Chapter 5 outline r 5 1 Introduction and




![PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram](https://slidetodoc.com/presentation_image_h2/84f6499ccaf7d7a847e53624a21170d5/image-12.jpg)





- Slides: 48

Chapter 5 outline r 5. 1 Introduction and r 5. 6 Hubs, bridges, and r r r services 5. 2 Error detection and correction 5. 3 Multiple access protocols 5. 4 LAN addresses and ARP 5. 5 Ethernet r r r switches 5. 7 Wireless links and LANs 5. 8 PPP 5. 9 ATM 5. 10 Frame Relay 5: Data. Link Layer 1

IEEE 802. 11 Wireless LAN r 802. 11 b m 2. 4 -5 GHz unlicensed radio spectrum m up to 11 Mbps m direct sequence spread spectrum (DSSS) in physical layer • all hosts use same chipping code m widely deployed, using base stations r 802. 11 a m 5 -6 GHz range m up to 54 Mbps r 802. 11 g m 2. 4 -5 GHz range m up to 54 Mbps r All use CSMA/CA for multiple access r All have base-station and ad-hoc network versions 5: Data. Link Layer 2

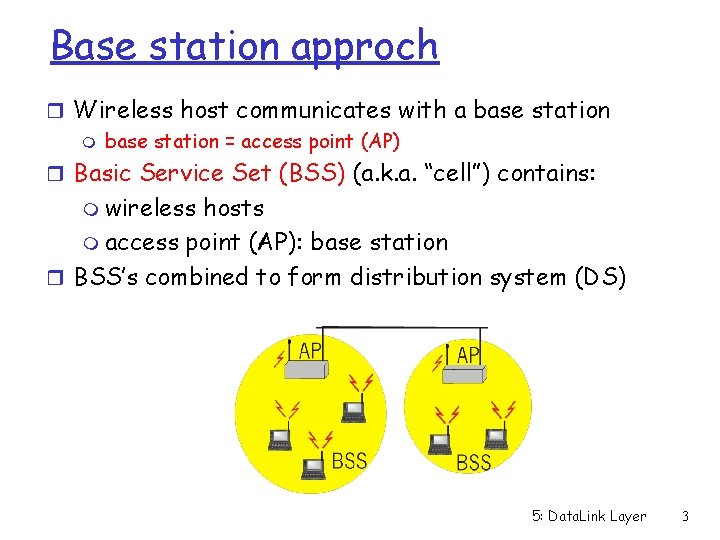
Base station approch r Wireless host communicates with a base station m base station = access point (AP) r Basic Service Set (BSS) (a. k. a. “cell”) contains: m wireless hosts m access point (AP): base station r BSS’s combined to form distribution system (DS) 5: Data. Link Layer 3

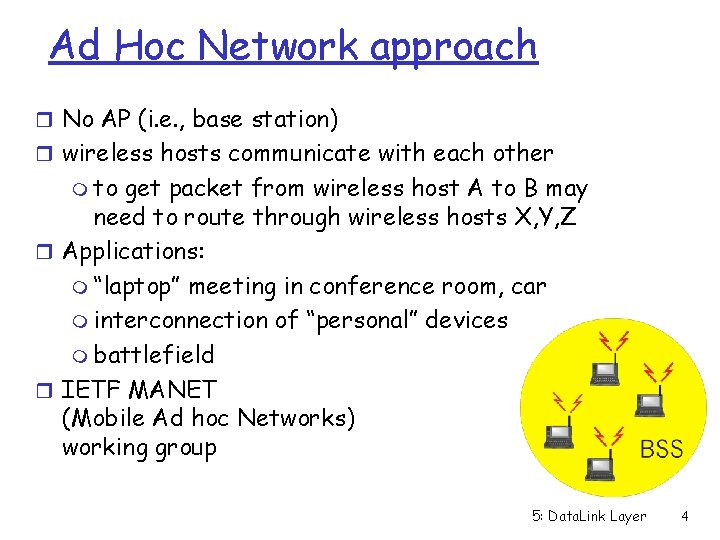
Ad Hoc Network approach r No AP (i. e. , base station) r wireless hosts communicate with each other m to get packet from wireless host A to B may need to route through wireless hosts X, Y, Z r Applications: m “laptop” meeting in conference room, car m interconnection of “personal” devices m battlefield r IETF MANET (Mobile Ad hoc Networks) working group 5: Data. Link Layer 4

