CIS 5371 Cryptography 6 Practical Constructions of SymmetricKey




- Slides: 28

CIS 5371 Cryptography 6. Practical Constructions of Symmetric-Key Primitives Based on: Jonathan Katz and Yehuda Lindell Introduction to Modern Cryptography 1

Stream ciphers ¡ 2

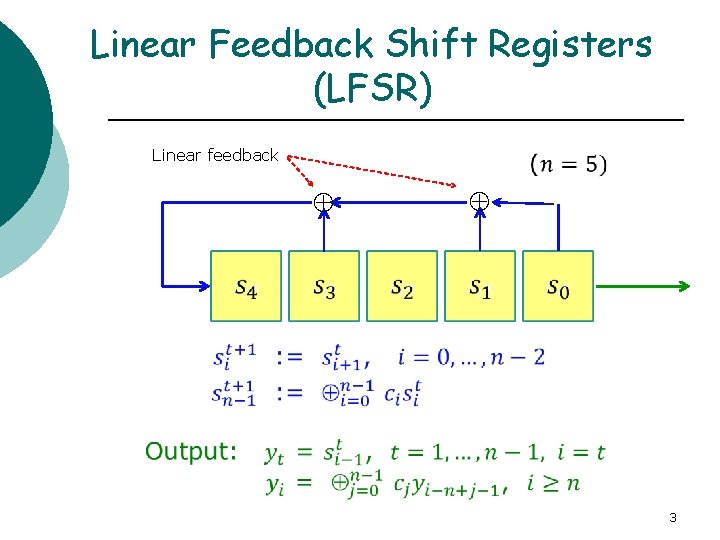
Linear Feedback Shift Registers (LFSR) Linear feedback 3

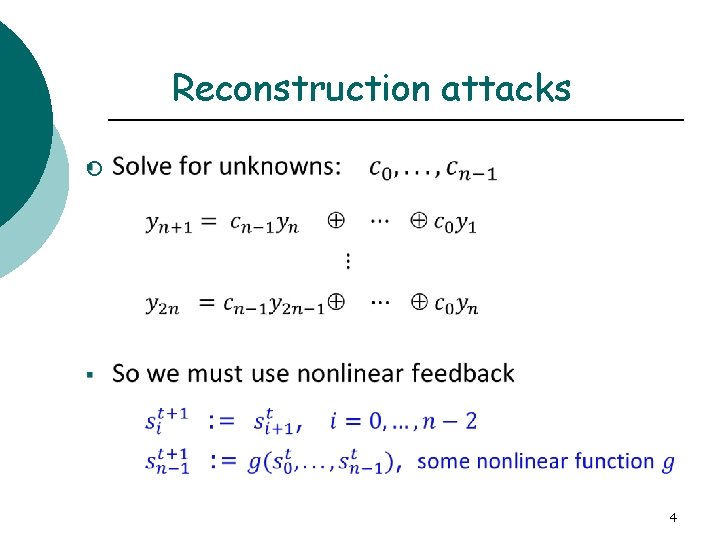
Reconstruction attacks ¡ 4

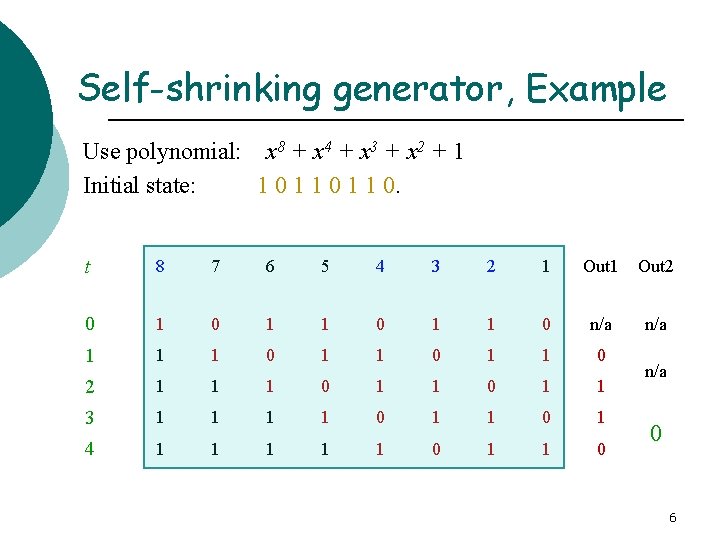
Self-shrinking generator § The self-shrinking generator uses alternating output bits of a single register to control its final output. 1. 2. 3. 4. 5. Clock two bits from the LFSR. If the pair is 10 output a zero. If the pair is 11 output a one. Otherwise, output nothing. Return to step one. 5

