Chapter 6 Linux User Account Management All Examples


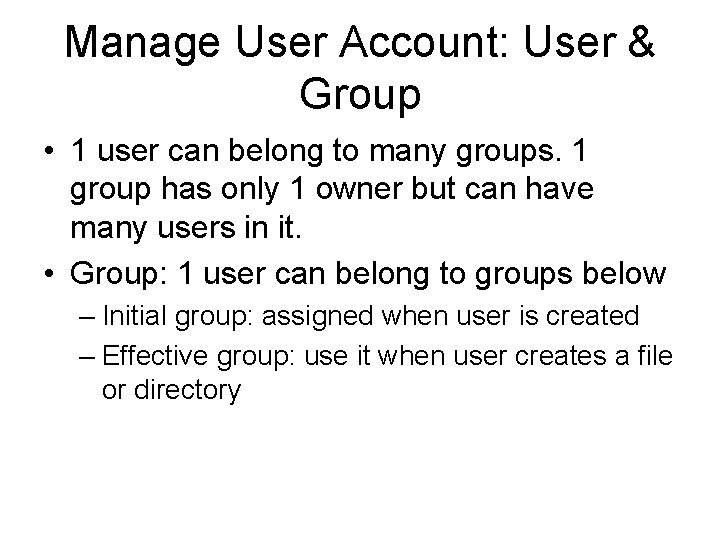

![Example [root@host ~]# ls -al /etc/skel total 32 drwxr-xr-x. 3 root 4096 Dec 26 Example [root@host ~]# ls -al /etc/skel total 32 drwxr-xr-x. 3 root 4096 Dec 26](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-6.jpg)


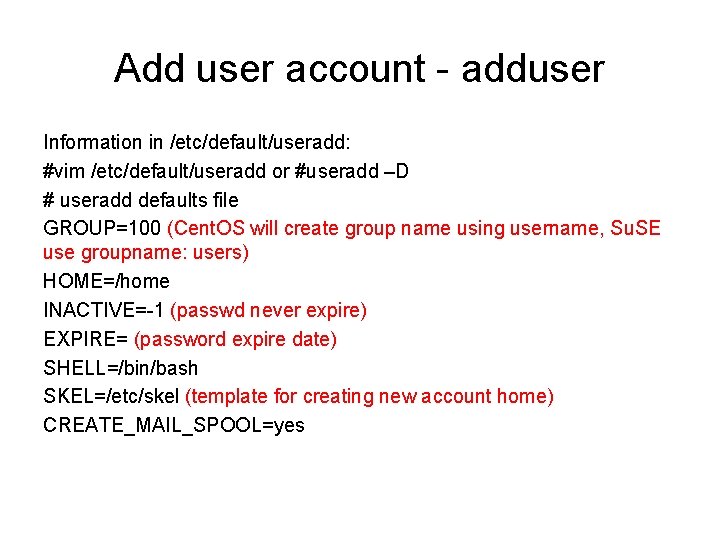
![Example [root@host ~]# useradd hduser [root@host ~]# grep hduser /etc/passwd /etc/shadow /etc/group /etc/passwd: hduser: Example [root@host ~]# useradd hduser [root@host ~]# grep hduser /etc/passwd /etc/shadow /etc/group /etc/passwd: hduser:](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-9.jpg)


![Example [root@host hduser]# passwd -S hduser PS 2015 -08 -22 0 99999 7 -1 Example [root@host hduser]# passwd -S hduser PS 2015 -08 -22 0 99999 7 -1](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-12.jpg)
![Password Aging • chage [-ld. EIMW] acct – l: list – d: col. 3 Password Aging • chage [-ld. EIMW] acct – l: list – d: col. 3](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-13.jpg)
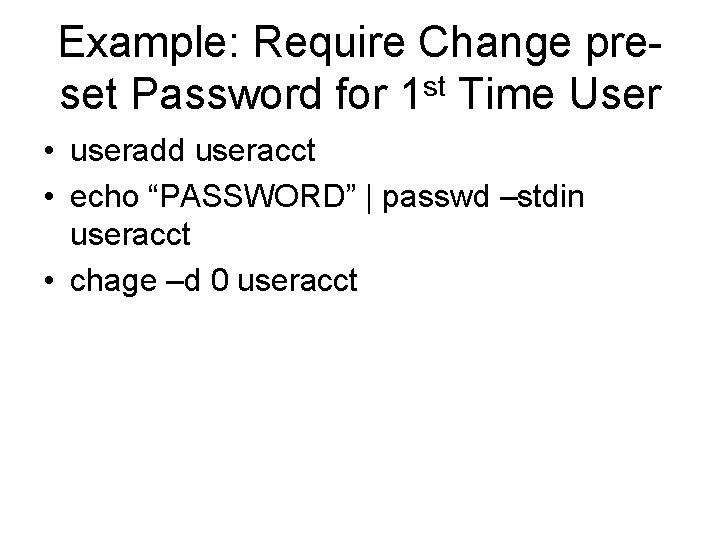
![Change User Password • passwd username (username’s passwd created by root) Example: [root@host ~]# Change User Password • passwd username (username’s passwd created by root) Example: [root@host ~]#](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-15.jpg)
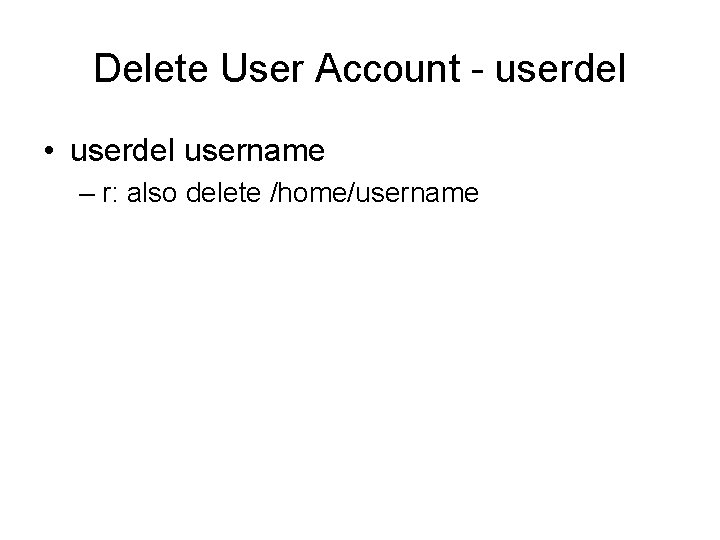
![Add Group- groupadd • groupadd [-g gid] [-r] groupname -r: for system group e. Add Group- groupadd • groupadd [-g gid] [-r] groupname -r: for system group e.](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-17.jpg)
![Update Group- groupmod • groupmod [-g gid] [-n groupname] groupname -n: modify to groupname Update Group- groupmod • groupmod [-g gid] [-n groupname] groupname -n: modify to groupname](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-18.jpg)

