Chapter 6 Concurrency Deadlock and Starvation I z











- Slides: 35

Chapter 6 Concurrency: Deadlock and Starvation I z z z z z Deadlock Conditions for Deadlock Prevention Deadlock Avoidance Banker’s Algorithm Deadlock Detection Strategies once Deadlock Detected Deadlock Detection Algorithm UNIX Concurrency Mechanisms

Deadlock z Deadlock can be defined as the permanent blocking of a set of processes that either compete for system resources or communicate with each other All deadlocks Involve conflicting needs for resources by two or more processes

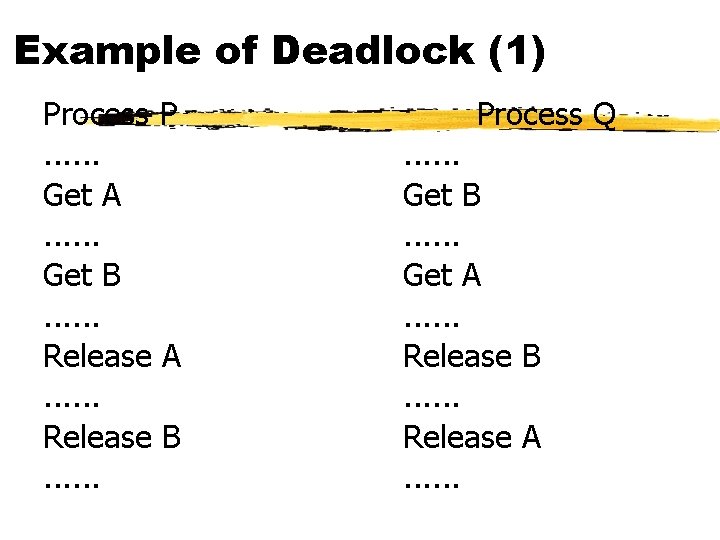
Example of Deadlock (1) Process P. . . Get A. . . Get B. . . Release A. . . Release B. . . Process Q. . . Get B. . . Get A. . . Release B. . . Release A. . .

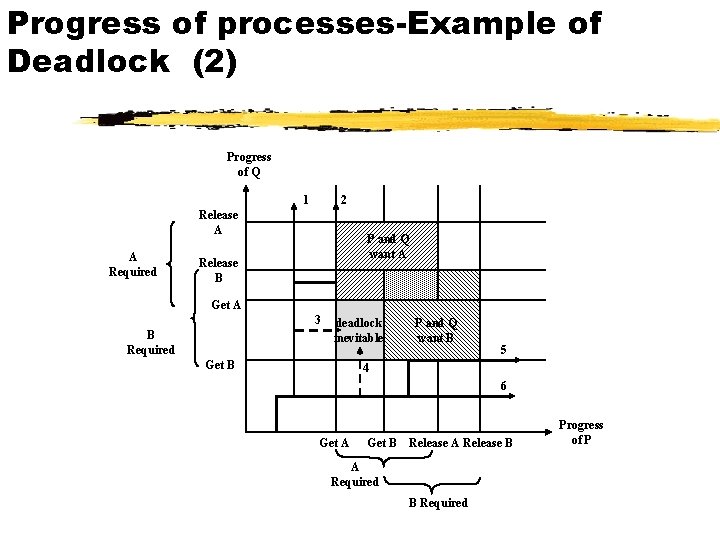
Progress of processes-Example of Deadlock (2) Progress of Q 2 1 Release A A Required P and Q want A Release B Get A 3 B Required deadlock inevitable Get B P and Q want B 5 4 6 Get A Get B Release A Release B A Required B Required Progress of P

Execution Paths -Example of Deadlock (3) 1. Q acquires B and then A, and then releases B and A. When P resumes execution, it will be able to acquire both resources. 2. Q acquires B and then A. P executes and blocks on a request for A. Q releases B and A. When P resumes execution, it will be able to acquire both resources. 5. P acquires A and then B. Q executes and blocks on a request for B. P releases A and B. When Q resumes execution, it will be able to acquire both resources. 6. P acquires A and then B, and then releases A and B. When Q resumes execution, it will be able to acquire both resources.

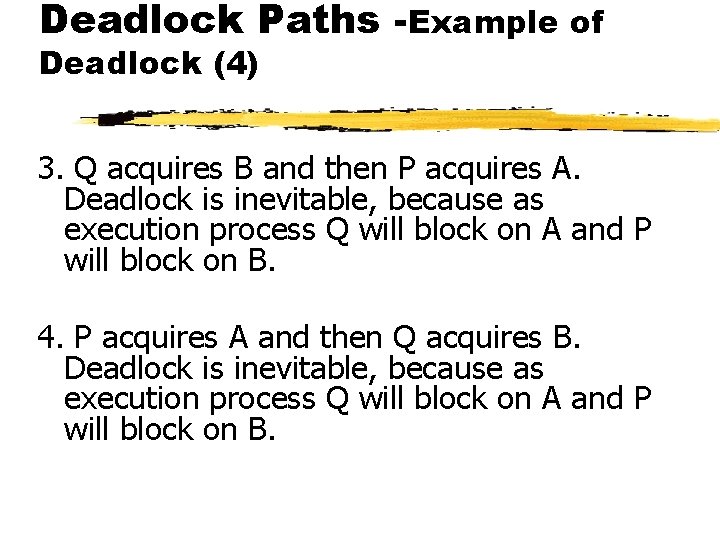
Deadlock Paths -Example of Deadlock (4) 3. Q acquires B and then P acquires A. Deadlock is inevitable, because as execution process Q will block on A and P will block on B. 4. P acquires A and then Q acquires B. Deadlock is inevitable, because as execution process Q will block on A and P will block on B.

