Chapter 7 Simple Date Types Dr Jiungyao Huang

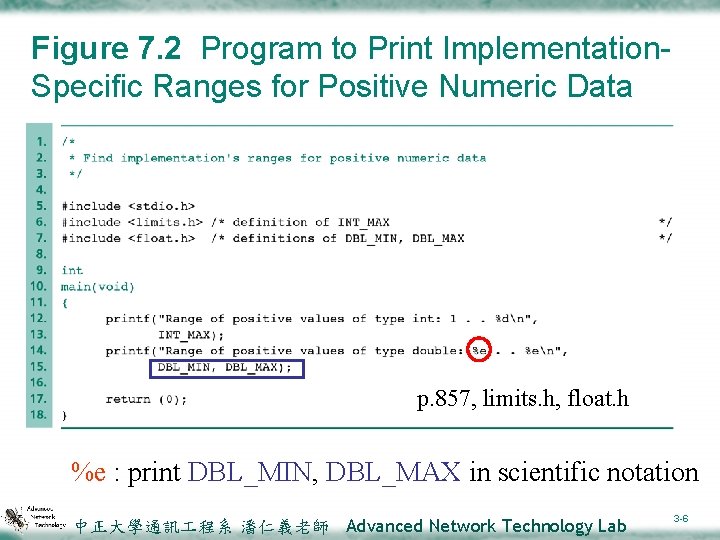



![Figure 7. 9 Three Possibilities That Arise When the Interval [xleft, xright] Is Bisected Figure 7. 9 Three Possibilities That Arise When the Interval [xleft, xright] Is Bisected](https://slidetodoc.com/presentation_image_h2/d13162d6a00006fb92bfb13a8952797f/image-32.jpg)


- Slides: 42

Chapter 7 Simple Date Types Dr. Jiung-yao Huang Dept. Comm. Eng. Nat. Chung Cheng Univ. E-mail : comjyh@ccu. edu. tw TA: 鄭筱親 陳昱豪

本章重點 v. Enumerated type v. Declaring a function parameter v. Bisection method 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -2

outline v 7. 1 REPRESENTATION AND CONVERSION OF NUMERIC TYPES v 7. 2 REPRESENTATION AND CONVERSION OF TYPE CHAR v 7. 3 ENUMERATED TYPES v 7. 4 ITERATIVE APPROXIMATIONS ²CASE STUDY: BISECTION METHOD FOR FINDING ROOTS v 7. 5 COMMON PROGRAMMING ERRORS 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -3

7. 1 Representation and Conversion of Numeric Types v. Simple data type ²A data type used to store a single value ²Uses a single memory cell to store a variable v. Different numeric types has different binary strings representation in memory 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -4

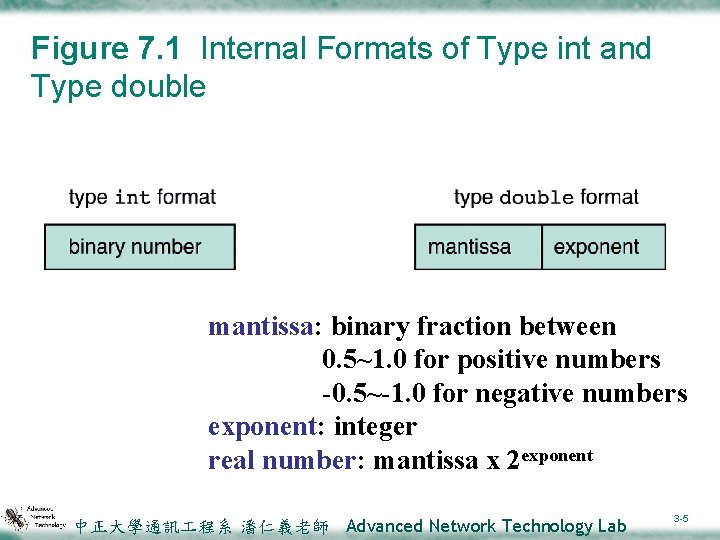
Figure 7. 1 Internal Formats of Type int and Type double mantissa: binary fraction between 0. 5~1. 0 for positive numbers -0. 5~-1. 0 for negative numbers exponent: integer real number: mantissa x 2 exponent 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -5

Figure 7. 2 Program to Print Implementation. Specific Ranges for Positive Numeric Data p. 857, limits. h, float. h %e : print DBL_MIN, DBL_MAX in scientific notation 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -6

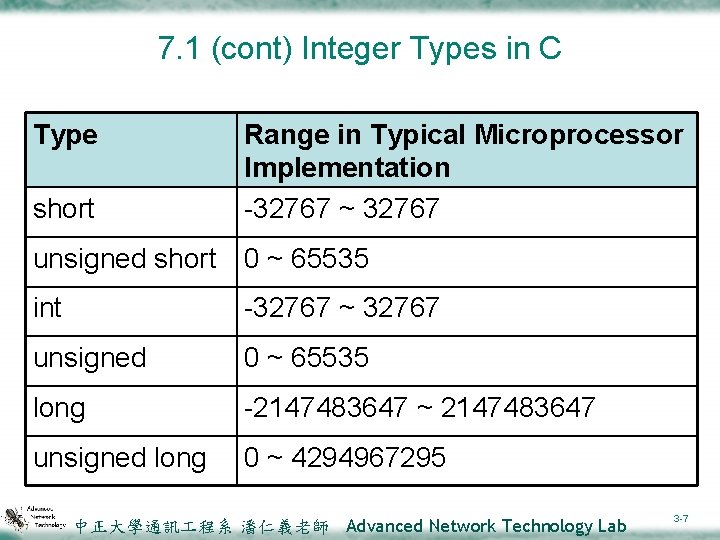
7. 1 (cont) Integer Types in C Type short Range in Typical Microprocessor Implementation -32767 ~ 32767 unsigned short 0 ~ 65535 int -32767 ~ 32767 unsigned 0 ~ 65535 long -2147483647 ~ 2147483647 unsigned long 0 ~ 4294967295 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -7

