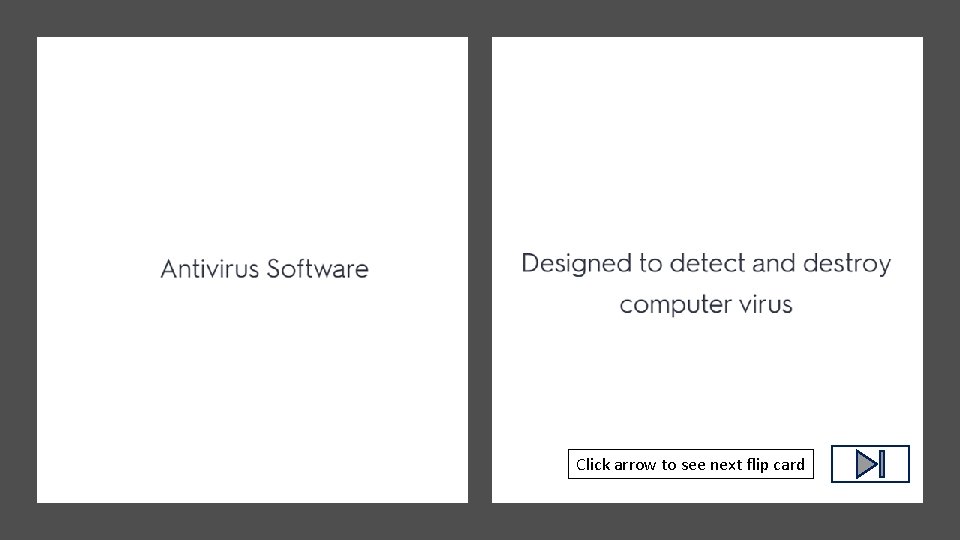
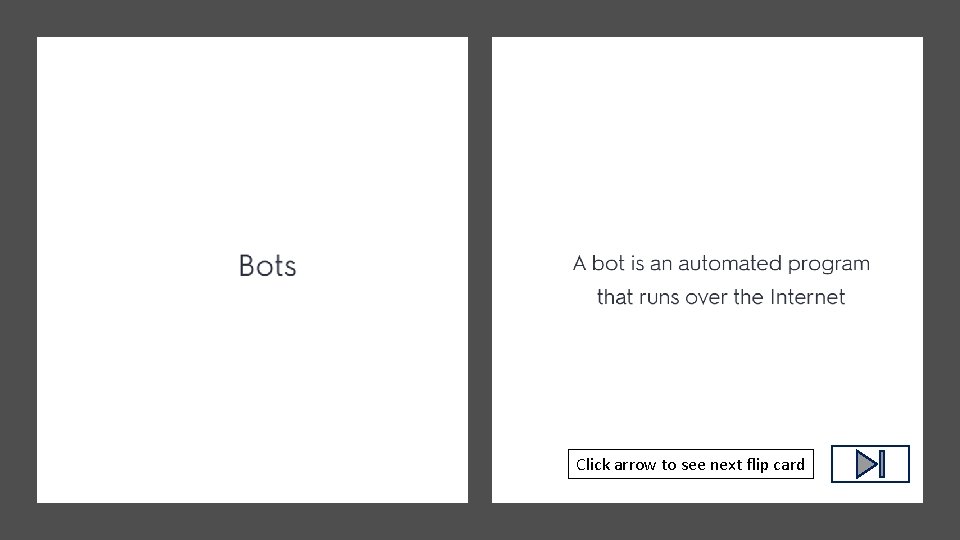
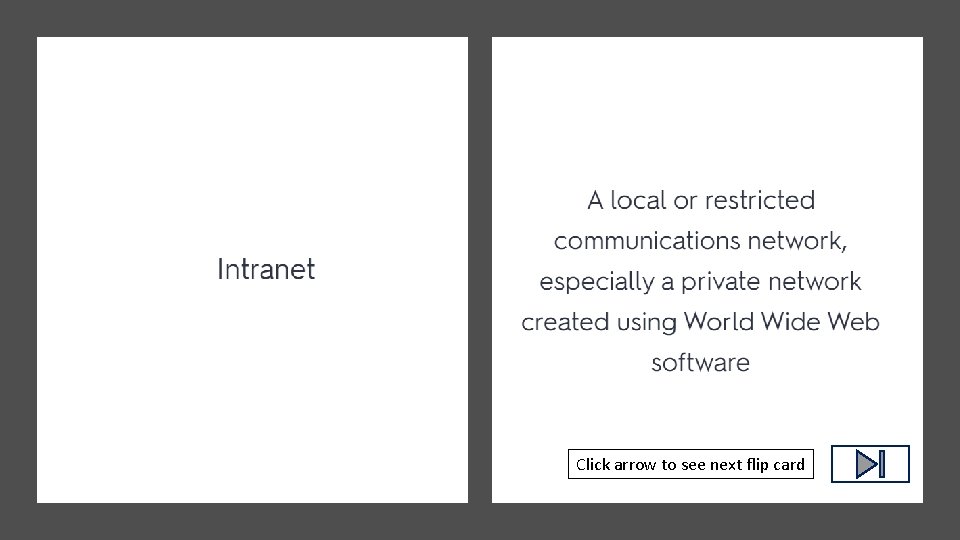
Click arrow to see definition Click arrow to


























