COEN 350 IPSec SSL SSH Communication Security n



















































- Slides: 71

COEN 350 IPSec, SSL, SSH,

Communication Security n Decision: What Layer? n Implemented at application level n n n Application change OS does not change Implemented at TCP/IP level n n OS changes Applications do not change

Communication Security n Session Key Establishment n Threat: Session Hijacking n Counter-measure: Encryption n n Use Session key for each session Session key needs to be unpredictable n Implementation of SSL used time, process id, parent process id to concoct session key n Attacker could narrow search space to about 30 b of key. Both partners should contribute to session key Threat: Packet replay n Counter-measure: Sequence number

Communication Security n Perfect Forward Security n Threat: n n n Eavesdropper captures traffic. Eavesdropper later acquires master key for both communicants. PFS: Eavesdropper can still not encrypt data. n n Diffie Hellman key exchange provides PFS Counter-example: n n n Encrypting all messages with a public key of partner Kerberos n Session key is inside ticket, encrypted with long-term secret key Sending session key encrypted with public key

Communication Security n Escrow-foilage n n Alice and Bob have to give their private keys to an escrow agency. Passive listener with those keys can still not decrypt traffic between Alice and Bob

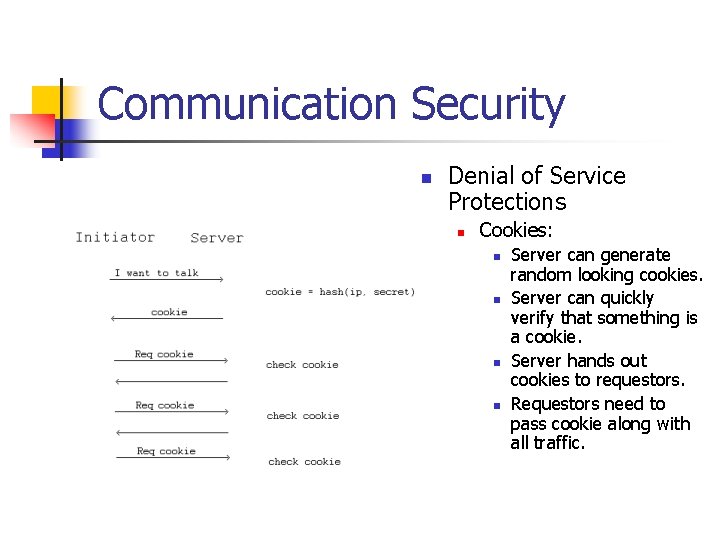
Communication Security n Denial of Service Protections n Cookies: n n Server can generate random looking cookies. Server can quickly verify that something is a cookie. Server hands out cookies to requestors. Requestors need to pass cookie along with all traffic.

Communication Security n Denial of Service Attack Protection n Puzzles n n n Server creates puzzles Client needs to solve puzzle in order to get work done. Client does more work than server DOS attack is harder

Communication Security n Replay prevention n n Use session keys Session Resumption n Goal is avoiding costly initial encryption exchange n Lotus Notes: n n n Server has secret that changes once a month. Server sends hash(client-name, server-secret) to client after authentication. Session key is calculated from this hash plus nonces.

Communication Security n Negotiation of crypto-parameters n Systems evolve: n n n Crypto-systems become breakable Newer crypto-systems demand larger resources. Potential Security Flaw n Negotiating in bad faith, insisting on breakable crypto-suites.

Communication Security n Endpoint identifier hiding n n n Establish secure tunnel (via Diffie Hellman) first. Then authenticate. Man-in-the-middle gets caught in the second step. n Can only find out one identity.

IPSec n RFC 1636 identified key areas where the internet needs to be made more secure. n n n Spoofing: Creating packets with false addresses. Eavesdropping / packet sniffing. True for both IPv 4 and IPv 6.

IPSec n n n Implemented below the transport layer. No application needs to be rewritten. Is part of the OS. Applications TCP IPsec IP lower layers

IPSec n n Provides confidentiality for IP connections Allows implementation of access policies Authenticates source IP addresses But not users.

