Chapter 5 PeertoPeer Protocols and Data Link Layer




















- Slides: 73

Chapter 5 Peer-to-Peer Protocols and Data Link Layer PART I: General Overview Peer-to-Peer Protocols Data Link Layer Functions

Peer-to-Peer Protocols l Peer-to-Peer protocols: many protocols involve the interaction between two peers l l l May be implemented at different layers. For example: Data Link Layer (PPP, HDLC, etc) Transport Layer (e. g. , TCP) Many networking services can be implemented at different layers: e. g. , Error Detection & Retransmission, Sequencing, Timing, Flow Control, Segmentation & Blocking, Multiplexing, Security (Encryption, Authentication) etc Focus mainly on Data Link Layer (DLC) services (in this part)

Service Models l l The service model specifies the information transfer service layer-n provides to layer(n+1) Important distinction is whether the service is: l l l Connection-oriented Connection-less Also, whether functions are implemented as: l l End-to-End Hop-by-Hop

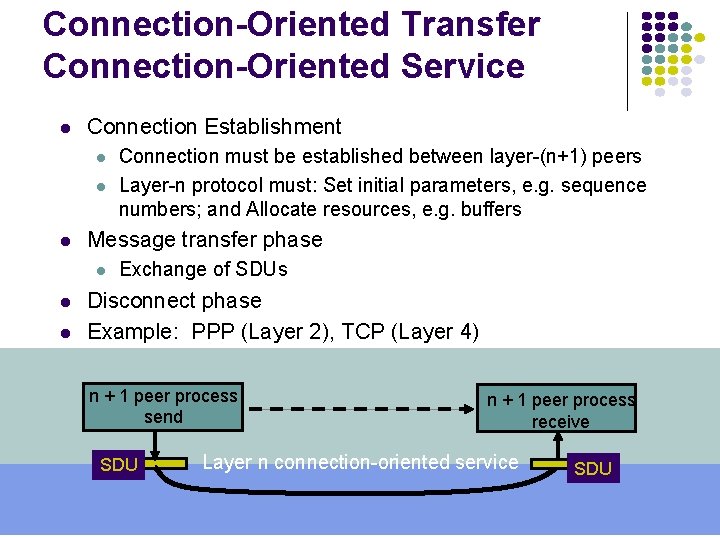
Connection-Oriented Transfer Connection-Oriented Service l Connection Establishment l l l Message transfer phase l l l Connection must be established between layer-(n+1) peers Layer-n protocol must: Set initial parameters, e. g. sequence numbers; and Allocate resources, e. g. buffers Exchange of SDUs Disconnect phase Example: PPP (Layer 2), TCP (Layer 4) n + 1 peer process send SDU n + 1 peer process receive Layer n connection-oriented service SDU

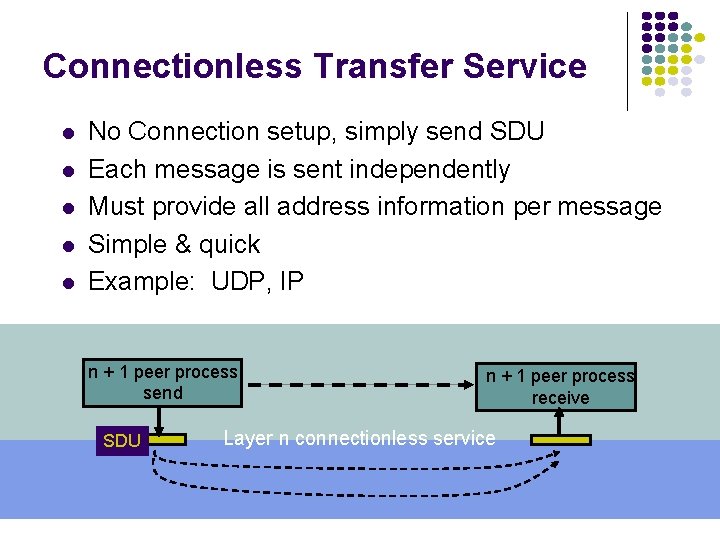
Connectionless Transfer Service l l l No Connection setup, simply send SDU Each message is sent independently Must provide all address information per message Simple & quick Example: UDP, IP n + 1 peer process send SDU n + 1 peer process receive Layer n connectionless service

End-to-End vs. Hop-by-Hop l A service feature can be provided by implementing a protocol l Example: l l l end-to-end across the network across every hop in the network Perform error control at every hop in the network or only between the source and destination? Perform flow control between every hop in the network or only between source & destination? There are tradeoffs between the two approaches

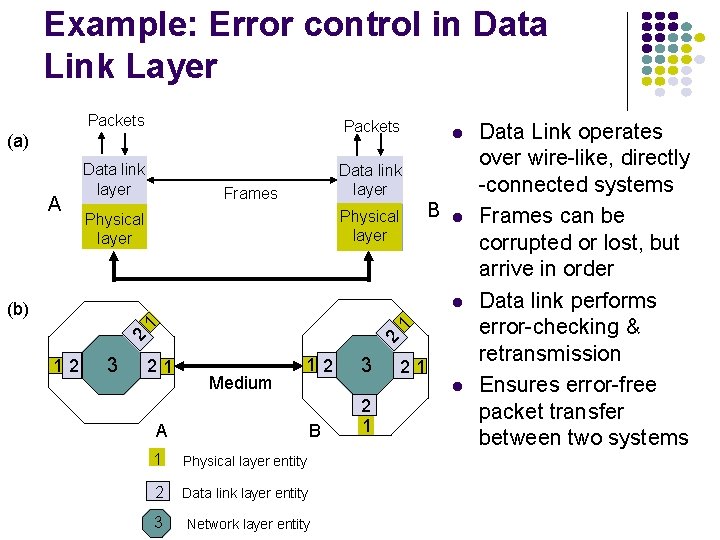
Example: Error control in Data Link Layer Packets Data link layer (a) A Frames B Physical layer l l l 12 3 2 2 1 1 (b) 21 Medium 12 21 l B A 3 1 Physical layer entity 2 Data link layer entity 3 Network layer entity 2 1 Data Link operates over wire-like, directly -connected systems Frames can be corrupted or lost, but arrive in order Data link performs error-checking & retransmission Ensures error-free packet transfer between two systems

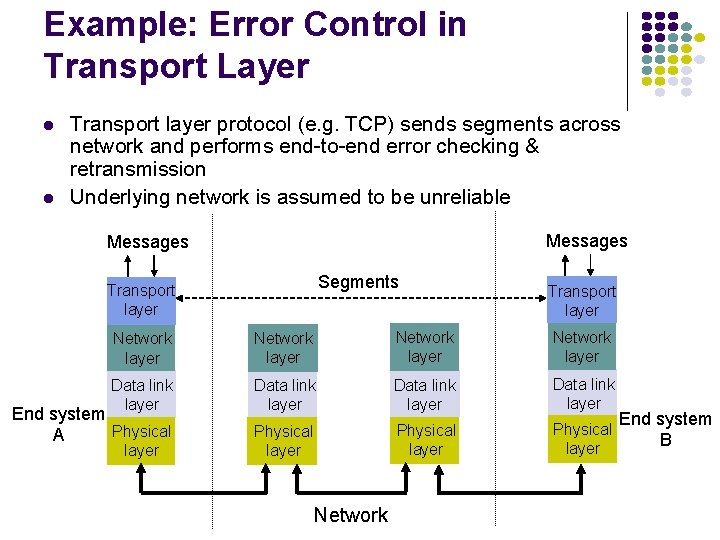
Example: Error Control in Transport Layer l l Transport layer protocol (e. g. TCP) sends segments across network and performs end-to-end error checking & retransmission Underlying network is assumed to be unreliable Messages Segments Transport layer Network layer Data link layer Physical layer End system Physical A Network End system B

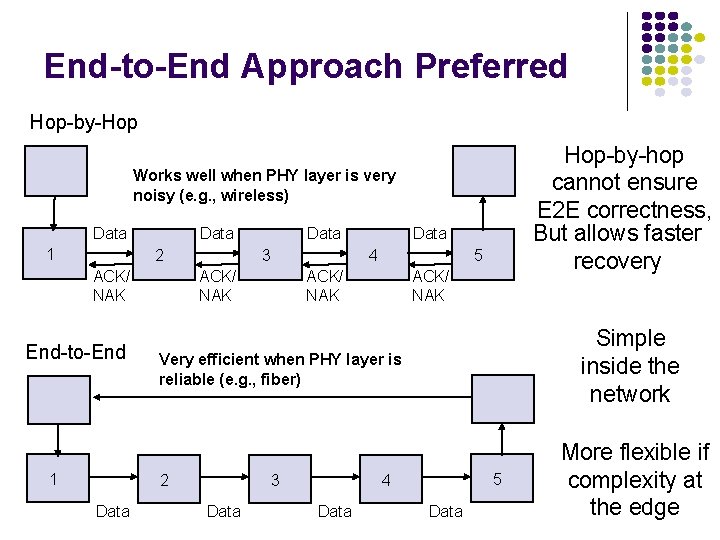
End-to-End Approach Preferred Hop-by-Hop Hop-by-hop cannot ensure E 2 E correctness, But allows faster recovery Works well when PHY layer is very noisy (e. g. , wireless) Data 1 Data 2 ACK/ NAK End-to-End 1 3 Data 4 ACK/ NAK 5 ACK/ NAK Simple inside the network Very efficient when PHY layer is reliable (e. g. , fiber) 2 Data 3 Data 5 4 Data More flexible if complexity at the edge

