COBIT 5MAVIM Click to see next slide Speed

COBIT 5@MAVIM Click to see next slide Speed up your GDPR program Develop your IT Management System Accelerate your Information Security System … WITHOUT expensive consultancy fees…. . ! Greet Volders Managing Consultant Voquals N. V.
Deliverables included in this service offering u Complete content of COBIT 5 – Available in the Data. Base – Presentable on your website u GDPR compliant processes & documents – Necessary procedures – Useful Information – Practical examples & templates Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 2
Deliverables included in this service offering u Based on COBIT for Security – Mapped to: » ISO 27001: 2013 » ISF (Information Security Forum) and » NIST (National Institute of Standards and Technology) u Additional integrated content – – – RACI Level 1 Process Capability Assessment IT related goals and metrics Specific templates for some processes Cross-reference to ITIL Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 3
Website - homepage On the home page, you get access to the 4 most important parts of COBIT 5, being : - The processes, with flow and descriptions - KPI’s based on the IT-related goals and KPI’s defined by Voquals - Level 1 Process Capability Assessment execution & results - RACI based on the standard RACI provided in COBIT 5 Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 4
Website - Processes • • • In this solution, you do not only manage your IT-related processes, but ALL company processes in an integrated, coherent way. All organisational structures are linked with the processes. Reporting is done in a consistent way. Do you want to learn a about. . . COBIT 5, Processes and reporting Greet Volders _ Voquals N. V. Voquals 4 GDPR MAVIM / COBIT 5 Voquals 4 Info Security The END Slide 5
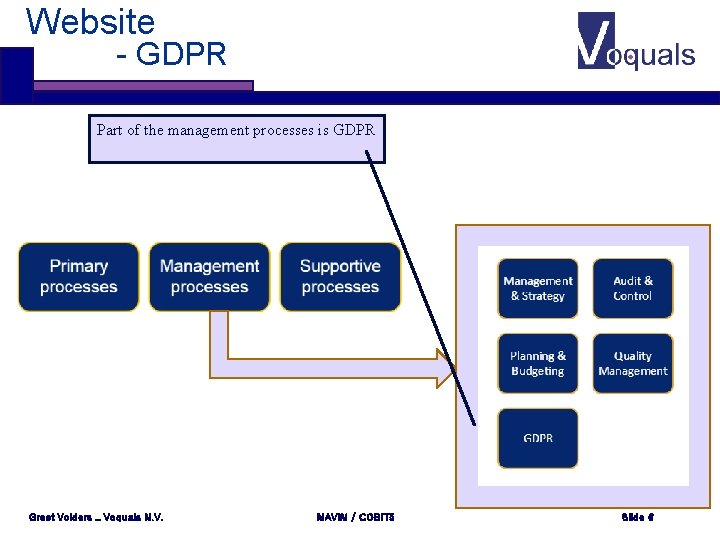
Website - GDPR Part of the management processes is GDPR Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 6