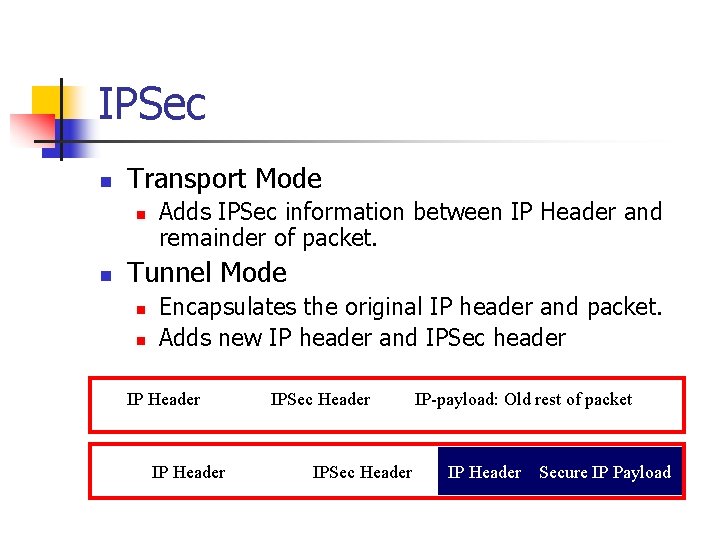
IPSec n Transport Mode n n Adds IPSec information between IP Header and remainder of packet. Tunnel Mode n n Encapsulates the original IP header and packet. Adds new IP header and IPSec header IP Header IPSec Header IP-payload: Old rest of packet IP Header Secure IP Payload

IPSec n n An IPSec packet in tunnel mode completely encapsulates the payload. IP Header is either an n n S e c I u P r I S AH: Authentication Header ESP: Encapsulating Security Payload that tells the user which Security Association to use.

IPSec n Developed by the Internet Engineering Task Force IETF n n n n Architecture ESP (Encapsulating Security Payload) AH (Authentication Header) Encryption Algorithm Authentication Algorithm Key Management DOI (Domain of Interpretation) (How to fit the work together. )

IPSec n Security Association n n Cryptographically protected connection. Paradigm to manage authentication and confidentiality between sender and receiver. Unidirectional. IPSec header contains SPI (Security Parameter Index) that identifies the security association. n Allows partner to look up the necessary data such as the key in SA database.

IPSec n Security Association Database n When X transmits to Y in IPSec, X looks up Y in the SA database. n n Provides key Provides SPI n n Security Parameter Index Provides algorithms to be used Provides sequence number When Y receives a transmission, Y uses the SPI and the destination address to find the SA.

IPSec n Security Policy Database n Specifies what to do with packets: n n Dropping Forwarded and accepted without IPSec protection Forwarded and protected by IPSec Decision based on fields in the IPsec packet.

IPSec n n Two types of IPsec headers. AH n n Authentication header. Provides integrity protection only. Allows firewalls to peek at TCP ports. ESP n Encapsulating Security Payload n n Optional integrity protection Optional encryption

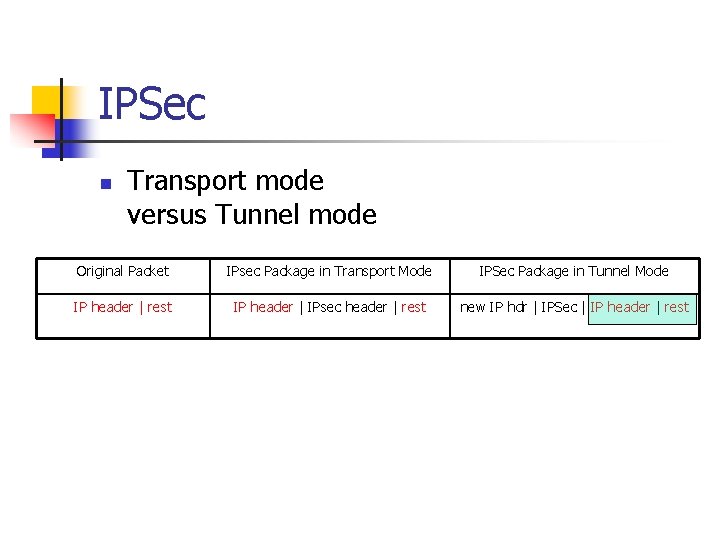
IPSec n n Two modes Transport mode n n Adding IPsec information between IP header and remainder of package. Tunnel mode n Keeps the original IP packet intact, but put it into a new packet with new IP header and IPsec data.