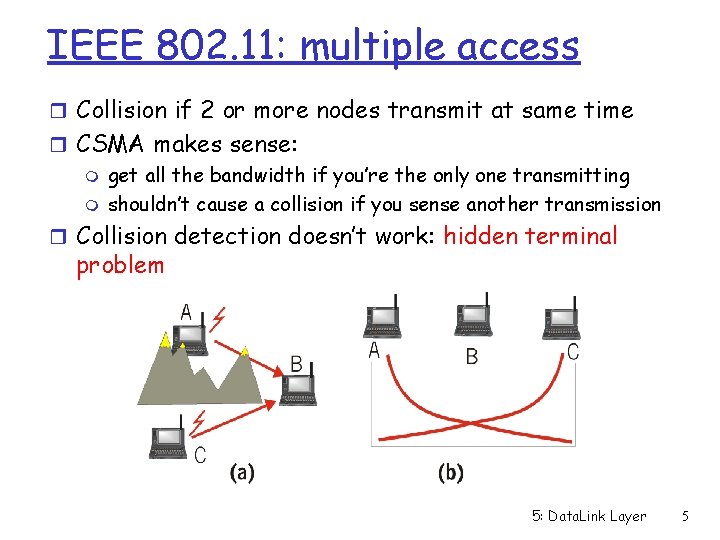
IEEE 802. 11: multiple access r Collision if 2 or more nodes transmit at same time r CSMA makes sense: m get all the bandwidth if you’re the only one transmitting m shouldn’t cause a collision if you sense another transmission r Collision detection doesn’t work: hidden terminal problem 5: Data. Link Layer 5

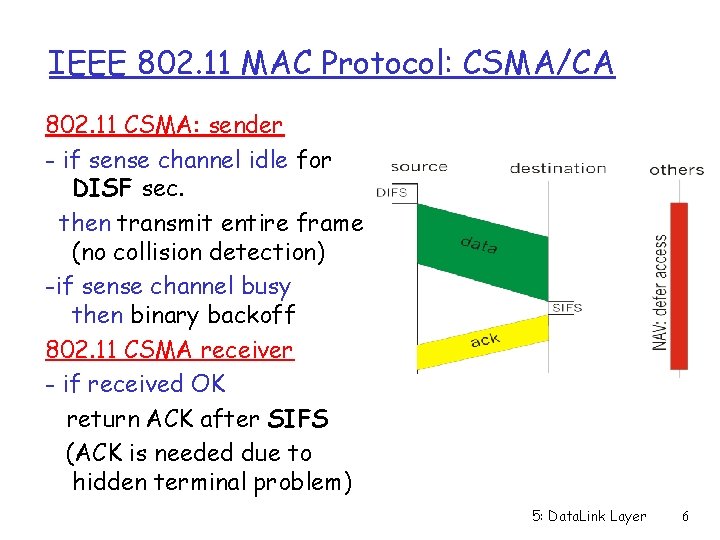
IEEE 802. 11 MAC Protocol: CSMA/CA 802. 11 CSMA: sender - if sense channel idle for DISF sec. then transmit entire frame (no collision detection) -if sense channel busy then binary backoff 802. 11 CSMA receiver - if received OK return ACK after SIFS (ACK is needed due to hidden terminal problem) 5: Data. Link Layer 6

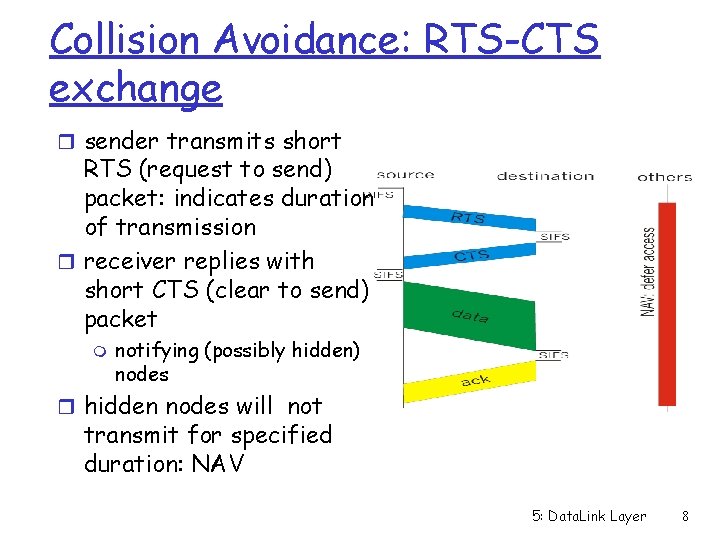
Collision avoidance mechanisms r Problem: m two nodes, hidden from each other, transmit complete frames to base station m wasted bandwidth for long duration ! r Solution: m small reservation packets m nodes track reservation interval with internal “network allocation vector” (NAV) 5: Data. Link Layer 7

Collision Avoidance: RTS-CTS exchange r sender transmits short RTS (request to send) packet: indicates duration of transmission r receiver replies with short CTS (clear to send) packet m notifying (possibly hidden) nodes r hidden nodes will not transmit for specified duration: NAV 5: Data. Link Layer 8

Collision Avoidance: RTS-CTS exchange r RTS and CTS short: m collisions less likely, of shorter duration m end result similar to collision detection r IEEE 802. 11 allows: m CSMA/CA: reservations m polling from AP 5: Data. Link Layer 9

Chapter 5 outline r 5. 1 Introduction and r 5. 6 Hubs, bridges, and r r r services 5. 2 Error detection and correction 5. 3 Multiple access protocols 5. 4 LAN addresses and ARP 5. 5 Ethernet r r r switches 5. 7 Wireless links and LANs 5. 8 PPP 5. 9 ATM 5. 10 Frame Relay 5: Data. Link Layer 10