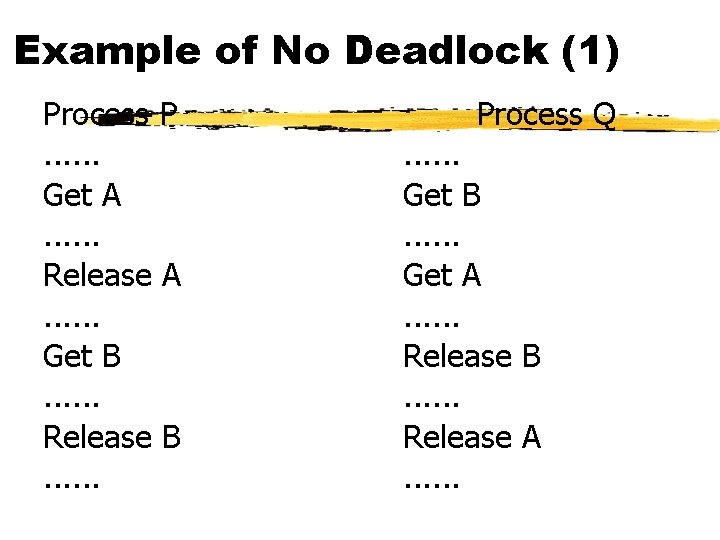
Example of No Deadlock (1) Process P. . . Get A. . . Release A. . . Get B. . . Release B. . . Process Q. . . Get B. . . Get A. . . Release B. . . Release A. . .

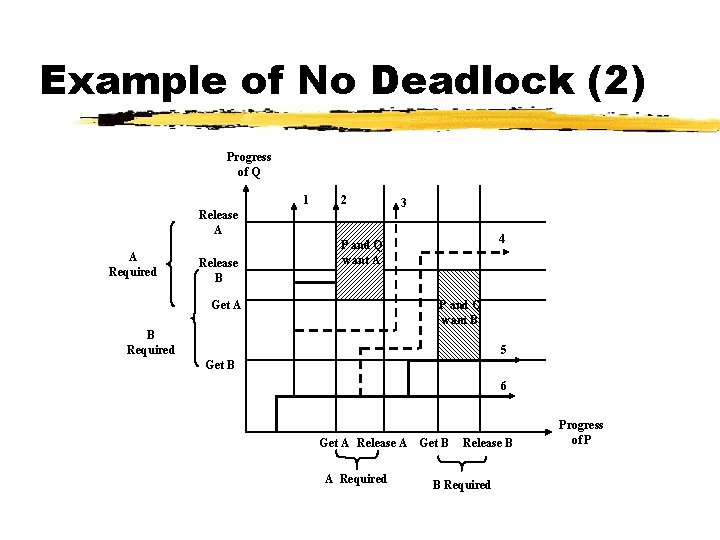
Example of No Deadlock (2) Progress of Q 1 2 Release A A Required Release B 3 4 P and Q want A Get A P and Q want B B Required 5 Get B 6 Get A Release A Get B A Required Release B B Required Progress of P

Question 1 - Exercise/Home Work (1) For Figure of No Deadlock, provide a narrative description of each of the six depicted paths.

Reusable Resources z A reusable resource is one that can be safely used by one process at a time and not depleted by that use z Processes obtain resources that they later release for reuse by other processes z Examples of reusable resources: processor time, I/O channels, main and secondary memory, files, databases, and semaphores z Deadlock occurs if each process holds one resource and requests the other

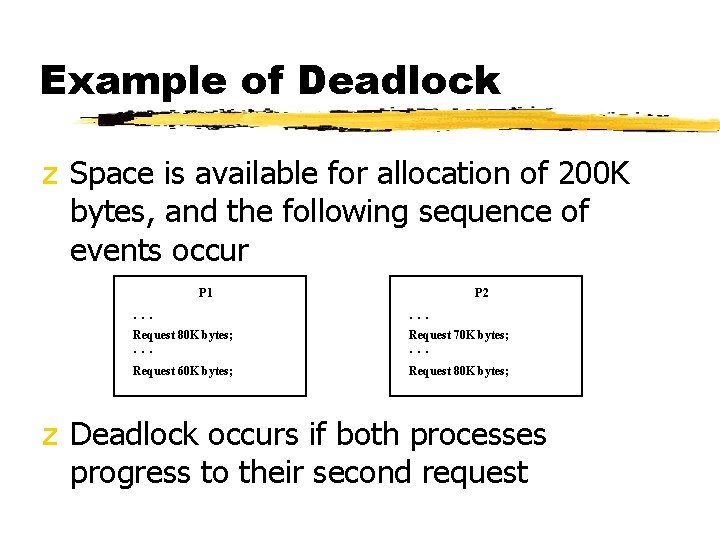
Example of Deadlock z Space is available for allocation of 200 K bytes, and the following sequence of events occur P 1 P 2 . . . Request 80 K bytes; Request 70 K bytes; . . . Request 60 K bytes; Request 80 K bytes; z Deadlock occurs if both processes progress to their second request