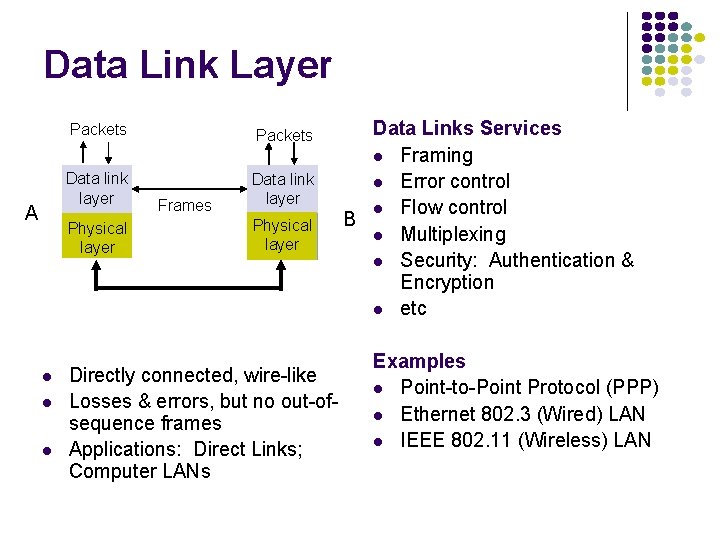
Data Link Layer A Packets Data link layer Physical layer l l l Frames Physical layer Directly connected, wire-like Losses & errors, but no out-ofsequence frames Applications: Direct Links; Computer LANs Data Links Services l Framing l Error control l Flow control B l Multiplexing l Security: Authentication & Encryption l etc Examples l Point-to-Point Protocol (PPP) l Ethernet 802. 3 (Wired) LAN l IEEE 802. 11 (Wireless) LAN

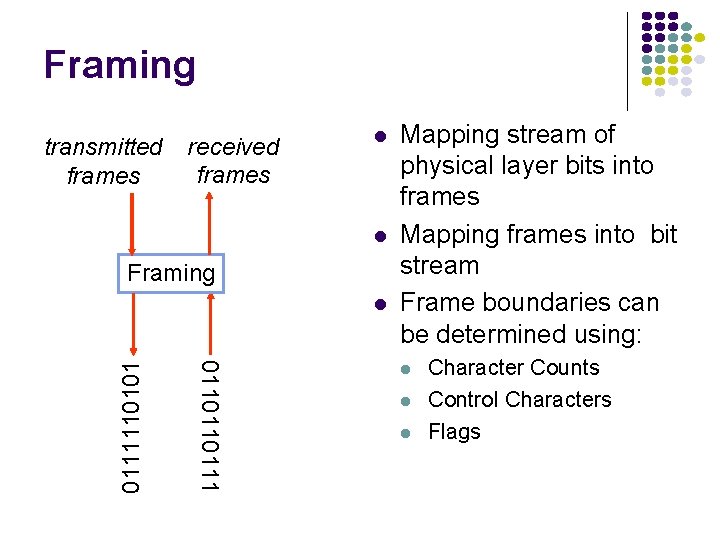
Framing transmitted frames received frames l l Framing 0110110111110101 l Mapping stream of physical layer bits into frames Mapping frames into bit stream Frame boundaries can be determined using: l l l Character Counts Control Characters Flags

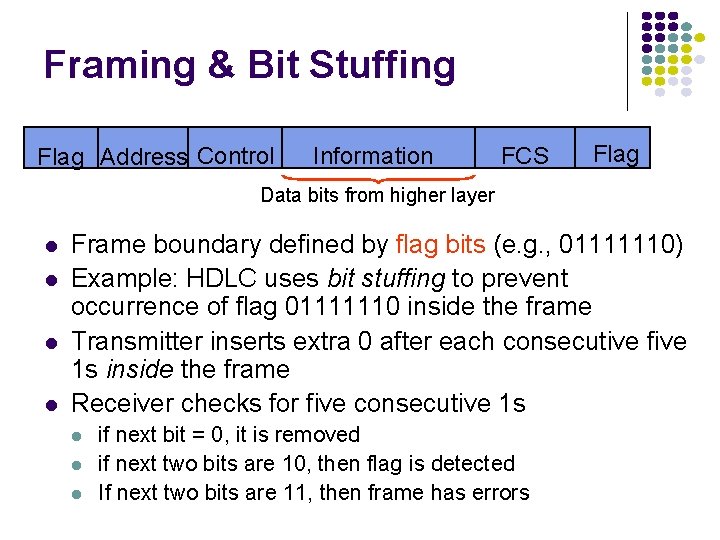
Framing & Bit Stuffing Flag Address Control Information FCS Flag Data bits from higher layer l l Frame boundary defined by flag bits (e. g. , 01111110) Example: HDLC uses bit stuffing to prevent occurrence of flag 01111110 inside the frame Transmitter inserts extra 0 after each consecutive five 1 s inside the frame Receiver checks for five consecutive 1 s l l l if next bit = 0, it is removed if next two bits are 10, then flag is detected If next two bits are 11, then frame has errors

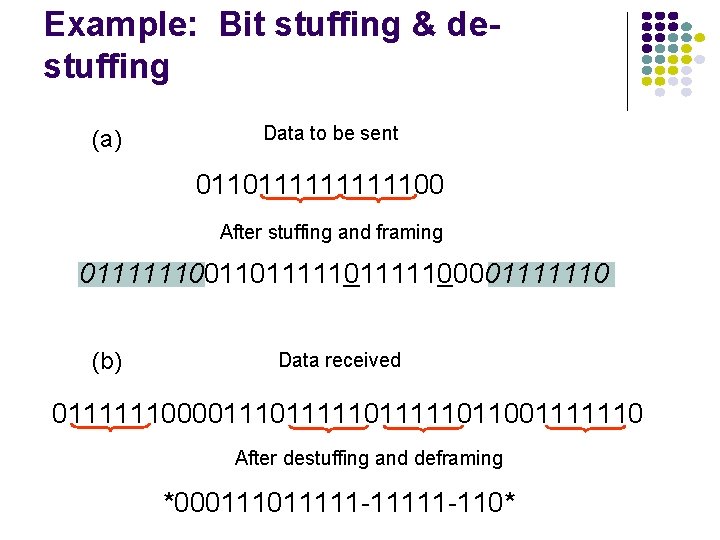
Example: Bit stuffing & destuffing (a) Data to be sent 01101111100 After stuffing and framing 0111111001101111100001111110 (b) Data received 0111111000011111011111011001111110 After destuffing and deframing *00011111 -11111 -110*

Error Detection & Retransmission l l Purpose: to ensure a sequence of information packets is delivered in order and without errors or duplications despite physical layer problems Technique known as: Automatic Repeat Request (ARQ) l l Stop-and-Wait ARQ Go-Back N ARQ Selective Repeat ARQ Basic elements of ARQ: l l l Error-detecting codes ACKs (acknowledgment messages) Timeout mechanisms

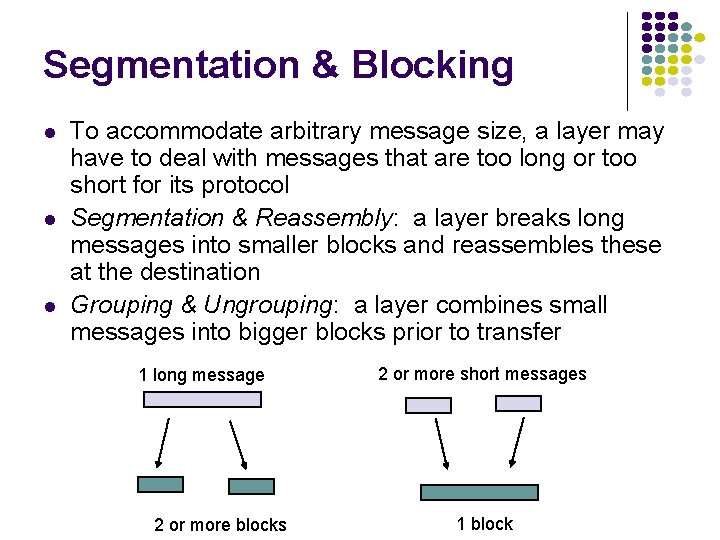
Segmentation & Blocking l l l To accommodate arbitrary message size, a layer may have to deal with messages that are too long or too short for its protocol Segmentation & Reassembly: a layer breaks long messages into smaller blocks and reassembles these at the destination Grouping & Ungrouping: a layer combines small messages into bigger blocks prior to transfer 1 long message 2 or more blocks 2 or more short messages 1 block

Pacing and Flow Control l l Messages can be lost if receiving system does not have sufficient buffering to store arriving messages If destination layer-(n+1) does not retrieve its information fast enough, destination layer-n buffers may overflow Flow Control provide backpressure mechanisms that control transfer according to availability of buffers at the destination Examples: TCP and HDLC

Timing l l l Applications involving voice and video generate units of information that are related temporally Destination application must reconstruct temporal relation in voice/video units Network transfer introduces delay & jitter Timing Recovery protocols use timestamps & sequence numbering to control the delay & jitter in delivered information Examples: RTP & associated protocols in Voice over IP

Multiplexing l l l Multiplexing enables multiple layer-(n+1) users to share a layer-n service A multiplexing tag is required to identify specific users at the destination Examples: UDP, IP

Privacy, Integrity, & Authentication l l Privacy: ensuring that information transferred cannot be read by others Integrity: ensuring that information is not altered during transfer Authentication: verifying that sender and/or receiver are who they claim to be Security protocols provide these services and are discussed in Chapter 11

Chapter 5 Peer-to-Peer Protocols and Data Link Layer ARQ Protocols and Reliable Data Transfer

Automatic Repeat Request (ARQ) l l l Purpose: to ensure a sequence of information packets is delivered in order and without errors or duplications despite transmission errors & losses Combines error detection and retransmission to ensure data is delivered accurately We will look at: l l Stop-and-Wait ARQ Go-Back N ARQ Selective Repeat ARQ Basic elements of ARQ: l l l Error-detecting codes ACKs (acknowledgment messages) Timeout mechanisms

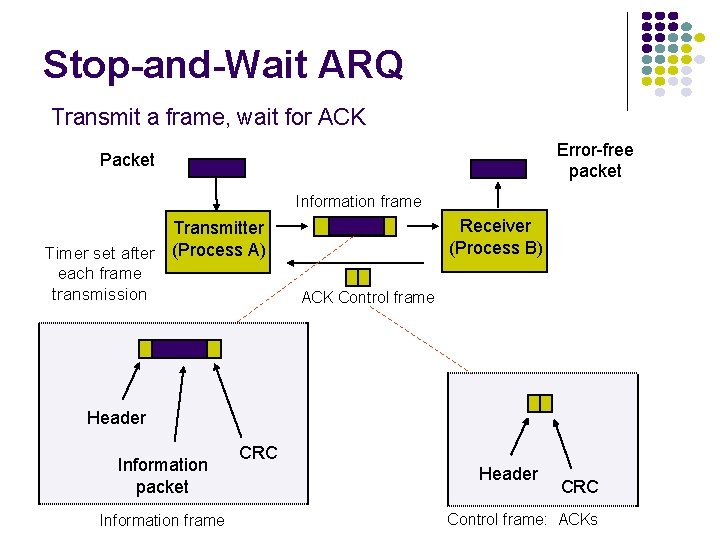
Stop-and-Wait ARQ Transmit a frame, wait for ACK Error-free packet Packet Information frame Receiver (Process B) Transmitter Timer set after (Process A) each frame transmission ACK Control frame Header Information packet Information frame CRC Header CRC Control frame: ACKs

