Cloud Computing Introduction to virtualization Outline o Motivation






- Slides: 43

Cloud Computing Introduction to virtualization

Outline o Motivation and introduction o Example: Xen n techniques n Evaluation

What is virtualization o Partitioning one physical server to multiple virtual servers n Virtual machines are isolated n One VM failure will not affect the others o Hypervisor software is the key n Or called virtualization manager n The layer between the hardware/OS and virtual machines n Manages the partitioning and isolation of system resources

Broader concept of virtualization o Combine multiple physical resources into one single virtual resource n Storage virtualization o Application virtualization: JVM, . Net o Network virtualization o Desktop virtualization

Benefits o Save money. n Many companies require one app on one machine for reliability o Save energy n Less physical servers, less energy consumption o Save time n Deploy, setup, startup quickly o Agile development n Developer can use multiple virtual OSes to simulate and test cross-platform software

History o Introduced by IBM in the 1960 s n To boost utilization of large, expensive mainframe systems o Gave away to C/S in 80 s and 90 s o Become hot again n Servers are cheap and powerful n Become the key component of cloud computing

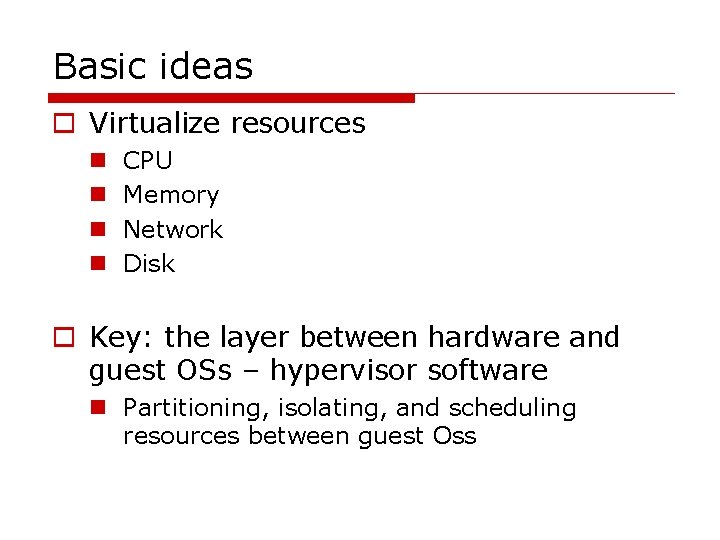
Basic ideas o Virtualize resources n n CPU Memory Network Disk o Key: the layer between hardware and guest OSs – hypervisor software n Partitioning, isolating, and scheduling resources between guest Oss

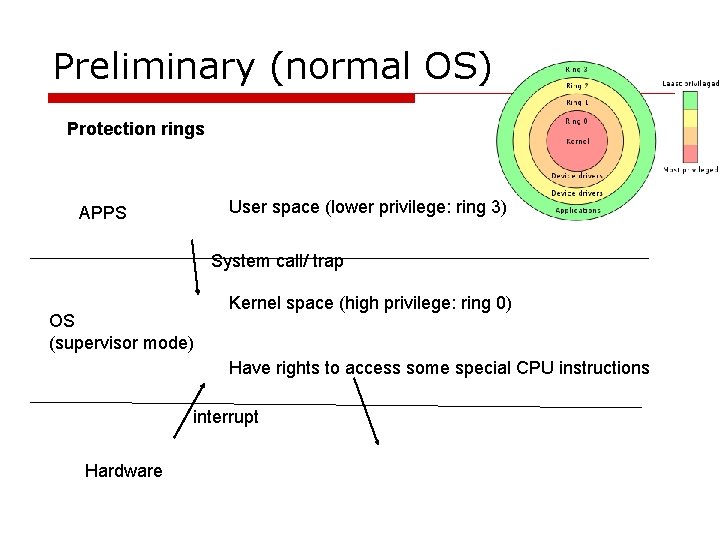
Preliminary (normal OS) Protection rings User space (lower privilege: ring 3) APPS System call/ trap OS (supervisor mode) Kernel space (high privilege: ring 0) Have rights to access some special CPU instructions interrupt Hardware