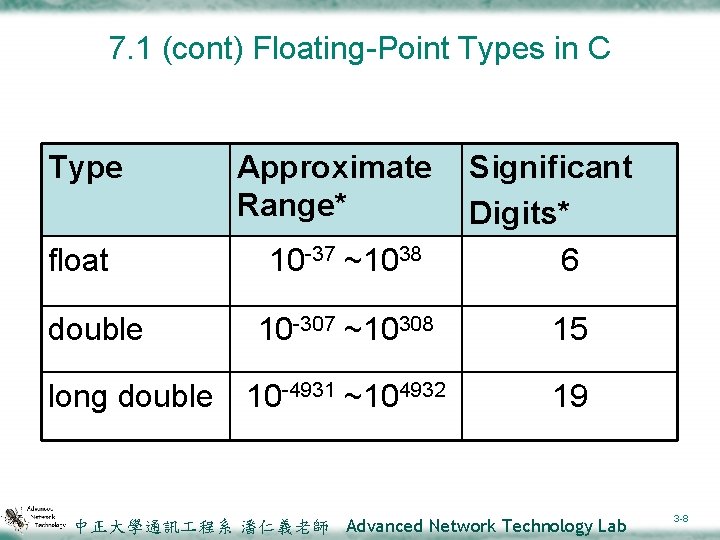
7. 1 (cont) Floating-Point Types in C Type float double long double Approximate Range* 10 -37 ~1038 Significant Digits* 6 10 -307 ~10308 15 10 -4931 ~104932 19 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -8

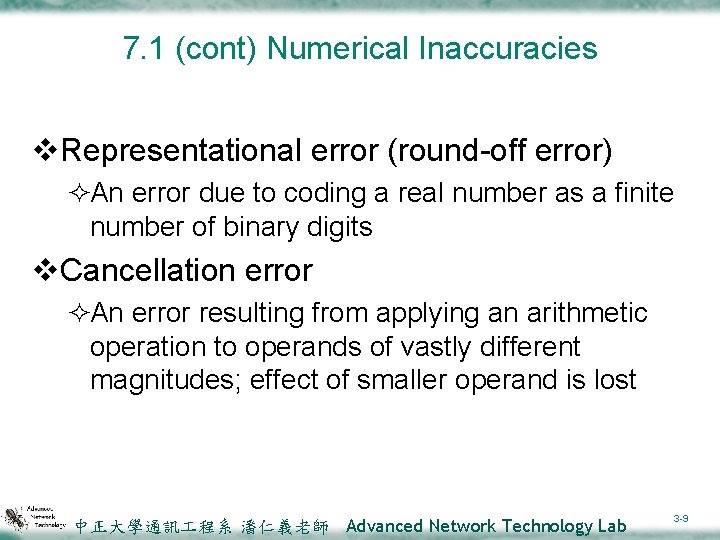
7. 1 (cont) Numerical Inaccuracies v. Representational error (round-off error) ²An error due to coding a real number as a finite number of binary digits v. Cancellation error ²An error resulting from applying an arithmetic operation to operands of vastly different magnitudes; effect of smaller operand is lost 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -9

7. 1 (cont) Numerical Inaccuracies v. Arithmetic underflow ²An error in which a very small computational result is represented as zero v. Arithmetic overflow ²An error that is an attempt to represent a computational result that is too large 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -10

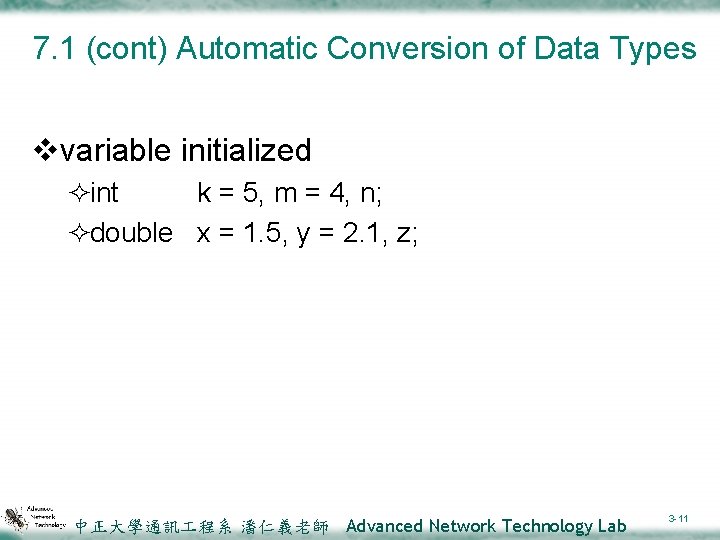
7. 1 (cont) Automatic Conversion of Data Types vvariable initialized ²int k = 5, m = 4, n; ²double x = 1. 5, y = 2. 1, z; 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -11

