Chapter 7 Program Security Stallings 9302020 Chp 7








![The Internet worm of 1988 [J 6] · Guessed and tried passwords with the The Internet worm of 1988 [J 6] · Guessed and tried passwords with the](https://slidetodoc.com/presentation_image/a4b7be6d1c0e23d0c7a09b32153f5a65/image-12.jpg)














- Slides: 41

Chapter 7 Program Security Stallings 9/30/2020 Chp. 7, 11, 12 Prof. Ehud Gudes Security Ch 7 1

Malicious code § Trojan Horses—A Trojan Horse is an apparently useful program that has hidden functions, usually harmful. A Trojan Horse can violate integrity more easily than confidentiality. § Viruses – A virus is a program that attaches itself to another program, propagates, and usually causes some data destruction. General virus detection is an undecidable problem, but we can detect specific viruses. §Worms—A worm is a program that propagates itself without infecting the host. 9/30/2020 Prof. Ehud Gudes Security Ch 7 2

Trojan Horses §Free program made available to unsuspecting user ©Actually contains code to do harm §Place altered version of utility program on victim's computer ©trick user into running that program 9/30/2020 Prof. Ehud Gudes Security Ch 7 3

Viruses and worms §Self-propagating §May destroy information and clog services §A mix of vandalism and ego trip §Take advantage of operating system and utilities flaws and uniformity of systems §Examples of recent viruses - next 9/30/2020 Prof. Ehud Gudes Security Ch 7 4

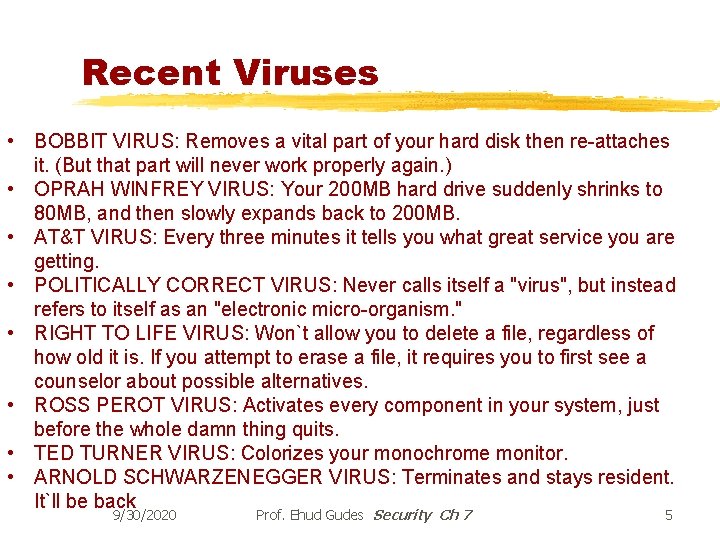
Recent Viruses • BOBBIT VIRUS: Removes a vital part of your hard disk then re-attaches it. (But that part will never work properly again. ) • OPRAH WINFREY VIRUS: Your 200 MB hard drive suddenly shrinks to 80 MB, and then slowly expands back to 200 MB. • AT&T VIRUS: Every three minutes it tells you what great service you are getting. • POLITICALLY CORRECT VIRUS: Never calls itself a "virus", but instead refers to itself as an "electronic micro-organism. " • RIGHT TO LIFE VIRUS: Won`t allow you to delete a file, regardless of how old it is. If you attempt to erase a file, it requires you to first see a counselor about possible alternatives. • ROSS PEROT VIRUS: Activates every component in your system, just before the whole damn thing quits. • TED TURNER VIRUS: Colorizes your monochrome monitor. • ARNOLD SCHWARZENEGGER VIRUS: Terminates and stays resident. It`ll be back 9/30/2020 Prof. Ehud Gudes Security Ch 7 5