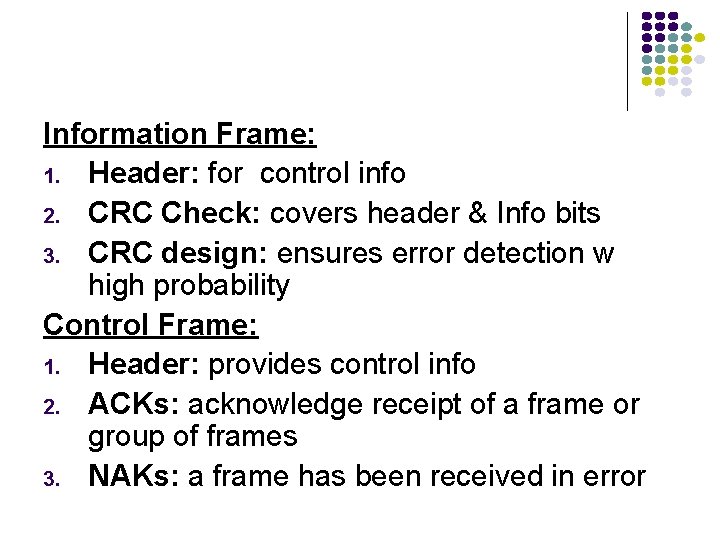
Information Frame: 1. Header: for control info 2. CRC Check: covers header & Info bits 3. CRC design: ensures error detection w high probability Control Frame: 1. Header: provides control info 2. ACKs: acknowledge receipt of a frame or group of frames 3. NAKs: a frame has been received in error

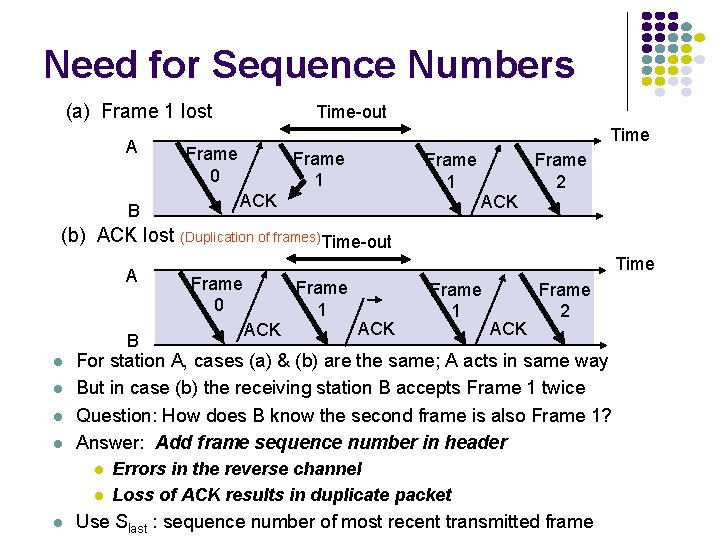
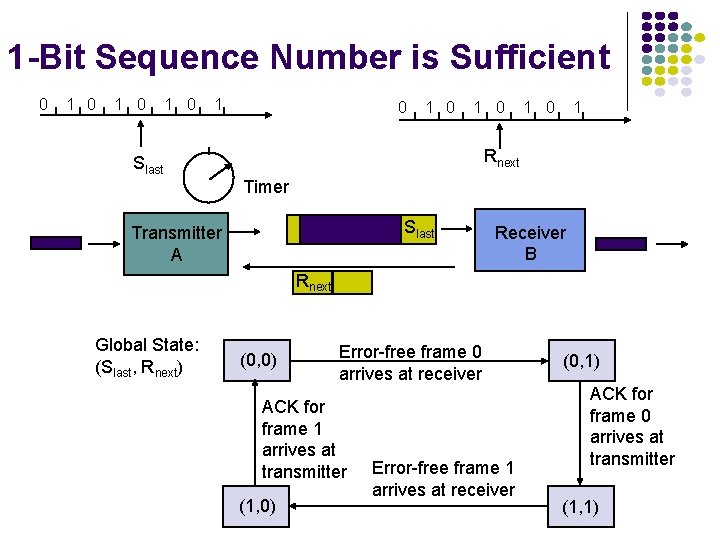
Need for Sequence Numbers (a) Frame 1 lost A B Time-out Time Frame 0 Frame 1 ACK Frame 2 ACK (b) ACK lost (Duplication of frames)Time-out A B l l Frame 0 Frame 1 ACK Frame 2 For station A, cases (a) & (b) are the same; A acts in same way But in case (b) the receiving station B accepts Frame 1 twice Question: How does B know the second frame is also Frame 1? Answer: Add frame sequence number in header l l l Time Errors in the reverse channel Loss of ACK results in duplicate packet Use Slast : sequence number of most recent transmitted frame

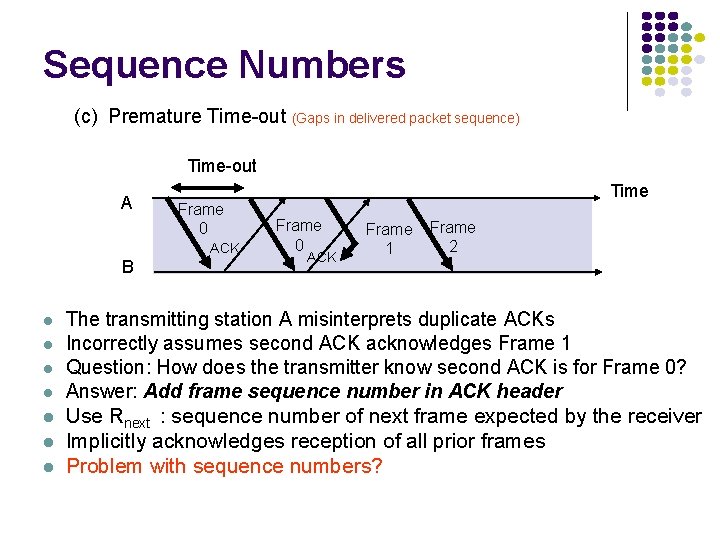
Sequence Numbers (c) Premature Time-out (Gaps in delivered packet sequence) Time-out A Frame 0 ACK B l l l l Time Frame 0 ACK Frame 1 Frame 2 The transmitting station A misinterprets duplicate ACKs Incorrectly assumes second ACK acknowledges Frame 1 Question: How does the transmitter know second ACK is for Frame 0? Answer: Add frame sequence number in ACK header Use Rnext : sequence number of next frame expected by the receiver Implicitly acknowledges reception of all prior frames Problem with sequence numbers?

1 -Bit Sequence Number is Sufficient 0 1 0 1 Rnext Slast Timer Slast Transmitter A Receiver B Rnext Global State: (Slast, Rnext) (0, 0) Error-free frame 0 arrives at receiver ACK for frame 1 arrives at transmitter (1, 0) Error-free frame 1 arrives at receiver (0, 1) ACK for frame 0 arrives at transmitter (1, 1)

Stop-and-Wait ARQ Transmitter Ready state l l l Await request from higher layer for packet transfer When request arrives, transmit frame with updated Slast and CRC Go to Wait State Receiver Always in Ready State l l Wait state l l Wait for ACK or timer to expire; block requests from higher layer If timeout expires l l l retransmit frame and reset timer l If sequence number is incorrect or if errors detected: ignore ACK If sequence number is correct (Rnext = Slast +1): accept frame, go to Ready state l l accept frame, update Rnext, send ACK frame with Rnext, deliver packet to higher layer If no errors detected and wrong sequence number l If ACK received: l Wait for arrival of new frame When frame arrives, check for errors If no errors detected and sequence number is correct (Slast=Rnext), then discard frame send ACK frame with Rnext If errors detected l discard frame

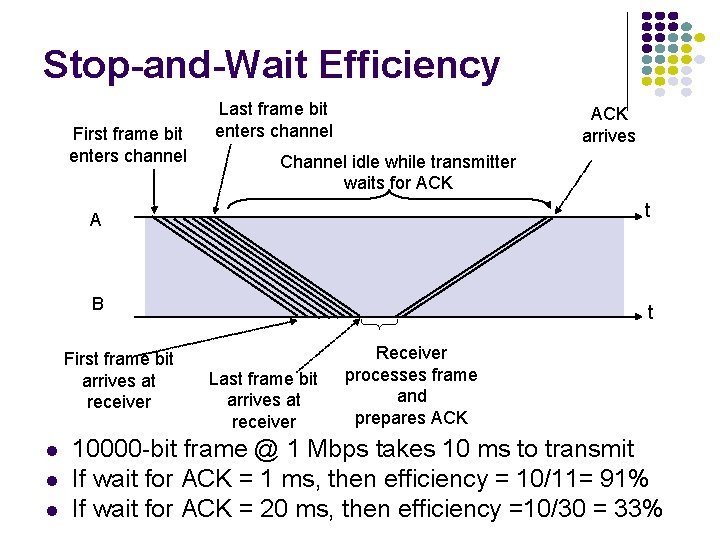
Stop-and-Wait Efficiency l l l Stop-and-wait works well over channels with small propagation delay Inefficient when prop delay is much larger than time to transmit frame Example: l l l Frame = 1000 bits over 1. 5 Mbps channel Time from beginning of Tx to receipt of ACK = 40 ms No of bits that can be tx is 40 ms X 1. 5 Mbps = 60, 000 bits Efficiency = 1000/60, 000 = 1. 6% Large delay-BW prod = prod of bit rate and delay before an action takes place Delay-BW prod = LOST OPPORTUNITY in terms of Tx bits

Stop-and-Wait Efficiency First frame bit enters channel Last frame bit enters channel ACK arrives Channel idle while transmitter waits for ACK t A B First frame bit arrives at receiver l l l t Last frame bit arrives at receiver Receiver processes frame and prepares ACK 10000 -bit frame @ 1 Mbps takes 10 ms to transmit If wait for ACK = 1 ms, then efficiency = 10/11= 91% If wait for ACK = 20 ms, then efficiency =10/30 = 33%