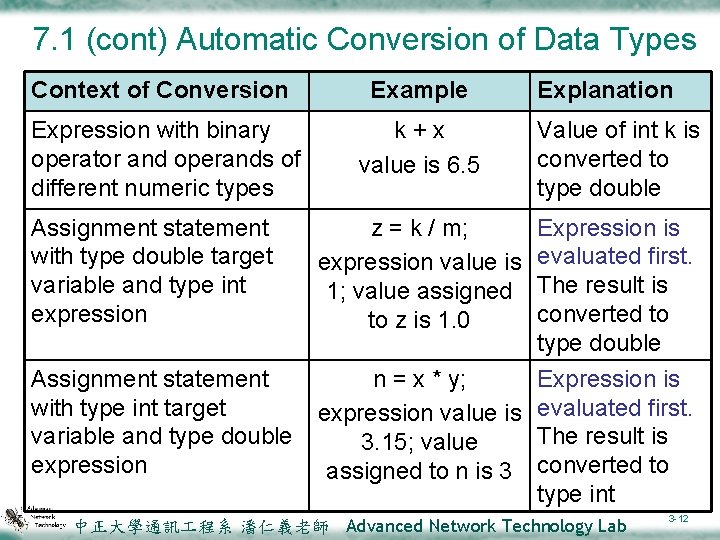
7. 1 (cont) Automatic Conversion of Data Types Context of Conversion Example Expression with binary operator and operands of different numeric types k+x value is 6. 5 Assignment statement with type double target variable and type int expression Assignment statement with type int target variable and type double expression Explanation Value of int k is converted to type double z = k / m; expression value is 1; value assigned to z is 1. 0 Expression is evaluated first. The result is converted to type double n = x * y; Expression is expression value is evaluated first. The result is 3. 15; value assigned to n is 3 converted to type int 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -12

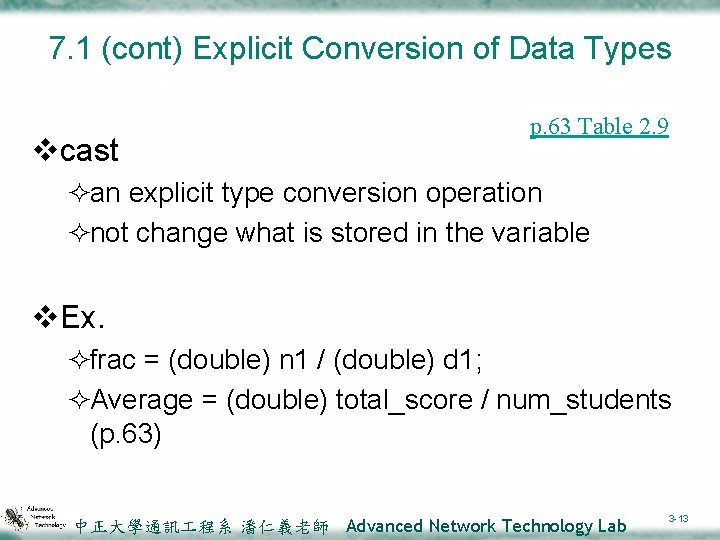
7. 1 (cont) Explicit Conversion of Data Types vcast p. 63 Table 2. 9 ²an explicit type conversion operation ²not change what is stored in the variable v. Ex. ²frac = (double) n 1 / (double) d 1; ²Average = (double) total_score / num_students (p. 63) 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -13

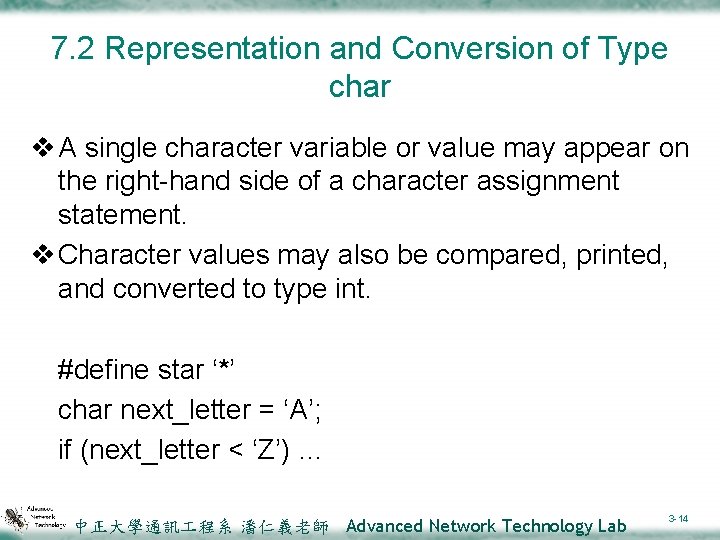
7. 2 Representation and Conversion of Type char v A single character variable or value may appear on the right-hand side of a character assignment statement. v Character values may also be compared, printed, and converted to type int. #define star ‘*’ char next_letter = ‘A’; if (next_letter < ‘Z’) … 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -14

7. 2 (cont) Three Common character codes (Appendix A) v. Digit character ²ASCII ‘ 0’ ~’ 9’ have code value 48~57 ²‘ 0’ < ‘ 1’ < ‘ 2’……. < ‘ 9’ v. Uppercase letters ²ASCII ‘A’~’Z’ have code values 65~90 ²‘A’ < ‘B’ < ‘C’……< ‘Z’ v. Lowercase letters ²ASCII ‘a’~’z’ have code values 97~122 ²‘a’ < ‘b’ < ‘c’……. < ‘z’ 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -15

7. 2 (cont) Example 7. 1 vcollating sequence ²A sequence of characters arranged by character code number v. Fig. 7. 3 uses explicit conversion of type int to type char to print part of C collating sequence 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -16

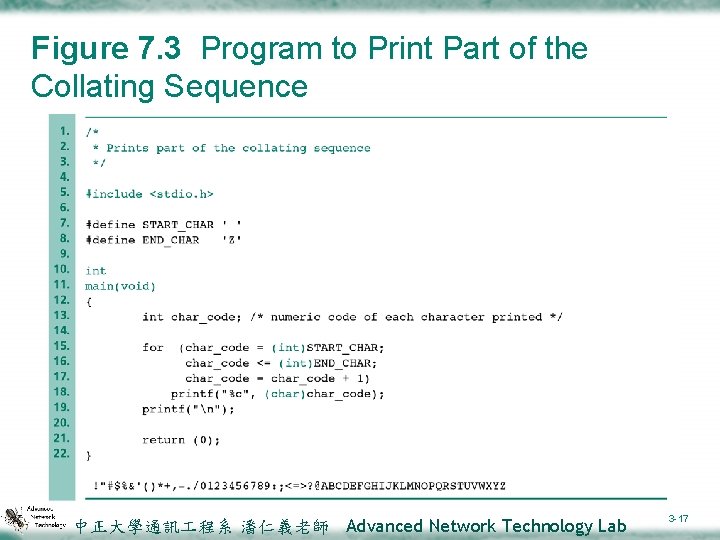
Figure 7. 3 Program to Print Part of the Collating Sequence 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -17