Self-shrinking generator, Example Use polynomial: x 8 + x 4 + x 3 + x 2 + 1 Initial state: 1 0 1 1 0. t 8 7 6 5 4 3 2 1 Out 2 0 1 1 0 n/a 1 1 1 0 2 1 1 1 0 1 1 3 1 1 0 1 4 1 1 1 0 n/a 0 6

Other nonlinear stream ciphers § Trivium, e. STREAM project --see textbook § These are hardware implementations of PRNG § Next we shall consider a software implementation. 7

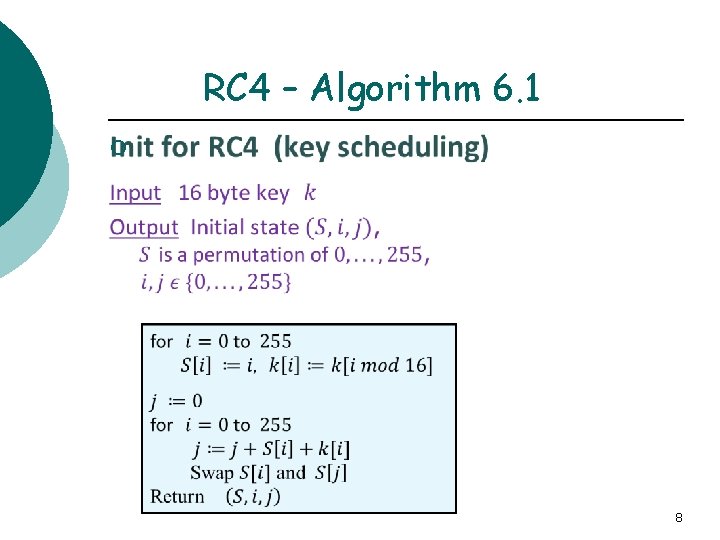
RC 4 – Algorithm 6. 1 ¡ 8

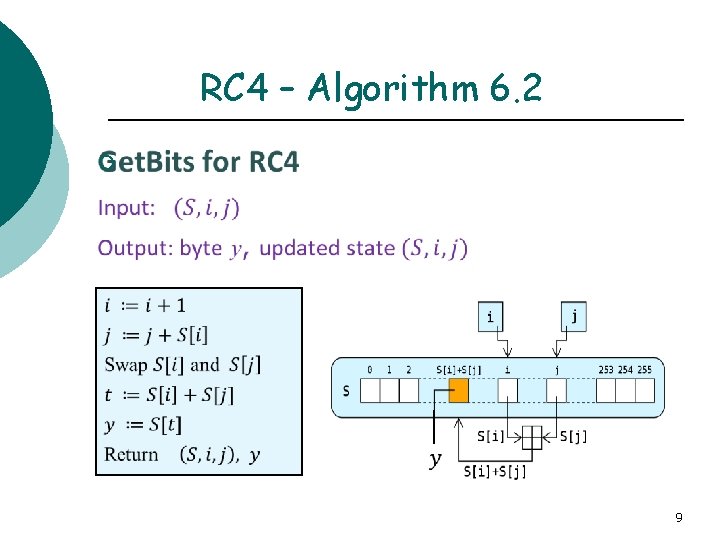
RC 4 – Algorithm 6. 2 ¡ 9

Attacks on RC 4 § § § There are several attacks on RC 4 known for some time and therefore this stream cipher should not be used anymore. A serious attack occurs when an IV is prepended to the key (though RC 4 was not designed to take and IV as input). This attack can be used to recover the key (regardless of it length), and was used to break the WEP encryption standard. It was influential in getting the standard replaced---see textbook for details of the attack. Should no longer be used: a more modern stream cipher or block cipher should be used. 10