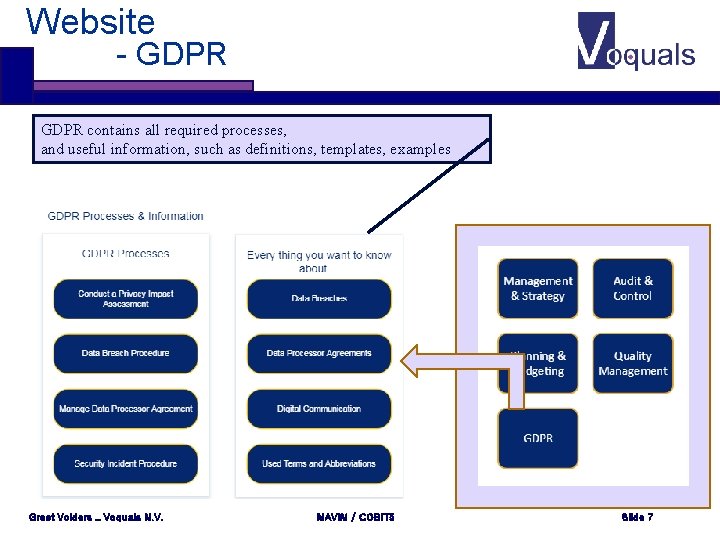
Website - GDPR contains all required processes, and useful information, such as definitions, templates, examples Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 7
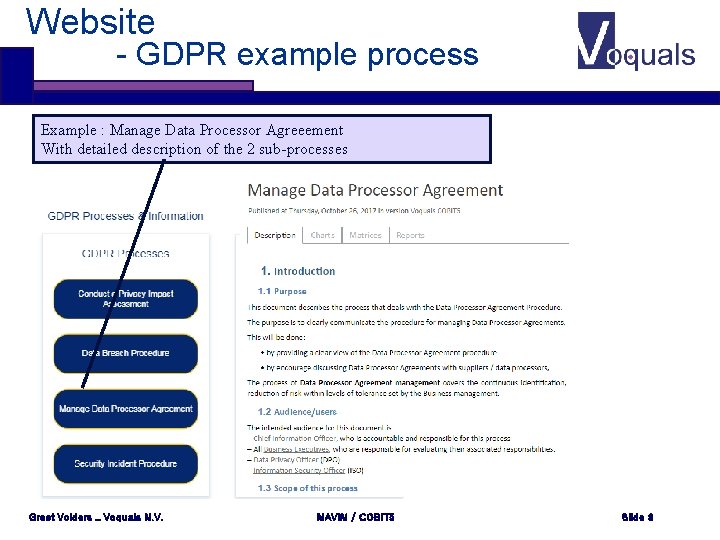
Website - GDPR example process Example : Manage Data Processor Agreeement With detailed description of the 2 sub-processes Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 8
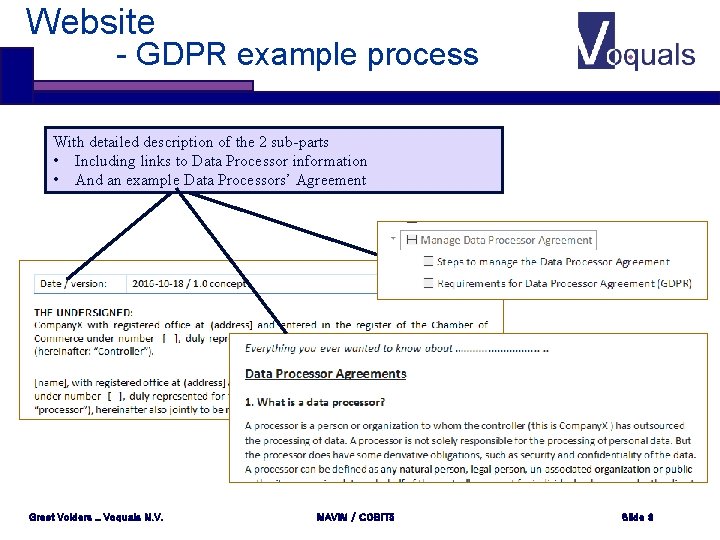
Website - GDPR example process With detailed description of the 2 sub-parts • Including links to Data Processor information • And an example Data Processors’ Agreement Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 9
Website - GDPR After the GDPR, do you want to learn a about. . . COBIT 5, Processes and reporting Greet Volders _ Voquals N. V. Voquals 4 GDPR MAVIM / COBIT 5 Voquals 4 Info Security The END Slide 10
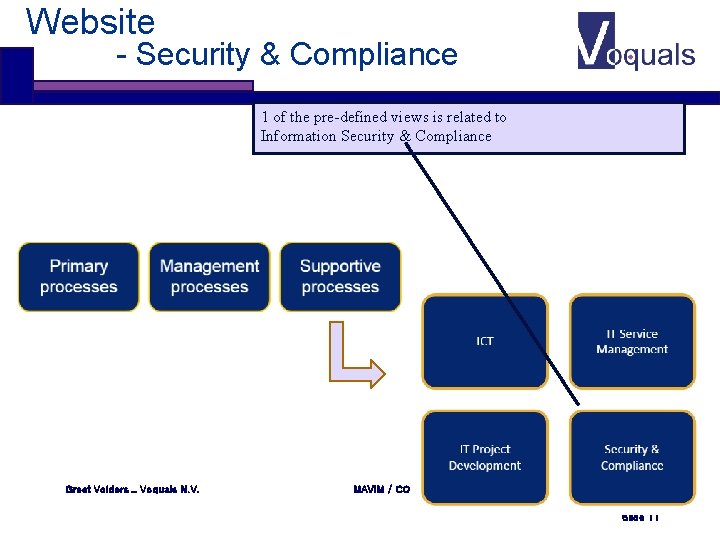
Website - Security & Compliance 1 of the pre-defined views is related to Information Security & Compliance Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 11
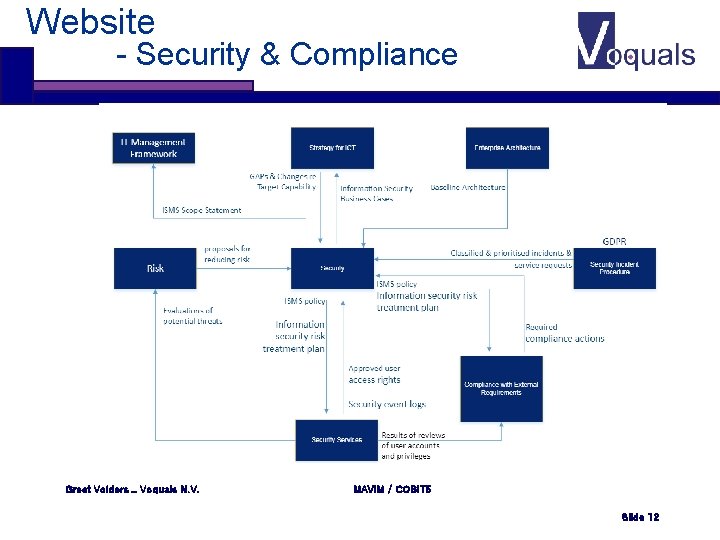
Website - Security & Compliance Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 12
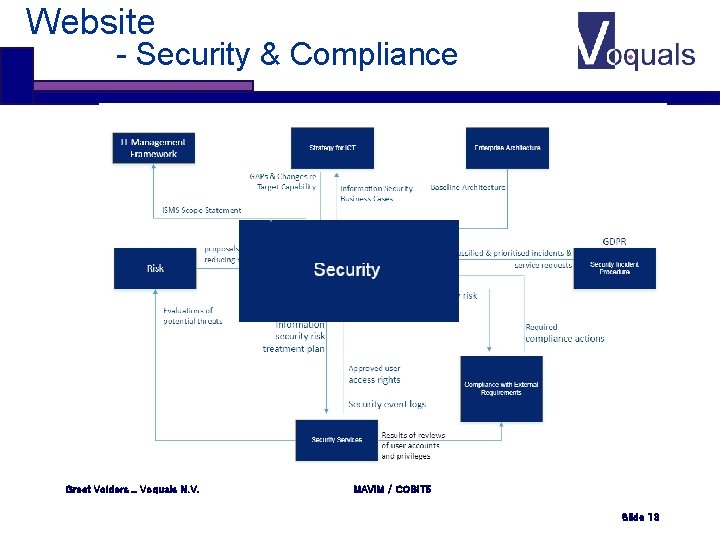
Website - Security & Compliance Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 13

Website - Security & Compliance Available description of the Manage Security process The same exist for all the other processes on the schema Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 14
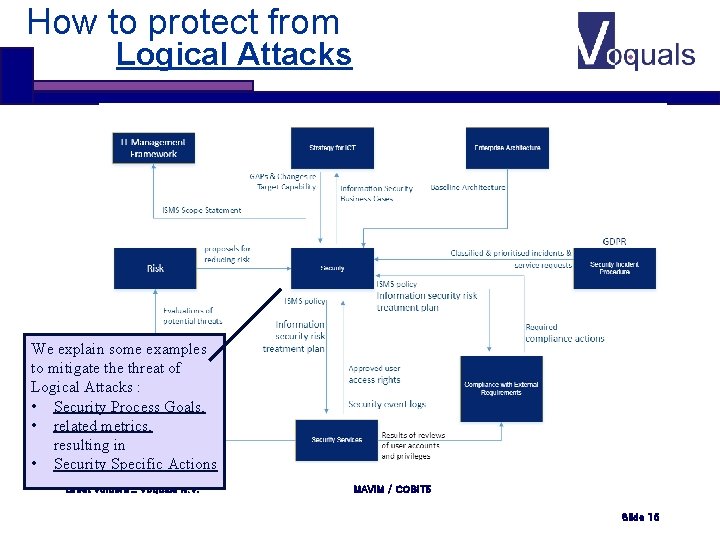
How to protect from Logical Attacks We explain some examples to mitigate threat of Logical Attacks : • Security Process Goals, • related metrics, resulting in • Security Specific Actions Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 15
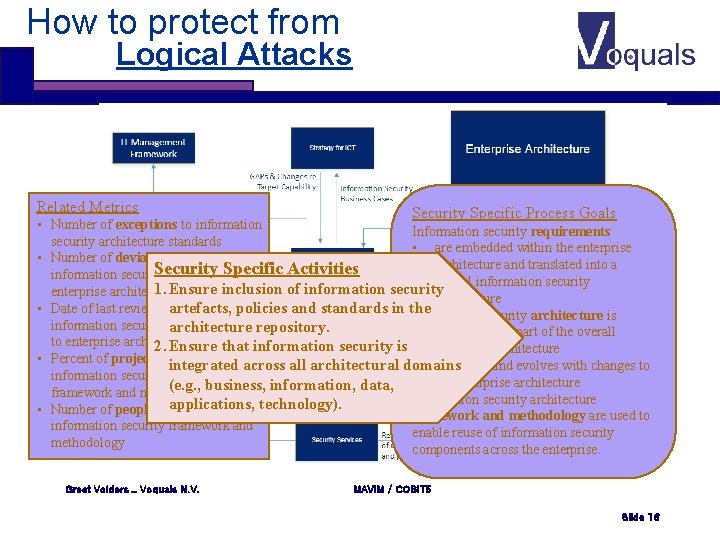