IPSec n Transport mode versus Tunnel mode Original Packet IPsec Package in Transport Mode IPSec Package in Tunnel Mode IP header | rest IP header | IPsec header | rest new IP hdr | IPSec | IP header | rest

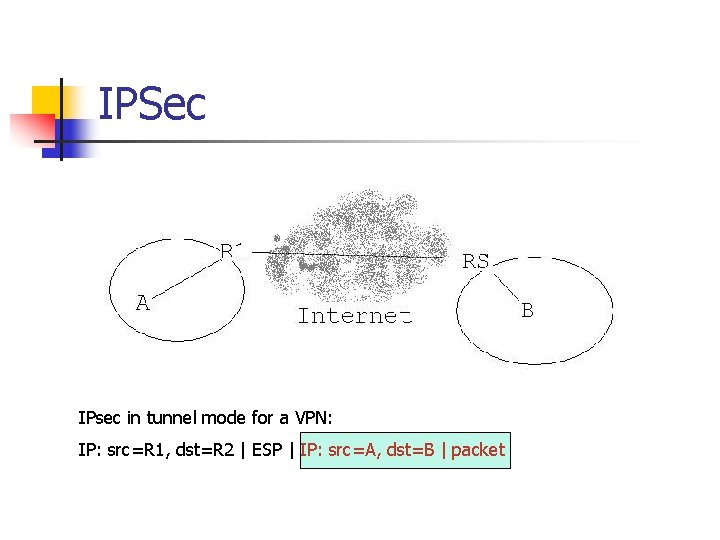
IPSec IPsec in tunnel mode for a VPN: IP: src=R 1, dst=R 2 | ESP | IP: src=A, dst=B | packet

IPSec n NAT n n Network address translation NAT boxes takes IP traffic from the outside. Based on port number, repackages packet to be send to an internal address and vice versa. Allows organization to make to do with few IP addresses.

IPSec n NAT n Have difficulties with incoming calls to dynamic hosts. n n n Need to maintain routing table dynamically. Usually, need to be application-aware. Function as a limited, package-based firewall.

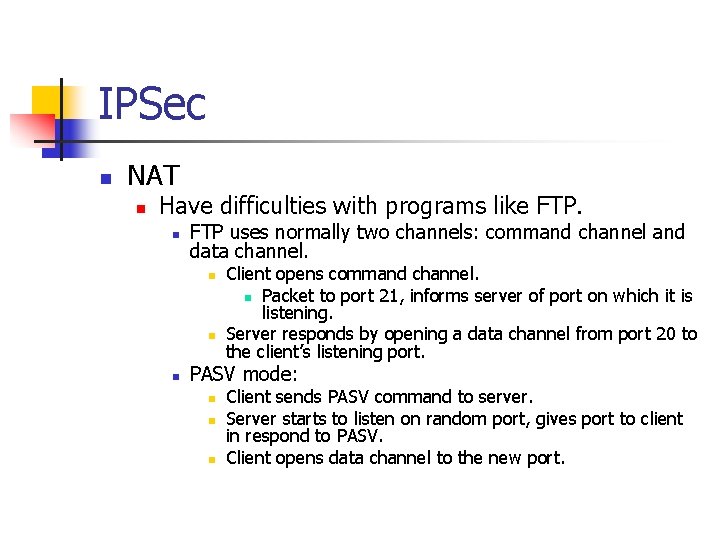
IPSec n NAT n Have difficulties with programs like FTP. n FTP uses normally two channels: command channel and data channel. n n n Client opens command channel. n Packet to port 21, informs server of port on which it is listening. Server responds by opening a data channel from port 20 to the client’s listening port. PASV mode: n n n Client sends PASV command to server. Server starts to listen on random port, gives port to client in respond to PASV. Client opens data channel to the new port.

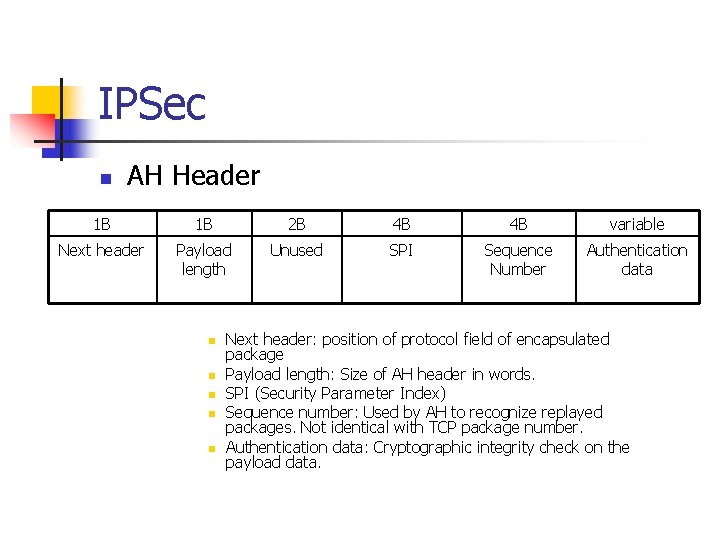
IPSec n AH Header 1 B 1 B 2 B 4 B 4 B variable Next header Payload length Unused SPI Sequence Number Authentication data n n n Next header: position of protocol field of encapsulated package Payload length: Size of AH header in words. SPI (Security Parameter Index) Sequence number: Used by AH to recognize replayed packages. Not identical with TCP package number. Authentication data: Cryptographic integrity check on the payload data.