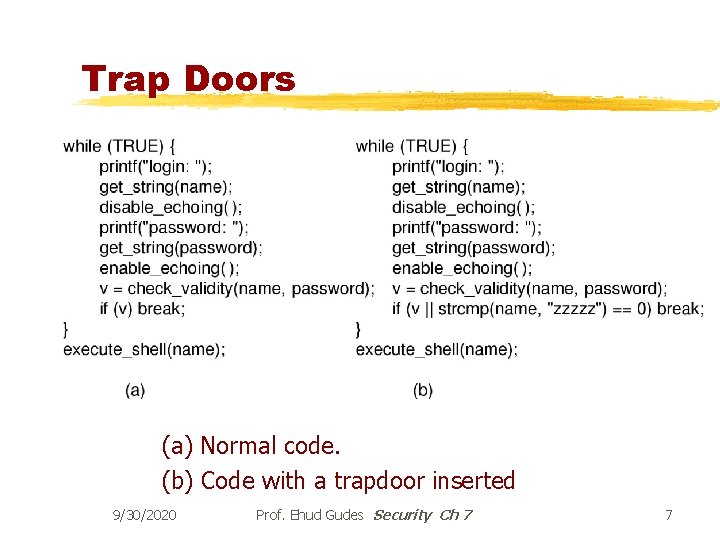
Program Threats §Trap door © Code segment that misuses its environment and allows malicious code (trojan horse) to execute. © Exploits mechanisms for allowing programs written by users to be executed by other users. §Trap Door examples © Specific user identifier or password that circumvents normal security procedures. © Could be included in a compiler (Kernighan’s C compiler). © Stack and Buffer Overflow - Exploits a bug in a program (overflow either the stack or memory buffers. ) 9/30/2020 Prof. Ehud Gudes Security Ch 7 6

Trap Doors (a) Normal code. (b) Code with a trapdoor inserted 9/30/2020 Prof. Ehud Gudes Security Ch 7 7

Logic Bombs §Company programmer writes program ©potential to do harm ©OK as long as he/she enters password daily ©if programmer is fired, no password and bomb explodes 9/30/2020 Prof. Ehud Gudes Security Ch 7 8

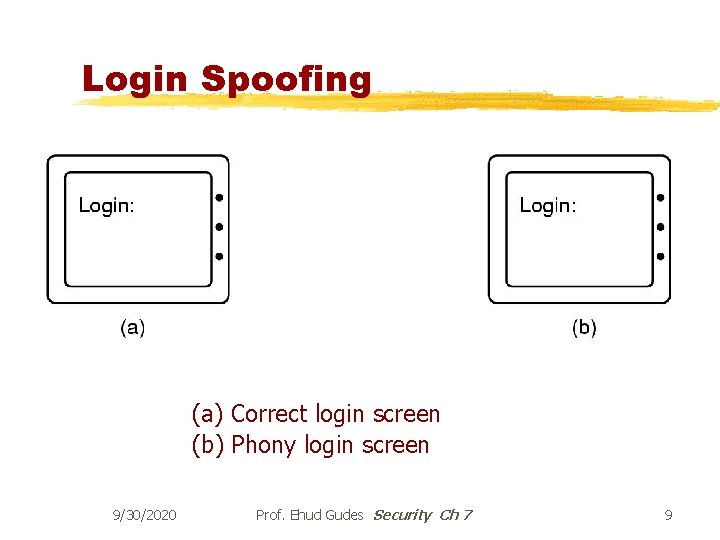
Login Spoofing (a) Correct login screen (b) Phony login screen 9/30/2020 Prof. Ehud Gudes Security Ch 7 9

Worms §replicating program that propagates over net ©using email, remote exec, remote login §has phases like a virus: ©dormant, propagation, triggering, execution ©propagation phase: searches for other systems, connects to it, copies self to it and runs §may disguise itself as a system process §concept seen in Brunner’s “Shockwave Rider” §implemented by Xerox Palo Alto labs in 1980’s

