CHAPTER 7 STRENGTH OF ENCRYPTION PUBLIC KEY INFRASTRUCTURE

CHAPTER 7 STRENGTH OF ENCRYPTION & PUBLIC KEY INFRASTRUCTURE CISSP Study Guide BIS 4113/6113
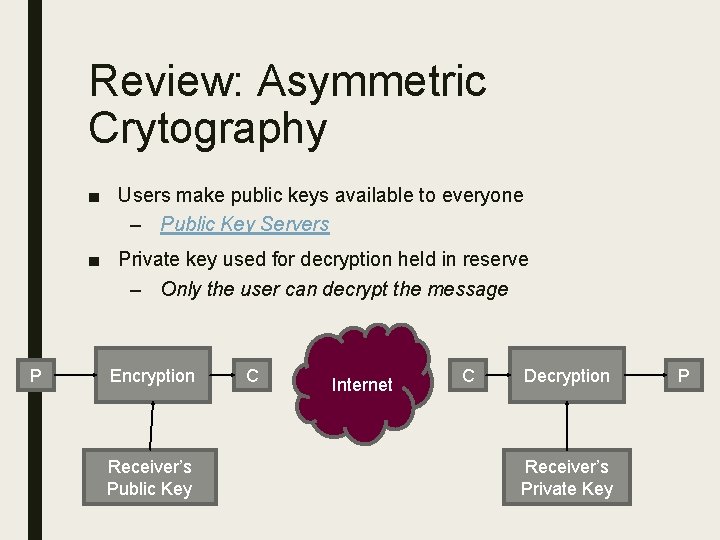
Review: Asymmetric Crytography ■ Users make public keys available to everyone – Public Key Servers ■ Private key used for decryption held in reserve – Only the user can decrypt the message P Encryption Receiver’s Public Key C Internet C Decryption Receiver’s Private Key P

