CIT 380 Securing Computer Systems Policies CIT 380
















- Slides: 19

CIT 380: Securing Computer Systems Policies CIT 380: Securing Computer Systems 1

Security Planning 1. 2. 3. 4. 5. Planning to address security needs. Risk assessment. Crafting policies to reflect risks and needs. Implementing security. Audit and incident response. CIT 380: Securing Computer Systems 2

Which Aspects are Important: CIA? CIT 380: Securing Computer Systems 3

Risk Assessment 1. What assets are you trying to protect? 2. What are the risks to those assets? 3. How well does each potential security solution mitigate those risks? 4. What other risks does the security solutions impose on me? 5. What costs and trade-offs do the security solutions create? CIT 380: Securing Computer Systems 4

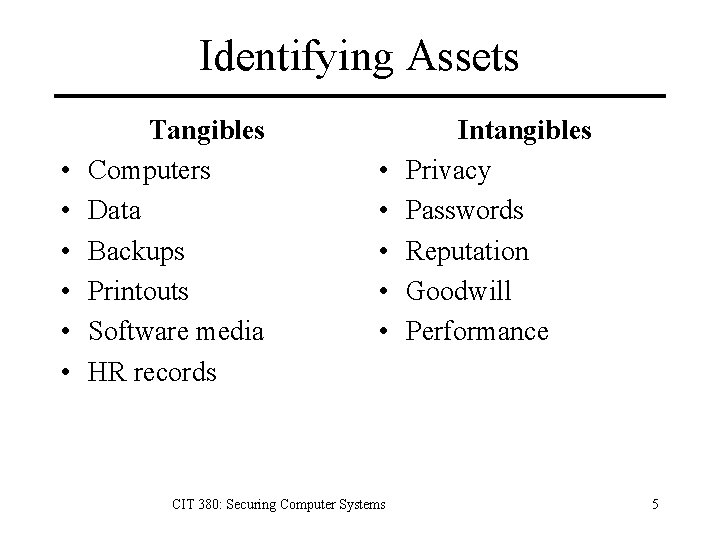
Identifying Assets • • • Tangibles Computers Data Backups Printouts Software media HR records • • • CIT 380: Securing Computer Systems Intangibles Privacy Passwords Reputation Goodwill Performance 5

Identifying Risks • • • Loss of key personnel Loss of key vendor or service provider Loss of power Loss of phone / network Theft of laptops, USB keys, backups Introduction of malware Hardware failure Software bugs Network attacks CIT 380: Securing Computer Systems 6

Risk Analysis Notes Update your risks regularly – Business, technology changes alter risks. Too many risks to defend against. – Rank risks to decide which ones to mitigate. – Insure against some risks. – Accept other risks. CIT 380: Securing Computer Systems 7

Cost-Benefit Analysis Cost of a Loss – – Direct cost of lost hardware. Cost of idle labor during outage. Cost of time to recover. Cost to reputation. Probability of a Loss – Insurance/power companies have some stats. – Records of past experience. Cost of Prevention – Remember that most risks cannot be eliminated. CIT 380: Securing Computer Systems 8

Best Practices • Risk Analysis is difficult and uncertain. • Follow best practices or due care – Firewall require as insurance co. due care. – Update patches, anti-virus. – Organizations differ in what they need. • Combine best practices + risk analysis. CIT 380: Securing Computer Systems 9

Security Policy Security policy partitions system states into: – Authorized (secure) • These are states the system is allowed to enter. – Unauthorized (nonsecure) • If the system enters any of these states, it’s a security violation. Secure system – Starts in authorized state. – Never enters unauthorized state. CIT 380: Securing Computer Systems 10

Role of Policy 1. Identifies what is being protected and why. 2. States responsibility for protection. 3. Provides ground on which to interpret and resolve later conflicts. CIT 380: Securing Computer Systems 11

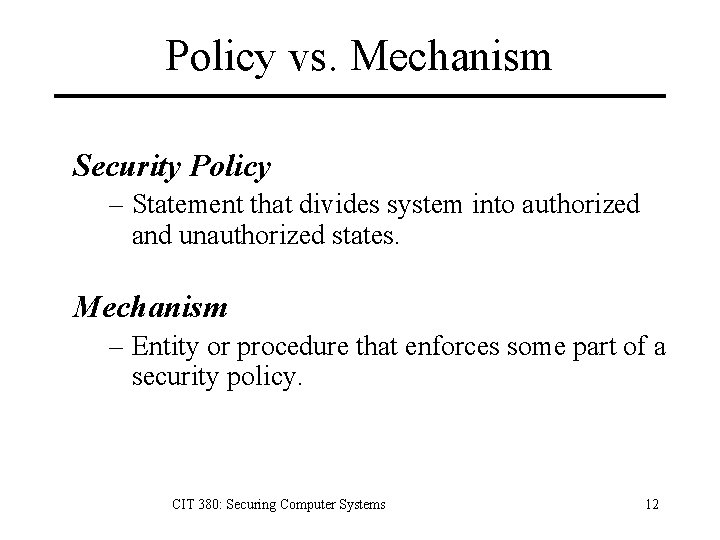
Policy vs. Mechanism Security Policy – Statement that divides system into authorized and unauthorized states. Mechanism – Entity or procedure that enforces some part of a security policy. CIT 380: Securing Computer Systems 12