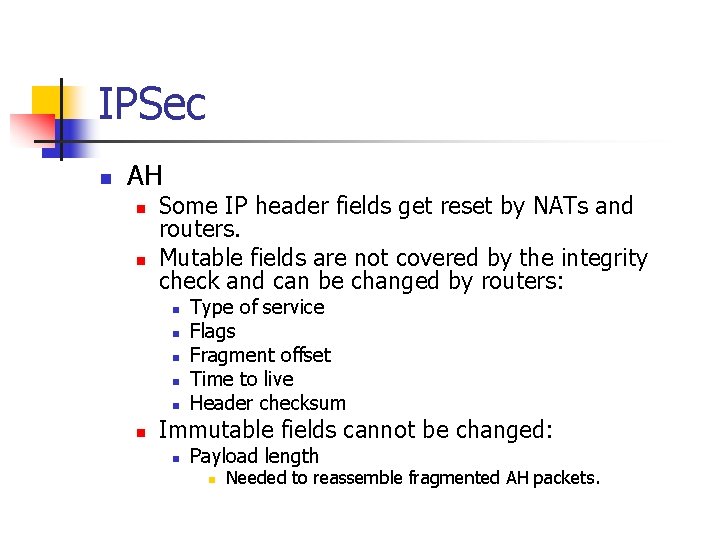
IPSec n AH n n Some IP header fields get reset by NATs and routers. Mutable fields are not covered by the integrity check and can be changed by routers: n n n Type of service Flags Fragment offset Time to live Header checksum Immutable fields cannot be changed: n Payload length n Needed to reassemble fragmented AH packets.

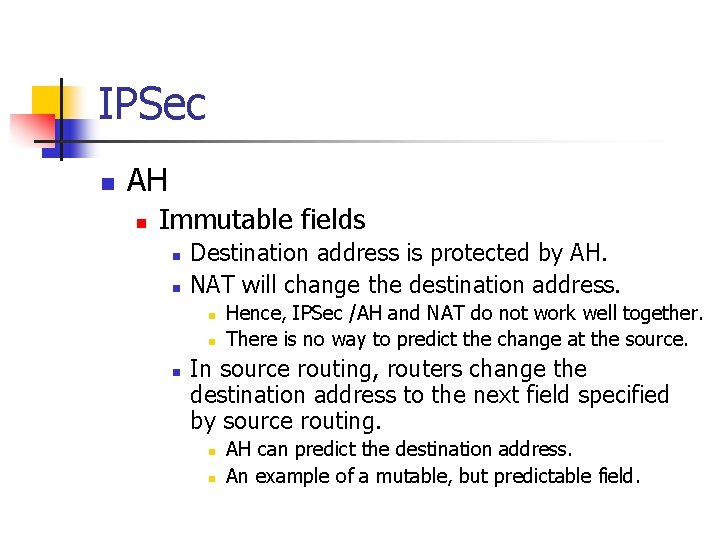
IPSec n AH n Immutable fields n n Destination address is protected by AH. NAT will change the destination address. n n n Hence, IPSec /AH and NAT do not work well together. There is no way to predict the change at the source. In source routing, routers change the destination address to the next field specified by source routing. n n AH can predict the destination address. An example of a mutable, but predictable field.

