Cloud Native Access Point CNAP Internet AWS Gov

- Slides: 7

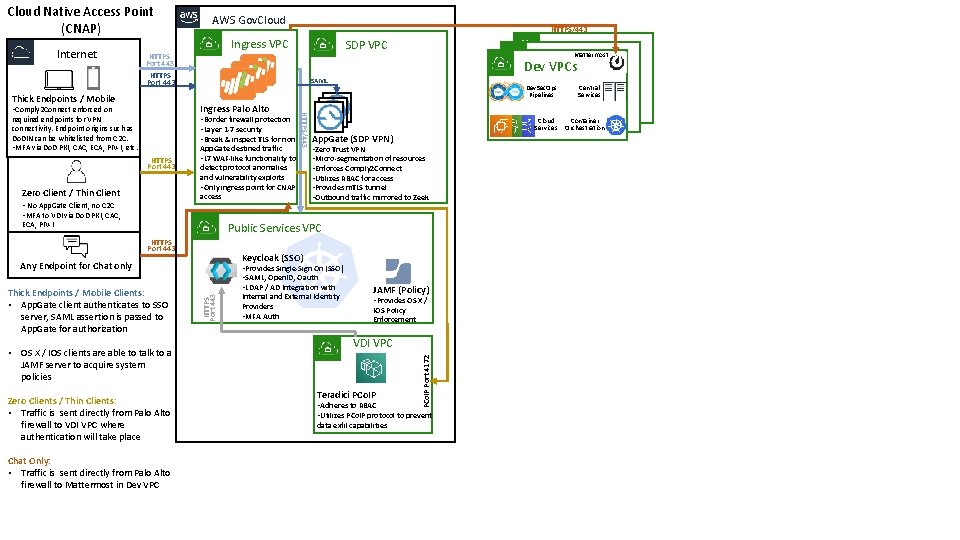
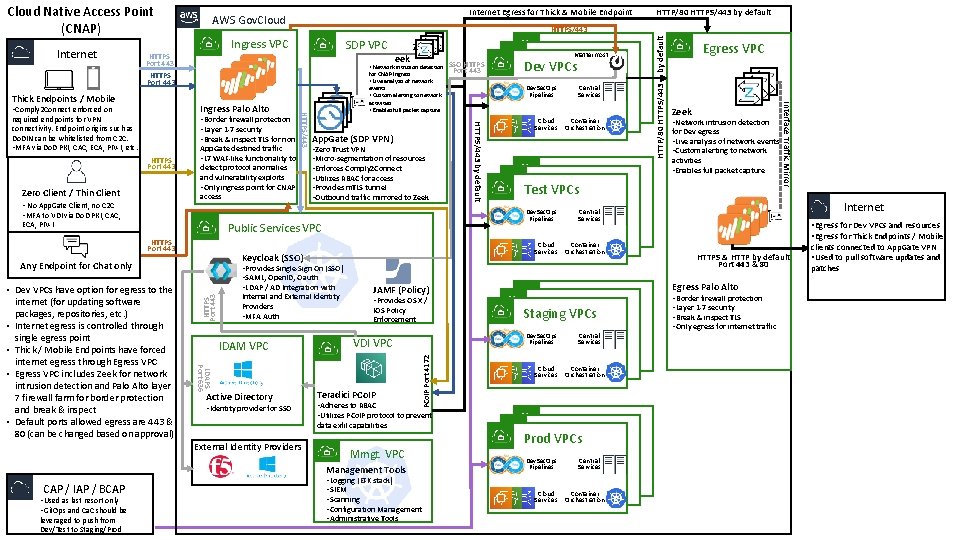
Cloud Native Access Point (CNAP) Internet AWS Gov. Cloud Ingress VPC HTTPS Port 443 Thick Endpoints / Mobile SDP VPC Ingress Palo Alto • Comply 2 Connect enforced on required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS Port 443 Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, ECA, PIV-I HTTPS Port 443 Any Endpoint for Chat only Access begins by end-user HTTPS traffic passing through Ingress Palo Alto which provides: • Break & inspect of TLS • Ingress border firewall protection • Layer 1 -7 security App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access App. Gate (SDP VPN) • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek

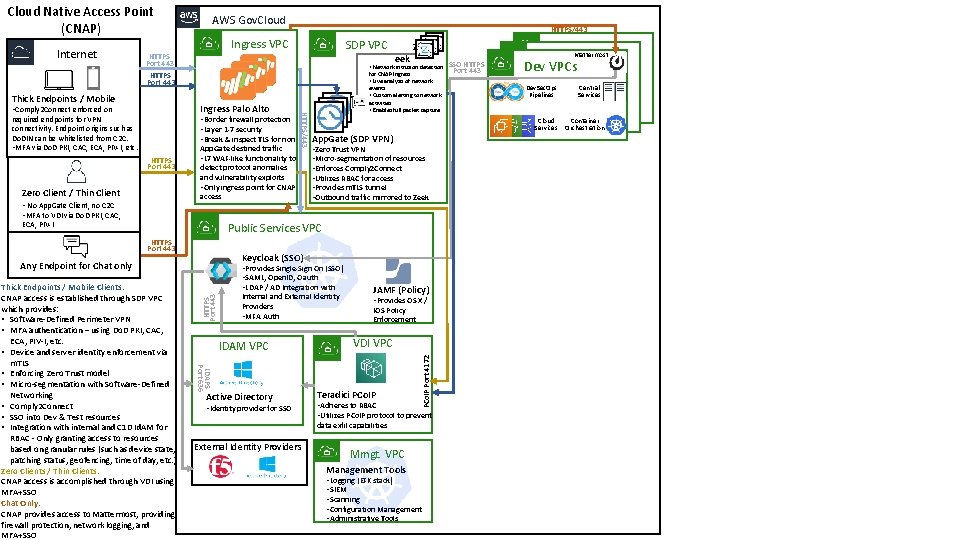
Cloud Native Access Point (CNAP) HTTPS/443 Ingress VPC SDP VPC HTTPS Port 443 Thick Endpoints / Mobile SAML required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS Port 443 Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access ECA, PIV-I HTTPS/443 Ingress Palo Alto • Comply 2 Connect enforced on Dev Mattermost VPCs Dev. Sec. Ops Pipelines Cloud Services App. Gate (SDP VPN) • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek Public Services VPC HTTPS Port 443 Keycloak (SSO) Any Endpoint for Chat only • OS X / IOS clients are able to talk to a JAMF server to acquire system policies Zero Clients / Thin Clients: • Traffic is sent directly from Palo Alto firewall to VDI VPC where authentication will take place Chat Only: • Traffic is sent directly from Palo Alto firewall to Mattermost in Dev VPC HTTPS Port 443 Thick Endpoints / Mobile Clients: • App. Gate client authenticates to SSO server, SAML assertion is passed to App. Gate for authorization • Provides Single-Sign On (SSO) • SAML, Open. ID, Oauth • LDAP / AD Integration with Internal and External Identity Providers • MFA Auth JAMF (Policy) • Provides OS X / IOS Policy Enforcement VDI VPC Teradici PCo. IP Port 4172 Internet AWS Gov. Cloud • Adheres to RBAC • Utilizes PCo. IP protocol to prevent data exfil capabilities Central Services Container Orchestration

