CLOUD SECURITY Concerns Complications and Considerations Dr Susan






















- Slides: 37

CLOUD SECURITY: Concerns, Complications and Considerations Dr. Susan Cole, CISSP, CCSK scole@faculty. ctuonline. edu

Agenda What is it? ¡ Definition ¡ Deployment Models ¡ Service Models Benefits Concerns Complications Risks Improvements Considerations December 10, 2013

What is it? - Definition Cloud computing is a model for enabling ubiquitous, convenient, ondemand network access to a shared pool of configurable computing resources (e. g. , networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. (Grance and Mell, 2011) What goes “into” the Cloud? • Data/information • Applications/functions/processes December 10, 2013

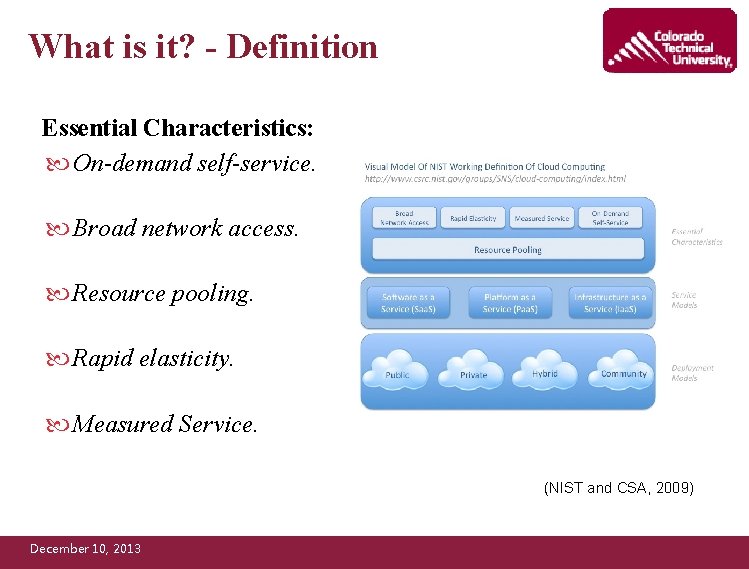
What is it? - Definition Essential Characteristics: On-demand self-service. Broad network access. Resource pooling. Rapid elasticity. Measured Service. (NIST and CSA, 2009) December 10, 2013

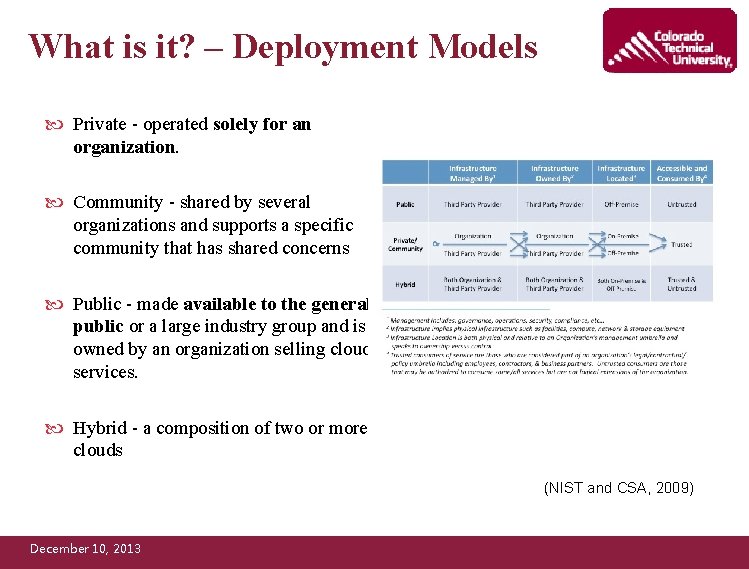
What is it? – Deployment Models Private - operated solely for an organization. Community - shared by several organizations and supports a specific community that has shared concerns Public - made available to the general public or a large industry group and is owned by an organization selling cloud services. Hybrid - a composition of two or more clouds (NIST and CSA, 2009) December 10, 2013