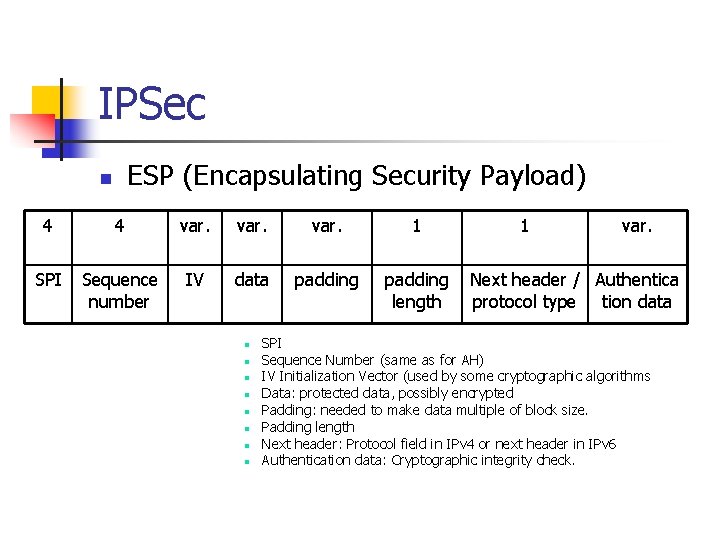
IPSec ESP (Encapsulating Security Payload) n 4 4 var. 1 SPI Sequence number IV data padding length n n n n 1 var. Next header / Authentica protocol type tion data SPI Sequence Number (same as for AH) IV Initialization Vector (used by some cryptographic algorithms Data: protected data, possibly encrypted Padding: needed to make data multiple of block size. Padding length Next header: Protocol field in IPv 4 or next header in IPv 6 Authentication data: Cryptographic integrity check.

IPSec n n n AH protects the IP header itself. ESP protects everything beyond the ESP header. Hence: AH provides additional (but useless? ) protection. n AH is less likely to fall under export restrictions.

IPSec n TF-ESP (Transport-friendly ESP) n Proposal to copy fields of interest of the original header in clear. n Firewalls and routers can look at these information. n n n Potential for information leak. Firewalls should not look at any data above layer 3. n But of course, they now do. IPSec protection is end-to-end, and intermediate routers / firewalls cannot trust the cleartext copies of these fields.

IPSec: IKE n Internet Key Exchange n Needed for n n mutual authentication to set up an SA … Compromise based on Photuris and Skip

Photuris n Uses Cookies n n n Different from web browser cookies. When Alice connects to Bob, Bob chooses a cookie and sends it to Alice. Bob only honors further requests from Alice with the cookie. Foils very simple Do. S attacks. To keep cookie stateless, the cookie is a function of Alice’s address and a secret known by Bob only.

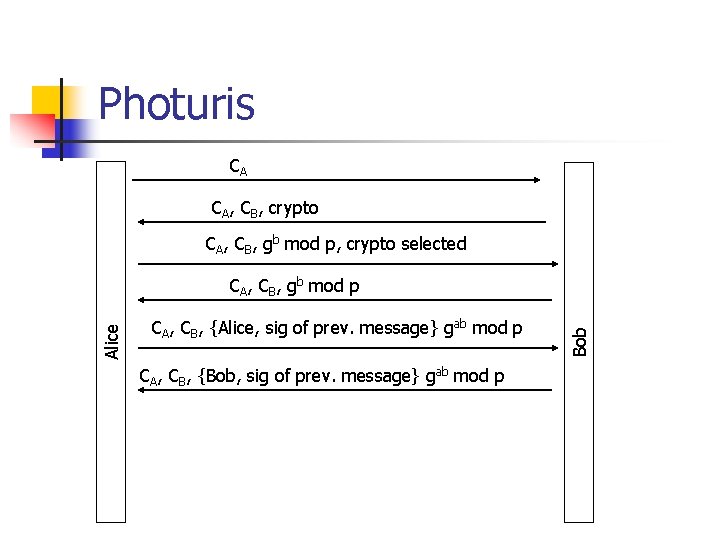
Photuris CA CA, CB, crypto CA, CB, gb mod p, crypto selected CA, CB, {Alice, sig of prev. message} gab mod p CA, CB, {Bob, sig of prev. message} gab mod p Bob Alice CA, CB, gb mod p

