COEN 252 Security Threats Hacking n Untargeted attacks



































- Slides: 44

COEN 252 Security Threats

Hacking n Untargeted attacks n Motivation is n Fun (I can do it) n n Financial Gain n n prevalent until ~2000 Selling access to compute resources n Creation of botnets for spamming, computation (distributed decryption, phishing, pharming …) Selling data n Credit Card Information n E-mails n … Targeted Denial of Service Attacks n Cloud Nine, a British ISP failed after suffering attacks Cyber-warfare, terrorism

Hacking n Targeted Attacks n n Theft of information Incapacitation of an organization to fulfill its purpose by destroying / impeding its use of computing resources

Hacking Phases of a Targeted Attack n n n Reconnaissance Scanning Gaining Access Expanding Access Covering Tracks

Reconnaissance n Social Engineering n Incite a human to act imprudently, furthering the goals of the attacker: n n “I cannot access my email. What do I do? ” Countermeasures: n n n Identify security issues Develop policies n Need to prevent leakage of information n Need buy-in by users and agents n Need to maintain user-friendliness of IT Physical Reconnaissance n Dumpster Diving n n Especially bountiful when people move Installation of scanning devices

Reconnaissance n Finding publicly available information n Contact information of internet registration n n Who. Is, ARIN, RIPE, … Internal documents made publicly available: n n Use search engines Check Internet Archive, … Identify naming conventions and guess file names Scrutinize publications n n A word document might contain the revision history with old versions of file A PDF file had confidential information obscured by a black box, that could be removed … Email, Usenet, Blog postings that identify names of internal machines, …

Reconnaissance: Scanning Once we have a target, we need to get to know it better. Methods: n War Dialing (to find out modem access) n War Driving n Network Mapping n n Largely obsolete due to better firewall rules Vulnerability Scanning

Scanning: War Dialing Purpose: Find a modem connection. n Many users in a company install remote PC software such as PCAnywhere without setting the software up correctly. n War Dialer finds these numbers by going through a range of phone numbers listening for a modem. n Demon Dialer tries a brute force password attack on a found connection. n Typically: war dialing will find an unsecured

Scanning: Network Mapping Ping: n ping is implemented using the Internet Control Message Protocol (ICMP) Echo Request. n A receiving station answers back to the sender. n Used by system administrators to check status of machines and connections.

Scanning: Network Mapping Traceroute: n Pings a system with ICMP echo requests with varying life spans (= # of hops allowed). n A system that receives a package with expired numbers of hops sends an error message back to sender. n Traceroute uses this to find the route to a given system. n Useful for System Administration

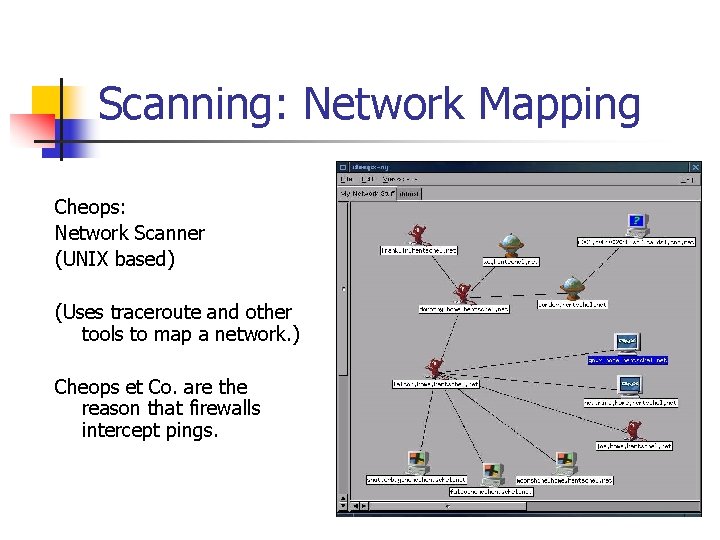
Scanning: Network Mapping Cheops: Network Scanner (UNIX based) (Uses traceroute and other tools to map a network. ) Cheops et Co. are the reason that firewalls intercept pings.

Reconnaissance: Port Scans n n Applications on a system use ports to listen for network traffic or send it out. 216 ports available, some for known services such as http (80), ftp, . . . Port scans send various type of IP packages to target on different ports. Reaction tells them whether the port is open (an application listens).

Reconnaissance: Nmap n Uses different types of packets to check for open ports. n n n Xmas tree, NULL, Syn, … Scans Can tell from the reaction what OS is running, including patch levels. Can run in stealth mode, in which it is not detected by many firewalls.