How to protect from Logical Attacks Related Metrics Security Specific Process Goals • Number of exceptions to information Information security requirements security architecture standards • are embedded within the enterprise • Number of deviations between architecture and translated into a Security Specific Activities information security architecture and formal information security 1. Ensure inclusion of information security enterprise architecture artefacts, and standards in the • Date of last review and/or updatepolicies to Information security architecture is information security controls appliedrepository. architecture • understood as part of the overall to enterprise architecture 2. Ensure that information security is enterprise architecture • Percent of projects that use the • is aligned and evolves with changes to integrated across all architectural domains information security architecture the enterprise architecture (e. g. , business, information, data, framework and methodology Information security architecture applications, technology). • Number of people trained in the framework and methodology are used to information security framework and enable reuse of information security methodology components across the enterprise. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 16
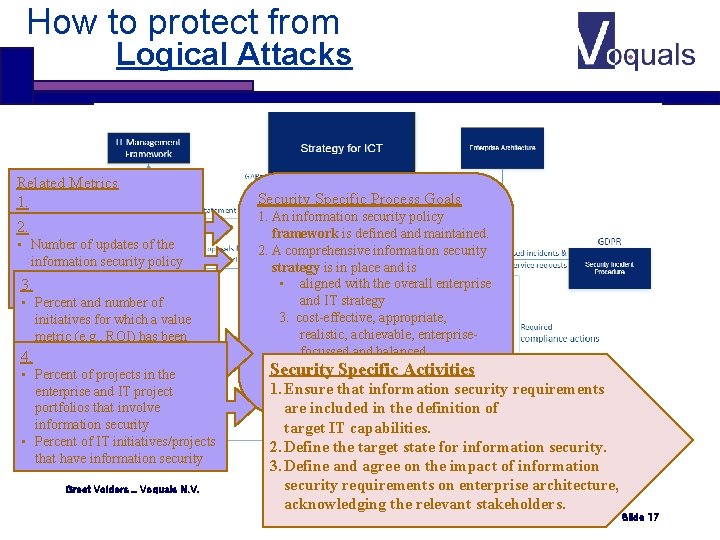
How to protect from Logical Attacks Related Metrics 1. • Number of updates of the 2. information security policy • Number of updates of the • Management approval of the information security policy • 3. Management approval of the security policy • information Percent and number of initiatives for which a value metric (e. g. , ROI) has been 4. calculated Enterprise stakeholder • • Percent of projects in the satisfaction survey feedback on enterprise and IT project the effectiveness of the portfolios that involve information security strategy • Percent of IT initiatives/projects that have information security Greet Volders _ Voquals N. V. Security Specific Process Goals 1. An information security policy framework is defined and maintained. 