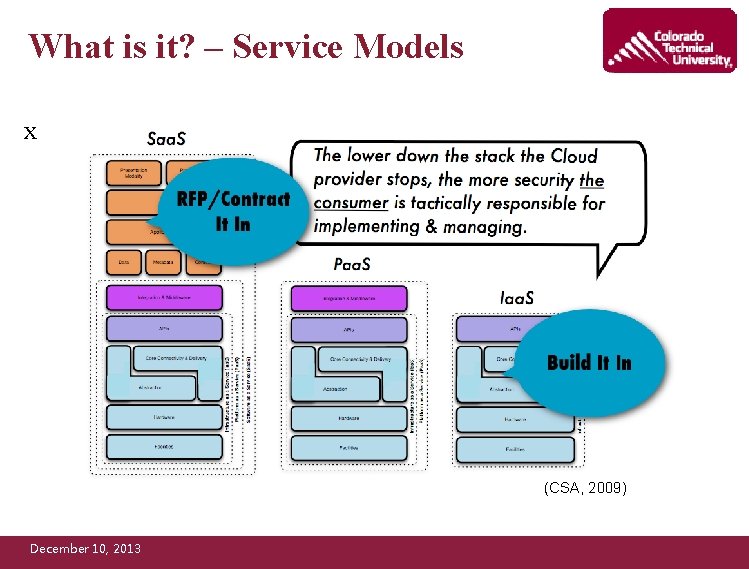
What is it? – Service Models Software as a Service (Saa. S) ¡ Delivers applications hosted on cloud as internet-based services ¡ Does not require installing apps on customers’ computers ¡ Example: Salesforce Platform as a Service (Paa. S) ¡ Delivers platforms, tools, services ¡ Without installing any of these platforms or support tools on local machines ¡ Example: Google Apps Infrastructure as a Service (Iaa. S) ¡ Delivers “computation resources, ” network and storage as internet-based service ¡ Example: Amazon EC 2 December 10, 2013

What is it? – Service Models x (CSA, 2009) December 10, 2013

Benefits Availability! Economic benefits! ¡ Cost Reduction ¡ Scalable ¡ Easier to collaborate (long-distance) ¡ Small and mid-size business access to tech at lower prices There’s a chance security will be as good or better if cloud provider is a quality service provider. December 10, 2013

Benefits Ways to Use the Cloud Social Media Business Applications Productivity Applications Email as a service Infrastructure Website hosting Storage Empower Mobile Devices (BYOD) December 10, 2013

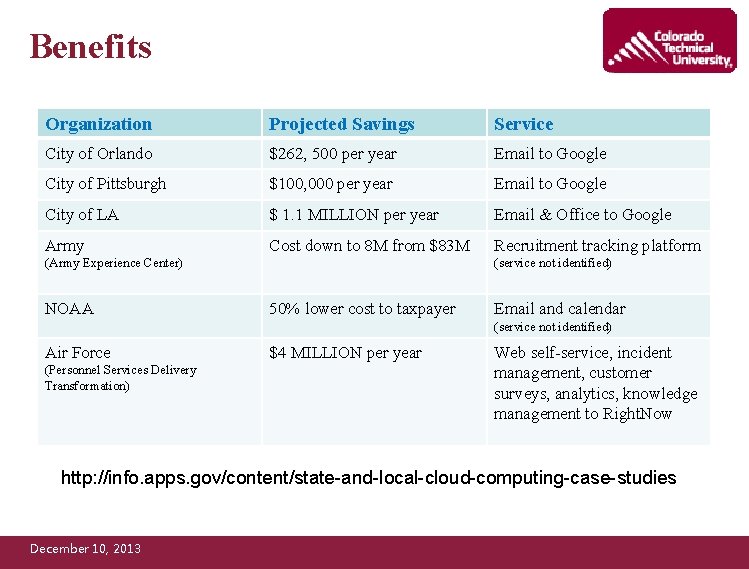
Benefits Organization Projected Savings Service City of Orlando $262, 500 per year Email to Google City of Pittsburgh $100, 000 per year Email to Google City of LA $ 1. 1 MILLION per year Email & Office to Google Army Cost down to 8 M from $83 M Recruitment tracking platform (Army Experience Center) NOAA (service not identified) 50% lower cost to taxpayer Email and calendar (service not identified) Air Force (Personnel Services Delivery Transformation) $4 MILLION per year Web self-service, incident management, customer surveys, analytics, knowledge management to Right. Now http: //info. apps. gov/content/state-and-local-cloud-computing-case-studies December 10, 2013