Reconnaissance Prevention n Firewalls can make it very difficult to scan from the outside. n n Drop scan packets. Patched OS do not have idiosyncratic behavior that allows OS determination. IDS can detect internal scans and warn against them. Example: Detect traceroute by not allowing in packets with very small TDL values

Gaining Access n Fault in Policy n n Fault in Implementation n n Weak or no authentication, unwarranted trust relationships, … Typical triggered by intentionally malformed input Extension of a security breach n Sniffing malware, …

Security Policy, Software defects, flaws, vulnerabilities n n A Security Policy is a set of rules and practices that specify or regulate how a system or organization provides security services to protect sensitive and critical system resources [Internet Society 00]. Software Defects: n n Security Flaw: n n n A software defect is the encoding of a human error into the software, including omissions. A security flaw is a software defect that poses a potential security risk. Eliminating software defects eliminate security flaws. Vulnerability n n n set of conditions that allows an attacker to violate an explicit or implicit security policy. Not all security flaws lead to vulnerabilities. Not all vulnerabilities are based on a security flaw.

Software Vulnerabilities n Attacker needs to control the environment of the application n or craft input in order to trigger a vulnerability. n

Software Vulnerabilities n n In a typical environment, attacker needs to be able to set a single value at a single address in order to execute arbitrary code. Typical Targets n Global Offset Table in Unix n n . dtors n n n Used to link to library functions Used by gcc to link to destructors that run at termination of program Virtual Function Tables Exception Handling Table in Windows

Software Vulnerabilities n Typical Vulnerabilities n Buffer Overruns: n n Format String Vulnerability: n n Input string is stored on a buffer, but buffer is too small Input located outside of buffer has overwritten data Stack based buffer overflow: Overwrite the return address of a function (Specific to C) Arises by not specifying a format string The %n construct allows attacker to control a random memory location Integer Overflow Race Conditions n Especially when accessing files

Software Vulnerabilities n Typical Vulnerabilities n Injection Attacks n n n Input (e. g. user input to web server) is used to generate arguments for a command to be executed: Command Injection Input (e. g. user input to web server) is used to generate arguments for a sql query to be executed and displayed: SQL Injection Name Resolution Attacks n Different modules use different ways to canonicalize / resolve names of resources such as files n n HFS 2 file names are not case sensitive, but Apache configuration is Homonyms (e. g. kyrillic vs. regular o)

Software Vulnerabilities n Use of magic names n Instance of security by obfuscation n n Magic URL Hidden Form Fields

Software Vulnerabilities n False amount of security information results in poor usability n n n Too many warnings: Users are confused and trained to ignore warnings Too few warnings: Users are not made aware of risks Bad networking protocols n n Unauthenticated key exchange Trusting network name resolution

Gaining Access through Network Attacks: Sniffing n n n Sniffer: Gathers traffic from a LAN. Examples: Snort www. snort. org, Sniffit reptile. rug. ac. be/~coder/sniffit. ht ml To gain access to packages, use spoofed ARP (Address Resolution Protocol) to reroute traffic.

Gaining Access through Network Attacks: Sniffing n Sniffing through a hub: n MAC flooding: n n n Switches store MAC addresses in a cache. Switches accept MAC advertising. Attacker sends a flood of MAC advertisings. Switch’s cache fills up. Switch moves into promiscuous mode. Spoofed ARP messages

Gaining Access through Network Attacks: Sniffing n Sniffing through a hub: n Spoofed ARP messages: n n n ARP resolves between IP addresses and MAC addresses. Step 1: Attacker sets up IP Forwarding to the default router on LAN. Step 2: Send a faked ARP reply to victims machine to reroute default router IP to attackers MAC address. Step 3: Victim sends out a message to the outside world. This is routed to the default router IP, i. e. to the attackers machine. Step 4: Attacker reads traffic. Step 5: Because of forwarding, packet is forwarded to actual default router.

Gaining Access through Network Attacks: Sniffing n Man in the Middle Attack with DSniff: n n n Step 1: Send fake DNS response with IP address for the web site to be attacked to the victim. Step 2: Victim connects to website. Step 3: DNS resolves to the attacker’s machine, request send there. Step 4: Attacker’s site receives request, acts as proxy, forwards it to real website. Step 5: Real website answers, attackers site forwards to victim. …

Gaining Access: Session Hijacking n n IP Address Spoofing: Send out IP packages with false IP addresses. If an attacker sits on a link through which traffic between two sites flows, the attacker can inject spoofed packages to “hijack the session”. Attacker inserts commands into the connection. Details omitted.

