Chapter 7 Linux Resource Management Security All Examples


![Manage Memory • Check memory: in bytes, KB, B, GB & total=RAM+swap free [-b|-k|-m|-g] Manage Memory • Check memory: in bytes, KB, B, GB & total=RAM+swap free [-b|-k|-m|-g]](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-3.jpg)
![System Sart Up Time- uptime Example: [root@host ~]# uptime 08: 56: 59 up 4 System Sart Up Time- uptime Example: [root@host ~]# uptime 08: 56: 59 up 4](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-5.jpg)
![Network Info- netstat –[atunlp] – A: all info – t: TCP info – u: Network Info- netstat –[atunlp] – A: all info – t: TCP info – u:](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-6.jpg)
![Example • [root@host ~]# netstat • Active Internet connections (w/o servers) • Proto Recv-Q Example • [root@host ~]# netstat • Active Internet connections (w/o servers) • Proto Recv-Q](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-7.jpg)
![Kernel Info- dmesg | more Example. [root@host ~]# dmesg | more Initializing cgroup subsys Kernel Info- dmesg | more Example. [root@host ~]# dmesg | more Initializing cgroup subsys](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-8.jpg)
![System Resource (CPU/RAM/Disk I/O) Change Detection- vmstat CPU: vmstat [-a] #time_per_second detection# RAM: vmstat System Resource (CPU/RAM/Disk I/O) Change Detection- vmstat CPU: vmstat [-a] #time_per_second detection# RAM: vmstat](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-9.jpg)
![Example- Check CPU • Check CPU, 1 time/sec, total 3 times [root@host ~]# vmstat Example- Check CPU • Check CPU, 1 time/sec, total 3 times [root@host ~]# vmstat](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-10.jpg)
![Example- Check Disk [root@host ~]# vmstat -d disk- ------reads------writes------IO-----total merged sectors ms cur sec Example- Check Disk [root@host ~]# vmstat -d disk- ------reads------writes------IO-----total merged sectors ms cur sec](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-11.jpg)
![Find Process using File/Dir- e. g. for device busy • fuser [-umv] [-k[i] [signal]] Find Process using File/Dir- e. g. for device busy • fuser [-umv] [-k[i] [signal]]](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-12.jpg)
![Find Process using File/Dir. Example [root@host ~]# fuser -mvu /proc USER PID ACCESS COMMAND Find Process using File/Dir. Example [root@host ~]# fuser -mvu /proc USER PID ACCESS COMMAND](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-13.jpg)
![List Open File by Process • lsof [-a. Uu] [+d] – a: all – List Open File by Process • lsof [-a. Uu] [+d] – a: all –](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-14.jpg)
![Example [root@host ~]# lsof +d/dev|more COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME Example [root@host ~]# lsof +d/dev|more COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-16.jpg)
![Find Current Running PID • pidof [-sx] program – s: list only PID – Find Current Running PID • pidof [-sx] program – s: list only PID –](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-17.jpg)

![Example- Security context (identitity: role: type) [root@host ~]# ls -Z -rw-------. root system_u: object_r: Example- Security context (identitity: role: type) [root@host ~]# ls -Z -rw-------. root system_u: object_r:](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-20.jpg)


![Example [root@host ~]# ll -Zd /usr/sbin/httpd /var/www/html -rwxr-xr-x. root system_u: object_r: httpd_exec_t: s 0 Example [root@host ~]# ll -Zd /usr/sbin/httpd /var/www/html -rwxr-xr-x. root system_u: object_r: httpd_exec_t: s 0](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-25.jpg)


![Check Supporting Mode [root@host ~]# getenforce Disabled [root@host ~]# getenforce Enforcing Check Supporting Mode [root@host ~]# getenforce Disabled [root@host ~]# getenforce Enforcing](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-28.jpg)

![Example [root@host ~]# sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode Example [root@host ~]# sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-30.jpg)
![Check SELinux Configuration File [root@host ~]# vi /etc/selinux/config# This file controls the state of Check SELinux Configuration File [root@host ~]# vi /etc/selinux/config# This file controls the state of](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-31.jpg)

![Example [root@host ~]# vi /boot/grub/menu. lst Take away selinux=0 # grub. conf generated by Example [root@host ~]# vi /boot/grub/menu. lst Take away selinux=0 # grub. conf generated by](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-33.jpg)

![Example [root@host ~]# setenforce 0 [root@host ~]# getenforce Permissive [root@host ~]# setenforce 1 [root@host Example [root@host ~]# setenforce 0 [root@host ~]# getenforce Permissive [root@host ~]# setenforce 1 [root@host](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-35.jpg)
![SELinux on Network Service. Hands on • Start Network Service [root@host ~]# ps aux SELinux on Network Service. Hands on • Start Network Service [root@host ~]# ps aux](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-36.jpg)
![SELinux on Network Service. Hands on (Cont. ) [root@host ~]# ps aux -Z | SELinux on Network Service. Hands on (Cont. ) [root@host ~]# ps aux -Z |](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-37.jpg)