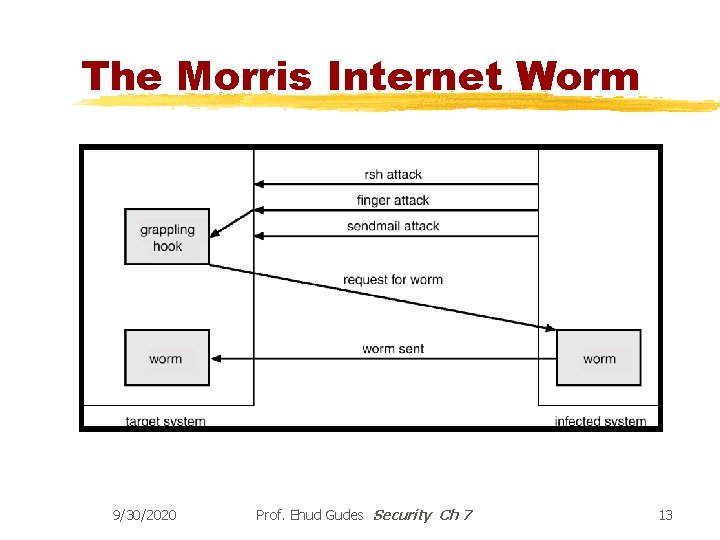
Morris Worm §one of best know worms §released by Robert Morris in 1988 §various attacks on UNIX systems ©cracking password file to use login/password to logon to other systems ©exploiting a bug in the finger protocol ©exploiting a bug in sendmail §if succeed have remote shell access ©sent bootstrap program to copy worm over
![The Internet worm of 1988 J 6 Guessed and tried passwords with the The Internet worm of 1988 [J 6] · Guessed and tried passwords with the](https://slidetodoc.com/presentation_image/a4b7be6d1c0e23d0c7a09b32153f5a65/image-12.jpg)
The Internet worm of 1988 [J 6] · Guessed and tried passwords with the use of a dictionary · Exploited bugs in the finger and sendmail programs, including buffer overflow. · Took advantage of the fact that some systems specify trusted computers from which remote logins are accepted without checking passwords. · Used encryption and other ways to hide its existence (a polymorphic virus). 9/30/2020 Prof. Ehud Gudes Security Ch 7 12

The Morris Internet Worm 9/30/2020 Prof. Ehud Gudes Security Ch 7 13

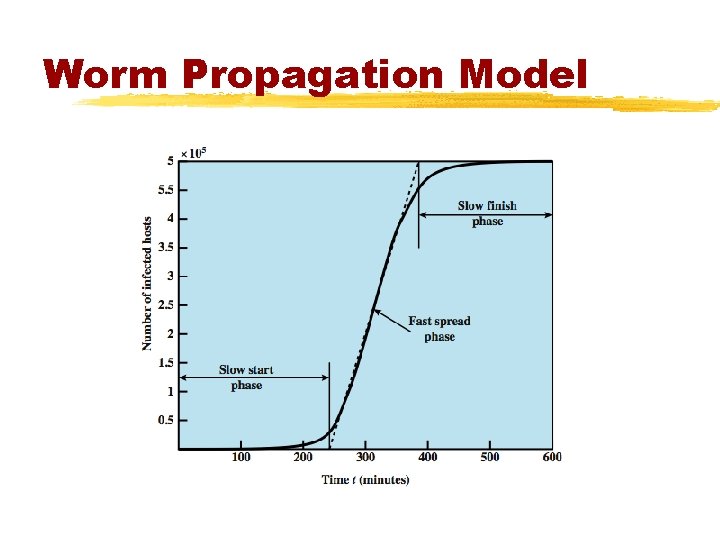
Worm Propagation Model

Recent Worm Attacks §Code Red ©July 2001 exploiting MS IIS bug ©probes random IP address, does DDo. S attack ©consumes significant net capacity when active §Code Red II variant includes backdoor §SQL Slammer ©early 2003, attacks MS SQL Server ©compact and very rapid spread §Mydoom ©mass-mailing e-mail worm that appeared in 2004 ©installed remote access backdoor in infected systems

New Worm Technology §multiplatform §multi-exploit §ultrafast spreading §polymorphic §metamorphic §transport vehicles §zero-day exploit

