CIS 725 Advanced Computer Networks Lecture 1 Email














- Slides: 31

CIS 725 Advanced Computer Networks Lecture 1

• • • Email: gurdip@ksu. edu http: //www. cis. ksu. edu/~singh Phone: (785) 532 -7945 Fax: (785) 532 -7353 Nichols 234 C

Books • Computer Networks (not required) Andrew Tanenbaum • Lecture notes • Papers

Evaluation • • Midterm 25% Final 30% 2 -3 homeworks 15% 3 programming assignments: 30% - SPIN: Promela modeling language - UDP/TCP programming

Course contents • Protocol Design • Network protocols • Issues in network protocol design and implementation • Current research topics – – high speed networks, wireless networks sensor networks multimedia networks

Pre-requisites • Undergraduate networking or OS course or equivalent experience

Network • A set of entities connected by communication links - telephone networks - ethernet - internet - hardware circuits

Types of Networks • • • Local Area Networks Metropolitan Area Networks Wide Area Networks Wireless Networks Home Networks Internetworks

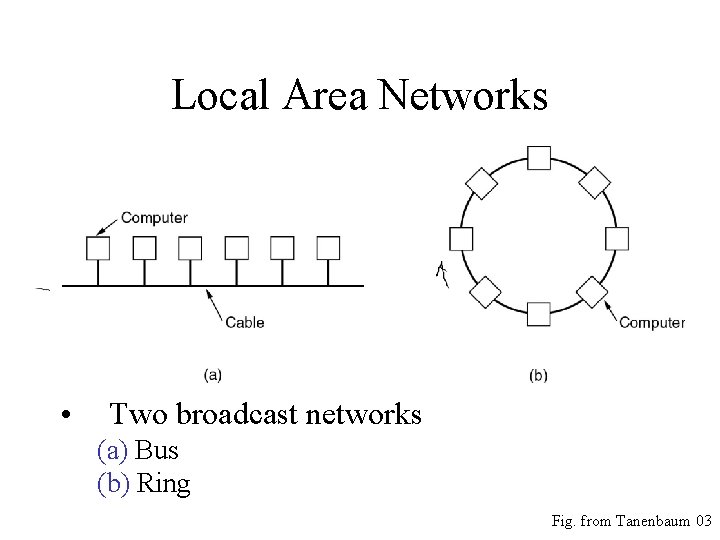
Local Area Networks • Two broadcast networks (a) Bus (b) Ring Fig. from Tanenbaum 03

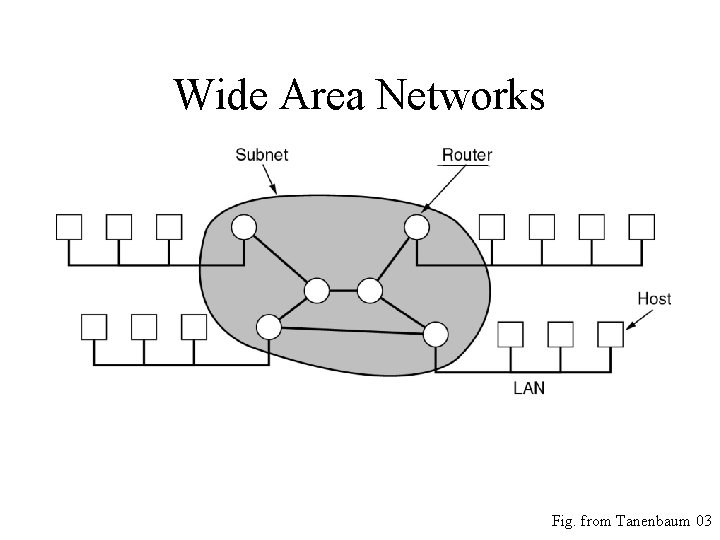
Wide Area Networks • Relation between hosts on LANs and the subnet. Fig. from Tanenbaum 03