2. A comprehensive information security strategy is in place and is • aligned with the overall enterprise and IT strategy 3. cost-effective, appropriate, realistic, achievable, enterprisefocussed and balanced 4. aligned Specific with long-term enterprise Security Activities strategic goals and objectives. 1. Ensure that information security requirements are included in the definition of target IT capabilities. 2. Define the target state for information security. 3. Define and agree on the impact of information security requirements MAVIM / COBIT 5 on enterprise architecture, acknowledging the relevant stakeholders. Slide 17
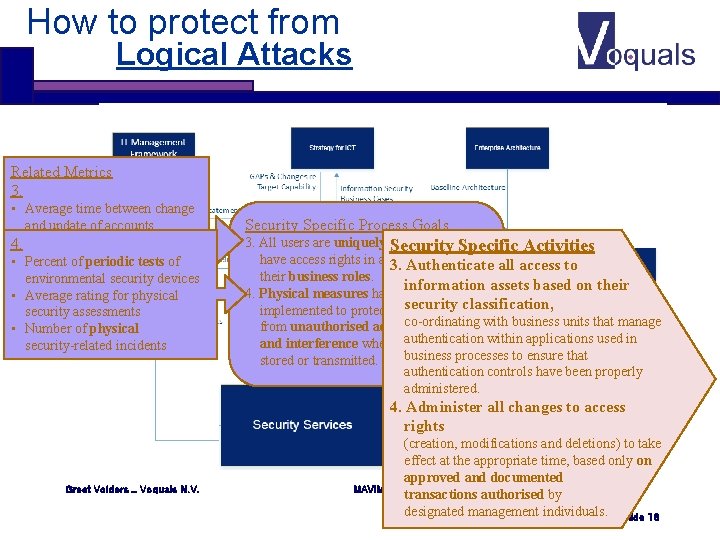
How to protect from Logical Attacks Related Metrics 3. • Average time between change and update of accounts • 4. Number of accounts (vs. authorisedtests of • number Percent of periodic users/staff) information environmental security devices security strategy • Average rating for physical security assessments • Number of physical security-related incidents Security Specific Process Goals 3. All users are uniquely identifiable and Security Specific Activities have access rights in accordance with 3. Authenticate all access to their business roles. information assets based on their 4. Physical measures have been security classification, implemented to protect information co-ordinating from unauthorised access, damage with business units that manage authentication and interference when being processed, within applications used in business processes to ensure that stored or transmitted. authentication controls have been properly administered. 4. Administer all changes to access rights Greet Volders _ Voquals N. V. (creation, modifications and deletions) to take effect at the appropriate time, based only on approved and documented MAVIM / COBIT 5 transactions authorised by designated management individuals. Slide 18