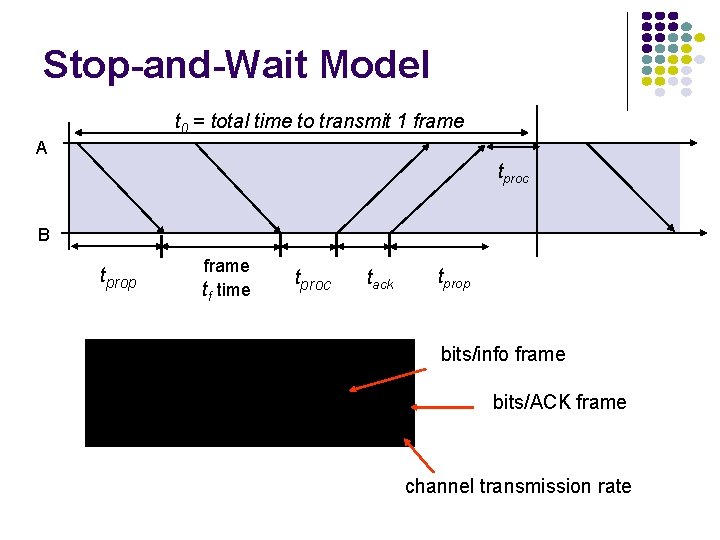
Stop-and-Wait Model t 0 = total time to transmit 1 frame A tproc B tprop frame tf time tproc tack tprop bits/info frame bits/ACK frame channel transmission rate

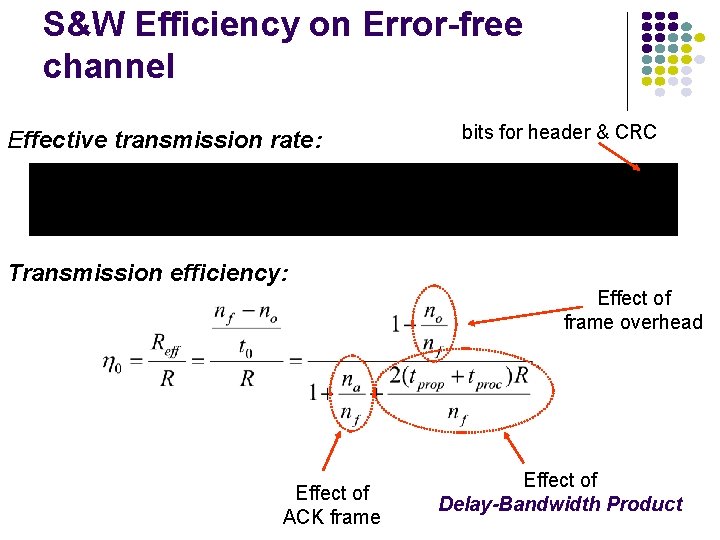
S&W Efficiency on Error-free channel Effective transmission rate: bits for header & CRC Transmission efficiency: Effect of frame overhead Effect of ACK frame Effect of Delay-Bandwidth Product

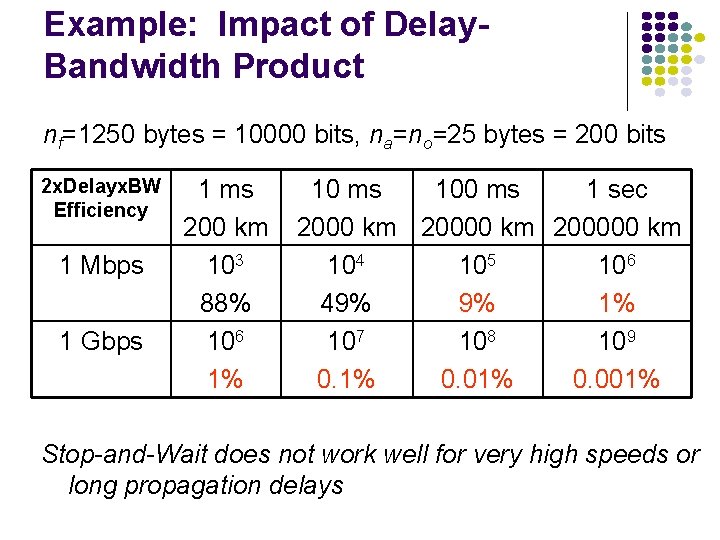
Example: Impact of Delay. Bandwidth Product nf=1250 bytes = 10000 bits, na=no=25 bytes = 200 bits 2 x. Delayx. BW Efficiency 1 Mbps 1 Gbps 1 ms 200 km 103 88% 106 1% 10 ms 100 ms 1 sec 2000 km 200000 km 104 105 106 49% 9% 1% 107 108 109 0. 1% 0. 001% Stop-and-Wait does not work well for very high speeds or long propagation delays

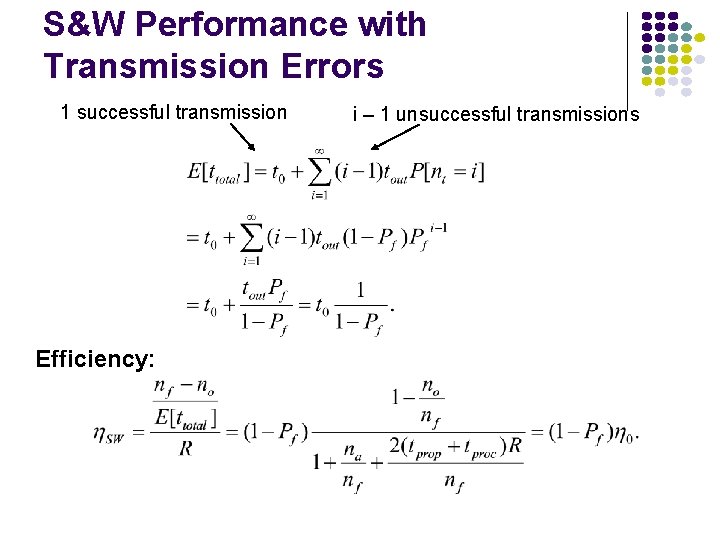
S&W Performance with Transmission Errors 1 successful transmission Efficiency: i – 1 unsuccessful transmissions

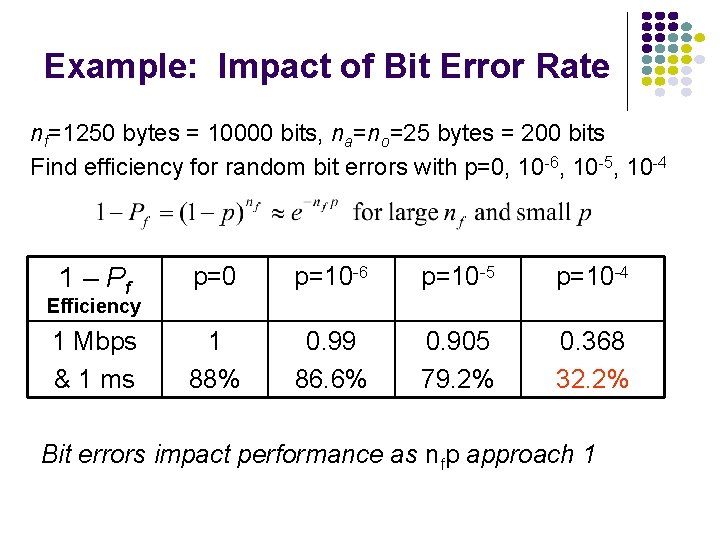
Example: Impact of Bit Error Rate nf=1250 bytes = 10000 bits, na=no=25 bytes = 200 bits Find efficiency for random bit errors with p=0, 10 -6, 10 -5, 10 -4 1 – Pf p=0 p=10 -6 p=10 -5 p=10 -4 1 Mbps & 1 ms 1 88% 0. 99 86. 6% 0. 905 79. 2% 0. 368 32. 2% Efficiency Bit errors impact performance as nfp approach 1

Go-Back-N ARQ l l l Improve Stop-and-Wait efficiency by not waiting! Keep channel busy by continuing to send frames Allow a window of Ws non-acknowledged frames Use m-bit sequence numbering If ACK for oldest frame arrives before window is exhausted, we can continue transmitting If window is exhausted, Go Back and retransmit all outstanding frames (starting from the oldest nonacknowledged one)

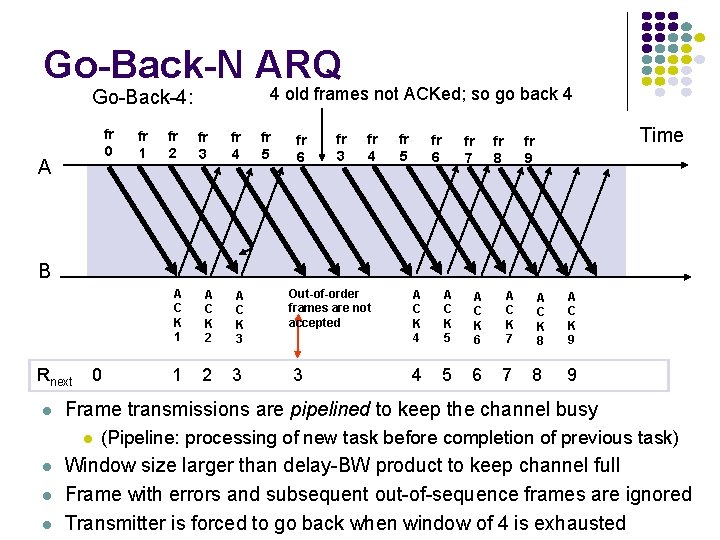
Go-Back-N ARQ 4 old frames not ACKed; so go back 4 Go-Back-4: fr 0 A fr 1 fr 2 fr 3 fr 4 fr 5 fr 6 fr 7 fr 8 Time fr 9 B Rnext l 0 l l A C K 2 A C K 3 1 2 3 Out-of-order frames are not accepted 3 A C K 4 A C K 5 A C K 6 A C K 7 4 5 6 7 A C K 8 8 A C K 9 9 Frame transmissions are pipelined to keep the channel busy l l A C K 1 (Pipeline: processing of new task before completion of previous task) Window size larger than delay-BW product to keep channel full Frame with errors and subsequent out-of-sequence frames are ignored Transmitter is forced to go back when window of 4 is exhausted