Point to Point Data Link Control r one sender, one receiver, one link: easier than broadcast link: m no Media Access Control m no need for explicit MAC addressing m e. g. , dialup link, ISDN line r popular point-to-point DLC protocols: m PPP (point-to-point protocol) m HDLC: High level data link control (Data link used to be considered “high layer” in protocol stack! 5: Data. Link Layer 11
![PPP Design Requirements RFC 1557 r packet framing encapsulation of networklayer r r datagram PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram](https://slidetodoc.com/presentation_image_h2/84f6499ccaf7d7a847e53624a21170d5/image-12.jpg)
PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram in data link frame m carry network layer data of any network layer protocol (not just IP) at same time m ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer address negotiation: endpoint can learn/configure each other’s network address 5: Data. Link Layer 12

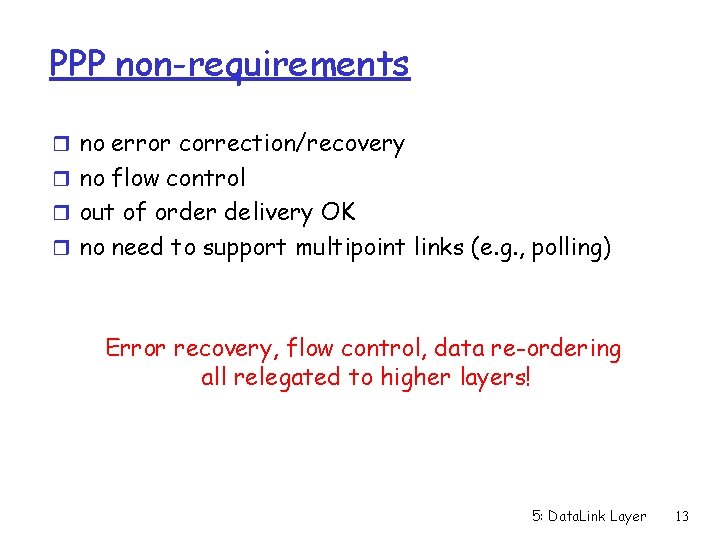
PPP non-requirements r no error correction/recovery r no flow control r out of order delivery OK r no need to support multipoint links (e. g. , polling) Error recovery, flow control, data re-ordering all relegated to higher layers! 5: Data. Link Layer 13

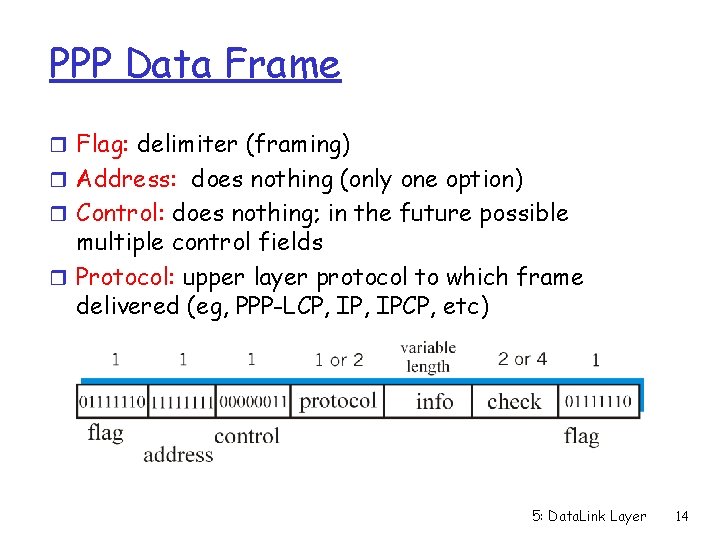
PPP Data Frame r Flag: delimiter (framing) r Address: does nothing (only one option) r Control: does nothing; in the future possible multiple control fields r Protocol: upper layer protocol to which frame delivered (eg, PPP-LCP, IPCP, etc) 5: Data. Link Layer 14

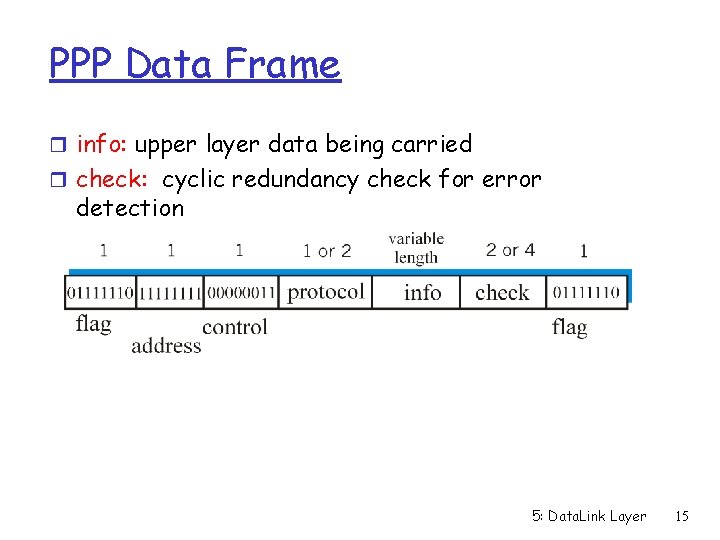
PPP Data Frame r info: upper layer data being carried r check: cyclic redundancy check for error detection 5: Data. Link Layer 15