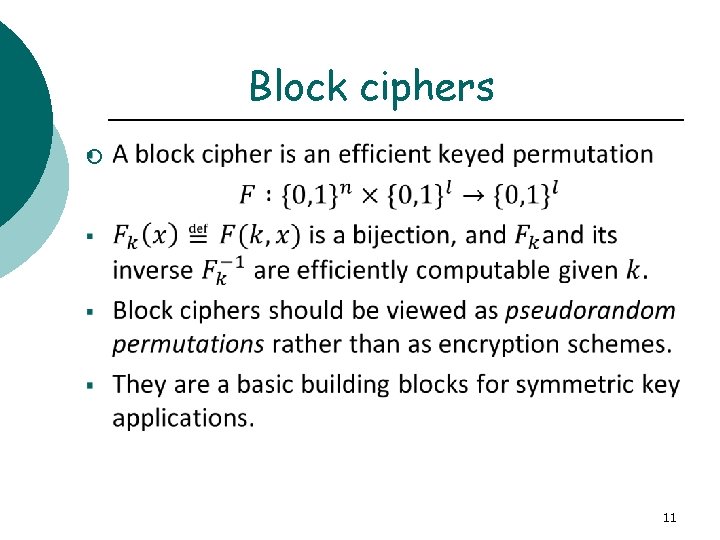
Block ciphers ¡ 11

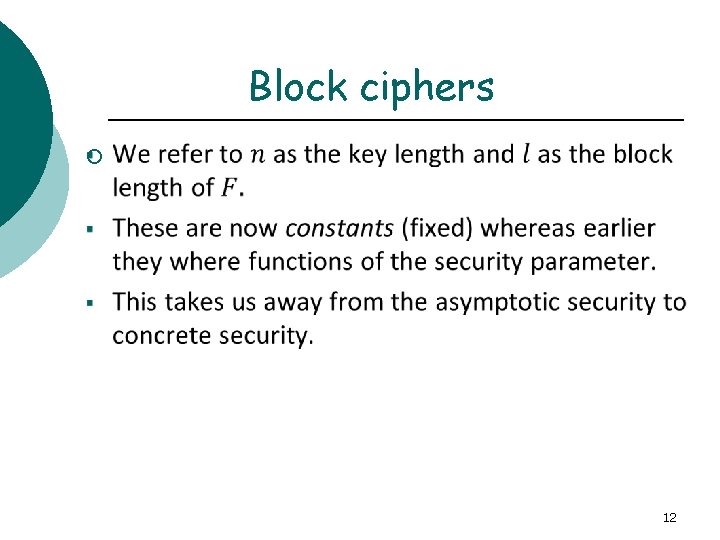
Block ciphers ¡ 12

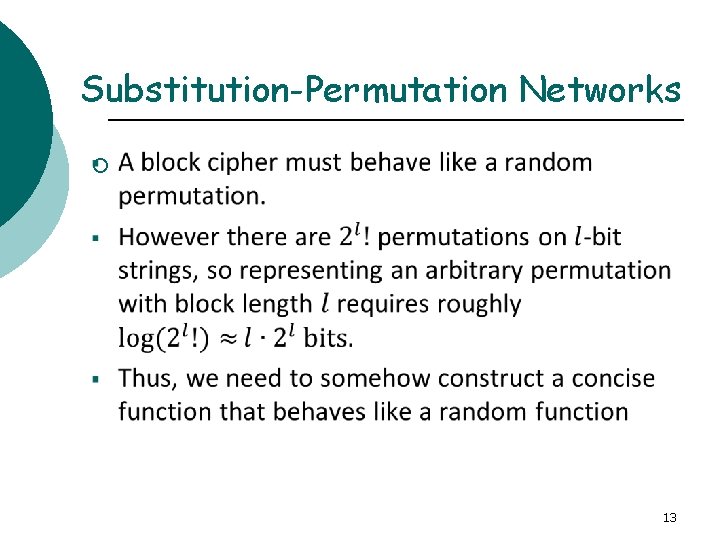
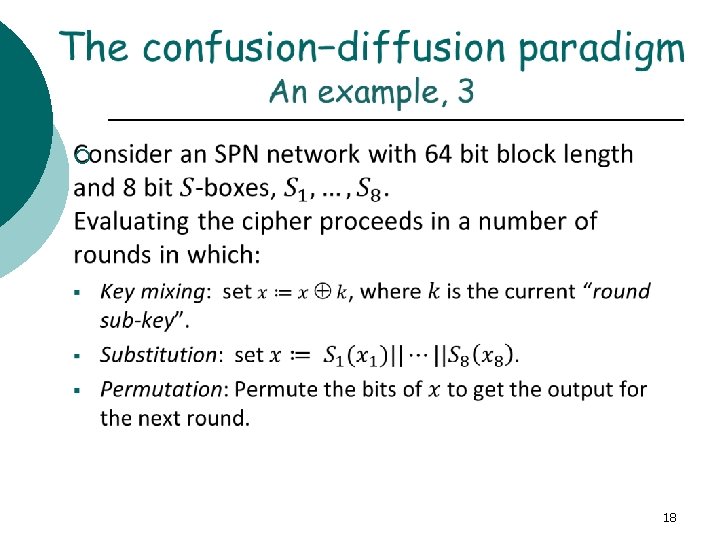