- Slides: 48

Click arrow to see definition

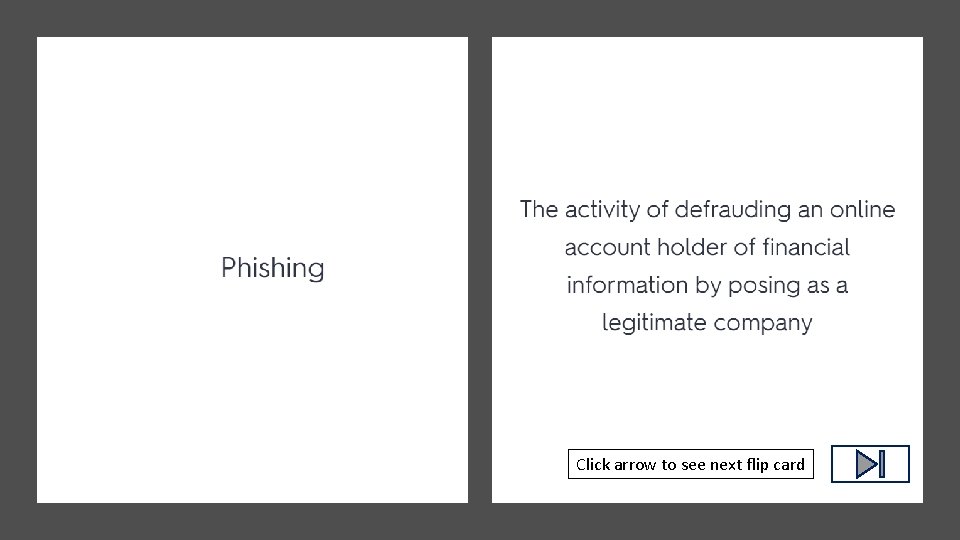
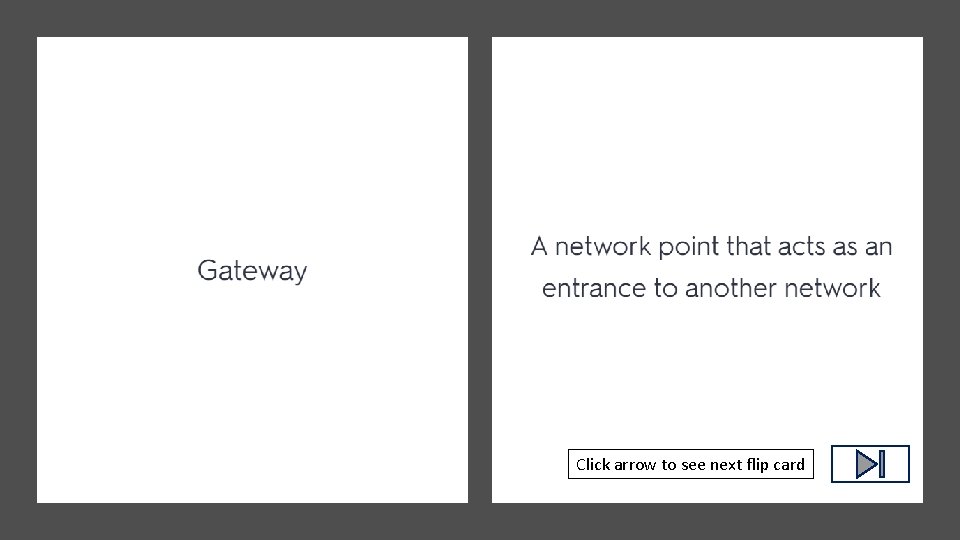
Click arrow to see next flip card