![Example [root@host~]# usermod -G hadoop hdusermod: group 'hadoop' does not exist [root@host hduser]# vim Example [root@host~]# usermod -G hadoop hdusermod: group 'hadoop' does not exist [root@host hduser]# vim](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-21.jpg)

![Linux ACL (Access Control List) • Start using ACL: [root@host ~]# mount -o remount, Linux ACL (Access Control List) • Start using ACL: [root@host ~]# mount -o remount,](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-26.jpg)

![Example: ACL to Username on File [root@host ~]# mkdir tmp [root@host ~]# cd tmp Example: ACL to Username on File [root@host ~]# mkdir tmp [root@host ~]# cd tmp](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-28.jpg)
![Example: ACL to Username on File (Cont. ) [root@host tmp]# setfacl -m u: hduser: Example: ACL to Username on File (Cont. ) [root@host tmp]# setfacl -m u: hduser:](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-29.jpg)
![ACL to Group on File • setfacl [-bk. Rd] [{-m|-x} g: groupname: perm] filename ACL to Group on File • setfacl [-bk. Rd] [{-m|-x} g: groupname: perm] filename](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-30.jpg)

![Example- visudo [root@slave 01 ~]# visudo ## Allow root to run any commands anywhere Example- visudo [root@slave 01 ~]# visudo ## Allow root to run any commands anywhere](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-33.jpg)
![Example- use sudo [root@slave 01 ~]# sudo -u sshd touch /tmp/mysshd [root@slave 01 ~]# Example- use sudo [root@slave 01 ~]# sudo -u sshd touch /tmp/mysshd [root@slave 01 ~]#](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-34.jpg)





![Example [root@host ~]# !! visudo [root@host ~]# su - pro 1 [pro 1@host ~]$ Example [root@host ~]# !! visudo [root@host ~]# su - pro 1 [pro 1@host ~]$](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-40.jpg)

![Login Authentication /etc/pam. d/login [root@slave 01 pam. d]# cat /etc/pam. d/login #%PAM-1. 0 auth Login Authentication /etc/pam. d/login [root@slave 01 pam. d]# cat /etc/pam. d/login #%PAM-1. 0 auth](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-42.jpg)

![Example [root@slave 01 pam. d]# cat /etc/pam. d/passwd #%PAM-1. 0 auth include system-auth account Example [root@slave 01 pam. d]# cat /etc/pam. d/passwd #%PAM-1. 0 auth include system-auth account](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-44.jpg)
![Example [root@slave 01 pam. d]# cat /etc/pam. d/system-auth #%PAM-1. 0 # This file is Example [root@slave 01 pam. d]# cat /etc/pam. d/system-auth #%PAM-1. 0 # This file is](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-45.jpg)

![Limit # of Users/File size vim /etc/security/limits. conf [root@host ~]# # - "soft" for Limit # of Users/File size vim /etc/security/limits. conf [root@host ~]# # - "soft" for](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-49.jpg)
![Limit # of users/file size ulimit -a [root@host ~]# core file size (blocks, -c) Limit # of users/file size ulimit -a [root@host ~]# core file size (blocks, -c)](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-50.jpg)
![Example- check nologin account [root@slave 01 pam. d]# pwck user 'ftp': directory '/var/ftp' does Example- check nologin account [root@slave 01 pam. d]# pwck user 'ftp': directory '/var/ftp' does](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-52.jpg)

- Slides: 53

Chapter 6 Linux User Account Management (All Examples Based on Fedora Linux) By C. Shing ITEC Dept Radford University

Objectives • Understand Linux account management • Understand create/delete/update user and group • Understand how to use ACL & sudo

Manage User Account: User & Group • 1 user can belong to many groups. 1 group has only 1 owner but can have many users in it. • Group: 1 user can belong to groups below – Initial group: assigned when user is created – Effective group: use it when user creates a file or directory

Add user account - adduser • useradd newusername (Bash) -u: UID -g: initial group -G: join all possible groups -m: homedirectory (without specify /home when using it) -r: system account (restricted)-s: shell (default /bin/bash) Example: useradd –m uhura (this creates a home directory /home/uhura) Note: useradd uses information in – /etc/default/useradd (create /etc/passwd and /etc/group files) – /etc/login. defs (create /etc/shadow file) – /etc/skel/* (create home directory files)