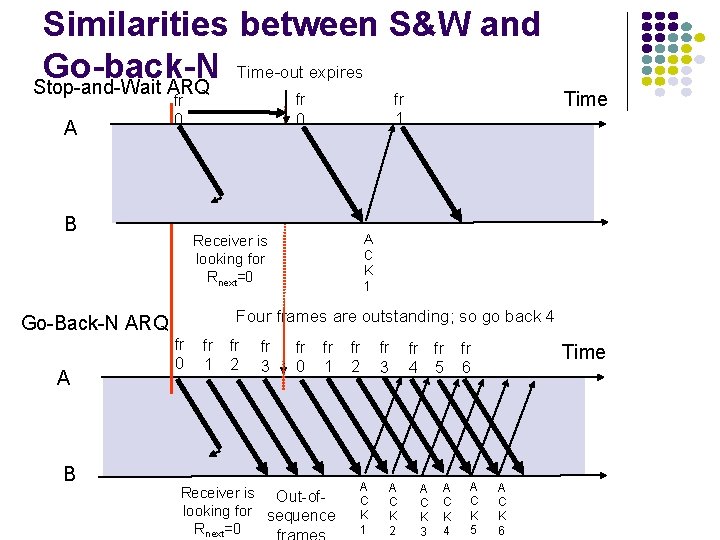
Similarities between S&W and Time-out expires Go-back-N Stop-and-Wait ARQ A B B Time A C K 1 Receiver is looking for Rnext=0 Four frames are outstanding; so go back 4 Go-Back-N ARQ A fr 1 fr 0 fr 1 fr 2 fr 3 fr 0 fr 1 Receiver is Out-oflooking for sequence Rnext=0 fr 2 A C K 1 fr 3 A C K 2 fr fr 4 5 A C K 3 A C K 4 fr 6 A C K 5 Time A C K 6

Similarities between S&W and go-back-N in error recovery Error: l S&W: error results in loss of Tx time equal to time-out period l Go-back-N: error results in loss of Tx time equal to the Tx of Ws frames Error Recovery: l S&W: Receiver is looking for frame with correct Rnext(0 or 1) Go-back-N: Receiver is looking for frame with l correct Rnext (0, 1, …, N-1)

Similarities between S&W and go-back-N in error recovery l l S&W: Transmitter keeps sending the frame every time-out period until acknowledged Go-back-N: Identify oldest outstanding unacknowledged frame and sent it together with the subsequent Ws-1 frames

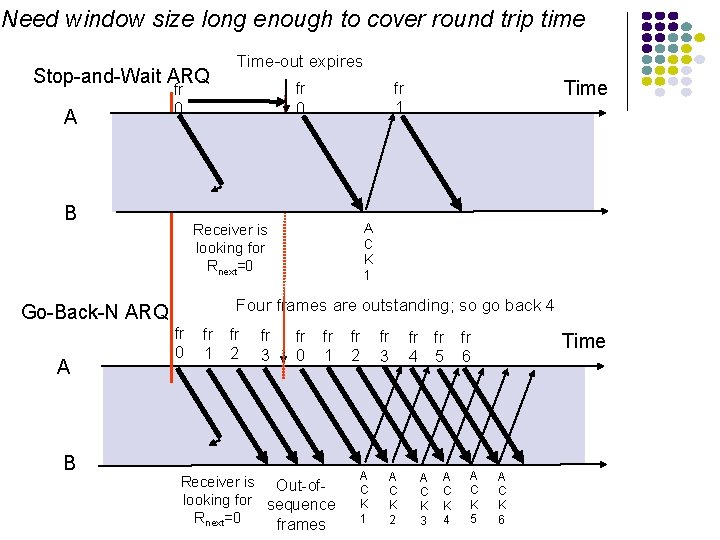
Need window size long enough to cover round trip time Stop-and-Wait ARQ A A C K 1 Receiver is looking for Rnext=0 Four frames are outstanding; so go back 4 Go-Back-N ARQ B Time fr 1 fr 0 B A Time-out expires fr 0 fr 1 fr 2 fr 3 fr 0 fr 1 Receiver is Out-oflooking for sequence Rnext=0 frames fr 2 A C K 1 fr 3 A C K 2 fr fr 4 5 A C K 3 A C K 4 fr 6 A C K 5 Time A C K 6

Go-Back-N with Timeout l Problem with Go-Back-N as presented: l l If frame is lost and source does not have frame to send, then window will not be exhausted and recovery will not be initiated Use a timeout with each frame l When timeout expires, resend all outstanding frames

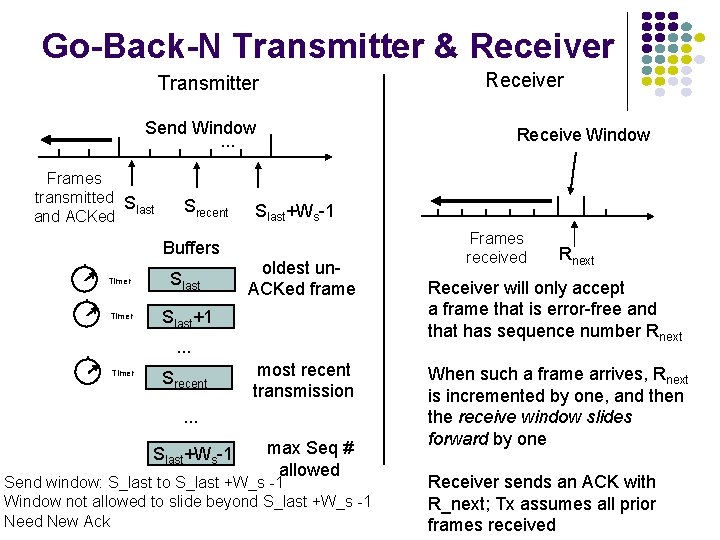
Go-Back-N Transmitter & Receiver Transmitter Send Window. . . Frames transmitted S last and ACKed Srecent Buffers Timer Slast+1 Receive Window Slast+Ws-1 oldest un. ACKed frame . . . Timer Srecent most recent transmission . . . Slast+Ws-1 max Seq # allowed Send window: S_last to S_last +W_s -1 Window not allowed to slide beyond S_last +W_s -1 Need New Ack Frames received Rnext Receiver will only accept a frame that is error-free and that has sequence number Rnext When such a frame arrives, Rnext is incremented by one, and then the receive window slides forward by one Receiver sends an ACK with R_next; Tx assumes all prior frames received

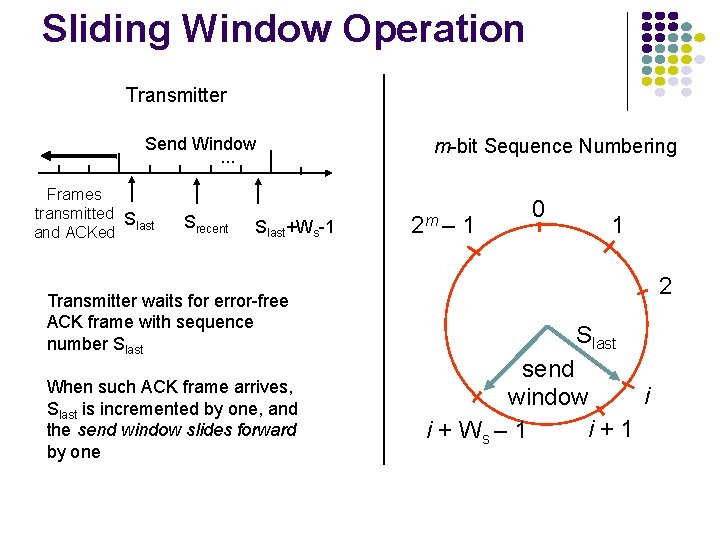
Sliding Window Operation Transmitter Send Window. . . Frames transmitted S last and ACKed Srecent Slast+Ws-1 Transmitter waits for error-free ACK frame with sequence number Slast When such ACK frame arrives, Slast is incremented by one, and the send window slides forward by one m-bit Sequence Numbering 2 m – 1 0 1 2 Slast send i window i+1 i + Ws – 1

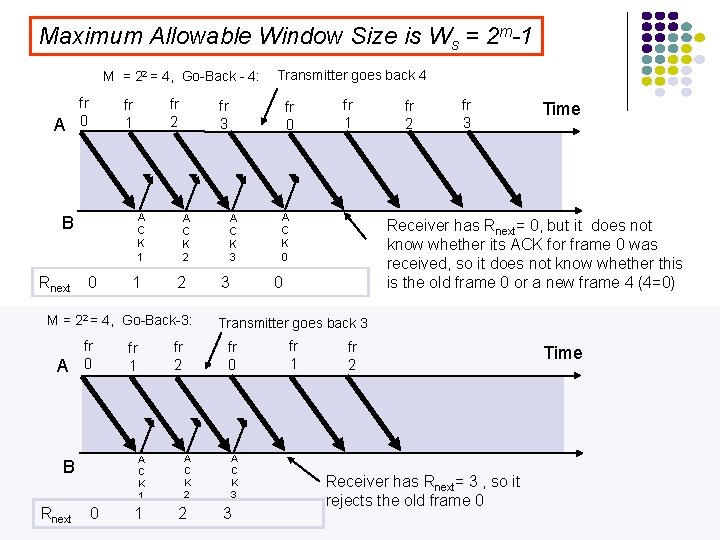
Maximum Allowable Window Size is Ws = 2 m-1 M = 22 = 4, Go-Back - 4: A fr 0 A C K 1 B Rnext fr 2 fr 1 0 1 fr 3 A C K 2 2 M = 22 = 4, Go-Back-3: A fr 0 A C K 1 B Rnext 0 1 fr 0 A C K 3 3 A C K 2 2 fr 1 A C K 0 fr 2 fr 3 Time Receiver has Rnext= 0, but it does not know whether its ACK for frame 0 was received, so it does not know whether this is the old frame 0 or a new frame 4 (4=0) 0 Transmitter goes back 3 fr 0 fr 2 fr 1 Transmitter goes back 4 A C K 3 3 fr 1 fr 2 Receiver has Rnext= 3 , so it rejects the old frame 0 Time

Bidirectional Links l l How can improve communication between A and B if information is flowing in both directions Both A and B are implementing the Go-Back. N ARQ So, both will have info to send + ACK (control frames) Can be piggyback (attach) the control frames on the info frames?