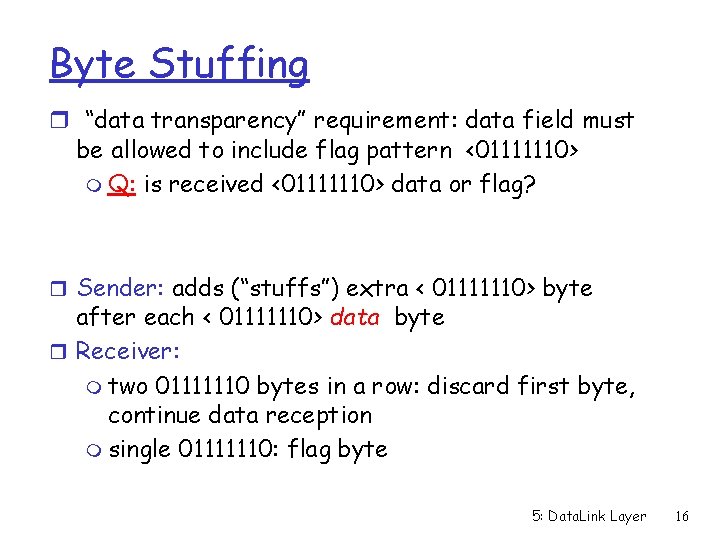
Byte Stuffing r “data transparency” requirement: data field must be allowed to include flag pattern <01111110> m Q: is received <01111110> data or flag? r Sender: adds (“stuffs”) extra < 01111110> byte after each < 01111110> data byte r Receiver: m two 01111110 bytes in a row: discard first byte, continue data reception m single 01111110: flag byte 5: Data. Link Layer 16

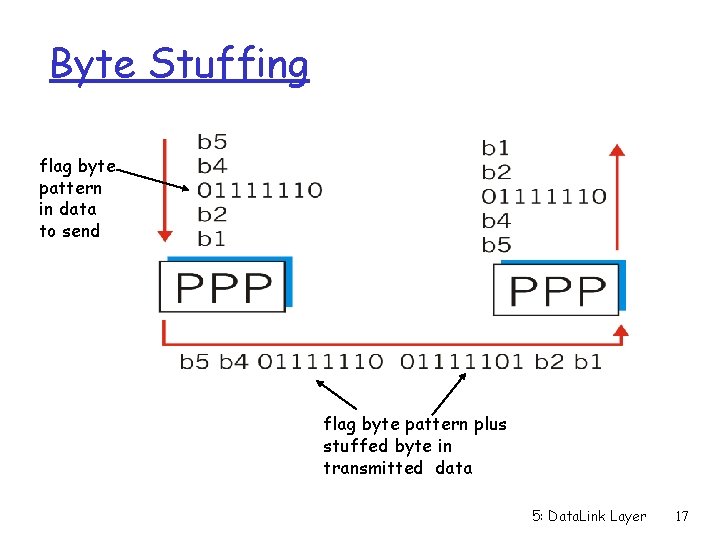
Byte Stuffing flag byte pattern in data to send flag byte pattern plus stuffed byte in transmitted data 5: Data. Link Layer 17

PPP Data Control Protocol Before exchanging networklayer data, data link peers must r configure PPP link (max. frame length, authentication) r learn/configure network layer information m for IP: carry IP Control Protocol (IPCP) msgs (protocol field: 8021) to configure/learn IP address 5: Data. Link Layer 18

Final Exam Review Topics r Chapters 4 and 5 (plus some global knowledge of Chapter 3) 5: Data. Link Layer 19

Chapter 4 roadmap 4. 1 Introduction and Network Service Models 4. 2 Routing Principles 4. 3 Hierarchical Routing 4. 4 The Internet (IP) Protocol 4. 5 Routing in the Internet 4. 6 What’s Inside a Router 5: Data. Link Layer 20

Chapter 4 roadmap 4. 1 Introduction and Network Service Models 4. 2 Routing Principles m m Link state routing Distance vector routing 4. 3 Hierarchical Routing 4. 4 The Internet (IP) Protocol 4. 5 Routing in the Internet 4. 6 What’s Inside a Router 5: Data. Link Layer 21

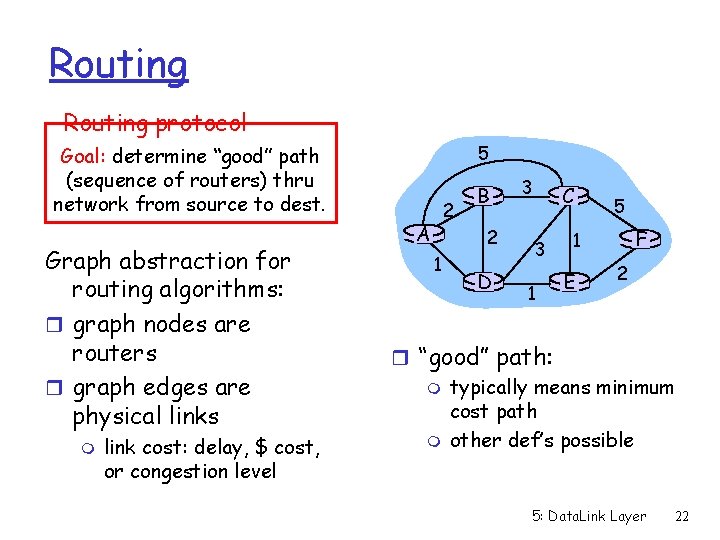
Routing protocol 5 Goal: determine “good” path (sequence of routers) thru network from source to dest. Graph abstraction for routing algorithms: r graph nodes are routers r graph edges are physical links m link cost: delay, $ cost, or congestion level 2 A B 2 1 D 3 C 3 1 5 F 1 E 2 r “good” path: m typically means minimum cost path m other def’s possible 5: Data. Link Layer 22