![SELinux Troubleshoot 1. Use setroubleshoot: /var/log/messages And use sealert [root@host ~]# chkconfig --list setroubleshoot SELinux Troubleshoot 1. Use setroubleshoot: /var/log/messages And use sealert [root@host ~]# chkconfig --list setroubleshoot](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-42.jpg)
![SELinux Troubleshoot 2. Use auditd: /var/log/audit. log And use audit 2 why [root@host ~]# SELinux Troubleshoot 2. Use auditd: /var/log/audit. log And use audit 2 why [root@host ~]#](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-43.jpg)


- Slides: 46

Chapter 7 Linux Resource Management & Security (All Examples Based on Fedora Linux) By C. Shing ITEC Dept Radford University

Objectives • Understand Linux memory management • Understand Linux network management • Understand SELinux
![Manage Memory Check memory in bytes KB B GB totalRAMswap free bkmg Manage Memory • Check memory: in bytes, KB, B, GB & total=RAM+swap free [-b|-k|-m|-g]](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-3.jpg)
Manage Memory • Check memory: in bytes, KB, B, GB & total=RAM+swap free [-b|-k|-m|-g] [-t] Example: [root@host ~]# free -m -t total used free shared buffers cached Mem: 2007 1252 754 0 185 901 -/+ buffers/cache: 166 1841 Swap: 4959 0 4959 Total: 6967 1252 5714

