Chapter 9 Intermediate TCPIP Access Control Lists ACLs






























- Slides: 34

Chapter 9 Intermediate TCP/IP/ Access Control Lists (ACLs) © 2004, Cisco Systems, Inc. All rights reserved. 1

Objectives © 2004, Cisco Systems, Inc. All rights reserved. 2

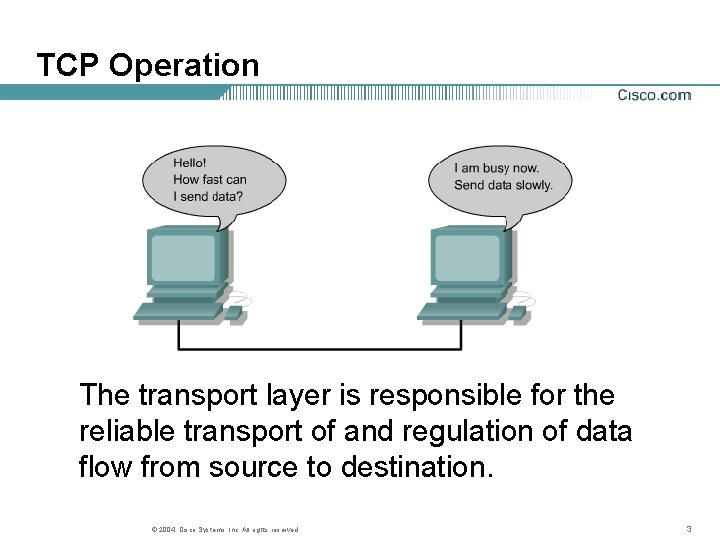
TCP Operation The transport layer is responsible for the reliable transport of and regulation of data flow from source to destination. © 2004, Cisco Systems, Inc. All rights reserved. 3

Synchronization or Three-Way Handshake © 2004, Cisco Systems, Inc. All rights reserved. 4

Denial-of-Service Attacks © 2004, Cisco Systems, Inc. All rights reserved. 5

Simple Windowing © 2004, Cisco Systems, Inc. All rights reserved. 6

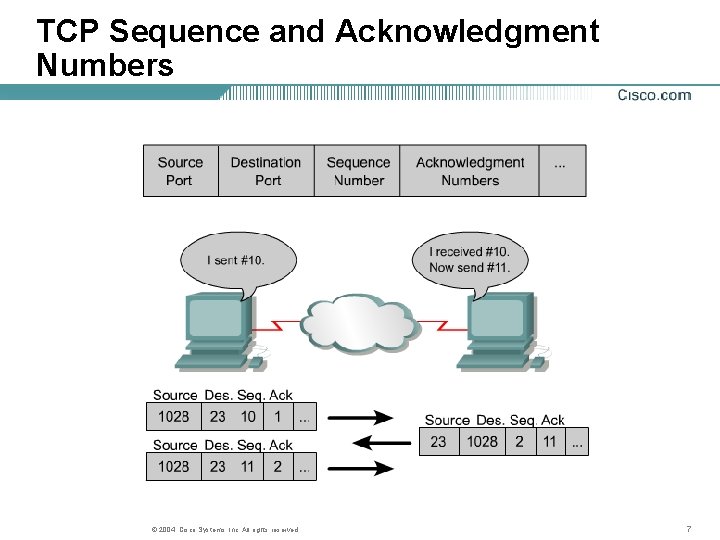
TCP Sequence and Acknowledgment Numbers © 2004, Cisco Systems, Inc. All rights reserved. 7

Positive ACK • Acknowledgement is a common step in the synchronization process which includes sliding windows and data sequencing. © 2004, Cisco Systems, Inc. All rights reserved. 8