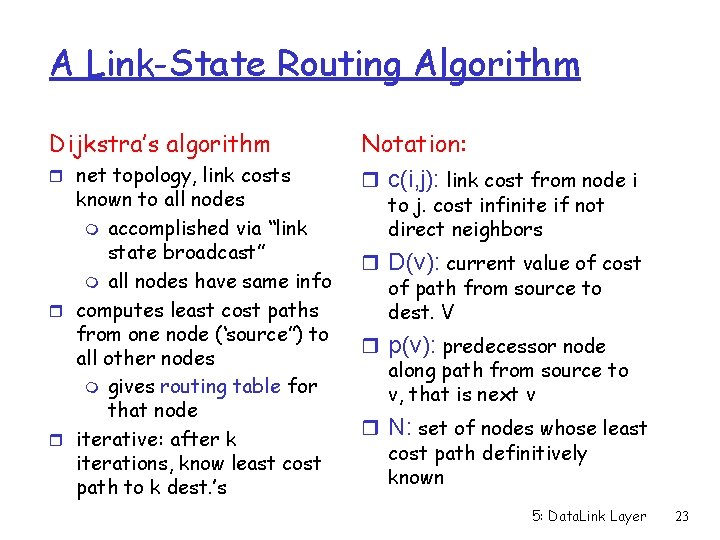
A Link-State Routing Algorithm Dijkstra’s algorithm r net topology, link costs known to all nodes m accomplished via “link state broadcast” m all nodes have same info r computes least cost paths from one node (‘source”) to all other nodes m gives routing table for that node r iterative: after k iterations, know least cost path to k dest. ’s Notation: r c(i, j): link cost from node i to j. cost infinite if not direct neighbors r D(v): current value of cost of path from source to dest. V r p(v): predecessor node along path from source to v, that is next v r N: set of nodes whose least cost path definitively known 5: Data. Link Layer 23

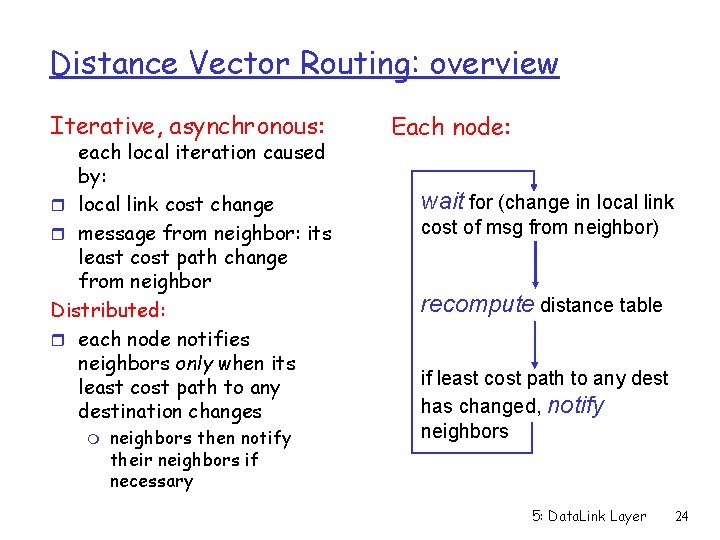
Distance Vector Routing: overview Iterative, asynchronous: each local iteration caused by: r local link cost change r message from neighbor: its least cost path change from neighbor Distributed: r each node notifies neighbors only when its least cost path to any destination changes m neighbors then notify their neighbors if necessary Each node: wait for (change in local link cost of msg from neighbor) recompute distance table if least cost path to any dest has changed, notify neighbors 5: Data. Link Layer 24

