Chapter 5 Transport Layer Introduction Networking CS 3470

![UDP: User Datagram Protocol [RFC 768] “No frills, ” “bare bones” Internet transport protocol UDP: User Datagram Protocol [RFC 768] “No frills, ” “bare bones” Internet transport protocol](https://slidetodoc.com/presentation_image_h2/3c157c710da9750b06e117ac724346ac/image-13.jpg)
![UDP: User Datagram Protocol [RFC 768] Why is there a UDP? No connection establishment UDP: User Datagram Protocol [RFC 768] Why is there a UDP? No connection establishment](https://slidetodoc.com/presentation_image_h2/3c157c710da9750b06e117ac724346ac/image-14.jpg)






- Slides: 34

Chapter 5 Transport Layer Introduction Networking CS 3470, Section 1

Chapter 5: Transport Layer Our goals: Principles behind transport layer services: multiplexing/demultiplexing, reliable data transfer, flow control, congestion control Protocols in the transport layer UDP connectionless transport TCP: connection-oriented transport TCP congestion control

How does this all fit together? 3

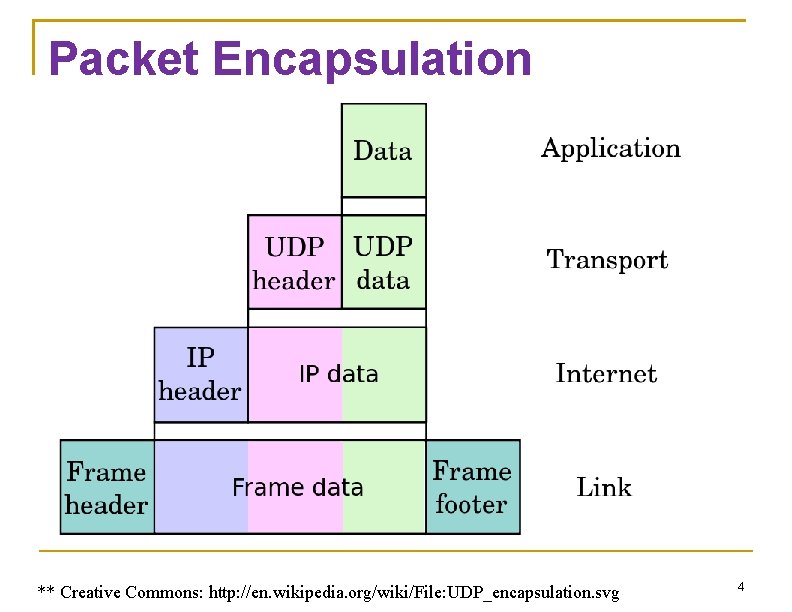
Packet Encapsulation ** Creative Commons: http: //en. wikipedia. org/wiki/File: UDP_encapsulation. svg 4

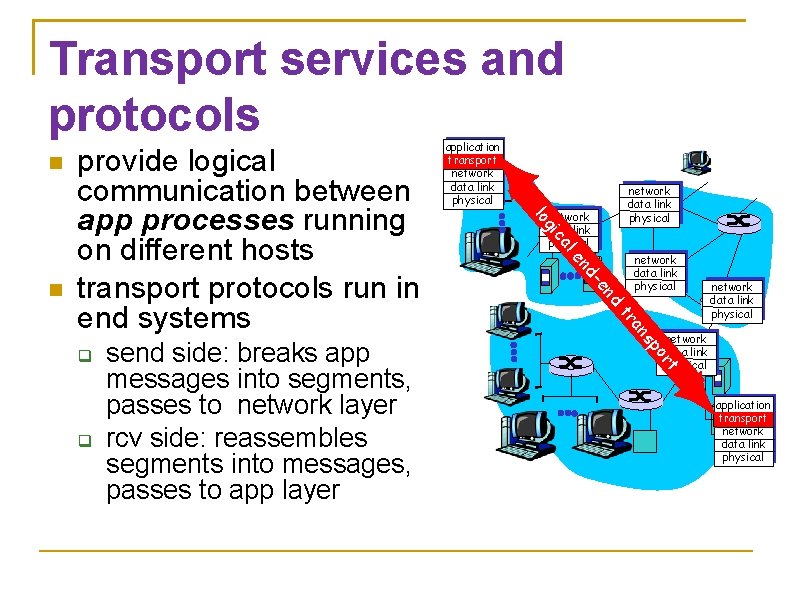
Transport services and protocols network data link physical d en den network data link physical tr network data link physical rt po s an send side: breaks app messages into segments, passes to network layer rcv side: reassembles segments into messages, passes to app layer l ca gi network data link physical lo provide logical communication between app processes running on different hosts transport protocols run in end systems application transport network data link physical

