CISSP Overview CISSP Overview 1 Introduction 2 CISSP


![1. Introduction CISSP Overview 1. 2 Why choose certification? Information security [IS] professionals invest 1. Introduction CISSP Overview 1. 2 Why choose certification? Information security [IS] professionals invest](https://slidetodoc.com/presentation_image_h2/09f783c75e966afd07c6e312aec45784/image-4.jpg)
























- Slides: 55

CISSP Overview

CISSP Overview 목 차 1. Introduction 2. CISSP의 의미와 시험준비방법 3. CBK 소개

1. Introduction CISSP Overview 1. 1 ISC 2 ? (ISC)2 = International Information Systems Security Certifications Consortium, Inc. (ISC)2 is a global, not-for-profit organization dedicated to: • Maintaining a Common Body of Knowledge for Information Security [IS]. • Certifying industry professionals and practitioners in an international IS standard • Administering training and certification examinations. • Ensuring credentials are maintained, primarily through continuing education. Governments, corporations, centers of higher learning and organizations worldwide demand a common platform for and proficiency in mastering the dynamic nature of information security. (ISC)2 helps fulfill these needs. Thousands of IS professionals in over 35 countries worldwide have attained certification in one of the two designations administered by (ISC) 2: • Certified Information Systems Security Professional [CISSP] • System Security Certified Practitioner [SSCP] Both credentials indicate those certified have demonstrated experience in the field of information security, passed a rigorous examination, subscribe to a Code of Ethics and maintain certification with continuing education.
![1 Introduction CISSP Overview 1 2 Why choose certification Information security IS professionals invest 1. Introduction CISSP Overview 1. 2 Why choose certification? Information security [IS] professionals invest](https://slidetodoc.com/presentation_image_h2/09f783c75e966afd07c6e312aec45784/image-4.jpg)
1. Introduction CISSP Overview 1. 2 Why choose certification? Information security [IS] professionals invest substantially in information assets, including technology, architecture and process. But how can protection of these assets be ensured? Only through the strengths of the professionals in charge. Industry standards, ethics and certification of IS professionals and practitioners becomes critical to ensuring a higher standard for security is achieved. (ISC) 2, as the only not-for-profit consortium charged with maintaining, administering and certifying IS professionals in the Common Body of Knowledge [CBK], is the premier resource for IS professionals worldwide. Benefits of (ISC)2 Certification to the Enterprise – Establishes best practices – Provides a solutions-orientation, not specialization, particularly with the broader understanding of the IS CBK – Access to a network of global industry and subject matter/domain experts – Resource for broad-based security information – Adds to credibility with the rigor and regimen of the certification examinations – Provides a business and technology orientation to risk management Benefits of (ISC)2 Certification to the Professional – Confirms a working knowledge of information security – Confirms passing of a rigorous examination – Career differentiator, with peer networking and added IS credibility – Broadening expectation of credentials

1. Introduction CISSP Overview 1. 3 How to become certified? (1) Determine which type of certification you are best qualified for: (2) CISSP [Certified Information Systems Security Professional] ? Tailored for IS professionals with a minimum of 3 years cumulative experience in one or more of the ten CBK domains (3) Understand accept the principles stated in the (ISC)2 Certification Code of Ethics, which all certified individuals are required to adhere to. (4) Broaden your IS understanding of the Common Body of Knowledge [CBK], usually achieved through personal study guides [which can be downloaded online], taking of CBK Review Seminars, keeping abreast of industry news, and familiarity with examination reference materials. (5) Taking and passing of the appropriate certification examination. (6) Upon passing the certification examination, continuing to keep your credential vital with continuing professional education, recertification every three years and other requirements to stay in good standing.

CISSP Overview 1. Introduction 1. 4 Code of Ethics Safety of the commonwealth, duty to our principals, and to each other requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior. Therefore, strict adherence to this code is a condition of certification. Canons § Protect society, the commonwealth, and the infrastructure. § Act honorably, honestly, justly, responsibly, and legally. § Provide diligent and competent service to principals. § Advance and protect the profession.