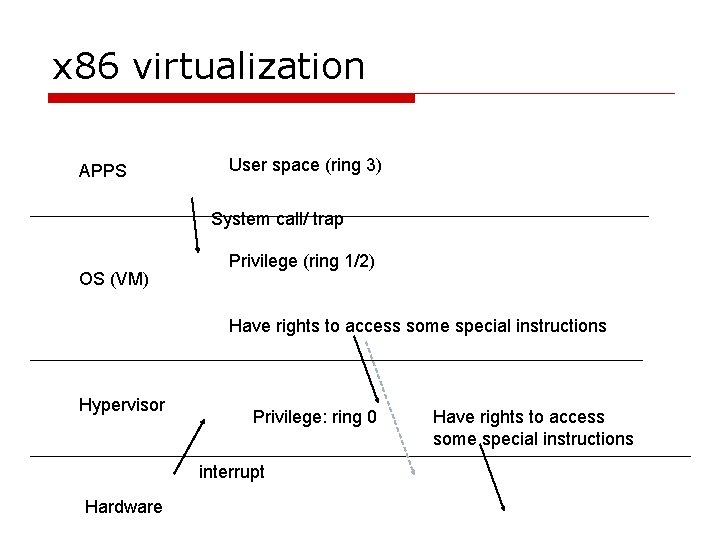
x 86 virtualization APPS User space (ring 3) System call/ trap OS (VM) Privilege (ring 1/2) Have rights to access some special instructions Hypervisor Privilege: ring 0 interrupt Hardware Have rights to access some special instructions

Types of virtualization o Container virtualization o Full virtualization o Para-virtualization

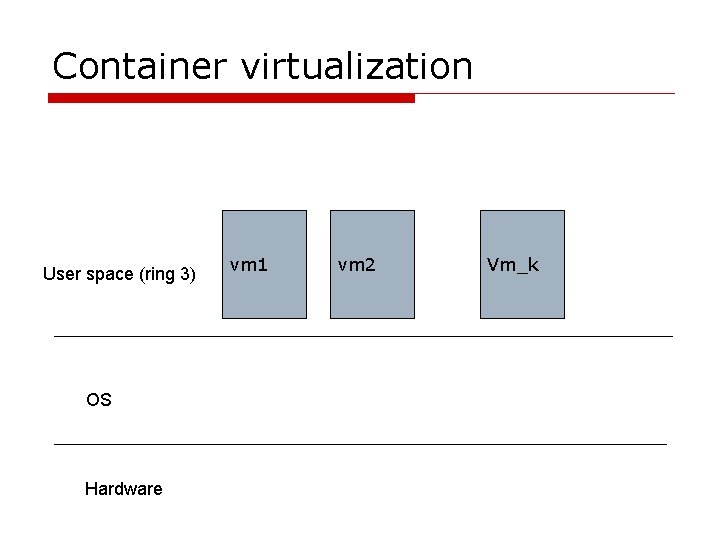
Container virtualization User space (ring 3) OS Hardware vm 1 vm 2 Vm_k

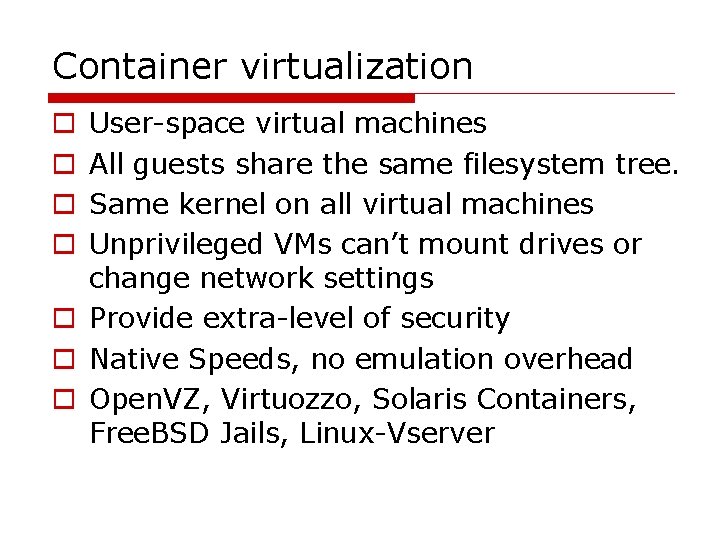
Container virtualization User-space virtual machines All guests share the same filesystem tree. Same kernel on all virtual machines Unprivileged VMs can’t mount drives or change network settings o Provide extra-level of security o Native Speeds, no emulation overhead o Open. VZ, Virtuozzo, Solaris Containers, Free. BSD Jails, Linux-Vserver o o