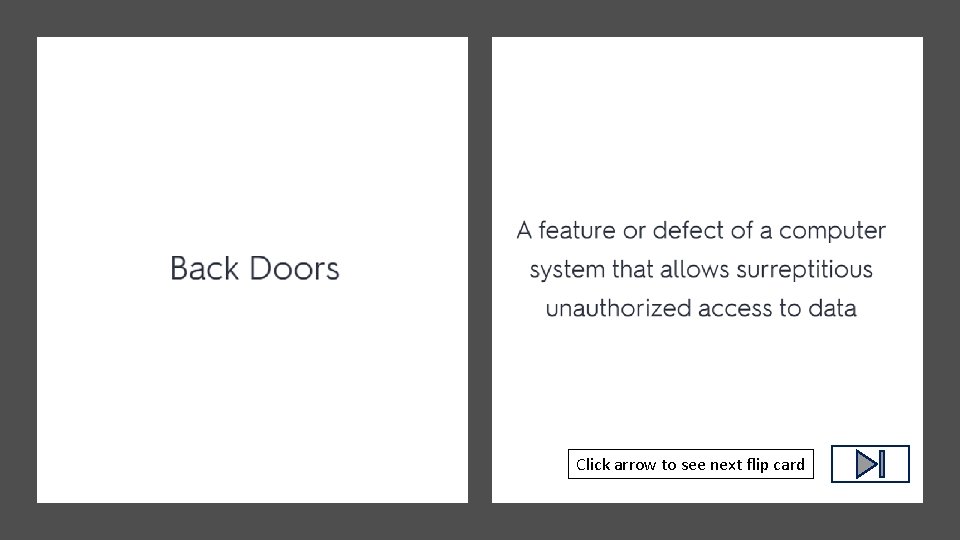
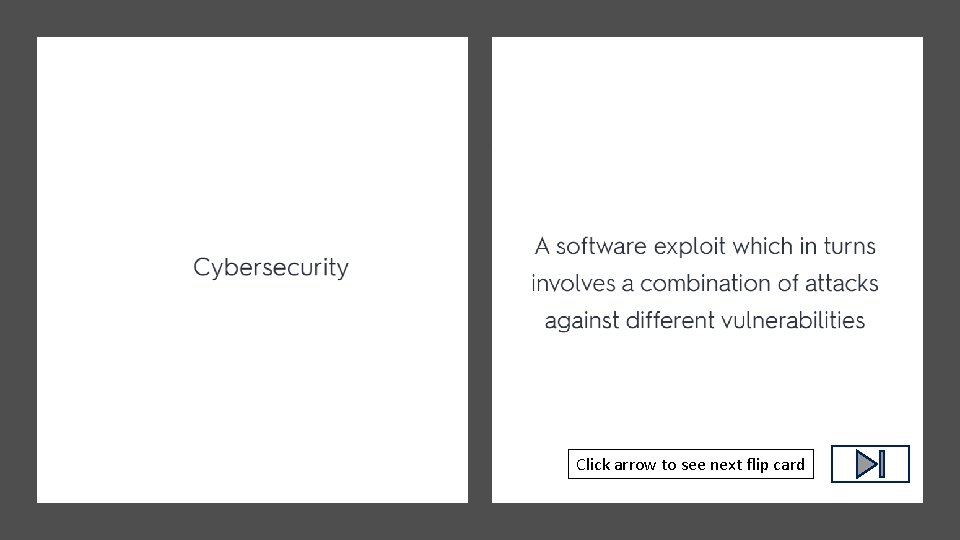
Click arrow to see definition