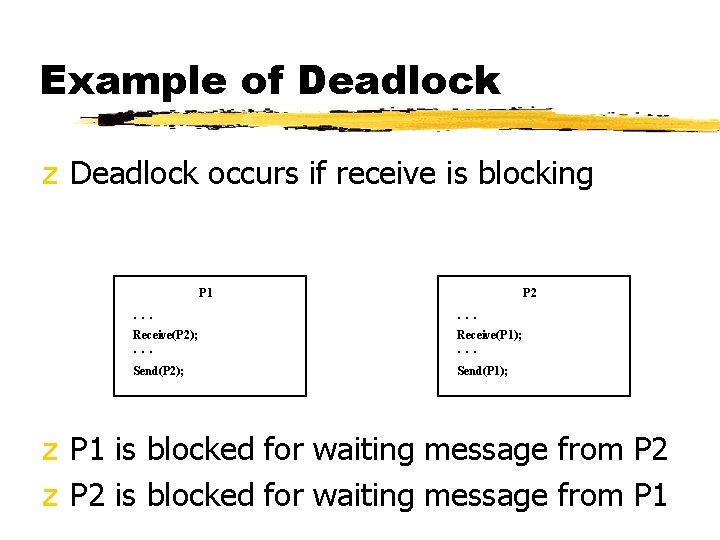
Consumable Resources z A consumable resource is one that can be created (produced) and destroyed (consumed) by a process z Examples of consumable resources: interrupts, signals, messages, and information in I/O buffers z Deadlock may occur if a Receive message is blocking z May take a rare combination of events to cause deadlock

Example of Deadlock z Deadlock occurs if receive is blocking P 1 P 2 . . . Receive(P 2); Receive(P 1); . . . Send(P 2); Send(P 1); z P 1 is blocked for waiting message from P 2 z P 2 is blocked for waiting message from P 1

Conditions for Deadlock Three conditions of policy must be present for a deadlock to be possible: z Mutual exclusion y only one process may use a resource at a time z Hold-and-wait y a process may hold allocated resources while awaiting assignment of others z No preemption y no resource can be forcibly removed from a process holding it

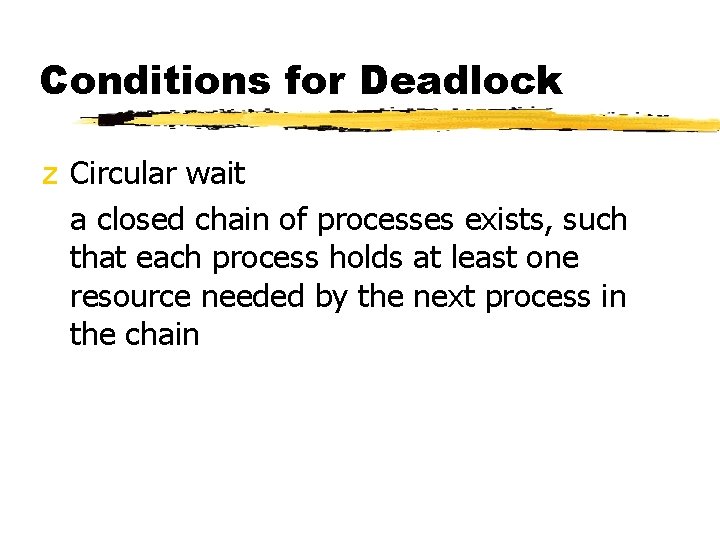
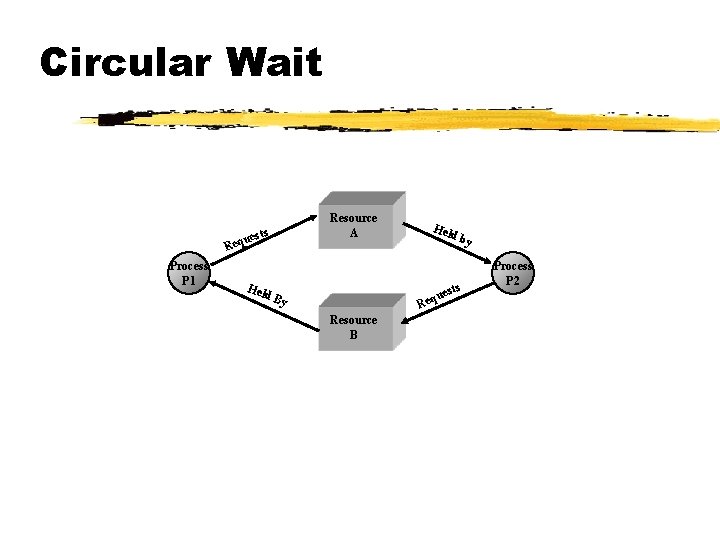
Conditions for Deadlock z Circular wait a closed chain of processes exists, such that each process holds at least one resource needed by the next process in the chain

Circular Wait Resource A s est equ R Process P 1 Hel db ests u q Re d. B y Resource B y Process P 2