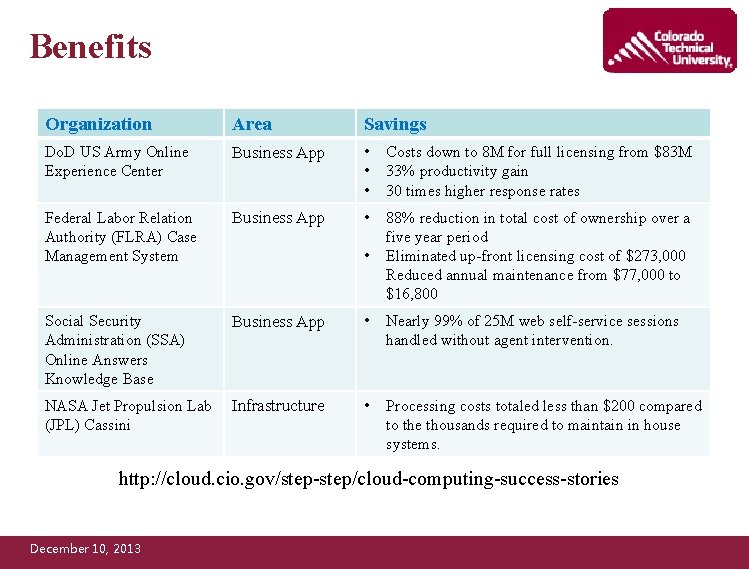
Benefits Organization Area Savings Do. D US Army Online Experience Center Business App • • • Costs down to 8 M for full licensing from $83 M 33% productivity gain 30 times higher response rates Federal Labor Relation Authority (FLRA) Case Management System Business App • 88% reduction in total cost of ownership over a five year period Eliminated up-front licensing cost of $273, 000 Reduced annual maintenance from $77, 000 to $16, 800 Social Security Administration (SSA) Online Answers Knowledge Base Business App • Nearly 99% of 25 M web self-service sessions handled without agent intervention. NASA Jet Propulsion Lab (JPL) Cassini Infrastructure • Processing costs totaled less than $200 compared to the thousands required to maintain in house systems. • http: //cloud. cio. gov/step-step/cloud-computing-success-stories December 10, 2013

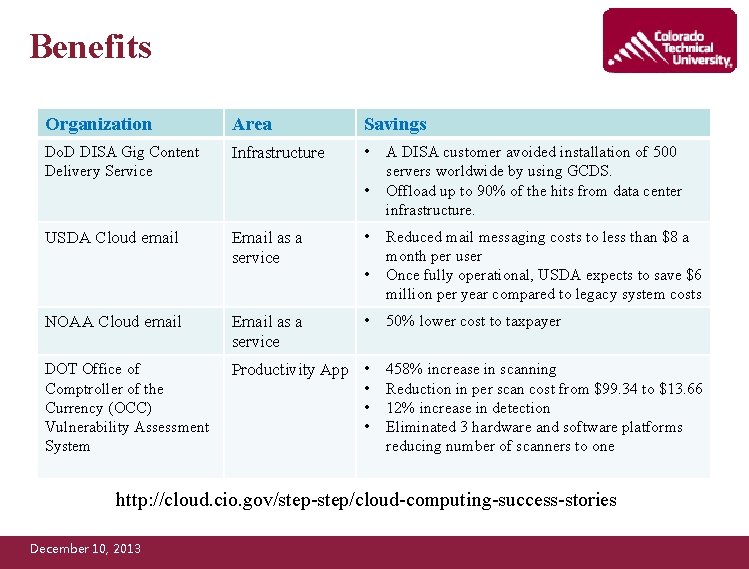
Benefits Organization Area Savings Do. D DISA Gig Content Delivery Service Infrastructure • • Email as a service • NOAA Cloud email Email as a service • DOT Office of Comptroller of the Currency (OCC) Vulnerability Assessment System Productivity App • • USDA Cloud email • A DISA customer avoided installation of 500 servers worldwide by using GCDS. Offload up to 90% of the hits from data center infrastructure. Reduced mail messaging costs to less than $8 a month per user Once fully operational, USDA expects to save $6 million per year compared to legacy system costs 50% lower cost to taxpayer 458% increase in scanning Reduction in per scan cost from $99. 34 to $13. 66 12% increase in detection Eliminated 3 hardware and software platforms reducing number of scanners to one http: //cloud. cio. gov/step-step/cloud-computing-success-stories December 10, 2013

