CISA CYBERSECURITY AND INFRASTRUCTURE SECURITY AGENCY PROPERTY RECORDS

CISA | CYBERSECURITY AND INFRASTRUCTURE SECURITY AGENCY PROPERTY RECORDS INDUSTRY ASSOCIATION CONFERENCE TACOMA, WA SEPTEMBER 10, 2019 RONALD D WATTERS JR M. ED GSLC CYBERSECURITY ADVISOR CISA REGION X Ron Watters May 22 2019 1
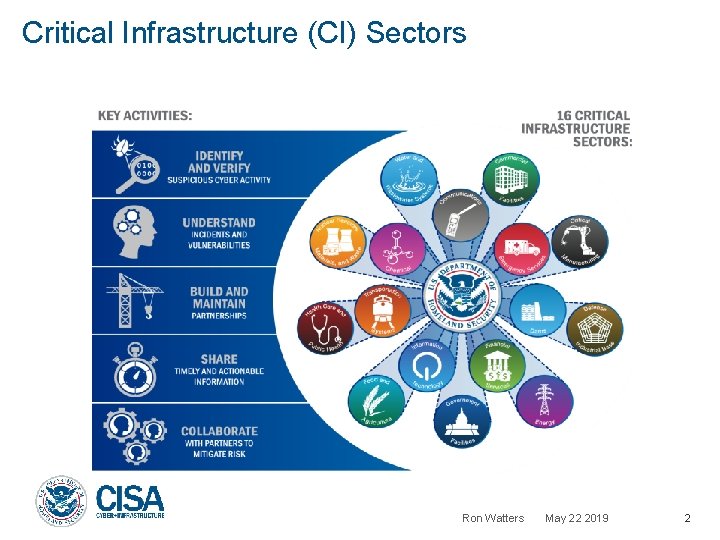
Critical Infrastructure (CI) Sectors Ron Watters May 22 2019 2

What Is Cyber Resilience? “… the ability to prepare for and adapt to changing conditions and withstand recover rapidly from disruptions. Resilience includes the ability to withstand recover from deliberate attacks, accidents, or naturally occurring threats or incidents…” - Presidential Policy Directive – PPD 21 February 12, 2013 Protect (Security) Sustain (Continuity) Perform (Capability) Repeat (Maturity) Ron Watters May 22 2019 3

CYBERSECURITY ADVISOR PROGRAM Ron Watters May 22 2019 4

Cybersecurity Advisor Program CISA mission: Lead the collaborative national effort to strengthen the security and resilience of America’s critical infrastructure In support of that mission: Cybersecurity Advisors (CSAs): • Assess: Evaluate critical infrastructure cyber risk. • Promote: Encourage best practices and risk mitigation strategies. • Build: Initiate, develop capacity, and support cyber communities-ofinterest and working groups. • Educate: Inform and raise awareness. • Listen: Collect stakeholder requirements. • Coordinate: Bring together incident support and lessons learned. Ron Watters May 22 2019 5
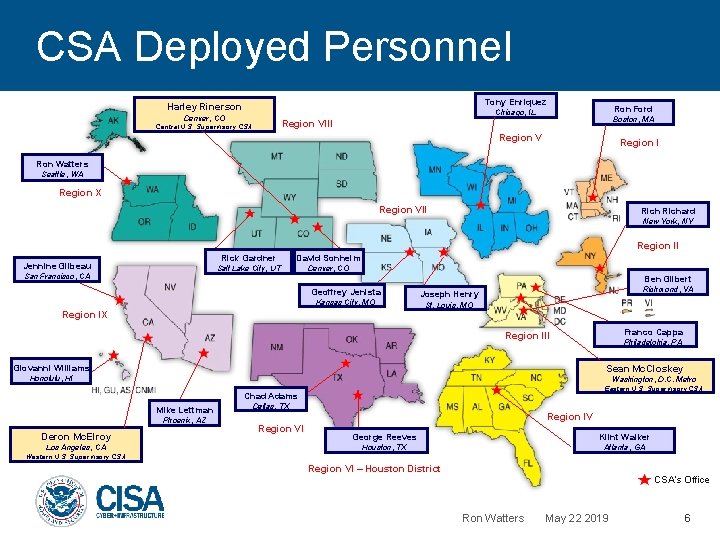
CSA Deployed Personnel Tony Enriquez Harley Rinerson Ron Ford Chicago, IL Denver, CO Boston, MA Region VIII Central U. S. Supervisory CSA Region V Region I Ron Watters Seattle, WA Region X Region VII Richard New York, NY Region II Jennine Gilbeau San Francisco, CA Rick Gardner David Sonheim Salt Lake City, UT Denver, CO Ben Gilbert Geoffrey Jenista Kansas City, MO Region IX Richmond, VA Joseph Henry St. Louis, MO Franco Cappa Region III Philadelphia, PA Giovanni Williams Sean Mc. Closkey Honolulu, HI Washington, D. C. Metro Eastern U. S. Supervisory CSA Chad Adams Mike Lettman Phoenix, AZ Deron Mc. Elroy Los Angeles, CA Dallas, TX Region IV Region VI Klint Walker George Reeves Region IV Houston, TX Atlanta, GA Western U. S. Supervisory CSA Region VI – Houston District CSA’s Office Ron Watters May 22 2019 6

