CMSC 414 Computer and Network Security Lecture 5

















- Slides: 18

CMSC 414 Computer (and Network) Security Lecture 5 Jonathan Katz

Attacks ¨ Ciphertext only ¨ Known plaintext ¨ Chosen ciphertext (includes chosen plaintext attacks)

Randomized encryption ¨ To be secure against chosen-plaintext attack, encryption must be randomized – We will see later how this comes into play

Block ciphers ¨ Keyed (invertible) permutation; input/output length ¨ Large key space; large input/output length – Both are critical ¨ Modeled as a (family of) random permutations…

A possible encryption scheme ¨ Example – “trivial” encryption: – C = FK(m) – This is not randomized…

An improved scheme ¨ <r, FK(r) m > ¨ Is this secure…? ¨ What about for longer messages?

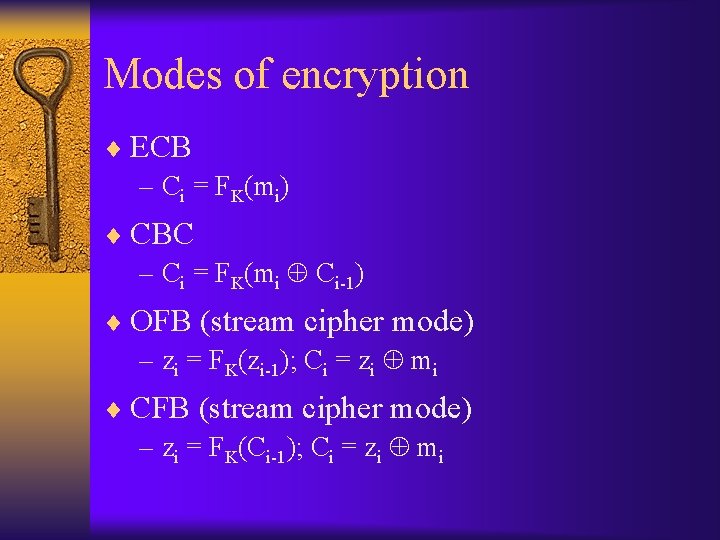
Modes of encryption ¨ ECB – Ci = FK(mi) ¨ CBC – Ci = FK(mi Ci-1) ¨ OFB (stream cipher mode) – zi = FK(zi-1); Ci = zi mi ¨ CFB (stream cipher mode) – zi = FK(Ci-1); Ci = zi mi

Security? ¨ All previous modes (except ECB) are secure against chosen-plaintext attacks ¨ None of these modes are secure against chosen-ciphertext attacks

Data Encryption Standard (DES) ¨ Developed in 1977 by NBS ¨ 56 -bit key, 64 -bit input/output – A 64 -bit key is derived from 56 random bits – One bit in each octet is a parity-check bit – The “short” key length is a major concern…

DES: High-level description ¨ Encryption proceeds in a sequence of 16 rounds ¨ Each round uses a 48 -bit key (derived from the main key), acts on a 64 -bit input, and produces a 64 -bit output

DES: High-level description ¨ Each round proceeds as follows: – Input is divided into (L, R) – L’ = R – R’ = L F(K, R), where K is the round key – F is a non-invertible function! • But we will see that decryption is still possible – (L’, R’) is then permuted in some fixed way to give the output at that round

3 -DES ¨ Expands the key length ¨ Now, key K = (K 1, K 2); |K| = 112 ¨ The “new” block cipher is just: – EK 1, K 2(m) = DESK 1(DES-1 K 2(DESK 1(m))) ¨ This is a permutation, and invertible…

Concerns about DES ¨ Short key length – DES “cracker”, built for $250 K, can break DES in days – Distributing the computation makes it faster ¨ Some (theoretical) attacks have been found ¨ Non-public design process ¨ 3 -DES is fairly slow

AES ¨ Public contest sponsored by NIST in ’ 97 – Narrowed to 5 finalists – 4 years of intense analysis ¨ Efficiency and security taken into account ¨ 128 -bit key length and 128 -bit block size (minimum) ¨ Rijndael selected as the AES – Supports variety of block/key sizes

Other ciphers? ¨ IDEA ¨ RC 4 ¨ No compelling reason to use anything other than AES, in general – Unless (possibly) you have very specific performance requirements – Even then, think twice

Public-key encryption (PKE)

Why PKE? ¨ Problem with private-key encryption is the need to securely share keys ¨ PKE allows users to publish their public key widely – only need to keep their private key secret ¨ Development of PKE was a huge advance – All classical systems, for 1000 years, were symmetric-key based

Some basic number theory ¨ Modular arithmetic: Zp, ZN ¨ Euclidean gcd algorithm, inverses, Z*N ¨ Efficient modular exponentiation ¨ Groups, order, (N), Fermat’s theorem ¨ Primality testing