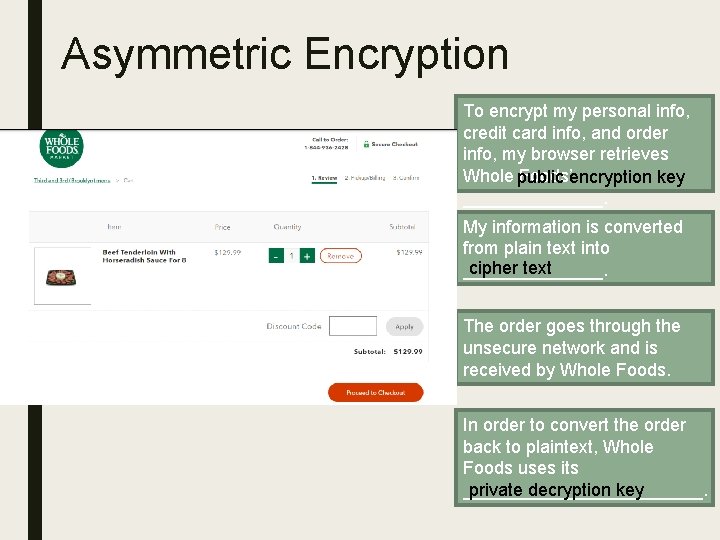
Asymmetric Encryption To encrypt my personal info, credit card info, and order info, my browser retrieves Whole public Foods’encryption key _______. My information is converted from plain text into cipher text _______. The order goes through the unsecure network and is received by Whole Foods. In order to convert the order back to plaintext, Whole Foods uses its private decryption key ____________.
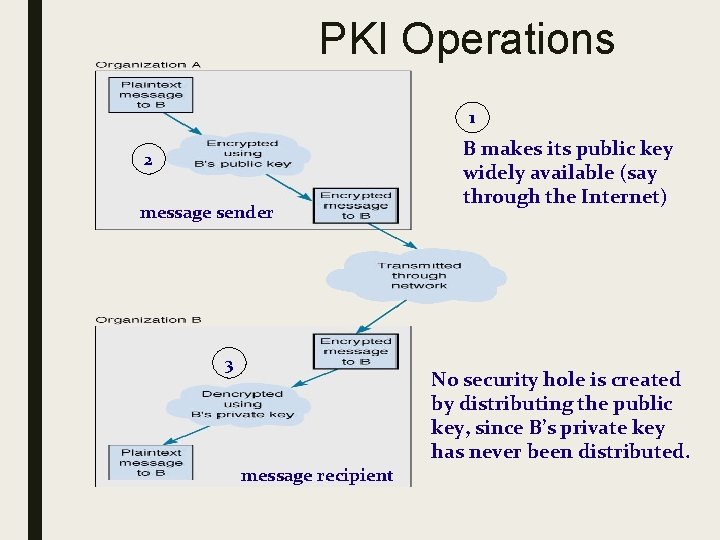
PKI Operations 1 2 message sender 3 B makes its public key widely available (say through the Internet) No security hole is created by distributing the public key, since B’s private key has never been distributed. message recipient
Message Source Authentication: Digital Signatures (p. 243) ■ Enforce non-repudiation ■ Ensure message integrity during transmission
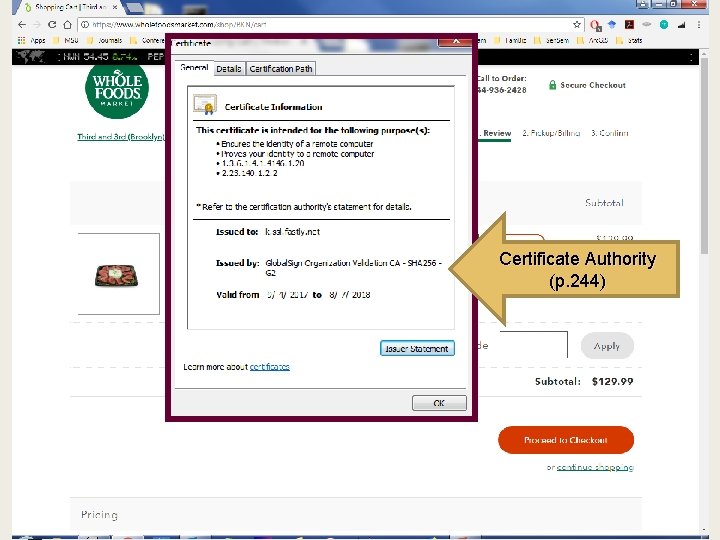
Certificate Authority (p. 244)
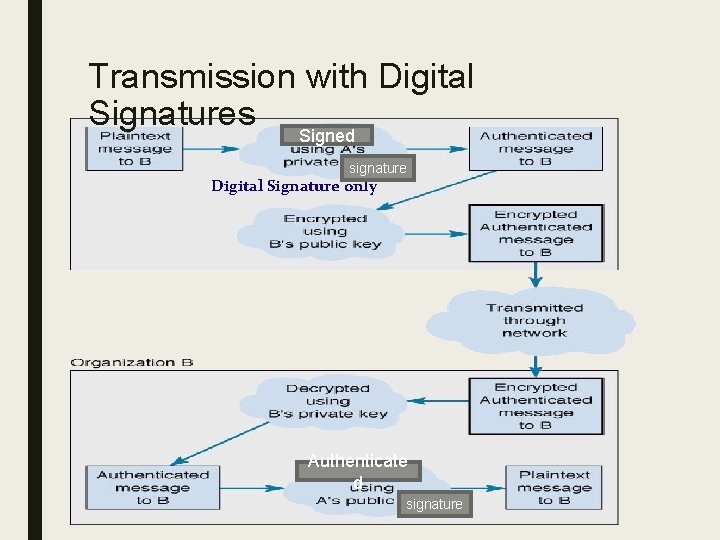
Transmission with Digital Signatures Signed signature Digital Signature only Authenticate d signature
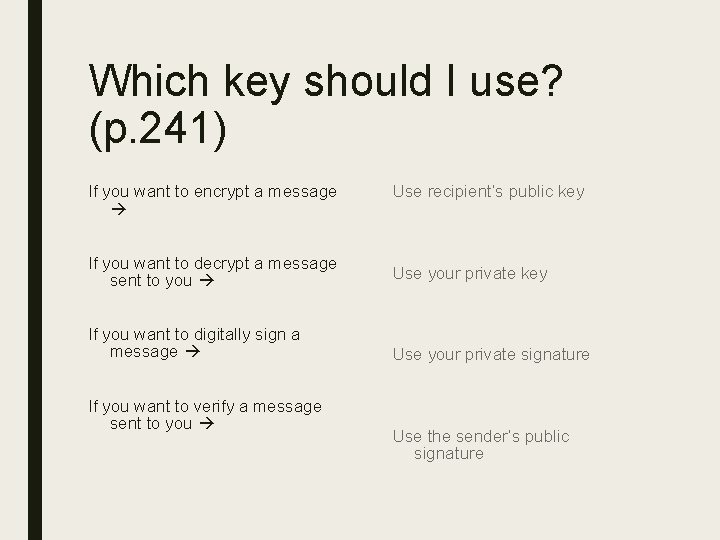
Which key should I use? (p. 241) If you want to encrypt a message Use recipient’s public key If you want to decrypt a message sent to you Use your private key If you want to digitally sign a message Use your private signature If you want to verify a message sent to you Use the sender’s public signature