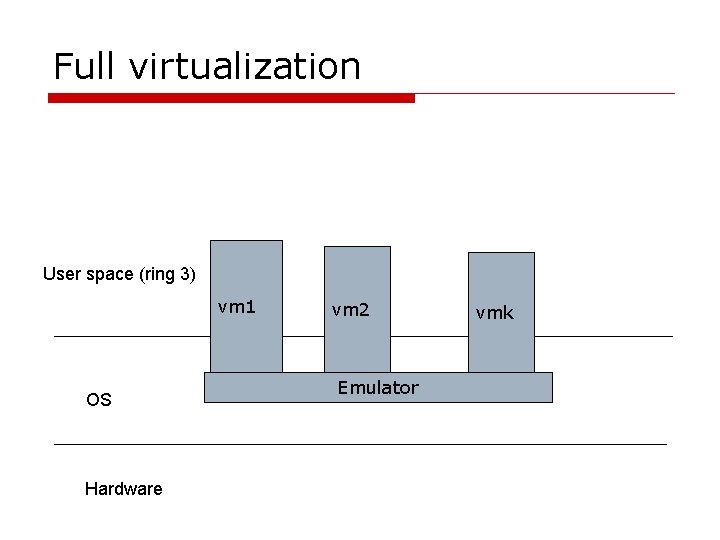
Full virtualization User space (ring 3) vm 1 OS Hardware vm 2 Emulator vmk

Full virtualization o Runs unmodified guests o Simulates bios, communicates with VMs through ACPI emulation, BIOS emulation, sometimes custom drivers n Guests cannot access hardware o Generally worst performance, but often acceptable o VMWare, Xen HVM, KVM, Microsoft VM, Parallels, virtualbox

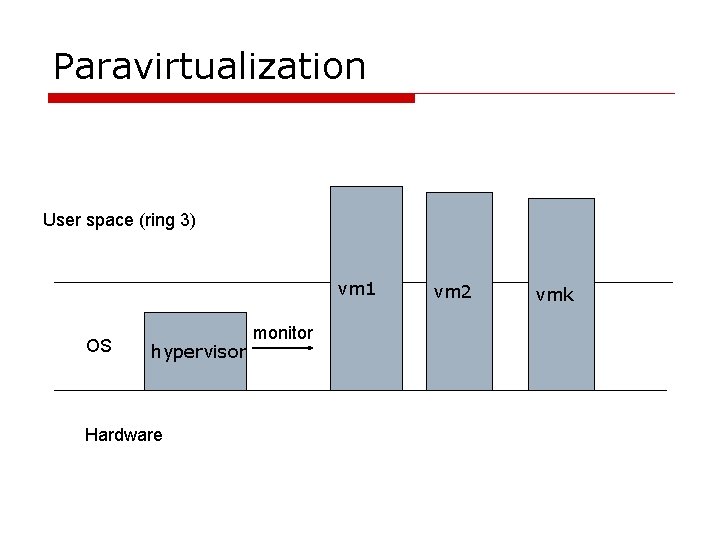
Paravirtualization User space (ring 3) vm 1 OS hypervisor Hardware monitor vm 2 vmk

Paravirtualization o Do not try to emulate everything n n n Work as a guard Pass safe instructions directly to CPU and device Guests have some exposure to the hardware o Better performance o Need to slightly modify guest OS, but no need to modify applications o Xen, Sun Logical Domains

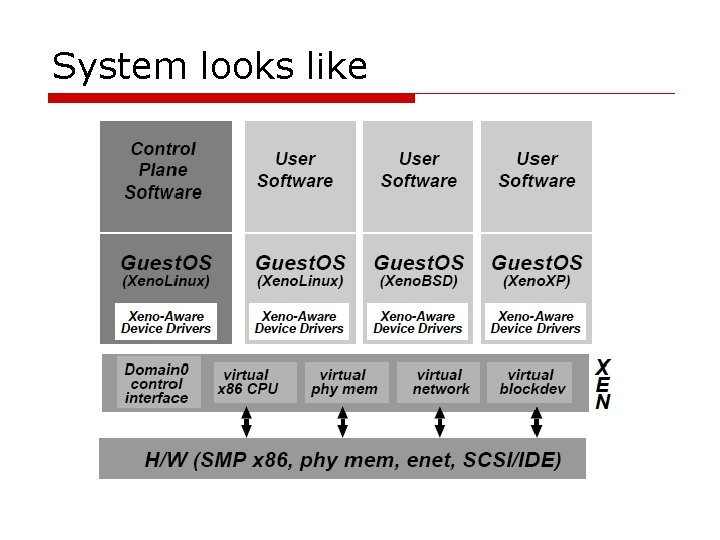
Xen: introduction o o Paravirtualization Faster than full virtualization Need to slightly change some guest OS Domain (1 -) : guest OS

