Citrix Overview Citrix Presentation Server 4 5 New



- Slides: 20

Citrix Overview

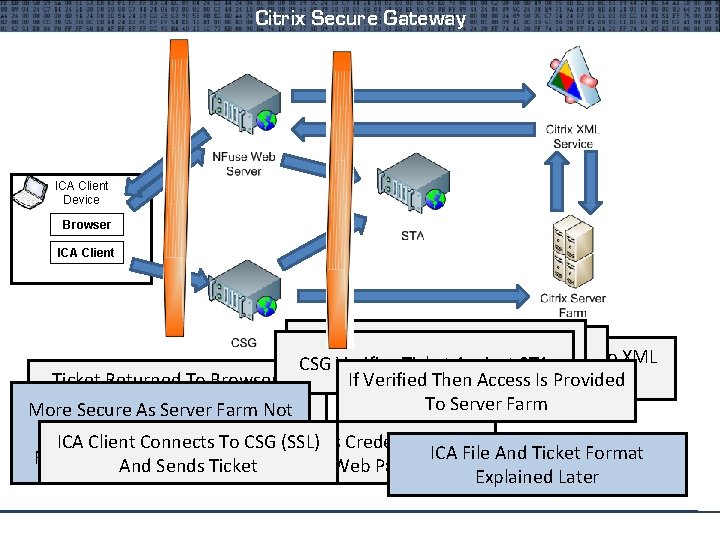
Citrix Presentation Server 4. 5 New version is called Xen. App/Server Common Deployments Nfuse classic CSG – Citrix Secure Gateway Citrix Components Server farm Citrix XML service ICA client device Nfuse Web server CSG – Citrix Secure Gateway STA – Secure Ticketing Authority

NFuse Classic Different Interfaces Browser accessible http: //server/Citrix/Access. Platform/auth/login. aspx Program neighbourhood http: //server/Citrix/PNAgent/config. xml Gateway for Citrix Conferencing Manager http: //server/Citrix/cmguest

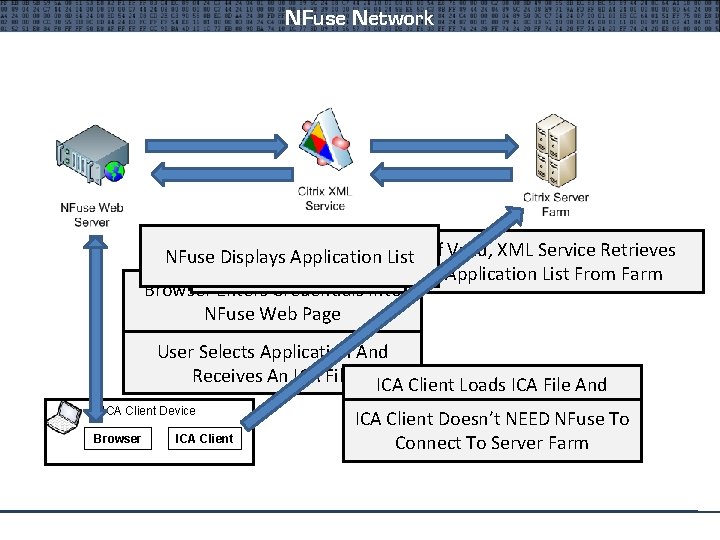
NFuse Network Sends Credentials Valid, XML Service Retrieves NFuse Displays Application List. To. If. XML Service To Validate Application List From Farm Browser Enters Credentials Into NFuse Web Page User Selects Application And Receives An ICA File ICA Client Loads ICA File And ICA Client Device Browser ICA Client Connects To Citrix ICA Client Doesn’t NEEDFarm NFuse To Connect To Server Farm

