulnerable. Search for vulnerable IVs. They leak key bytes probabilistically. Large number of packets does it.

RC 4 Fluhrer, Mantin, Shamir Attack n n Optimization needs about 5, 000 to 1, 000 packages. Counter-measures: n n Change key frequently. Change IV counters to avoid bad IVs.
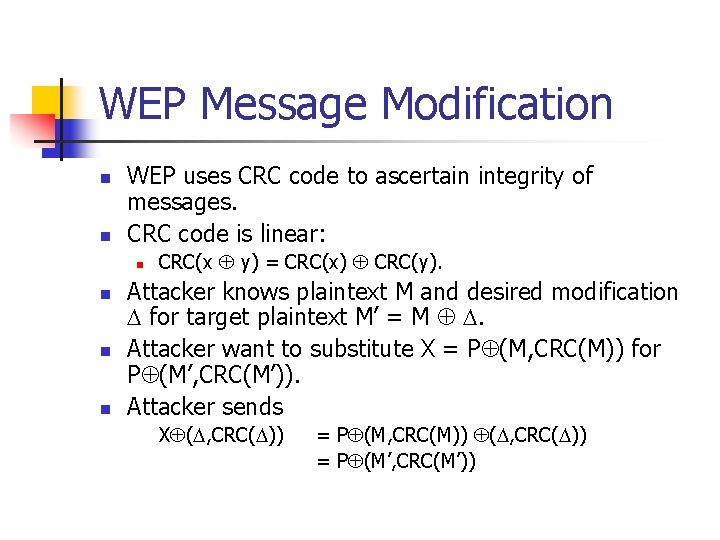
WEP Message Modification n n WEP uses CRC code to ascertain integrity of messages. CRC code is linear: n n CRC(x y) = CRC(x) CRC(y). Attacker knows plaintext M and desired modification for target plaintext M’ = M . Attacker want to substitute X = P (M, CRC(M)) for P (M’, CRC(M’)). Attacker sends X ( , CRC( )) = P (M, CRC(M)) ( , CRC( )) = P (M’, CRC(M’))

Wireless Insecurity Problems n Wi. Fi card software allows users to change the MAC address.

Wireless Security n Casual user, low yield traffic n n WEP is good enough. Enterprise, Commercial n Combine WEP with higher order security n n n SSH VPN IPSec

WPA n Created by Wi. Fi Alliance n n Certification started April 2003 Uses 802. 1 X authentication server n n Distributed different keys to each user. Can also be used in “pre-shared key” (PSK) mode n n Every user uses the same passphrase. Called WPA Personal
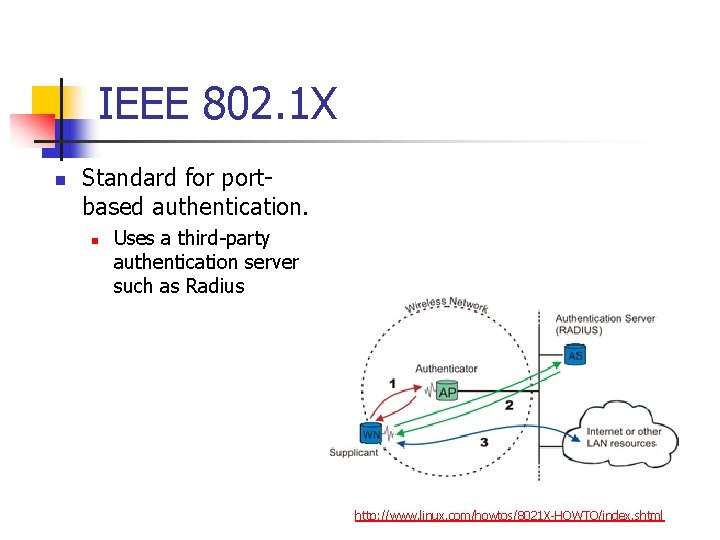
IEEE 802. 1 X n Standard for portbased authentication. n Uses a third-party authentication server such as Radius http: //www. linux. com/howtos/8021 X-HOWTO/index. shtml
WPA n Protocol changes over WEP n CRC is replaced by “Michael” MIC. n n n MIC now includes a frame counter, preventing replay attacks. Payload bit flipping is now impossible. Data encryption still uses RC 4, but now n Prevents key recovery attacks on WEP by using n n n 128 b Key 48 b Initialization vector Temporal Key Integrity Protocol (TKIP) changes key dynamically.

TKIP n Temporal Key Integrity Protocol n Ensures that every data packet has its own encryption key.
802. 11 i n n n Uses AES instead of RC 4. Subset published as WPA 2 Uses 802. 1 X authentication
Protocol Layers n WEP n n n Privacy only. Very elementary security. WPA n Temporal Key Exchange Protocol n n AES: Advanced Encryption Standard n n n 802. 11 i Military grade encryption, replaces DES 802. 1 X n n Fixes WEP that scrambles keys between packages and adds a secure message check. General purpose and extensible framework for authentication users and generating / distributing keys. Simple Secure Network (SSN) n Recipe for authentication based on 802. 1 X
- Slides: 31