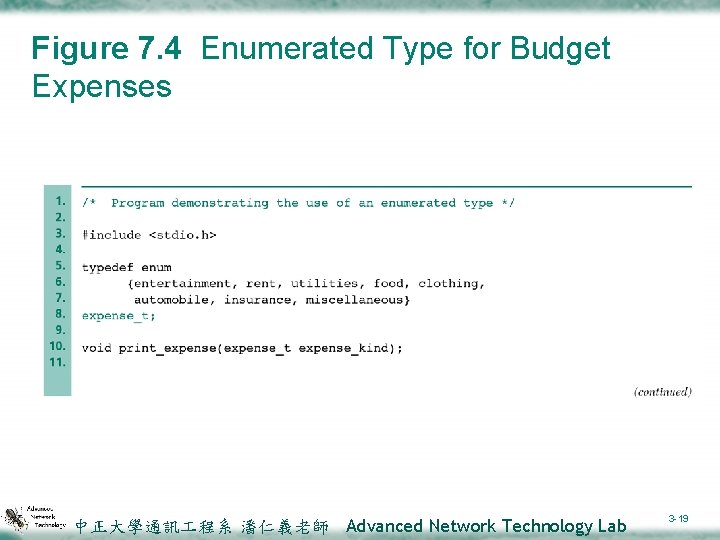
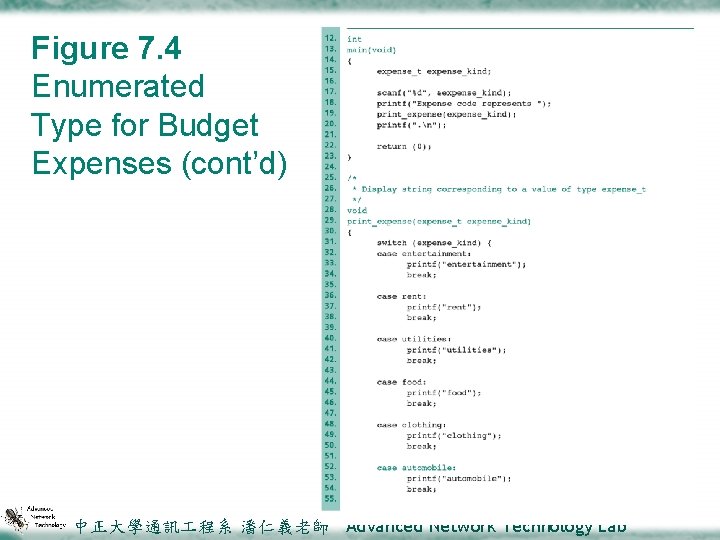
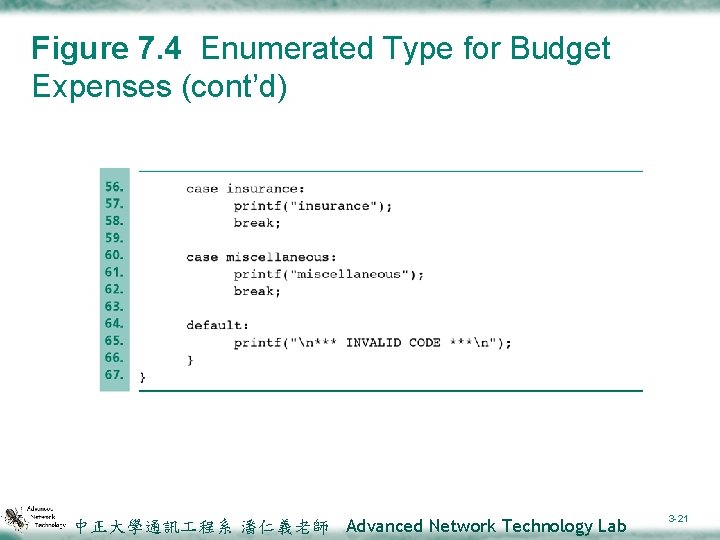
7. 3 Enumerated Types v. Enumerated type ²A data type whose list of values is specified by the programmer in a type declaration v. Enumeration constant ²An identifier that is one of the values of an enumerated type v. Fig. 7. 4 shows a program that scans an integer representing an expense code and calls a function that uses a switch statement to display the code meaning. 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -18

Figure 7. 4 Enumerated Type for Budget Expenses 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -19

Figure 7. 4 Enumerated Type for Budget Expenses (cont’d) 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -20

Figure 7. 4 Enumerated Type for Budget Expenses (cont’d) 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -21

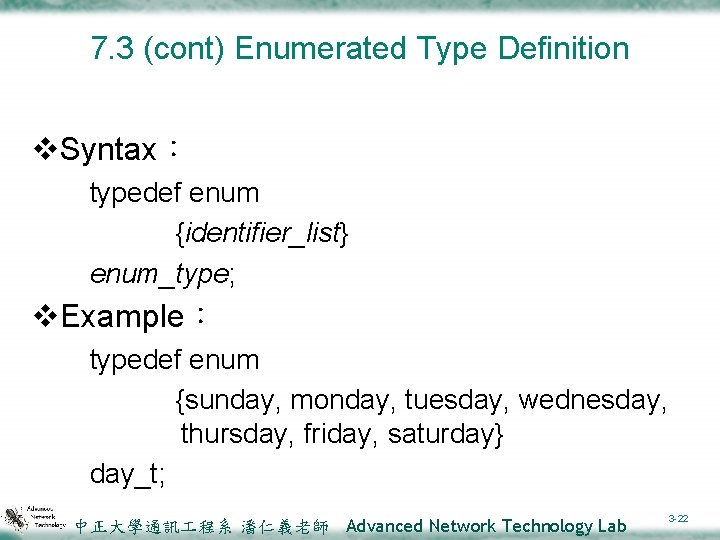
7. 3 (cont) Enumerated Type Definition v. Syntax: typedef enum {identifier_list} enum_type; v. Example: typedef enum {sunday, monday, tuesday, wednesday, thursday, friday, saturday} day_t; 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -22