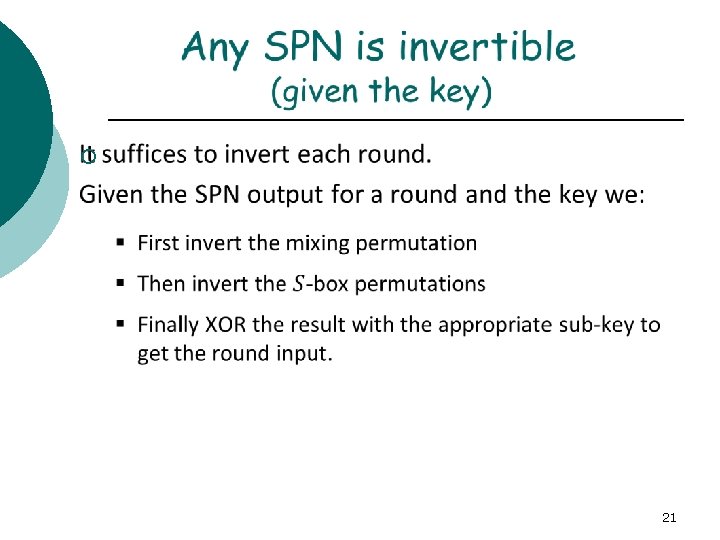
Substitution-Permutation Networks ¡ 13






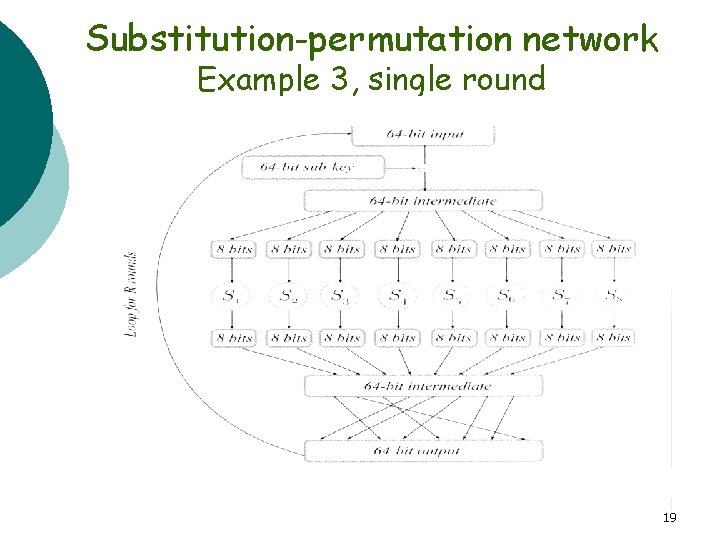
Substitution-permutation network Example 3, single round 19

