CIT 380 Securing Computer Systems Voting Security CIT






















- Slides: 29

CIT 380: Securing Computer Systems Voting Security CIT 380: Securing Computer Systems 1

Topics 1. 2. 3. 4. 5. Do we have a right to vote? Voting methods Voting fraud techniques History of voting Electronic voting CIT 380: Securing Computer Systems 2

Voting Rights Do we have a right to vote? CIT 380: Securing Computer Systems 3

Voting Rights • Non-discrimination is protected – 15 th (race) – 19 th (sex) – 26 th (age) • But the SCOTUS majority concluded: "the individual citizen has no federal constitutional right to vote for electors for the President of the United States. " (Bush v. Gore, 531 U. S. 98, 104 (2000)) CIT 380: Securing Computer Systems 4

Binary Voting Methods Plurality – First-past-the-post, largest number wins. Approval – Vote for multiple candidates; largest number wins. Runoff – Multiple rounds of plurality until majority winner. – Typical: select top 2, then hold election with just those 2. Random – People vote for their candidate. – Randomly selected ballot determines winner. CIT 380: Securing Computer Systems 5

Preferential Voting Methods Voters rank candidates in order of preference. CIT 380: Securing Computer Systems 6

Preferential Voting Methods Instant Runoff – Exclude non-top candidates, redistribute their votes to top candidates based on voter preferences on ballot. – Used in Australia, Ireland, London. Condorcet – – Rank the candidates in preference order (ties allowed. ) Comparing all candidates pairwise, recording wins. Sum these wins for all ballots cast. Candidate with largest number of wins is elected. CIT 380: Securing Computer Systems 7

Voting Criteria Majority criterion — If there exists a majority preferring a single candidate, does he always win if that majority votes sincerely? Monotonicity criterion — Is it impossible to cause a winning candidate to lose by ranking him higher, or to cause a losing candidate to win by ranking him lower? Consistency criterion — If the electorate is divided in two and a choice wins in both parts, does it always win overall? Participation criterion — Is it always better to vote honestly than to not vote? Condorcet criterion — If a candidate beats every other candidate in pairwise comparison, does that candidate always win? Arrow’s Impossibility Theorem CIT 380: Securing Computer Systems 8

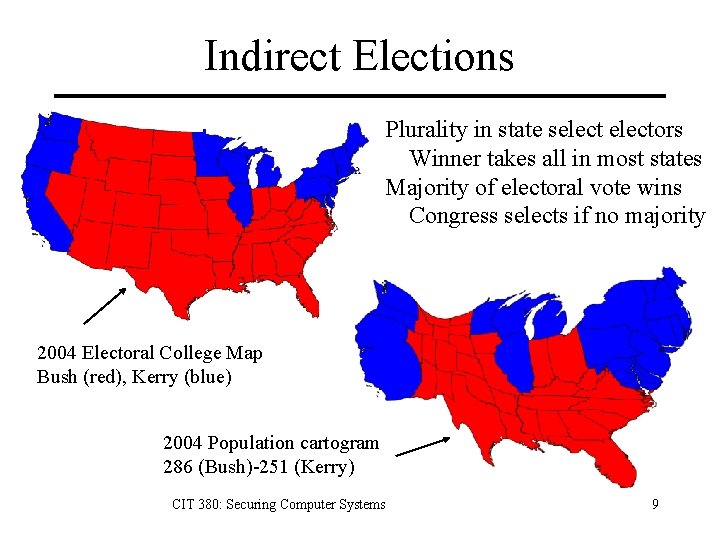
Indirect Elections Plurality in state selectors Winner takes all in most states Majority of electoral vote wins Congress selects if no majority 2004 Electoral College Map Bush (red), Kerry (blue) 2004 Population cartogram 286 (Bush)-251 (Kerry) CIT 380: Securing Computer Systems 9

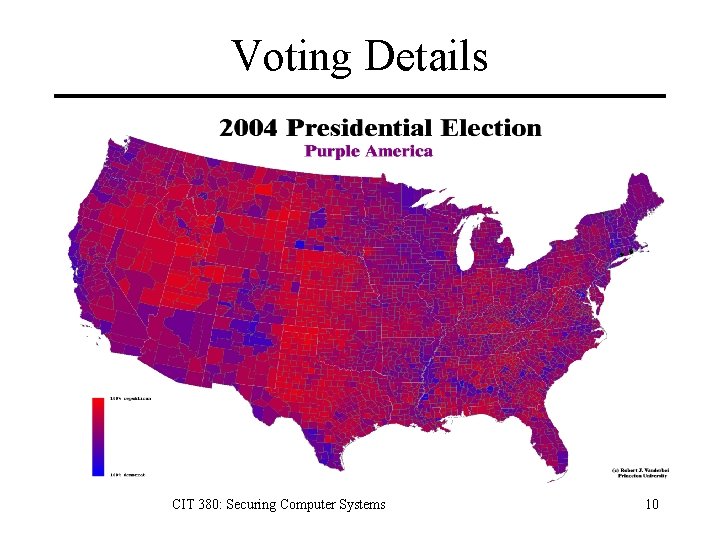
Voting Details CIT 380: Securing Computer Systems 10