Transport vs. network layer Why can’t we just use the network layer to send messages from host to host? …What’s wrong with just IP? ?

Transport vs. network layer Why can’t we just use the network layer to send messages from host to host? …What’s wrong with just IP? ? IP is not end-to-end – it is best effort

Transport vs. network layer Why can’t we just use the network layer to send messages from host to host? …What’s wrong with just IP? ? IP is not end-to-end – it is best effort IP has no port numbers. What do port numbers do?

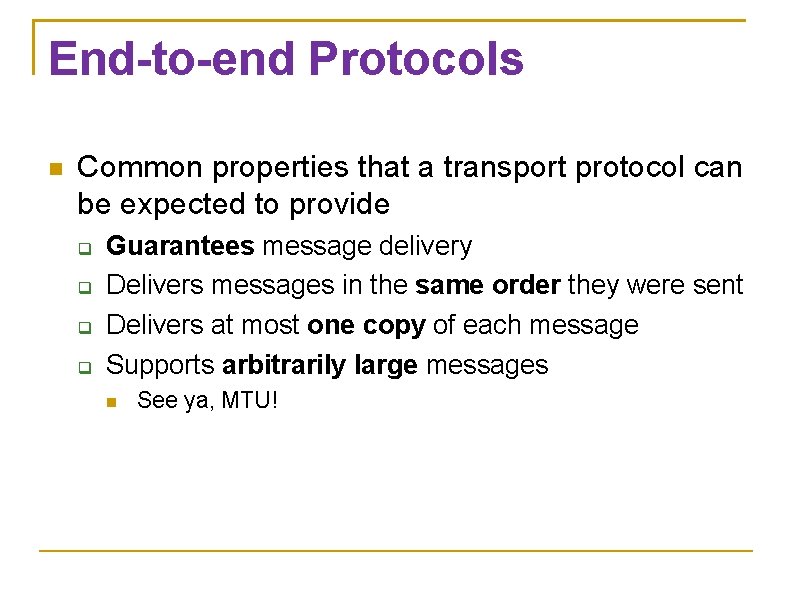
End-to-end Protocols Common properties that a transport protocol can be expected to provide Guarantees message delivery Delivers messages in the same order they were sent Delivers at most one copy of each message Supports arbitrarily large messages See ya, MTU!

