CJIS Security Policy Version 5 4 10062015 Stephen

















- Slides: 20

CJIS Security Policy Version 5. 4, 10/06/2015 Stephen “Doc” Petty, CISSP, SSCP CJIS Technical Auditor Texas Dept of Public Safety

Policy Changes

What’s New in 5. 4 � 2. 3 Risk Based Compliance Approach � 5. 5. 6 Remote Access (Virtual Escorting) � 5. 6. 2. 2 Advanced Authentication (Clarify Certificates) � 5. 10. 1. 2 Encryption Exception � 5. 10. 3. 2 Virtualization and Partitioning (Clarification) Whats Ahead? �Explore upcoming topics of APB discussion Q&A �Open discussion for questions and concerns

Risk Based Compliance

2. 3 Risk Based Compliance �Under CJIS Security Policy Approach, Begin a more risk based approach to compliance measures. �Section 2. 3 Risk versus Realism �Executive Summary integrating Risk-Based Compliance and Requirements Tiering into the Policy.

Virtual Escorting

5. 5. 6 Remote Access �Section 5. 5. 6 Remote Access �Virtual Escorting – compelling operational needs �Process must be documented within security plan �Must meet 5 requirements as outlined within policy.

AA Certificates

5. 6. 2. 2 Advanced Authentication • Clarifying the Types of Certificates: 1. Must be specific to an individual user and not to a particular device. 2. Prohibit multiple users from utilizing the same certificate. 3. Require the user to “activate” that certificate for each use in some manner (e. g. , passphrase or user-specific PIN).

Encryption Exception

5. 10. 1. 2 Encryption Exception Encryption shall not be required if the transmission medium meets all the following requirements: � The agency owns, operates, manages, or protects the medium. � Medium terminates within physically secure locations at both ends with no interconnections between. � Physical access to the medium is controlled by the agency using the requirements in Section 5. 9. 1 and 5. 12 � Protection includes safeguards (e. g. , acoustic, electromagnetic, and physical) and if feasible countermeasures (e. g. , alarms, notifications ) to permit its use for the transmission of unencrypted information through an area of lesser classification or control. � With prior approval of the CSO. (Alan Ferretti has been assigned).

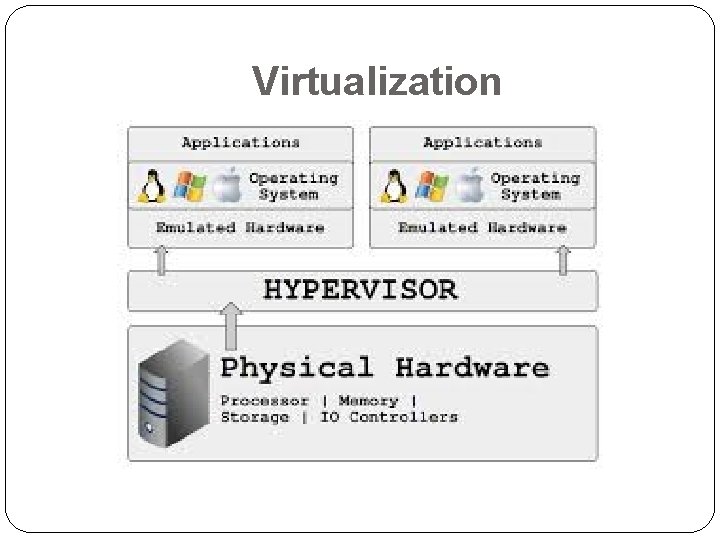
Virtualization

5. 10. 3. 2 Virtualization and Partitioning (Clarification) �Clarification of Virtualization and Partitioning in the CJIS Security Policy. �Isolate host from virtual machine �Maintain audit logs �Physically separate from virtual machines( if internet facing). �Critical Drivers should be specific to the virtual machine. No sharing - secured as independently as possible.

For Future Consideration…

Faxing Requirements

Section 5. 13 Mobile Devices

Mobile Device Management

LEO Website (LEEP)

Contacts Alan Ferretti (512) 424 -7186 alan. ferretti@dps. texas. gov Stephen “Doc” Petty (512) 424 -7055 stephen. petty@dps. tex as. gov

Questions?