Voting Fraud • Altering voter lists – Register false voters. – Remove voters of groups unlikely to support you. • Voter coercion and social engineering – Intimidate voters from going to polling place. – Threaten to fire employees. • Physical tampering – Ballot stuffing – Destruction of ballot boxes CIT 380: Securing Computer Systems 11

Voting Fraud • Social Engineering – “Helping” blind or elderly people vote. – Voting in multiple precincts. – Impersonating another voter. – Selling votes. • Control the counting of votes – Spoiling votes (making extra marks) – Subverting election officials. – Alter software that tallies votes. CIT 380: Securing Computer Systems 12

Legal Voting Fraud • Gerrymandering – Structure districts to control votes. – Maximize wasted votes for opposition. • Excessive security – Require expensive ID. • Unreasonable deadlines – Prevent military ballots. • Limiting candidates – DC’s “Jesse Jackson” law. – Third party candidate rules. CIT 380: Securing Computer Systems 13

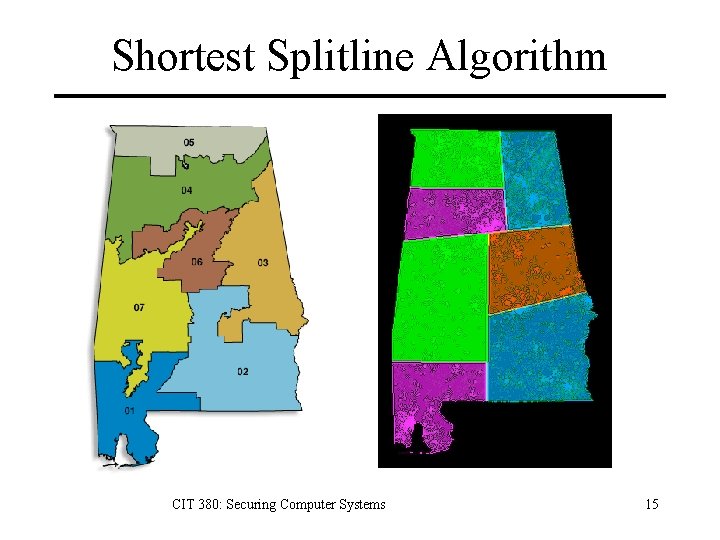
Shortest Splitline Algorithm 1. Start with the boundary outline of the state. 2. Let N=A+B where A and B are as nearly equal whole numbers as possible. (ex: 7=4+3. ) 3. Among all possible dividing lines that split the state into two parts with population ratio A: B, choose the shortest. 4. We now have two hemi-states, each to contain a specified number (namely A and B) of districts. Handle them recursively via the same splitting procedure. CIT 380: Securing Computer Systems 14

Shortest Splitline Algorithm CIT 380: Securing Computer Systems 15

History of Voting Voice Voting – Observers can record votes. – So can others, leading to bribery and coercion. Ballots – Clay or tokens to represent vote from Greeks. – Black balls used for negative, white for positive. Paper Ballots – Used in Rome as early as 139 BCE. – Originally supplied by voters, later by parties. – Difficult to ensure privacy while avoiding fraud. CIT 380: Securing Computer Systems 16

History of Voting Australian Paper Ballot 1858 – Standardized paper ballot provided by govt. – Adopted in US after fraud in 1884. – Problem: how to interpret marks • What type of mark (X, check)? • In-box vs. out of box? • Multiple selections? CIT 380: Securing Computer Systems 17

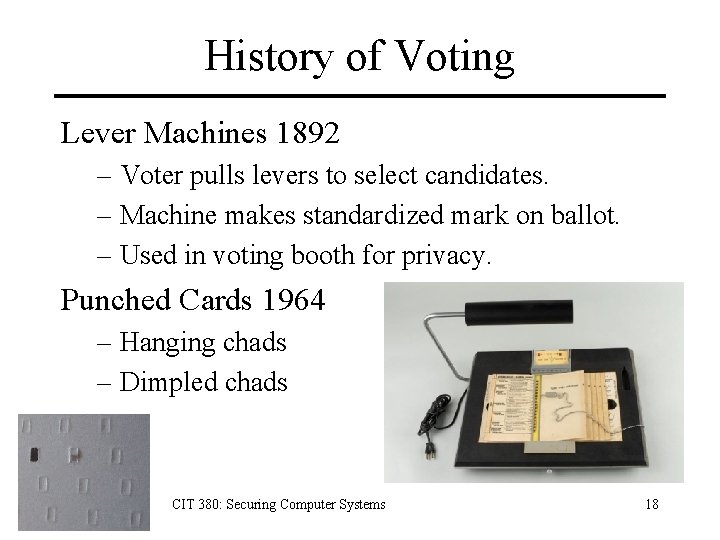
History of Voting Lever Machines 1892 – Voter pulls levers to select candidates. – Machine makes standardized mark on ballot. – Used in voting booth for privacy. Punched Cards 1964 – Hanging chads – Dimpled chads CIT 380: Securing Computer Systems 18