1. Introduction CISSP Overview 1. 5 CISSP Exam Structure • • • The CISSP Certification examination consists of 250 multiplechoice questions. Candidates have up to 6 hours to complete the examination. Ten CISSP information systems security test domains are covered in the examination pertaining to the Common Body of Knowledge: Access Control Systems & Methodology Applications & Systems Development Business Continuity & Disaster Recovery Planning Cryptography Law, Investigation & Ethics Operations Security (Computer) Physical Security Architecture & Models Security Management Practices Telecommunications & Network Security ? I & II






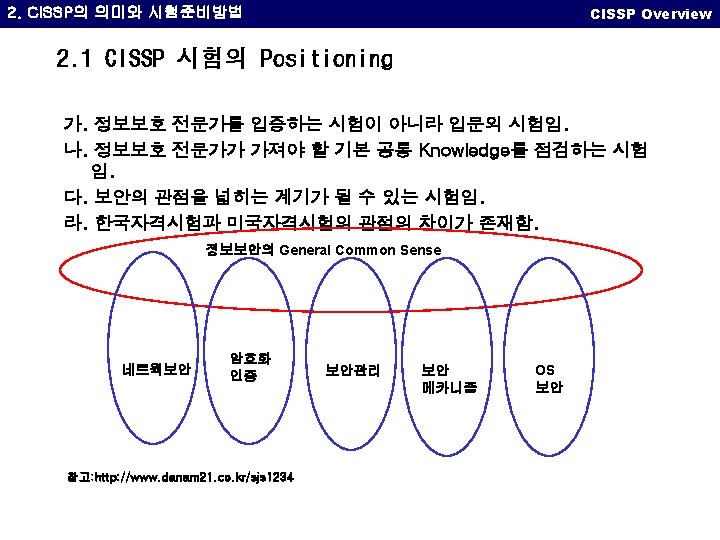
2. CISSP의 의미와 시험준비방법 CISSP Overview 2. 5 CISSP 시험 준비방법 Adrien de Beaupr의 Tips&Tricks to help you in your studies 에서 발췌 가. 아래의 책을 봐라. - Information Security Management Handbook, Tipton & Krause - CISSP Examination Textbook, Rao 나. Hal Tipton의 자료를 봐라 다. ISC 2의 Study Guide를 봐라 라. Ben Rothke의 PPT 를 봐라 마. 매일 한시간씩 읽어라 바. 최소 한달은 집중 공부해라. 사. 자신의 Study note를 만들어라 아. 시험 2주전에는 문제를 풀어봐라 자. 한주전에는 열심히 복습을 하라 차. Study group을 만들어서 서로 정보를 공유하라 카. 아래의 Site를 북마크하고 자주 들르라 - www. cccure. org, www. isc 2. org, www. sans. org, www. cissps. com



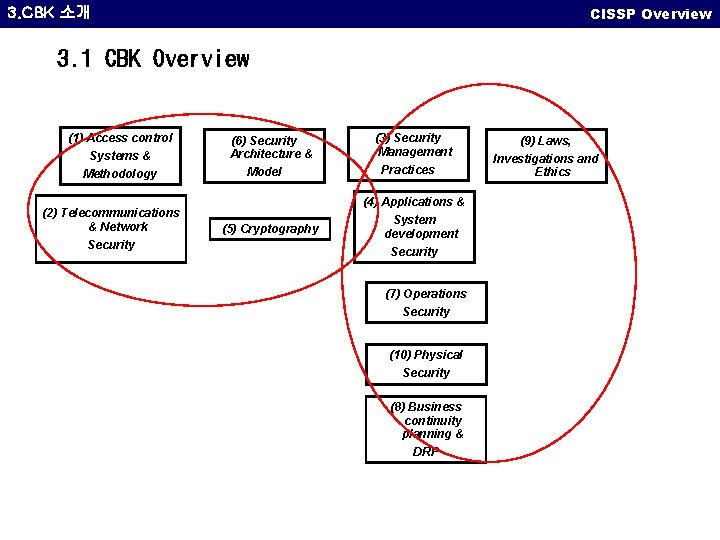
CISSP Overview 3. CBK 소개 3. 1 CBK Overview (1) Access control Systems & Methodology (2) Telecommunications & Network Security (6) Security Architecture & Model (3) Security Management Practices (4) Applications & (5) Cryptography System development Security (7) Operations Security (10) Physical Security (8) Business continuity planning & DRP (9) Laws, Investigations and Ethics

