CHAPTER 7 Architectures and Protocols Based on Companion

CHAPTER 7 Architectures and Protocols Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 1
ARCHITECTURE • The blueprint for an entire network. • The network design philosophy and logical structure which affects: – – – Data throughout CPU utilization Cost recovery Reliability Compatibility • A manufacturer’s strategy for conning its hosts, terminals and communications equipment. Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 2
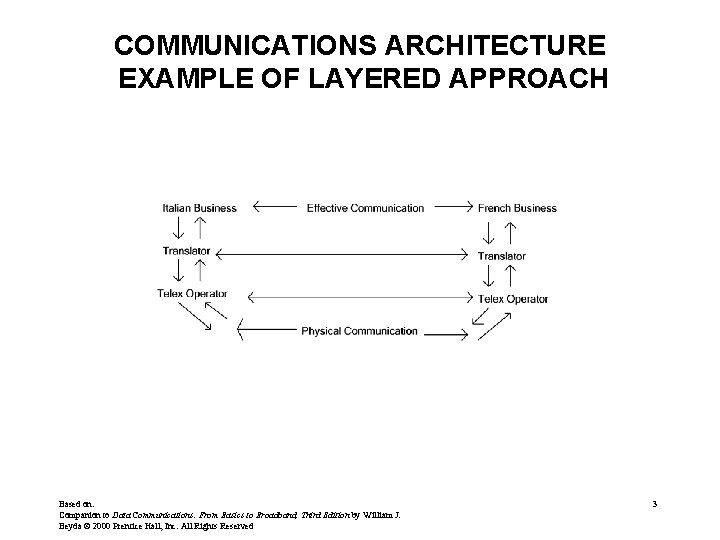
COMMUNICATIONS ARCHITECTURE EXAMPLE OF LAYERED APPROACH Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 3
PROTOCOLS • Architectures establish broad framework for connecting different network components • Protocols describe the specifics of those connections and how devices will communicate. • Examples of protocols: – How does the business person request the services of a translator? – Does the translated text have to be on a special form for the telex operator to send the message? – How do the two telex machines communicate (connection type, character code, etc. )? Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 4
COMMUNICATION/NETWORK PARADIGMS -- Batch Processing - • All work done by host and computer operator • Billing, order processing, jobs with sequential input • Remote Job Entry (RJE) extended job input over network to locations remote from host Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 5
COMMUNICATION/NETWORK PARADIGMS -- Terminal to Host - • • • Users instead of operators access host All work still done by host -- terminals slaved to host Mostly text-based applications Originally, terminals collocated with host Terminals could be extended within a building – port sharing devices, line splitters and LANs • Extended over wider areas using – remote intelligent controllers and the leased line networks • • Overall network is hierarchical in nature with host at root IBM was king of Terminal-to-Host architectures – BSC Protocol (data link layer 2 protocol) – SNA Architecture with SDLC Protocol for layer 2 • • OSI model developed primarily for this paradigm Introduction of PCs and terminal emulation software Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 6