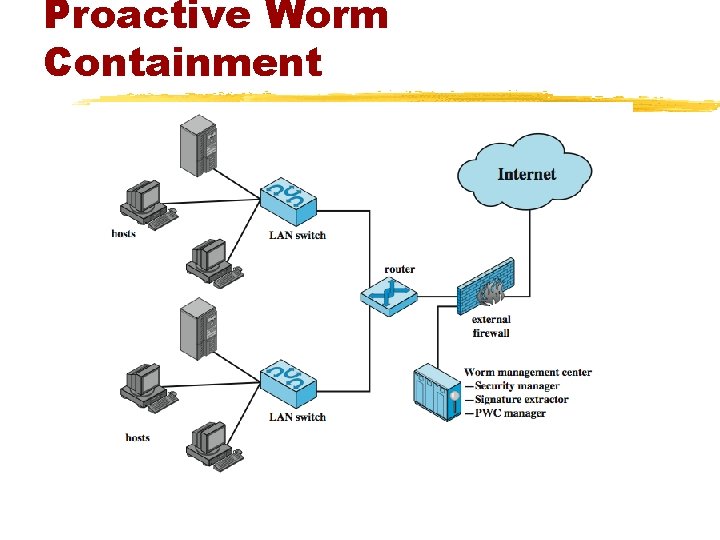
Worm Countermeasures §overlaps with anti-virus techniques §once worm on system A/V can detect §worms also cause significant net activity §worm defense approaches include: ©signature-based worm scan filtering ©filter-based worm containment ©payload-classification-based worm containment ©threshold random walk scan detection ©rate limiting and rate halting

Proactive Worm Containment

Viruses §piece of software that infects programs ©modifying them to include a copy of the virus ©so it executes secretly when host program is run §specific to operating system and hardware ©taking advantage of their details and weaknesses §a typical virus goes through phases of: ©dormant ©propagation ©triggering ©execution

Virus Damage Scenarios §Blackmail (ask for money for decryption key) §Denial of service as long as virus runs (fill out disk, clog CPU or memory) §Permanently damage hardware (BIOS) §Target a competitor's computer ©do harm ©Espionage §Intra-corporate dirty tricks ©sabotage another corporate officer's files 9/30/2020 Prof. Ehud Gudes Security Ch 7 20

Viruses - program “segments” §Program segments attached to another executable §When program is run, the virus proliferates actually a type of Trojan horse… but not personal. . §Numerous possible actions: © erasing, modifying, encrypting files © display extortion note: send $$$ © damage boot sector on hard disk (or ask for password. . ) §Defenses: © look for known viruses in files © perform checksum on files © make directories of binary files unwritable for users. . . 9/30/2020 Prof. Ehud Gudes Security Ch 7 21

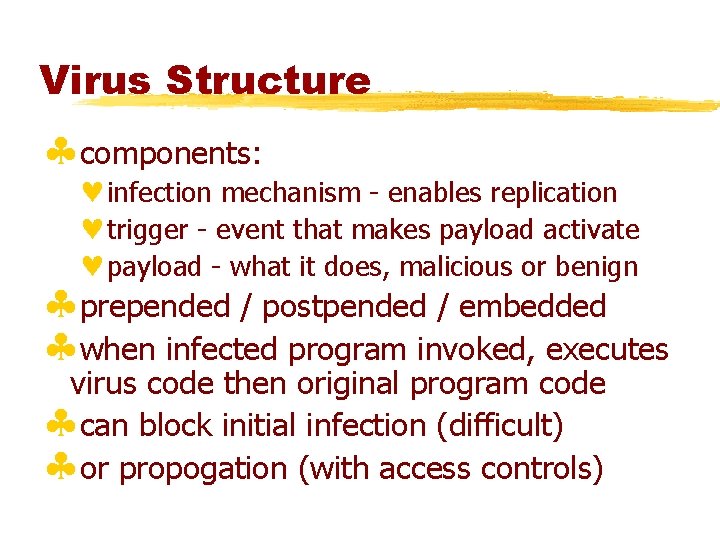
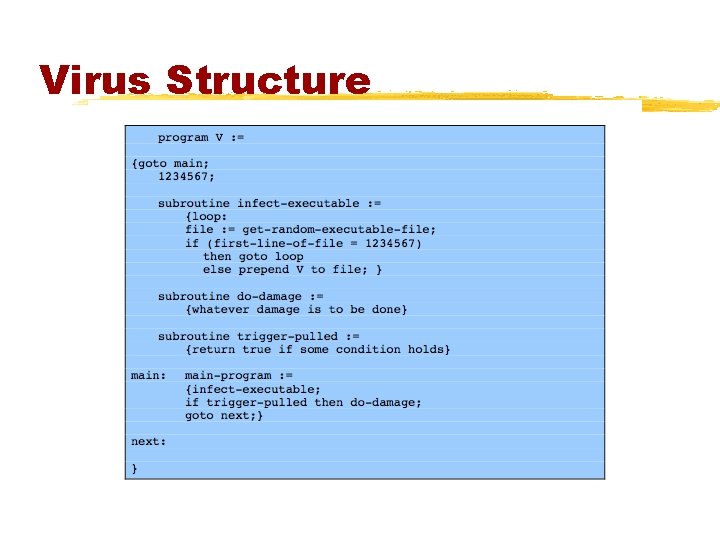
Virus Structure §components: ©infection mechanism - enables replication ©trigger - event that makes payload activate ©payload - what it does, malicious or benign §prepended / postpended / embedded §when infected program invoked, executes virus code then original program code §can block initial infection (difficult) §or propogation (with access controls)