RSA Encryption (p. 233 -234) Used by Microsoft, Nokia, Cisco, and 90% of Fortune 500 Works using “large” prime numbers Choose two: p and q 200 digits each n = p * q Select another number (e) e is less than n e is prime e and (n-1) * (q-1) have no common factors Select another number (d) (e*d – 1) mod ((p-1)(q-1)) = 0 e and n are public keys, d is private key (1088 bit) CT = PTE mod N PT = CTD mod N

Strength of Encryption ■ Key length (or key size) – Measured in bits – Key of n bits = 2 n possible keys – Algorithm cannot be larger than key size, but can be smaller ■ Encryption as a weapon? – Export Administration Regulations (EAR) – Limits: 64 bit symmetric, 768 bits asymmetric

Breaking encryption Brute force 56 bit encryption considered insufficient RSA Secret Key Challenge (1997) 56 bit key broken in 250 days It’s time to move to a longer key length 64 bit key broken in 5 years (1000 s of PCs) Some things are better left unread Distributed. net: Rc 5 -72 challenge Asymmetric key information in public key helps Keys with 128 bits are practically unbreakable SSL 128 -256 bits (next slides) Federal minimum for top secret info: 256 bits
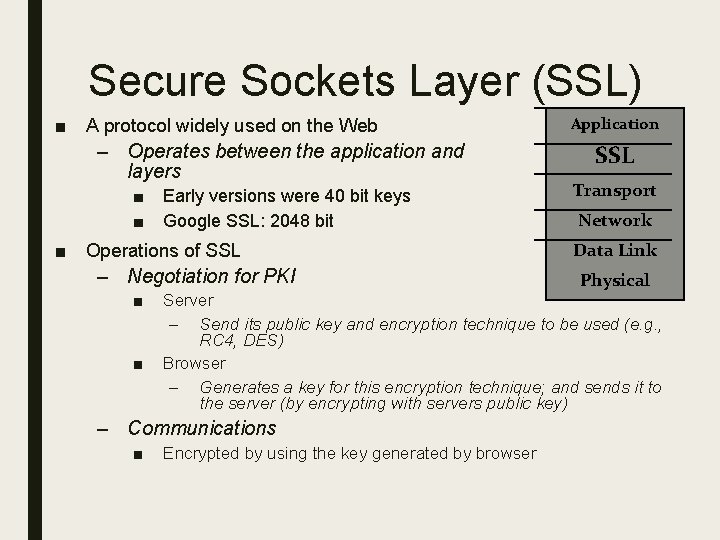
Secure Sockets Layer (SSL) ■ A protocol widely used on the Web – Operates between the application and layers ■ ■ Early versions were 40 bit keys Google SSL: 2048 bit ■ Operations of SSL – Negotiation for PKI ■ ■ transport SSL Transport Network Data Link Physical Server – Send its public key and encryption technique to be used (e. g. , RC 4, DES) Browser – Generates a key for this encryption technique; and sends it to the server (by encrypting with servers public key) – Communications ■ Application Encrypted by using the key generated by browser

Digital Rights Management (p. 252 -254) ■ Encryption used to enforce copyright standards for digital media – Music – Movie – E-books – Documents – Video games Steve Jobs’ open letter against DRM (2/6/2007) “The problem, of course, is that there are many smart people in the world, some with a lot of time on their hands, who love to discover such secrets and publish a way for everyone to get free (and stolen) music. They are often successful in doing just that, so any company trying to protect content using a DRM must frequently update it with new and harder to discover secrets. It is a cat -and-mouse game. ”
- Slides: 17