Chapter Eight MANAGING RISK Which of the following














































- Slides: 60

Chapter Eight MANAGING RISK

Which of the following is most closely associated with residual risk? A. Risk acceptance B. Risk avoidance C. Risk deterrence D. Risk mitigation E. Risk transference

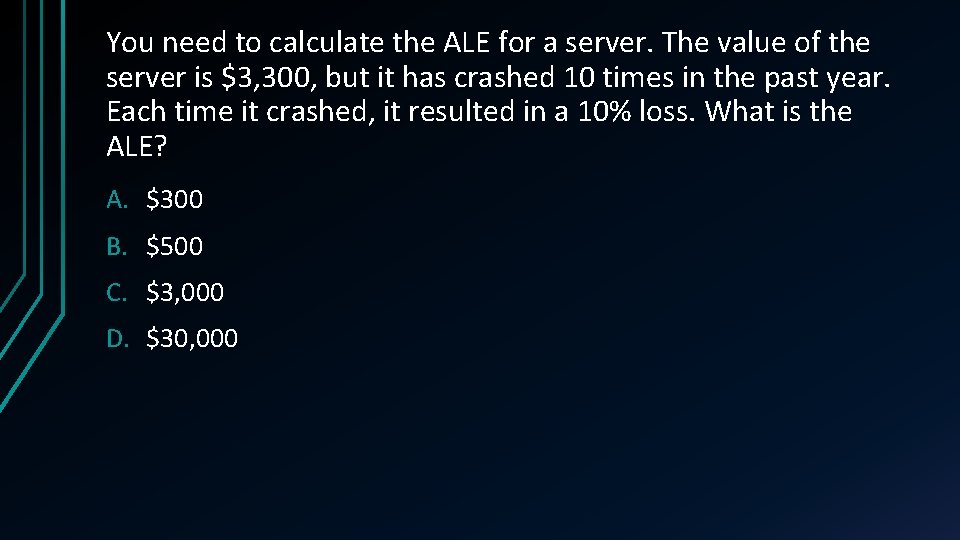
You need to calculate the ALE for a server. The value of the server is $3, 300, but it has crashed 10 times in the past year. Each time it crashed, it resulted in a 10% loss. What is the ALE? A. $300 B. $500 C. $3, 000 D. $30, 000

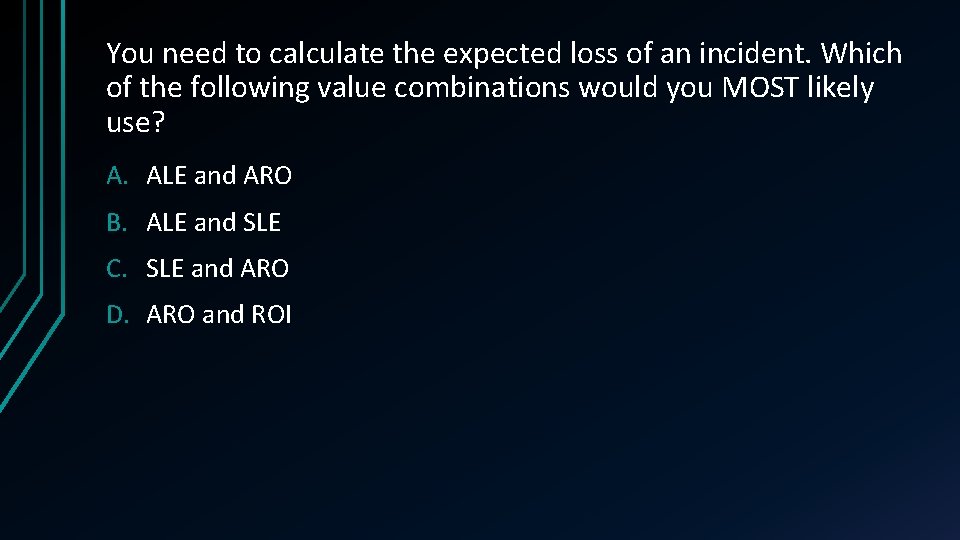
You need to calculate the expected loss of an incident. Which of the following value combinations would you MOST likely use? A. ALE and ARO B. ALE and SLE C. SLE and ARO D. ARO and ROI