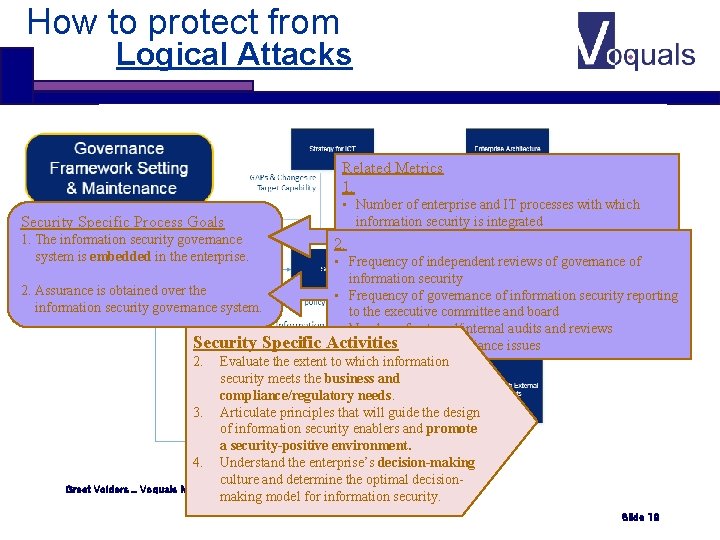
How to protect from Logical Attacks Related Metrics 1. Security Specific Process Goals 1. The information security governance system is embedded in the enterprise. 2. Assurance is obtained over the information security governance system. • Number of enterprise and IT processes with which information security is integrated 2. • Percent of processes and practices with clear traceability to principles • Frequency of independent reviews of governance of • information Number of security information security breaches related to non-compliance with ethical and professional behaviour • Frequency of governance of information security reporting guidelines to the executive committee and board • Number of external/internal audits and reviews Security Specific Activities • Number of non-compliance issues 2. Evaluate the extent to which information security meets the business and compliance/regulatory needs. 3. Articulate principles that will guide the design of information security enablers and promote a security-positive environment. 4. Understand the enterprise’s decision-making culture and determine the optimal decision. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 making model for information security. Slide 19
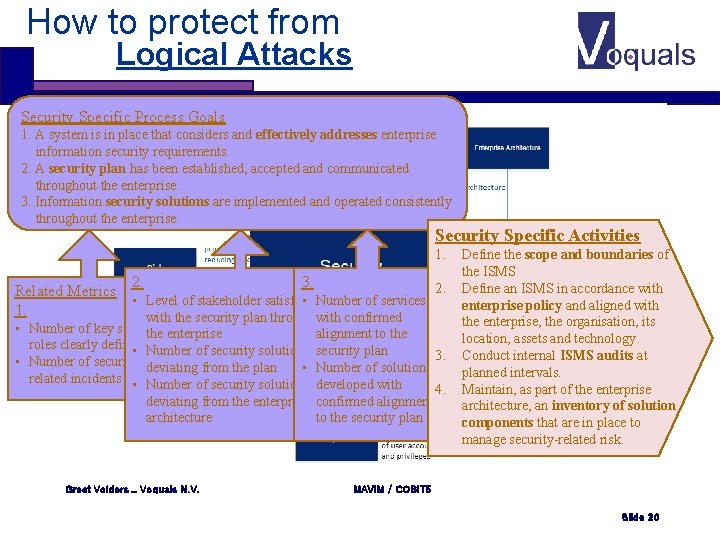
How to protect from Logical Attacks Security Specific Process Goals 1. A system is in place that considers and effectively addresses enterprise information security requirements. 2. A security plan has been established, accepted and communicated throughout the enterprise. 3. Information security solutions are implemented and operated consistently throughout the enterprise. Security Specific Activities 1. 3. 2. 