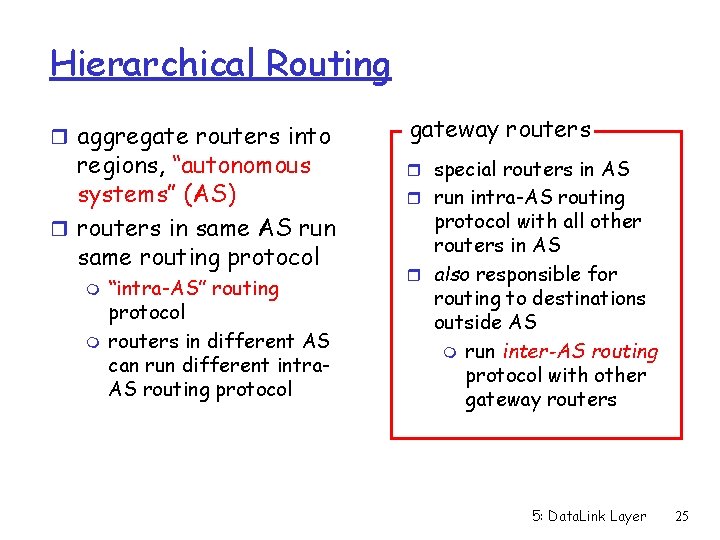
Hierarchical Routing r aggregate routers into regions, “autonomous systems” (AS) r routers in same AS run same routing protocol m m “intra-AS” routing protocol routers in different AS can run different intra. AS routing protocol gateway routers r special routers in AS r run intra-AS routing protocol with all other routers in AS r also responsible for routing to destinations outside AS m run inter-AS routing protocol with other gateway routers 5: Data. Link Layer 25

Chapter 4 roadmap 4. 1 Introduction and Network Service Models 4. 2 Routing Principles 4. 3 Hierarchical Routing 4. 4 The Internet (IP) Protocol m 4. 4. 1 IPv 4 addressing m 4. 4. 2 Moving a datagram from source to destination m 4. 4. 3 Datagram format m 4. 4. 4 IP fragmentation m 4. 4. 5 ICMP: Internet Control Message Protocol m 4. 4. 6 DHCP: Dynamic Host Configuration Protocol m 4. 4. 7 NAT: Network Address Translation 4. 5 Routing in the Internet 4. 6 What’s Inside a Router 4. 7 IPv 6 4. 8 Multicast Routing 4. 9 Mobility 5: Data. Link Layer 26

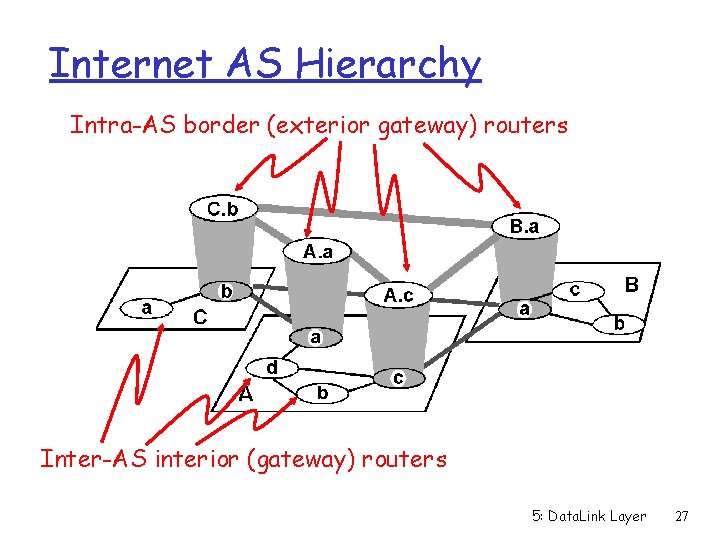
Internet AS Hierarchy Intra-AS border (exterior gateway) routers Inter-AS interior (gateway) routers 5: Data. Link Layer 27

Intra-AS Routing r Also known as Interior Gateway Protocols (IGP) r Most common Intra-AS routing protocols: m RIP: Routing Information Protocol m OSPF: Open Shortest Path First m IGRP: Interior Gateway Routing Protocol (Cisco proprietary) 5: Data. Link Layer 28

Internet inter-AS routing: BGP r BGP (Border Gateway Protocol): the de facto standard r Path Vector protocol: m similar to Distance Vector protocol m each Border Gateway broadcast to neighbors (peers) entire path (i. e. , sequence of AS’s) to destination m BGP routes to networks (ASs), not individual hosts m E. g. , Gateway X may send its path to dest. Z: Path (X, Z) = X, Y 1, Y 2, Y 3, …, Z 5: Data. Link Layer 29

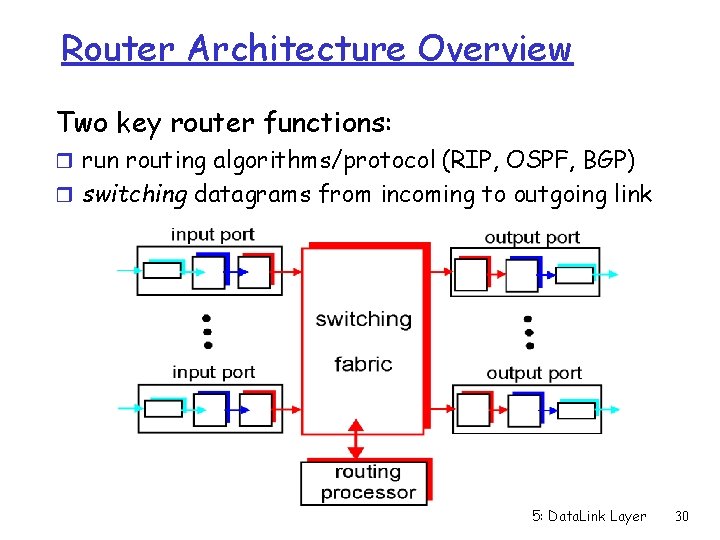
Router Architecture Overview Two key router functions: r run routing algorithms/protocol (RIP, OSPF, BGP) r switching datagrams from incoming to outgoing link 5: Data. Link Layer 30