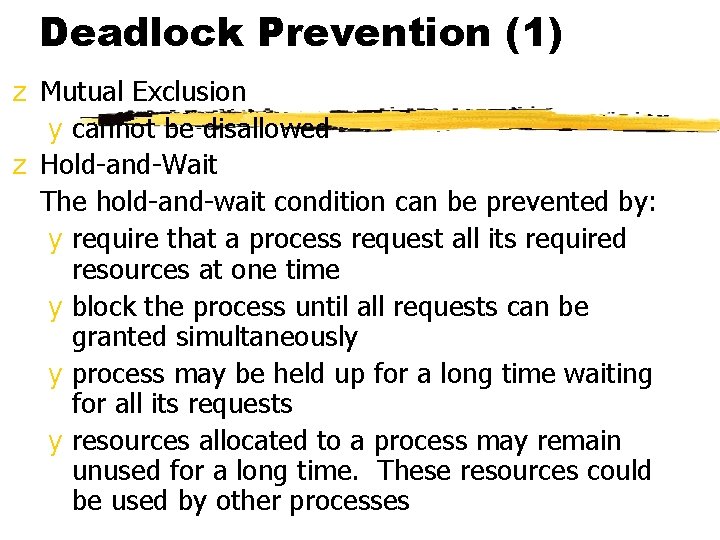
Deadlock Prevention (1) z Mutual Exclusion y cannot be disallowed z Hold-and-Wait The hold-and-wait condition can be prevented by: y require that a process request all its required resources at one time y block the process until all requests can be granted simultaneously y process may be held up for a long time waiting for all its requests y resources allocated to a process may remain unused for a long time. These resources could be used by other processes

Deadlock Prevention (2) z No preemption z This condition can be prevented in several ways: y if a process is denied a further request, the process must release the original resources y if a process cannot obtain a resource, the process may have to release its resources. Must have capability to restore to current state. y This approach is practical only when the state can be easily saved and restored later, such as the processor.

Deadlock Prevention (3) z Circular wait z The circular-wait condition can be prevented by : y define a linear ordering for resources y once a resource R is obtained, then it may subsequently request only those resources of types following R in the ordering.

Deadlock Avoidance (1) z Do not start a process if its demands might lead to deadlock z Do not grant an incremental resource request to a process if this allocation might lead to deadlock

Deadlock Avoidance (2) z Maximum resource requirement must be stated in advance z Processes under consideration must be independent; no synchronization requirements z There must be a fixed number of resources to allocate z No process may exit while holding resources

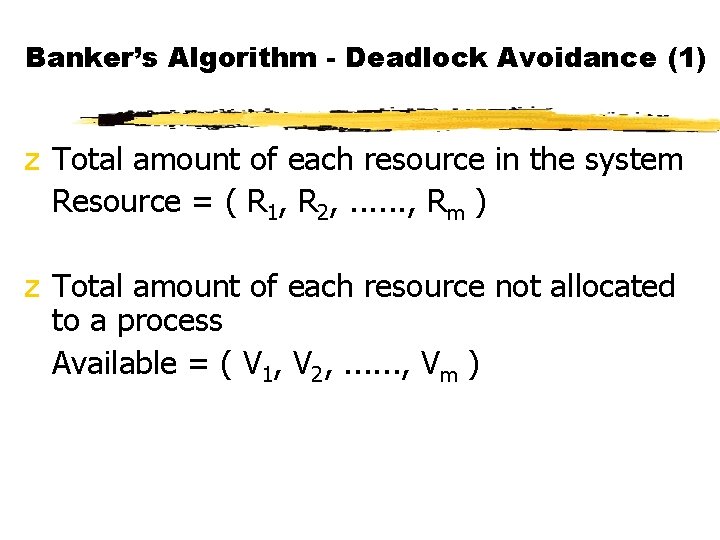
Banker’s Algorithm - Deadlock Avoidance (1) z Total amount of each resource in the system Resource = ( R 1, R 2, . . . , Rm ) z Total amount of each resource not allocated to a process Available = ( V 1, V 2, . . . , Vm )

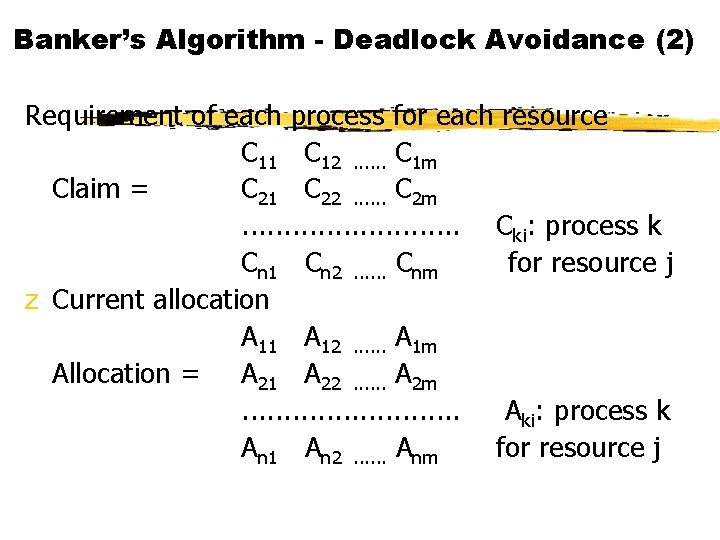
Banker’s Algorithm - Deadlock Avoidance (2) Requirement of each process for each resource C 11 C 12. . . C 1 m Claim = C 21 C 22. . . C 2 m. . . Cki: process k Cn 1 Cn 2. . . Cnm for resource j z Current allocation A 11 A 12. . . A 1 m Allocation = A 21 A 22. . . A 2 m. . . Aki: process k An 1 An 2. . . Anm for resource j