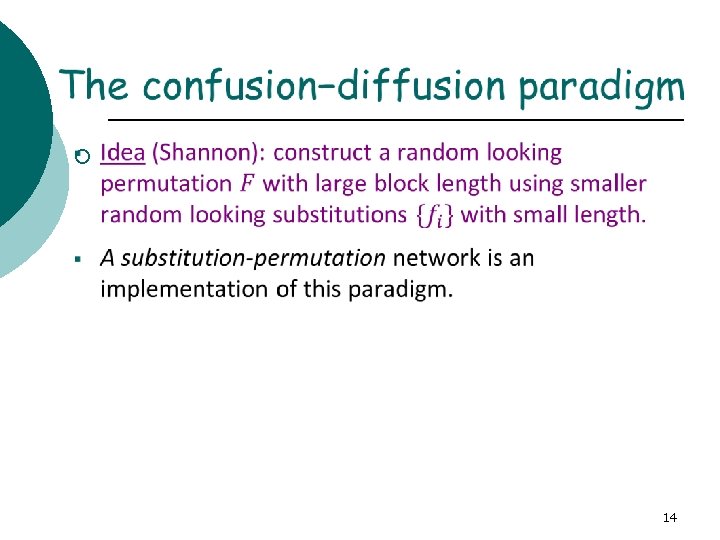
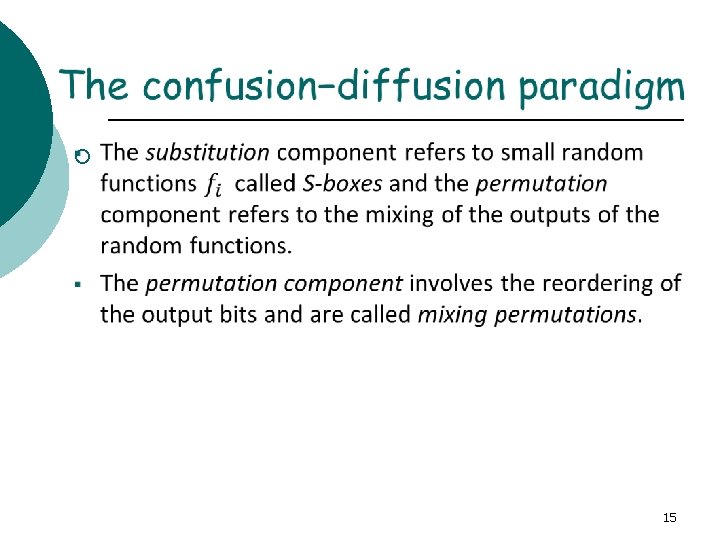
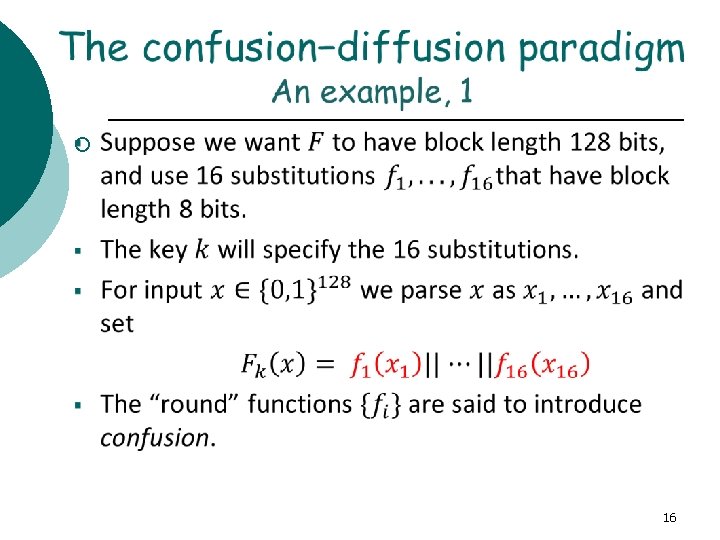
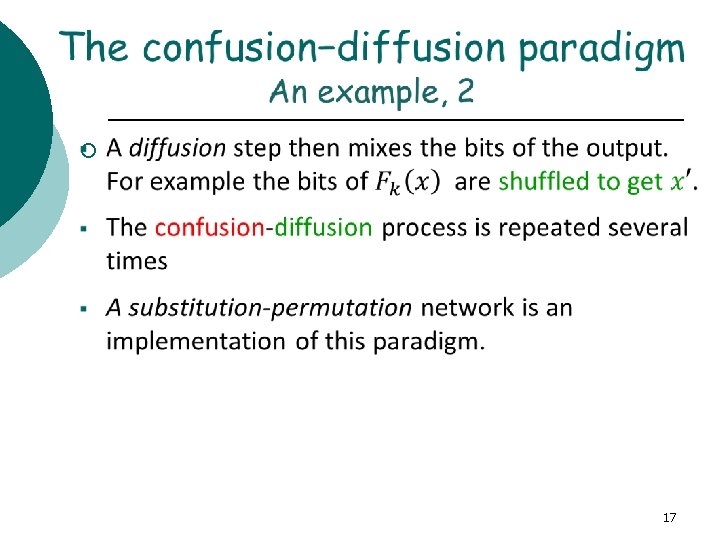
§ § § The basic idea is to break the input up into small parts and then feed these parts through different S -boxes (random permutations). The outputs are then mixed together. The process is repeated a given number of times, called a rounds. The S-boxes introduce confusion into the construction. In order to spread the confusion throughout, the results are mixed together, achieving diffusion. 20