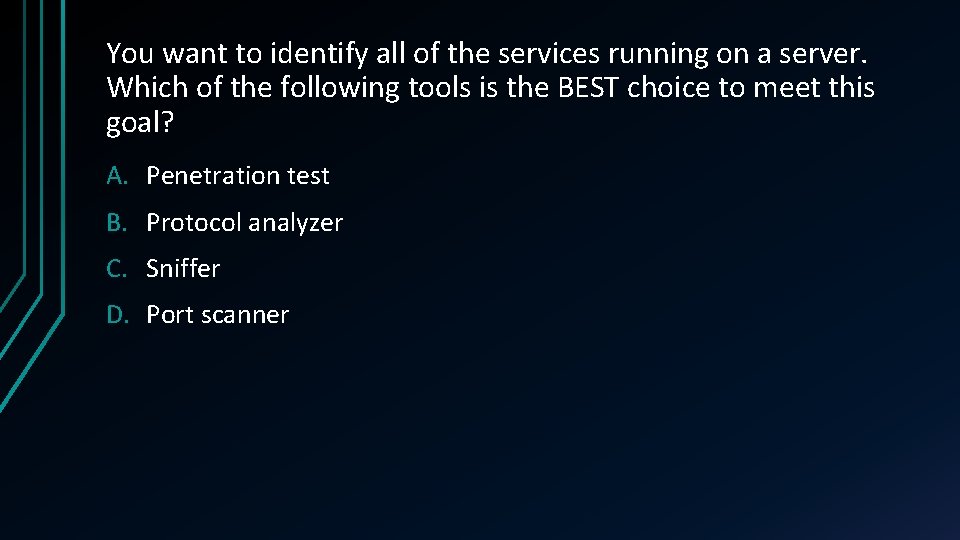
You want to identify all of the services running on a server. Which of the following tools is the BEST choice to meet this goal? A. Penetration test B. Protocol analyzer C. Sniffer D. Port scanner

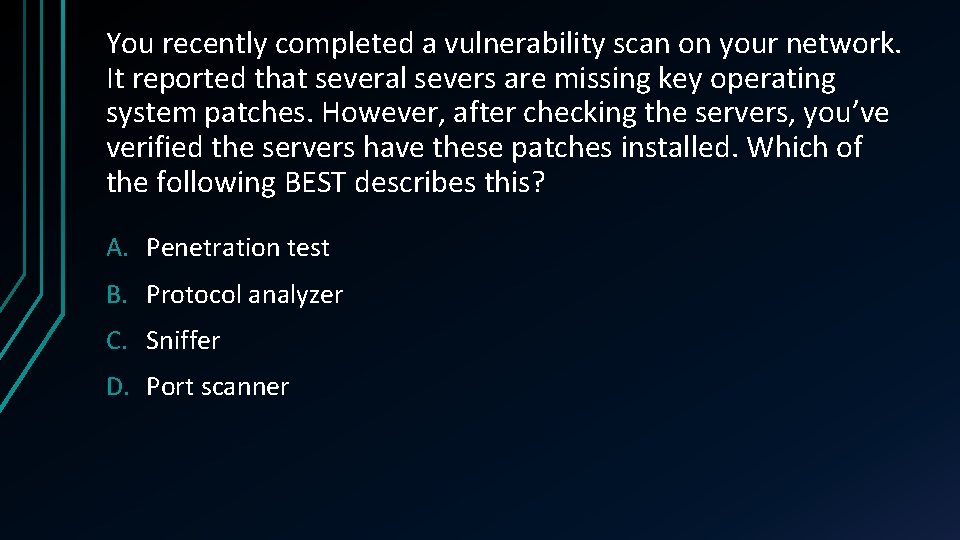
You recently completed a vulnerability scan on your network. It reported that several severs are missing key operating system patches. However, after checking the servers, you’ve verified the servers have these patches installed. Which of the following BEST describes this? A. Penetration test B. Protocol analyzer C. Sniffer D. Port scanner