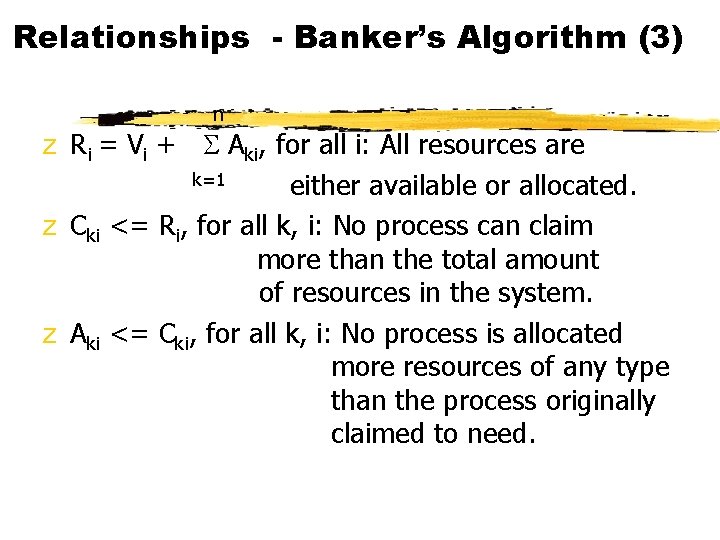
Relationships - Banker’s Algorithm (3) n z Ri = Vi + S Aki, for all i: All resources are k=1 either available or allocated. z Cki <= Ri, for all k, i: No process can claim more than the total amount of resources in the system. z Aki <= Cki, for all k, i: No process is allocated more resources of any type than the process originally claimed to need.

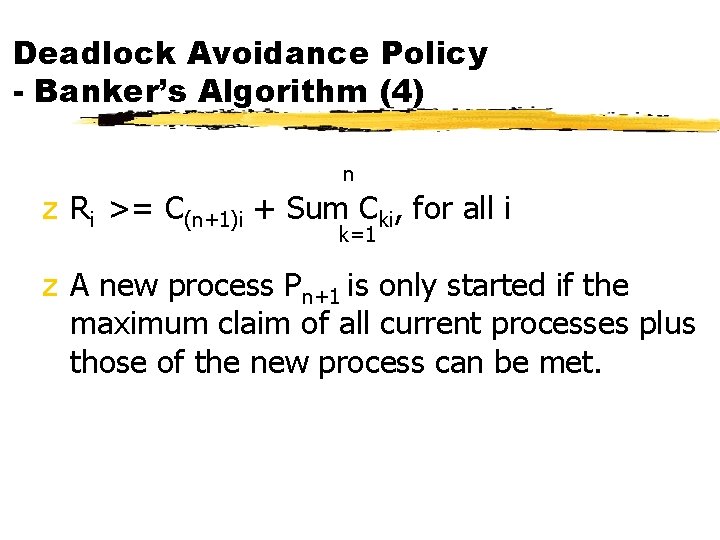
Deadlock Avoidance Policy - Banker’s Algorithm (4) n z Ri >= C(n+1)i + Sum Cki, for all i k=1 z A new process Pn+1 is only started if the maximum claim of all current processes plus those of the new process can be met.

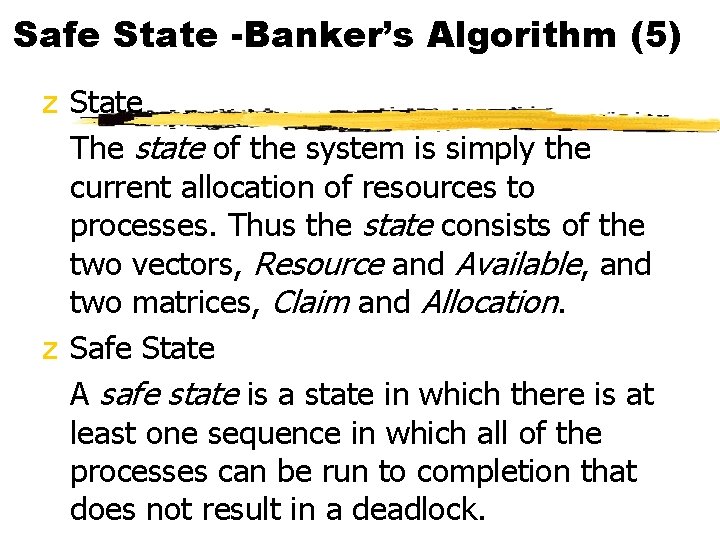
Safe State -Banker’s Algorithm (5) z State The state of the system is simply the current allocation of resources to processes. Thus the state consists of the two vectors, Resource and Available, and two matrices, Claim and Allocation. z Safe State A safe state is a state in which there is at least one sequence in which all of the processes can be run to completion that does not result in a deadlock.