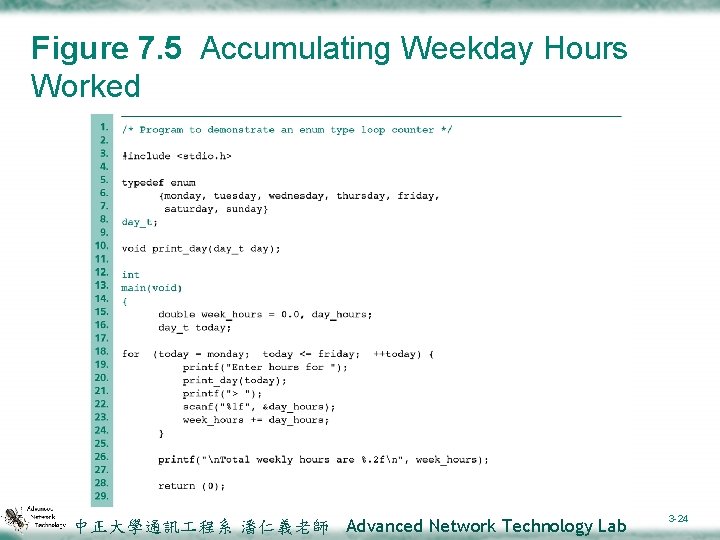
7. 3 (cont) Example 7. 3 v. The for loop in Fig. 7. 5 scans the hours worked each weekday for an employee and accumulates the sum of these hours in week_hours. 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -23

Figure 7. 5 Accumulating Weekday Hours Worked 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -24

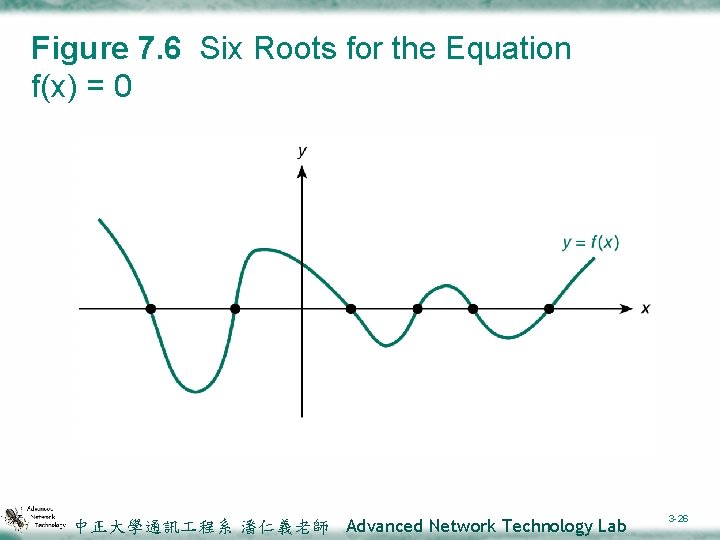
7. 4 Iterative Approximations vroot (zero of a function) ²A function argument value that causes the function result to be zero v. Bisection method ²Repeatedly generates approximate roots until a true root is discovered. 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -25

Figure 7. 6 Six Roots for the Equation f(x) = 0 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -26

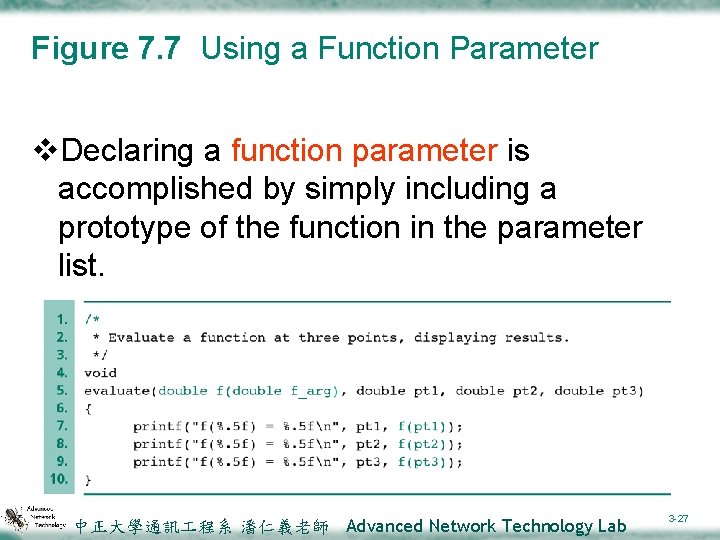
Figure 7. 7 Using a Function Parameter v. Declaring a function parameter is accomplished by simply including a prototype of the function in the parameter list. 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -27