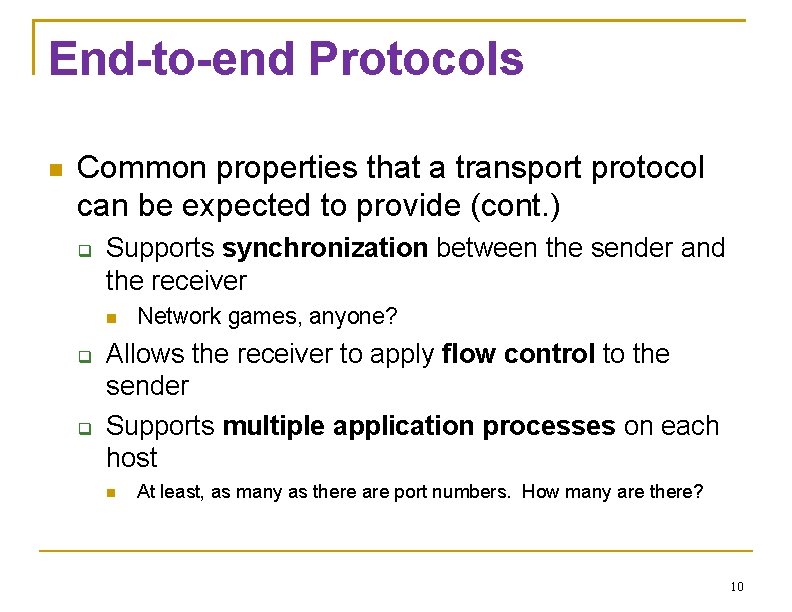
End-to-end Protocols Common properties that a transport protocol can be expected to provide (cont. ) Supports synchronization between the sender and the receiver Network games, anyone? Allows the receiver to apply flow control to the sender Supports multiple application processes on each host At least, as many as there are port numbers. How many are there? 10

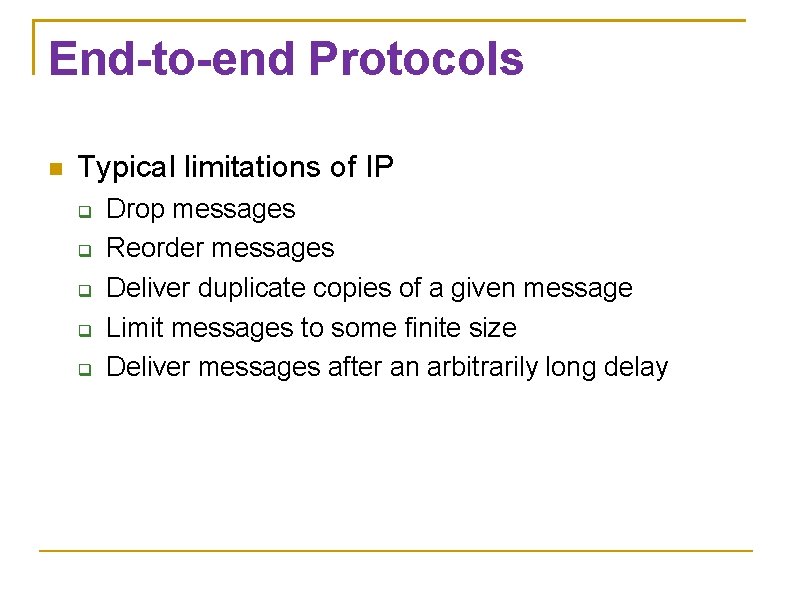
End-to-end Protocols Typical limitations of IP Drop messages Reorder messages Deliver duplicate copies of a given message Limit messages to some finite size Deliver messages after an arbitrarily long delay