Add user account - adduser Information in /etc/default/useradd: #vim /etc/default/useradd or #useradd –D # useradd defaults file GROUP=100 (Cent. OS will create group name using username, Su. SE use groupname: users) HOME=/home INACTIVE=-1 (passwd never expire) EXPIRE= (password expire date) SHELL=/bin/bash SKEL=/etc/skel (template for creating new account home) CREATE_MAIL_SPOOL=yes
![Example roothost ls al etcskel total 32 drwxrxrx 3 root 4096 Dec 26 Example [root@host ~]# ls -al /etc/skel total 32 drwxr-xr-x. 3 root 4096 Dec 26](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-6.jpg)
Example [root@host ~]# ls -al /etc/skel total 32 drwxr-xr-x. 3 root 4096 Dec 26 2011. drwxr-xr-x. 97 root 12288 Aug 23 03: 06. . -rw-r--r--. 1 root 18 May 26 2011. bash_logout -rw-r--r--. 1 root 176 May 26 2011. bash_profile -rw-r--r--. 1 root 124 May 26 2011. bashrc drwxr-xr-x. 2 root 4096 Nov 23 2010. gnome 2 [root@host ~]# vim /etc/login. defs MAIL_DIR /var/spool/mail #MAIL_FILE. mail # Password aging controls: # # PASS_MAX_DAYS Maximum number of days a password may be used. # PASS_MIN_DAYS Minimum number of days allowed between password changes. # PASS_MIN_LEN Minimum acceptable password length. # PASS_WARN_AGE Number of days warning given before a password expires. # PASS_MAX_DAYS 99999 PASS_MIN_DAYS 0 PASS_MIN_LEN 5 PASS_WARN_AGE 7

Use useradd Completed Jobs • Insert username and related information in /etc/passwd • Insert username (1 st col. ) in /etc/shadow, locked(!!)/used(#) (2 nd col. ) {record passwd when changed(3 rd col. ), how long not allowed to change(4 th col. ), how long must be changed(5 th col. ), change warning days (col. 6), extended days(col. 7), expired date(col. 8), reserve(col. 9)} • Insert an entry in /etc/group • Create /home/username with 700 privilege

/etc/shadow Example: user hduser /etc/shadow: hduser: !!: 16669: 0: 99999: 7: : : Passwd: not created, locked by !! Acct created date: 16669 days from 1/1/1970 Passwd not allowed to change days=0 (can change anytime) how long must be changed=99999 (don’t need to change) change warning days=7 extended days: not set expired date: passwd not expired if not change; 0 if just lock account
![Example roothost useradd hduser roothost grep hduser etcpasswd etcshadow etcgroup etcpasswd hduser Example [root@host ~]# useradd hduser [root@host ~]# grep hduser /etc/passwd /etc/shadow /etc/group /etc/passwd: hduser:](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-9.jpg)
Example [root@host ~]# useradd hduser [root@host ~]# grep hduser /etc/passwd /etc/shadow /etc/group /etc/passwd: hduser: x: 500: 501: : /home/hduser: /bin/bash /etc/shadow: hduser: !!: 16669: 0: 99999: 7: : : /etc/group: hduser: x: 501: [root@host ~]# ls -l /home|grep hduser drwx------ 3 hduser 4096 Aug 22 14: 49 hduser [root@host ~]# grep hduser /etc/gshadow hduser: !: : [root@host ~]# groups hduser : hduser Note: UID 500 for hduser, group ID 501 for hduser, no password set for user: hduser (/etc/shadow) and no group password set for group: hduser (/etc/gshadow)

Update User Account - usermod • usermod username – – – c: modify real name in /etc/passwd d: modify home dir in /etc/passwd e: expire date, col. 8 in /etc/shadow f: col 7 in /etc/shadow g: modify GID (must exist in /etc/group beforehand) G: modify entries in /etc/group (must exist in /etc/group beforehand) – L: lock username – s: specify shell – U: unlock

Change User Password & Aging • passwd username (username’s passwd created by root) --stdin: using shell script -l: lock acct by add ! in /etc/shadow col. 2 -u: unlock acct -S: show info in /etc/shadow -n: col. 4 in /etc/shadow -x: col. 5 in /etc/shadow -w: col. 6 in /etc/shadow
![Example roothost hduser passwd S hduser PS 2015 08 22 0 99999 7 1 Example [root@host hduser]# passwd -S hduser PS 2015 -08 -22 0 99999 7 -1](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-12.jpg)
Example [root@host hduser]# passwd -S hduser PS 2015 -08 -22 0 99999 7 -1 (Password set, SHA 512 crypt. ) hduser’s passwd 60 days must change, 10 days expire [root@host hduser]# passwd –x 60 –I 10 hduser [root@host hduser]# echo “hduserpassword” | passwd –stdin hduser
![Password Aging chage ld EIMW acct l list d col 3 Password Aging • chage [-ld. EIMW] acct – l: list – d: col. 3](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-13.jpg)
Password Aging • chage [-ld. EIMW] acct – l: list – d: col. 3 in /etc/shadow – E: col 8 in /etc/shadow – I: col 7 in /etc/shadow – m: col. 4 in /etc/shadow – M: col. 5 in /etc/shadow – W: col. 6 in /etc/shadow

Example: Require Change preset Password for 1 st Time User • useradd useracct • echo “PASSWORD” | passwd –stdin useracct • chage –d 0 useracct
![Change User Password passwd username usernames passwd created by root Example roothost Change User Password • passwd username (username’s passwd created by root) Example: [root@host ~]#](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-15.jpg)
Change User Password • passwd username (username’s passwd created by root) Example: [root@host ~]# passwd hduser Changing password for user hduser. New password: BAD PASSWORD: it is based on a dictionary word BAD PASSWORD: is too simple Retype new password: passwd: all authentication tokens updated successfully. [root@host ~]# su hduser [hduser@host root]$ cd [hduser@host ~]$ pwd /home/hduser

Delete User Account - userdel • userdel username – r: also delete /home/username
![Add Group groupadd groupadd g gid r groupname r for system group e Add Group- groupadd • groupadd [-g gid] [-r] groupname -r: for system group e.](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-17.jpg)
Add Group- groupadd • groupadd [-g gid] [-r] groupname -r: for system group e. g groupadd –r security
![Update Group groupmod groupmod g gid n groupname groupname n modify to groupname Update Group- groupmod • groupmod [-g gid] [-n groupname] groupname -n: modify to groupname](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-18.jpg)
Update Group- groupmod • groupmod [-g gid] [-n groupname] groupname -n: modify to groupname