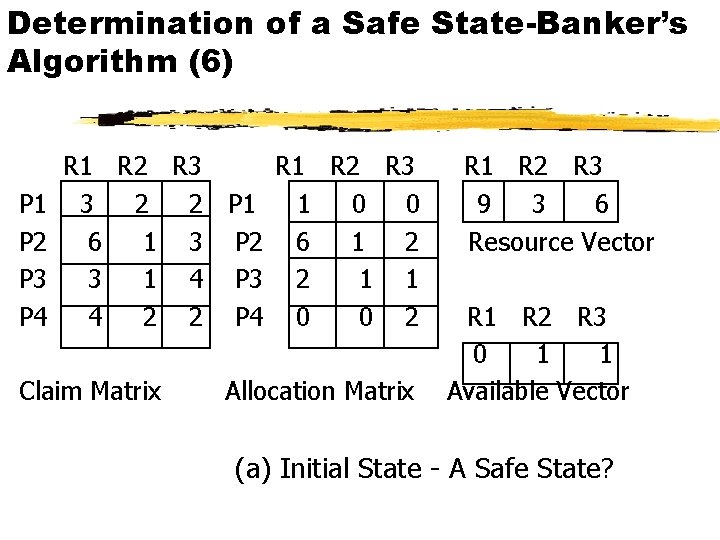
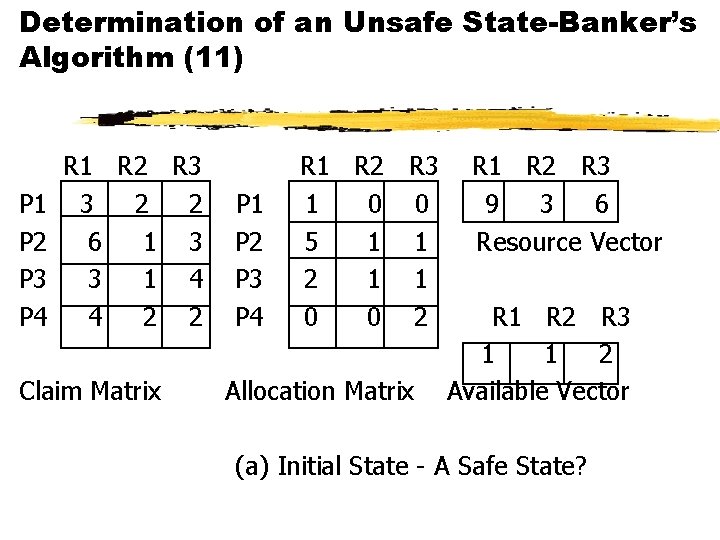
Determination of a Safe State-Banker’s Algorithm (6) P 1 P 2 P 3 P 4 R 1 R 2 R 3 3 2 2 P 1 1 0 0 6 1 3 P 2 6 1 2 3 1 4 P 3 2 1 1 4 2 2 P 4 0 0 2 Claim Matrix Allocation Matrix R 1 R 2 R 3 9 3 6 Resource Vector R 1 R 2 R 3 0 1 1 Available Vector (a) Initial State - A Safe State?

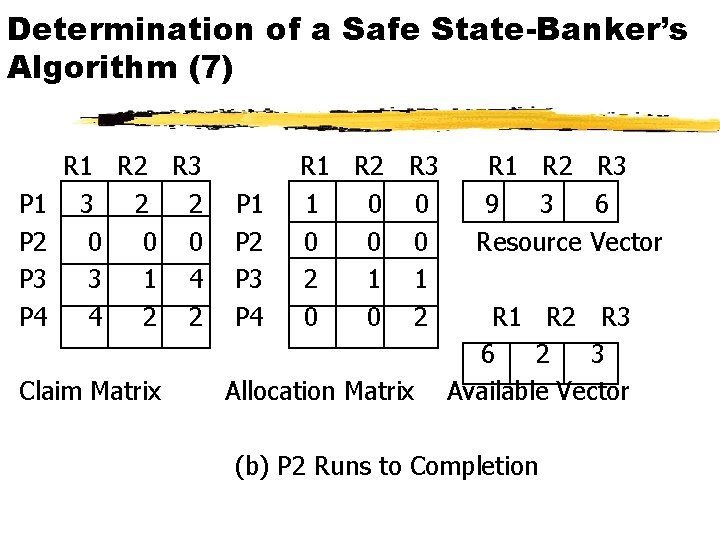
Determination of a Safe State-Banker’s Algorithm (7) P 1 P 2 P 3 P 4 R 1 R 2 R 3 3 2 2 0 0 0 3 1 4 4 2 2 Claim Matrix P 1 P 2 P 3 P 4 R 1 R 2 R 3 1 0 0 0 2 1 1 0 0 2 Allocation Matrix R 1 R 2 R 3 9 3 6 Resource Vector R 1 R 2 R 3 6 2 3 Available Vector (b) P 2 Runs to Completion