2. Related Metrics • Number of services • Level of stakeholder satisfaction 1. with confirmed with the security plan throughout • Number of key security the enterprise roles clearly defined • Number of security solutions • Number of security- deviating from the plan • related incidents • Number of security solutions alignment to the security plan 3. Number of solutions developed with 4. deviating from the enterprise confirmed alignment to the security plan architecture Greet Volders _ Voquals N. V. Define the scope and boundaries of the ISMS Define an ISMS in accordance with enterprise policy and aligned with the enterprise, the organisation, its location, assets and technology. Conduct internal ISMS audits at planned intervals. Maintain, as part of the enterprise architecture, an inventory of solution components that are in place to manage security-related risk. MAVIM / COBIT 5 Slide 20
Website - Security & Compliance After Information Security & Compliance, do you want to learn a about. . . COBIT 5, Processes and reporting Greet Volders _ Voquals N. V. Voquals 4 GDPR MAVIM / COBIT 5 Voquals 4 Info Security The END Slide 21
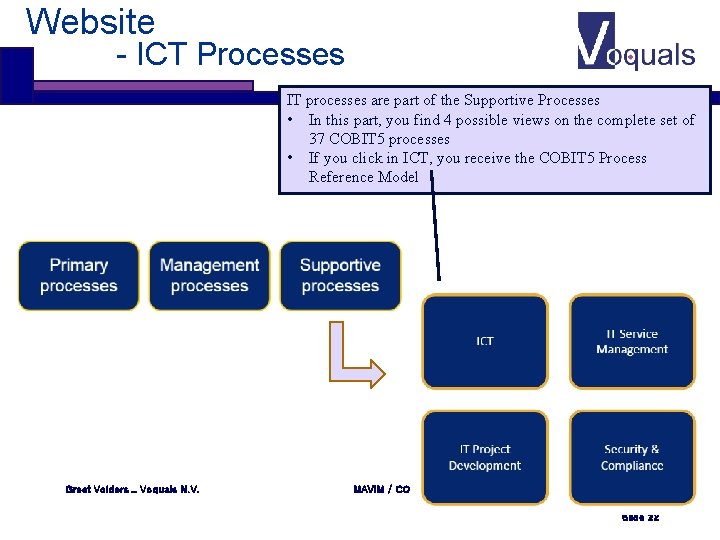
Website - ICT Processes IT processes are part of the Supportive Processes • In this part, you find 4 possible views on the complete set of 37 COBIT 5 processes • If you click in ICT, you receive the COBIT 5 Process Reference Model Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 22
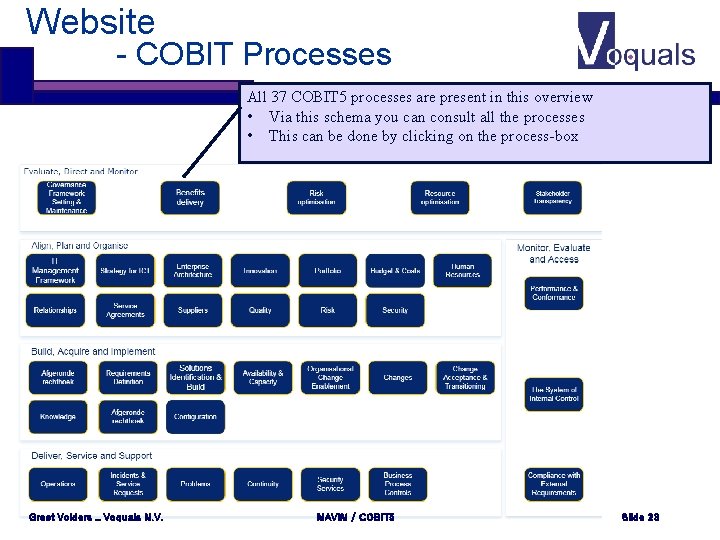
Website - COBIT Processes All 37 COBIT 5 processes are present in this overview • Via this schema you can consult all the processes • This can be done by clicking on the process-box Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 23
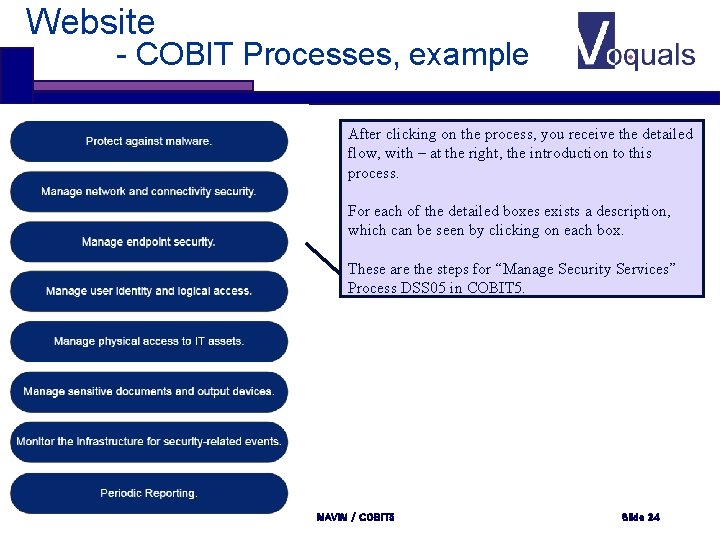
Website - COBIT Processes, example After clicking on the process, you receive the detailed flow, with – at the right, the introduction to this process. For each of the detailed boxes exists a description, which can be seen by clicking on each box. These are the steps for “Manage Security Services” Process DSS 05 in COBIT 5. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 24