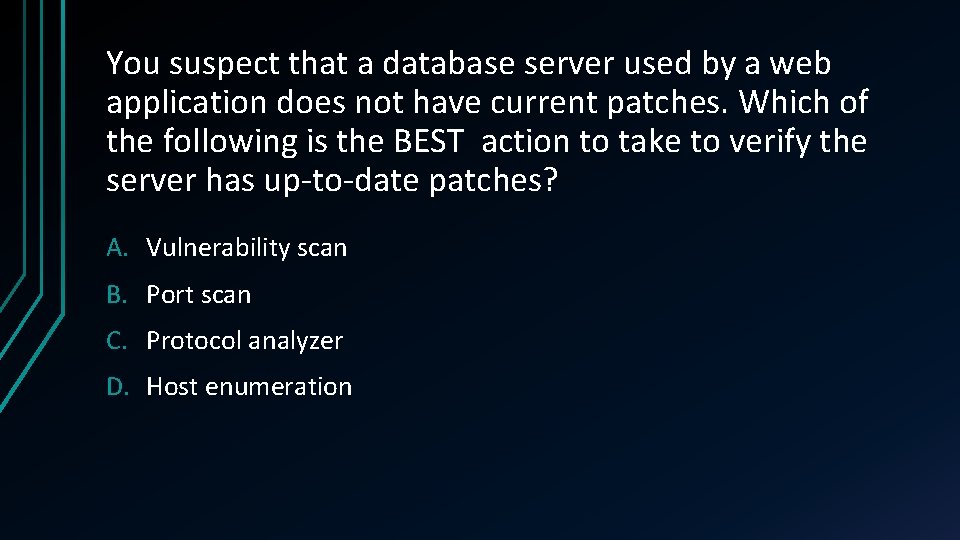
You suspect that a database server used by a web application does not have current patches. Which of the following is the BEST action to take to verify the server has up-to-date patches? A. Vulnerability scan B. Port scan C. Protocol analyzer D. Host enumeration

You need to perform test on your network to identify missing security controls. However, you want to have the least impact on systems that users are accessing. Which of the following tools is the best to meet this need? A. Code review B. Vulnerability scan C. Ping sweep D. Penetration test

Lisa needs to identify if a risk exists on a web application and if attackers can potentially bypass security controls. However, she should not actively test the application. Which of the following is the BEST choice? A. Perform a penetration test. B. Perform a port scan. C. Perform a vulnerability scan. D. Perform traffic analysis with a sniffer.

A recent vulnerability scan reported that a web application server is missing some patches. However, after inspecting the server, you realize that the patches are for a protocol that administrators removed from the server. Which of the following is the BEST explanation for this disparity? A. False negative B. False positive C. Lack of patch management tools D. The patch isn’t applied

Your organization develops web application software, which it sells to other companies for commercial use. Your organization wants to ensure that the software isn’t susceptible to common vulnerabilities, such as buffer overflow attacks and race conditions. What should the organization implement to ensure software meets this standard? A. Input validation B. Change management C. Code review D. Regression testing

Your organization has a legacy server within the DMZ. It is running older software that is not compatible with current patches, so it remains unpatched. Management accepts the risk on this system, but wants to know if attackers can access the internal network if they successfully compromise this server. Which of the following is the MOST appropriate? A. Vulnerability scan B. Port scan C. Code review D. Pentest

Testers do not have access to product documentation or any experience with an application. What type of test will they MOST likely perform? A. Gray box B. White box C. Black box D. Black hat

Your organization has hired a group of external testers to perform a black box penetration test. One of the testers asks you to provide information about your internal network. What should you provide? A. A list of IP ranges and the types of security devices operational on a network B. Network diagrams but without internal IP addresses C. Some network diagrams and some IP addresses, but not all D. Nothing

A network administrator is troubleshooting a communication problem between a web server and a database server. Which of the following tools would MOST likely by useful in this scenario? A. Protocol analyzer B. Port scanner C. Switch D. URL filter