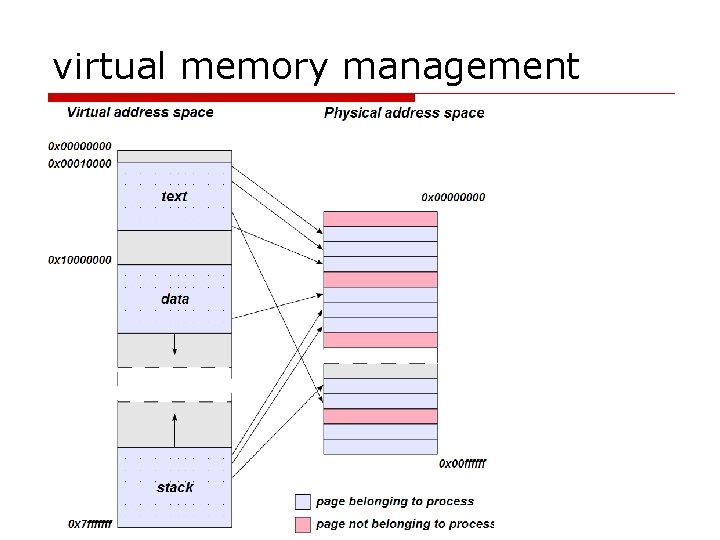
virtual memory management

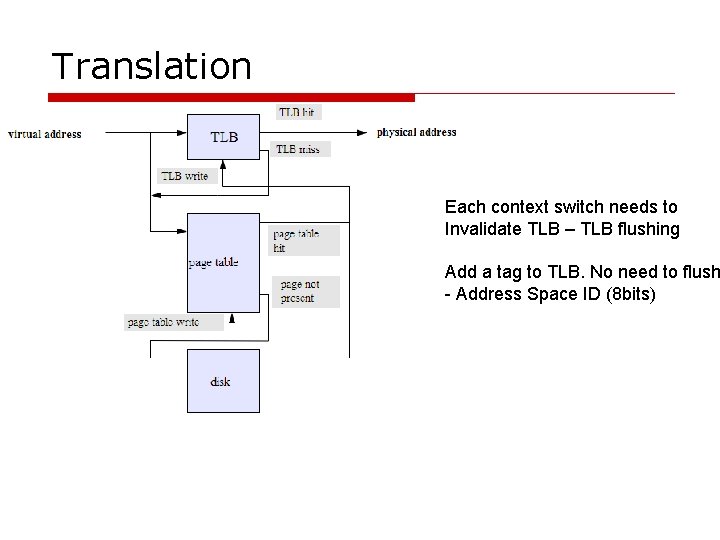
Translation Each context switch needs to Invalidate TLB – TLB flushing Add a tag to TLB. No need to flush - Address Space ID (8 bits)