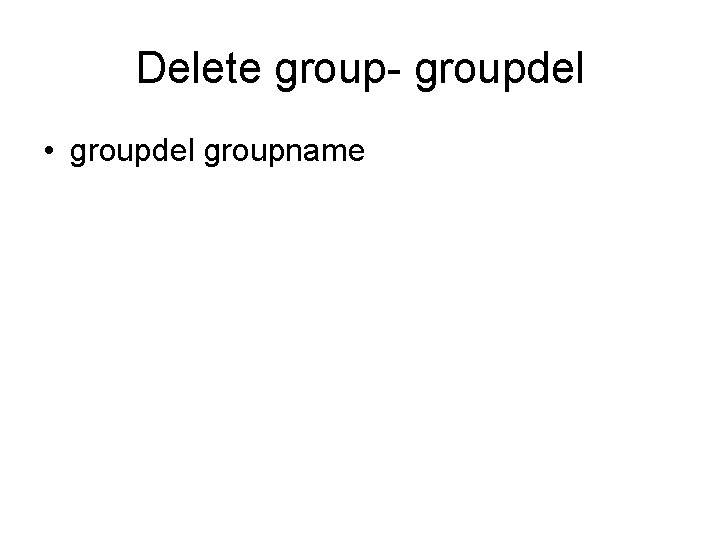
Delete group- groupdel • groupdel groupname

Change Group Password • You may use • gpasswd groupname to set group password (this will add an entry to /etc/gshadow)
![Example roothost usermod G hadoop hdusermod group hadoop does not exist roothost hduser vim Example [root@host~]# usermod -G hadoop hdusermod: group 'hadoop' does not exist [root@host hduser]# vim](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-21.jpg)
Example [root@host~]# usermod -G hadoop hdusermod: group 'hadoop' does not exist [root@host hduser]# vim /etc/group #Add the hadoop line below: hduser: x: 501: hadoop: x: 502: [hduser@host ~]$ groups hduser [hduser@host ~]$ touch tmp 1 [hduser@host ~]$ ls -l -rw-rw-r-- 1 hduser 0 Aug 22 16: 05 tmp 1 [root@host hduser]# vi /etc/group [root@host hduser]# usermod -G hadoop hduser [root@hos hduser]# groups hduser : hduser hadoop [root@host hduser]# su hduser [hduser@host ~]$ touch tmp 2 [hduser@host ~]$ ls -l tmp* -rw-rw-r-- 1 hduser 0 Aug 22 16: 05 tmp 1 -rw-rw-r-- 1 hduser 0 Aug 22 16: 15 tmp 2

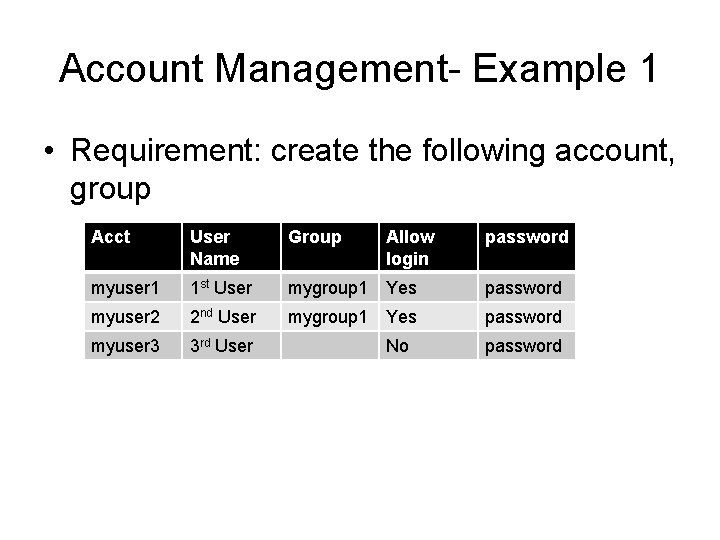
Account Management- Example 1 • Requirement: create the following account, group Acct User Name Group Allow login password myuser 1 1 st User mygroup 1 Yes password myuser 2 2 nd User mygroup 1 Yes password myuser 3 3 rd User No password

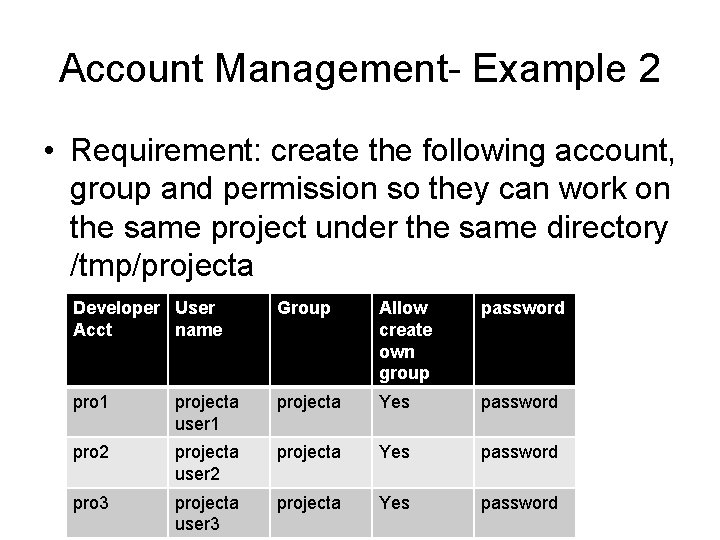
Account Management- Example 2 • Requirement: create the following account, group and permission so they can work on the same project under the same directory /tmp/projecta Developer User Acct name Group Allow create own group password pro 1 projecta user 1 projecta Yes password pro 2 projecta user 2 projecta Yes password pro 3 projecta user 3 projecta Yes password

Question: Account Management - Example 2 • How to set up an assistant: myuser 1 who can be in the group: projecta and can read all files, but not making changes? useradd –G projecta –c “project assistant” myuser 1 echo “password” | passwd –stdin myuser 1 • Solution: use ACL