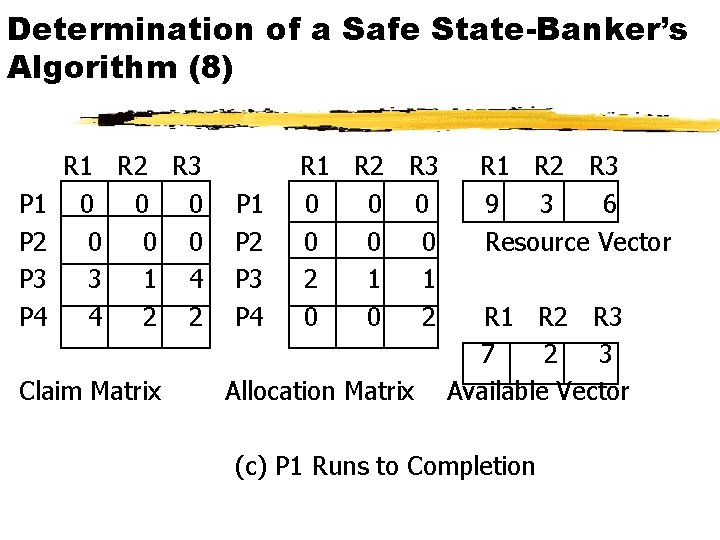
Determination of a Safe State-Banker’s Algorithm (8) P 1 P 2 P 3 P 4 R 1 R 2 R 3 0 0 0 3 1 4 4 2 2 Claim Matrix P 1 P 2 P 3 P 4 R 1 R 2 R 3 0 0 0 2 1 1 0 0 2 Allocation Matrix R 1 R 2 R 3 9 3 6 Resource Vector R 1 R 2 R 3 7 2 3 Available Vector (c) P 1 Runs to Completion

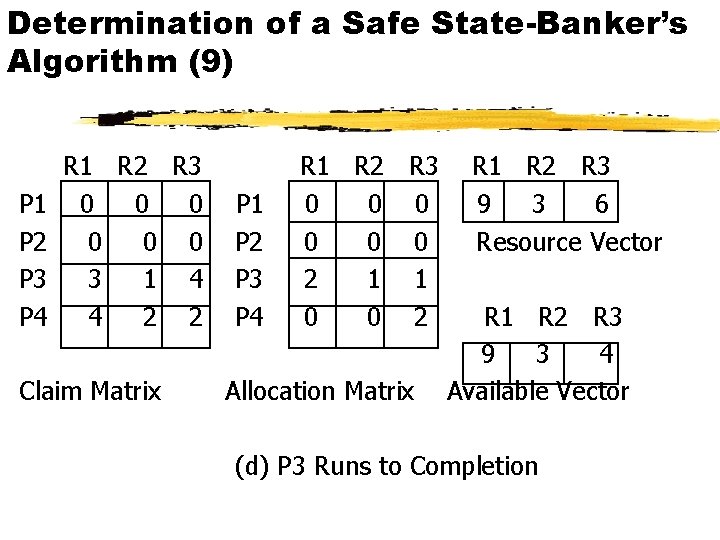
Determination of a Safe State-Banker’s Algorithm (9) P 1 P 2 P 3 P 4 R 1 R 2 R 3 0 0 0 3 1 4 4 2 2 Claim Matrix P 1 P 2 P 3 P 4 R 1 R 2 R 3 0 0 0 2 1 1 0 0 2 Allocation Matrix R 1 R 2 R 3 9 3 6 Resource Vector R 1 R 2 R 3 9 3 4 Available Vector (d) P 3 Runs to Completion

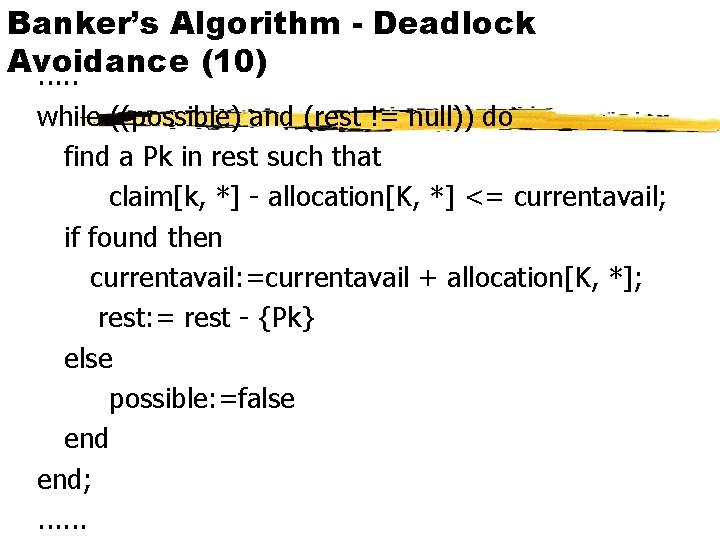
Banker’s Algorithm - Deadlock Avoidance (10). . . while ((possible) and (rest != null)) do find a Pk in rest such that claim[k, *] - allocation[K, *] <= currentavail; if found then currentavail: =currentavail + allocation[K, *]; rest: = rest - {Pk} else possible: =false end; . . .

Determination of an Unsafe State-Banker’s Algorithm (11) P 1 P 2 P 3 P 4 R 1 R 2 R 3 3 2 2 6 1 3 3 1 4 4 2 2 Claim Matrix P 1 P 2 P 3 P 4 R 1 R 2 R 3 1 0 0 5 1 1 2 1 1 0 0 2 Allocation Matrix R 1 R 2 R 3 9 3 6 Resource Vector R 1 R 2 R 3 1 1 2 Available Vector (a) Initial State - A Safe State?