COMMUNICATION/NETWORK PARADIGMS -- Peer to Peer - • Required by increase in distributed databases and smaller computers (e. g. , minicomputers & PCs) • Originally designed for two hosts or two terminals to communicate • Both devices on equal footing. No master/slave relationship • Most often used for file transfers or sharing – Early application for local area networks • SNA was updated with new higher layer protocols to enable P 2 P communications – Advanced Peer to Peer Networking (2 nd Generation SNA) – Implemented using LU 6. 2 (aka APPC - Advanced Program to Program Communication) protocol in session layer (5) Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 7
COMMUNICATION/NETWORK PARADIGMS -- Client/Server - • Distributed form of computing w/ multiple destinations • Move away from master/slave relationship • Terminals (now PCs) able to process information – Client software runs on PC – Client requests information to process from host (now server) – Use of GUI applications to present and manipulate data • Less communication with server required – Longer messages appear – Traffic more infrequent and bursty • Originally found in local area network environments • Could be implemented over wider areas using packet switching - hierarchy not flexible enough Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 8
COMMUNICATION/NETWORK PARADIGMS -- Internet-Based Communication - • Can use the internet to provide connections for each paradigm – Terminal to Host • Telnet - terminal access to text-based applications – Peer to Peer • Napster - file transfer from one PC to another • Rendezvous - chat program without server/controller – Client / Server • FTP - file transfer • POP, SMTP - email programs like Netscape & Outlook • HTTP - transfer of web pages • Based on TCP/IP packet network technology Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 9