Virus Structure

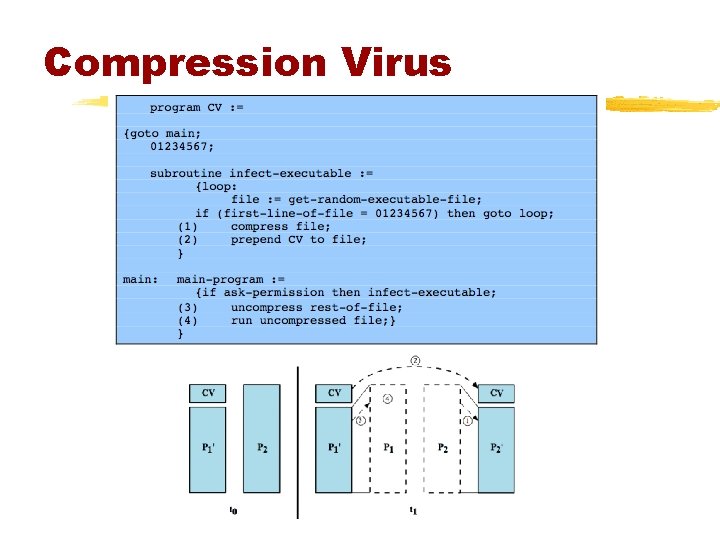
Compression Virus

Virus Classification §boot sector §file infector §macro virus §encrypted virus §stealth virus §polymorphic virus §metamorphic virus

How Viruses Spread §Virus placed where likely to be copied §When copied ©infects programs on hard drive, floppy ©may try to spread over LAN §Attach to innocent looking email ©when it runs, use mailing list to replicate(News-group) ©Use naïve subjects: I miss you, I am ill, etc §Hide inside application macros (Ms-word, MS-excel) 9/30/2020 Prof. Ehud Gudes Security Ch 7 26

How Viruses Work (1) §Virus written in assembly language §Inserted into another program ©use tool called a “dropper” §Virus dormant until program executed ©then infects other programs ©eventually executes its “payload” 9/30/2020 Prof. Ehud Gudes Security Ch 7 27

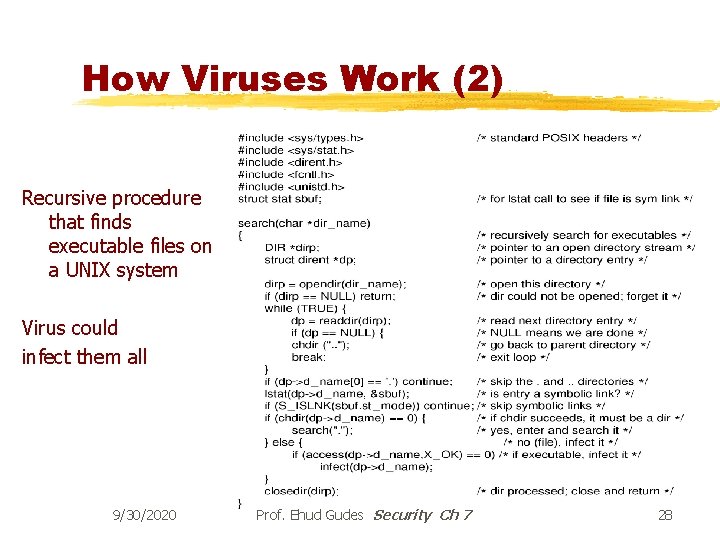
How Viruses Work (2) Recursive procedure that finds executable files on a UNIX system Virus could infect them all 9/30/2020 Prof. Ehud Gudes Security Ch 7 28