Benefits Organization Area Savings Benefits. gov Hybrid Cloud Implementation Website Hosting • Initially, a 60% reduction in costs due to a discount provided by USDA Bureau of Engraving and Printing Public-Facing Website Hosting • Reduced infrastructure costs from $800, 000 to $1, 550 http: //cloud. cio. gov/step-step/cloud-computing-success-stories December 10, 2013

Concerns Migration Costs Additional training for staff New monitoring systems (Ashford, 2012) December 10, 2013

Concerns Security is “arguably the most significant barrier to faster and more widespread adoption of cloud computing. ” (Chen, et al, 2010) December 10, 2013

Concerns Shared Risks Outsourcing security to a 3 rd party = loss of control Coexistence of different tenants using same instance of service but unaware of strength of the other’s security controls Lack of security guarantees in SLAs Hosting on publicly available infrastructure increases probability of attacks December 10, 2013

Concerns Shared Risks “Cloud providers priorities do not always align with the customer’s objectives. ” Self-preservation Reporting to customer or externally… Is your cloud provider using services from yet another cloud provider? Need to protect not only data… but activity patterns Possible reverse engineering by others in the cloud to find out customer base, revenue, etc. December 10, 2013

Concerns Shared Risks Auditability in the cloud… Already required for banking and health sectors Should be “mutual” for provider and customer “Sharing of resources violates the confidentiality of tenants’ IT assets which leads to the need for secure multitenancy. ” (Morsey, et al, 2010) December 10, 2013

Complications BYOD Can’t avoid! Saves $ if employees provide devices Single device solution No need to carry multiple devices Improves morale Increases productivity Employees willing to work after-hours; always connected Federal Agencies have Pilot BYOD Programs NSA (mobile for classified by not BYOD yet) NIST 800 -124 December 10, 2013

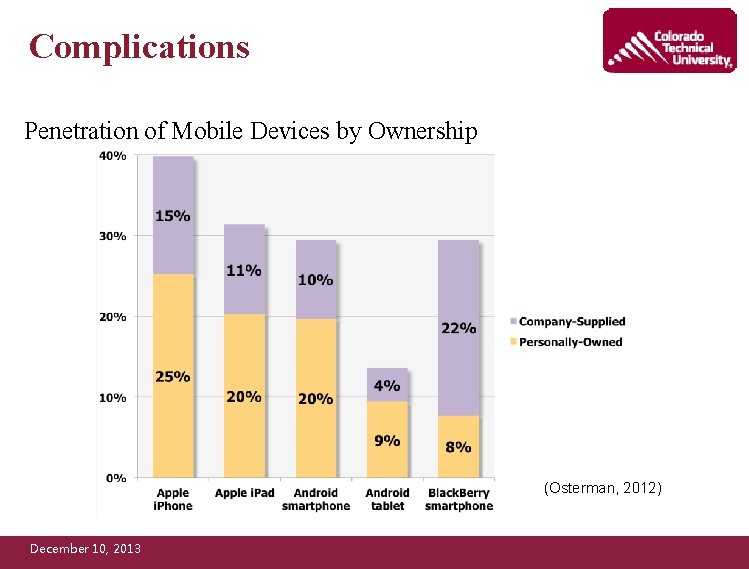
Complications Penetration of Mobile Devices by Ownership (Osterman, 2012) December 10, 2013

Complications Beyond the device… ¡What does access with a device like this mean? ¡Next generation has to have technology tools! Recruitment December 10, 2013

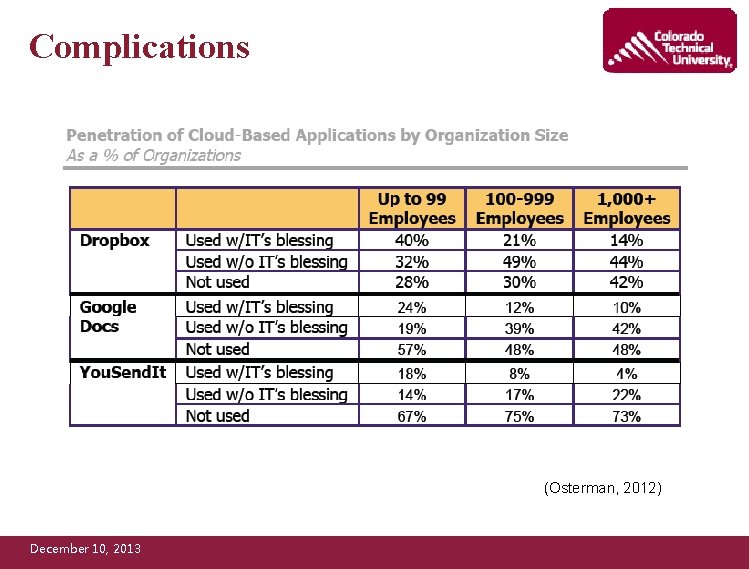
Complications (Osterman, 2012) December 10, 2013