A UNIVERSAL ARCHITECTURE? • Each manufacturer has its own architecture • Need for a single architecture to connect equipment from different manufacturers • International Standards Organization (ISO) developed a general architecture model known as the “Open Systems Interconnection” or OSI Model • Provides a common method for describing communication architectures, tasks and functions. • Meant to help connect equipment from multiple manufacturers – Supported in principle but not in fact – Often referred to as a “Reference Model” Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 10
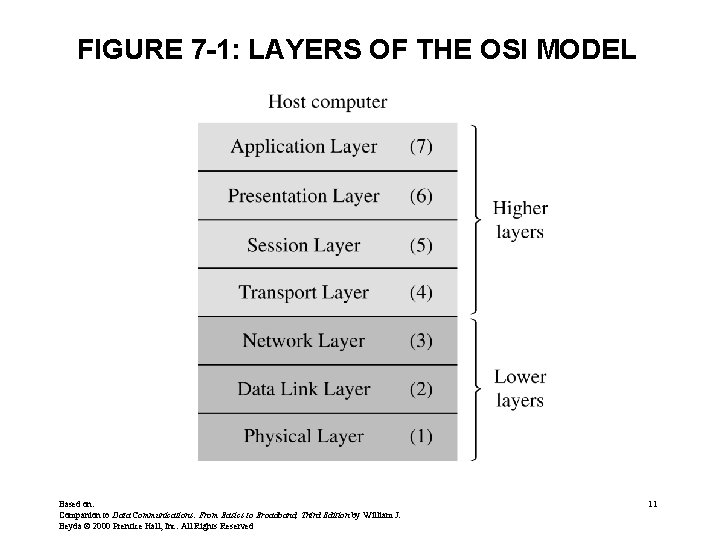
FIGURE 7 -1: LAYERS OF THE OSI MODEL Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 11
OSI MODEL • PHYSICAL LAYER (1) – Bits physically transmitted between devices – Typically defined by an interface specification • e. g. , RS-232, RS-449, USB, Ethernet – Only layer requiring hardware implementation • DATA LINK LAYER (2) – Assembles /disassembles bits into characters, blocks or frames – Ensures error-free transmission • Detects errors • Requests retransmission as needed Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 12
OSI MODEL (CONTINUED) • NETWORK LAYER (3) – Determines route of messages through network – Understands physical network topology • TRANSPORT LAYER (4) – Isolates upper layers from lower layers – Breaks message into blocks and reassembles as needed – Converts addresses from local scheme to match actual network Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 13
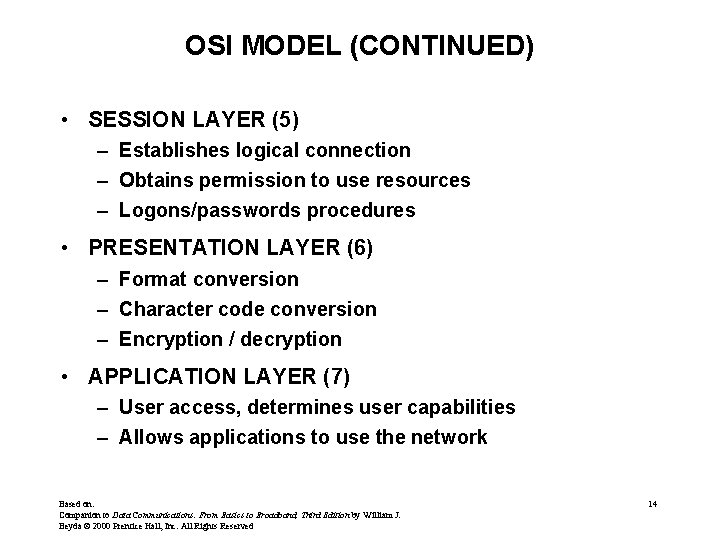
OSI MODEL (CONTINUED) • SESSION LAYER (5) – Establishes logical connection – Obtains permission to use resources – Logons/passwords procedures • PRESENTATION LAYER (6) – Format conversion – Character code conversion – Encryption / decryption • APPLICATION LAYER (7) – User access, determines user capabilities – Allows applications to use the network Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 14
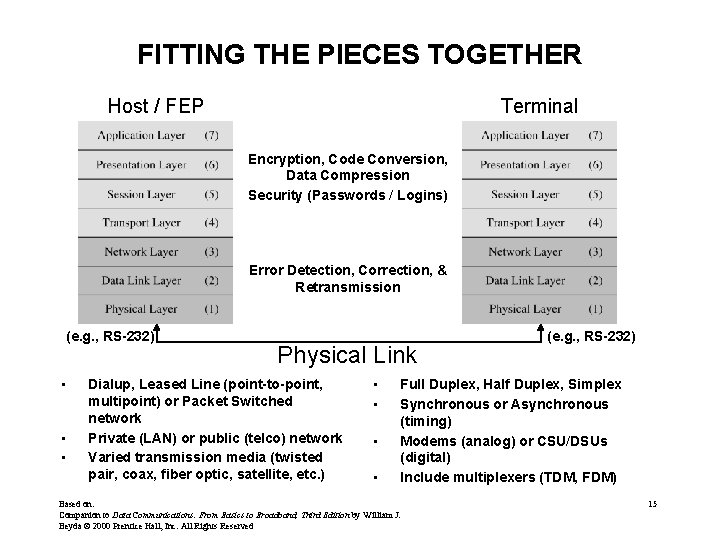
FITTING THE PIECES TOGETHER Host / FEP Terminal Encryption, Code Conversion, Data Compression Security (Passwords / Logins) Error Detection, Correction, & Retransmission (e. g. , RS-232) • • • Physical Link Dialup, Leased Line (point-to-point, multipoint) or Packet Switched network Private (LAN) or public (telco) network Varied transmission media (twisted pair, coax, fiber optic, satellite, etc. ) • • (e. g. , RS-232) Full Duplex, Half Duplex, Simplex Synchronous or Asynchronous (timing) Modems (analog) or CSU/DSUs (digital) Include multiplexers (TDM, FDM) Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 15