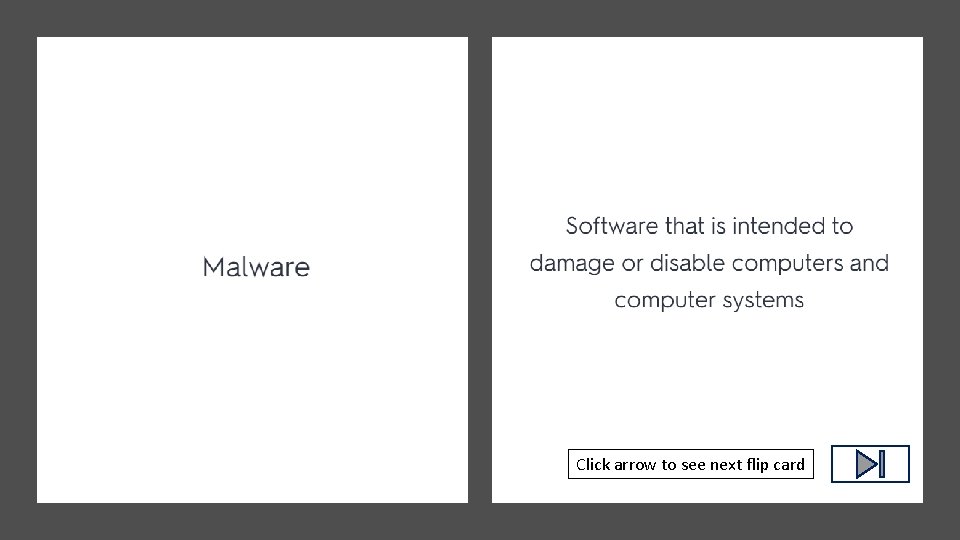
Click arrow to see next flip card

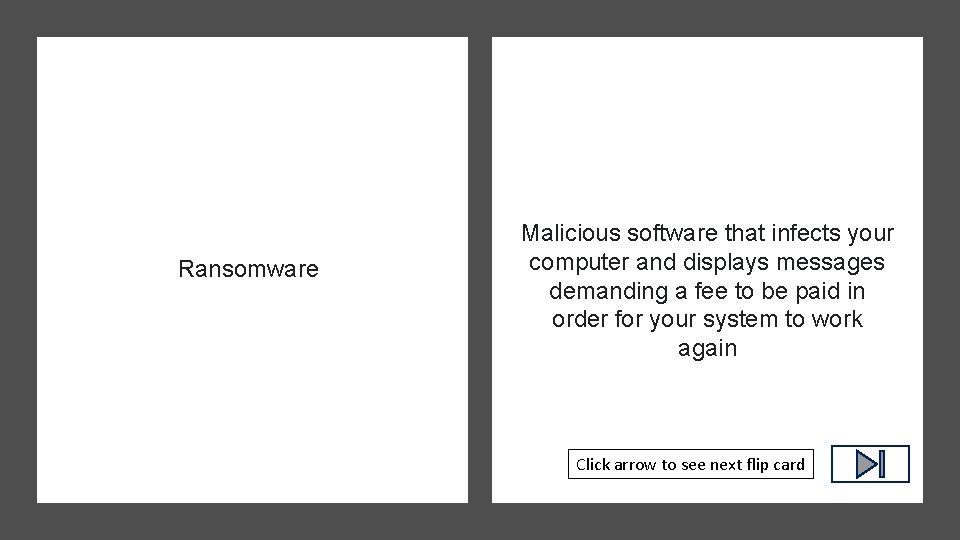
Ransomware Click arrow to see definition