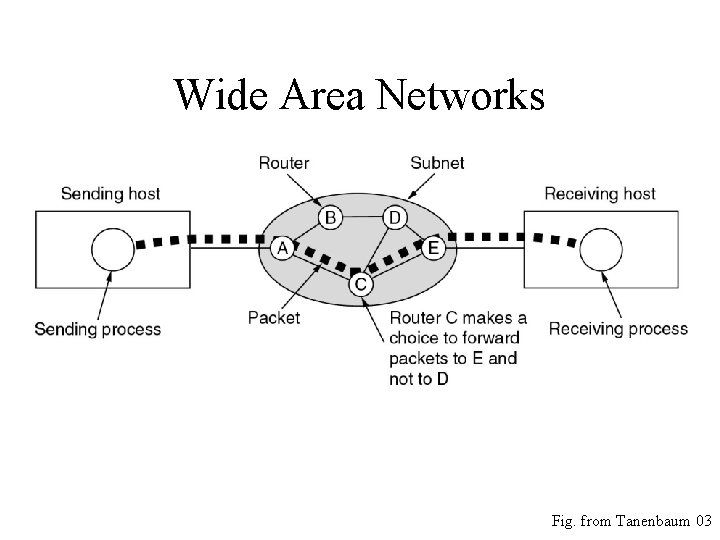
Wide Area Networks • A stream of packets from sender to receiver. Fig. from Tanenbaum 03

Wireless Networks

Home Networks • • • Computers (desktop PC, PDA, shared peripherals) Entertainment (TV, DVD, VCR, camera, stereo, MP 3) Telecomm (telephone, cell phone, intercom, fax) Appliances (microwave, fridge, clock, furnace) Telemetry (utility meter, burglar alarm, babycam).

Protocol • A set of rules for communicating - who should speak when - what is the language for communication • What are the common problems - Correctness: deadlocks, livelocks, … - Efficiency • Specification languages

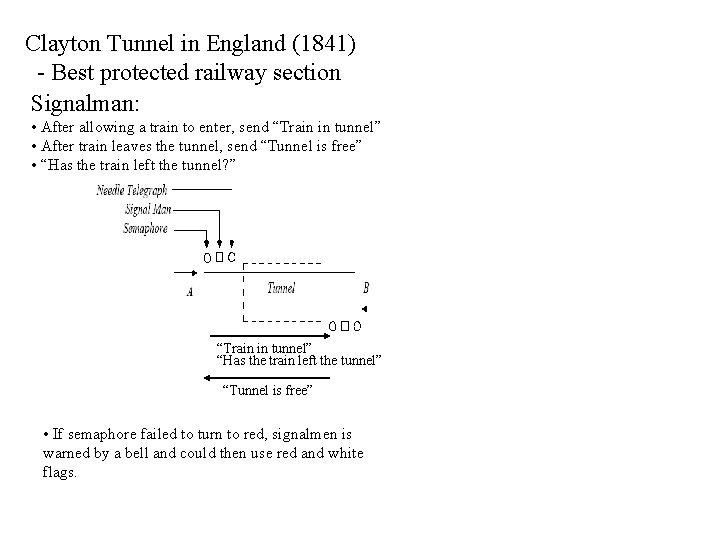
Clayton Tunnel in England (1841) - Best protected railway section Signalman: • After allowing a train to enter, send “Train in tunnel” • After train leaves the tunnel, send “Tunnel is free” • “Has the train left the tunnel? ” “Train in tunnel” “Has the train left the tunnel” “Tunnel is free” • If semaphore failed to turn to red, signalmen is warned by a bell and could then use red and white flags.

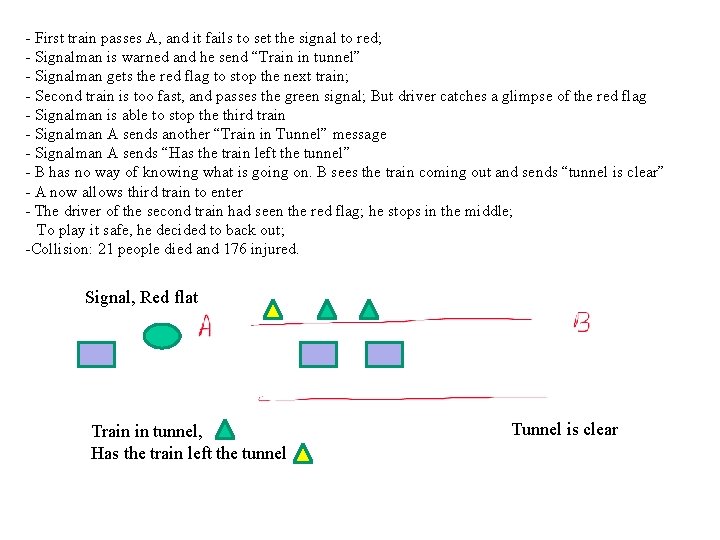
- First train passes A, and it fails to set the signal to red; - Signalman is warned and he send “Train in tunnel” - Signalman gets the red flag to stop the next train; - Second train is too fast, and passes the green signal; But driver catches a glimpse of the red flag - Signalman is able to stop the third train - Signalman A sends another “Train in Tunnel” message - Signalman A sends “Has the train left the tunnel” - B has no way of knowing what is going on. B sees the train coming out and sends “tunnel is clear” - A now allows third train to enter - The driver of the second train had seen the red flag; he stops in the middle; To play it safe, he decided to back out; -Collision: 21 people died and 176 injured. Signal, Red flat Train in tunnel, Has the train left the tunnel Tunnel is clear