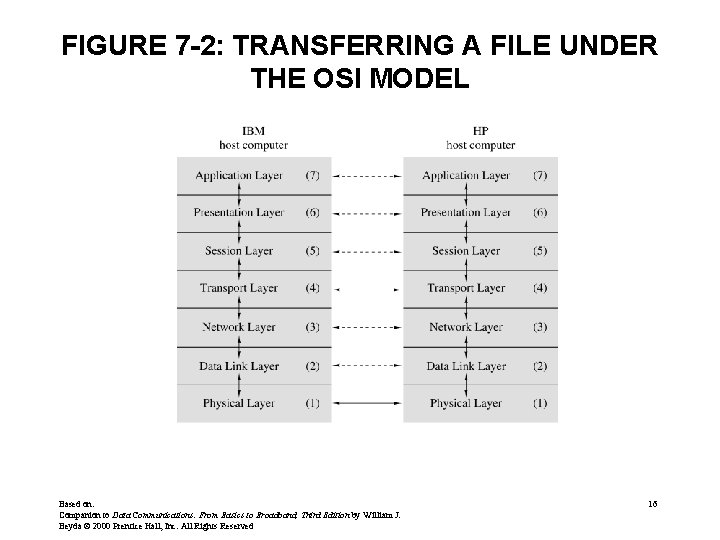
FIGURE 7 -2: TRANSFERRING A FILE UNDER THE OSI MODEL Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 16
OSI FILE TRANSFER EXAMPLE - IBM HOST • Application Layer (7) – User issues command to transfer file to HP host • Presentation Layer (6) – File reformatted or encrypted if necessary • Session Layer (5) – Requests connection to HP Host • Transport Layer (4) – Breaks file into manageable blocks • Network Layer (3) – Selects route for data. Addresses each block • Data Link Layer (2) – Adds error checking information (e. g. , checksum) • Physical Layer (1) – Transmits bits across communication channel Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 17
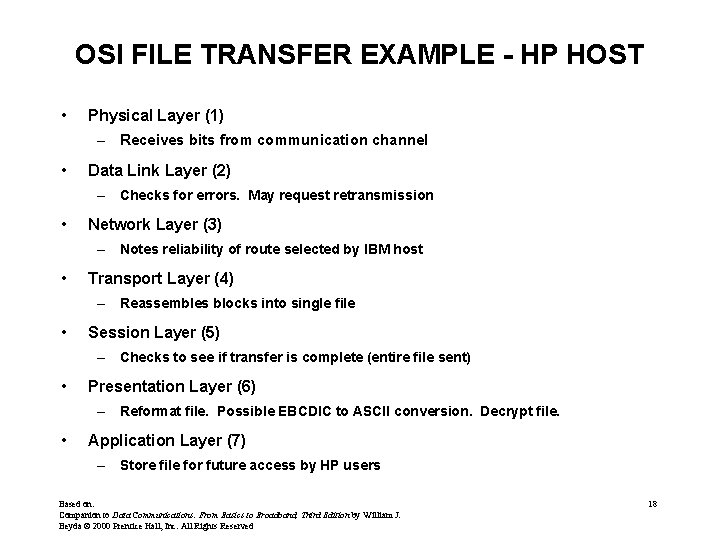
OSI FILE TRANSFER EXAMPLE - HP HOST • Physical Layer (1) – Receives bits from communication channel • Data Link Layer (2) – Checks for errors. May request retransmission • Network Layer (3) – Notes reliability of route selected by IBM host • Transport Layer (4) – Reassembles blocks into single file • Session Layer (5) – Checks to see if transfer is complete (entire file sent) • Presentation Layer (6) – Reformat file. Possible EBCDIC to ASCII conversion. Decrypt file. • Application Layer (7) – Store file for future access by HP users Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 18
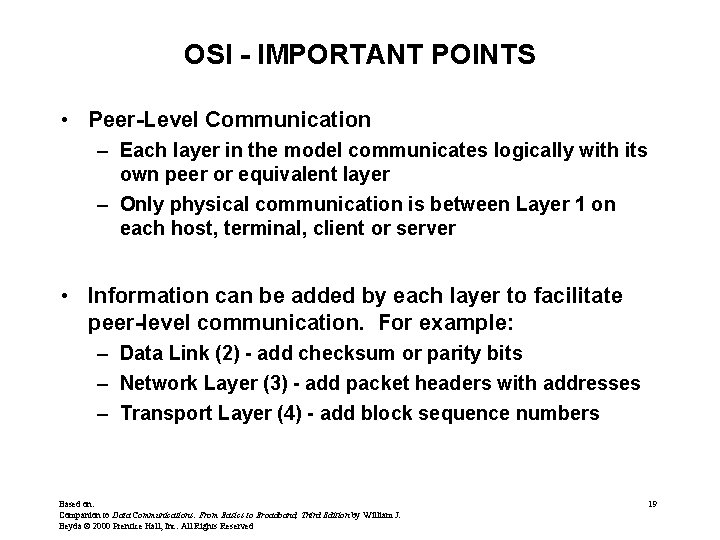
OSI - IMPORTANT POINTS • Peer-Level Communication – Each layer in the model communicates logically with its own peer or equivalent layer – Only physical communication is between Layer 1 on each host, terminal, client or server • Information can be added by each layer to facilitate peer-level communication. For example: – Data Link (2) - add checksum or parity bits – Network Layer (3) - add packet headers with addresses – Transport Layer (4) - add block sequence numbers Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 19