Cloud Native Access Point (CNAP) HTTPS/443 Ingress VPC SDP VPC HTTPS Port 443 Thick Endpoints / Mobile eek • Network intrusion detection • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS Port 443 Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access ECA, PIV-I HTTPS/443 required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. for CNAP Ingress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture SAML Ingress Palo Alto • Comply 2 Connect enforced on Z App. Gate (SDP VPN) • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek Public Services VPC HTTPS Port 443 Keycloak (SSO) Any Endpoint for Chat only HTTPS Port 443 • Provides Single-Sign On (SSO) • SAML, Open. ID, Oauth • LDAP / AD Integration with Internal and External Identity Providers • MFA Auth IDAM VPC LDAPS Port 636 Thick Endpoints / Mobile Clients: CNAP access is established through SDP VPC which provides: • Software-Defined Perimeter VPN • MFA authentication – using Do. D PKI, CAC, ECA, PIV-I, etc. • Device and server identity enforcement via m. TLS • Enforcing Zero Trust model • Micro-segmentation with Software-Defined Networking • Comply 2 Connect • SSO into Dev & Test resources • Integration with internal and C 1 D Id. AM for RBAC - Only granting access to resources based on granular rules (such as device state, patching status, geofencing, time of day, etc. ) Zero Clients / Thin Clients: CNAP access is accomplished through VDI using MFA+SSO Chat Only: CNAP provides access to Mattermost, providing firewall protection, network logging, and MFA+SSO Active Directory • Identity provider for SSO JAMF (Policy) • Provides OS X / IOS Policy Enforcement VDI VPC Teradici PCo. IP • Adheres to RBAC • Utilizes PCo. IP protocol to prevent data exfil capabilities External Identity Providers SSO HTTPS Port 443 Dev Mattermost VPCs Dev. Sec. Ops Pipelines Cloud Services PCo. IP Port 4172 Internet AWS Gov. Cloud Mmgt. VPC Management Tools • Logging (EFK stack) • SIEM • Scanning • Configuration Management • Administrative Tools Central Services Container Orchestration

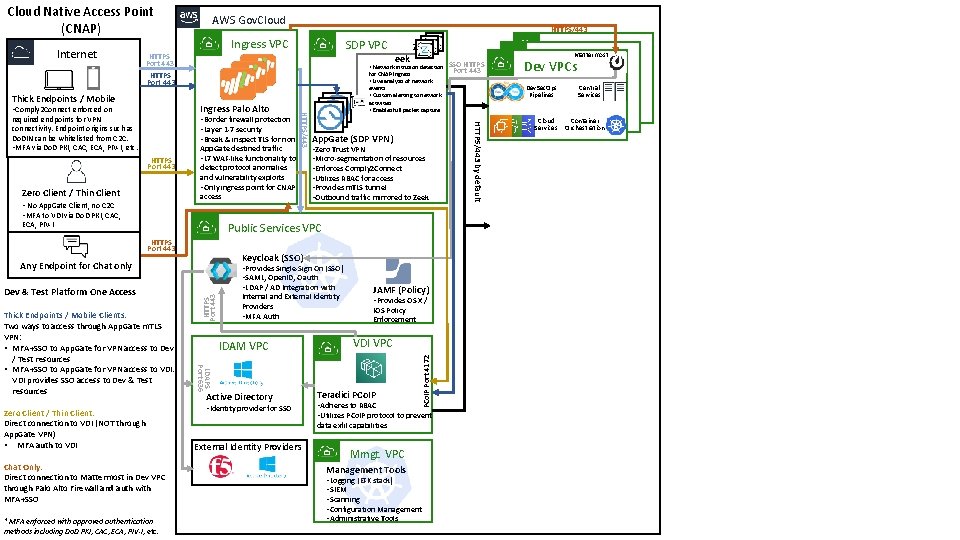
Cloud Native Access Point (CNAP) HTTPS/443 Ingress VPC SDP VPC HTTPS Port 443 Thick Endpoints / Mobile eek • Network intrusion detection HTTPS Port 443 Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access ECA, PIV-I App. Gate (SDP VPN) • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek Public Services VPC HTTPS Port 443 Keycloak (SSO) Any Endpoint for Chat only Zero Client / Thin Client: Direct connection to VDI (NOT through App. Gate VPN) • MFA auth to VDI Chat Only: Direct connection to Mattermost in Dev VPC through Palo Alto Firewall and auth with MFA+SSO * MFA enforced with approved authentication