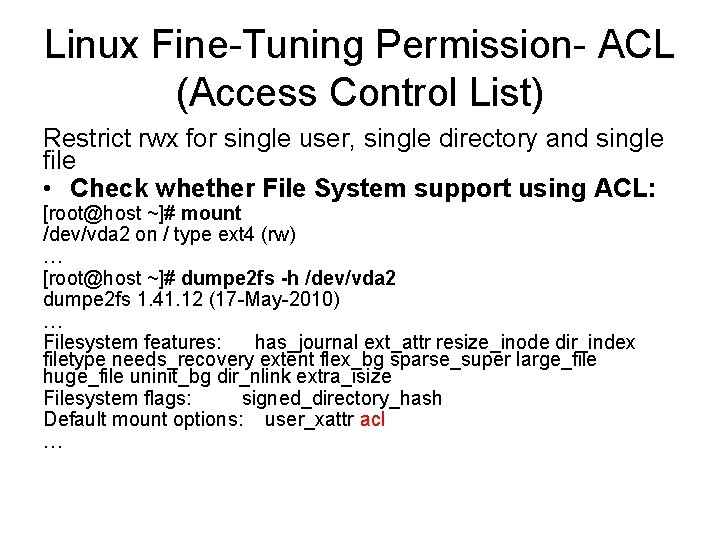
Linux Fine-Tuning Permission- ACL (Access Control List) Restrict rwx for single user, single directory and single file • Check whether File System support using ACL: [root@host ~]# mount /dev/vda 2 on / type ext 4 (rw) … [root@host ~]# dumpe 2 fs -h /dev/vda 2 dumpe 2 fs 1. 41. 12 (17 -May-2010) … Filesystem features: has_journal ext_attr resize_inode dir_index filetype needs_recovery extent flex_bg sparse_super large_file huge_file uninit_bg dir_nlink extra_isize Filesystem flags: signed_directory_hash Default mount options: user_xattr acl …
![Linux ACL Access Control List Start using ACL roothost mount o remount Linux ACL (Access Control List) • Start using ACL: [root@host ~]# mount -o remount,](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-26.jpg)
Linux ACL (Access Control List) • Start using ACL: [root@host ~]# mount -o remount, acl / [root@host ~]# mount /dev/vda 2 on / type ext 4 (rw, acl). . If you want to use ACL from now on after reboot, use [root@host ~]# vim /etc/fstab UUID=52 ca 1 ca 3 -479 b-4 a 7 b-9 aeb-c 551765 e 786 f / ext 4 defaults, acl 11

Set Up ACL: User Access File/Directory Permission • Check ACL: getfacl filename • Set ACL to username: setfacl [-bk. Rd] [{-m|-x} u: username: perm] filename -x: delete u: username: perm -b: remove perm -k: remove default perm -R: recursively for directory -d: for directory only
![Example ACL to Username on File roothost mkdir tmp roothost cd tmp Example: ACL to Username on File [root@host ~]# mkdir tmp [root@host ~]# cd tmp](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-28.jpg)
Example: ACL to Username on File [root@host ~]# mkdir tmp [root@host ~]# cd tmp [root@host tmp]# pwd /root/tmp [root@host tmp]# touch acl_testfile 1 [root@host tmp]# ll acl_testfile 1 (or ls –l acl_testfile 1) -rw-r--r-- 1 root 0 Aug 23 04: 17 acl_testfile 1 [root@host tmp]# getfacl acl_testfile 1 # file: acl_testfile 1 # owner: root # group: root user: : rwgroup: : r-other: : r--
![Example ACL to Username on File Cont roothost tmp setfacl m u hduser Example: ACL to Username on File (Cont. ) [root@host tmp]# setfacl -m u: hduser:](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-29.jpg)
Example: ACL to Username on File (Cont. ) [root@host tmp]# setfacl -m u: hduser: rx acl_testfile 1 [root@host tmp]# ll acl_testfile 1 -rw-r-xr--+ 1 root 0 Aug 23 04: 17 acl_testfile 1 [root@host tmp]# setfacl -m u: : rwx acl_testfile 1 [root@host tmp]# ll acl_testfile 1 -rwxr-xr--+ 1 root 0 Aug 23 04: 17 acl_testfile 1 [root@hosttmp]# getfacl acl_testfile 1 # file: acl_testfile 1 # owner: root # group: root user: : rwx user: hduser: r-x group: : r-mask: : r-x other: : r--
![ACL to Group on File setfacl bk Rd mx g groupname perm filename ACL to Group on File • setfacl [-bk. Rd] [{-m|-x} g: groupname: perm] filename](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-30.jpg)
ACL to Group on File • setfacl [-bk. Rd] [{-m|-x} g: groupname: perm] filename Example: [root@host tmp]# setfacl -m g: hadoop: rx acl_testfile 1 [root@host tmp]# getfacl acl_testfile 1 # file: acl_testfile 1 # owner: root # group: root user: : rwx user: hduser: r-x group: : r-group: hadoop: r-x mask: : r-x other: : r--

Effective Permission - Use Mask: Limit User&Group Permission in ACL setfacl –m m: perm filename Example: ACL to Group on File [root@host tmp]# setfacl -m m: r acl_testfile 1 [root@host tmp]# getfacl acl_testfile 1 # file: acl_testfile 1 # owner: root # group: root user: : rwx user: hduser: r-x #effective: r-group: hadoop: r-x #effective: r-mask: : r-other: : r--