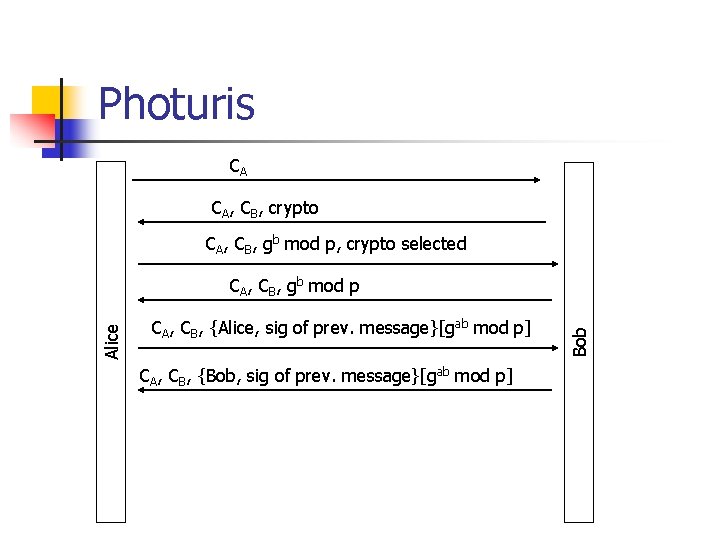
Photuris n n Alice chooses cookie CA in order to keep different login attempts separated. Bob uses a stateless cookie CB in order to keep Do. D attacks at bay. Messages 3 and 4 consists of a Diffie-Hellman encryption. Messages 5 and 6 serve for authentication. Encrypted with Diffie-Hellman key.

Photuris CA CA, CB, crypto CA, CB, gb mod p, crypto selected CA, CB, {Alice, sig of prev. message}[gab mod p] CA, CB, {Bob, sig of prev. message}[gab mod p] Bob Alice CA, CB, gb mod p

SKIP n Simple Key Management for Internet Protocols n Principals have n n n Certified Diffie-Hellman public keys ga mod p n Long-time use Private key a. Alice wants to talk to Bob: b th n Alice takes Bob’s public key g and raises it to the a power. a th n Bob takes Alice’s public key g and raises it to the b power. ab mod p. n Both share the secret g

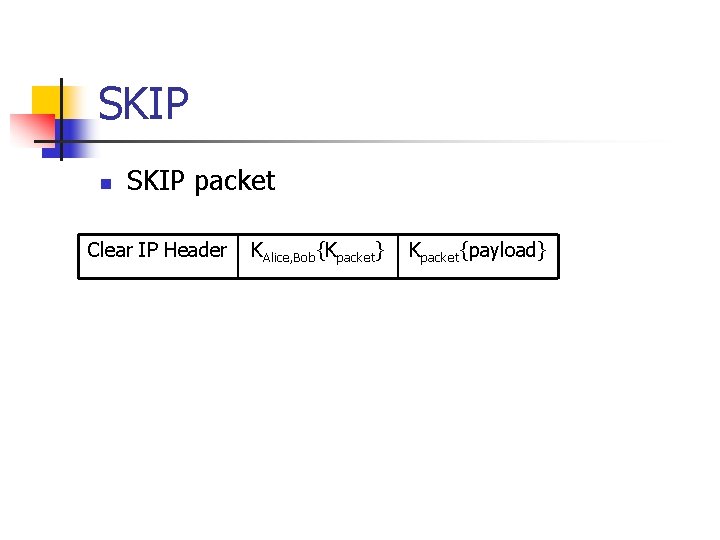
SKIP n SKIP derives a key KAlice, Bob from the mutually shared secret between Alice and Bob. n n Such as the lower bits of gab mod p. Each packet is encrypted / authenticated with a randomly generated key Kpacket. The key Kpacket is encrypted with KAlice, Bob and added to the packet. The header of the packet is in clear text.

SKIP n SKIP packet Clear IP Header KAlice, Bob{Kpacket} Kpacket{payload}

SKIP n Changing a principal’s key is a difficult, but needed operation. n n n Minimizes exposure of the key and makes crypt-analysis more difficult. Updating the master key prevents reusing compromised traffic keys. Each new key needs to be certified.

SKIP n Make the master key KAlice, Bob dependent on a version that automatically updates: KAlice, Bob = hash(gab, counter-value) n n Allows still principals to get a brand-new certified key. Prevents some replay attacks.

IPSec: IKE n Phases n Phase 1: n n n Phase 2: n n n Does mutual authentication and establishes session keys. Known as KSAKMP SA / IKE SA Establishes an ESP or AH SA Phase 1 is necessarily expensive. The two phases try to have phase 2 profit from a phase 1 interchange used for another protocol, connection, …

IPSec: IKE n Phase 1 IKE: n Aggressive mode n n Use a single crypto-proposal Main mode n Negotiate the strongest crypto-proposal that both parties can agree to.