Exploiting and Maintaining Address After successful intrusion, an attacker should: n Attack privileged programs to gain root or administrator privileges. n Erase traces (e. g. change log entries). n Take measures to maintain access. n Erase security holes so that no-one else can gain illicit access and do something stupid to wake up the sys. ad.

Maintaining Access: Trojans n A program with an additional, evil payload. n n Running MS Word also reinstalls a backdoor. ps does not display the installed sniffer.

Maintaining Access: Backdoors Bypass normal security measures. Example: netcat n Install netcat on victim with the GAPING_SECURITY_HOLE option. C: nc -1 –p 12345 –e cmd. sh n In the future: connect to port 12345 and start typing commands. n

Maintaining Access: Backdoors n n BO 2 K (Back Orifice 2000) runs in stealth mode (you cannot discover it by looking at the processes tab in the TASK MANAGER. Otherwise, it is a remote control program like pc. Any. Where, that allows accessing a computer over the net.

Maintaining Access: Backdoors n Root. Kit: A backdoor built as a Trojan of system executables such as ipconfig. n Kernel-Level Root. Kit: Changes the OS, not only system executables.

Covering Tracks: n n n Altering logs. Create difficult to find files and directories. Covert Channels through Networks: n n Loki uses ICMP messages as the carrier. Use WWW traffic. Use unused fields in TCP/IP headers. Use antiforensics n n Change registry values to delete traces of installed programs Change Date-Time stamps

Hacker Profile n Internal Hacker n n Disgruntled employee Contracted employee n n n Targets for corporate espionage. Are not bound by employee policies and procedures. Indirectly contracted employee n Perform shared or subcontracted services

Hacker Profile n External Hacker n Recreational Hacker n n n 85% 90% male. Between 12 and 25. Highly intelligent low-achiever. Typically from dysfunctional families. Professional Hacker n n Hackers for hire. Electronic warfare, corporate espionage. So-called “Security Consultants” who look for blackmail or exploit for hire Security Consultants

Hacker Profile n Virus writers 1 n n n Teenagers, College Students, Professionals Drop out of the scene as adults or have social problems. Intelligent, educated, male. Study by Sarah Gordon, IBM, in Beiser, Vince, “Inside the Virus Writer’s Mind”

Hacker Profile n Script Kiddy n n Uses scripts of programs written by others to exploit known vulnerabilities Goal is bragging rights, defacing web sites Sweep IP addresses for vulnerability Typically not explicitly malicious, but can cause damage inadvertently

Hacker Profile n Dedicated Hacker n n n Does research. Knows in and outs of OS, system, auditing and security tools. Writes or modifies programs and shell scripts Reads security bulletins (CERT, NIST) Searches the underground.

Hacker Profile n Skilled Hacker n n Thorough understanding of system at the level of Sys Ad or above. Can read OS source code. Understands network protocols. Superhacker n n Does not brag or post. Can enter or bring down any system. http: //www. securityfocus. com/news/203

Hacker Motives n Intellectually Motivated n Educational experimentation n n “Harmless Fun” n n 28 year old computer expert diverted 2585 US West computers to search for a new prime number. Used 10. 63 years of computer time. Lengthened telephone number lookup to 5 minutes Almost shut down the Phoenix Service Delivery Center Web defacing Wake-up Call n Free-lance security consultant (still illegal)

Hacker Motives n Personally motivated n n Disgruntled employee. Cyber-stalking n n E. g. to show of superiority to someone they feel / are inferior to. Danger of escalation to physical attack. n n n A 50 -year old security guard used the internet to solicit the rape of a 28 -year old woman who rejected him. Impersonated her in chat rooms and online bulletins. Impersonated rape fantasies. At least six man knocked at her door at night offering to rape her. Six years in prison.

Hacker Motives n Socially motivated n n Cyber-activism Politically motivated n n Hacking KKK or NAACP websites Cyber-Terrorism n Threatens serious disruption of the infrastructure n n n Power Water Transportation Communication 1988: Israeli Virus and logic bomb in Israeli government computers Cyber-warfare

Hacker Motives n Financially Motivated n Personal profit. n n n Damage to the organization. n n Two Cisco Systems consultants issued almost $8 M Cisco stock to themselves. Accessed a system used to manage stock option disbursals to find control numbers forged authorization forms. British internet provider, Cloud Nine, went out of business after crippling series of DOS attacks. Ego Motivated

Hacking Damage n n Releasing Information Releasing Software n n n By circumventing copying protection. Through IP theft Consuming Unused(? ) Resources Discover and Document Vulnerabilities Compromise Systems and Increase their Vulnerabilities Website Vandalism