3. CBK 소개 CISSP Overview 3. 2 Access Control Systems & Methodology Access control is the collection of mechanisms that permits managers of a system to exercise a directing or restraining influence over the behavior, use & content of a system. In permits management to specify what users can do, which resources they can access, and what operations they can perform on a system. • • • Accountability Access control technique Access control Administration Access control model Identification & Authentication Techniques Access control methodologies & Implementation File & Data ownership & custodianship Methods of Attack Monitoring Penetration Testing 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 2 Access Control Systems & Methodology 이해필요사항…. • • Access control concepts, methodologies and implementation within centralized & decentralized environments across the enterprises’ computer system Access control techniques, detective and corrective measures should be studied to understands the potential risks, vulnerabilities, and exposures. 참고: CISSP Study Guide , ISC 2

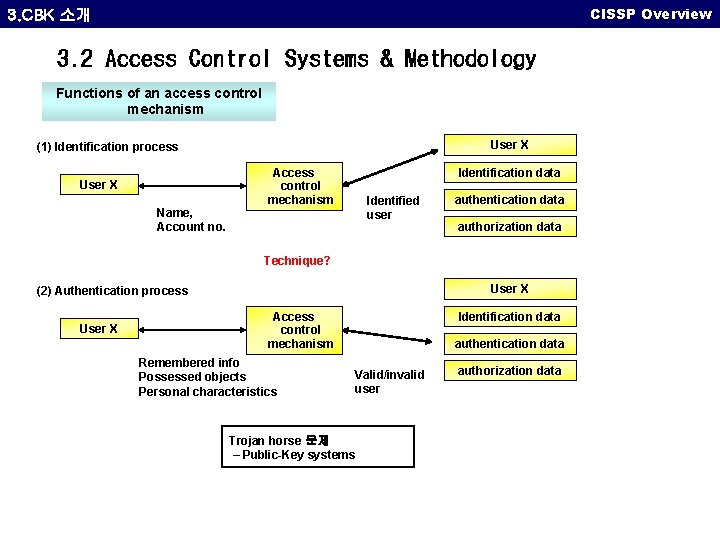
CISSP Overview 3. CBK 소개 3. 2 Access Control Systems & Methodology Functions of an access control mechanism User X (1) Identification process User X Name, Account no. Access control mechanism Identification data Identified user authentication data authorization data Technique? User X (2) Authentication process User X Access control mechanism Remembered info Possessed objects Personal characteristics Identification data authentication data Valid/invalid user Trojan horse 문제 – Public-Key systems authorization data

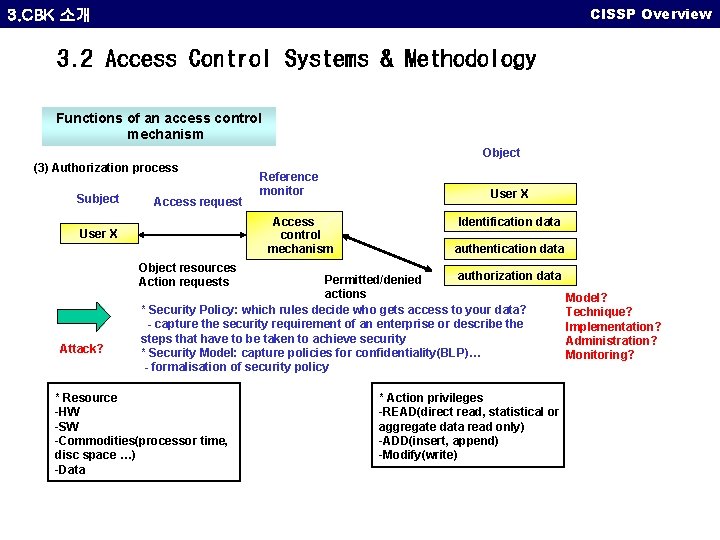
CISSP Overview 3. CBK 소개 3. 2 Access Control Systems & Methodology Functions of an access control mechanism Object (3) Authorization process Subject Access request Reference monitor Access control mechanism User X Identification data authentication data Object resources Action requests Attack? authorization data Permitted/denied actions * Security Policy: which rules decide who gets access to your data? - capture the security requirement of an enterprise or describe the steps that have to be taken to achieve security * Security Model: capture policies for confidentiality(BLP)… - formalisation of security policy * Resource -HW -SW -Commodities(processor time, disc space …) -Data * Action privileges -READ(direct read, statistical or aggregate data read only) -ADD(insert, append) -Modify(write) Model? Technique? Implementation? Administration? Monitoring?