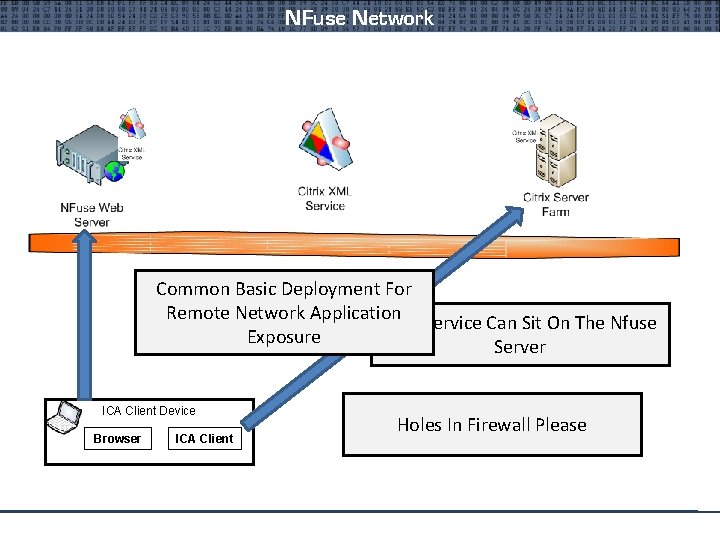
NFuse Network Common Basic Deployment For Remote Network Application XMLService XML Service Can. Sit Can On On. Sit One The On. Of Nfuse The Exposure Independent App Servers Web Server ICA Client Device Browser ICA Client Holes In Firewall Please

Citrix Secure Gateway ICA Client Device Browser ICA Client User Selects Application And If Valid, XML Service Retrieves NFuse Sends Credentials CSG Verifies Ticket Against STA NFuse Requests Ticket From STA To XML Application List From Farm Ticket Returned To Browser As If Verified Then Access Provided Service To Is Validate Part ICA File To Server Farm More Secure As. Of Server Farm Not Exposed. ICA Client Connects Browser To CSG (SSL) Enters Credentials Into ICA File And Ticket Format Firewalls In. And Between Sends Segments Ticket NFuse Web Page Explained Later

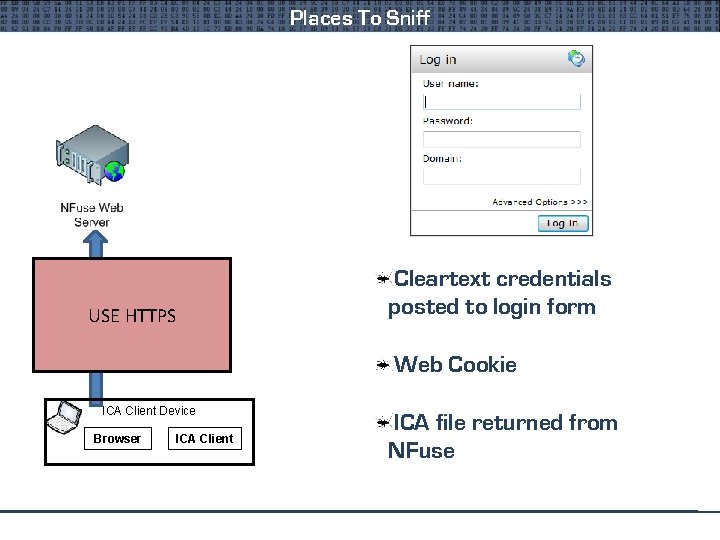
Places To Sniff HTTP Traffic Between Browser USE HTTPS And Nfuse Cleartext credentials posted to login form Web Cookie ICA Client Device Browser ICA Client ICA file returned from NFuse

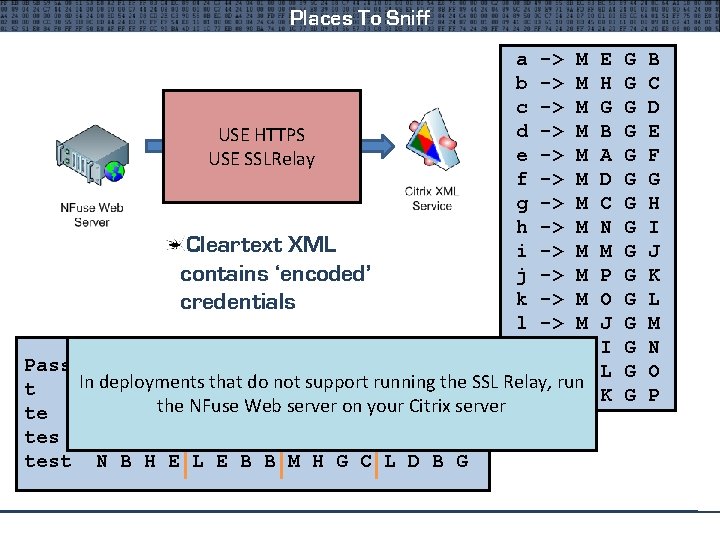
Places To Sniff a -> M b -> M c -> M HTTP Traffic d -> M USE HTTPS Between NFuse And e -> M USE XMLSSLRelay Service f -> M g -> M h -> M Cleartext XML i -> M contains ‘encoded’ j -> M k -> M credentials l -> M m -> M Password n -> M In deployments that do not support running the SSL Relay, run t N B H E o -> M te N B H the E NFuse L E BWeb B server on your Citrix server test N B H E L E B B M H G C L D B G E H G B A D C N M P O J I L K G G G G B C D E F G H I J K L M N O P