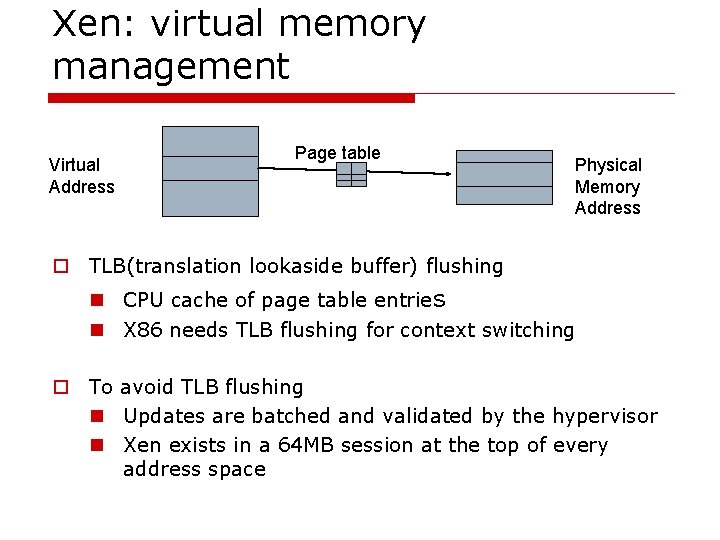
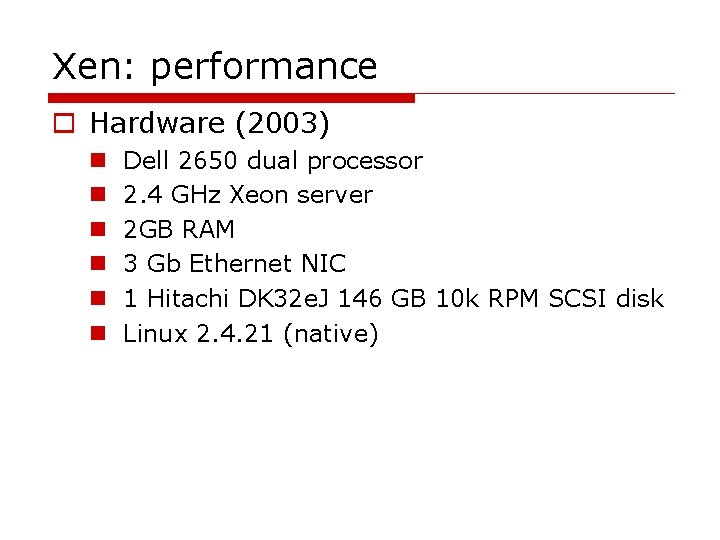
Xen: virtual memory management Virtual Address Page table Physical Memory Address o TLB(translation lookaside buffer) flushing n CPU cache of page table entries n X 86 needs TLB flushing for context switching o To avoid TLB flushing n Updates are batched and validated by the hypervisor n Xen exists in a 64 MB session at the top of every address space

o Minimize complexity n Let guest OSes allocate and manage the hardware page tables n Minimal involvement to ensure safety and isolation

Xen: memory allocation o At the beginning of creating guest OS n A fixed amount of physical memory is allocated (reservation) n Claim additional memory from Xen, when needed; release memory to Xen after finish o Allocated memory are not contiguous n “Physical memory” a virtual view of contiguous memory by guest OS n “hardware memory”: real physical memory n Guest OS builds a map between physical memory and hardware memory

When start a new process o Guest OS requires a new page table o Allocates and initializes a page from its own memory reservation and register it with Xen o Relinquish write privileges to the pagetable memory – all updates must be validated by Xen

Xen: CPU scheduling o Guest OS runs at a lower privilege level than Xen o Guest OS must register exception (trap) handlers with Xen n Xen will check the handler n Page fault is handled differently o System calls : no Xen intervention o Use a lightweight event system to handle hardware interrupts

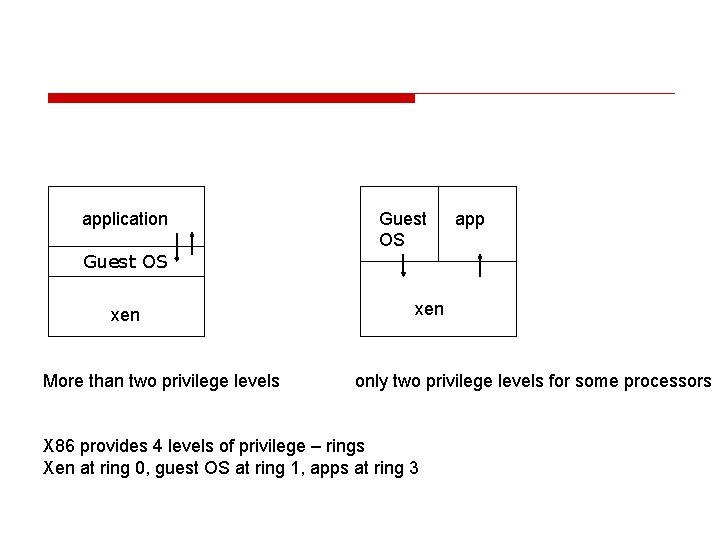
application Guest OS xen More than two privilege levels Guest OS app xen only two privilege levels for some processors X 86 provides 4 levels of privilege – rings Xen at ring 0, guest OS at ring 1, apps at ring 3

o Two types of frequent exception n System calls n Page faults o Improve performance of system calls n A fast exception handler accessed directly by the processor without via ring 0; validated before installing it in the hardware exception table n Validation: check the handler’s code segment – no execution in ring 0