3. CBK 소개 CISSP Overview 3. 2 Access Control Systems & Methodology 1. The Computer Security Policy Model the Orange Book is based on is: the Bell-La. Padula Model the Data Encryption Standard (DES) Kerberos Tempest 2. Which of the following is needed for System Accountability? audit mechanisms documented design as laid out in the Common Criteria authorization Formal verification of system design

3. CBK 소개 CISSP Overview 3. 3 Telecommunications & Network Security Telecommunication & Network Security domain encompasses the structures, transmission methods, transport formats, & security measures used to provide integrity, availability, authentication, and confidentiality for transmissions over private & public communications networks and media. • • • ISO/OSI Layers and characteristics Communication Network Security Internet/Intranet/Extranet - Firewalls, Routers, Switches, Gateways, Proxies Protocols, Services, Security techniques • • • E-mail Security Facsimile Security Secure Voice Communications Security boundaries and how to translate security policy to control Network Attacks & countermeasures 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 3 Telecommunications & Network Security 이해 필요사항 • • Communications & network security as it relates to voice communications Data communications in terms of local area, wide area, and remote access Intranet/Internet/Extranet in terms of Firewalls, Routers, & TCP/IP Communications security management & techniques in terms of preventive, detective and corrective measures. 참고: CISSP Study Guide , ISC 2

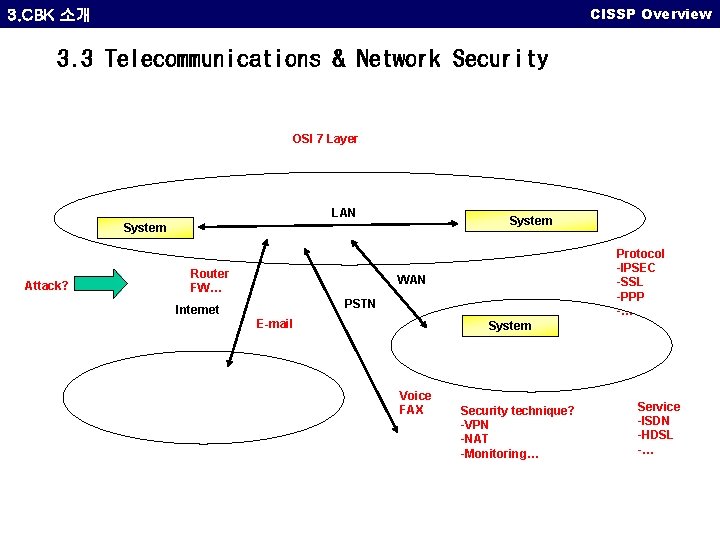
CISSP Overview 3. CBK 소개 3. 3 Telecommunications & Network Security OSI 7 Layer LAN System Attack? Router FW… Protocol -IPSEC -SSL -PPP -… WAN PSTN Internet E-mail System Voice FAX Security technique? -VPN -NAT -Monitoring… Service -ISDN -HDSL -…

3. CBK 소개 CISSP Overview 3. 3 Telecommunications & Network Security 10. Which one of the following benefits resulting from the use of secure gateways (firewalls) is not true: reduces the risks from malicious hackers prevents the spread of viruses reduces the threat level on internal system allow centralize management and control of services

3. CBK 소개 CISSP Overview 3. 4 Security Management Practices Security management entails the identification of an organizations’ information assets and the development, documentation, and implementation of policies, standards, procedures, and guidelines that ensure confidentiality, Integrity, and availability. Management tools such as data classification, risk assessment, and risk analysis are used to identify the threats, classify assets, and to rate their vulnerabilities so that effective security controls can be implemented. • • • Security Management Concepts & Principles Change Control/Management Data Classification Information/Data Employment policies & Practices Policies, Standards, Guideline and Procedures Role & Responsibilities Security Awareness Training Security Management Planning 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 4 Security Management Practices 이해 필요사항 • • • The planning, organization, and roles of individuals in identifying and securing an organization’s information assets The development and use of policies stating management’s views and position on particular topics and the use of guidelines, standards, and procedures, to support the policies Security Awareness training The importance of confidentiality, proprietary and private information Employment agreement, hiring, and termination practices Risk Management practices 참고: CISSP Study Guide , ISC 2