IPSec: IKE n Phase 1 Aggressive Mode: ga, Alice, crypto-proposal gb, crypto-choice, Proof that I’m Bob. Alice Proof that I’m Alice Bob

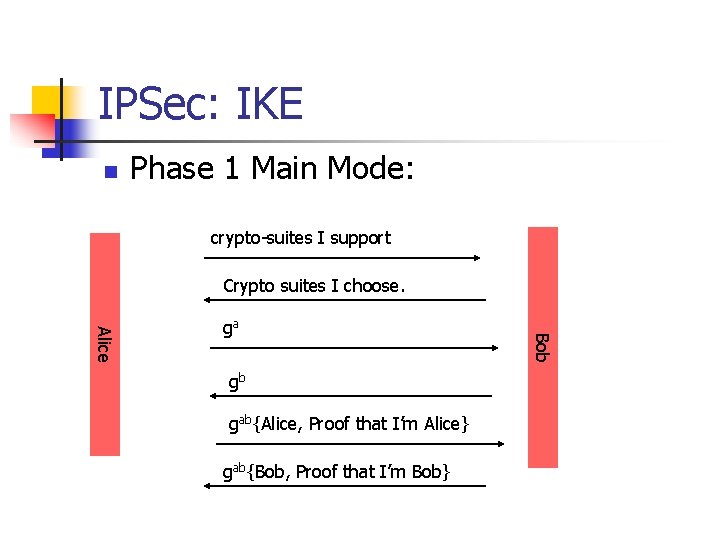
IPSec: IKE n Phase 1 Main Mode: crypto-suites I support Crypto suites I choose. gb gab{Alice, Proof that I’m Alice} gab{Bob, Proof that I’m Bob} Bob Alice ga

IPSec: IKE n Key Types n Pre-shared secret Public key for encryption / decryption Public key for signing n 8 variants of Phase 1!!! n n

IPSec: IKE n Phase 1 establishes two session keys: n n n Integrity key Encryption key for the last exchange in phase 1 and all exchanges in phase 2. Establishes a pair of cookies to keep different sessions different.

IPSec: IKE n Phase 1 protocols n Read them!

IPSec: IKE n Phase 2: A. k. a. quick mode. n n n Uses a pair X of cookies generated in phase 1. Session nonce for phase 2 session. All messages are encrypted with Phase 1 encryption key SKEYID_e All messages are integrity protected with Phase 1 intergrity key SKEYID_a. Can be initiated by either participant of Phase 1.

IPSec: IKE Alice X, Y, Crypto-protocol, SPIA, nonce. A, X, Y, Crypto-protocol accepted, SPIB, nonce. B X, Y Ack SPI: Security Parameter Index Bob

Secure Socket Layer n n 1995: deployed in Netscape Navigator as SSLv 2. 1995: Microsoft fixes SSLv 2 and introduces a similar protocol n Private Communication Technology (PCT) n 1996: Netscape introduces SSLv 3 1999: IETF introduces Transport Layer Security. n SSLv 3 remains the most implemented protocol. n

Secure Socket Layer n SSL is built on top of TCP. n n TCP provides reliable packet delivery. Rogue packet problem: n Maliciously introduced TCP packet. n n Easy to do, since it only needs to satisfy the noncryptographic TCP checksum. SSL disregards the package. TCP however will not accept the true packet, because it looks like a double to it. SSL will have to start over.

Secure Socket Layer n n Various keys are formed from various random numbers exchanged during the protocol. Negotiate crypto-protocols.

Secure Socket Layer n n SSL sessions are long-lived. Many SSL connections can be derived from an SSL session.