System and Kernel Info- uname • uname (Bash) -a: all -r: version -m: hardware -p: CPU type Example: [root@host ~]# uname -a Linux host 2. 6. 32 -131. 0. 15. el 6. x 86_64 #1 SMP Sat May 21 10: 27: 57 CDT 2011 x 86_64 GNU/Linux
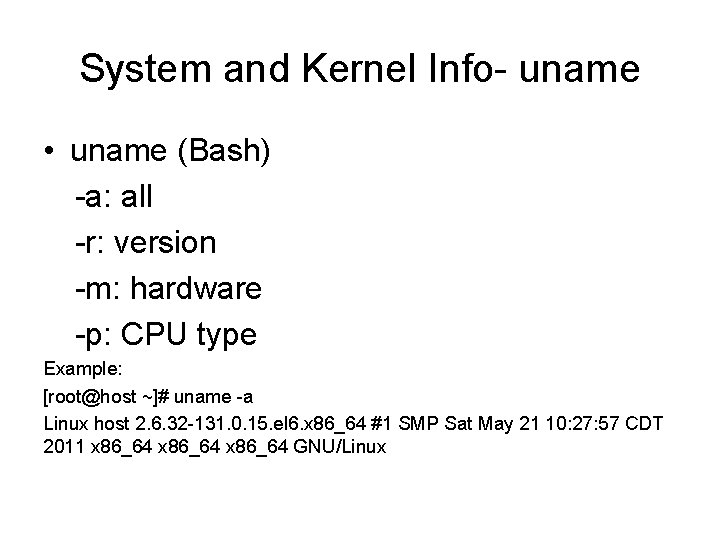
![System Sart Up Time uptime Example roothost uptime 08 56 59 up 4 System Sart Up Time- uptime Example: [root@host ~]# uptime 08: 56: 59 up 4](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-5.jpg)
System Sart Up Time- uptime Example: [root@host ~]# uptime 08: 56: 59 up 4 days, 9 min, 1 user, load average: 0. 00, 0. 00
![Network Info netstat atunlp A all info t TCP info u Network Info- netstat –[atunlp] – A: all info – t: TCP info – u:](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-6.jpg)
Network Info- netstat –[atunlp] – A: all info – t: TCP info – u: UDP info – n: port info – l: listen service info – p: service PID info
![Example roothost netstat Active Internet connections wo servers Proto RecvQ Example • [root@host ~]# netstat • Active Internet connections (w/o servers) • Proto Recv-Q](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-7.jpg)
Example • [root@host ~]# netstat • Active Internet connections (w/o servers) • Proto Recv-Q Send-Q Local Address Foreign Address State • tcp 0 52 host. twg: ssh DHCP-21109. iis. sinica: 16962 ESTABLISHED • udp 0 0 host-117 -103 -96 -1: 48550 239. 2. 11. 71: 8649 ESTABLISHED • Active UNIX domain sockets (w/o servers) • Proto Ref. Cnt Flags Type State I-Node Path • unix 2 [] DGRAM 8369 /var/run/portreserve/socket • unix 2 [] DGRAM 6808 @/org/kernel/udevd • unix 2 [] DGRAM 8815 @/org/freedesktop/hal/udev_event • … [root@host ~]# netstat -tlnp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0. 0: 22 0. 0: * LISTEN 1347/sshd tcp 0 0 127. 0. 0. 1: 25 0. 0: * LISTEN 1439/master tcp 0 0 0. 0: 8649 0. 0: * LISTEN 1363/gmond tcp 0 0 0. 0: 111 0. 0: * LISTEN 1196/rpcbind tcp 0 0 : : : 22 : : : * LISTEN 1347/sshd tcp 0 0 : : : 111 : : : * LISTEN 1196/rpcbind
![Kernel Info dmesg more Example roothost dmesg more Initializing cgroup subsys Kernel Info- dmesg | more Example. [root@host ~]# dmesg | more Initializing cgroup subsys](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-8.jpg)
Kernel Info- dmesg | more Example. [root@host ~]# dmesg | more Initializing cgroup subsys cpuset Initializing cgroup subsys cpu Linux version 2. 6. 32 -131. 0. 15. el 6. x 86_64 (mockbuild@sl 6. fnal. gov) (gcc version 4. 4. 5 20110214 (Red Hat 4. 4. 5 -6) (GCC) ) #1 SMP Sat May 21 10: 27: 57 CDT 2011 Command line: ro root=UUID=52 ca 1 ca 3 -479 b-4 a 7 b-9 aeb-c 551765 e 786 f rd_NO_LUKS rd_NO _LVM rd_NO_MD rd_NO_DM LANG=en_US. UTF-8 SYSFONT=latarcyrheb-sun 16 KEYBOARDTYPE=p c KEYTABLE=us crashkernel=auto rhgb quiet KERNEL supported cpus: Intel Genuine. Intel AMD Authentic. AMD Centaur. Hauls BIOS-provided physical RAM map: BIOS-e 820: 00000000 - 0000009 dc 00 (usable) BIOS-e 820: 0000009 dc 00 - 000000 a 0000 (reserved) BIOS-e 820: 000000 f 0000 - 00000100000 (reserved) BIOS-e 820: 00000100000 - 00007 fffd 000 (usable) BIOS-e 820: 00007 fffd 000 - 000080000000 (reserved) BIOS-e 820: 0000 fffbc 000 - 000000010000 (reserved) DMI 2. 4 present. SMBIOS version 2. 4 @ 0 x. FDA 30 e 820 update range: 00000000 - 0000001000 (usable) ==> (reserved) e 820 remove range: 000000 a 0000 - 00000100000 (usable) last_pfn = 0 x 7 fffd max_arch_pfn = 0 x 40000
![System Resource CPURAMDisk IO Change Detection vmstat CPU vmstat a timepersecond detection RAM vmstat System Resource (CPU/RAM/Disk I/O) Change Detection- vmstat CPU: vmstat [-a] #time_per_second detection# RAM: vmstat](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-9.jpg)
System Resource (CPU/RAM/Disk I/O) Change Detection- vmstat CPU: vmstat [-a] #time_per_second detection# RAM: vmstat [-fs] I/O: vmstat [-S] unit Disk: vmstat [-d] Partition: vmstat [-p partition]
![Example Check CPU Check CPU 1 timesec total 3 times roothost vmstat Example- Check CPU • Check CPU, 1 time/sec, total 3 times [root@host ~]# vmstat](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-10.jpg)
Example- Check CPU • Check CPU, 1 time/sec, total 3 times [root@host ~]# vmstat 1 3 procs ------memory----- ---swap-- -----io---- -system-- -----cpu----r b swpd free buff cache si so bi bo in us sy id wa st 1 0 0 773316 189600 923236 0 0 1 7 18 0 0 99 0 0 0 773316 189600 923236 0 0 14 0 0 100 0 0 773316 189600 923236 0 0 11 0 0 100 0 0 cs 24 43 17
![Example Check Disk roothost vmstat d disk readswritesIOtotal merged sectors ms cur sec Example- Check Disk [root@host ~]# vmstat -d disk- ------reads------writes------IO-----total merged sectors ms cur sec](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-11.jpg)
Example- Check Disk [root@host ~]# vmstat -d disk- ------reads------writes------IO-----total merged sectors ms cur sec ram 0 0 0 ram 1 0 0 0 0 0 … loop 0 0 0 … loop 3 0 0 0 0 0 disk- ------reads------writes------IO-----total merged sectors ms cur sec loop 4 0 0 0 0 0 … loop 7 0 0 0 0 0 vda 32858 5490 1008220 99526 382362 219714 4811848 3561484 1621 0
![Find Process using FileDir e g for device busy fuser umv ki signal Find Process using File/Dir- e. g. for device busy • fuser [-umv] [-k[i] [signal]]](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-12.jpg)
Find Process using File/Dir- e. g. for device busy • fuser [-umv] [-k[i] [signal]] file/dir – u: list process user – v: show command – M: check up to top layer Example. [root@host ~]# cat /proc/1/cmdline /sbin/init[root@host ~]# fuser -uv. USER PID ACCESS COMMAND. : root 9977. . c. . (root)bash root 10595. . c. . (root)vi root 10651. . c. . (root)vi
![Find Process using FileDir Example roothost fuser mvu proc USER PID ACCESS COMMAND Find Process using File/Dir. Example [root@host ~]# fuser -mvu /proc USER PID ACCESS COMMAND](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-13.jpg)
Find Process using File/Dir. Example [root@host ~]# fuser -mvu /proc USER PID ACCESS COMMAND /proc: root 1154 f. . (root)rsyslogd root 1256 f. . (root)acpid haldaemon 1265 f. . (haldaemon)hald [root@host ~]# find /var -type p /var/run/autofs. fifo-misc /var/run/autofs. fifo-net /var/spool/postfix/public/qmgr /var/spool/postfix/public/pickup [root@host ~]# fuser -uv /var/run/autofs. fifo-misc USER PID ACCESS COMMAND /var/run/autofs. fifo-misc: root 1328 F. . (root)automount
![List Open File by Process lsof a Uu d a all List Open File by Process • lsof [-a. Uu] [+d] – a: all –](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-14.jpg)
List Open File by Process • lsof [-a. Uu] [+d] – a: all – U: Unix-Like socket type – u: username +d: directory