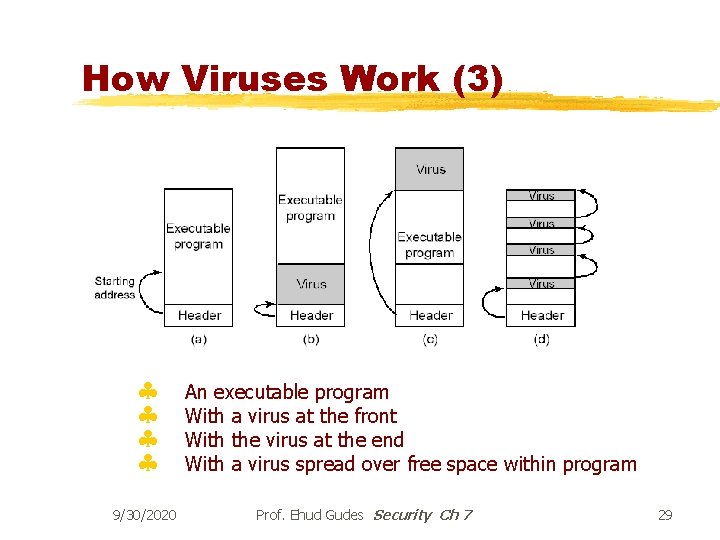
How Viruses Work (3) § § 9/30/2020 An executable program With a virus at the front With the virus at the end With a virus spread over free space within program Prof. Ehud Gudes Security Ch 7 29

Macro Virus §became very common in mid-1990 s since ©platform independent ©infect documents ©easily spread §exploit macro capability of office apps ©executable program embedded in office doc ©often a form of Basic §more recent releases include protection §recognized by many anti-virus programs

E-Mail Viruses §more recent development §e. g. Melissa ©exploits MS Word macro in attached doc ©if attachment opened, macro activates ©sends email to all on users address list ©and does local damage §then saw versions triggered reading email §hence much faster propagation

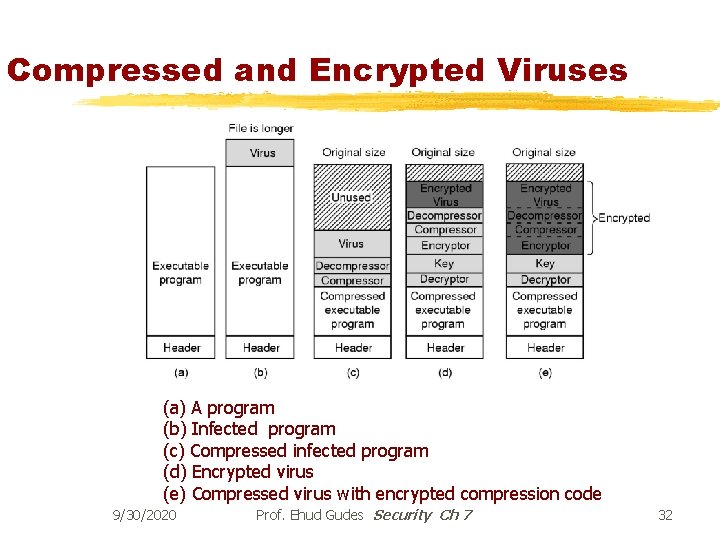
Compressed and Encrypted Viruses (a) A program (b) Infected program (c) Compressed infected program (d) Encrypted virus (e) Compressed virus with encrypted compression code 9/30/2020 Prof. Ehud Gudes Security Ch 7 32