Risks Application control Data Loss Labor laws Privacy Issues Regulatory requirements Lost and stolen devices Data recovery Expectation of Cloud Providers to manage security December 10, 2013

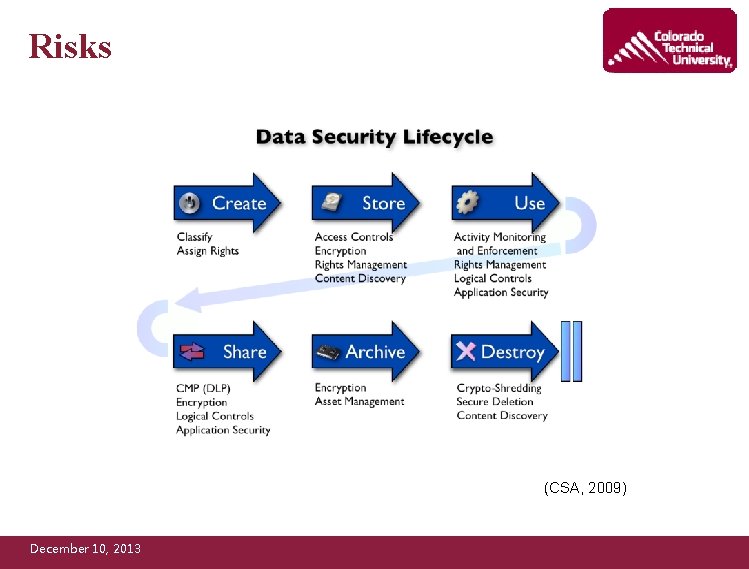
Risks (CSA, 2009) December 10, 2013

Improvements Cloud is becoming more secure ¡Fed. RAMP ¡Cloud Security Alliance STAR ¡Cloud Service Providers Built in versus added on December 10, 2013

Improvements Standards and Regulations ¡ http: //cloud. cio. gov/action/manage-your-cloud ¡ 25 Point Implementation Plan to Reform Information Technology Management Download: http: //cloud. cio. gov/document/25 -pointimplementaton-plan-reform-information-technologymanagement ¡ Federal Cloud Computing Strategy Download: http: //cloud. cio. gov/document/federal-cloudcomputing-strategy ¡ Federal IT Shared Services Strategy Download: http: //cloud. cio. gov/document/federal-it-shared-services -strategy December 10, 2013

Improvements Federal Data Center Consolidation Initiative (FDCCI) ¡https: //cio. gov/deliver/data-center-consolidation/ That could affect Cloud Security: ¡Legislation ¡TPM chips ¡Self-Encrypting Drives (SEDs) December 10, 2013

Considerations Identity Management Remote Management Virtualization Data-at-Rest Portability December 10, 2013

Considerations How to Apply Security 1. Determine what needs to go (data and/or functions) 2. Evaluate importance to organization 3. Evaluate deployment models 4. Evaluate service models 5. Evaluate cloud provider December 10, 2013 (CSA, 2009)

Considerations Three Options 1. Accept whatever assurances the service provider offers 2. Evaluate the service provider yourself 3. Use a neutral 3 rd party to conduct a security assessment The cloud provider should perform regular security assessment and provide reports to their clients. December 10, 2013

Considerations Security Assessments “Traditional service providers submit to external audits and security certifications, providing their customers with information on the specific controls that were evaluated. A cloud-computing provider that is unwilling or unable to do this is signaling that customers can only use them for the most trivial functions. ” (Heiser and Nicolett, 2008) December 10, 2013

Considerations How to Take Control Decide what (data and/or functions) should be migrated to the cloud… ¡ Cost/benefit analysis: not all are good choice ¡ Risk Assessment Investigate physical security of where data will be housed… Encrypt December 10, 2013

Considerations How to take control Schedule monthly meeting with security personnel of the cloud provider. Employ legal experts (experienced with “cloud”) early to formulate contract. Much easier than bringing in lawyers after the fact to fight Get definitions and procedures outlined in advance… (incidents, disasters, etc) December 10, 2013