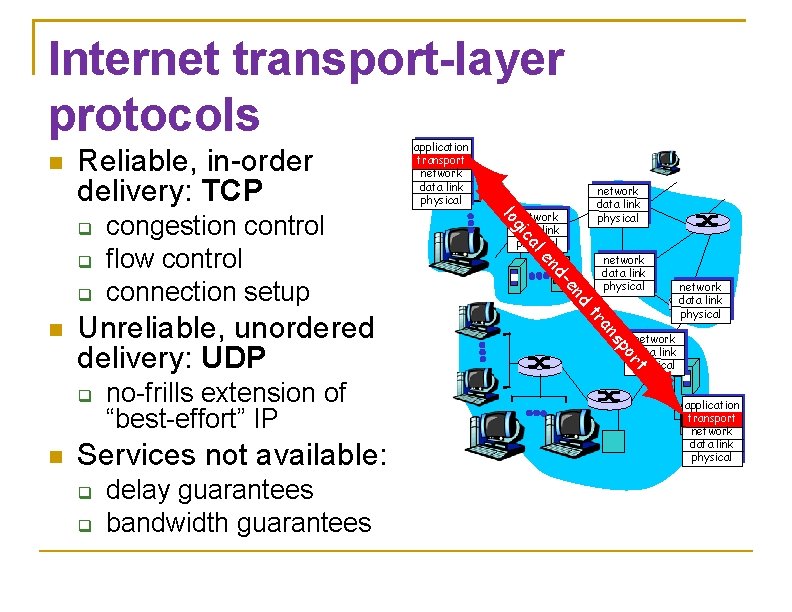
Internet transport-layer protocols Reliable, in-order delivery: TCP Services not available: delay guarantees bandwidth guarantees network data link physical rt po no-frills extension of “best-effort” IP s an network data link physical tr Unreliable, unordered delivery: UDP d en network data link physical den network data link physical l ca gi congestion control flow control connection setup lo application transport network data link physical
![UDP User Datagram Protocol RFC 768 No frills bare bones Internet transport protocol UDP: User Datagram Protocol [RFC 768] “No frills, ” “bare bones” Internet transport protocol](https://slidetodoc.com/presentation_image_h2/3c157c710da9750b06e117ac724346ac/image-13.jpg)
UDP: User Datagram Protocol [RFC 768] “No frills, ” “bare bones” Internet transport protocol “Best effort” service, UDP segments may be: lost delivered out of order to app Connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others 13
![UDP User Datagram Protocol RFC 768 Why is there a UDP No connection establishment UDP: User Datagram Protocol [RFC 768] Why is there a UDP? No connection establishment](https://slidetodoc.com/presentation_image_h2/3c157c710da9750b06e117ac724346ac/image-14.jpg)
UDP: User Datagram Protocol [RFC 768] Why is there a UDP? No connection establishment (which can add delay) Simple: no connection state at sender, receiver Small segment header No congestion control: UDP can blast away as fast as desired 14

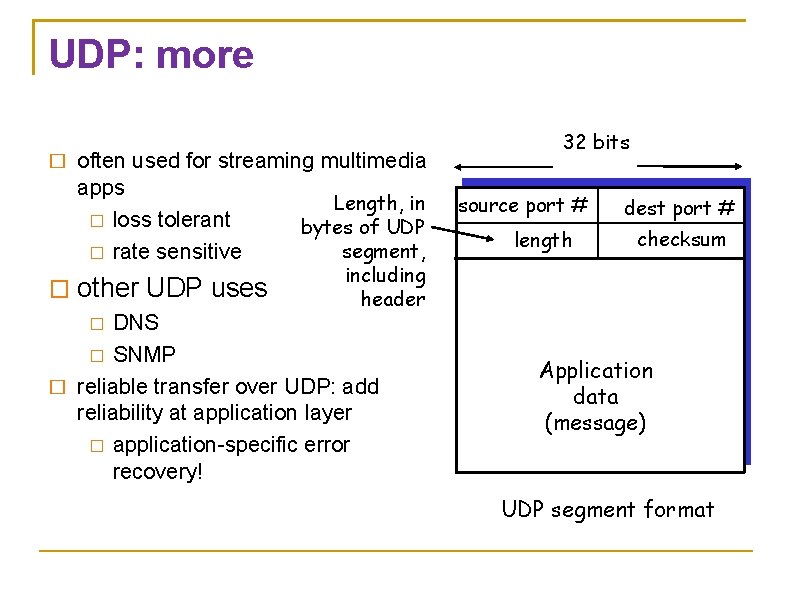
UDP: more � often used for streaming multimedia apps � loss tolerant � rate sensitive � other UDP uses Length, in bytes of UDP segment, including header DNS � SNMP � reliable transfer over UDP: add reliability at application layer � application-specific error recovery! 32 bits source port # length dest port # checksum � Application data (message) UDP segment format