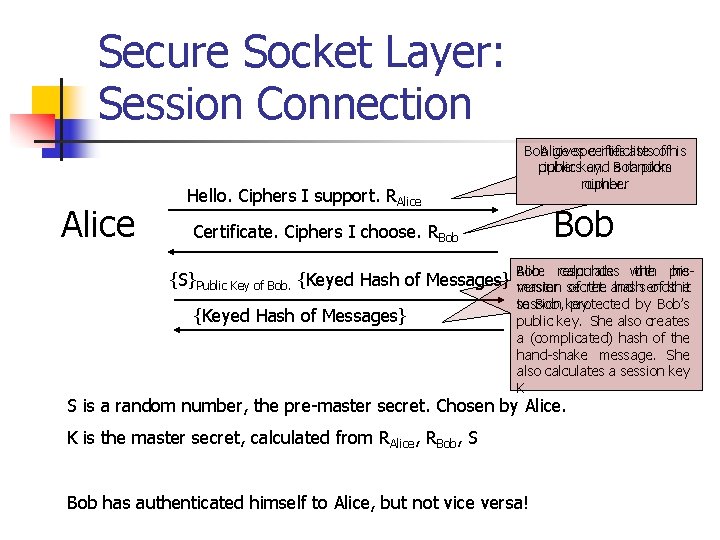
Secure Socket Layer: Session Connection Alice Hello. Ciphers I support. RAlice Bob Alice gives specifies certificate listsofofhis ciphers public key. and Bob a random picks number cipher. Bob Certificate. Ciphers I choose. RBob {S}Public Key of Bob. {Keyed Hash of Messages} Bob responds Alice calculates with the prehis master secret version of the and hashsends of the it to Bob, key. session protected by Bob’s public key. She also creates a (complicated) hash of the hand-shake message. She also calculates a session key K S is a random number, the pre-master secret. Chosen by Alice. K is the master secret, calculated from RAlice, RBob, S Bob has authenticated himself to Alice, but not vice versa!

Secure Socket Layer: Session Resumption n If Bob wants to have multiple connections per session, he sends in Message 2 a session id. If Alice presents in Message 1 a session id, they skip the handshake. Alice can still negotiate ciphers with Bob who might have changed policies. Alice Session ID. Ciphers I support. RAlice Session ID. Certificate. Ciphers I choose. RBob {Keyed Hash of Messages} Bob

Secure Socket Layer: Session Resumption n n Session resumption is not stateless. Server Bob needs to maintain a database entry of session id and master secret.

Secure Socket Layer n n n SSL comes deployed with public keys of various trusted organizations. User can modify this list. User verifies public keys by sending certificate requests to the organizations in the list.

Secure Socket Layer n SSLv 3 upgrades: n Protects against the “downgrade attack” n n Active attacker replaces the initial messages with ones containing weak crypto. Protects against the “truncation attack” n Active attacker sends a TCP close (FIN) message. n TCP is not protected, so the connection is abnormally terminated without SSL being aware of it.

Secure Shell: SSH n n n SSH client and server are applications (running on top of OS). SSH consists of a bunch of applications. But SSH is not a UNIX shell.

Secure Shell: SSH n Provides n n n Authentication Encryption Integrity

Secure Shell: SSH n SSH provides n n n scp: secure file transfer Secure remote command execution Automatic authentication: n n n n Delegate limited authentication. n n Place public key files on remote computers Enable SSH clients (scp, ssh) to access remote accounts Invoke ssh-agent program Choose keys needed for remote logins. Load private keys with ssh-add (invoking passphrase) ssh-agent keeps private keys in memory. Secretary can only read the email. Port forwarding

Secure Shell: SSH 1 n Client contacts server. n n n By going to port 22 by convention. Client and server disclose the SSH versions they support. Client and server switch to a packet based protocol. n Packet consists of n n n 4 B length, 1 -8 B of random padding, one-byte packet type code, packet payload data, four-byte integrity check field.

Secure Shell: SSH 1 n Server identifies itself by sending n n n Host key Server key 8 random bytes (use as cookie) List of encryption, compression, authentication methods. Both sides compute a 128 b session identifier.

Secure Shell: SSH n n When the client receives the host key, the client looks into the known host database. If the host key matches the one in the database then the client proceeds. If the host is in the database but with a different key, then the client queries the user. Otherwise, the client warns the user and proposes to add host and key to the known host database.

Secure Shell: SSH n Client randomly generates a session key. n n n Clients sends the session key encrypted with the server key and then with the host’s public key. Together with the choice of crypto-suites. Both sides now use the session key for encryption. n n Server sends confirmation message encrypted with the session key. This proves the server’s authenticity to the client.

Secure Shell: SSH n Authentication phase starts: n SSH 1 tries out n n n Kerberos Rhosts. RSA Public key TIS Password

Secure Shell: SSH n n n At this point, a secure communication channel has been established. Client is sure of the authenticity of server. Server now authenticates the client.

Secure Shell: SSH n SSH 2 changes: n SSH 2 consists of modules: n n n SSH Transport layer protocol SSH Authentication protocol SSH Connection protocol SSH 2 allows for additional parameter negotiation More general session key exchange possibilities

Secure Shell: SSH n SSH-2 changes: n n n SSH-2 uses better integrity checking for messages. Supports password changes. User-authentication methods more restricted: n n n Public key (DSA, RSA, Open. PGP) Hostbased password