CHAPTER 9 OPERATING SYSTEM PROTECTION AND SECURITY LEARNING









- Slides: 20

CHAPTER 9 OPERATING SYSTEM: PROTECTION AND SECURITY

LEARNING OBJECTIVES Focus on various part of the operating system can achieve the security and protection according to the organization’s requirement. External and internal security. Security threat such as virus, malware and worms. Security issues and its approach implementation. LEARNING OUTCOMES l Students knows the security and protection related in computing environment. l. The importance of security and protection for all operating system l. Various type of security threats

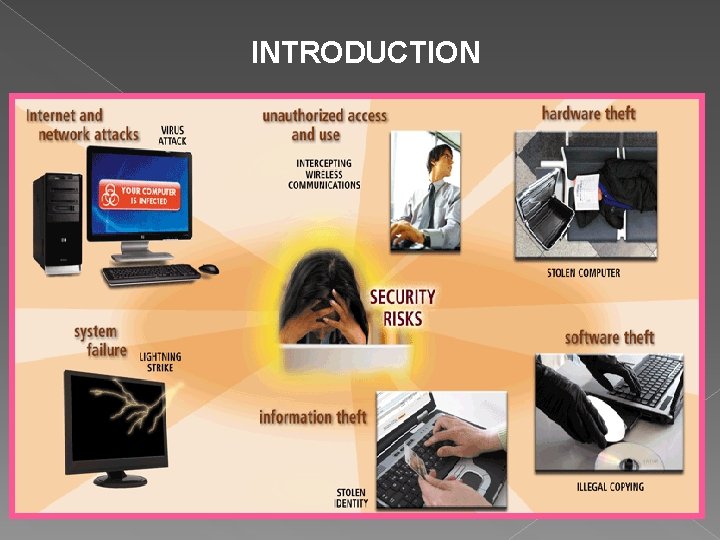
INTRODUCTION

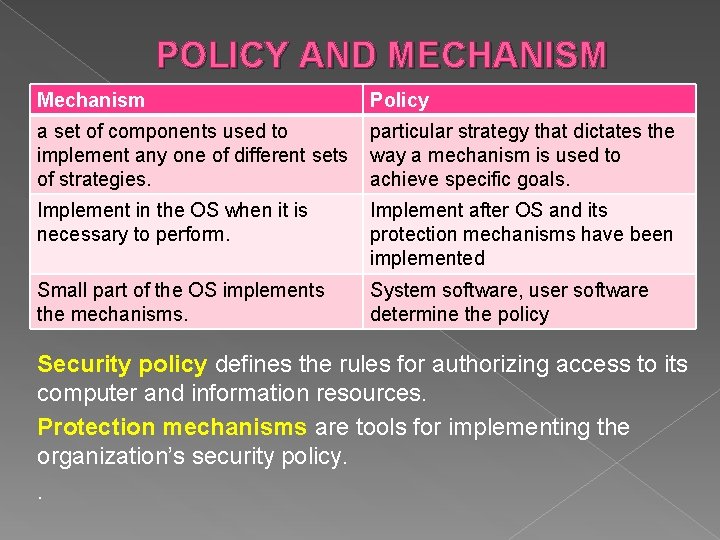
POLICY AND MECHANISM Mechanism Policy a set of components used to implement any one of different sets of strategies. particular strategy that dictates the way a mechanism is used to achieve specific goals. Implement in the OS when it is necessary to perform. Implement after OS and its protection mechanisms have been implemented Small part of the OS implements the mechanisms. System software, user software determine the policy Security policy defines the rules for authorizing access to its computer and information resources. Protection mechanisms are tools for implementing the organization’s security policy. .