Bidirectional Links l l What is the adv. of this piggybacking? What if a frame arrives (carrying ACK) is in error? What if a frame arrives (carrying ACK) is out of sequence? What happens if the receiver has no info frames to send at this moment? How can be piggyback? Do we wait for info frame to come? Does a timer help here?

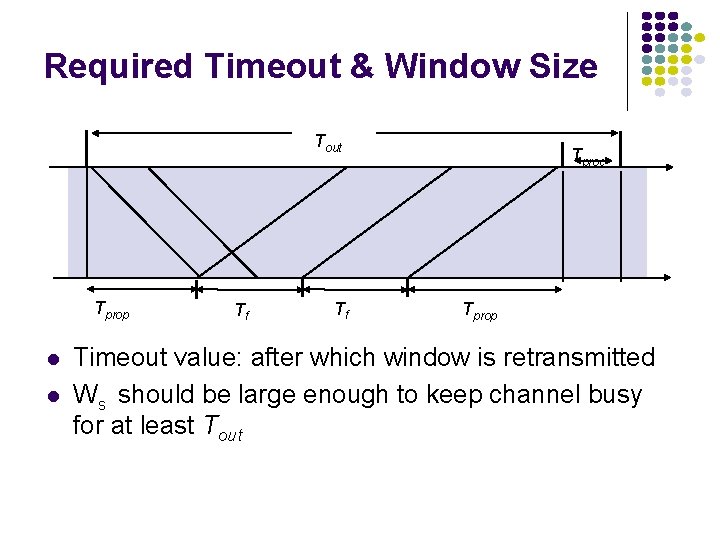
Required Timeout & Window Size Tout Tprop l l Tf Tf Tproc Tprop Timeout value: after which window is retransmitted Ws should be large enough to keep channel busy for at least Tout

Applications of Go-Back-N ARQ l l HDLC (High-Level Data Link Control): bitoriented data link control V. 42 modem: error control over telephone modem links

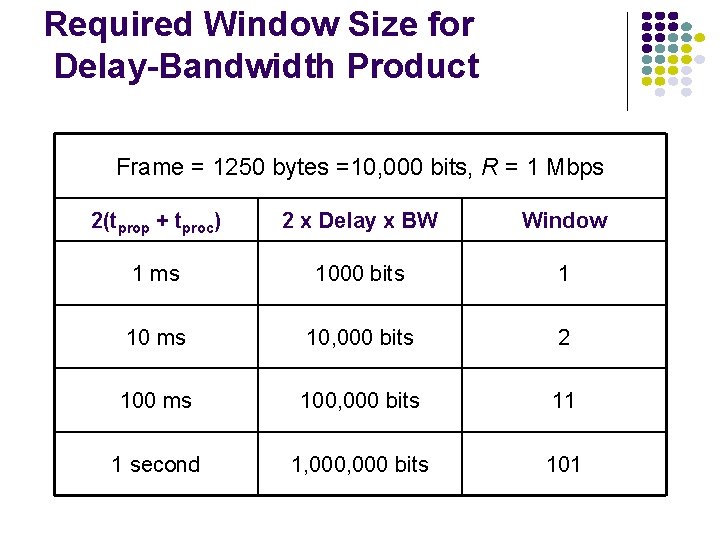
Required Window Size for Delay-Bandwidth Product Frame = 1250 bytes =10, 000 bits, R = 1 Mbps 2(tprop + tproc) 2 x Delay x BW Window 1 ms 1000 bits 1 10 ms 10, 000 bits 2 100 ms 100, 000 bits 11 1 second 1, 000 bits 101

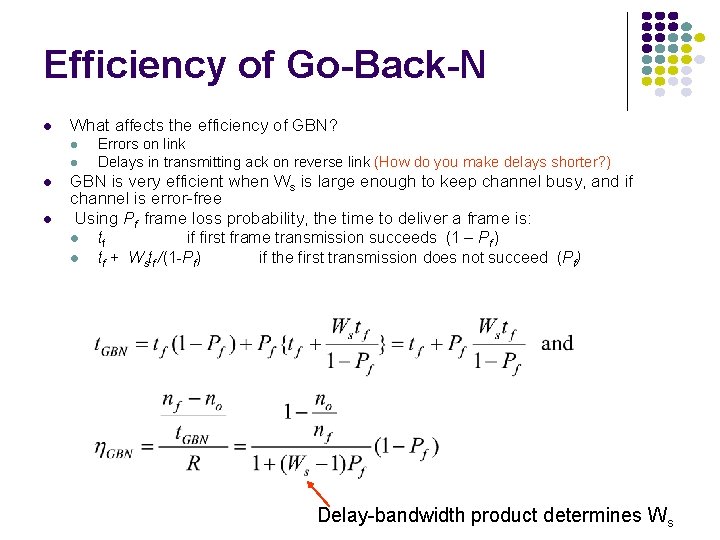
Efficiency of Go-Back-N l What affects the efficiency of GBN? l l Errors on link Delays in transmitting ack on reverse link (How do you make delays shorter? ) GBN is very efficient when Ws is large enough to keep channel busy, and if channel is error-free Using Pf frame loss probability, the time to deliver a frame is: l l tf if first frame transmission succeeds (1 – Pf ) tf + Wstf /(1 -Pf) if the first transmission does not succeed (Pf) Delay-bandwidth product determines Ws

Selective Repeat ARQ l l l Go-Back-N ARQ inefficient because multiple frames are resent when errors or losses occur Modify GBN in two ways l Make receiver window lager than 1 to allow for frames out of order l Modify retransmission so that only indiv. frames are retransmitted Selective Repeat retransmits only an individual frame l Timeout causes individual corresponding frame to be resent l NAK causes retransmission of oldest un-acked frame Transmit window remains same as in GBN Receiver maintains a receive window of sequence numbers that can be accepted (Rnext to Rnext + W_R -1), l Error-free, but out-of-sequence frames with sequence numbers within the receive window are buffered l Arrival of frame with Rnext causes window to slide forward by 1 or more

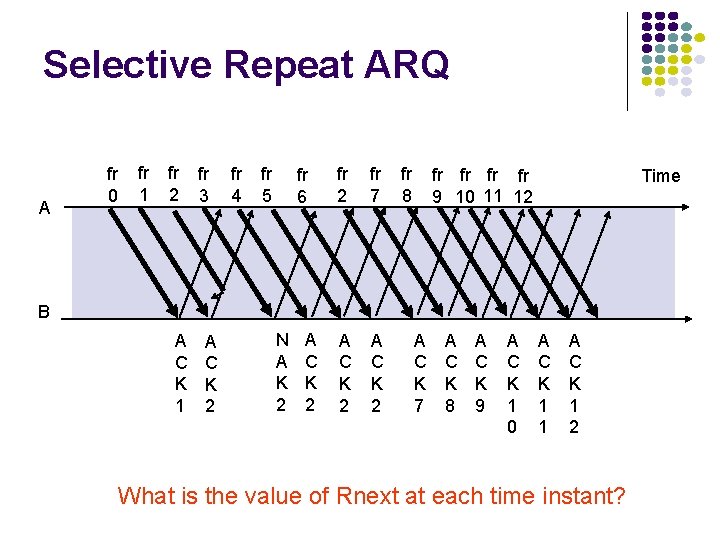
Selective Repeat ARQ A fr 0 fr 1 fr 2 fr 3 fr 4 fr 5 fr 6 fr 2 fr 7 A C K 2 fr 8 fr fr 9 10 11 12 Time B A C K 1 A C K 2 N A K 2 A C K 7 A C K 8 A C K 9 A C K 1 0 A C K 1 1 A C K 1 2 What is the value of Rnext at each time instant?

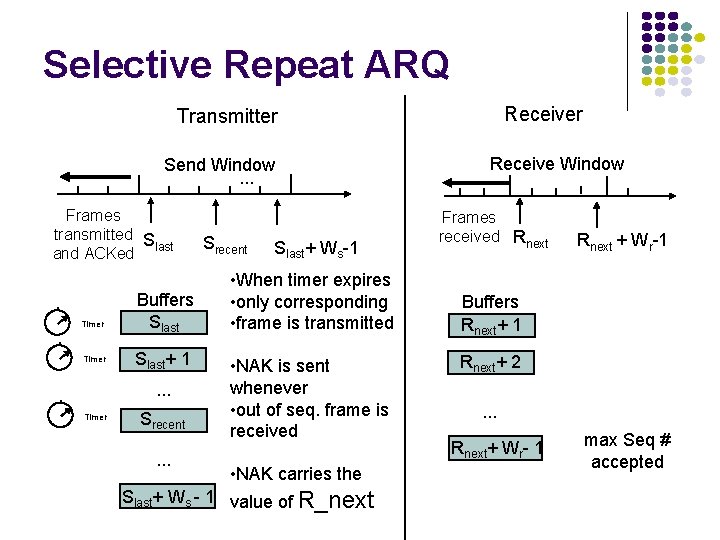
Selective Repeat ARQ Receiver Transmitter Send Window. . . Frames transmitted S last and ACKed Timer Buffers Slast+ 1. . . Timer Srecent. . . Srecent Slast+ Ws-1 • When timer expires • only corresponding • frame is transmitted • NAK is sent whenever • out of seq. frame is received • NAK carries the Slast+ Ws - 1 value of R_next Receive Window Frames received Rnext + Wr-1 Buffers Rnext+ 1 Rnext+ 2. . . Rnext+ Wr- 1 max Seq # accepted

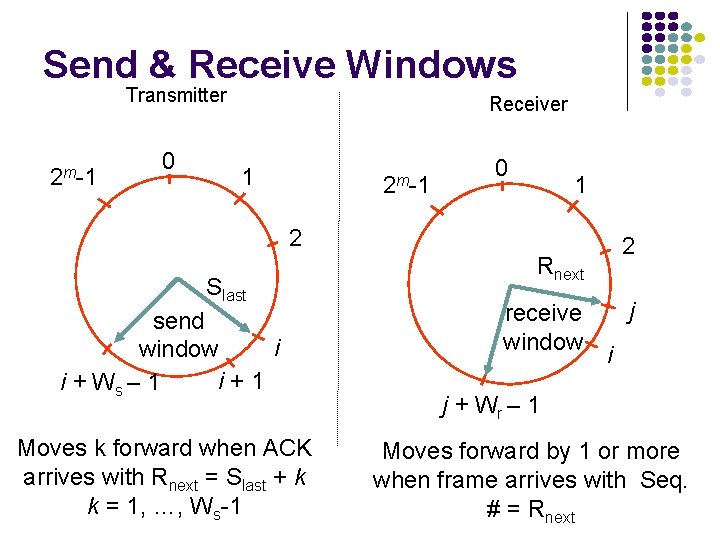
Send & Receive Windows Transmitter 2 m-1 0 Receiver 1 2 m-1 0 1 2 Slast send i window i+1 i + Ws – 1 Moves k forward when ACK arrives with Rnext = Slast + k k = 1, …, Ws-1 2 Rnext receive window j i j + Wr – 1 Moves forward by 1 or more when frame arrives with Seq. # = Rnext