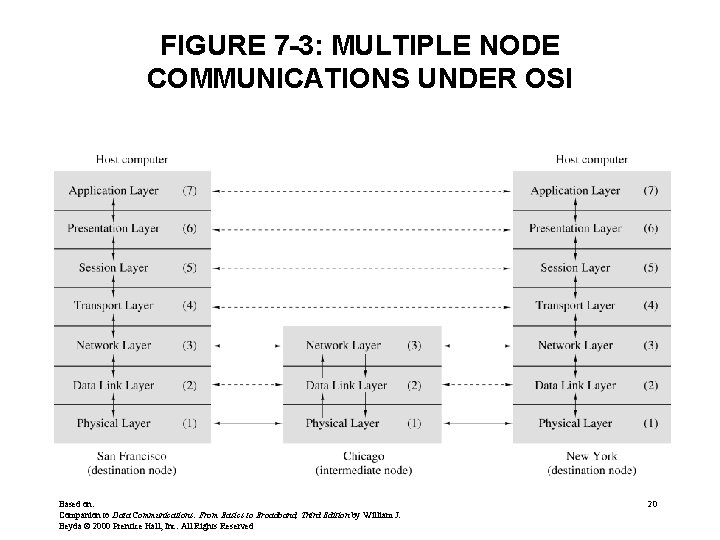
FIGURE 7 -3: MULTIPLE NODE COMMUNICATIONS UNDER OSI Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 20
HIERARCHICAL NETWORKS • Terminal to Host Paradigm – Logical connection between user and application – Physical connection between host and terminal • Message intensive – Contention for physical link can be a problem – Use Polling and Selecting to control access to physical link • Use error detection with retransmission as error control approach • Number of proprietary architectures to choose from: Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 21
IBM SNA • Systems Network Architecture • Developed in 1974 • Originally hierarchical for terminal/host networking • Scalable architecture (allows for growth) • Includes sophisticated network management functions • Like OSI model, SNA has seven layers – Some layers differ in specific functions Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 22
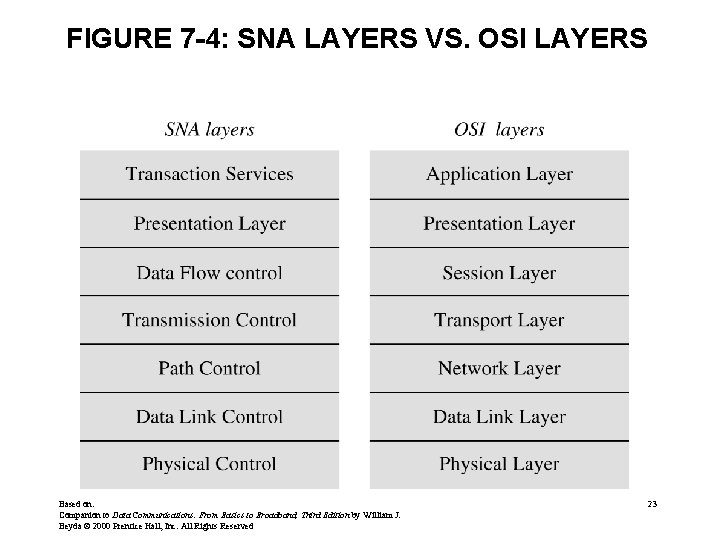
FIGURE 7 -4: SNA LAYERS VS. OSI LAYERS Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 23
SNA (cont. ) • Separates users from the network – Users can be people or application programs – Users don’t need to know how network functions • Physical Components of an SNA network – – Host Processor (host computers) Workstations (terminals) Communications controller (similar to FEP) Cluster controllers (similar to remote intelligent contr. ) • Major components of network organized as nodes Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 24
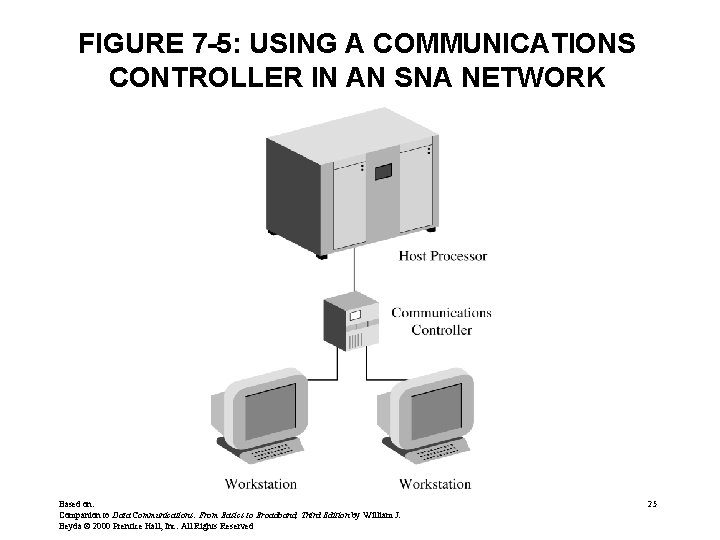
FIGURE 7 -5: USING A COMMUNICATIONS CONTROLLER IN AN SNA NETWORK Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 25
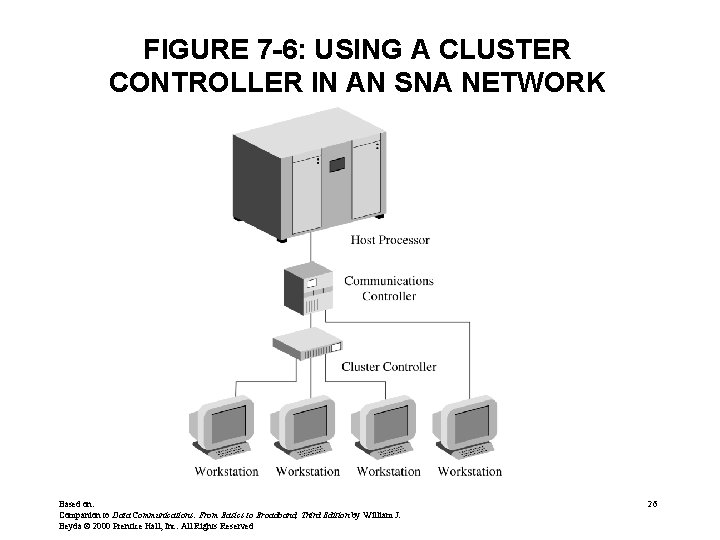
FIGURE 7 -6: USING A CLUSTER CONTROLLER IN AN SNA NETWORK Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 26
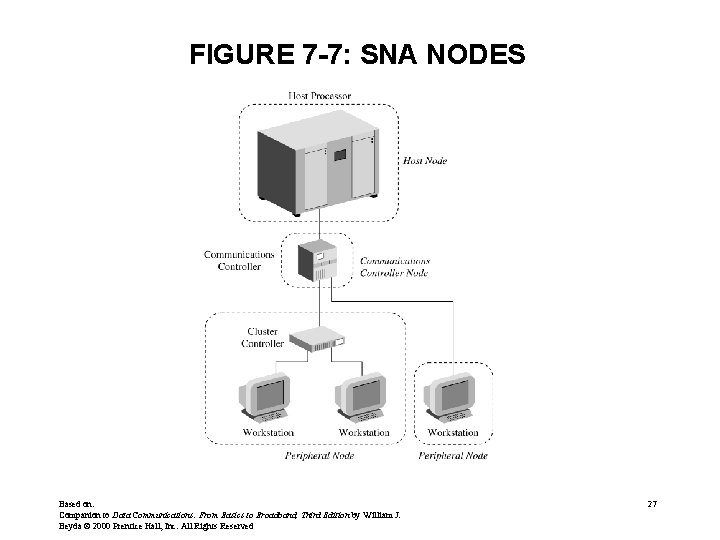
FIGURE 7 -7: SNA NODES Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 27
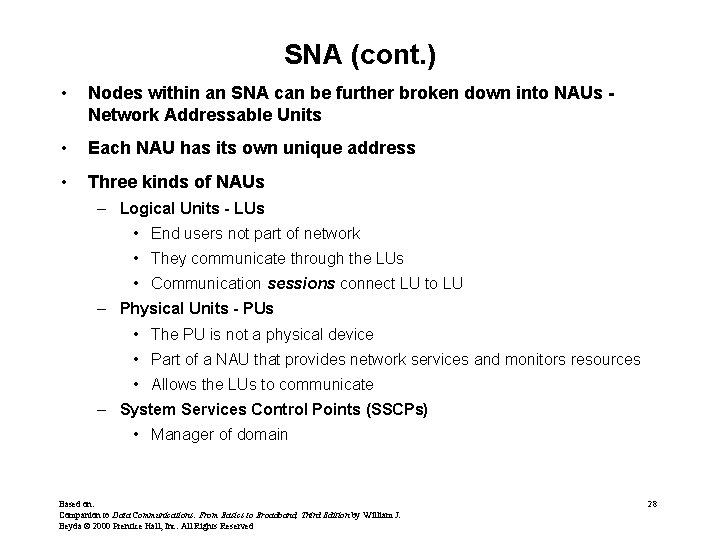