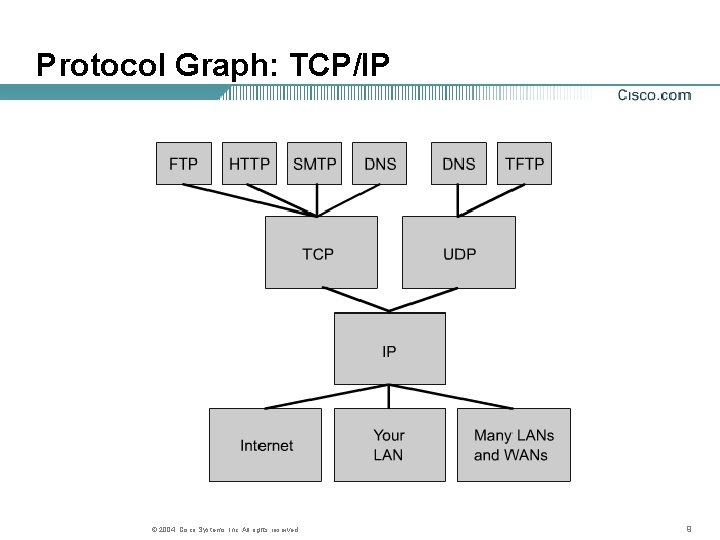
Protocol Graph: TCP/IP © 2004, Cisco Systems, Inc. All rights reserved. 9

UDP Segment Format © 2004, Cisco Systems, Inc. All rights reserved. 10

Port Numbers © 2004, Cisco Systems, Inc. All rights reserved. 11

Telnet Port Numbers © 2004, Cisco Systems, Inc. All rights reserved. 12

Reserved TCP and UDP Port Numbers © 2004, Cisco Systems, Inc. All rights reserved. 13

Ports for Clients • Whenever a client connects to a service on a server, a source and destination port must be specified. • TCP and UDP segments contain fields for source and destination ports. © 2004, Cisco Systems, Inc. All rights reserved. 14

Port Numbering and Well-Known Port Numbers • Port numbers are divided into three different categories: well-known ports registered ports dynamic or private ports © 2004, Cisco Systems, Inc. All rights reserved. 15

Port Numbers and Socket © 2004, Cisco Systems, Inc. All rights reserved. 16

Comparison of MAC addresses, IP addresses, and port numbers • A good analogy can be made with a normal letter. • The name on the envelope would be equivalent to a port number, the street address is the MAC, and the city and state is the IP address. © 2004, Cisco Systems, Inc. All rights reserved. 17

Summary © 2004, Cisco Systems, Inc. All rights reserved. 18

Access Control Lists (ACLs) © 2004, Cisco Systems, Inc. All rights reserved. 19

Objectives © 2004, Cisco Systems, Inc. All rights reserved. 20

What are ACLs? • ACLs are lists of conditions used to test network traffic that tries to travel across a router interface. These lists tell the router what types of packets to accept or deny. © 2004, Cisco Systems, Inc. All rights reserved. 21

How ACLs Work © 2004, Cisco Systems, Inc. All rights reserved. 22

Protocols with ACLs Specified by Numbers © 2004, Cisco Systems, Inc. All rights reserved. 23

Creating ACLs © 2004, Cisco Systems, Inc. All rights reserved. 24

The Function of a Wildcard Mask © 2004, Cisco Systems, Inc. All rights reserved. 25

Verifying ACLs • There are many show commands that will verify the content and placement of ACLs on the router. show ip interface show access-lists Show running-config © 2004, Cisco Systems, Inc. All rights reserved. 26

Standard ACLs © 2004, Cisco Systems, Inc. All rights reserved. 27

Extended ACLs © 2004, Cisco Systems, Inc. All rights reserved. 28

Named ACLs © 2004, Cisco Systems, Inc. All rights reserved. 29

Placing ACLs • Standard ACLs should be placed close to the destination. • Extended ACLs should be placed close to the source. © 2004, Cisco Systems, Inc. All rights reserved. 30

Firewalls A firewall is an architectural structure that exists between the user and the outside world to protect the internal network from intruders. © 2004, Cisco Systems, Inc. All rights reserved. 31

Restricting Virtual Terminal Access © 2004, Cisco Systems, Inc. All rights reserved. 32

Summary © 2004, Cisco Systems, Inc. All rights reserved. 33

Question/Answer © 2004, Cisco Systems, Inc. All rights reserved. 34