Attack at 5 am

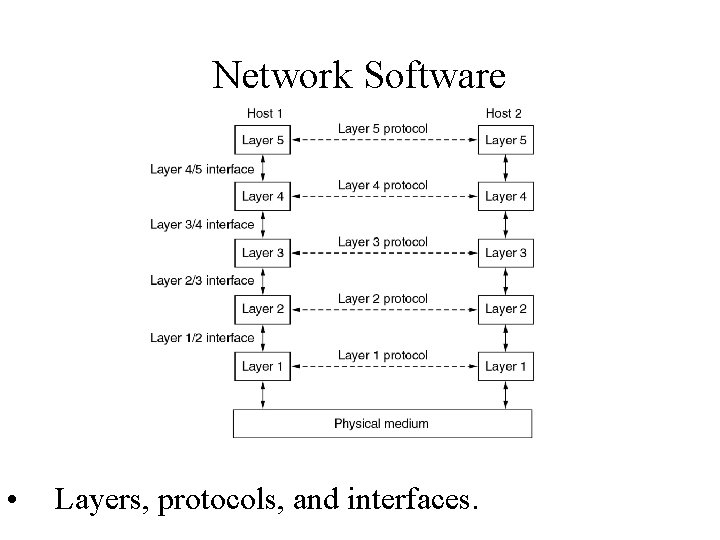
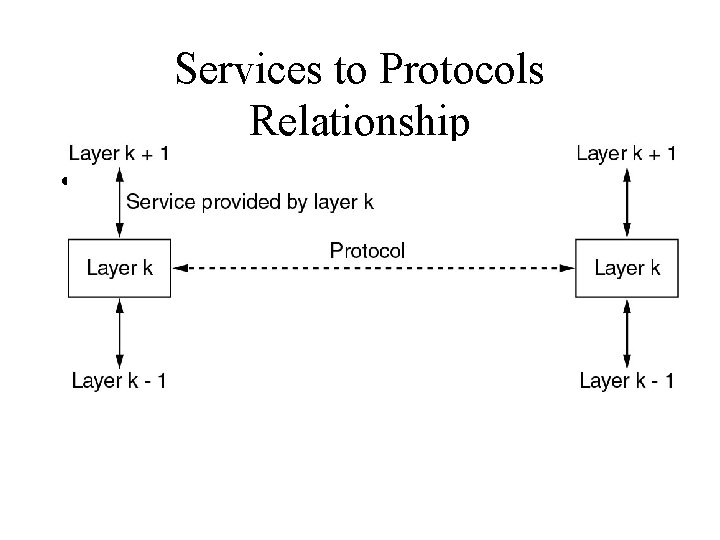
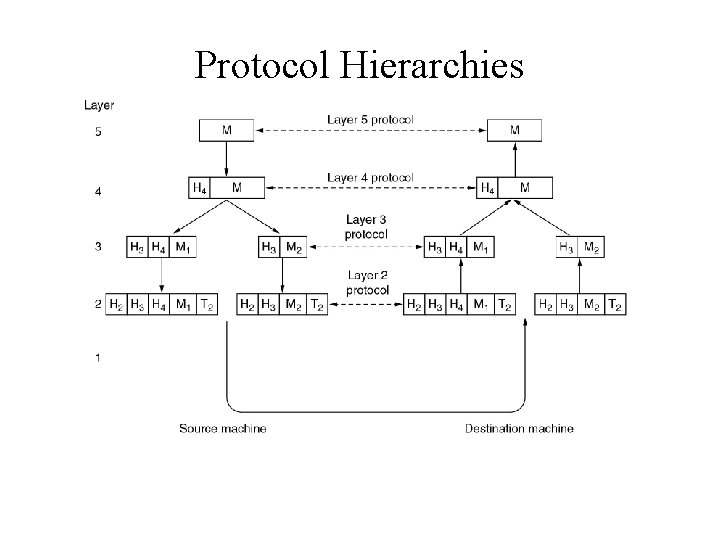
Network Software Protocol Hierarchies • Layers, protocols, and interfaces.