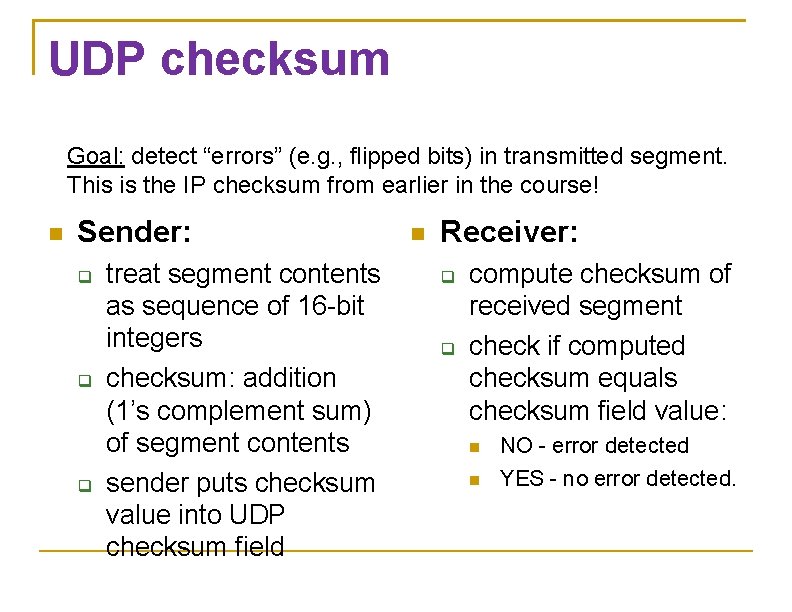
UDP checksum Goal: detect “errors” (e. g. , flipped bits) in transmitted segment. This is the IP checksum from earlier in the course! Sender: treat segment contents as sequence of 16 -bit integers checksum: addition (1’s complement sum) of segment contents sender puts checksum value into UDP checksum field Receiver: compute checksum of received segment check if computed checksum equals checksum field value: NO - error detected YES - no error detected.

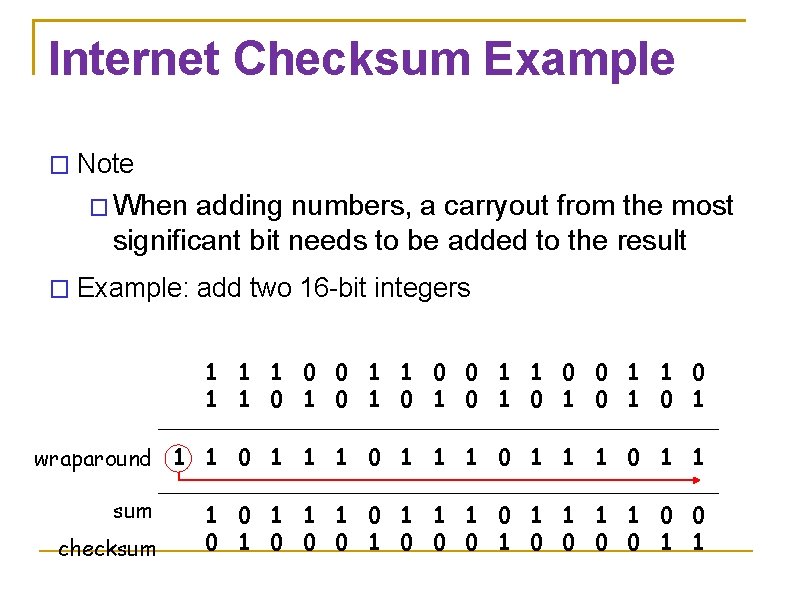
Internet Checksum Example � Note � When adding numbers, a carryout from the most significant bit needs to be added to the result � Example: add two 16 -bit integers 1 1 0 0 1 1 1 0 1 0 1 wraparound 1 1 0 1 1 sum 1 1 0 1 1 0 0 checksum 1 0 0 0 0 1 1

Internet Checksum Example What if we are adding three numbers? Add first two numbers Add sum of first two numbers with third number Deal with carryout from most significant bit (if necessary) Obtain the 1’s compliment by converting all 0 s to 1 s and all 1 s to 0 s (flip the bits) Same general algorithm for adding > 3 numbers 18