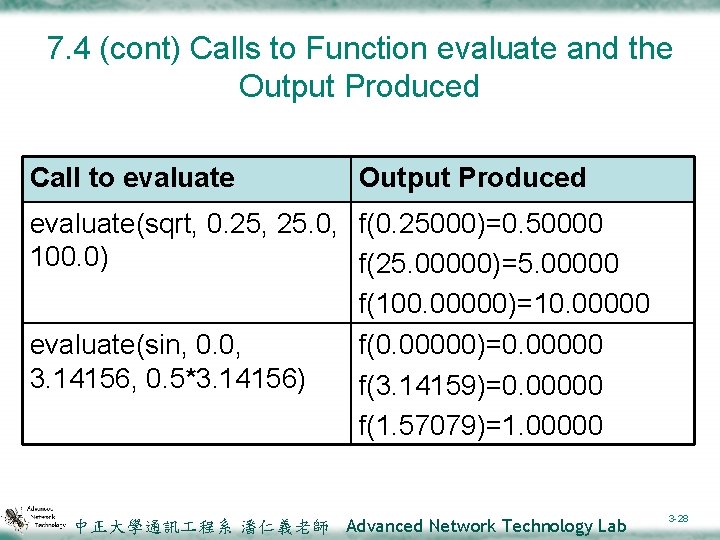
7. 4 (cont) Calls to Function evaluate and the Output Produced Call to evaluate Output Produced evaluate(sqrt, 0. 25, 25. 0, f(0. 25000)=0. 50000 100. 0) f(25. 00000)=5. 00000 f(100. 00000)=10. 00000 evaluate(sin, 0. 0, f(0. 00000)=0. 00000 3. 14156, 0. 5*3. 14156) f(3. 14159)=0. 00000 f(1. 57079)=1. 00000 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -28

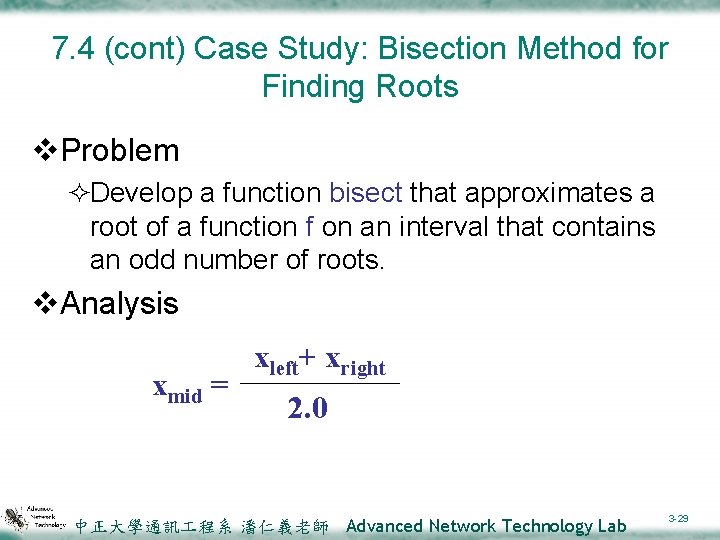
7. 4 (cont) Case Study: Bisection Method for Finding Roots v. Problem ²Develop a function bisect that approximates a root of a function f on an interval that contains an odd number of roots. v. Analysis xmid = xleft+ xright 2. 0 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -29

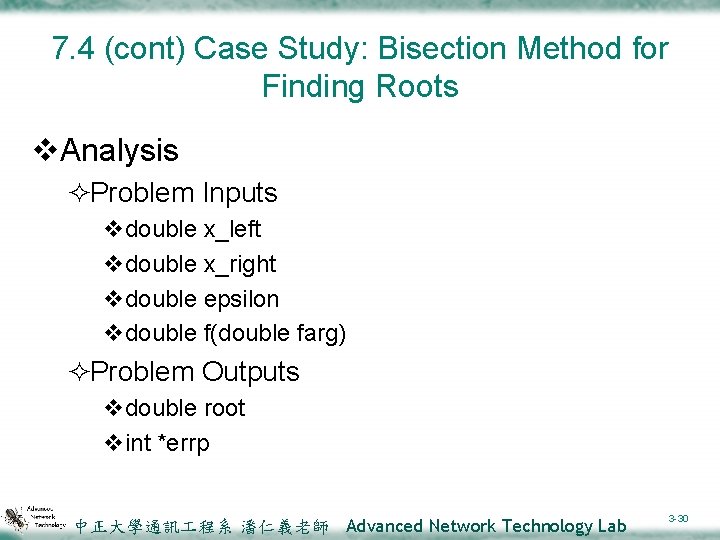
7. 4 (cont) Case Study: Bisection Method for Finding Roots v. Analysis ²Problem Inputs vdouble x_left vdouble x_right vdouble epsilon vdouble f(double farg) ²Problem Outputs vdouble root vint *errp 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -30

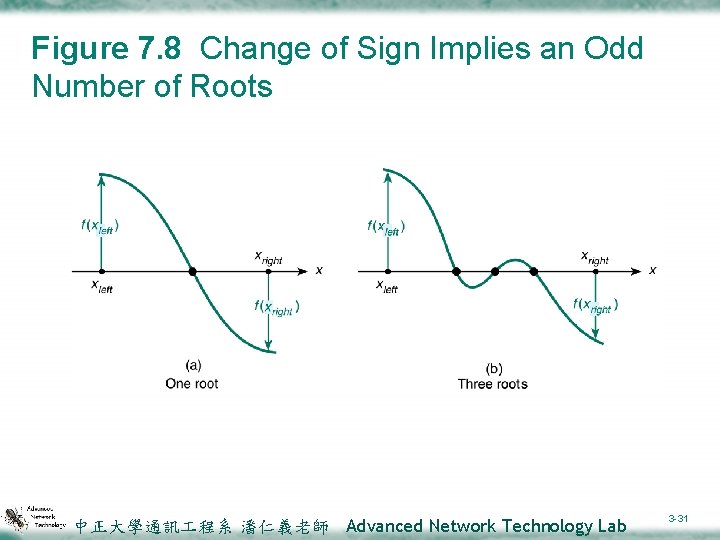
Figure 7. 8 Change of Sign Implies an Odd Number of Roots 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -31
![Figure 7 9 Three Possibilities That Arise When the Interval xleft xright Is Bisected Figure 7. 9 Three Possibilities That Arise When the Interval [xleft, xright] Is Bisected](https://slidetodoc.com/presentation_image_h2/d13162d6a00006fb92bfb13a8952797f/image-32.jpg)
Figure 7. 9 Three Possibilities That Arise When the Interval [xleft, xright] Is Bisected 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -32