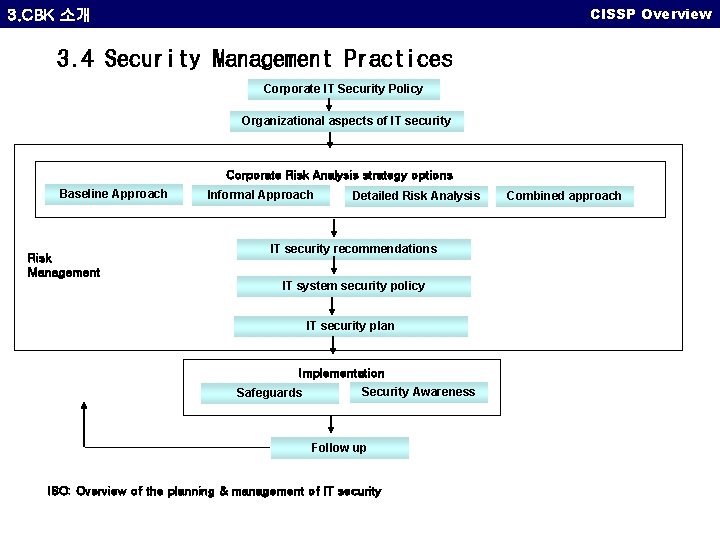
CISSP Overview 3. CBK 소개 3. 4 Security Management Practices Corporate IT Security Policy Organizational aspects of IT security Corporate Risk Analysis strategy options Baseline Approach Risk Management Informal Approach Detailed Risk Analysis IT security recommendations IT system security policy IT security plan Implementation Safeguards Security Awareness Follow up ISO: Overview of the planning & management of IT security Combined approach

3. CBK 소개 CISSP Overview 3. 4 Security Management Practices 15. Which of the following is the best reason for the use of an automated risk analysis tool: much of the data gathered during the review cannot be reused for subsequent analysis's automated methodologies require minimal training and knowledge of risk analysis most software tools have user interfaces that are easy to use minimal information gathering is required due to the amount of information built into the tool

3. CBK 소개 CISSP Overview 3. 5 Application & Systems Development Security Applications and systems development security refers to the controls that are included within systems and applications software and the steps used in their development. Applications refer to agents, applets, SW, DB, DW, KB systems. • • Application Issues Database & DW Data/Information storage Knowledge-based Systems System Development Controls Malicious Code Methods of Attack 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 5 Application & Systems Development Security 이해 필요사항 • Security & controls of System development process, system life cycle, application control, DW, DM, KB systems, program interfaces, and concepts used to ensure data and application integrity, security and availability 참고: CISSP Study Guide , ISC 2

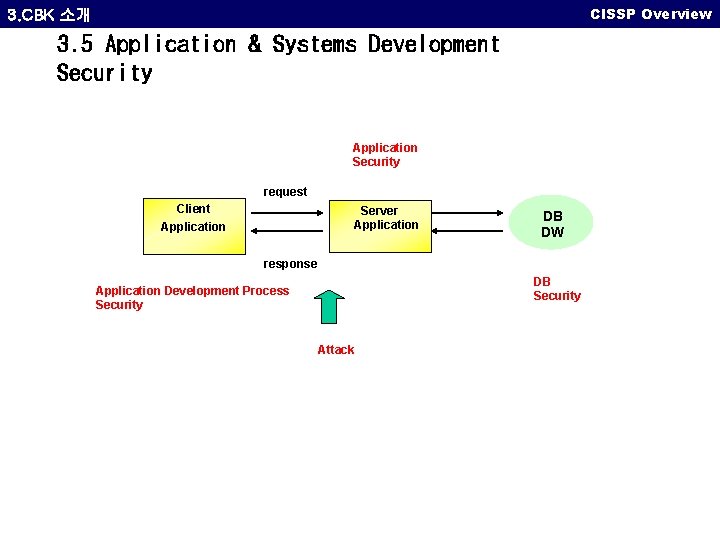
CISSP Overview 3. CBK 소개 3. 5 Application & Systems Development Security Application Security request Client Server Application DB DW response DB Security Application Development Process Security Attack