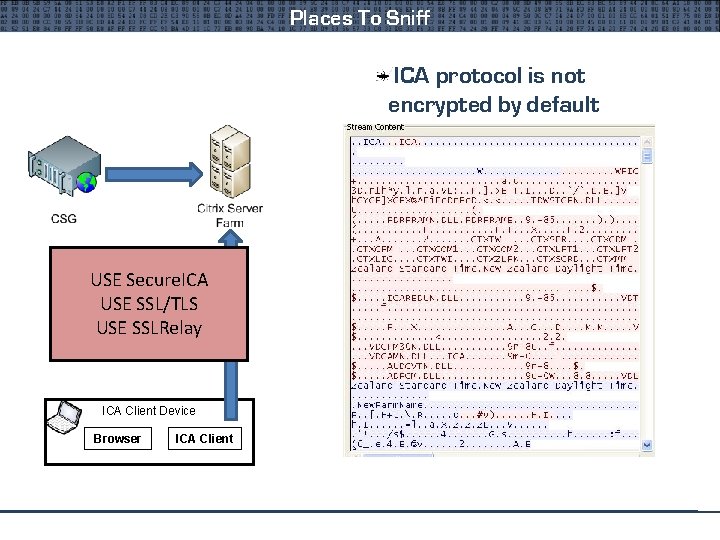
Places To Sniff ICA protocol is not encrypted by default USETraffic Secure. ICA From USE SSL/TLS Client Or CSG USE SSLRelay ICA Client Device Browser ICA Client

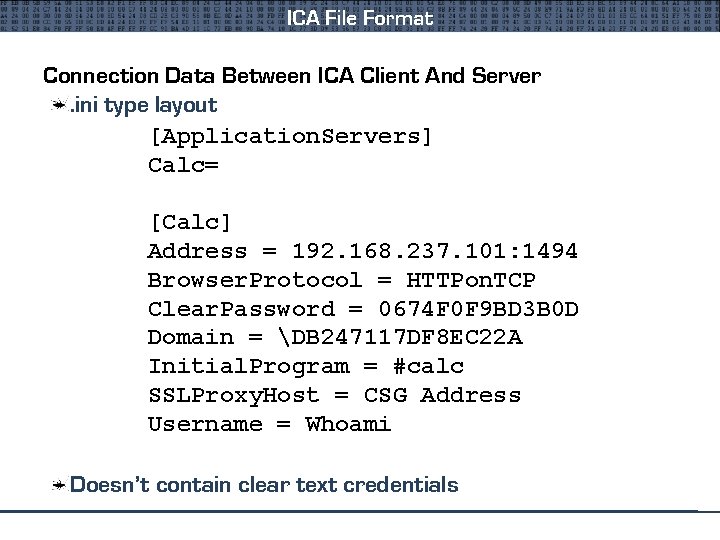
ICA File Format Connection Data Between ICA Client And Server. ini type layout [Application. Servers] Calc= [Calc] Address = 192. 168. 237. 101: 1494 Browser. Protocol = HTTPon. TCP Clear. Password = 0674 F 0 F 9 BD 3 B 0 D Domain = DB 247117 DF 8 EC 22 A Initial. Program = #calc SSLProxy. Host = CSG Address Username = Whoami Doesn’t contain clear text credentials