Types of Electronic Voting Optical scan – Voter marks paper ballots, which are counted based on darkness of mark like scan-tron tests. Direct-recording electronic (DRE) – Records vote count electronically. Networked DRE – Uploads vote count electronically. – Includes Internet voting. CIT 380: Securing Computer Systems 19

Advantages of e-voting • Accessibility • Cheaper election costs due to no paper – Multi-lingual ballots • Speed of tabulation • Remote voting CIT 380: Securing Computer Systems 20

Disadvantages of e-voting • • Voters could be tracked Lack of reliability Lack of verification Lack of transparency Undetectable fraud (Rice’s theorem) Wholesale fraud More expensive due to voting machines CIT 380: Securing Computer Systems 21

Are Voting Machines Reliable? Columbus, OH – An error while a Danaher / Guardian ELECTronic 1242 was plugged into a laptop to download results gave President Bush 3, 893 extra votes. : http: //www. usatoday. com/tech/news/techpolicy/evoting/2004 -11 -06 -ohio -evote-trouble_x. htm Carteret Co. , NC – More early voters voted on Unilect Inc. ’s Patriot voting system than the system could handle resulting in the loss of more than 4, 500 votes. : http: //www. usatoday. com/news/politicselections/vote 2004/2004 -11 -04 -voteslost_x. htm Broward Co. , FL – ES&S software on their machines only reads 32, 000 votes at a precinct then it starts counting backwards (see this update): http: //www. news 4 jax. com/politics/3890292/detail. html Mecklenburg Co. , NC – More votes registered than voters: http: //www. charlotte. com/mld/charlotte/news/politics/10094165. htm La. Porte County, IN - A bug in ES&S’ software causes each precinct to be reported as only having (exactly) 300 voters each; all reports add up to 22, 000 voters in a county that has more than 79, 000 registered voters. : http: //www. heraldargus. com/content/story. php? storyid=5304 Utah County, UT - 33, 000 straight-party ballots are not counted due to a programming error in punchcard counting equipment. : http: //deseretnews. com/dn/view/0, 1249, 595105309, 00. html CIT 380: Securing Computer Systems 22

Are Voting Machines Secure? “As long as I count the votes, what are you going to do about it? ” – William Marcy “Boss” Tweed, 1871 CIT 380: Securing Computer Systems 23

Diebold Ballot. Station 1. Setup – D/L ballot setup 2. Pre-Election – L&A testing 3. Election – Voting 4. Post-Election – Print result tape – Transfer votes CIT 380: Securing Computer Systems 24

Attack Scenarios • Transferring Votes – Transfer vote from one candidate to another. – Leaves total number of votes unchanged. • Denial of Service – Target precinct that votes for opponent. – Malware shuts down or wipes machine. – Forged administrative smartcard attack. CIT 380: Securing Computer Systems 25

Injecting Attack Code • Direct installation – Reboot using smartcard with bootloader. – Exploit backdoor to install from smartcard. – Replace EPROM. – Voting machines use standard minibar keys. • Virus – Infects memory cards. – Memory cards infect machines on boot. – Software upgrades delivered via memory cards. CIT 380: Securing Computer Systems 26

Concealing Voting Malware • Timing – Software only active in Election mode. – Software only active on certain dates / times. • Knock – Software actives only after secret “knock” given. • Hiding processes and files – Rootkit techniques – Virtualization CIT 380: Securing Computer Systems 27

Mitigating Attacks • Be like an XBox. • Digital signatures for software updates • Securing audit logs and counters – Specialized hardware – Cryptographic techniques • Chain of custody for memory cards • Voter verifiable paper trail CIT 380: Securing Computer Systems 28

References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. Caltech/MIT Voting Project, “Residual Votes Attributable to Technology, ” http: //www. hss. caltech. edu/~voting/Cal. Tech_MIT_Report_Version 2. pdf#search=%22 mit%20 caltech%20 uncounted%20 ballots%22, 2001. “More e-voting problems, ” http: //www. evoting-experts. com/, December 12, 2004. Ariel J. Feldman, J. Alex Halderman, Edward W. Felten, “Security Analysis of the Diebold Accu. Vote-TS Voting Machine, ” http: //itpolicy. princeton. edu/voting, Sep 13, 2006. Douglas Jones, “Illustrated Voting Machine History, ” http: //www. cs. uiowa. edu/~jones/voting/pictures/, 2003. Tadayoshi Kohno, Adam Stubblefield, Aviel D. Rubin, Dan S. Wallach, “Analysis of an Electronic Voting System, ” IEEE Symposium on Security and Privacy, Oakland, CA, May, 2004 Mark Newman, “Election Result Maps, ” http: //wwwpersonal. umich. edu/~mejn/election/, 2004. Avi Rubin, Brave New Ballot, Morgan Road Books, 2006. Kim Zetter, “House Dems seek Election Inquiry, ” http: //www. wired. com/news/evote/0, 2645, 65623, 00. html, Nov 5, 2004. http: //en. wikipedia. org/wiki/Gerrymandering, 2007. http: //en. wikipedia. org/wiki/Voting_fraud, 2007. http: //en. wikipedia. org/wiki/Voting_system, 2006. CIT 380: Securing Computer Systems 29