Best Practices A strong password is your strongest defense. Passwords should be unique for every account. Use a password manager to help you maintain multiple complex passwords for your many accounts. Privacy and security settings exist for a reason. Use these settings on social networks and remember that you may not want to overshare details online with your digital network of friends. Personal information is like money—value it. Protect it. Be thoughtful about what you post online. Update your technology and the applications you use. Updates exist to patch known vulnerabilities. Don’t get left behind with outdated, risky software that cyber criminals can exploit. Stay protected while connected digitally. Before you connect to any public wireless hotspot – like on an airplane or in an airport, hotel, or café – be sure to confirm the name of the network and login procedures with appropriate staff. This will help to ensure that the network is legitimate. For more useful tips about secure Wi. Fi, visit https: //www. dhs. gov/stopthinkconnect. Play hard to get with strangers. Cyber criminals will often offer a financial reward, threaten you if you don’t engage, or claim that someone is in need of help. Don’t fall for it! Keep your personal information as private as possible. Cyber criminals can also use social engineering with these details to try to manipulate you into skipping normal security protocols. For more information, please visit https: //www. dhs. gov/be-cyber-smart. Use the National Initiative for Cybersecurity Careers and Studies (NICCS) website, an online national resource for cybersecurity education, careers, and training. Visit https: //niccs. us-cert. gov/ for more information today. Ron Watters May 22, 2019 7

Strong Password What makes a strong password? § Should be at least 12 characters § Should include Caps § Should Include Lower Case § Should include Numbers § Should Include Special Characters § Should not be associative to user § Should not be a derivative of “Password” § P@$$W 0 rd § Password 1 Ron Watters May 22, 2019 8

Strong Password Recent Findings by Microsoft of Passwords in the PNW Recent Strength Findings in study by CMU Ron Watters May 22, 2019 9

Privacy and Security Settings Don’t allow web sites to collect any more information than necessary to conduct business Make sure your e. Footprint is minimal OPSEC, OPSEC The world looks at Social Media Ron Watters May 22, 2019 10
Update your technology and applications you use Update your O/S Regularly § Set to do Window's update automatically Update Adobe regularly Update Firefox Regularly Control your own system YOUR RISK IS MY RISK!! Ron Watters May 22, 2019 11

Stay protected while connected digitally Be careful on what access point you connect to. Utilize VPN technology Never use “Open” Access Points without VPN You connect to the WORLD Ron Watters May 22, 2019 12

Play hard to get with strangers Remember the following: § Microsoft is not going to call you to tell you that there is a virus on your system § The IRS is not going to call you to tell you that you cheated on your taxes and there is a warrant for your arrest § Don’t ever give your CC number to phone solicitors § File a complaint at the IC 3 website (Internet Crime Complaint Center)(Http: //www. ic 3. gov) Ron Watters May 13 22, 2019 13

CISA | CYBERSECURITY AND INFRASTRUCTURE SECURITY AGENCY CRITICAL QUESTIONS FOR CONSIDERATION Ron Watters May 22 2019

Some Critical Cybersecurity Questions: • How do you measure if your cybersecurity efforts are going well? Ron Watters May 22, 2019 15

Some Critical Cybersecurity Questions: • How do you measure if your cybersecurity efforts are going well? • Do you plan your cybersecurity activities? Ron Watters May 22, 2019 16

Some Critical Cybersecurity Questions: • How do you measure if your cybersecurity efforts are going well? • Do you plan your cybersecurity activities? • Do you adhere to a cybersecurity standard of practice? Is your system accredited? Is the Accreditation reviewed regularly? Ron Watters May 22, 2019 17

Some Critical Cybersecurity Questions: • How do you measure if your cybersecurity efforts are going well? • Do you plan your cybersecurity activities? • Do you adhere to a cybersecurity standard of practice? Is your system accredited? Is the Accreditation reviewed regularly? • Who is responsible and accountable for cybersecurity? Are they measuring and managing the effort? Ron Watters May 22, 2019 18

Some Critical Cybersecurity Questions: • What’s at risk? Have you identified the potential consequences if your systems are compromised? Is your system scalable? Ron Watters May 22, 2019 19

Some Critical Cybersecurity Questions: • What’s at risk? Have you identified the potential consequences if your systems are compromised? Is your system scalable? • Have you planned for cyber incident management and exercised that plan? Ron Watters May 22, 2019 20

Some Critical Cybersecurity Questions: • What’s at risk? Have you identified the potential consequences if your systems are compromised? Is your system scalable? • Have you planned for cyber incident management and exercised that plan? • Can you sustain operations of critical processes following a significant cyber incident? Ron Watters May 22, 2019 21

DHS Offers a Wide Range of Cyber Resources for Critical Infrastructure § National Cybersecurity and Communications Integration Center (NCCIC) § US-CERT Operations Center § Remote / On-Site Assistance § Malware Analysis § Incident Response Teams § ICS-CERT Operations Center § ICS-CERT Malware Lab § Incident Response Teams § Cyber Exercise Program § Cyber Security Advisors § Protective Security Advisors § Preparedness Activities § § § National Cyber Awareness System Vulnerability Notes Database Security Publications Technical Threat Indicators Cybersecurity Training Information Products and Recommended Practices § Control Systems Evaluations § Cyber Security Evaluation Tool § ICS Design Architecture Reviews / Network Architecture Analysis § Other Cyber Security Evaluations § § Cyber Resilience Review Cyber Infrastructure Survey Tool Cyber Hygiene service Risk and Vulnerability Assessment (aka “Pen” Test) Ron Watters May 22 2019

Incident Response and Information Sharing ncciccustomerservice@hq. dhs. gov General Inquiries cyberadvisor@hq. dhs. gov Contact Information Ronald Watters Cybersecurity Advisor Region X Seattle, WA Ronald. watters@hq. dhs. gov (206)348 -4071 Ron Watters May 22 2019 23

Ron Watters May 22 2019 24
- Slides: 24