Example /usr/lib/locale-archive bash 9977 root mem REG 252, 2 61624 4983 /lib 64/libnss_files-2. 12. so bash 9977 root mem REG 252, 2 26050 5273 /usr/lib 64/gconvmodules. cache bash 9977 root 0 u CHR 136, 0 0 t 0 3 /dev/pts/0 … [root@host ~]# lsof -u root -a -U|more COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME init 1 root 7 u unix 0 xffff 88003787 c 680 0 t 0 6648 socket init 1 root 9 u unix 0 xffff 8800374 dd 380 0 t 0 8655 socket udevd 474 root 4 u unix 0 xffff 880037 f 279 c 0 0 t 0 6808 socket udevd 474 root 8 u unix 0 xffff 880037 f 276 c 0 0 t 0 6823 socket udevd 474 root 9 u unix 0 xffff 88003787 c 080 0 t 0 6824 socket dhclient 1087 root 6 u unix 0 xffff 880079 f 606 c 0 0 t 0 1273359 socket auditd 1129 root 7 u unix 0 xffff 880079 f 600 c 0 0 t 0 1307702 socket portreser 1147 root 1 u unix 0 xffff 88003787 cc 80 0 t 0 8369 /var/run/portres erve/socket rsyslogd 1154 root 0 u unix 0 xffff 880079 f 609 c 0 0 t 0 1272991 /dev/log acpid 1256 root 4 u unix 0 xffff 880037 e 460 c 0 0 t 0 8758 /var/run/acpid. s ocket
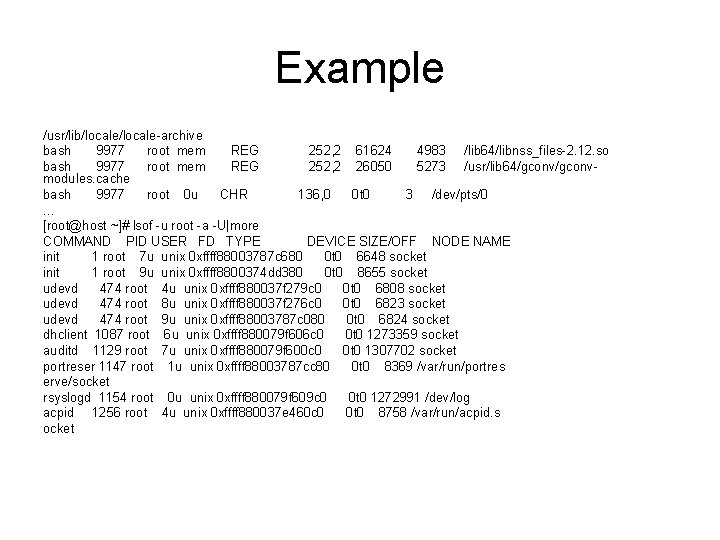
![Example roothost lsof ddevmore COMMAND PID USER FD TYPE DEVICE SIZEOFF NODE NAME Example [root@host ~]# lsof +d/dev|more COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-16.jpg)
Example [root@host ~]# lsof +d/dev|more COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME init 1 root 0 u CHR 1, 3 0 t 0 3593 /dev/null init 1 root 1 u CHR 1, 3 0 t 0 3593 /dev/null init 1 root 2 u CHR 1, 3 0 t 0 3593 /dev/null udevd 474 root 0 u CHR 1, 3 0 t 0 3593 /dev/null udevd 474 root 1 u CHR 1, 3 0 t 0 3593 /dev/null udevd 474 root 2 u CHR 1, 3 0 t 0 3593 /dev/null dhclient 1087 root 0 u CHR 1, 3 0 t 0 3593 /dev/null dhclient 1087 root 1 u CHR 1, 3 0 t 0 3593 /dev/null dhclient 1087 root 2 u CHR 1, 3 0 t 0 3593 /dev/null [root@host ~]# lsof -u root | grep bash |more bash 9977 root cwd DIR 252, 2 4096 19 /root bash 9977 root rtd DIR 252, 2 4096 2/ bash 9977 root txt REG 252, 2 938672 130759 /bin/bash 9977 root mem REG 252, 2 155696 58735 /lib 64/ld -2. 12. so bash 9977 root mem REG 252, 2 22536 58744 /lib 64/li bdl-2. 12. so
![Find Current Running PID pidof sx program s list only PID Find Current Running PID • pidof [-sx] program – s: list only PID –](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-17.jpg)
Find Current Running PID • pidof [-sx] program – s: list only PID – x: list more info Example: [root@host ~]# pidof init syslog 1