Internet Checksum Example At the receiver, all 16 -bit words are added (including the checksum) If no errors introduced, the sum at the receiver will be all 1’s If any of the bits are zero, then we know error(s) have been introduced into the packet 19

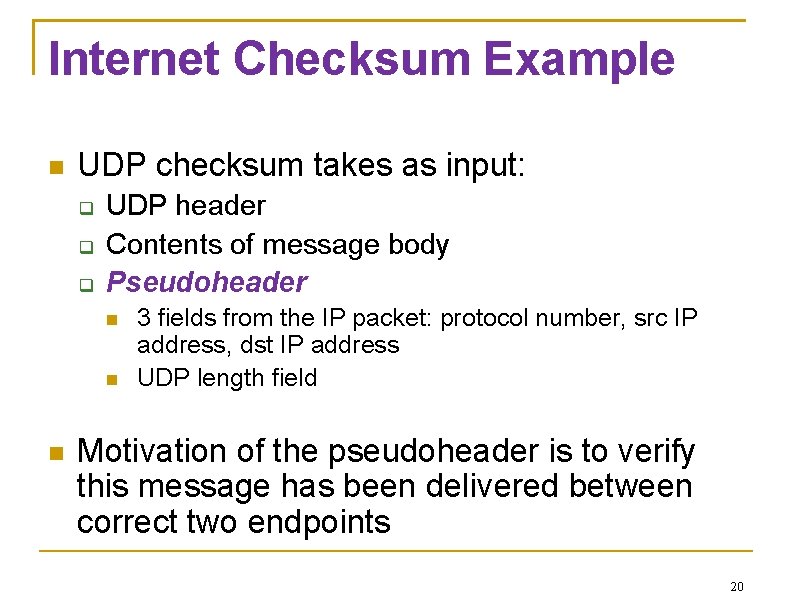
Internet Checksum Example UDP checksum takes as input: UDP header Contents of message body Pseudoheader 3 fields from the IP packet: protocol number, src IP address, dst IP address UDP length field Motivation of the pseudoheader is to verify this message has been delivered between correct two endpoints 20

Reliable Byte Stream (TCP) In contrast to UDP, Transmission Control Protocol (TCP) offers the following services Reliable Connection oriented Byte-stream service

Flow control VS Congestion control Flow control involves preventing senders from overrunning the capacity of the receivers Congestion control involves preventing too much data from being injected into the network, thereby causing switches or links to become overloaded

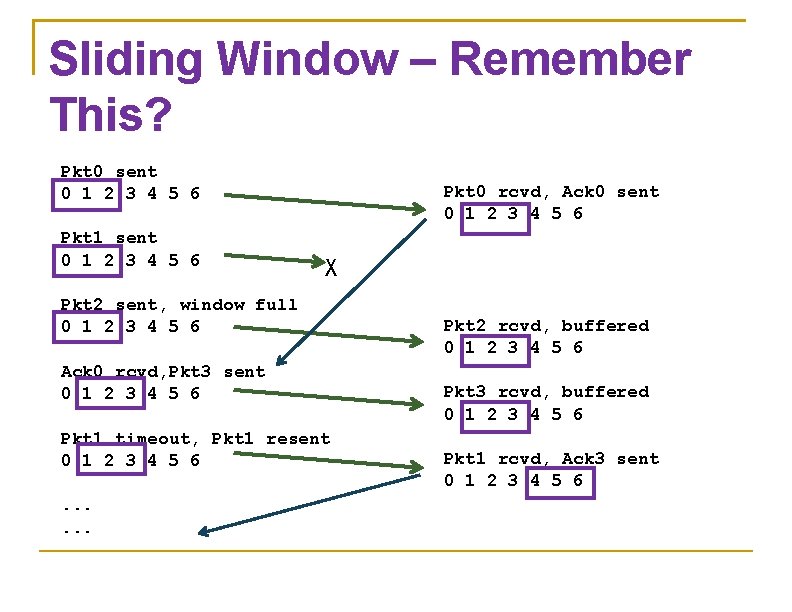
End-to-end Issues At the heart of TCP is the sliding window algorithm (discussed in Chapter 2)