methods including Do. D PKI, CAC, ECA, PIV-I, etc. Internal and External Identity Providers • MFA Auth IDAM VPC LDAPS Port 636 Thick Endpoints / Mobile Clients: Two ways to access through App. Gate m. TLS VPN: • MFA+SSO to App. Gate for VPN access to Dev / Test resources • MFA+SSO to App. Gate for VPN access to VDI provides SSO access to Dev & Test resources HTTPS Port 443 Dev & Test Platform One Access • Provides Single-Sign On (SSO) • SAML, Open. ID, Oauth • LDAP / AD Integration with Active Directory • Identity provider for SSO JAMF (Policy) • Provides OS X / IOS Policy Enforcement VDI VPC Teradici PCo. IP • Adheres to RBAC • Utilizes PCo. IP protocol to prevent data exfil capabilities External Identity Providers Mmgt. VPC Management Tools • Logging (EFK stack) • SIEM • Scanning • Configuration Management • Administrative Tools SSO HTTPS Port 443 Dev Mattermost VPCs Dev. Sec. Ops Pipelines HTTPS/443 by default • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS/443 required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. for CNAP Ingress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture SAML Ingress Palo Alto • Comply 2 Connect enforced on Z PCo. IP Port 4172 Internet AWS Gov. Cloud Services Central Services Container Orchestration

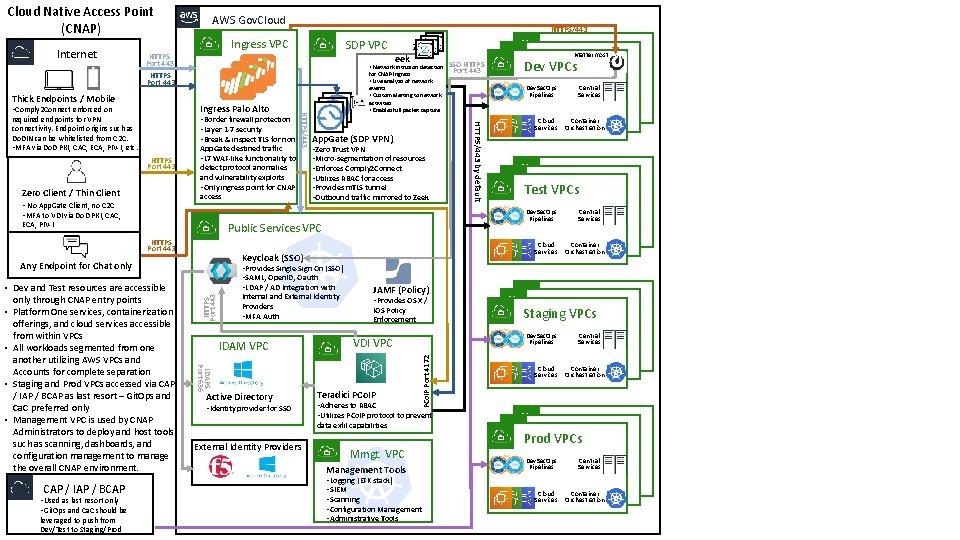
Cloud Native Access Point (CNAP) Ingress VPC Thick Endpoints / Mobile eek Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access ECA, PIV-I • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek HTTPS Port 443 • Provides Single-Sign On (SSO) • SAML, Open. ID, Oauth • LDAP / AD Integration with Internal and External Identity Providers • MFA Auth IDAM VPC LDAPS Port 636 • Dev and Test resources are accessible only through CNAP entry points • Platform One services, containerization offerings, and cloud services accessible from within VPCs • All workloads segmented from one another utilizing AWS VPCs and Accounts for complete separation • Staging and Prod VPCs accessed via CAP / IAP / BCAP as last resort – Git. Ops and Ca. C preferred only • Management VPC is used by CNAP Administrators to deploy and host tools such as scanning, dashboards, and configuration management to manage the overall CNAP environment. Active Directory • Identity provider for SSO JAMF (Policy) • Provides OS X / IOS Policy Enforcement Cloud Services Teradici PCo. IP • Adheres to RBAC • Utilizes PCo. IP protocol to prevent Mmgt. VPC Management Tools • Logging (EFK