References and Background Info December 10, 2013

References Almond, Carl. (2009). “A Practical Guide to Cloud Computing Security: What you need to know about your business and cloud security. ” Avanade Inc. Al Morsey, M. , Grundy, J. , and I. Muller. (2010). “An Analysis of The Cloud Computing Security Problem. ” APSEC 2010 Cloud Workshop, Sydney, Australia. Ashford, W. (2012). “Cloud Computing: Could it Cost More? ” Tech. Target. http: //www. computerweekly. com/news/2240163197/Cloud-computing-Could-it-cost-more Ashford, W. (2011). “Self-encrypting drives: SED the best-kept secret in hard drive encryption security ” Tech. Target. http: //www. computerweekly. com/feature/Self-encrypting-drives-SED-the-best-kept-secret-in-hard-drive-encryption-security Avanade (2012). “Global Survey: Dispelling Six Myths of Consumerization of IT. ” http: //www. avanade. com/Documents/Resources/consumerization-of-it-executive-summary. pdf Chen, Y. , Paxson, V. , and R. Katz. (2010). “What’s New About Cloud Computing Security? ” Electrical Engineering and Computer Sciences, University of California at Berkeley. Cloud Security Alliance (CSA) (2009). “Security Guidance for Critical Areas of Focus in Cloud Computing V 2. 1” Cox, P. (2010). “Remote management threatens Infrastructure as a Service security” Tech. Target. http: //searchcloudcomputing. techtarget. com/tip/How-to-use-Infrastructure-as-a-Service-securely-part-2 Grance, T. and P. Mell (2011). “The NIST Definition of Cloud Computing (Draft). ” NIST Special Publication 800 -145 (Draft). December 10, 2013 35

References Grance, T. and P. Mell (2011). “The NIST Definition of Cloud Computing (Draft). ” NIST Special Publication 800 -145 (Draft). Heiser, J. and M. Nicolett. (2008). “Assessing the Security Risks of Cloud Computing. ” Gartner. Hess, K, (2012). “BYOD busted? It's OK we know you're doing it. ” ZDNet. http: //www. zdnet. com/blog/consumerization/byodbusted-its-ok-we-know-youre-doing-it/169 Holland, K. (2011). “Pros and Cons of Cloud Computing. ” Beckon. http: //www. thebeckon. com/pros-and-cons-of-cloudcomputing/ Iyengar, G. (2011). “Cloud Computing – Maze in the Haze. ” SANS: GIAC (GSEC) Gold Certification Paper. Jacobs, D. (2013). “The TPM chip: An unexploited resource for network security. ” Tech. Target. http: //searchnetworking. techtarget. com/tip/The-TPM-chip-An-unexploited-resource-for-network-security Mimosa, M. (2012). “TPM Chip in Windows 8 Lays Foundation for Widespread Enhancements to Hardware-Based Security. ” Threatpost. http: //threatpost. com/en_us/blogs/tpm-chip-windows-8 -lays-foundation-widespread-enhancements-hardware-basedsecurity-102612 Osterman (2012), sponsored by Accellion. “Putting IT Back in Control of BYOD: An Osterman Research White Paper” December 10, 2013 36

References Reed, J. (2010). “Following Incident into the Cloud. ” SANS: GIAC (GCIH) Gold Certification Paper. Rouse, M. (2012). “Identity as a Service. ” Tech. Target. http: //searchconsumerization. techtarget. com/definition/identity-as-a. Service-IDaa. S Sinclair, J. (2010). “Auditing in Cloud Computing. ” SAP RESEARCH. http: //www. slideshare. net/jonathansinclair 86/cloudauditing Tutti, C. (2011). “NIST Cloud Roadmap: Too much too fast? ” Federal Computer Week. Vizard, M. (2012) “The Keys to the Cloud Security Kingdom. ” IT Business Edge. http: //www. itbusinessedge. com/cm/blogs/vizard/the-keys-to-the-cloud-securitykingdom/? cs=49788&utm_source=feedburner&utm_medium=twitter&utm_campaign=Feed%3 A+Mike. Vizard+%28 Mike+Vizard %29 Winkler, V. (2011). “Cloud Computing: Virtual Cloud Security Concerns. ” Tech. Net. http: //technet. microsoft. com/enus/magazine/hh 641415. aspx December 10, 2013 37