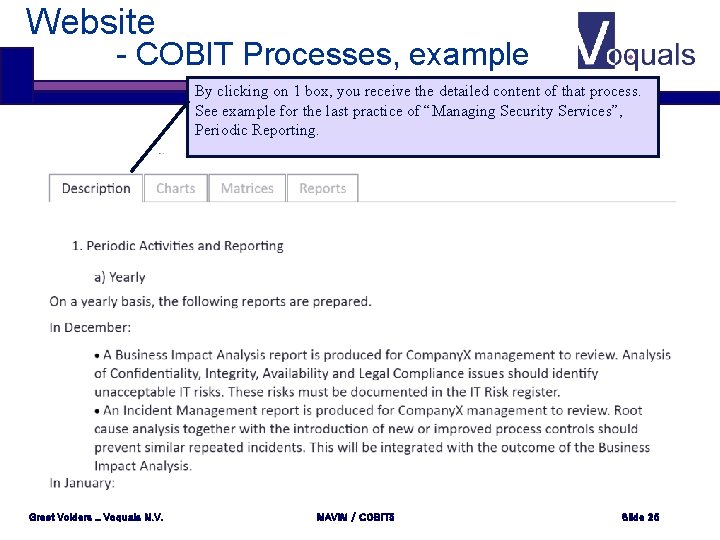
Website - COBIT Processes, example By clicking on 1 box, you receive the detailed content of that process. See example for the last practice of “Managing Security Services”, Periodic Reporting. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 25
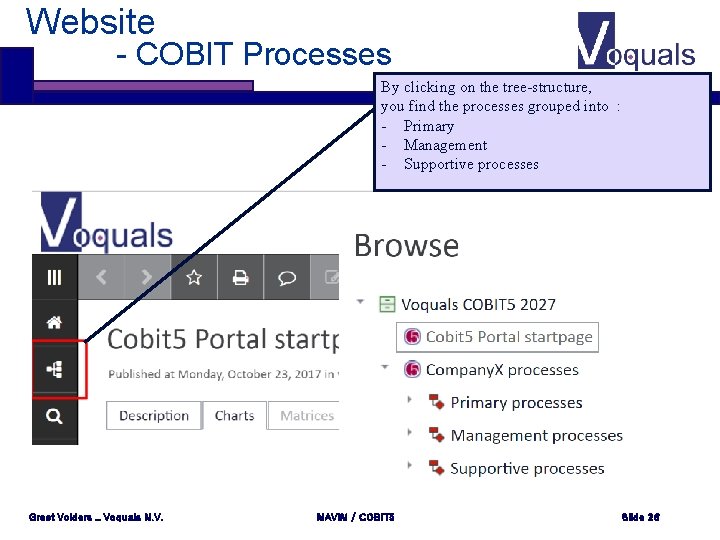
Website - COBIT Processes By clicking on the tree-structure, you find the processes grouped into : - Primary - Management - Supportive processes Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 26
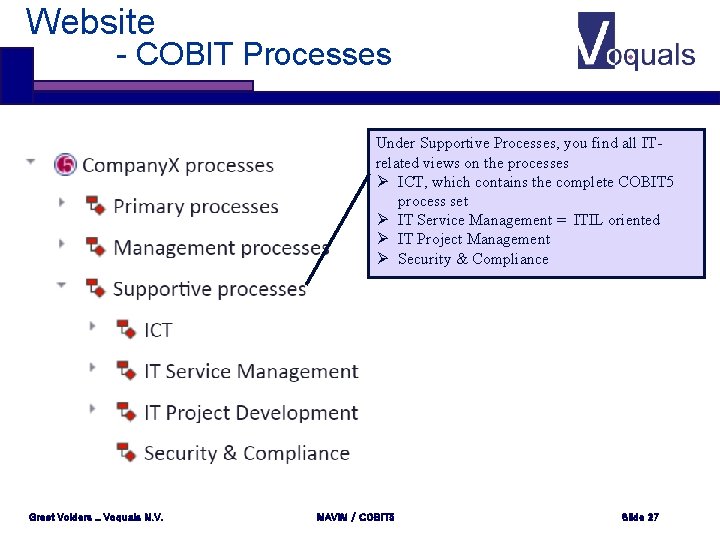
Website - COBIT Processes Under Supportive Processes, you find all ITrelated views on the processes Ø ICT, which contains the complete COBIT 5 process set Ø IT Service Management = ITIL oriented Ø IT Project Management Ø Security & Compliance Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 27
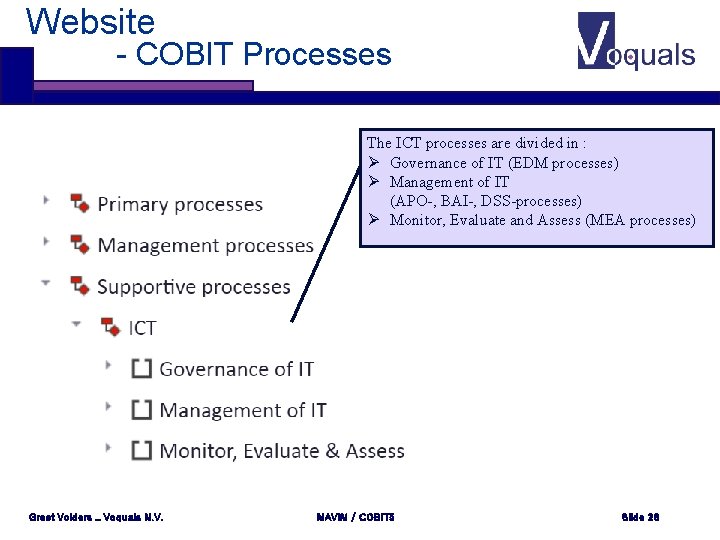
Website - COBIT Processes The ICT processes are divided in : Ø Governance of IT (EDM processes) Ø Management of IT (APO-, BAI-, DSS-processes) Ø Monitor, Evaluate and Assess (MEA processes) Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 28
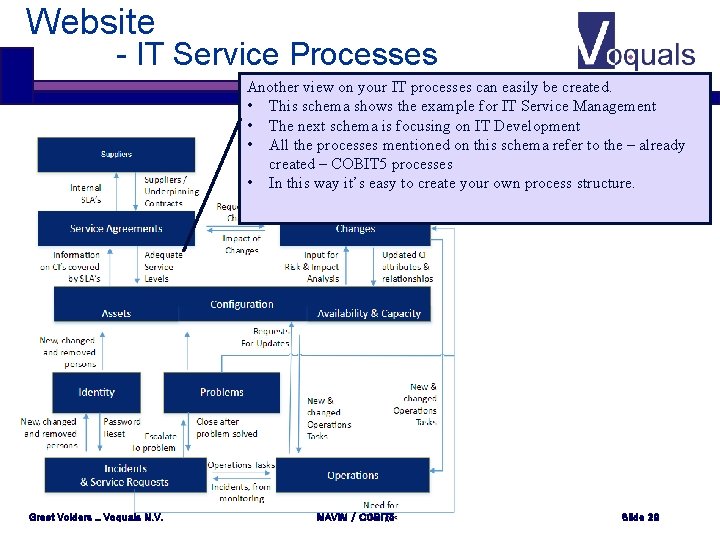
Website - IT Service Processes Another view on your IT processes can easily be created. • This schema shows the example for IT Service Management • The next schema is focusing on IT Development • All the processes mentioned on this schema refer to the – already created – COBIT 5 processes • In this way it’s easy to create your own process structure. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 29
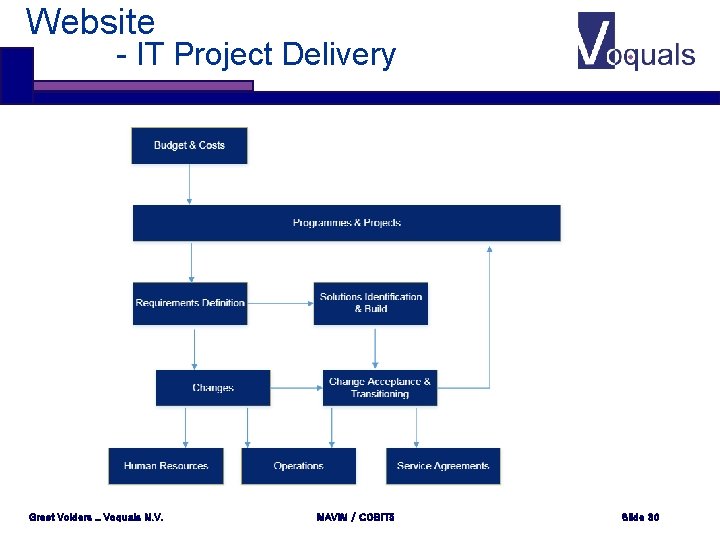
Website - IT Project Delivery Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 30