stack) • SIEM • Scanning • Configuration Management • Administrative Tools Central Services Container Orchestration Dev VPCs Test VPCs Central Services Container Orchestration Dev VPCs Staging VPCs Dev. Sec. Ops Pipelines VDI VPC data exfil capabilities External Identity Providers Dev. Sec. Ops Pipelines Cloud Services Keycloak (SSO) Any Endpoint for Chat only Dev Mattermost VPCs Dev. Sec. Ops Pipelines Public Services VPC HTTPS Port 443 leveraged to push from Dev/Test to Staging/Prod App. Gate (SDP VPN) SSO HTTPS Port 443 HTTPS/443 by default • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS Port 443 for CNAP Ingress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture SAML HTTPS/443 required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. Z • Network intrusion detection Ingress Palo Alto • Comply 2 Connect enforced on • Used as last resort only • Git. Ops and Ca. C should be SDP VPC HTTPS Port 443 CAP / IAP / BCAP HTTPS/443 PCo. IP Port 4172 Internet AWS Gov. Cloud Services Central Services Container Orchestration Dev VPCs Prod VPCs Dev. Sec. Ops Pipelines Cloud Services Central Services Container Orchestration

SDP VPC • Network intrusion detection HTTPS Port 443 Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access ECA, PIV-I App. Gate (SDP VPN) • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek HTTPS Port 443 • Provides Single-Sign On (SSO) • SAML, Open. ID, Oauth • LDAP / AD Integration with Internal and External Identity Providers • MFA Auth IDAM VPC LDAPS Port 636 • Dev VPCs have option for egress to the internet (for updating software packages, repositories, etc. ) • Internet egress is controlled through single egress point • Thick / Mobile Endpoints have forced internet egress through Egress VPC • Egress VPC includes Zeek for network intrusion detection and Palo Alto layer 7 firewall farm for border protection and break & inspect • Default ports allowed egress are 443 & 80 (can be changed based on approval) Active Directory • Identity provider for SSO JAMF (Policy) • Provides OS X / IOS Policy Enforcement Teradici PCo. IP • Adheres to RBAC • Utilizes PCo. IP protocol to prevent Mmgt. VPC Management Tools CAP / IAP / BCAP • Used as last resort only • Git. Ops and Ca. C should be leveraged to push from Dev/Test to Staging/Prod Cloud Services • Logging (EFK stack) • SIEM • Scanning • Configuration Management • Administrative Tools Central Services Container Orchestration Dev VPCs Test