Chapter 5 Telecommunication and Networks Chapter 5 Telecommunication












- Slides: 28

Chapter 5 Telecommunication and Networks Chapter 5

Telecommunication Principles and Applications § Communication • The exchange of information between two parties § Telecommunication • Communication at a distance Chapter 5 2

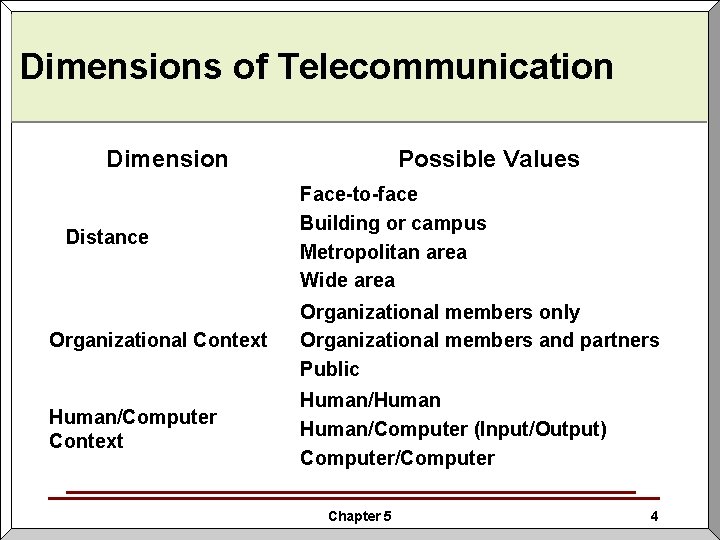
Telecommunication Principles and Applications § Dimensions of Telecommunication • Distance significantly affects options for communication • Organizational context establishes the nature of the relationships between the communicating parties Chapter 5 3

Dimensions of Telecommunication Dimension Distance Possible Values Face-to-face Building or campus Metropolitan area Wide area Organizational Context Organizational members only Organizational members and partners Public Human/Computer Context Human/Human/Computer (Input/Output) Computer/Computer Chapter 5 4

Telecommunication Principles and Applications § Telecommunication Process • Sender initiates message communication • Device puts sender’s message onto a telecommunication medium • Telecommunication medium transfers message to receiver’s location Chapter 5 5

Telecommunication Principles and Applications § Telecommunication Process • Device takes message off the communication medium • Recipient receives the message Chapter 5 6

Telecommunication Principles and Applications § Types of Business Applications • Coordination of business activities • Group decision making • Electronic commerce Chapter 5 7

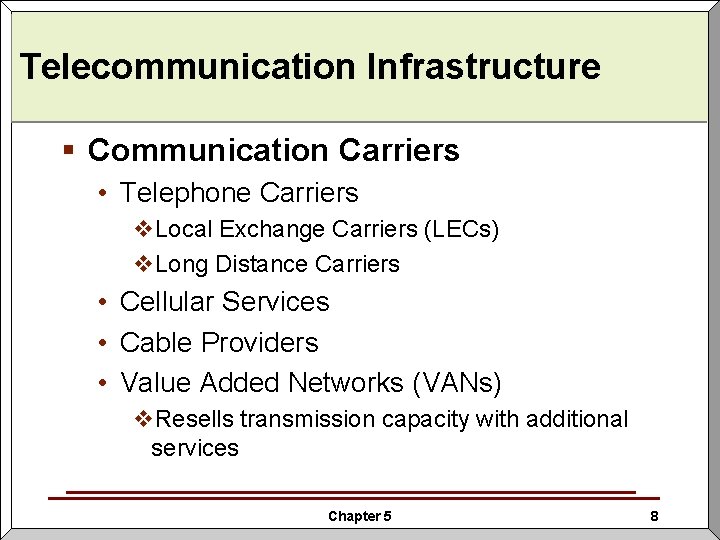
Telecommunication Infrastructure § Communication Carriers • Telephone Carriers v. Local Exchange Carriers (LECs) v. Long Distance Carriers • Cellular Services • Cable Providers • Value Added Networks (VANs) v. Resells transmission capacity with additional services Chapter 5 8

Telecommunication Infrastructure § International Issues • Monopoly government providers in many countries • Decreasing regulation worldwide • Cross-border data flow regulations • Differences in privacy rules Chapter 5 9

Telecommunication Technology § Standards • Characteristics of telecommunications media, hardware, and software § Open Systems Interconnection (OSI) Model • Provides a framework for thinking about communication standards Chapter 5 10