Layered Network Architecture • Each layer takes care of some concerns • Number of layers may vary in different networks • Each layer provides an interface to the upper layer with more functionality added.

Services to Protocols Relationship • The relationship between a service and a protocol.

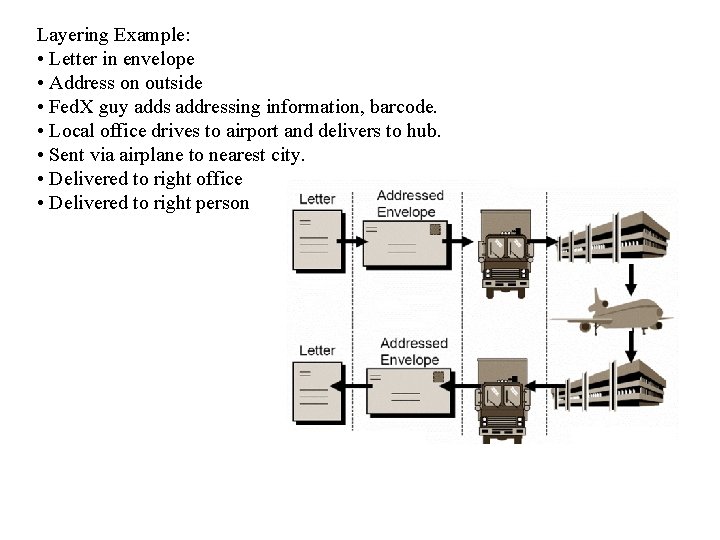
Layering Example: • Letter in envelope • Address on outside • Fed. X guy adds addressing information, barcode. • Local office drives to airport and delivers to hub. • Sent via airplane to nearest city. • Delivered to right office • Delivered to right person

Protocol Hierarchies

Problems in a network • • Naming Routing Congestion control Error Handling Flow control Security Quality of service

Seven Layer Model (ISO) • Physical Layer: - transmission of raw data over a physical channel - twisted pair, coaxial cables, fiber optics, wireless

Data Link Layer • Physical layer may lose, corrupt, reorder and duplicate data/bits. • Data link layer provides - framing - error free transmission

Network Layer • Provides communication between any pair of nodes in the network; • Provides an illusion that everyone is directly connected to everyone else • Routing • Congestion control

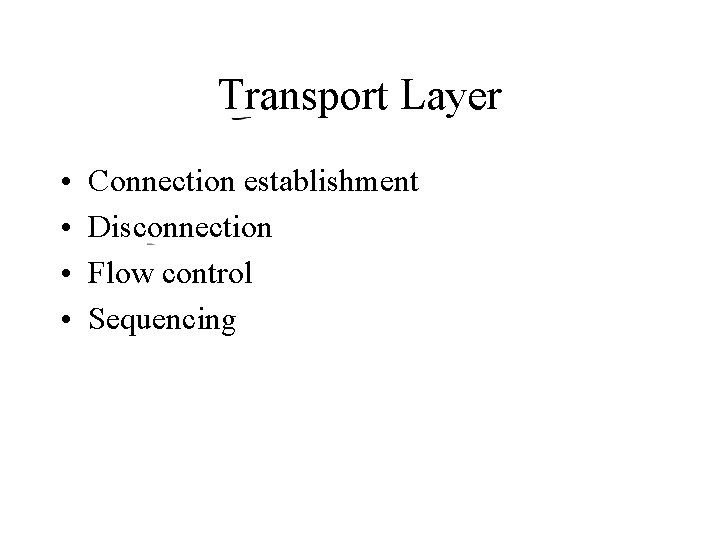
Transport Layer • • Connection establishment Disconnection Flow control Sequencing