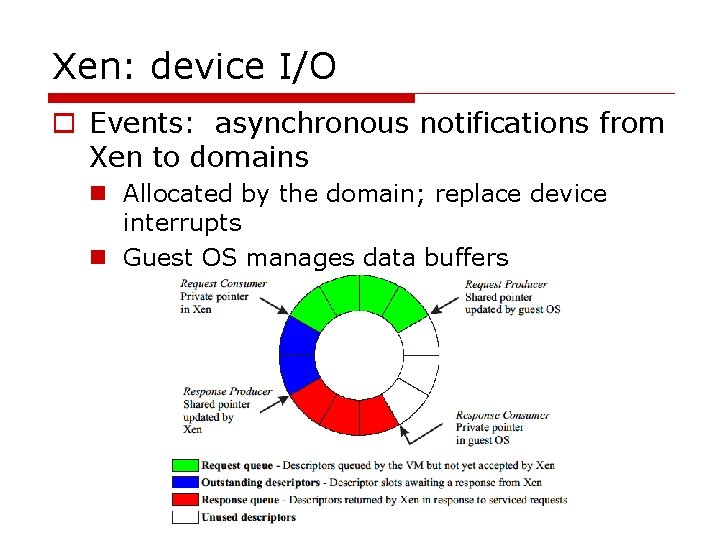
Xen: device I/O o Events: asynchronous notifications from Xen to domains n Allocated by the domain; replace device interrupts n Guest OS manages data buffers

Xen: device I/O o Only Domain 0 has direct access to disks o Other domains need to use virtual block devices n Use the I/O ring n Reorder requests prior to enqueuing them on the ring n use DMA (zero copy)

Xen: network o Virtual firewall-router attached to all domains o To send a packet, enqueue a buffer descriptor into the I/O ring o Use DMA (no packet copying)

Partitioning resources between guest OSes o Memory- preallocated physical memory o Disk – quota o CPU and network n Involves more complicated procedures

Domain 0 o The representative to the Xen hypervisor o Provide bootstrap code for different types of VMs o Creating/deleting virtual network interfaces and virtual block devices for other domains

System looks like

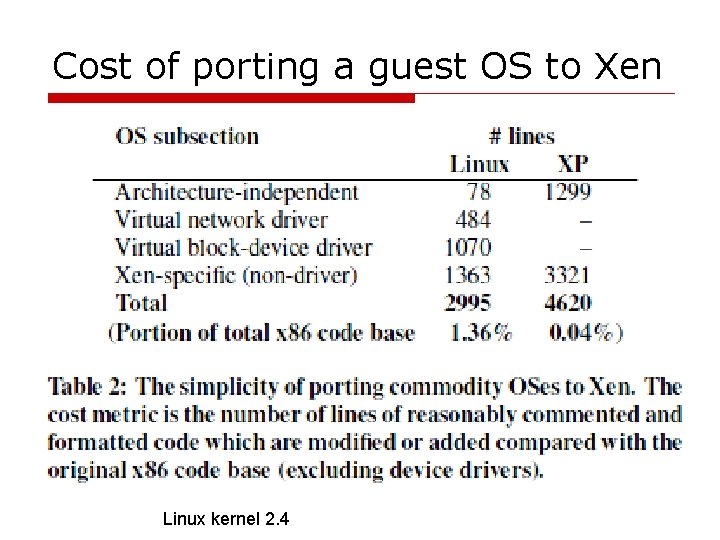
Cost of porting a guest OS to Xen Linux kernel 2. 4

Xen: performance o Hardware (2003) n n n Dell 2650 dual processor 2. 4 GHz Xeon server 2 GB RAM 3 Gb Ethernet NIC 1 Hitachi DK 32 e. J 146 GB 10 k RPM SCSI disk Linux 2. 4. 21 (native)