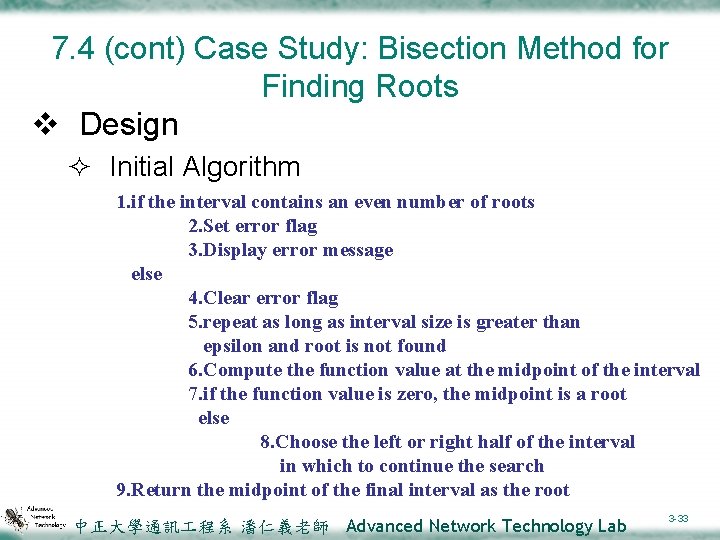
7. 4 (cont) Case Study: Bisection Method for Finding Roots v Design ² Initial Algorithm 1. if the interval contains an even number of roots 2. Set error flag 3. Display error message else 4. Clear error flag 5. repeat as long as interval size is greater than epsilon and root is not found 6. Compute the function value at the midpoint of the interval 7. if the function value is zero, the midpoint is a root else 8. Choose the left or right half of the interval in which to continue the search 9. Return the midpoint of the final interval as the root 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -33

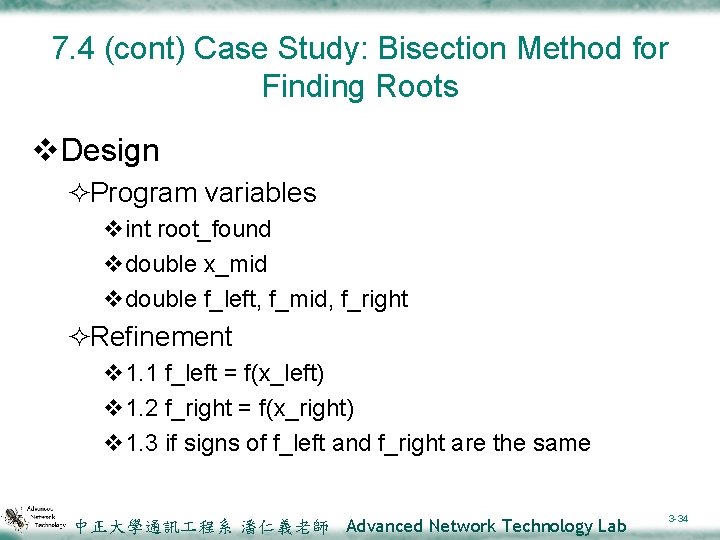
7. 4 (cont) Case Study: Bisection Method for Finding Roots v. Design ²Program variables vint root_found vdouble x_mid vdouble f_left, f_mid, f_right ²Refinement v 1. 1 f_left = f(x_left) v 1. 2 f_right = f(x_right) v 1. 3 if signs of f_left and f_right are the same 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -34

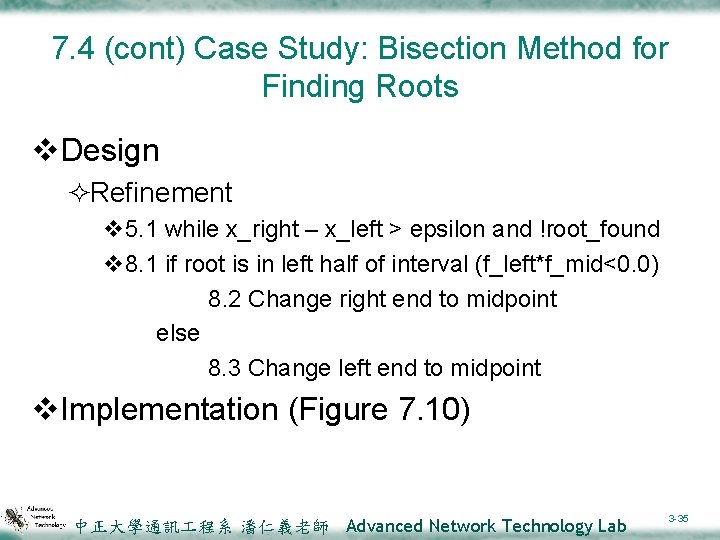
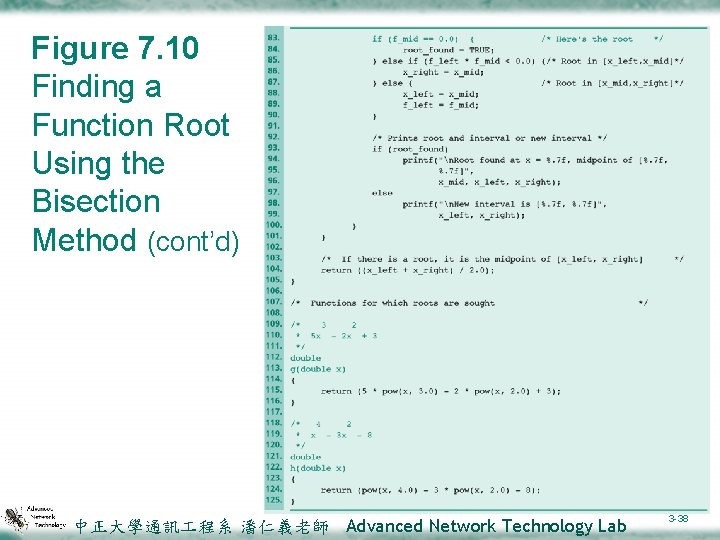
7. 4 (cont) Case Study: Bisection Method for Finding Roots v. Design ²Refinement v 5. 1 while x_right – x_left > epsilon and !root_found v 8. 1 if root is in left half of interval (f_left*f_mid<0. 0) 8. 2 Change right end to midpoint else 8. 3 Change left end to midpoint v. Implementation (Figure 7. 10) 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -35