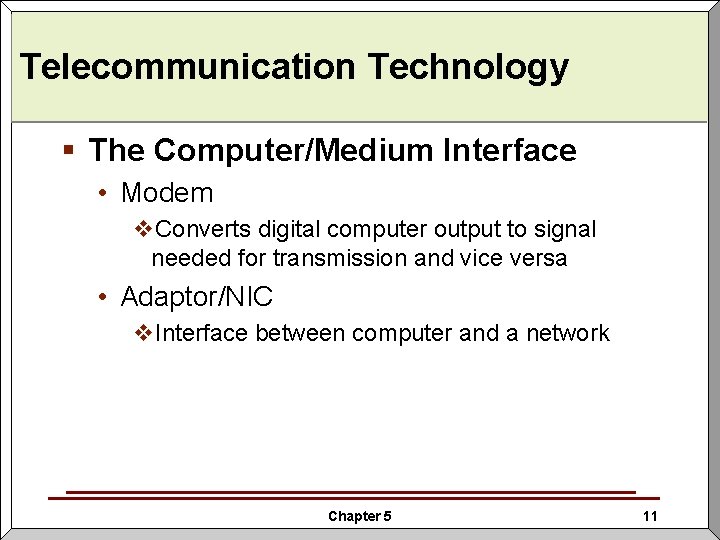
Telecommunication Technology § The Computer/Medium Interface • Modem v. Converts digital computer output to signal needed for transmission and vice versa • Adaptor/NIC v. Interface between computer and a network Chapter 5 11

Telecommunication Technology § Transmission Media • • • Twisted pair wire Coaxial cable Fiber optic cable Microwave signals Infrared signals Radio signals Chapter 5 12

Telecommunication Technology § Switching and Routing Technologies • Devices v. Hub v. Switch v. Router v. Gateway • Protocol v. Standard for how a message is packaged, secured, sent routed, received, and acknowledged by the receiver within a network Chapter 5 13

Telecommunication Technology § LAN Protocols • • Ethernet Token ring Wi-Fi Bluetooth Chapter 5 14

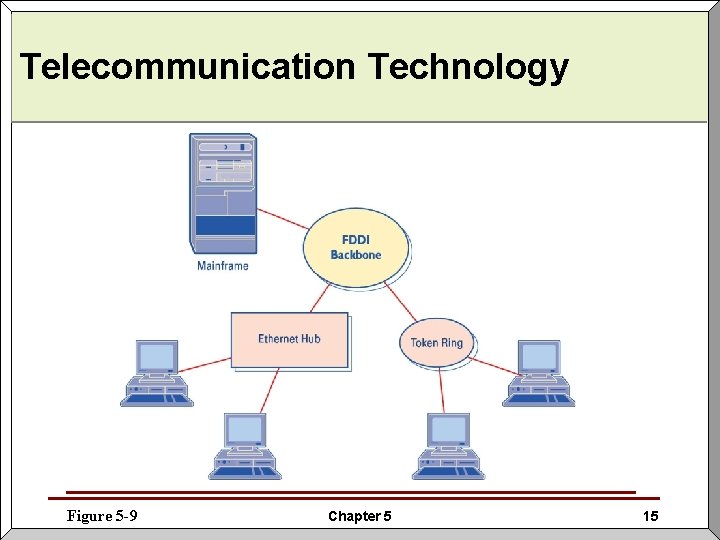
Telecommunication Technology Figure 5 -9 Chapter 5 15

Telecommunication Technology § WAN Services • • Leased lines Switched circuit data services Packet switched services Cellular services Chapter 5 16

Internet Concepts § Who Manages The Internet? • Companies, individuals, and governments own pieces of the Internet, but the Internet as a whole has no owners or operators Chapter 5 17

Internet Concepts § Network Addressing • IP Number v. Consists of two parts—a network number and a device number • Domain Name v. Translated to IP number by Domain Name Servers (DNSs) Chapter 5 18

Network Management § Simple Network Management Protocol • Defines how network devices maintain and communicate information about their own activity and performance Chapter 5 19

Network Management § Network Analyzer • Plugs into a network and analyzes the traffic that passes by or through it Chapter 5 20

Network Management v. Network Management Software v. Device management v. Recognizes the devices, including computers and printers, that are connected to the network v. Security services v. Provide entry into the network and establish a relationship between a user and a client station Chapter 5 21

Network Management § Network Management Software • File services v. Provide access to shared files • Print services v. Provide central access to a common printer • Fax services v. Allow network users to send or receive a facsimile electronically Chapter 5 22

Network Management § Network Management Software • Directory services v. Provide an enterprise-wide telephone book that identifies and connects network users to each other and to software Chapter 5 23

Ensuring Telecommunication Security § Key: A secret code that can scramble or unscramble a message § Public Key Cryptography • Uses a pair of keys v. Message scrambled by one key can only be unscrambled by the other Chapter 5 24

Ensuring Telecommunication Security Figure 5 -9 Public Key Cryptography Chapter 5 25

Ensuring Telecommunication Security § Public key cryptography ensures • Security • Non-repudiation • Authentication v. Requires certificate authority • Non-repudiation v. Via digital signature • Integrity Chapter 5 26

Ensuring Telecommunication Security § Firewall • Hardware and/or software intended to separate an organization’s intranet, and the data on it, from its extranet and the Internet § Virtual Private Network (VPN) • Simulates a private network by using a public network, such as Internet, and security protocols Chapter 5 27

End of Chapter 5 Telecommunication and Networks Chapter 5