SNA (cont. ) • Nodes within an SNA can be further broken down into NAUs Network Addressable Units • Each NAU has its own unique address • Three kinds of NAUs – Logical Units - LUs • End users not part of network • They communicate through the LUs • Communication sessions connect LU to LU – Physical Units - PUs • The PU is not a physical device • Part of a NAU that provides network services and monitors resources • Allows the LUs to communicate – System Services Control Points (SSCPs) • Manager of domain Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 28
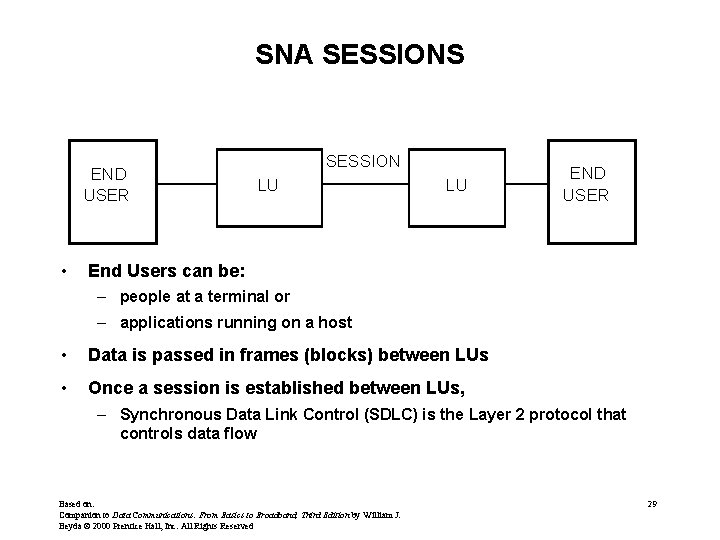
SNA SESSIONS END USER • SESSION LU LU END USER End Users can be: – people at a terminal or – applications running on a host • Data is passed in frames (blocks) between LUs • Once a session is established between LUs, – Synchronous Data Link Control (SDLC) is the Layer 2 protocol that controls data flow Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 29
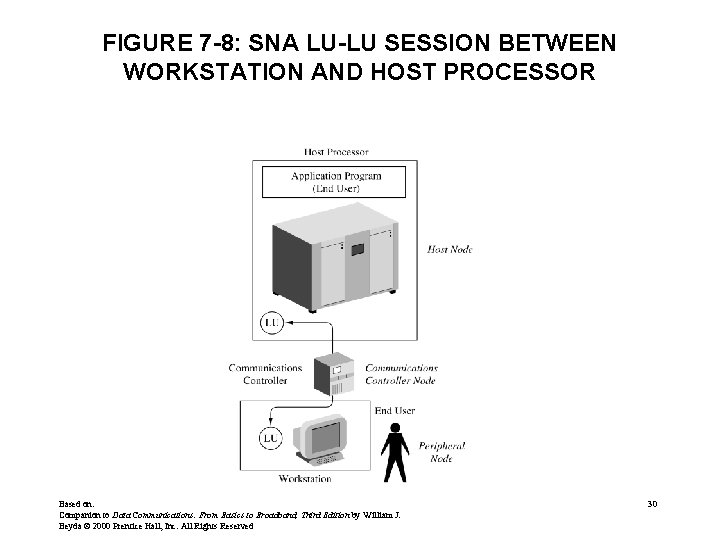
FIGURE 7 -8: SNA LU-LU SESSION BETWEEN WORKSTATION AND HOST PROCESSOR Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 30
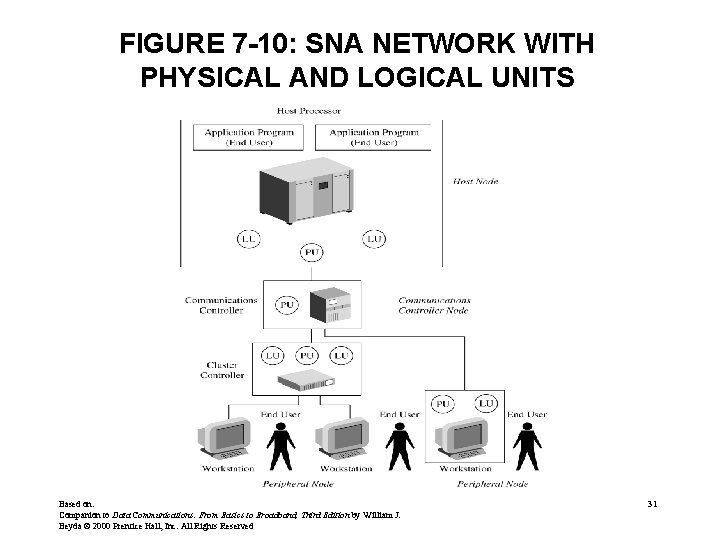
FIGURE 7 -10: SNA NETWORK WITH PHYSICAL AND LOGICAL UNITS Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 31
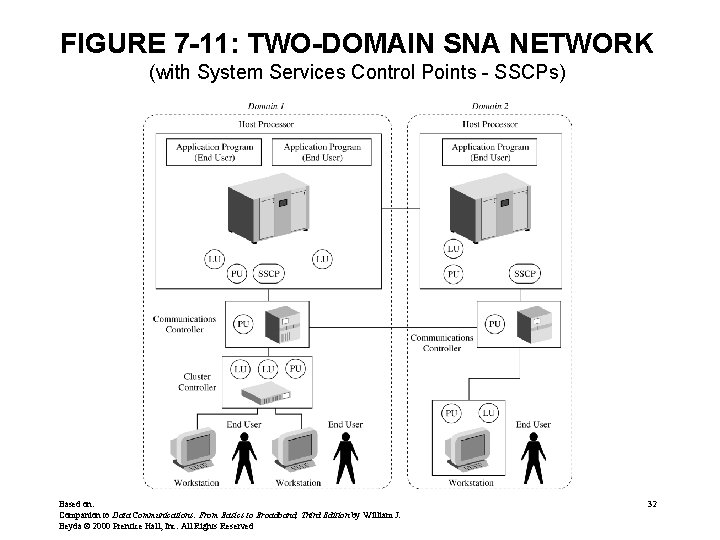
FIGURE 7 -11: TWO-DOMAIN SNA NETWORK (with System Services Control Points - SSCPs) Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 32

POLLING & SELECTING • Selecting: Asking terminal if its ready to receive data – Terminal replies with status • Polling: Asking terminal it wants to transmit data – Roll Call Polling • 1, wait, 2, wait, 3, wait, 4, wait. . . etc – Fast Select Polling • 1, 2, 3, 4, 5, wait, 6, 7, 8, 9, 10, wait, 11, 12, etc – Hub Go Ahead Polling • Terminals/Nodes pass polling message to each other, freeing up host Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 33
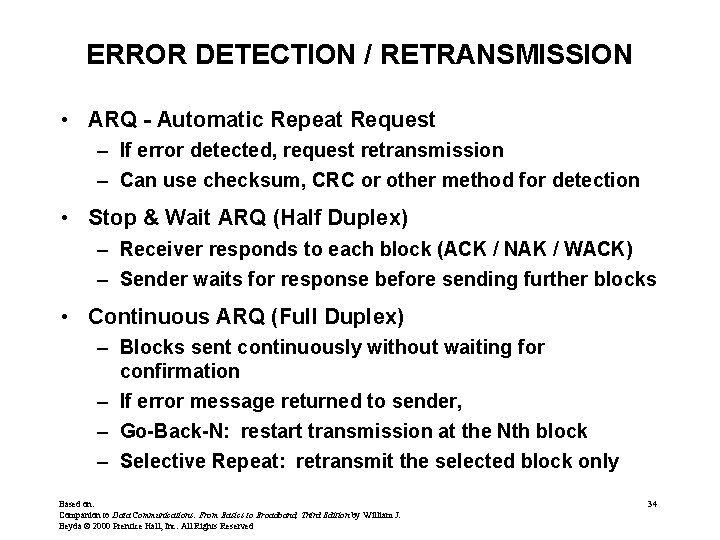