A network administrator needs to identify the type of traffic and packet flags used in traffic sent from a specific IP address. Which of the following is the BEST tool to meet this need? A. UTM security appliance B. Router logs C. Protocol analyzer D. Vulnerability scan

While analyzing a packet capture log, you notice the following entry: 1612: 50, src 10. 80. 1, 5: 3389, dst 192. 168. 1. 100: 8080, syn/ack Of the following choices, what is the BEST explanation of the entry? A. An HTTP connection attempt B. An RDP connection attempt C. An FTP connection attempt D. A buffer overflow attack

Security administrators have recently implemented several security controls to enhance the network’s security posture. Management wants to ensure that these controls continue to function as intended Which of the following tools is the BEST choice to meet this goal? A. Routine audit B. Change management C. Design review D. Black box test

Your organization recently hired an outside security auditor to review internal processes. The auditor identified several employees who had permissions for previously held jobs within the company. What should the organization implement to prevent this in the future? A. Design reviews B. Code reviews C. Baseline review D. User rights and permission reviews

Your organization’s security policy states that administrators should follow the principle of least privilege. Which of the following tools can ensure that administrators are following the policy? A. User rights and permissions review B. Risk assessment C. Vulnerability assessment D. Threat assessment

Your organization wants to ensure that security controls continue to function, helping to maintain an appropriate security posture. Which of the following is the BEST choice to meet this goal? A. Auditing logs B. Routine audits C. Continuous security monitoring D. Vulnerability scans

You are configuring a fleet of Windows 7 laptops for traveling employees, some of whom prefer using USB mice. It is critical that the machines are as secure as possible. What should you configure? (Choose three. ) A. Disable USB ports. B. Require USB device encryption. C. Enable and configure the Windows firewall. D. Install and configure antivirus software. E. Enable a power management scheme.

Your intranet provides employees with the ability to search through an SQL database for their past travel expenses once that have logged in. One employee from the IT department discovers that if they enter an SQL string such as SELECT * FROM EXPENSES WHERE EMPID = ‘x’; it returns all employee travel expense records. What secure coding guideline was ignored? A. SQL injection prevention B. Input validation C. Disabling of SQL indexes D. User authentication

You are the founder of Acme Data Mining. The business focuses on retrieving relevant consumer habits from various sources, and that data is then sold to retailers. Because of the amount of data that must be processed, you must implement the fastest possible solution. Which type of technology should you implement? A. SQL B. No. SQL C. SATA D. No. SATA

You are conducting a risk analysis for a stock brokerage firm in Miami, Florida. What factors should you consider? (Choose two. ) A. Server downtime because of earthquakes B. Destruction of government regulation documentation because of file C. Server downtime because of power outages D. Customer invoicing data destroyed because of fire

You are responsible for completing an IT asset report for your company. All IT-related equipment and data must be identified and given a value. A. Asset identification B. Risk assessment C. Risk mitigation D. Threat analysis

You are identifying security threats to determine the likelihood of virus infection. Identify potential sources of infection. (Choose two. ) A. USB flash drives B. USB keyboard C. Smartcard D. Downloaded documentation from a business partner web site

During a risk analysis meeting you are asked to specify internal threats being considered. Choose which item is not considered an internal threat from the list that follows. A. Embezzlement B. Hackers breaking in through the firewall C. Employees using corporate assets for personal gain D. Users plugging in personal USB flash drives.

A client conveys their concern to your regarding malicious Internet users gaining access to corporate resources. What type of assessment would you perform to determine this likelihood? A. Threat assessment B. Risk analysis C. Asset identification D. Total cost of ownership

You are an IT consultant performing a risk analysis for a seafood company. The client is concerned with specific cooking and packaging techniques the company uses being disclosed to competitors. What type of security concern is this? A. Integrity B. Confidentiality C. Availability D. Authorization

After identifying internal and external threats, you must determine how these potential risks will affect business operations. What is this called? A. Risk analysis B. Fault tolerance C. Availability D. Impact analysis