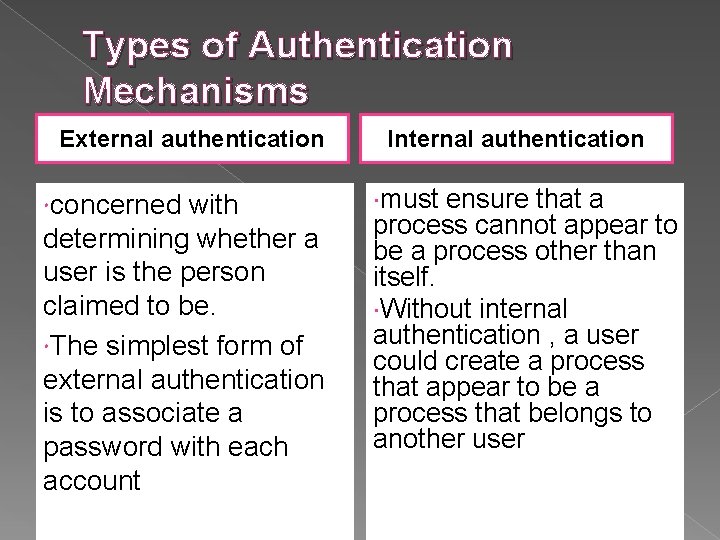
Types of Authentication Mechanisms External authentication concerned with determining whether a user is the person claimed to be. The simplest form of external authentication is to associate a password with each account Internal authentication must ensure that a process cannot appear to be a process other than itself. Without internal authentication , a user could create a process that appear to be a process that belongs to another user

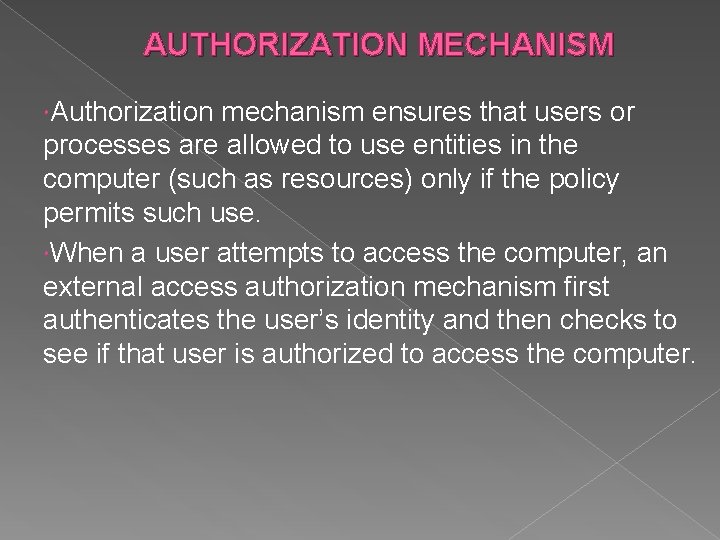
AUTHORIZATION MECHANISM Authorization mechanism ensures that users or processes are allowed to use entities in the computer (such as resources) only if the policy permits such use. When a user attempts to access the computer, an external access authorization mechanism first authenticates the user’s identity and then checks to see if that user is authorized to access the computer.

Authentication systems provide an answer to the questions: › Who is the user? › Is the user really who she/he represents himself to be? Authorization system provide answer to the questions: › Is user X authorized to access resource R? Authentication and authorization are somewhat tightly – coupled mechanism authorization system depends on secure authentication system.

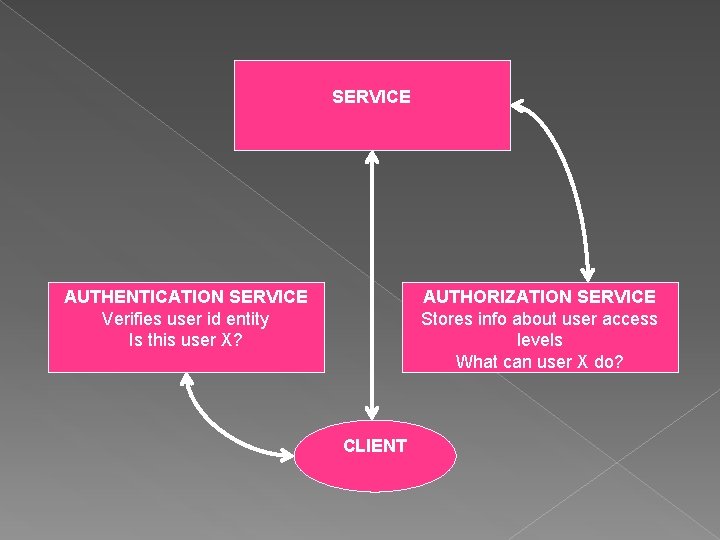
SERVICE AUTHENTICATION SERVICE Verifies user id entity Is this user X? AUTHORIZATION SERVICE Stores info about user access levels What can user X do? CLIENT