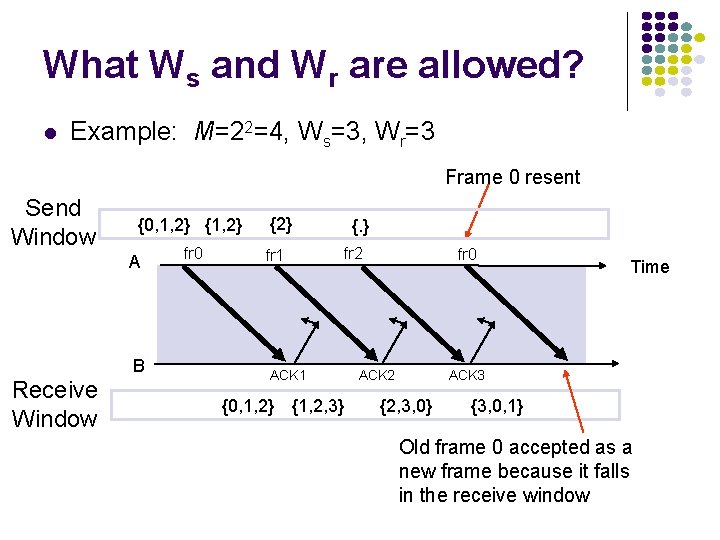
What Ws and Wr are allowed? l Example: M=22=4, Ws=3, Wr=3 Frame 0 resent Send Window {0, 1, 2} {1, 2} A B Receive Window fr 0 {2} fr 1 {. } fr 2 ACK 1 {0, 1, 2} {1, 2, 3} fr 0 ACK 2 Time ACK 3 {2, 3, 0} {3, 0, 1} Old frame 0 accepted as a new frame because it falls in the receive window

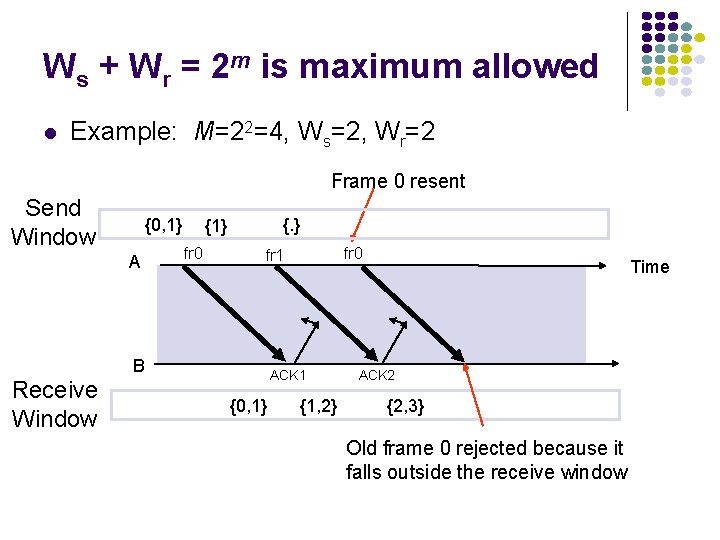
Ws + Wr = 2 m is maximum allowed l Example: M=22=4, Ws=2, Wr=2 Frame 0 resent Send Window {0, 1} A {. } {1} fr 0 B Receive Window fr 0 fr 1 ACK 1 {0, 1} {1, 2} Time ACK 2 {2, 3} Old frame 0 rejected because it falls outside the receive window

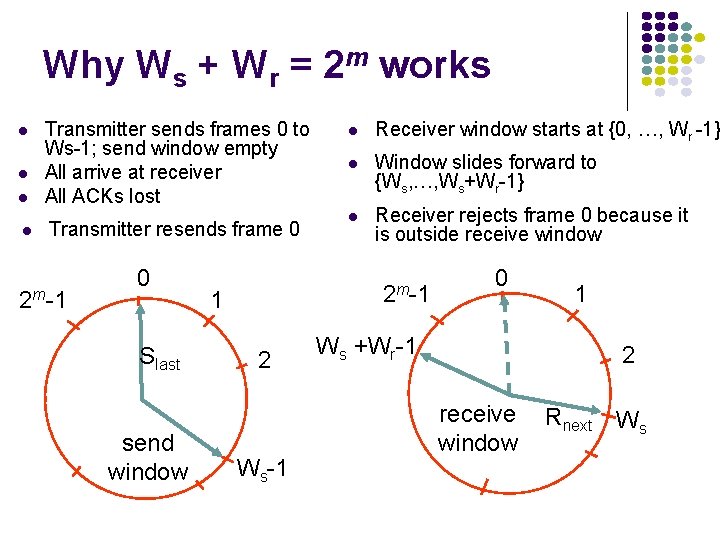
Why Ws + Wr = 2 m works l l Transmitter sends frames 0 to Ws-1; send window empty All arrive at receiver All ACKs lost Transmitter resends frame 0 2 m-1 0 Slast send window l Receiver window starts at {0, …, Wr -1} l Window slides forward to {Ws, …, Ws+Wr-1} l Receiver rejects frame 0 because it is outside receive window 2 m-1 1 2 Ws-1 0 Ws +Wr-1 1 2 receive window Rnext Ws

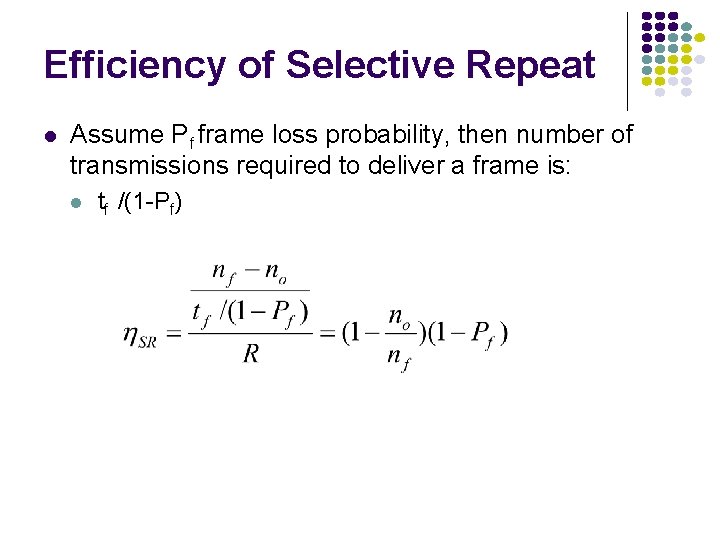
Efficiency of Selective Repeat l Assume Pf frame loss probability, then number of transmissions required to deliver a frame is: l tf /(1 -Pf)

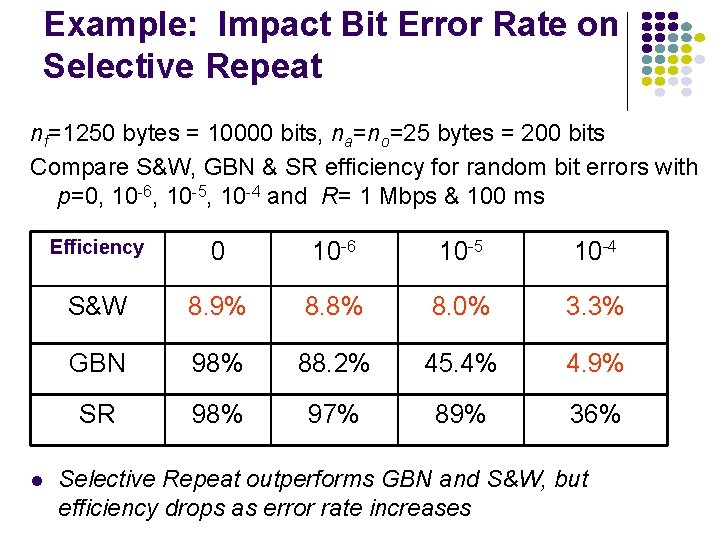
Example: Impact Bit Error Rate on Selective Repeat nf=1250 bytes = 10000 bits, na=no=25 bytes = 200 bits Compare S&W, GBN & SR efficiency for random bit errors with p=0, 10 -6, 10 -5, 10 -4 and R= 1 Mbps & 100 ms l Efficiency 0 10 -6 10 -5 10 -4 S&W 8. 9% 8. 8% 8. 0% 3. 3% GBN 98% 88. 2% 45. 4% 4. 9% SR 98% 97% 89% 36% Selective Repeat outperforms GBN and S&W, but efficiency drops as error rate increases

Summary of ARQ Efficiencies Assume na and no are negligible relative to nf, and L = 2(tprop+tproc)R/nf =(Ws-1), then Selective-Repeat: Go-Back-N: Stop-and-Wait:

Chapter 5 Peer-to-Peer Protocols and Data Link Layer Framing

Framing l l l Identify beginning an end of a block Presupposes presence of enough synch. At physical layer to identify bit or byte Two levels of synch. Accuracy: l l Asynch data tx l Example: RS-232 for serial line interface l Tx does not occur at regular intervals l Rx resynch’s at start and end of each 8 -bit charcter l Uses start and stop bits Synch data transmission l Bits tx at regular interval l Phase locked loop to track bits l Synch facilitated by having enough transitions in bit stream

Types of Frames l l Framing means Delineating (outlining) boundaries between frames Frames could l l Have fixed length Have variable length Contain any number of bits Integer number of characters of certain length (e. g. , octets or 32 -bit words)