ERROR DETECTION / RETRANSMISSION • ARQ - Automatic Repeat Request – If error detected, request retransmission – Can use checksum, CRC or other method for detection • Stop & Wait ARQ (Half Duplex) – Receiver responds to each block (ACK / NAK / WACK) – Sender waits for response before sending further blocks • Continuous ARQ (Full Duplex) – Blocks sent continuously without waiting for confirmation – If error message returned to sender, – Go-Back-N: restart transmission at the Nth block – Selective Repeat: retransmit the selected block only Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 34

BSC • Binary Synchronous Communications – Layer 2 - Data Link Control protocol – Character oriented • All messages use complete characters – Half duplex protocol – Supports EBCDIC, ASCII, and Transcode (rare 6 -bit code) – Stop-and-Wait ARQ (Automatic Repeat Request) – Error Checking • A block check character (BCC) in data frame contains error checking information • CRC is the most popular method for calculating the BCC. Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 35
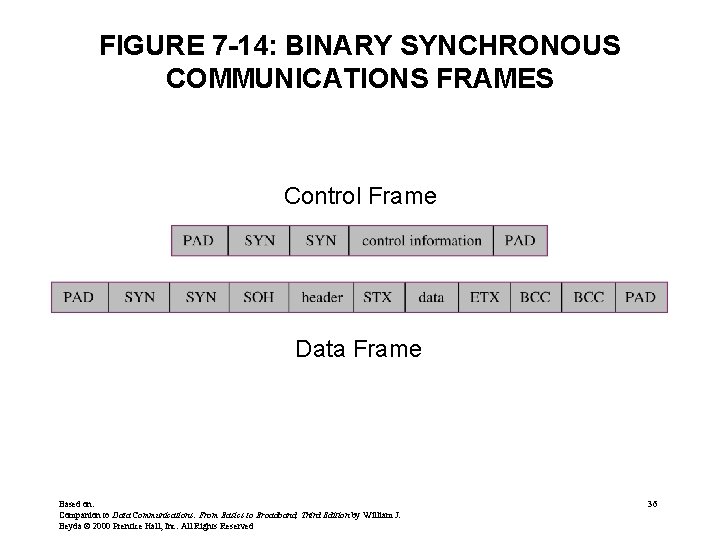
FIGURE 7 -14: BINARY SYNCHRONOUS COMMUNICATIONS FRAMES Control Frame Data Frame Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 36
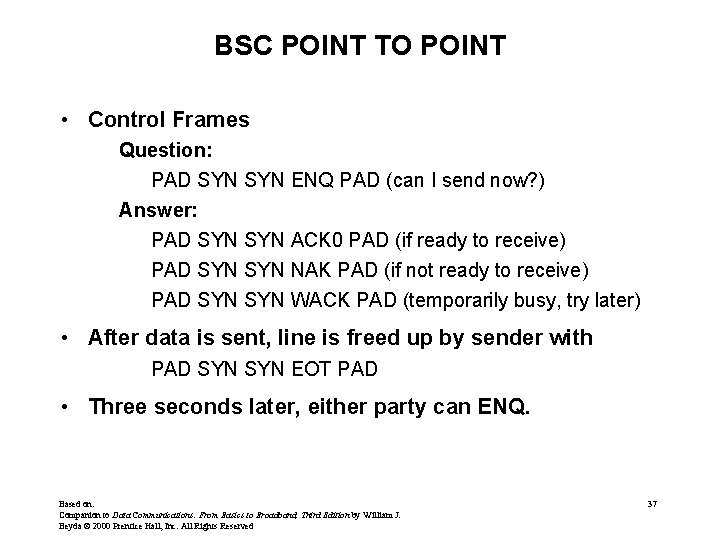
BSC POINT TO POINT • Control Frames Question: PAD SYN ENQ PAD (can I send now? ) Answer: PAD SYN ACK 0 PAD (if ready to receive) PAD SYN NAK PAD (if not ready to receive) PAD SYN WACK PAD (temporarily busy, try later) • After data is sent, line is freed up by sender with PAD SYN EOT PAD • Three seconds later, either party can ENQ. Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 37
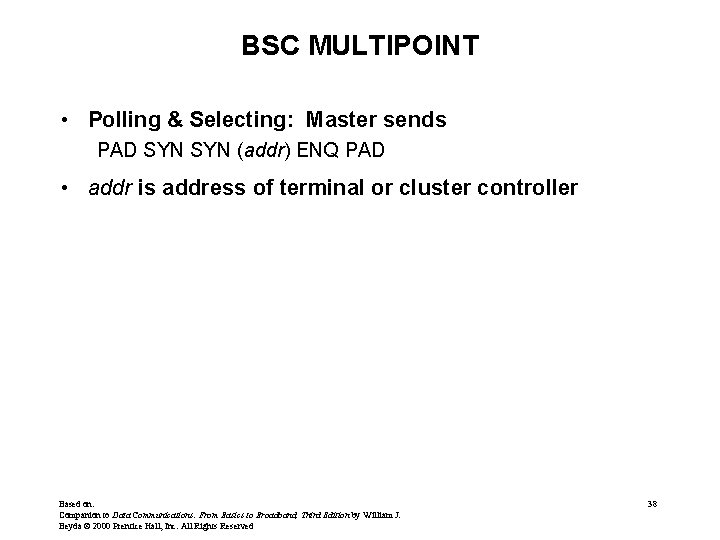
BSC MULTIPOINT • Polling & Selecting: Master sends PAD SYN (addr) ENQ PAD • addr is address of terminal or cluster controller Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 38

BSC MULTIPOINT (cont. ) • The polled/selected station can respond several ways: – If anything waiting to send to host: PAD SYN SOH (Header) STX (Data) ETX BCC PAD SYN EOT PAD (Finished sending) PAD SYN STX ENQ PAD (give me 2 seconds to get ready and then I'll start sending, but don't give the line to someone else) – Otherwise (nothing to send to host): PAD SYN ACK 0 PAD (ready to receive) PAD SYN NAK PAD (not ready to receive) PAD SYN WACK PAD (temporarily busy, try again later) Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 39