3. CBK 소개 3. 5 Application & Systems Development Security 16. Which of the following can be used as a covert channel? Storage and timing Storage and low bits Storage and permissions Storage and classification CISSP Overview

3. CBK 소개 CISSP Overview 3. 6 Cryptography domain addressed the principles, means, and methods of disguising information to ensure its integrity, confidentiality, and authenticity. • • Use of Cryptography to achieve Cryptographic concepts, methodologies, and practices Private key algorithms Public Key algorithms PKI System architecture for implementing cryptographic functions Method of attack 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 6 Cryptography 이해 필요사항 • • • Public key and private key algorithms in terms of their applications and uses Algorithm construction, key distribution and management, and methods of attack The application, construction, and use of digital signatures to provide authenticity of electronic transactions, and nonrepudiation of the parties involved. 참고: CISSP Study Guide , ISC 2

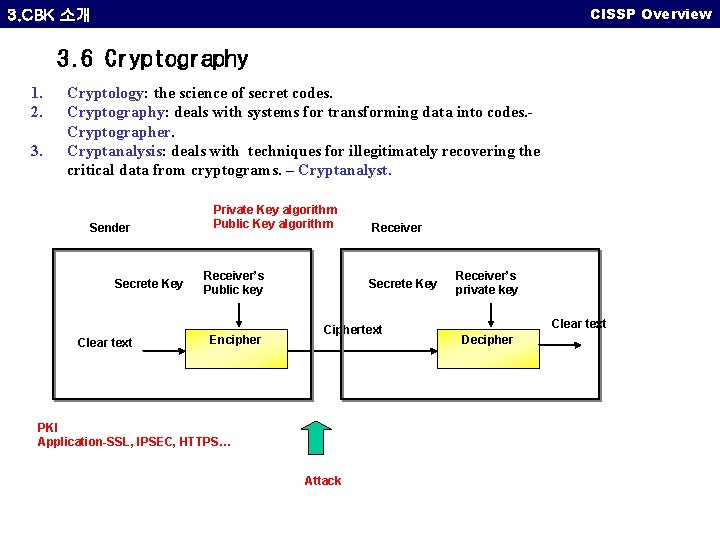
CISSP Overview 3. CBK 소개 3. 6 Cryptography 1. 2. 3. Cryptology: the science of secret codes. Cryptography: deals with systems for transforming data into codes. Cryptographer. Cryptanalysis: deals with techniques for illegitimately recovering the critical data from cryptograms. – Cryptanalyst. Sender Secrete Key Clear text Private Key algorithm Public Key algorithm Receiver’s Public key Encipher Receiver Secrete Key Ciphertext PKI Application-SSL, IPSEC, HTTPS… Attack Receiver’s private key Clear text Decipher

3. CBK 소개 CISSP Overview 3. 6 Cryptography Which one of the following statements about digital signatures is not true: it enhances authentication it makes repudiation by the sender possible it prevents non-repudiation by the receiver it makes repudiation by the sender impossible

3. CBK 소개 CISSP Overview 3. 7 Security Architecture & Models The security architectures and models contains the concepts, principles, structures, and standards used to design, implement, monitor, and secure, operating systems, equipment, networks, applications, and those controls used to inforce various levels of confidentiality, integrity, and availability. • • • Principles of common computer and network organizations, architectures and designs. Principles of common security models(BLP…), architectures(IPSEC. . ), and evaluation criteria(Orange Book, ITSEC. . ). Common flaw and security issues associated with system architectures and designs 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 7 Security Architecture & Models 이해 필요사항 • • Security models in terms of confidentiality, integrity, information flow, commercial vs. government requirements System models in terms of CC, ITSEC, TCSE, IETF IPSEC Technical platforms in terms of HW, firmware, and SW System security techniques in terms of preventative, detective, and corrective controls 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 7 Security Architecture & Models 26. In Mandatory Access Control, sensitivity labels contain what information? the item's classification and catagory set the item's classification, catagory and compartment the item's classification and it's compartment