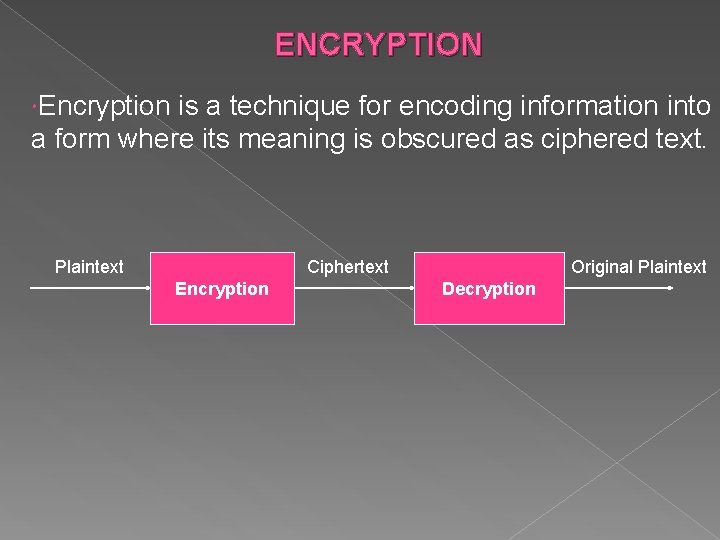
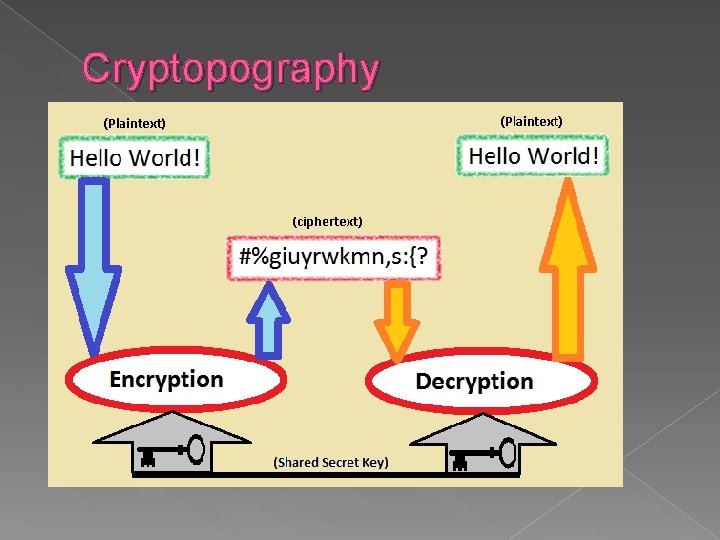
ENCRYPTION Encryption is a technique for encoding information into a form where its meaning is obscured as ciphered text. Plaintext Ciphertext Encryption Original Plaintext Decryption

ENCRYPTION

USER AUTHENTICATION The OS is the software agent with which users interact when they initiate a session with the system. The OS needs to verify that users are who they claim to be. The combination of user identification and password is widely used in operating systems for user identification. Contemporary protection systems may even resort to methods such as fingerprint or eye scan identification.

AUTHENTICATION IN NETWORKS Today network authentication mechanism are especially necessary to detect incoming files that may contain a virus or a worm. A virus is a software module hidden inside another module. Established in a file system by replacing some existing module as a bug fix or as an upgrade. A worm is an active penetrating entity, may enter the machine as file, but then will begin execution on its own. Once a file containing a worm has been placed in the file system, the worm finds a loophole in the process manager in order to execute itself


INTERNAL ACCESS AUTHORIZATION Sharing parameters: A process’s resources policy may be violated if other processes can indiscriminately change parameter values within its address space. Confinement: confinement is a generalization of the problem of sharing parameters. Limit the distribution of info to others. Allocating rights: a protection system may allow a process to provide another process with specific rights to use its resources. Trojan horse: the Trojan horse problem is a special case of the problem of allocating rights – a service program being used by a client process using its own right.