Ransomware Malicious software that infects your computer and displays messages demanding a fee to be paid in order for your system to work again Click arrow to see next flip card

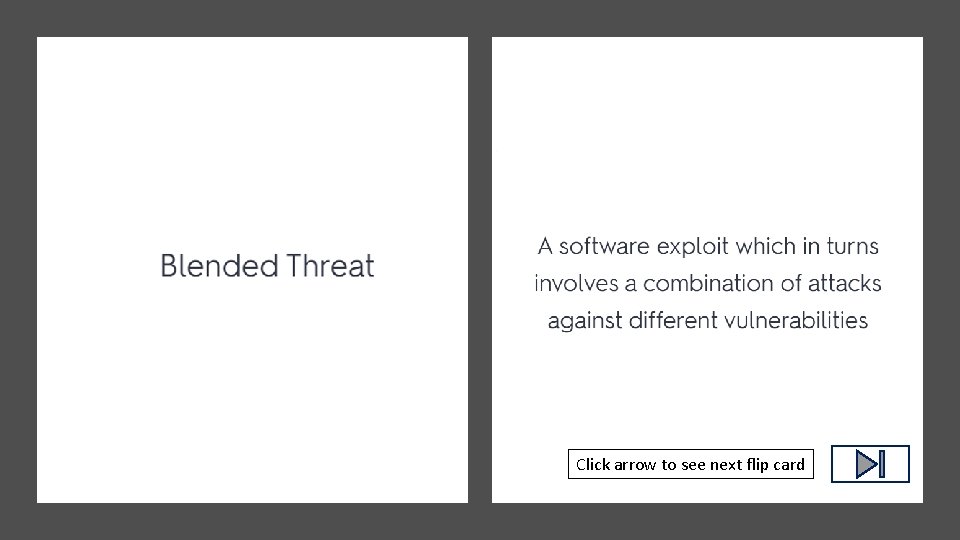
Click arrow to see definition

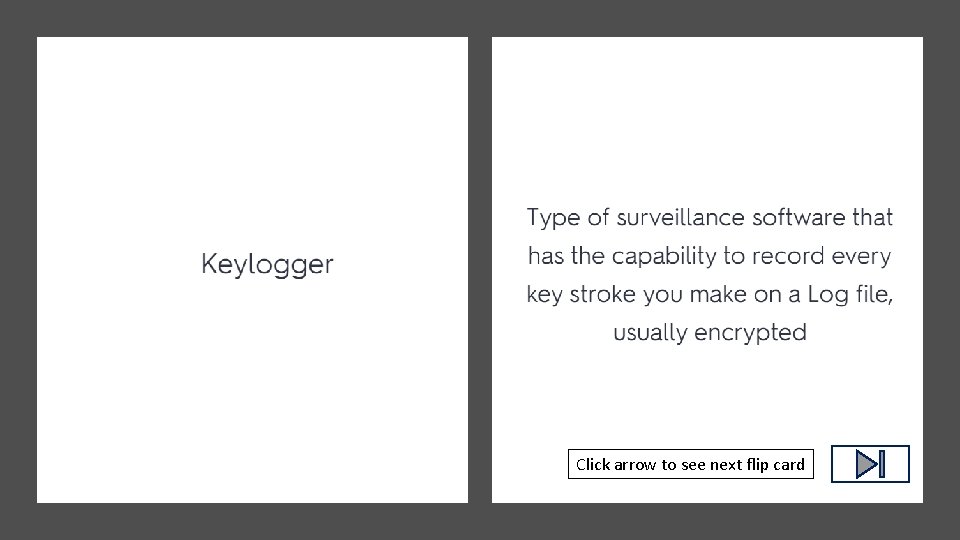
Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