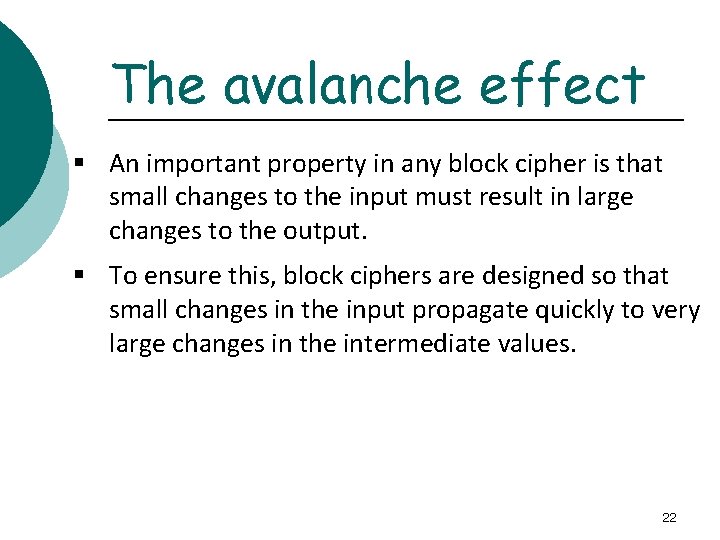
The avalanche effect § An important property in any block cipher is that small changes to the input must result in large changes to the output. § To ensure this, block ciphers are designed so that small changes in the input propagate quickly to very large changes in the intermediate values. 22