Chapter 5 outline r 5. 1 Introduction and r r services 5. 2 Error detection and correction 5. 3 Multiple access protocols 5. 4 LAN addresses and ARP 5. 5 Ethernet r 5. 6 Hubs, bridges, and switches r 5. 7 Wireless links and LANs r 5. 8 PPP 5: Data. Link Layer 31

Link Layer Services r Framing, link access: m encapsulate datagram into frame, adding header, trailer m channel access if shared medium m ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! r Reliable delivery between adjacent nodes m we learned how to do this already (chapter 3)! m seldom used on low bit error link (fiber, some twisted pair) m wireless links: high error rates • Q: why both link-level and end-end reliability? 5: Data. Link Layer 32

Link Layer Services (more) r Flow Control: m pacing between adjacent sending and receiving nodes r Error Detection: m errors caused by signal attenuation, noise. m receiver detects presence of errors: • signals sender for retransmission or drops frame r Error Correction: m receiver identifies and corrects bit error(s) without resorting to retransmission r Half-duplex and full-duplex m with half duplex, nodes at both ends of link can transmit, but not at same time 5: Data. Link Layer 33

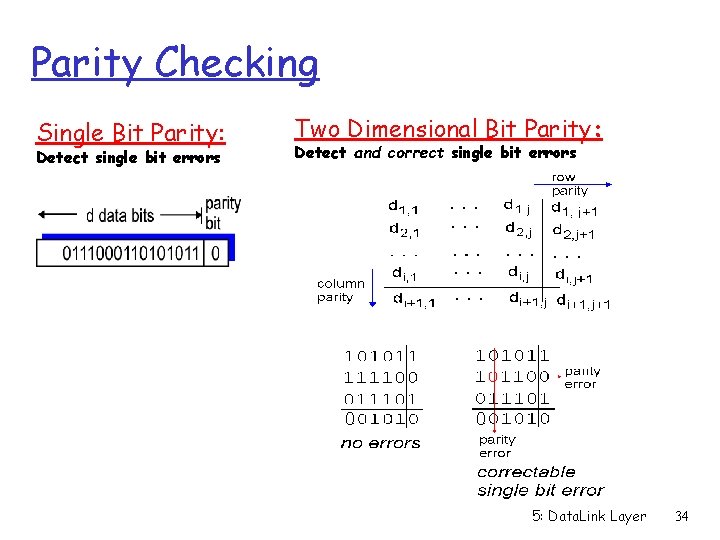
Parity Checking Single Bit Parity: Detect single bit errors Two Dimensional Bit Parity: Detect and correct single bit errors 0 0 5: Data. Link Layer 34

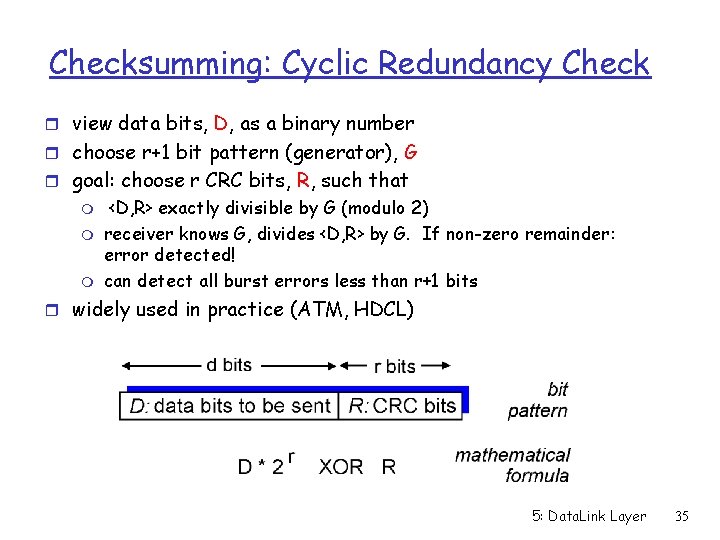
Checksumming: Cyclic Redundancy Check r view data bits, D, as a binary number r choose r+1 bit pattern (generator), G r goal: choose r CRC bits, R, such that m m m <D, R> exactly divisible by G (modulo 2) receiver knows G, divides <D, R> by G. If non-zero remainder: error detected! can detect all burst errors less than r+1 bits r widely used in practice (ATM, HDCL) 5: Data. Link Layer 35

Multiple Access Links and Protocols Two types of “links”: r point-to-point m PPP for dial-up access m point-to-point link between Ethernet switch and host r broadcast (shared wire or medium) m traditional Ethernet m upstream HFC m 802. 11 wireless LAN 5: Data. Link Layer 36

MAC Protocols: a taxonomy Three broad classes: r Channel Partitioning m m divide channel into smaller “pieces” (time slots, frequency, code) allocate piece to node for exclusive use r Random Access m channel not divided, allow collisions m “recover” from collisions r “Taking turns” m tightly coordinate shared access to avoid collisions 5: Data. Link Layer 37