Sliding Window – Remember This? Pkt 0 sent 0 1 2 3 4 5 6 Pkt 1 sent 0 1 2 3 4 5 6 Pkt 0 rcvd, Ack 0 sent 0 1 2 3 4 5 6 X Pkt 2 sent, window full 0 1 2 3 4 5 6 Ack 0 rcvd, Pkt 3 sent 0 1 2 3 4 5 6 Pkt 1 timeout, Pkt 1 resent 0 1 2 3 4 5 6. . . Pkt 2 rcvd, buffered 0 1 2 3 4 5 6 Pkt 3 rcvd, buffered 0 1 2 3 4 5 6 Pkt 1 rcvd, Ack 3 sent 0 1 2 3 4 5 6

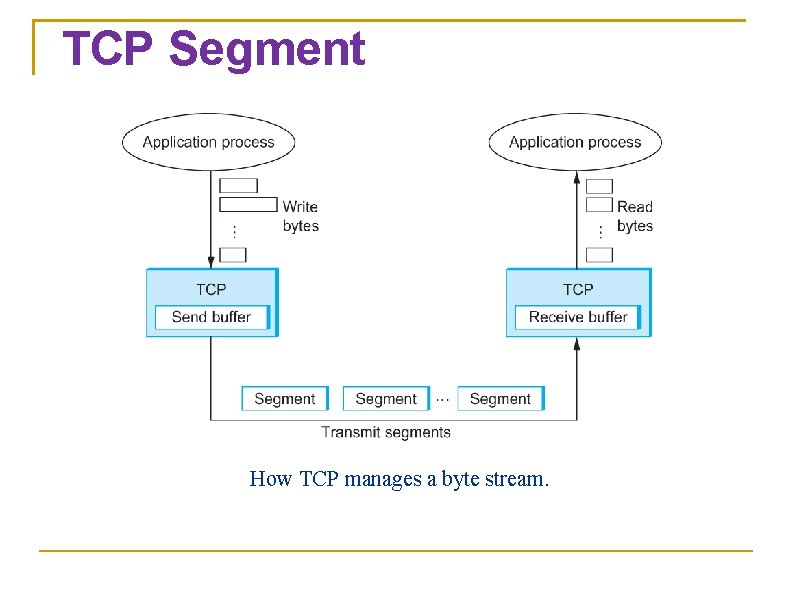
TCP Segment TCP on the source host buffers enough bytes from the sending process to fill a reasonably sized packet and then sends this packet to its peer on the destination host. TCP on the destination host then empties the contents of the packet into a receive buffer, and the receiving process reads from this buffer at its leisure. The packets exchanged between TCP peers are called segments.

TCP Segment How TCP manages a byte stream.