SELinux (Security Enhanced Linux) • NSA design to prevent configuration error • Include MAC (Mandatory Access control) in Linux DAC (Discretionary Access control): depends on process, root may not be God. • Control Process access resources privilege (e. g. network service is a also process) • Include security policy

SELinux Model • Subject: process • Object: file system • Policy: – Targeted: less restriction for host, more for network service – Strict: complete restriction • Security context (stored in both subject and object inside inode): similar to file system permission set up- subject must follow rules in Policy, then compare subject with object according to security context. If success, then subject can use object. Otherwise, it fails to use resource.
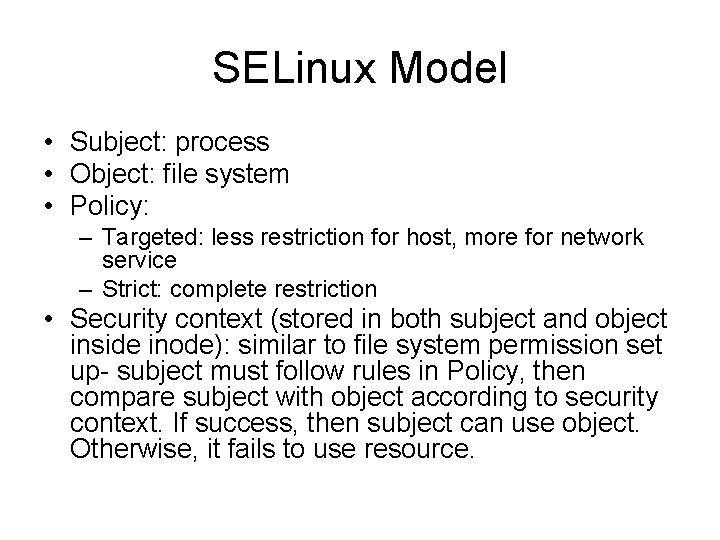
![Example Security context identitity role type roothost ls Z rw root systemu objectr Example- Security context (identitity: role: type) [root@host ~]# ls -Z -rw-------. root system_u: object_r:](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-20.jpg)
Example- Security context (identitity: role: type) [root@host ~]# ls -Z -rw-------. root system_u: object_r: admin_home_t: s 0 anaconda -ks. cfg -rw-r--r-- root ? catfile 2 -rw-r--r-- root ? catfile 3 drwxr-xr-x root ? tmp -rw-r--r-- root ? tmp 1

Security Context: Identity • Identity: for account info – Root – System_u: process for system – User_u: info for user

Security Context: Role • Role – Object_r: file/dir role – System_r: process role

Security Context: Type • Type (important for targeted Policy) – Type: for object – Domain: for subject