MMU (memory management) performance

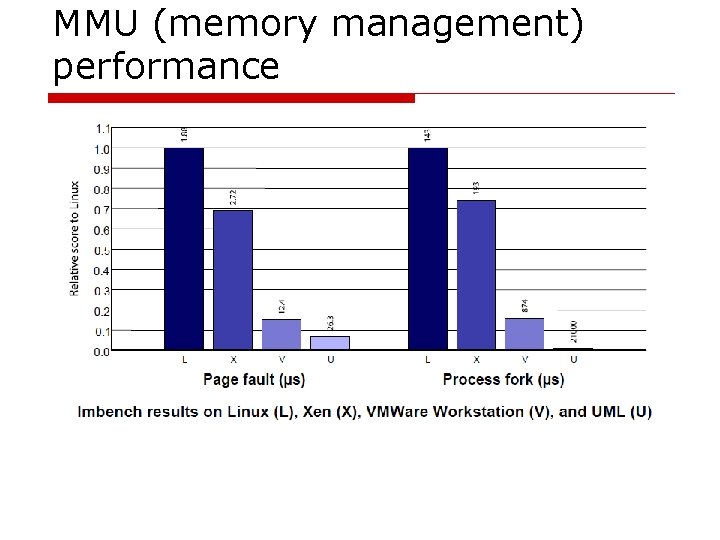
Various benchmarks

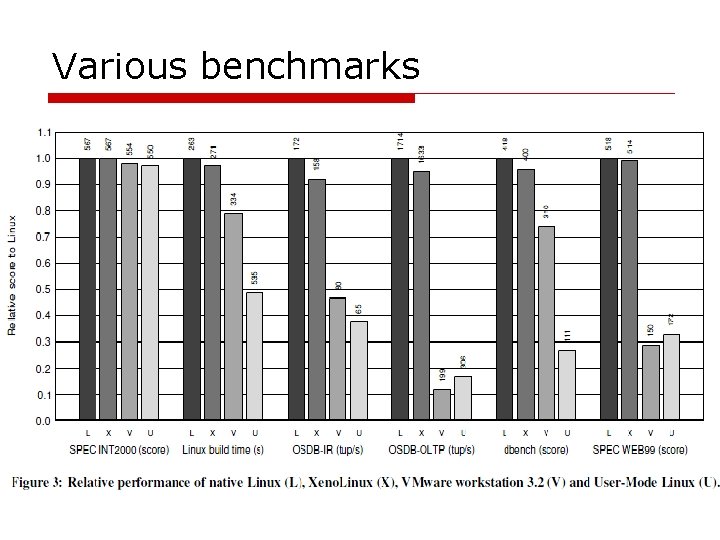
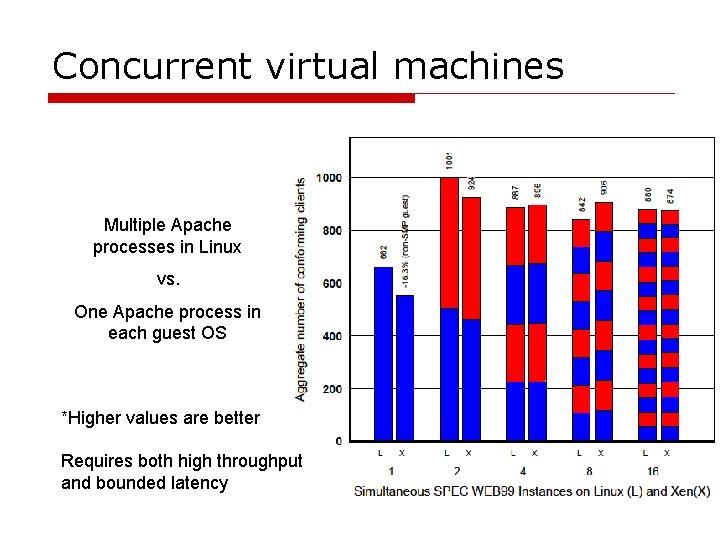
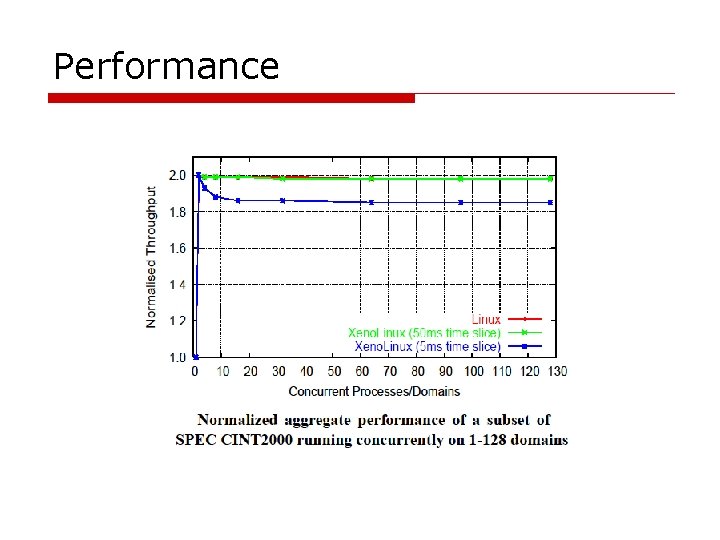
Concurrent virtual machines Multiple Apache processes in Linux vs. One Apache process in each guest OS *Higher values are better Requires both high throughput and bounded latency