Website - KPI’s Other management tools available are : - Level 1 Process Capability Assessment - KPI’s (Key Performance Indicators) - RACI (Responsibility matrix) Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 31
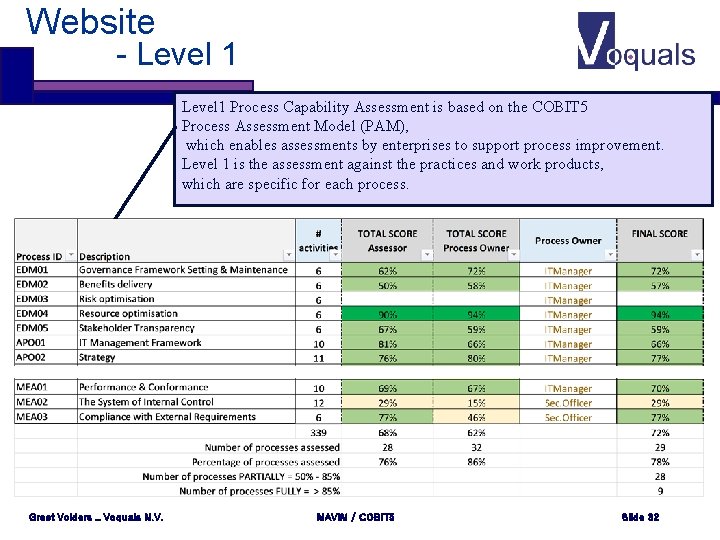
Website - Level 1 Process Capability Assessment is based on the COBIT 5 Process Assessment Model (PAM), which enables assessments by enterprises to support process improvement. Level 1 is the assessment against the practices and work products, which are specific for each process. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 32
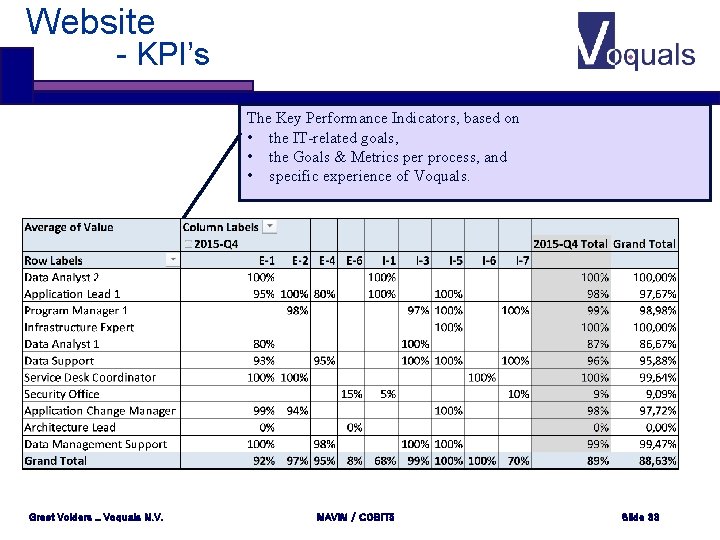
Website - KPI’s The Key Performance Indicators, based on • the IT-related goals, • the Goals & Metrics per process, and • specific experience of Voquals. Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 33
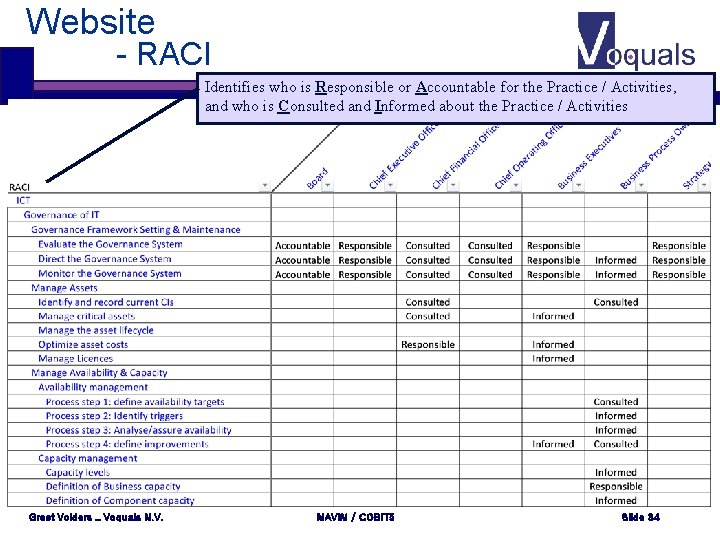
Website - RACI Identifies who is Responsible or Accountable for the Practice / Activities, and who is Consulted and Informed about the Practice / Activities Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 34
Website - Processes After the generic information on the COBIT 5 solution, do you want to learn a about. . . COBIT 5, Processes and reporting Greet Volders _ Voquals N. V. Voquals 4 GDPR MAVIM / COBIT 5 Voquals 4 Info Security The END Slide 35

More Information - Coordinates Voquals N. V. Greet Volders Genebroek 34 2450 Meerhout, Belgium Phone Mobile E-mail Website +32 14 22 54 04 +32 475 63 45 06 Gvolders@voquals. be www. voquals. be MAVIM See video’s for more information on MAVIM and their other solutions u Business Process & Quality Management and demonstration u Governance, Risk & Compliance and demonstration u Application Implementation Management and demonstration u IT Portfolio Management and demonstration u Strategic Portfolio Management and demonstration u Enterprise Architecture and demonstration Greet Volders _ Voquals N. V. MAVIM / COBIT 5 Slide 36
- Slides: 36