Relation: Identity, Role & Type Identity Role Meaning (targeted Policy) Root System_r permission obtained by root when login System_u System_r System running process User_u System_r Process for login user
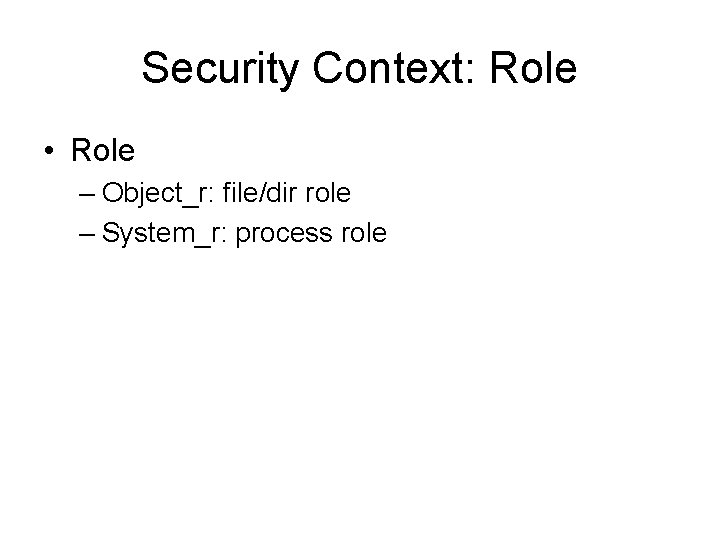
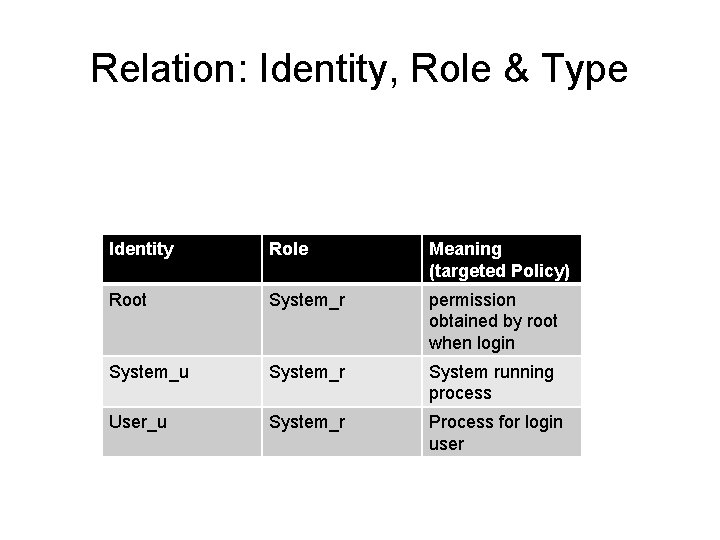
![Example roothost ll Zd usrsbinhttpd varwwwhtml rwxrxrx root systemu objectr httpdexect s 0 Example [root@host ~]# ll -Zd /usr/sbin/httpd /var/www/html -rwxr-xr-x. root system_u: object_r: httpd_exec_t: s 0](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-25.jpg)
Example [root@host ~]# ll -Zd /usr/sbin/httpd /var/www/html -rwxr-xr-x. root system_u: object_r: httpd_exec_t: s 0 /usr/sbin/httpd drwxr-xr-x. root system_u: object_r: httpd_sys_content_t: s 0 /var/www/html

Explain Both http & html are files (object_r) httpd is domain type: can execute html is object type: sys_content 1. Start executable file (w. httpd-exec_t) in /usr/sbin/httpd 2. Step 1 let subject owns httpd domain. In Policy, this domain allow to read httpd_sys_content_d object resource 3. Your web page put under /var/www/html directory so httpd process can read 4. Whether it can read successfully depends on Linux permission

Support SELinux Mode • enforcing: restrict domain/type • permissive: give warning only, for debug • disable: not using SELinux
![Check Supporting Mode roothost getenforce Disabled roothost getenforce Enforcing Check Supporting Mode [root@host ~]# getenforce Disabled [root@host ~]# getenforce Enforcing](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-28.jpg)
Check Supporting Mode [root@host ~]# getenforce Disabled [root@host ~]# getenforce Enforcing

Check Policy • sestatus – v: check /etc/sestatus. conf – b: list policy rule [root@host ~]# sestatus SELinux status: disabled
![Example roothost sestatus SELinux status enabled SELinuxfs mount selinux Current mode enforcing Mode Example [root@host ~]# sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-30.jpg)
Example [root@host ~]# sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode from config file: enforcing Policy version: 24 Policy from config file: targeted [root@host ~]# sestatus -b Policy booleans: abrt_anon_write off allow_console_login on allow_cvs_read_shadow off allow_daemons_dump_core on allow_daemons_use_tcp_wrapper off allow_daemons_use_tty on allow_domain_fd_use on allow_execheap off allow_execmem on allow_execmod on allow_execstack on allow_ftpd_anon_write off allow_ftpd_full_access off allow_ftpd_use_cifs off allow_ftpd_use_nfs off allow_gssd_read_tmp on allow_guest_exec_content off …
![Check SELinux Configuration File roothost vi etcselinuxconfig This file controls the state of Check SELinux Configuration File [root@host ~]# vi /etc/selinux/config# This file controls the state of](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-31.jpg)
Check SELinux Configuration File [root@host ~]# vi /etc/selinux/config# This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - SELinux is fully disabled. SELINUX=disabled # SELINUXTYPE= type of policy in use. Possible values are: # targeted - Only targeted network daemons are protected. # strict - Full SELinux protection. SELINUXTYPE=targeted