When determining how best to mitigate risk, which items should you consider? (Choose two. ) A. Insurance coverage B. Number of server hard disks C. How fast CPUs in new computers will be D. Network bandwidth

You are listing preventative measures for potential risks. Which of the following would you document? (Choose three. ) A. Larger flat-screen monitors B. Data backup C. Employee training D. Comparing reliability of network load balancing appliances

An insurance company charges an additional $200 monthly premium for natural disaster coverage for your business site. What figure must you compare this against to determine whether to accept this additional coverage? A. ALE B. ROI C. Total cost of ownership D. Total monthly insurance premium

Which of the following is true regarding qualitative risk analysis? A. Only numerical data is considered. B. ALE must be calculated. C. Threats must be identified. D. ROI must be calculated.

Which values must be calculated to derive annual loss expectancy? (Choose two. ) A. Single loss expectancy B. Annual rate of occurrence C. Monthly loss of expectancy D. Quarterly loss expectancy

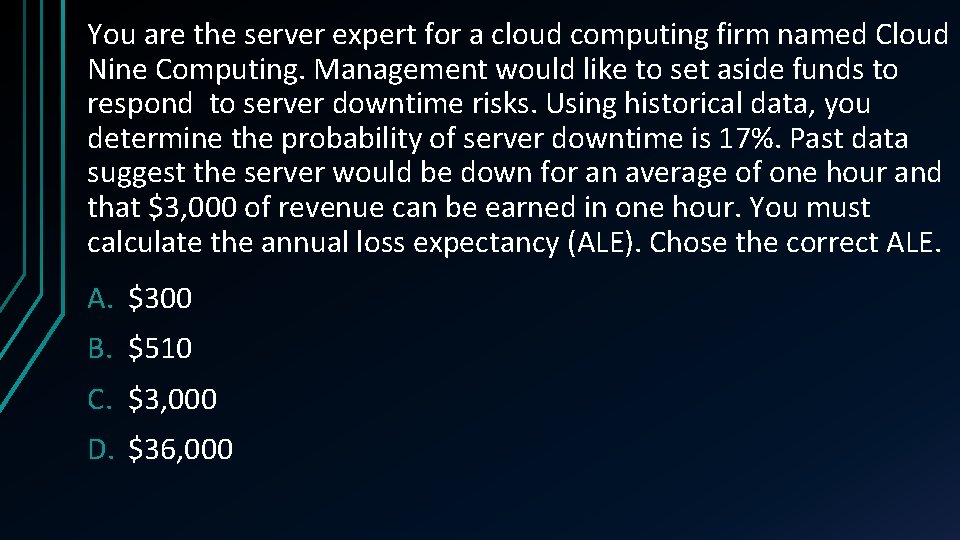
You are the server expert for a cloud computing firm named Cloud Nine Computing. Management would like to set aside funds to respond to server downtime risks. Using historical data, you determine the probability of server downtime is 17%. Past data suggest the server would be down for an average of one hour and that $3, 000 of revenue can be earned in one hour. You must calculate the annual loss expectancy (ALE). Chose the correct ALE. A. $300 B. $510 C. $3, 000 D. $36, 000