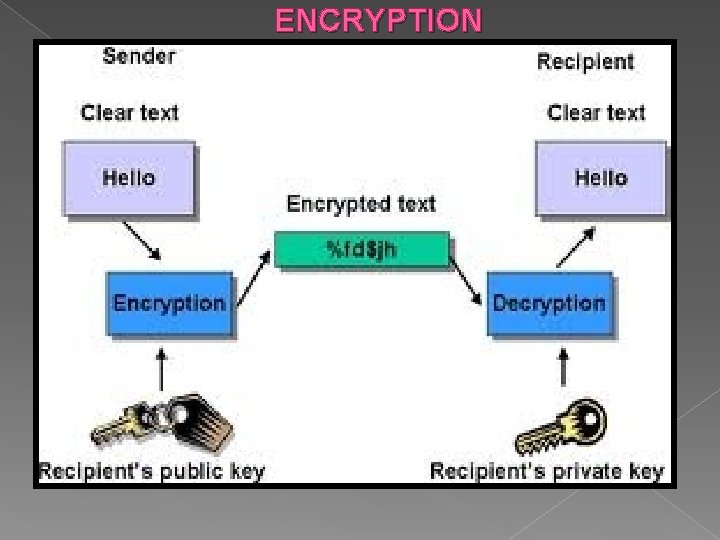
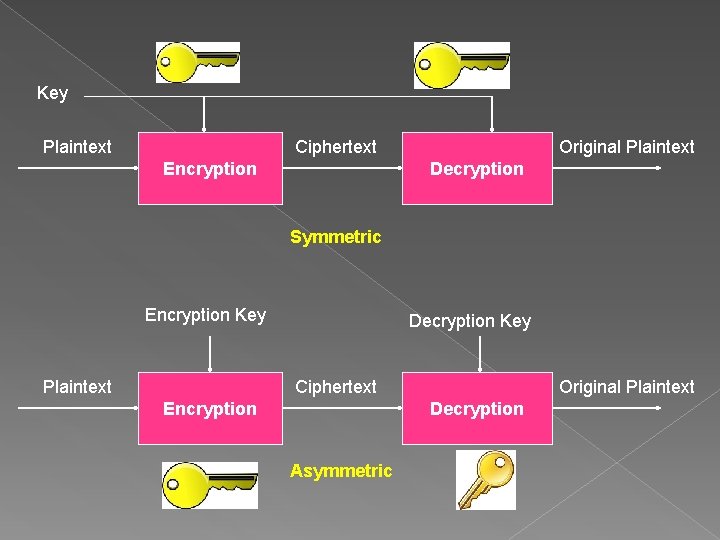
CRYPTOGRAPHY Cryptography techniques can be used to convert clear text (or plain text) to ciphered text to protect the text whenever it is exposed on an unprotected medium. There is a class of symmetric encryption technique in which the encryption key is the same as the decryption key. Asymmetric encryption and decryption are required in cases in which different subjects perform the encryption and decryption.

Key Plaintext Ciphertext Encryption Original Plaintext Decryption Symmetric Encryption Key Plaintext Decryption Key Ciphertext Encryption Original Plaintext Decryption Asymmetric

Cryptopography

Nov 2011 1. Which of these description below is TRUE for the following function: Encrypt(key, clear. Text) = clear. Text Encodes the clear text into ciphertext B. Decrypt the clear text into ciphertext C. Encodes to translate the ciphertext back into clear text D. Decrypt to translate the ciphertext back into clear text A.

2. The _____ is a generalization of the problem of sharing parameters. 3. Security policy defines the rules for authorizing access to its computer and information resources. Differentiate between Mechanisms and Policy(2 m). 4. Describe 2 types of Authentication Mechanisms(4 m). 5. Internal authorization is part of the task of managing resource sharing. List 4 internal access authorization mechanisms. (4 m)

April 2009/nov 2010 6. Briefly explain each term given below: Policy(2 m) Protection Mechanism(2 m) Encryption(2 m) Security policy(2 m) 7. Differentiate between authentication and authorization(4 m). 8. State the differentiate between computer virus and worm