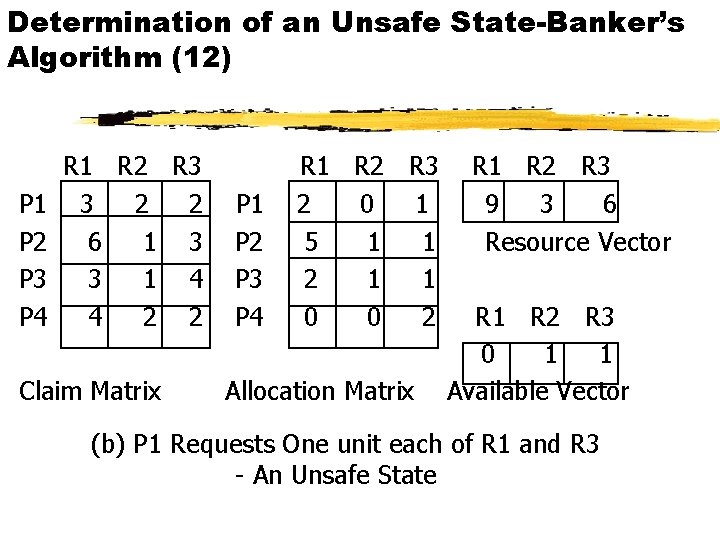
Determination of an Unsafe State-Banker’s Algorithm (12) P 1 P 2 P 3 P 4 R 1 R 2 R 3 3 2 2 6 1 3 3 1 4 4 2 2 Claim Matrix P 1 P 2 P 3 P 4 R 1 R 2 R 3 2 0 1 5 1 1 2 1 1 0 0 2 Allocation Matrix R 1 R 2 R 3 9 3 6 Resource Vector R 1 R 2 R 3 0 1 1 Available Vector (b) P 1 Requests One unit each of R 1 and R 3 - An Unsafe State

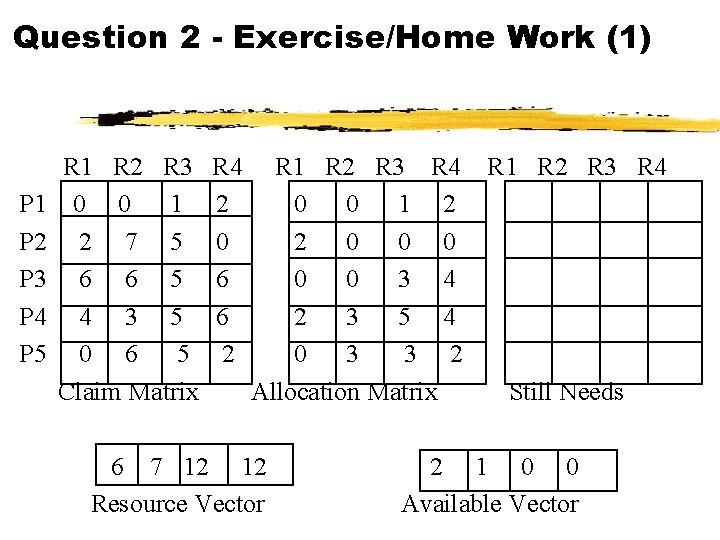
Question 2 - Exercise/Home Work (1) P 1 P 2 P 3 P 4 P 5 R 1 R 2 R 3 0 0 1 2 7 5 6 6 5 4 3 5 0 6 5 Claim Matrix R 4 2 0 6 6 2 R 1 R 2 R 3 R 4 0 0 1 2 2 0 0 0 3 4 2 3 5 4 0 3 3 2 Allocation Matrix Still Needs 6 7 12 12 Resource Vector 2 1 0 0 Available Vector

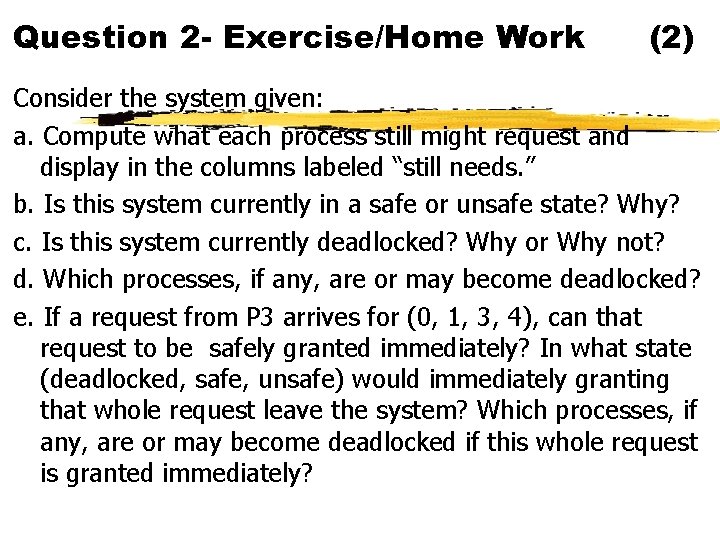
Question 2 - Exercise/Home Work (2) Consider the system given: a. Compute what each process still might request and display in the columns labeled “still needs. ” b. Is this system currently in a safe or unsafe state? Why? c. Is this system currently deadlocked? Why or Why not? d. Which processes, if any, are or may become deadlocked? e. If a request from P 3 arrives for (0, 1, 3, 4), can that request to be safely granted immediately? In what state (deadlocked, safe, unsafe) would immediately granting that whole request leave the system? Which processes, if any, are or may become deadlocked if this whole request is granted immediately?