Dirty Politics Republican Senate staffers gained access to Democrat computer files 2002 -2003. – Both parties share computer server. – 2001 misconfiguration allowed access w/o pw. – Defence: "The bottom line here is that the technology staff of the Democrats was negligent. They put these memos in a shared hard drive. It was like putting the memos on our desk. ” – Manuel Miranda CIT 380: Securing Computer Systems 13

Developing a Policy Assign responsibility – Need to know who is responsible for protecting what, i. e. users for their own accounts. – Authority needs to accompany responsibility. Be positive – People respond better to do than don’t. Consider user needs – Privacy, protecting PII Need to educate users. CIT 380: Securing Computer Systems 14

Security Perimeter • Perimeter defines what is within your control. • Historically – Within walls of building or fences of campus. – Within router that connects to ISP. • Modern perimeters are more complex – Laptops, PDAs. – USB keys, CDs, DVDs, portable HDs. – Wireless networks. – Home PCs that connect to your network. CIT 380: Securing Computer Systems 15

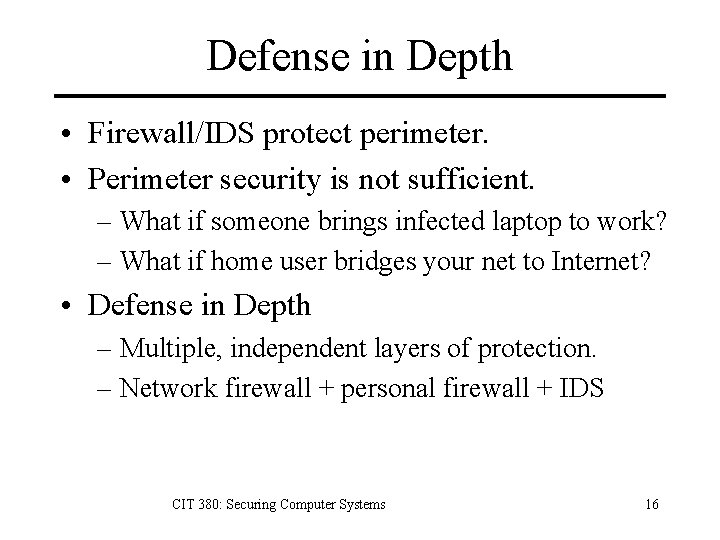
Defense in Depth • Firewall/IDS protect perimeter. • Perimeter security is not sufficient. – What if someone brings infected laptop to work? – What if home user bridges your net to Internet? • Defense in Depth – Multiple, independent layers of protection. – Network firewall + personal firewall + IDS CIT 380: Securing Computer Systems 16

Compliance Audits • Your policy is great, but is it being followed? • Audit your systems and personnel regularly. • Audit failures may result from – Personnel shortcomings • Insufficient education or overwork – Material shortcomings • Insufficient resources or maintenance – Organizational shortcomings • Lack of authority, conflicting responsibilities – Policy shortcomings • Unforseen risks, missing or conflicting policies CIT 380: Securing Computer Systems 17

Key Points • Policy divides system into – Authorized (secure) states. – Unauthorized (insecure) states. • Policy vs Mechanism – Policy: describes what security is. – Mechanism: how security policy is enforced. • Written policy and enforced policy will differ. – Compliance audits look for those differences. • Security Perimeter – Describes what is within your control. – Defense in depth: defend perimeter and inside. CIT 380: Securing Computer Systems 18

References 1. Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. 2. Simson Garfinkel, Gene Spafford, and Alan Schwartz, Practical UNIX and Internet Security, 3/e O’Reilly, 2003. 3. NKU, Acceptable Use Policy, http: //it. nku. edu/pdf/Acceptable. Use. Policyrv 51. pdf, 2002. 4. SANS, SANS Security Policy Project, http: //www. sans. org/resources/policies/ CIT 380: Securing Computer Systems 19