BSC (cont. ) • Major drawbacks – Stop-and-wait ARQ – Half duplex – Not well suited to transmission delays • What would happen with satellite link? Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 40
SDLC • Synchronous Data Link Control – Bit oriented protocol – Full or half duplex – Continuous go-back-N ARQ • Uses Frames: – Beginning and end of frame denoted by eight-bit flag • 01111110 • If you need to send the flag as part of the data, you send 011111010 instead • Data errors are checked using a sixteen bit CRC known as a Frame Check Sequence, or FCS Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 41
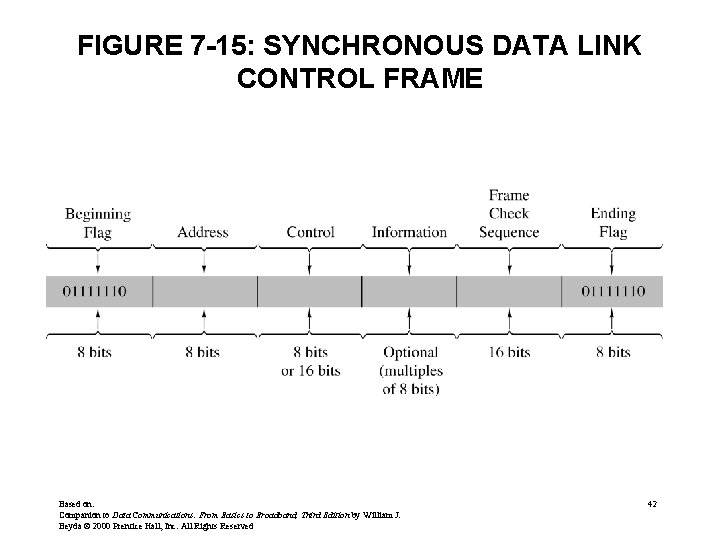
FIGURE 7 -15: SYNCHRONOUS DATA LINK CONTROL FRAME Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 42
SDLC (cont. ) • Control information sent in supervisory or unnumbered frames • Data is sent in an information or I-Frame – In full duplex, I-Frames are sent continuously, and acknowledgements are received continuously – No more than 7 or 127 I-Frames can be unacknowledged – In half duplex, every 7 or 127 I-Frames the line is turned around acknowledgements are sent Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 43

SDLC (cont. ) • For multipoint, – 1 primary station – Rest are secondary stations. – Secondary stations can not communicate with each other (only to primary). • Address field always refers to the secondary station Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 44
SDLC CONTROL BITS • Vary by type of frame (I, S, U) - examples include: • P/F Bit (P=Poll, F=Final) – When the primary sends something with the P/F bit turned on, it's a poll to the secondary (gives that station access to the line) – Secondary transmits with P/F bit off. When secondary station done transmitting, it turns the P/F bit back on, indicating that it is finished. • Mode Bits (2) – RR (Receiver ready) – RNR (Receiver not ready) – REJ (Reject) • Sequence numbers for frames (3 bits) Based on: Companion to Data Communications: From Basics to Broadband, Third Edition by William J. Beyda © 2000 Prentice Hall, Inc. All Rights Reserved 45
- Slides: 45