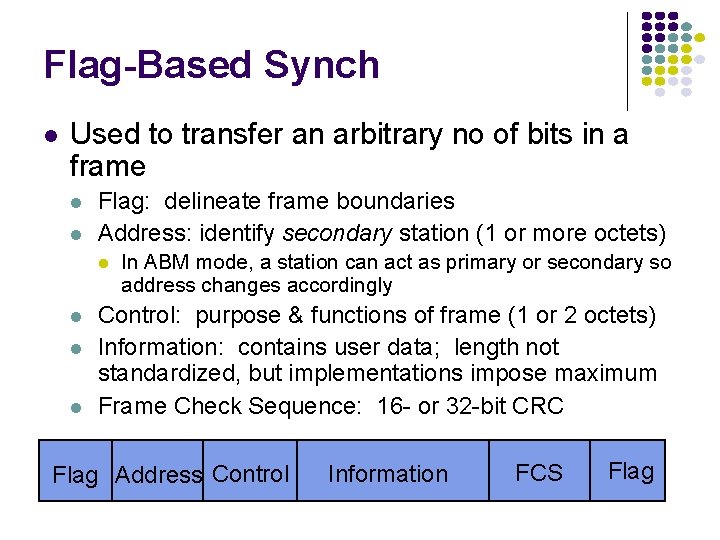
Character-based synch l Used when info in frame consists of integer no. of characters l l l E. g. tx a sequence of printable characters using 8 bit ASCII code Use special 8 bit characters that don’t correspond to printable characters All HEX values that are less than 20 correspond to non-printable characters l l l STX (start of text) has HEX value 02, to begin frame ETX (end of text) has HEX value 03, to end frame When would this method fail?

l l l Method works if frame contains printable characters only It fails if frame contains computer data l Frame might contain ETX causing frame to be truncated To solve this, use byte stuffing l Introduce a new character DLE (data link escapae) with HEX value 10 l Use DLE STX for beginning l Use DLE ETX for end l To deal with possible occurrence of DLE STX or DEL ETX inside frame, an extra DLE is stuffed before occurrence of DLE l So DLE’s inside the data will actually have 2 DLE’s l Only case when there is only one DLE is at beginning or end of frame

l l l What are the problems with this Characterbased sync. ? Variable no. of characters Possibility for user to inflate BW he is using

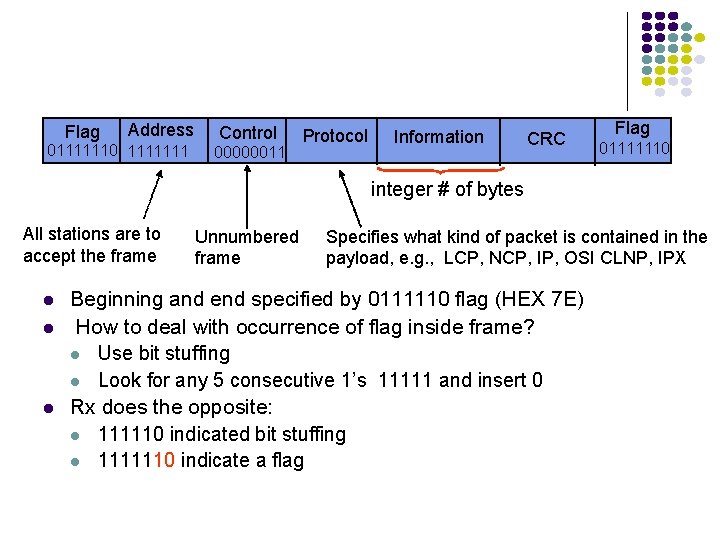
Flag-Based Synch l Used to transfer an arbitrary no of bits in a frame l l Flag: delineate frame boundaries Address: identify secondary station (1 or more octets) l l In ABM mode, a station can act as primary or secondary so address changes accordingly Control: purpose & functions of frame (1 or 2 octets) Information: contains user data; length not standardized, but implementations impose maximum Frame Check Sequence: 16 - or 32 -bit CRC Flag Address Control Information FCS Flag

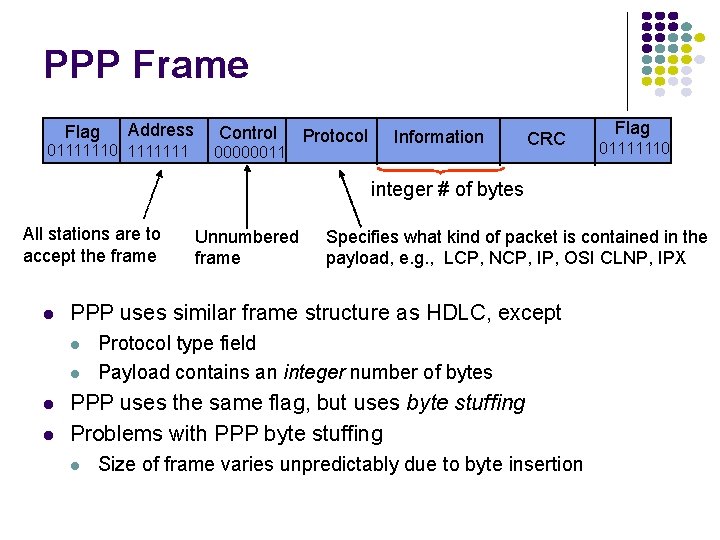
Flag Address 01111110 1111111 Control 00000011 Protocol Information CRC Flag 01111110 integer # of bytes All stations are to accept the frame l l l Unnumbered frame Specifies what kind of packet is contained in the payload, e. g. , LCP, NCP, IP, OSI CLNP, IPX Beginning and end specified by 0111110 flag (HEX 7 E) How to deal with occurrence of flag inside frame? l Use bit stuffing l Look for any 5 consecutive 1’s 11111 and insert 0 Rx does the opposite: l 111110 indicated bit stuffing l 1111110 indicate a flag

PPP Frame Flag Address 01111110 1111111 Control 00000011 Protocol Information CRC Flag 01111110 integer # of bytes All stations are to accept the frame l l l Specifies what kind of packet is contained in the payload, e. g. , LCP, NCP, IP, OSI CLNP, IPX PPP uses similar frame structure as HDLC, except l l Unnumbered frame Protocol type field Payload contains an integer number of bytes PPP uses the same flag, but uses byte stuffing Problems with PPP byte stuffing l Size of frame varies unpredictably due to byte insertion

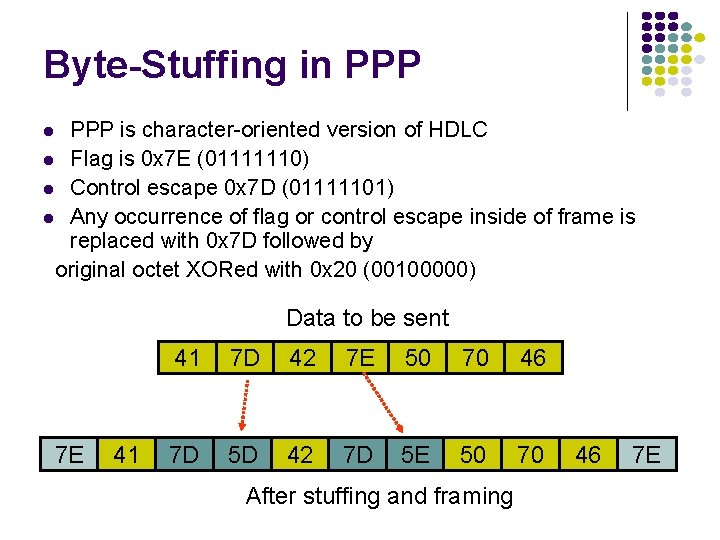
Byte-Stuffing in PPP is character-oriented version of HDLC l Flag is 0 x 7 E (01111110) l Control escape 0 x 7 D (01111101) l Any occurrence of flag or control escape inside of frame is replaced with 0 x 7 D followed by original octet XORed with 0 x 20 (00100000) l Data to be sent 7 E 41 41 7 D 42 7 E 50 70 46 7 D 5 D 42 7 D 5 E 50 70 After stuffing and framing 46 7 E

CRC-Based Framing l l l l Generic Framing Procedure (GFP) l Problem with byte an bit stuffing is that you can not know length of frame ahead of time l Opportunity for malicious users to inflate BW by inserting patterns in a frame GFP combines frame length with Header Error Control Idea: We need just to know the beginning of a frame and its length To know length, look at length indication field Count number of bytes to know beginning of new frame Works if there are no errors To deal with errors, use HEC for error control

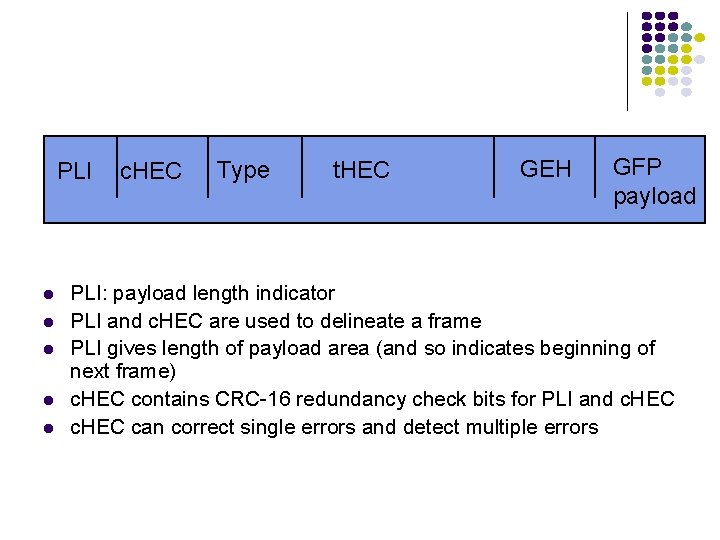
PLI l l l c. HEC Type t. HEC GEH GFP payload PLI: payload length indicator PLI and c. HEC are used to delineate a frame PLI gives length of payload area (and so indicates beginning of next frame) c. HEC contains CRC-16 redundancy check bits for PLI and c. HEC can correct single errors and detect multiple errors

l GFP receiver synchronizes to boundary through a 3 -state process l Hunt state: l l Pre-sync state: l l l examines 4 bytes at a time to see if they constitute a valid code-word (how to do that? ) If no match, receiver moves by one octet If it finds a match, it moves to next state Use the PLI info to determine location of next frame boundary If target number N of successful frame detections is achieved, receiver moves to sync state Sync. State: Normal state where l l receiver examines PLI validates using c. HEC Extracts payload and moves to next frame Single error correcting capability of CRC-16 is activated (can we activate it before? )