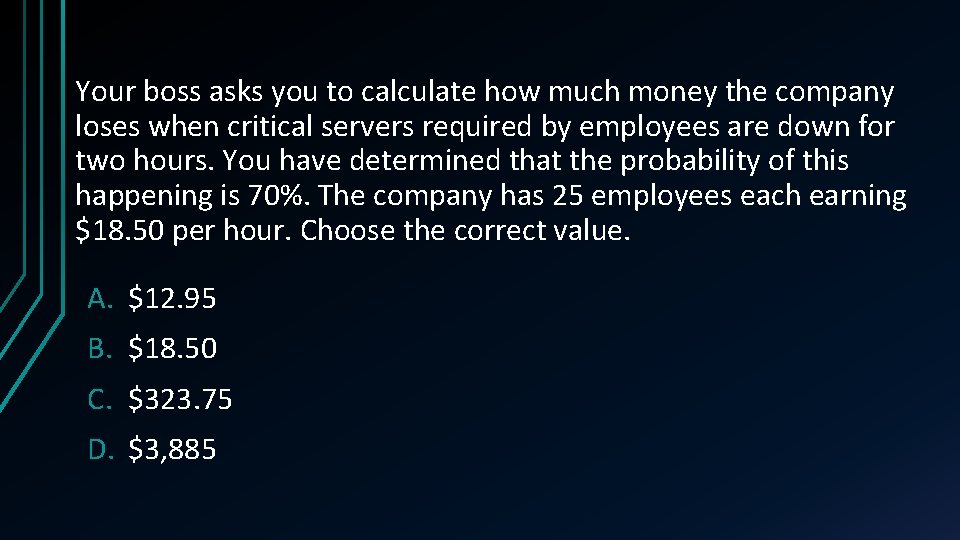
Your boss asks you to calculate how much money the company loses when critical servers required by employees are down for two hours. You have determined that the probability of this happening is 70%. The company has 25 employees each earning $18. 50 per hour. Choose the correct value. A. $12. 95 B. $18. 50 C. $323. 75 D. $3, 885

Your company is considering having the e-mail server hosted by Hosted Solutions, Inc. , to reduce hardware and mail server technician costs at the local site. What type of document formally states the reliability and recourse of the reliability is not met? A. BPA – Business Partners Agreement B. MOU – Memorandum of Understanding C. SLA – Service Level Agreement D. ISA – Interconnection Security Agreement

Which term best describes monies spent to minimize the impact that threats and unfavorable conditions have on a business? A. Risk management B. Security audit C. Budgetary constraints D. Impact analysis

Which risk analysis approach makes use of ALE? A. Best possible outcome B. Quantitative C. ROI D. Qualitative

You are presenting data at a risk analysis meeting. During your presentation you display a list of ALE values sorted ranked by dollar amount. Bob, a meeting participant, asks how reliable the numeracy used to calculate the ALE is. What can you tell Bob? A. The numbers are 100 percent reliable. B. The numbers are 50 percent reliable. C. ALEs are calculated using probability values that vary. D. ALEs are calculated using percentages and are accurate.

Which of the following should be performed when conducting a qualitative risk assessment? (Choose two. ) A. Asset valuation B. ARO C. SLE D. Ranking of potential threats

You are the IT security analyst for Big John’s Gourmet Foods. Big John’s plans to open a plant in Oranjestad, Aruba next year. You are meeting with a planning committee in the next week and must come up with questions to ask the committee about the new location so you can prepare a risk analysis report. Which of the following would be the most relevant questions to ask? (Choose two. ) A. How hot does it get in the summer? B. How reliable is the local power? C. What kind of physical premise security is in place? D. How close is the nearest highway?

Your corporate web site is being hosted by an Internet service provider. How does this apply to the concept of risk? A. Risk avoidance B. Risk transference C. Risk analysis D. Increase in ALE

Which of the following regarding risk management is true? A. Funds invested in risk management could have earned much more profit it spent elsewhere. B. ALEs are only estimates and are subject to being inaccurate. C. IT security risks are all handled by the corporate firewall. D. Qualitative risk analysis results are expressed in dollar amounts.

Your competitors are offering a new product that is predicted to sell well. After much careful study, your company has decided against launching a competing product because of the uncertainty of the market and the enormous investment required. Which term best describes your company’s decision? A. Risk analysis B. Risk transfer C. Risk avoidance D. Product avoidance

How can management determine which risks should be given the most attention? A. Threat vector B. Rank risks by likelihood C. Ranks risks by probable date of occurrence D. Rank risks by SLE

Which factors could influence your risk management strategy? A. B. C. D. E. Government regulations Moving operations to a new building The purchase of a newer firewall solution None of the above All the above

Identify the two drawbacks to quantitative risk analysis compared to qualitative risk analysis. (Choose two. ) A. Quantitative risk analysis entails complex calculations. B. Risks are not prioritized by monetary value. C. Quantitative analysis is more time-consuming than qualitative. D. It is difficult to determine how much money to allocate to reduce a risk.