Share Management- sudo • All sudoers accounts and jobs are specified in /etc/sudoers Format: sudoer source_host=(su_user) command myuser 1 ALL=(root) /usr/bin/passwd Note: myuser 1 can use own passwd to substitute as root and issue $sudo passwd username from any host • Use visudo to edit the file • 1 st time use sudo, may need to enter passwd. Within 5 min. use sudo again, no need to enter again.
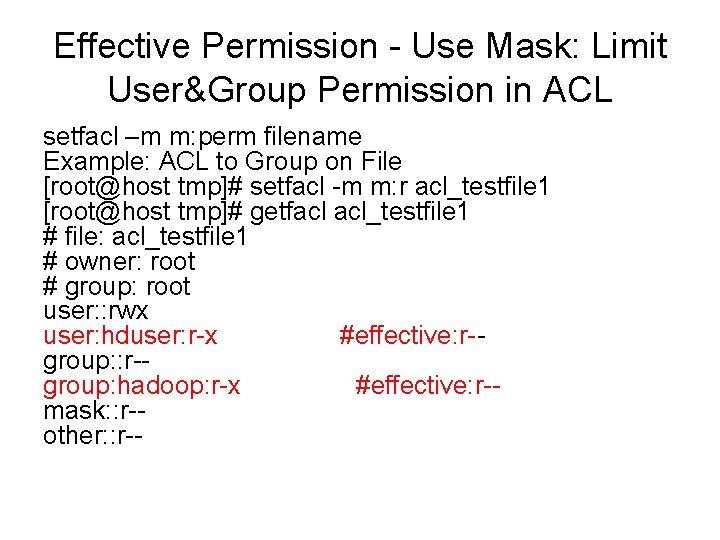
![Example visudo rootslave 01 visudo Allow root to run any commands anywhere Example- visudo [root@slave 01 ~]# visudo ## Allow root to run any commands anywhere](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-33.jpg)
Example- visudo [root@slave 01 ~]# visudo ## Allow root to run any commands anywhere root ALL=(ALL) ALL ## Allows members of the 'sys' group to run networking, software, ## service management apps and more. # %sys ALL = NETWORKING, SOFTWARE, SERVICES, STORAGE, DELEGATING, PROCESSES, LOCATE, DRIVERS ## Allows people in group wheel to run all commands %wheel ALL=(ALL) ALL ## Same thing without a password # %wheel ALL=(ALL) NOPASSWD: ALL ## Allows members of the users group to mount and unmount the ## cdrom as root # %users ALL=/sbin/mount /mnt/cdrom, /sbin/umount /mnt/cdrom ## Allows members of the users group to shutdown this system # %users localhost=/sbin/shutdown -h now ## Read drop-in files from /etc/sudoers. d (the # here does not mean a comment)
![Example use sudo rootslave 01 sudo u sshd touch tmpmysshd rootslave 01 Example- use sudo [root@slave 01 ~]# sudo -u sshd touch /tmp/mysshd [root@slave 01 ~]#](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-34.jpg)
Example- use sudo [root@slave 01 ~]# sudo -u sshd touch /tmp/mysshd [root@slave 01 ~]# ll /tmp/mysshd -rw-r--r-- 1 sshd 0 Aug 23 16: 43 /tmp/mysshd [root@slave 01 ~]# sudo -u hduser sh -c "mkdir ~hduser/www; cd ~hduser/www; echo 'This is index. html file'>index. html" [root@slave 01 ~]# ll -a ~hduser/www total 8 drwxr-xr-x 2 hduser hadoop 23 Aug 23 16: 45. drwx------. 9 hduser hadoop 4096 Aug 23 16: 45. . -rw-r--r-- 1 hduser hadoop 24 Aug 23 16: 45 index. html

Set Up sudo: allow pro 1 as root Without Password • visudo Make sure it includes a line: %wheel ALL=(ALL) NOPASSWD: ALL • Add pro 1 into wheel group usermod –a –G wheel pro 1 [root@host ~]# usermod -a -G wheel pro 1 [root@host ~]# groups pro 1 : pro 1 wheel projecta [root@host ~]# groups pro 2 : pro 2 projecta [root@host ~]# su - pro 1 [pro 1@host ~]$ sudo tail -n 1 /etc/shadow myuser 1: $6$1 CAr. S 7 QK$WZgez. K/a 6 Kfu. Nhka 4 Uh. FMTUWB 40 Xr. Z 9/4 Ex. JAp. Yyak. Vj. Qb. Le. Iu. Xw/m. Rj. Qp. E 5 f. Myxy p 8 l. SCHAg. B 5. JVm 4 OILx 50: 16670: 0: 99999: 7: : : [pro 1@host ~]$ exit logout [root@host ~]# su pro 2 [pro 2@host root]$ sudo tail -n 1 /etc/shadow We trust you have received the usual ethics lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility.

Set Up sudo: allow myuser 1 as root can change password for everyone except root • visudo Make sure it includes a line: myuser 1 ALL=(root) !/usr/bin/passwd, /usr/bin/passwd [A-Za-z]*, !/usr/bin/passwd root [root@host ~]# visudo [root@host ~]# su - myuser 1 [myuser 1@host ~]$ sudo passwd pro 2 We trust you have received the usual ethics lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. [sudo] password for myuser 1: Changing password for user pro 2. New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: all authentication tokens updated successfully. Meaning of !/usr/bin/passwd root [myuser 1@host ~]$ sudo passwd root Sorry, user myuser 1 is not allowed to execute '/usr/bin/passwd root' as root on host.

Use Alias to Set Up sudo: allow anyone can change password for everyone except root • visudo Make sure it includes lines: User_Alias ADMPW=pro 1, pro 2, pro 3, myuser 1 Cmnd_Alias ADMPWCOM = !/usr/bin/passwd, /usr/bin/passwd [A-Za-z]*, !/usr/bin/passwd root ADMPW ALL=(root) ADMPWCOM [root@host ~]# visudo [root@host ~]# su - pro 1 [pro 1@host ~]$ sudo passwd myuser 1 [sudo] password for pro 1: Changing password for user myuser 1. New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: all authentication tokens updated successfully. [pro 1@host ~]$ exit logout

Use Alias to Set Up sudo: allow anyone can change password for everyone except root (Cont. ) [root@host ~]# su -l pro 2 [pro 2@host ~]$ sudo passwd myuser 1 [sudo] password for pro 2: Changing password for user myuser 1. New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: all authentication tokens updated successfully. [pro 2@host ~]$ exit logout [root@host ~]# su - pro 3 [pro 3@host ~]$ id uid=503(pro 3) gid=506(pro 3) groups=506(pro 3), 503(projecta) [pro 3@host ~]$ sudo passwd pro 1 [sudo] password for pro 3: Changing password for user pro 1. New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: e all authentication tokens updat