Start Up SELinux • $vi /etc/selinux/config Need 2 lines below: SELINUX=enforcing SELINUX=targeted • $vi /boot/grub/menu. lst Take away selinux=0 • Reboot
![Example roothost vi bootgrubmenu lst Take away selinux0 grub conf generated by Example [root@host ~]# vi /boot/grub/menu. lst Take away selinux=0 # grub. conf generated by](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-33.jpg)
Example [root@host ~]# vi /boot/grub/menu. lst Take away selinux=0 # grub. conf generated by anaconda # # Note that you do not have to rerun grub after making changes to this file # NOTICE: You have a /boot partition. This means that # all kernel and initrd paths are relative to /boot/, eg. # root (hd 0, 0) # kernel /vmlinuz-version ro root=/dev/vda 2 # initrd /initrd-[generic-]version. img #boot=/dev/vda default=0 timeout=5 splashimage=(hd 0, 0)/grub/splash. xpm. gz hiddenmenu title Scientific Linux (2. 6. 32 -131. 0. 15. el 6. x 86_64) root (hd 0, 0) kernel /vmlinuz-2. 6. 32 -131. 0. 15. el 6. x 86_64 ro root=UUID=52 ca 1 ca 3 -479 b-4 a 7 b-9 aeb-c 551765 e 786 f rd_NO_LUKS rd_NO_LVM rd_NO_MD rd_NO_DM LANG=en_US. UTF-8 SYSFONT=latarcyrheb-sun 16 KEYBOARDTYPE=pc KEYTABLE=us crashkernel=auto rhgb quiet initrd /initramfs-2. 6. 32 -131. 0. 15. el 6. x 86_64. img

Debug- switch between enforcing & permissive From enforcing to permissive: $setenforce 0 $getenforce Switch back: $setenforce 1 $getenforce
![Example roothost setenforce 0 roothost getenforce Permissive roothost setenforce 1 roothost Example [root@host ~]# setenforce 0 [root@host ~]# getenforce Permissive [root@host ~]# setenforce 1 [root@host](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-35.jpg)
Example [root@host ~]# setenforce 0 [root@host ~]# getenforce Permissive [root@host ~]# setenforce 1 [root@host ~]# getenforce Enforcing
![SELinux on Network Service Hands on Start Network Service roothost ps aux SELinux on Network Service. Hands on • Start Network Service [root@host ~]# ps aux](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-36.jpg)
SELinux on Network Service. Hands on • Start Network Service [root@host ~]# ps aux | grep httpd root 1612 0. 0 103228 840 pts/0 S+ 03: 53 0: 00 grep httpd [root@host ~]# /etc/init. d/httpd restart Stopping httpd: [FAILED] Starting httpd: [ OK ] [root@host ~]# pstree | grep httpd |-httpd---8*[httpd]
![SELinux on Network Service Hands on Cont roothost ps aux Z SELinux on Network Service. Hands on (Cont. ) [root@host ~]# ps aux -Z |](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-37.jpg)
SELinux on Network Service. Hands on (Cont. ) [root@host ~]# ps aux -Z | grep httpd unconfined_u: system_r: httpd_t: s 0 root 1639 0. 0 0. 3 215008 7632 ? Ss 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1641 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1642 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1643 0. 0 0. 3 216524 6764 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1644 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1645 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1646 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1647 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: system_r: httpd_t: s 0 apache 1648 0. 0 0. 3 216524 6760 ? S 03: 54 0: 00 /usr/sbin/httpd unconfined_u: unconfined_r: unconfined_t: s 0 -s 0: c 0. c 1023 root 1665 0. 0 103228 848 pts/0 S+ 03: 57 0: 00 grep httpd

SELinux on Network Service. Hands on (Cont. ) • Create web page under SELinux [root@host ~]# echo "My 1 st SELinux Test page. " > /var/www/html/index. html Check console web page using URL: http: //127. 0. 0. 1/ Seems correct. [root@host ~]# ll -Z /var/www/html/index. html -rw-r--r--. root unconfined_u: object_r: httpd_sys_content_t: s 0 /var/www/html/index. html

SELinux on Network Service. Hands on (Cont. ) • Security check for wrongly created page [root@host ~]# echo "My 2 nd Wrongly created SELinux web page. " > index. html [root@host ~]# rm /var/www/html/index. html rm: remove regular file `/var/www/html/index. html'? y [root@host ~]# mv index. html /var/www/html Check console web page using URL: http: //127. 0. 0. 1/ Forbidden error message [root@host ~]# ll -Z /var/www/html/index. html rw-r--r--. root unconfined_u: object_r: admin_home_t: s 0 /var/www/html/index. html