VPCs Cloud Services Container Orchestration Central Services Container Orchestration Dev VPCs Prod VPCs Dev. Sec. Ops Pipelines Cloud Services Egress VPC Zeek • Network intrusion detection for Dev egress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture Internet Central Services Dev VPCs Staging VPCs Dev. Sec. Ops Pipelines VDI VPC data exfil capabilities External Identity Providers Dev. Sec. Ops Pipelines Cloud Services Keycloak (SSO) Any Endpoint for Chat only Dev Mattermost VPCs Dev. Sec. Ops Pipelines Public Services VPC HTTPS Port 443 SSO HTTPS Port 443 HTTPS/443 by default • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS/443 required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. for CNAP Ingress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture SAML Ingress Palo Alto • Comply 2 Connect enforced on Z Interface Traffic Mirror Thick Endpoints / Mobile eek by default Ingress VPC HTTPS Port 443 HTTP/80 HTTPS/443 by default HTTPS/443 PCo. IP Port 4172 Internet Egress for Thick & Mobile Endpoint AWS Gov. Cloud HTTP/80 HTTPS/443 Cloud Native Access Point (CNAP) Central Services Container Orchestration • Egress for Dev VPCs and resources • Egress for Thick Endpoints / Mobile HTTPS & HTTP by default Port 443 & 80 Egress Palo Alto • Border firewall protection • Layer 1 -7 security • Break & inspect TLS • Only egress for internet traffic clients connected to App. Gate VPN • Used to pull software updates and patches

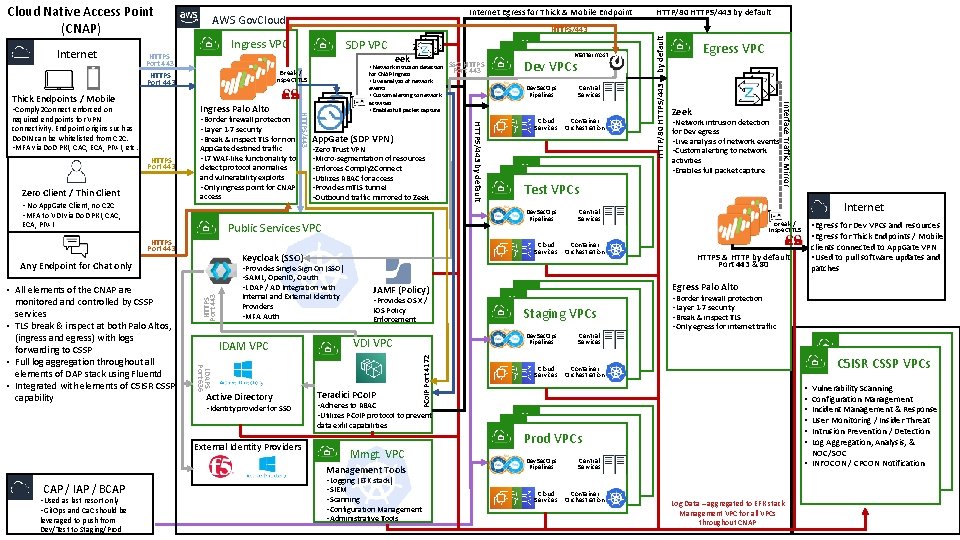
SDP VPC • Border firewall protection • Layer 1 -7 security • Break & inspect TLS for non HTTPS Port 443 Zero Client / Thin Client • No App. Gate Client, no C 2 C • MFA to VDI via Do. D PKI, CAC, App. Gate destined traffic • L 7 WAF-like functionality to detect protocol anomalies and vulnerability exploits • Only ingress point for CNAP access ECA, PIV-I for CNAP Ingress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture App. Gate (SDP VPN) • Zero Trust VPN • Micro-segmentation of resources • Enforces Comply 2 Connect • Utilizes RBAC for access • Provides m. TLS tunnel • Outbound traffic mirrored to Zeek HTTPS Port 443 • Provides Single-Sign On (SSO) • SAML, Open. ID, Oauth • LDAP / AD Integration with Internal and External Identity Providers • MFA Auth IDAM VPC LDAPS Port 636 • All elements of the CNAP are monitored and controlled by CSSP services • TLS break & inspect at both Palo Altos, (ingress and egress) with logs forwarding to CSSP • Full log aggregation throughout all elements of DAP stack using Fluentd • Integrated with elements of C 5 ISR CSSP capability Active Directory • Identity provider for SSO JAMF (Policy) • Provides OS X / IOS Policy Enforcement Teradici PCo. IP • Adheres to RBAC • Utilizes PCo. IP protocol to prevent Mmgt. VPC Management Tools CAP / IAP / BCAP • Used as last resort only • Git. Ops and Ca. C should be leveraged to push from Dev/Test to Staging/Prod Cloud Services • Logging (EFK stack) • SIEM • Scanning • Configuration Management • Administrative Tools Central Services Container Orchestration Dev VPCs Test VPCs Cloud Services Egress VPC Zeek • Network intrusion detection for Dev egress • Live analysis of network events • Custom alerting to network activities • Enables full packet capture Internet Central Services Container Orchestration Dev VPCs Staging VPCs Dev. Sec. Ops Pipelines VDI VPC data exfil capabilities External Identity Providers Dev. Sec. Ops Pipelines Cloud Services Keycloak (SSO) Any Endpoint for Chat only Dev Mattermost VPCs Dev. Sec. Ops Pipelines Public Services VPC HTTPS Port 443 SSO HTTPS Port 443 HTTPS/443 by default required endpoints for VPN connectivity. Endpoint origins such as Do. DIN can be whitelisted from C 2 C. • MFA via Do. D PKI, CAC, ECA, PIV-I, etc. HTTPS/443 Ingress Palo Alto • Comply 2 Connect enforced on • Network intrusion detection Break / Inspect TLS SAML Z Central Services Interface Traffic Mirror Thick Endpoints / Mobile eek by default Ingress VPC HTTPS Port 443 HTTP/80 HTTPS/443 by default HTTPS/443 PCo. IP Port 4172 Internet Egress for Thick & Mobile Endpoint AWS Gov. Cloud HTTP/80 HTTPS/443 Cloud Native Access Point (CNAP) Break / Inspect TLS Cloud Services clients connected to App. Gate VPN • Used to pull software updates and patches HTTPS & HTTP by default Port 443 & 80 Egress Palo Alto • Border firewall protection • Layer 1 -7 security • Break & inspect TLS • Only egress for internet traffic C 5 ISR CSSP VPCs Container Orchestration • • • Vulnerability Scanning Configuration Management Incident Management & Response User Monitoring / Insider Threat Intrusion Prevention / Detection Log Aggregation, Analysis, & NOC/SOC • INFOCON / CPCON Notification Dev VPCs Prod VPCs Dev. Sec. Ops Pipelines • Egress for Dev VPCs and resources • Egress for Thick Endpoints / Mobile Central Services Container Orchestration Log Data – aggregated to EFK stack Management VPC for all VPCs throughout CNAP