CISSP Overview 3. CBK 소개 3. 8 Operations Security Operation Security is used to identify the controls over HW, media, and the operator with access privileges to any resources. • • • • Administrative management Concepts Control Types Operation controls Resource Protection Auditing Audit trails Monitoring tools and techniques Intrusion detection Penetrating testing techniques Threats and countermeasures Violation, Breaches, and reporting 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 8 Operations Security 이해 필요사항 • The resources that must be protected, the privileges that must be restricted, the control mechanisms available, the potential for abuse of access, the appropriate controls, and the principles of good practice. 참고: CISSP Study Guide , ISC 2

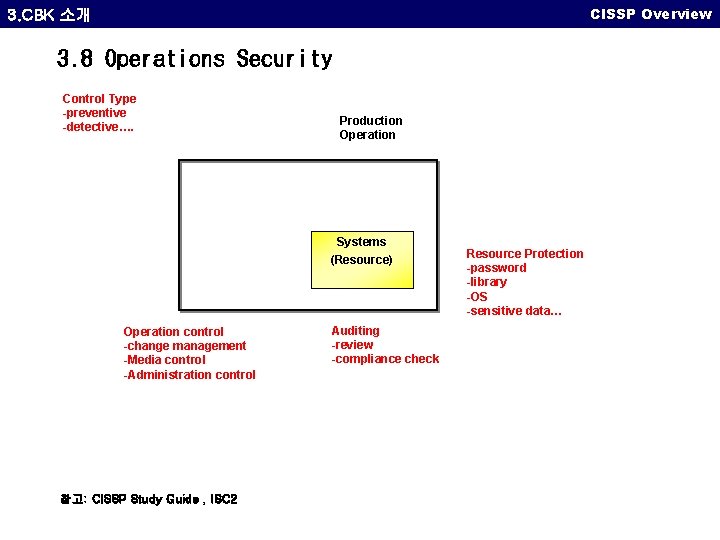
CISSP Overview 3. CBK 소개 3. 8 Operations Security Control Type -preventive -detective…. Production Operation Systems (Resource) Operation control -change management -Media control -Administration control 참고: CISSP Study Guide , ISC 2 Auditing -review -compliance check Resource Protection -password -library -OS -sensitive data…

3. CBK 소개 CISSP Overview 3. 8 Operations Security 32. It is a violation of the "separation of duties" principle when which of the following individuals access the security systems software: security administrator security analyst systems auditor systems programmer 참고: CISSP Study Guide , ISC 2

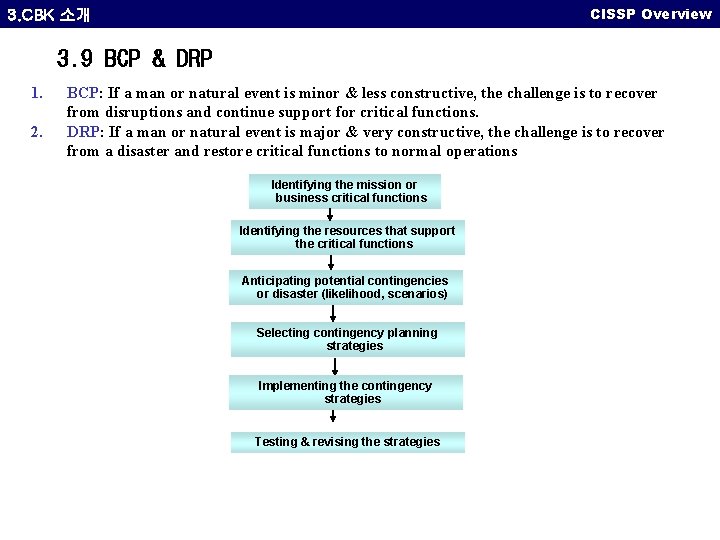
CISSP Overview 3. CBK 소개 3. 9 BCP & DRP The BCP & DRP domain addresses the preservation of the business in the face of major disruptions to normal business operations. BCP & DRP involve the preparation, testing and updating of specific actions to protect critical business processes from the effect of major system and network failure. • • BCP DRP Element of business continuity planning BCP/DRP Events 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 9 BCP & DRP 이해 필요사항 • • • The difference of BCP & DRP Business continuity planning in terms of project scope and planning, business impact analysis, recovery strategies, recovery plan development, and implementation. DR in terms of recovery plan development, implementation and restoration. 참고: CISSP Study Guide , ISC 2