SELinux on Network Service. Hands on (Cont. ) • Fix Problem: (1) Use chcon [root@host ~]# chcon -t httpd_sys_content_t /var/www/html/index. html [root@host ~]# ll -Z /var/www/html/index. html -rw-r--r--. root unconfined_u: object_r: httpd_sys_content_t: s 0 /var/www/html/index. html

SELinux on Network Service. Hands on (Cont. ) • Fix Problem: (2) Use restorecon [root@host ~]# echo "My 3 rd Wrongly created SELinux web page. " > index. html You have new mail in /var/spool/mail/root [root@host ~]# rm /var/www/html/index. html rm: remove regular file `/var/www/html/index. html'? y [root@host ~]# mv index. html /var/www/html [root@host ~]# ll -Z /var/www/html/index. html rw-r--r--. root unconfined_u: object_r: admin_home_t: s 0 /var/www/html/index. html [root@host ~]# restorecon -Rv /var/www/html/index. html restorecon reset /var/www/html/index. html context unconfined_u: object_r: admin_home_t: s 0>system_u: object_r: httpd_sys_content_t: s 0
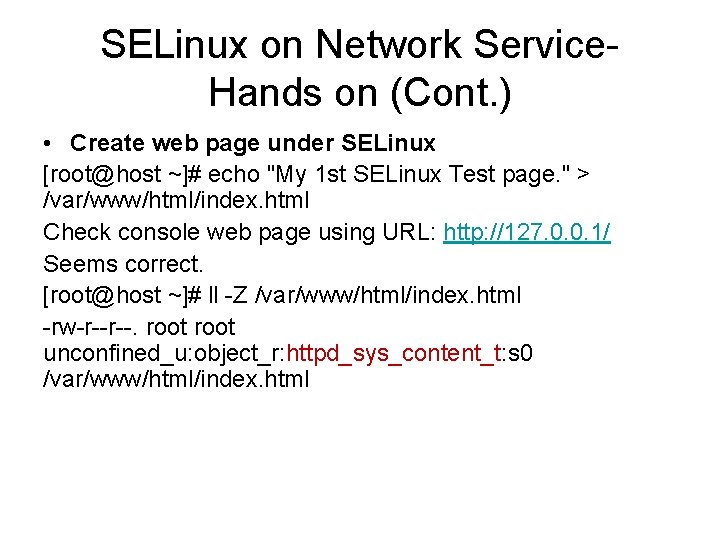
![SELinux Troubleshoot 1 Use setroubleshoot varlogmessages And use sealert roothost chkconfig list setroubleshoot SELinux Troubleshoot 1. Use setroubleshoot: /var/log/messages And use sealert [root@host ~]# chkconfig --list setroubleshoot](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-42.jpg)
SELinux Troubleshoot 1. Use setroubleshoot: /var/log/messages And use sealert [root@host ~]# chkconfig --list setroubleshoot error reading information on service setroubleshoot: No such file or directory If exists, #chkconfig setroubleshoot on #cat /var/log/messages | grep setroubleshoot Find docid #sealer –l docid
![SELinux Troubleshoot 2 Use auditd varlogaudit log And use audit 2 why roothost SELinux Troubleshoot 2. Use auditd: /var/log/audit. log And use audit 2 why [root@host ~]#](https://slidetodoc.com/presentation_image_h2/4ca69baf9bb5223895dd8b2666a5df58/image-43.jpg)
SELinux Troubleshoot 2. Use auditd: /var/log/audit. log And use audit 2 why [root@host ~]# chkconfig --list auditd 0: off 1: off 2: on 3: on 4: on 5: on 6: off #chkconfig auditd on (Use when 3: off, 5: off) [root@host ~]# audit 2 why < /var/log/audit. log -bash: audit 2 why: command not found

SELinux Policy&Rule Management • Policy Search #seinfo –b |grep httpd #sesearch –a –t httpd_sys_content_t #sesearch –s httpd_t –t httpd_* -a #sesearch –b httpd_enable_homdirs -a

SELinux Policy&Rule Management • Check and Modify Boolean Values #getsebool -a #getsebool httpd_enable_homdirs #setsebool –P httpd_enable_homdirs=0 #getsebool httpd_enable_homdirs

SELinux Policy&Rule Management • Check and Modify Security Context Defaults #semanage fcontext –l #mkdir /srv/samba #ll –Zd /srv/samba #semanage fcontext –l |grep ‘/srv’ #semanage fcontext –a –t public_content_t “/srv/samba(/. *)? ” #cat /etc/selinux/targeted/contexs/file_contexts/local #restorecon –Rv /srv/samba*