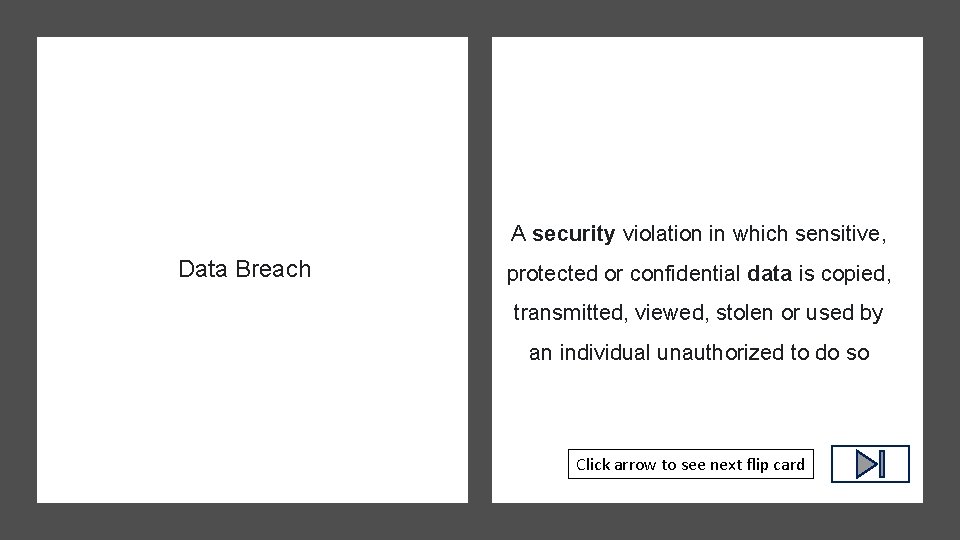
Data Breach Click arrow to see definition

A security violation in which sensitive, Data Breach protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized to do so Click arrow to see next flip card

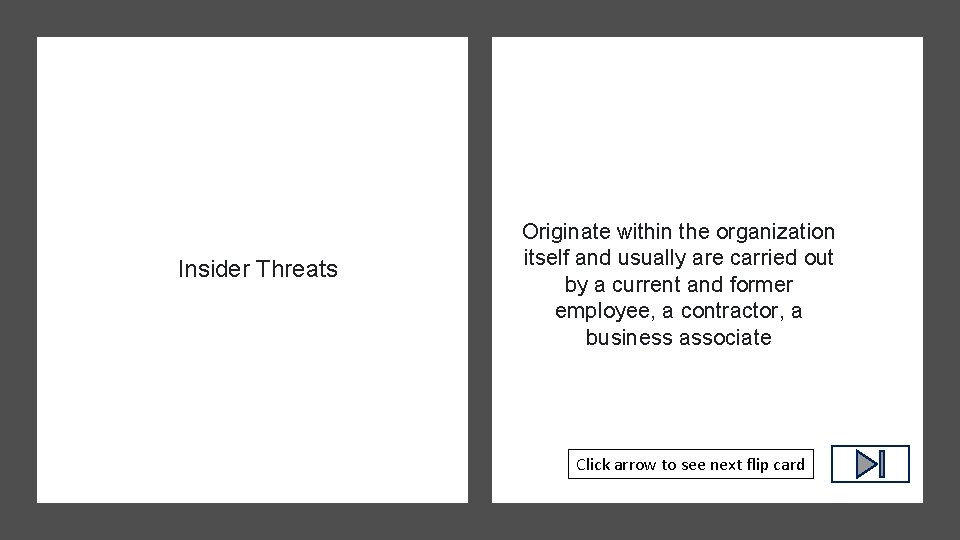
Insider Threats Click arrow to see definition

Insider Threats Originate within the organization itself and usually are carried out by a current and former employee, a contractor, a business associate Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