Set Up root group but enter user’s own password • visudo Make sure it includes lines: User_Alias ADMS=pro 1, pro 2, pro 3, myuser 1 ADMS ALL=(root) /bin/su -
![Example roothost visudo roothost su pro 1 pro 1host Example [root@host ~]# !! visudo [root@host ~]# su - pro 1 [pro 1@host ~]$](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-40.jpg)
Example [root@host ~]# !! visudo [root@host ~]# su - pro 1 [pro 1@host ~]$ sudo passwd yuser 1 [sudo] password for pro 1: Sorry, user pro 1 is not allowed to execute '/usr/bin/passwd yuser 1' as root on host. [pro 1@host ~]$ sudo su [sudo] password for pro 1: [root@host ~]# passwd myuser 1 Changing password for user myuser 1. New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: all authentication tokens updated successfully. [root@host ~]# exit logout [pro 1@host ~]$ exit logout [root@host ~]# su - myuser 1 [myuser 1@host ~]$ sudo su [sudo] password for myuser 1: [root@host ~]# tail -n 1 /etc/gshadow myuser 1: !: : [root@host ~]# exit logout [myuser 1@host ~]$ exit logout

Security: Authentication- PAM (Pluggable Authentication Module) • PAM: API, provide authentication mechanism. User requests for authentication, PAM will return success or fail.
![Login Authentication etcpam dlogin rootslave 01 pam d cat etcpam dlogin PAM1 0 auth Login Authentication /etc/pam. d/login [root@slave 01 pam. d]# cat /etc/pam. d/login #%PAM-1. 0 auth](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-42.jpg)
Login Authentication /etc/pam. d/login [root@slave 01 pam. d]# cat /etc/pam. d/login #%PAM-1. 0 auth [user_unknown=ignore success=ok ignore=ignore default=bad] pam_securetty. so auth substack system-auth include postlogin account required pam_nologin. so account include system-auth password include system-auth # pam_selinux. so close should be the first session rule session required pam_selinux. so close session required pam_loginuid. so session optional pam_console. so # pam_selinux. so open should only be followed by sessions to be executed in the user context session required pam_selinux. so open session required pam_namespace. so session optional pam_keyinit. so force revoke session include system-auth session include postlogin -session optional pam_ck_connector. so

PAM Tasks for passwd 1. User uses /usr/bin/passwd, enter passwd 2. passwd calls PAM for authentication 3. PAM goes to /etc/pam. d/ to find same name configuration file 4. PAM analyzes authentication process such as acct lock info. based on configuration files in /etc/pam. d/passwd (or /etc/pam. d/pam. conf) 5. Return result(success/failure) back to passwd 6. Passwd will react (either proceed if success, or enter new passwd)
![Example rootslave 01 pam d cat etcpam dpasswd PAM1 0 auth include systemauth account Example [root@slave 01 pam. d]# cat /etc/pam. d/passwd #%PAM-1. 0 auth include system-auth account](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-44.jpg)
Example [root@slave 01 pam. d]# cat /etc/pam. d/passwd #%PAM-1. 0 auth include system-auth account include system-auth password substack system-auth -password optional pam_gnome_keyring. so use_authtok password substack postlogin Note: 1 st line auth: authenticated by passwd - means follow the rules auth in /etc/pam. d/system-auth
![Example rootslave 01 pam d cat etcpam dsystemauth PAM1 0 This file is Example [root@slave 01 pam. d]# cat /etc/pam. d/system-auth #%PAM-1. 0 # This file is](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-45.jpg)
Example [root@slave 01 pam. d]# cat /etc/pam. d/system-auth #%PAM-1. 0 # This file is auto-generated. # User changes will be destroyed the next time authconfig is run. auth required pam_env. so auth sufficient pam_unix. so nullok try_first_pass auth requisite pam_succeed_if. so uid >= 1000 quiet_success auth required pam_deny. so account password required sufficient required requisite sufficient required pam_unix. so pam_localuser. so pam_succeed_if. so uid < 1000 quiet pam_permit. so pam_pwquality. so try_first_pass local_users_only retry=3 authtok_type= pam_unix. so sha 512 shadow nullok try_first_pass use_authtok pam_deny. so session optional pam_keyinit. so revoke session required pam_limits. so -session optional pam_systemd. so session [success=1 default=ignore] pam_succeed_if. so service in crond quiet use_uid session required pam_unix. so Note: for auth rules Required: rule must be checked by pam_env. so. No matter result (label-logged) is success or fail, it must be checked next. The next one is: Sufficient: if rule checked by pam_unix. so. If success, return “Success”. Otherwise, checked next one: Requisite: If rule checked by pam_succeed_if. so (if UID>= 1000), then rerun “Success”. Otherwise, it return “Failure”. Required: The next one also returned “Failure” by pam_deny. so.

Example (Cont. ) The 2 nd line in /etc/pam. d/passwd: account include system-auth Check account: account privilegeaccount required pam_unix. so account sufficient pam_localuser. so account sufficient pam_succeed_if. so uid < 1000 quiet account required pam_permit. so

Example (Cont. ) The 3 rd line in /etc/pam. d/passwd: password substack system-auth Check password: modify password requisite pam_pwquality. so try_first_pass local_users_only retry=3 authtok_type= password sufficient pam_unix. so sha 512 shadow nullok try_first_pass use_authtok password required pam_deny. so