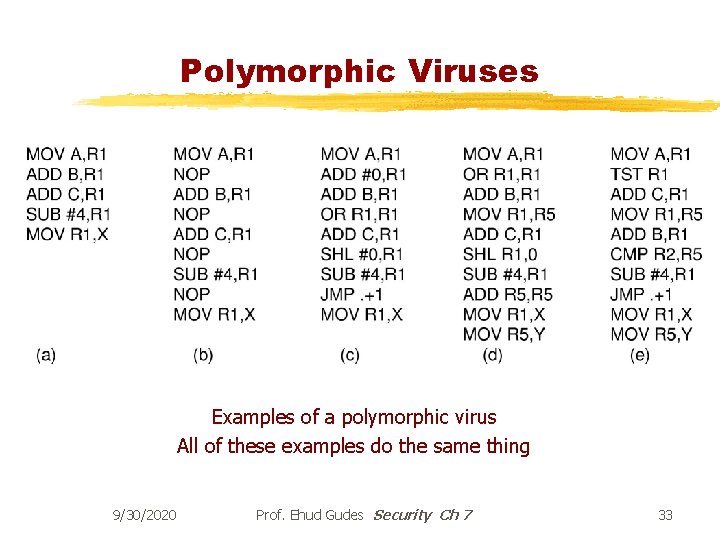
Polymorphic Viruses Examples of a polymorphic virus All of these examples do the same thing 9/30/2020 Prof. Ehud Gudes Security Ch 7 33

Virus Countermeasures §prevention - ideal solution but difficult §realistically need: ©detection ©identification ©removal §if detect but can’t identify or remove, must discard and replace infected program

Anti-Virus Evolution [J 7[ §virus & antivirus tech have both evolved §early viruses simple code, easily removed §as become more complex, so must the countermeasures §generations ©first - signature scanners ©second - heuristics ©third - identify actions ©fourth - combination packages

Antivirus and Anti-Antivirus Techniques §Integrity checkers §Behavioral checkers §Virus avoidance ©good OS ©install only shrink-wrapped software ©use antivirus software ©do not click on attachments to email ©frequent backups §Recovery from virus attack ©halt computer, reboot from safe disk, run antivirus 9/30/2020 Prof. Ehud Gudes Security Ch 7 36

Antivirus and Anti-Antivirus Techniques §Inoculation – insert code like a virus. A virus does not attack a file which is already “affected”. Problem: need to know which virus will attack next? ! §Disinfection – returning the original entry point and erasing virus code. Problem: what if this was an overwriting virus or apadding virus §Scanning and checking file size and signature during OPEN Problem: a boot sector or a ROM virus may override open and bypass this check! Summary: a never ending war! 9/30/2020 Prof. Ehud Gudes Security Ch 7 37