Session Layer • Establish sessions - a session may have several connections • Recovery

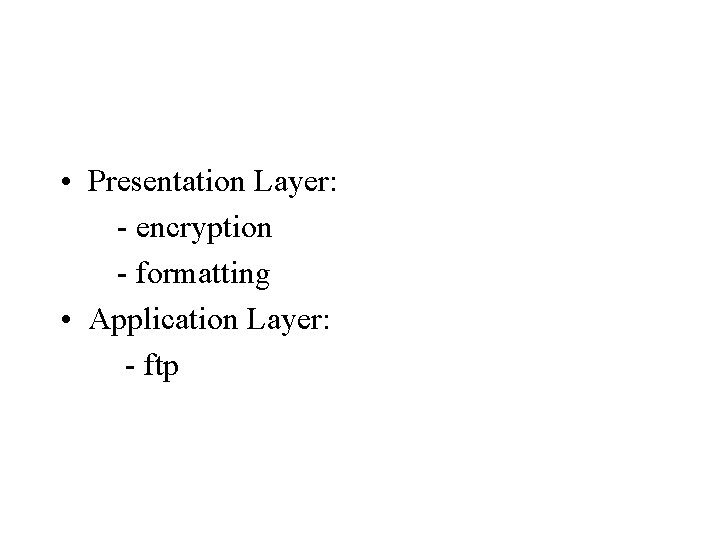
• Presentation Layer: - encryption - formatting • Application Layer: - ftp

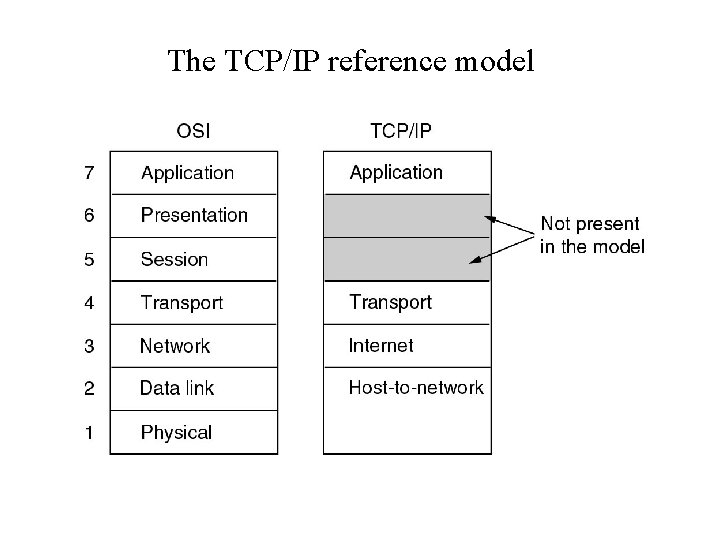
The TCP/IP reference model

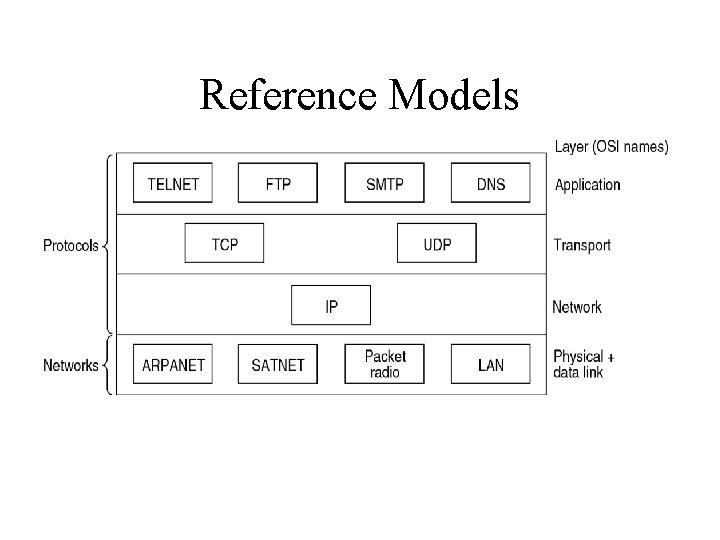
Reference Models • Protocols and networks in the TCP/IP model initially.