What is the difference between risk assessment and risk management? A. They are the same thing. B. Risk assessment identifies and prioritizes risks; risk management is the governing of risks to minimize their impact. C. Risk management identifies and prioritizes risks; risk assessment is the governing of risks to minimize their impact D. Risk assessment identifies threats; risk management controls those threats.

Title and Content Layout with Chart Series 1 Series 2 Series 3 6 5 4 3 2 1 0 Category 1 Category 2 Category 3 Category 4

Two Content Layout with Table • First bullet point here Group 1 Group 2 • Second bullet point here Class 1 82 95 • Third bullet point here Class 2 76 88 Class 3 84 90

Two Content Layout with Smart. Art • First bullet point here • Second bullet point here Task 1 • Third bullet point here Task 2 Task 3






 Flat shape with eight sides
Flat shape with eight sides A short section of corrugated roadway that warns of hazards
A short section of corrugated roadway that warns of hazards Market risk credit risk operational risk
Market risk credit risk operational risk Chapter 1 managing risk when driving
Chapter 1 managing risk when driving Chapter 5 managing risk with the ipde process
Chapter 5 managing risk with the ipde process Write the terms associated with ipde process
Write the terms associated with ipde process Managing risk with the ipde process
Managing risk with the ipde process Orderly visual search pattern
Orderly visual search pattern Orderly visual search pattern
Orderly visual search pattern Chapter 7 managing risk vision and perception
Chapter 7 managing risk vision and perception Criminogenico
Criminogenico Central eight risk factors
Central eight risk factors Central eight risk factors
Central eight risk factors What are the eight steps to following a recipe correctly
What are the eight steps to following a recipe correctly What are the eight steps to following a recipe correctly
What are the eight steps to following a recipe correctly Managing clinical risk
Managing clinical risk Module 4 topic 1 assessing and managing risk
Module 4 topic 1 assessing and managing risk Module 4 topic 1 assessing and managing risk
Module 4 topic 1 assessing and managing risk Module 7 managing risk answer key
Module 7 managing risk answer key Identifying and managing project risk tom kendrick
Identifying and managing project risk tom kendrick Lending policies and procedures managing credit risk
Lending policies and procedures managing credit risk Managing clinical risk
Managing clinical risk Managing property and liability risk
Managing property and liability risk Measuring and managing credit risk
Measuring and managing credit risk Loss event category
Loss event category Prism with 12 vertices
Prism with 12 vertices Chapter 8 the great gatsby summary
Chapter 8 the great gatsby summary Lord of the flies zusammenfassung
Lord of the flies zusammenfassung Draw rmmm plan
Draw rmmm plan Risk avoidance insurance
Risk avoidance insurance Relative risk calculation
Relative risk calculation Residual risk and secondary risk pmp
Residual risk and secondary risk pmp Ar = ir x cr x dr
Ar = ir x cr x dr Absolute risk vs relative risk
Absolute risk vs relative risk Thinking algebraically stock market game answer key
Thinking algebraically stock market game answer key Firm risk scorecard
Firm risk scorecard Pembiayaan risiko (risk financing)
Pembiayaan risiko (risk financing) The biggest risk is not taking any risk
The biggest risk is not taking any risk Key risk indicators template
Key risk indicators template Business risk vs audit risk
Business risk vs audit risk Business risk vs financial risk capital structure
Business risk vs financial risk capital structure Attributable risk formula
Attributable risk formula Risk map risk management
Risk map risk management Parirt
Parirt Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Frameset trong html5
Frameset trong html5 Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Glasgow thang điểm
Glasgow thang điểm Hát lên người ơi alleluia
Hát lên người ơi alleluia Các môn thể thao bắt đầu bằng tiếng bóng
Các môn thể thao bắt đầu bằng tiếng bóng Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính thế năng
Công thức tính thế năng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư anh em như thể tay chân
Mật thư anh em như thể tay chân 101012 bằng
101012 bằng Phản ứng thế ankan
Phản ứng thế ankan Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thể thơ truyền thống
Thể thơ truyền thống