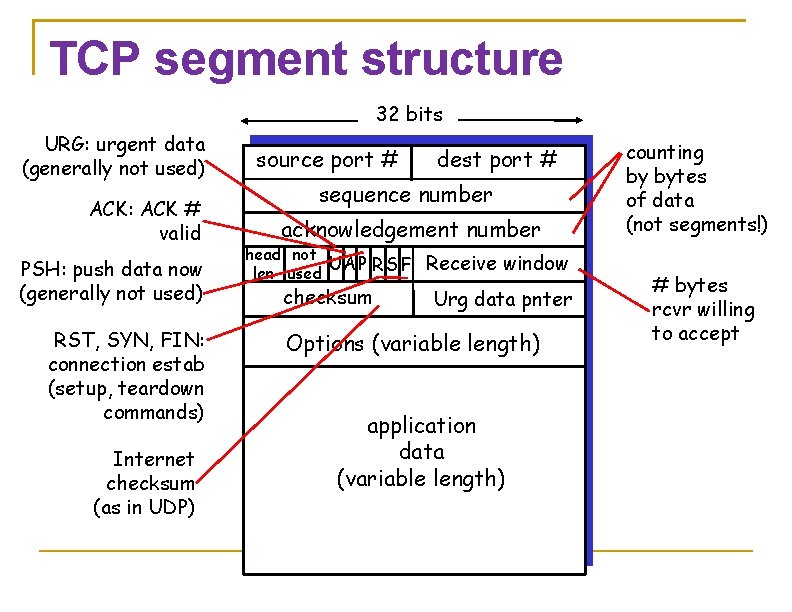
TCP segment structure 32 bits URG: urgent data (generally not used) ACK: ACK # valid PSH: push data now (generally not used) RST, SYN, FIN: connection estab (setup, teardown commands) Internet checksum (as in UDP) source port # dest port # sequence number acknowledgement number head not UA P R S F len used checksum Receive window Urg data pnter Options (variable length) application data (variable length) counting by bytes of data (not segments!) # bytes rcvr willing to accept

Multiplexing/demultiplexing What do these words mean, again? 28

Multiplexing/demultiplexing What do these words mean, again? Multiplexing – combines multiple streams of information for transmission over a shared medium Demultiplexing – takes combined streams of information and separates the streams Often abbreviated as demux 29

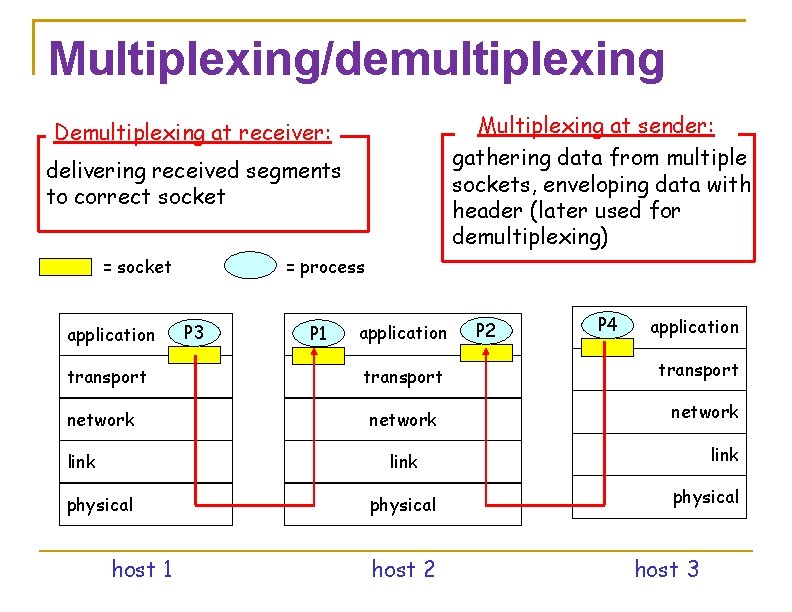
Multiplexing/demultiplexing Multiplexing at sender: gathering data from multiple sockets, enveloping data with header (later used for demultiplexing) Demultiplexing at receiver: delivering received segments to correct socket = process = socket application transport network link P 3 P 1 application transport network P 2 P 4 application transport network link physical host 1 physical host 2 physical host 3

How demultiplexing works Host uses IP addresses & port numbers to direct segment to appropriate socket

Source Ports and Destination Ports How does UDP (or TCP) know which source and destination ports to use? 32

Source Ports and Destination Ports How does UDP (or TCP) know which source and destination ports to use? Servers tend to listen on “well-known ports” We can utilize this information Client uses well-known destination port number (e. g. port 80 to connect to web server) Server uses well-known source port number to listen for incoming connections (e. g. port 80 if web server) 33

Source Ports and Destination Ports What about the client’s source port? Operating systems pick a random, temporary port Guaranteed to be > 1024 IANA suggests between 49, 152 – 65, 535 What about the server’s destination port? 34