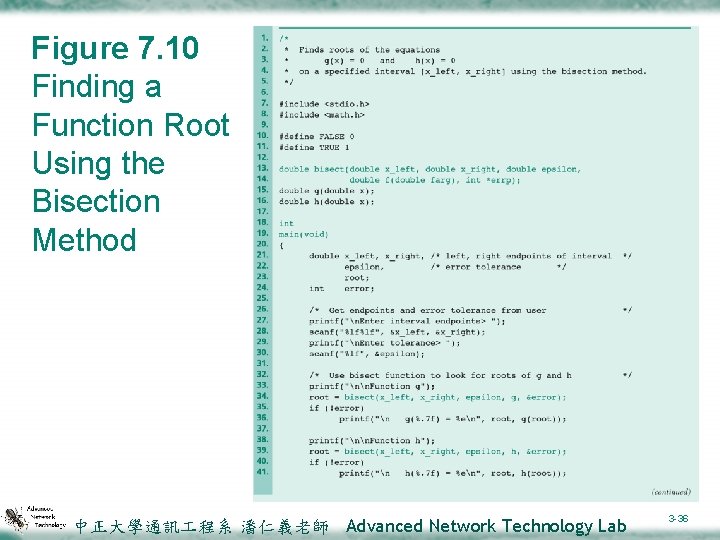
Figure 7. 10 Finding a Function Root Using the Bisection Method 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -36

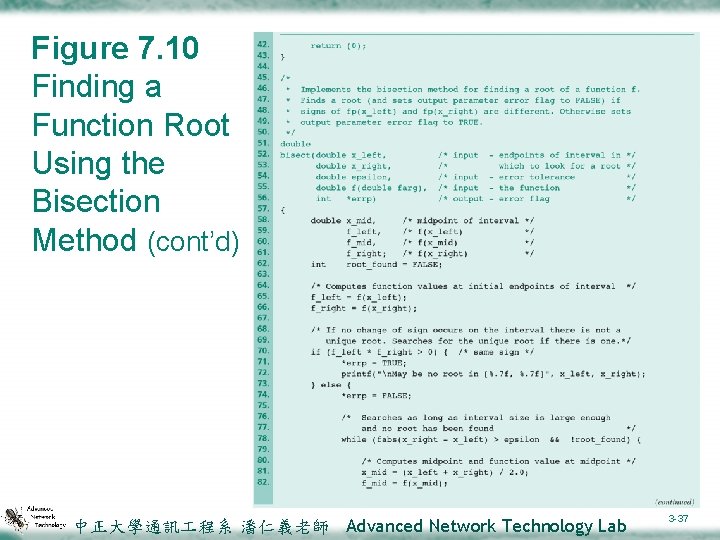
Figure 7. 10 Finding a Function Root Using the Bisection Method (cont’d) 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -37

Figure 7. 10 Finding a Function Root Using the Bisection Method (cont’d) 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -38

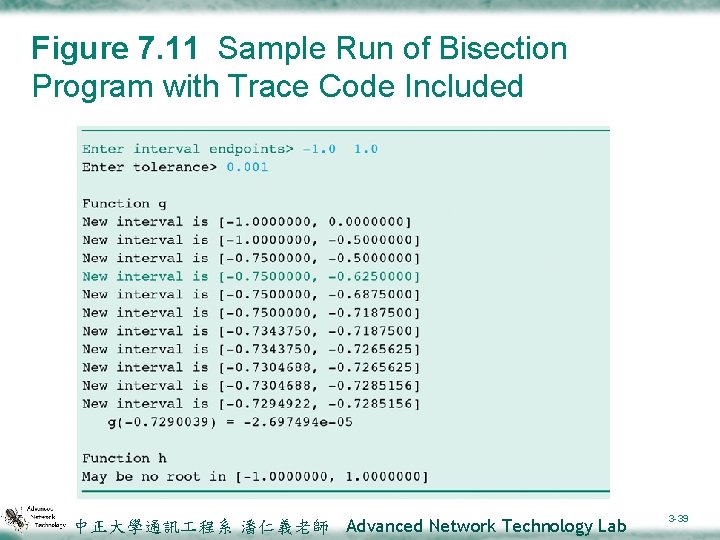
Figure 7. 11 Sample Run of Bisection Program with Trace Code Included 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -39

7. 5 Common Programming Errors v. Arithmetic underflow and overflow resulting from a poor choice of variable type are causes of erroneous results. v. Programs that approximate solutions to numerical problems by repeated calculations often magnify small errors. v. Not reuse the enumerated identifiers in another type or as a variable name v. C does not verify the value validity in enum variables 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -40

Chapter Review(1) v. Type int and double have different internal representations. v. Arithmetic with floating-point data may not be precise, because not all real numbers can be represented exactly. v. Type char data are represented by storing a binary code value for each symbol. v. Defining an enumerated type requires listing the identifier that are the values of the type. 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -41

Chapter Review(2) v. A variable or expression can be explicitly converted to another type by writing the new type’s name in parentheses before the value to convert. v. A function can take another function as a parameter. v. The bisection method is a technique for iterative approximation of a root of a function. 中正大學通訊 程系 潘仁義老師 Advanced Network Technology Lab 3 -42