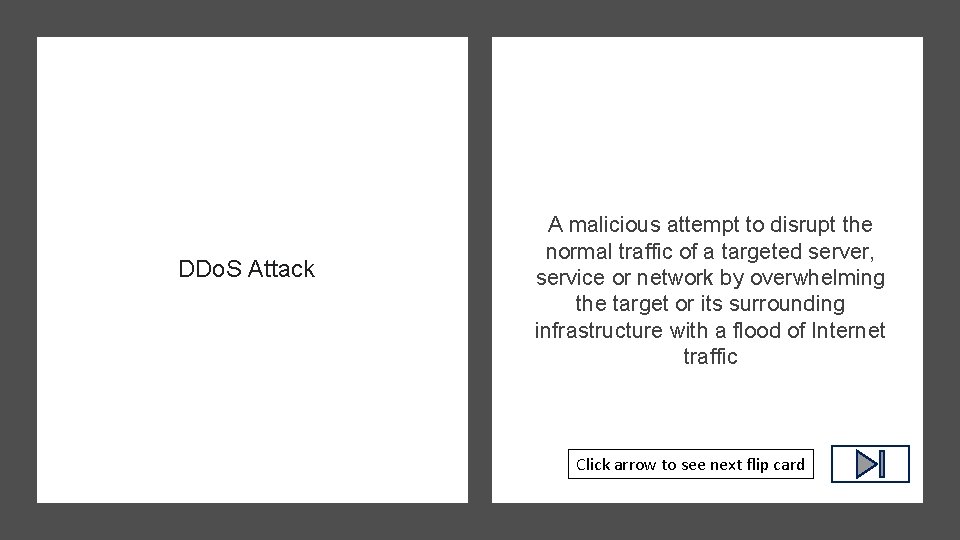
DDo. S Attack Click arrow to see definition

DDo. S Attack A malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Business Email Compromise Click arrow to see definition

Business Email Compromise A type of email cyber crime scam in which an attacker targets businesses to defraud the company Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

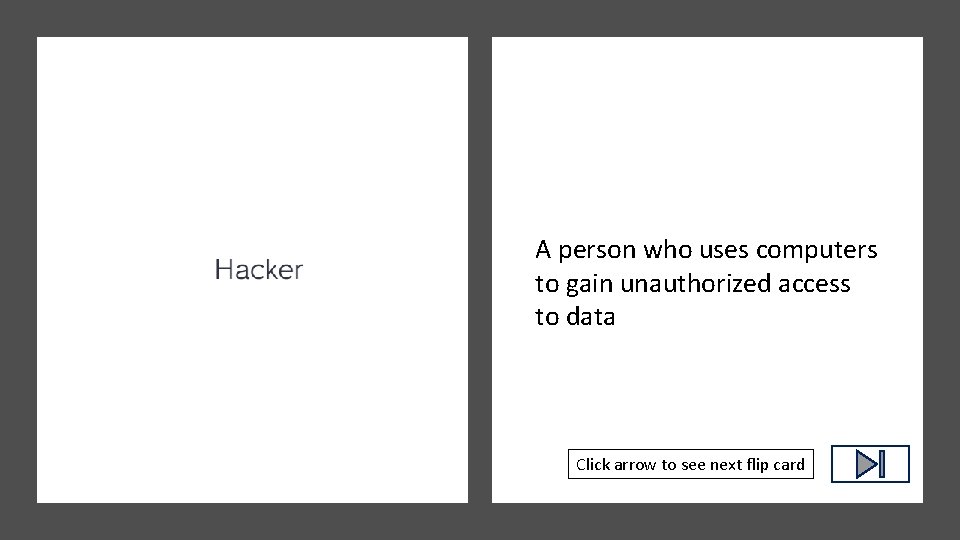
Click arrow to see definition

A person who uses computers to gain unauthorized access to data Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card

Click arrow to see definition

Click arrow to see next flip card