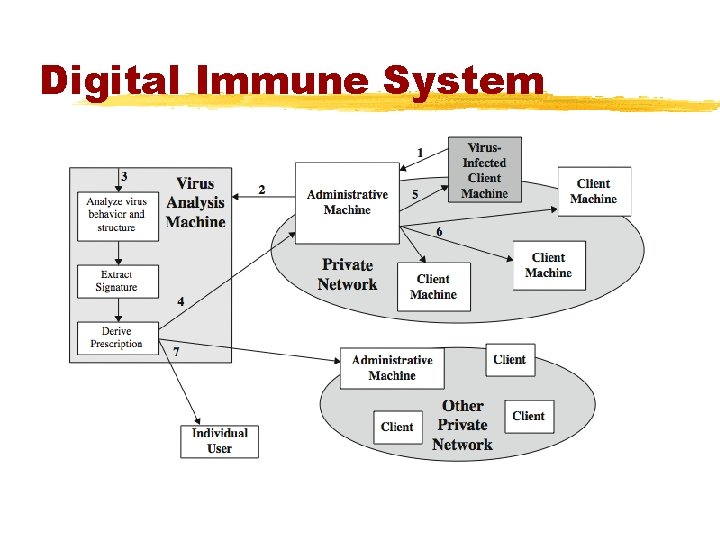
Digital Immune System

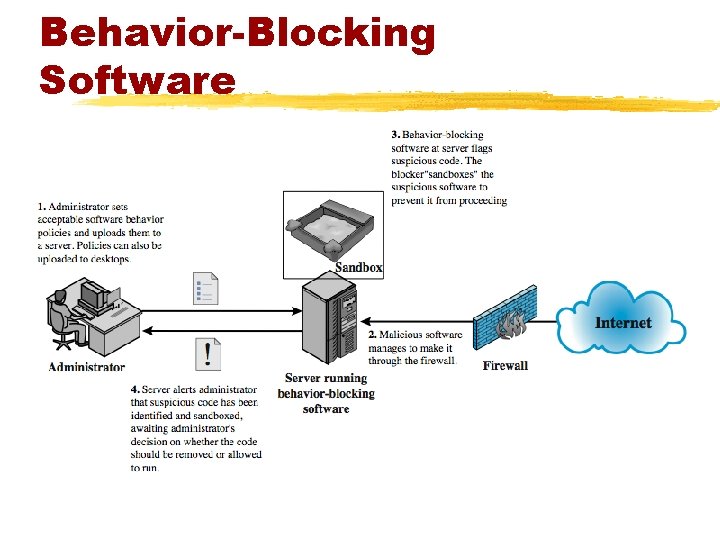
Behavior-Blocking Software

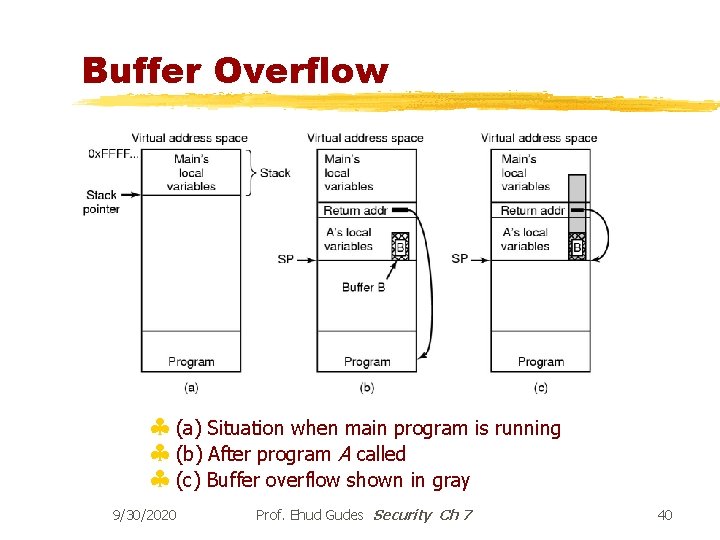
Buffer Overflow § (a) Situation when main program is running § (b) After program A called § (c) Buffer overflow shown in gray 9/30/2020 Prof. Ehud Gudes Security Ch 7 40

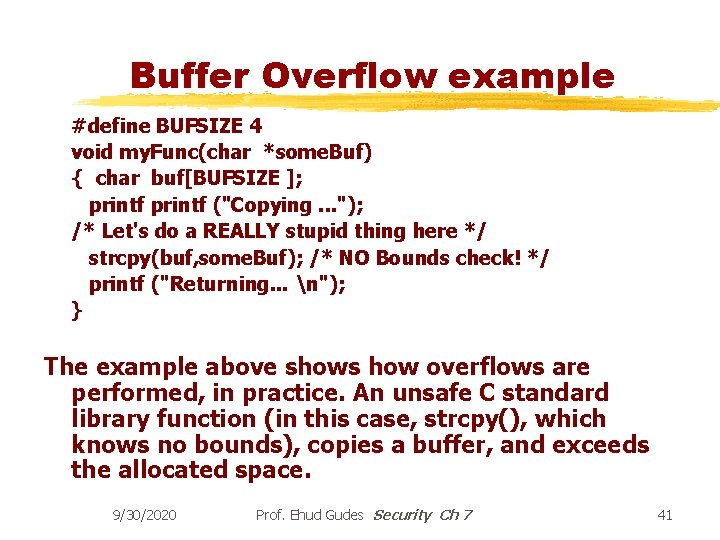
Buffer Overflow example #define BUFSIZE 4 void my. Func(char *some. Buf) { char buf[BUFSIZE ]; printf ("Copying. . . "); /* Let's do a REALLY stupid thing here */ strcpy(buf, some. Buf); /* NO Bounds check! */ printf ("Returning. . . n"); } The example above shows how overflows are performed, in practice. An unsafe C standard library function (in this case, strcpy(), which knows no bounds), copies a buffer, and exceeds the allocated space. 9/30/2020 Prof. Ehud Gudes Security Ch 7 41