CISSP Overview 3. CBK 소개 3. 9 BCP & DRP 1. 2. BCP: If a man or natural event is minor & less constructive, the challenge is to recover from disruptions and continue support for critical functions. DRP: If a man or natural event is major & very constructive, the challenge is to recover from a disaster and restore critical functions to normal operations Identifying the mission or business critical functions Identifying the resources that support the critical functions Anticipating potential contingencies or disaster (likelihood, scenarios) Selecting contingency planning strategies Implementing the contingency strategies Testing & revising the strategies

3. CBK 소개 CISSP Overview 3. 9 BCP & DRP 37. Which of the following *must* be at a "hot site"? Backup data, computers, climate control, cables and peripherals Computers, peripherals, and dedicated climate control systems Dedicated climate control systems

CISSP Overview 3. CBK 소개 3. 10 Law, Investigations & Ethics The Law, Investigations, and Ethics domain address computer crime laws & regulations; the investigative measures and techniques which can be used to determine if a crime has been committed, methods to gather evidence if it has, as well as the ethical issues and code of conduct for the security professional. • • • Laws Major categories and types of laws Investigations Major categories of computer crimes Incident handling Ethics 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 10 Law, Investigations & Ethics 이해 필요사항 • • • The method for determining whether a computer crime has been committed The law that would be applicable for the crime Laws prohibiting specific types of computer crime Methods to gather and preserve evidence of a computer crime, investigative methods and techniques The way in which RFC 1087 and ISC 2 code of ethics 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 10 Law, Investigations & Ethics 44. The ISC 2 Code of Ethics does not include which of the following behaviors for a CISSP: moral ethical legal control

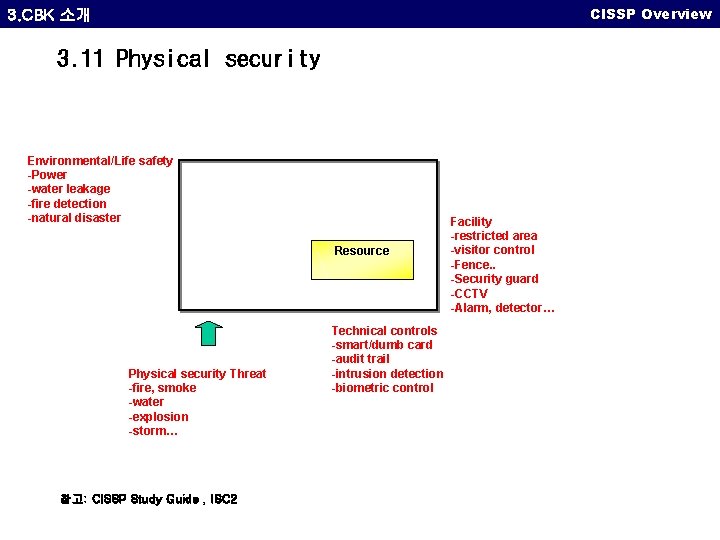
CISSP Overview 3. CBK 소개 3. 11 Physical security The Physical security domain addresses the threats, vulnerabilities, and countermeasures that can be utilized to physically protect an enterprise’s resources and sensitive information. These resources include people, the facility in which they work, and the data, equipment, support system, media, and supplies they utilize. • • • Facility Requirements Technical Controls Environment/Life Safety Physical security threats Elements of physical security 참고: CISSP Study Guide , ISC 2

3. CBK 소개 CISSP Overview 3. 11 Physical security 이해 필요사항 • The elements involved in choosing a secure site, its design and configuration, and the methods for securing the facility against unauthorized access, theft of equipment and information, and the environmental and safety measures needed to protect people, the facility, and its resources. 참고: CISSP Study Guide , ISC 2

CISSP Overview 3. CBK 소개 3. 11 Physical security Environmental/Life safety -Power -water leakage -fire detection -natural disaster Resource Physical security Threat -fire, smoke -water -explosion -storm… 참고: CISSP Study Guide , ISC 2 Technical controls -smart/dumb card -audit trail -intrusion detection -biometric control Facility -restricted area -visitor control -Fence. . -Security guard -CCTV -Alarm, detector…

3. CBK 소개 CISSP Overview 3. 11 Physical security 46. Which is the last line of defense in a physical security sense: people interior barriers exterior barriers perimeter barriers