Performance

Issues o Performance isolation vs. maximizing overall system utilization n Easy to partition memory and disk n Not easy to partition CPU and network o Time issue

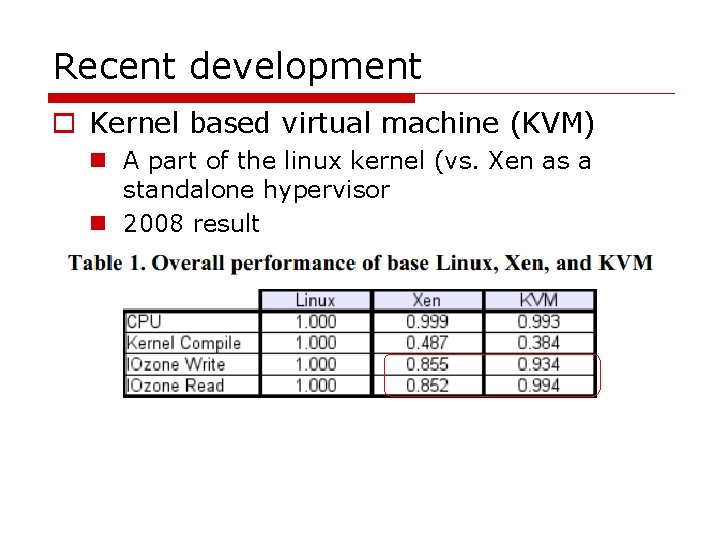
Recent development o Kernel based virtual machine (KVM) n A part of the linux kernel (vs. Xen as a standalone hypervisor n 2008 result

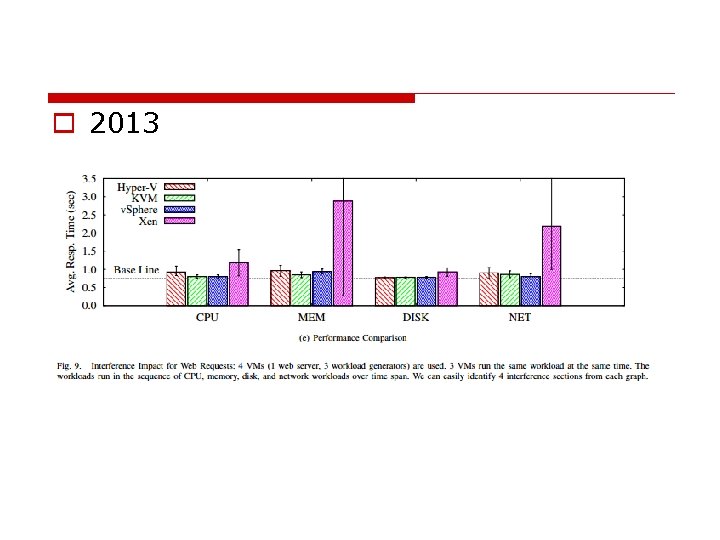
o 2013

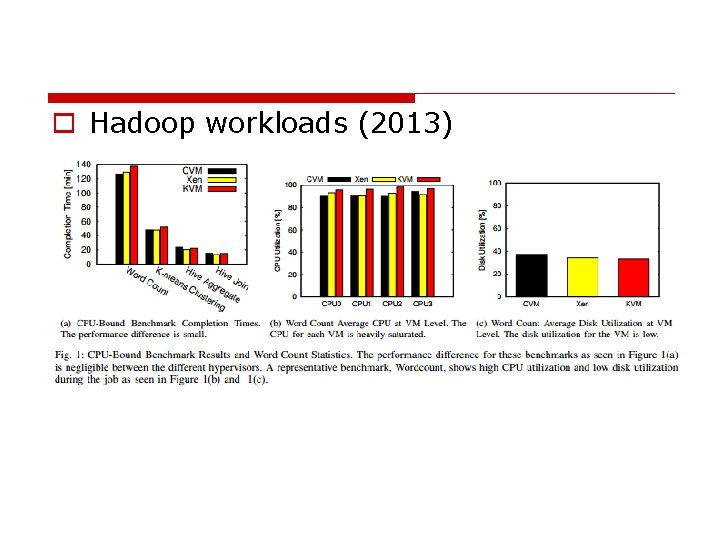
o Hadoop workloads (2013)

Conclusion o o Xen is a complete and robust GPL VMM Outstanding performance and scalability Excellent resource control and protection Linux 2. 6 port required no modifications to core code*