Example (Cont. ) The 4 th line in /etc/pam. d/passwd: password substack postlogin Check password change after login Note: for Session: record between login and logout such as using su or sudo.
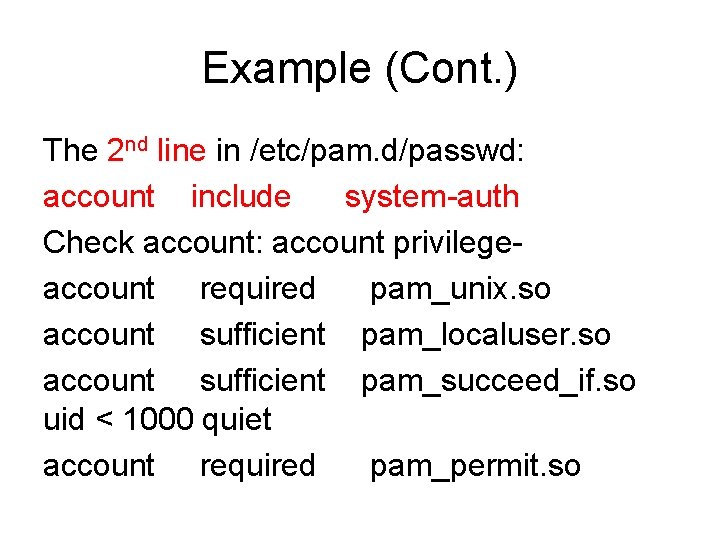
![Limit of UsersFile size vim etcsecuritylimits conf roothost soft for Limit # of Users/File size vim /etc/security/limits. conf [root@host ~]# # - "soft" for](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-49.jpg)
Limit # of Users/File size vim /etc/security/limits. conf [root@host ~]# # - "soft" for enforcing the soft limits # - "hard" for enforcing hard limits # #<item> can be one of the following: # - core - limits the core file size (KB) # - data - max data size (KB) # - fsize - maximum filesize (KB) # - memlock - max locked-in-memory address space (KB) # - nofile - max number of open files # - rss - max resident set size (KB) # - stack - max stack size (KB) # - cpu - max CPU time (MIN) # - nproc - max number of processes # - as - address space limit (KB) # - maxlogins - max number of logins for this user # - maxsyslogins - max number of logins on the system #* soft core 0 #* hard rss 10000 #@student hard nproc 20 #@faculty soft nproc 20 #@faculty hard nproc 50 #ftp hard nproc 0 #@student maxlogins 4
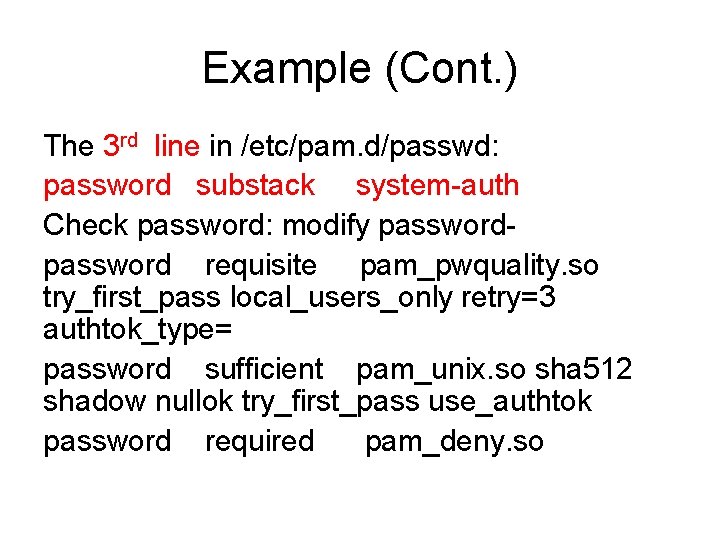
![Limit of usersfile size ulimit a roothost core file size blocks c Limit # of users/file size ulimit -a [root@host ~]# core file size (blocks, -c)](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-50.jpg)
Limit # of users/file size ulimit -a [root@host ~]# core file size (blocks, -c) 0 data seg size (kbytes, -d) unlimited scheduling priority (-e) 0 file size (blocks, -f) unlimited pending signals (-i) 15918 max locked memory (kbytes, -l) 64 max memory size (kbytes, -m) unlimited open files (-n) 1024 pipe size (512 bytes, -p) 8 POSIX message queues (bytes, -q) 819200 real-time priority (-r) 0 stack size (kbytes, -s) 10240 cpu time (seconds, -t) unlimited max user processes (-u) 1024 virtual memory (kbytes, -v) unlimited file locks (-x) unlimited

Other PAM Configuration Files • They are in /etc/security • PAM logs: – /var/log/secure – /var/log/messages
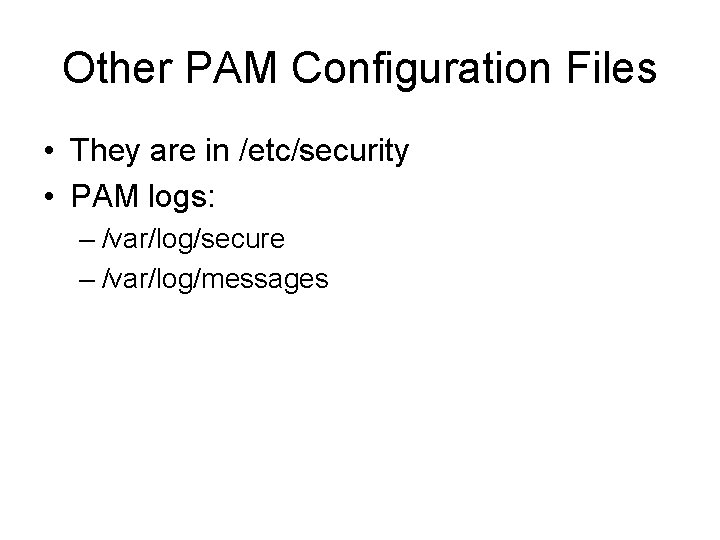
![Example check nologin account rootslave 01 pam d pwck user ftp directory varftp does Example- check nologin account [root@slave 01 pam. d]# pwck user 'ftp': directory '/var/ftp' does](https://slidetodoc.com/presentation_image_h2/313132fc93cc0237c037f1cd094d2b9c/image-52.jpg)
Example- check nologin account [root@slave 01 pam. d]# pwck user 'ftp': directory '/var/ftp' does not exist user 'avahi-autoipd': directory '/var/lib/avahiautoipd' does not exist pwck: no changes

Delete account script #! /bin/bash usernames=$(cat user. passwd|cut –d ‘: ’ –f 1) for username in $usernames do echo “userdel –r $username” userdel –r $username done