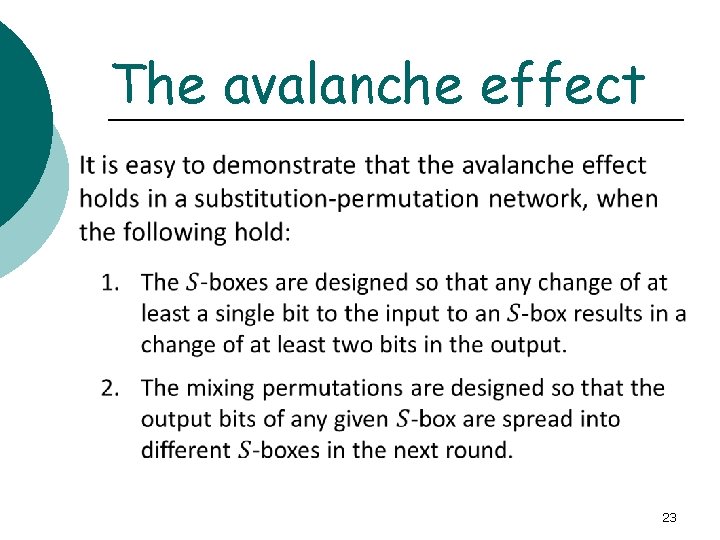
The avalanche effect 23

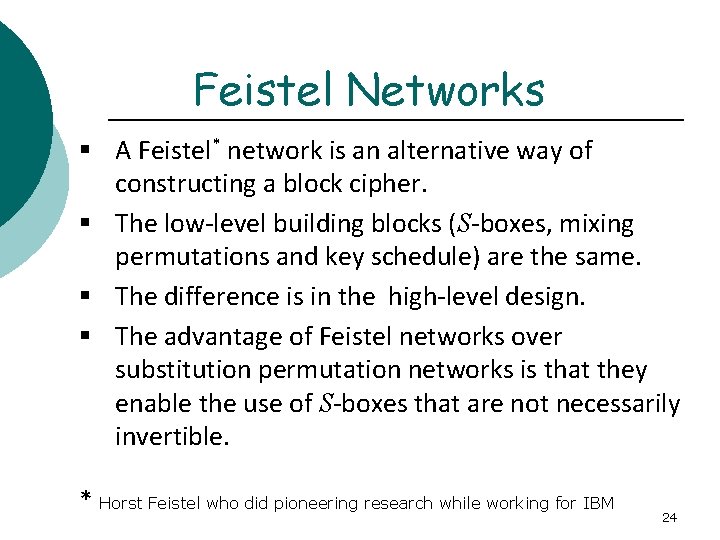
Feistel Networks § A Feistel* network is an alternative way of constructing a block cipher. § The low-level building blocks (S-boxes, mixing permutations and key schedule) are the same. § The difference is in the high-level design. § The advantage of Feistel networks over substitution permutation networks is that they enable the use of S-boxes that are not necessarily invertible. * Horst Feistel who did pioneering research while working for IBM 24

Feistel Networks § This is important because a good block cipher has chaotic behavior (it should look random). § Requiring that all of the components of the construction be invertible inherently introduces structure, which contradicts the need for chaos. 25

Feistel Networks § A Feistel network is thus a way of constructing an invertible function from non-invertible components. § This seems like a contradiction in terms---if you cannot invert the components, how can you invert the overall structure. § Nevertheless, the Feistel design ingeniously overcomes this obstacle. 26

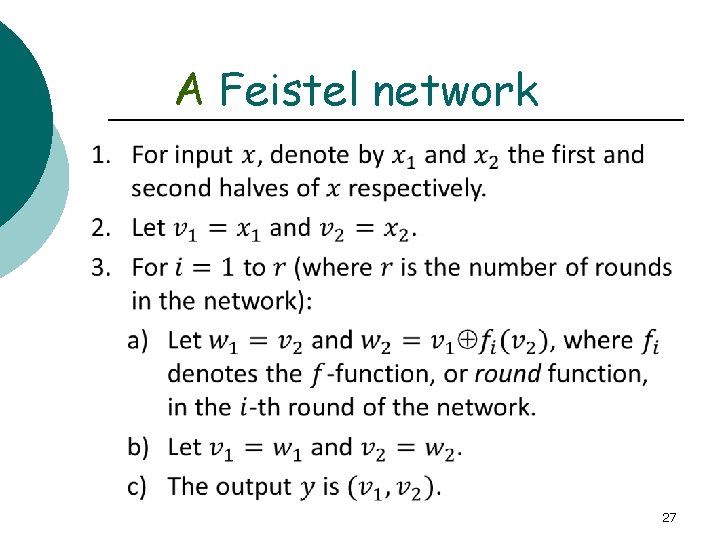
A Feistel network 27

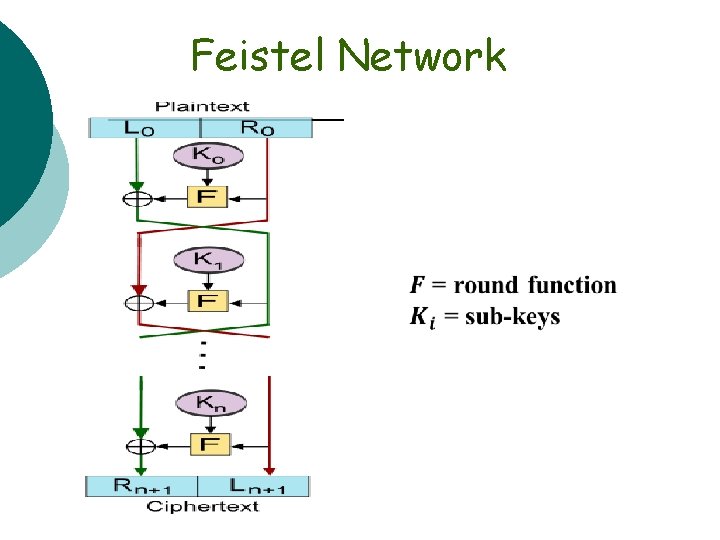
. Feistel Network mm mmm 28