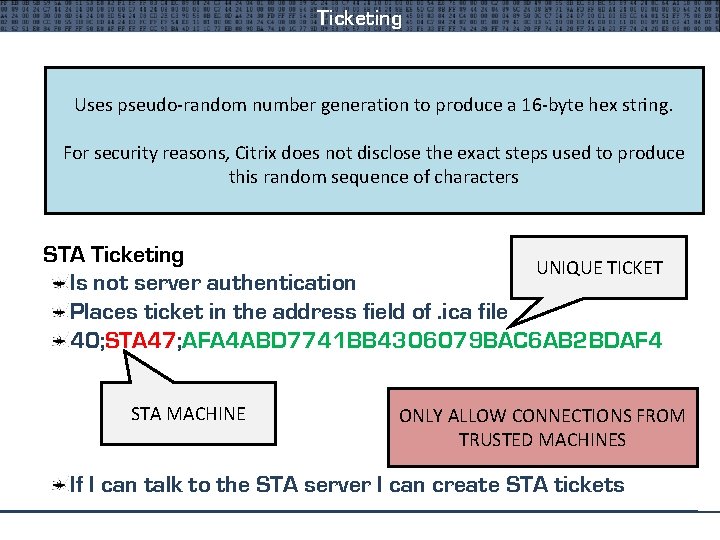
Ticketing Nfuse Ticket Uses pseudo-random generation Apparently it has number an expiry time to produce a 16 -byte hex string. XOR credentials and send to XML server For security reasons, Citrix does not disclose the exact steps used to produce Get Ticket in response this random sequence of characters Split ticket prepend and place into domain: password STA Ticketing UNIQUE TICKET Is not server authentication Places ticket in the address field of. ica file 40; STA 47; AFA 4 ABD 7741 BB 4306079 BAC 6 AB 2 BDAF 4 STA MACHINE ONLY ALLOW CONNECTIONS FROM TRUSTED MACHINES If I can talk to the STA server I can create STA tickets

Shadowing Allows Snooping On Other Sessions On by default Prompts user

Authentication NFuse Web Application Controls access to the Web Application

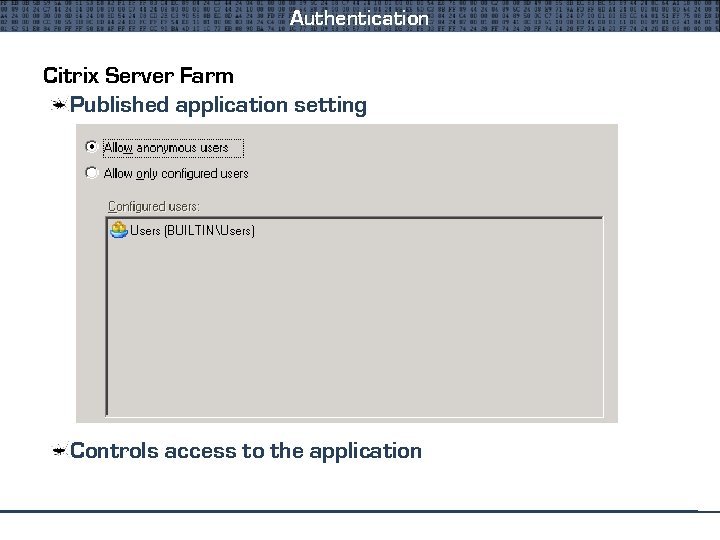
Authentication Citrix Server Farm Published application setting Controls access to the application

Anonymous Accounts Anon 001 – Anon 014 Created upon install Password set on each use Anonymous Access Easy to use Used for ‘temporary’ application use

Citrix XML Service Installed By Default On Port 80 ISAPI extension under IIS Can be set for different port Sensitive Operations Require Auth Unless turned off for smartcard passthru Used by Nfuse and PNAgent Validate Credentials STA Requests Server Enumeration

Gaining Access Brute Force Web Page Brute force the NFuse login page Brute Force ICA File Will attempt to connect to Citrix application server Active. X and API makes this easy Ask The IMA Service Sits on UDP port 1604 Unauthenticated requests will respond with application list Ask The XML Service By default sits on TCP port 80 If you ask politely it tell you

Demonstration Gaining Access Anonymous vs Standard Internal User Breaking The Citrix Sandbox Weak security settings Uploading Tools Alternative file transfer methods Privilege Escalation Third party or windows vulnerability Token Theft Full domain control

Recap No Citrix Vulnerability Exploited Weak / default configuration Anonymous Application Access Was only part of the issue Pretty Common Scenario Most citrix reviews involve gaining ‘shell’ access

Securing Lockdown Citrix Disable file sharing Enabled ‘run only published applications’ Turn on encryption and use SSL Lockdown OS Use group policy to enforce restrictions Disable the runas service Lockdown File System Restrict users access to directories and commands Understand The Weaknesses Hopefully this demonstration has helped