Summary of MAC protocols r What do you do with a shared media? m Channel Partitioning, by time, frequency or code • Time Division, Code Division, Frequency Division m Random partitioning (dynamic), • ALOHA, S-ALOHA, CSMA/CD • carrier sensing: easy in some technologies (wire), hard in others (wireless) • CSMA/CD used in Ethernet m Taking Turns • polling from a central site, token passing 5: Data. Link Layer 38

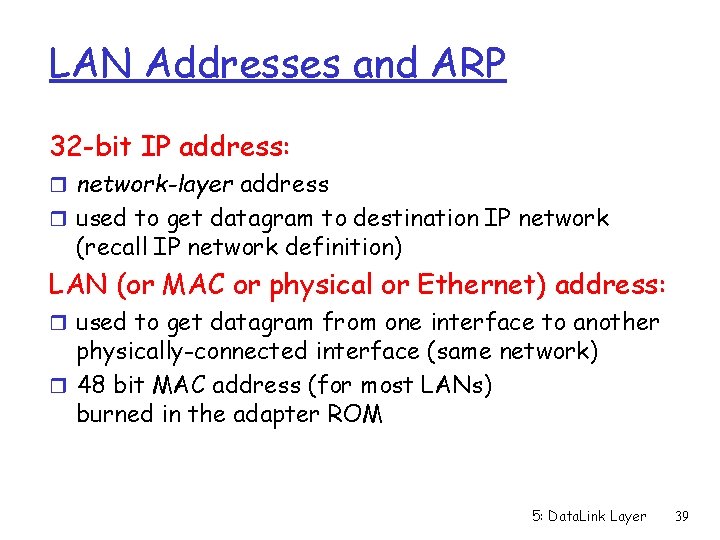
LAN Addresses and ARP 32 -bit IP address: r network-layer address r used to get datagram to destination IP network (recall IP network definition) LAN (or MAC or physical or Ethernet) address: r used to get datagram from one interface to another physically-connected interface (same network) r 48 bit MAC address (for most LANs) burned in the adapter ROM 5: Data. Link Layer 39

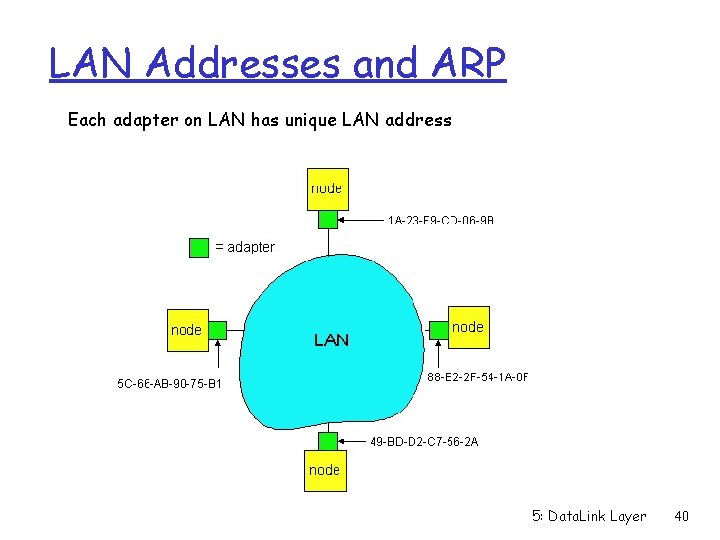
LAN Addresses and ARP Each adapter on LAN has unique LAN address 5: Data. Link Layer 40

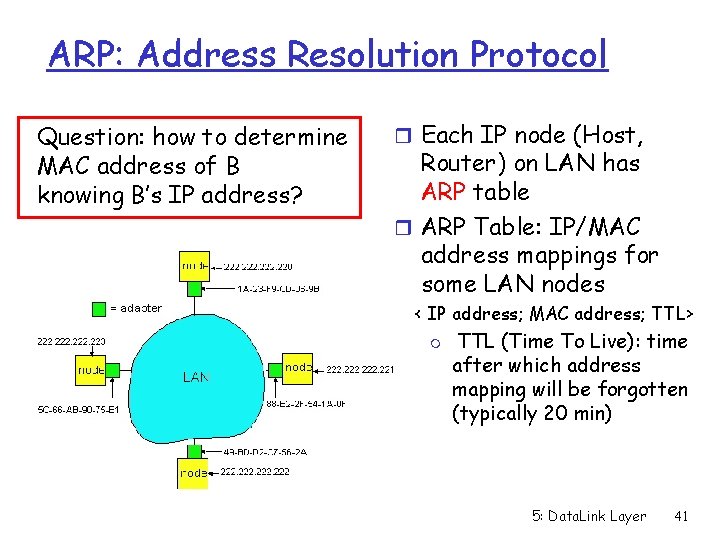
ARP: Address Resolution Protocol Question: how to determine MAC address of B knowing B’s IP address? r Each IP node (Host, Router) on LAN has ARP table r ARP Table: IP/MAC address mappings for some LAN nodes < IP address; MAC address; TTL> m TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) 5: Data. Link Layer 41

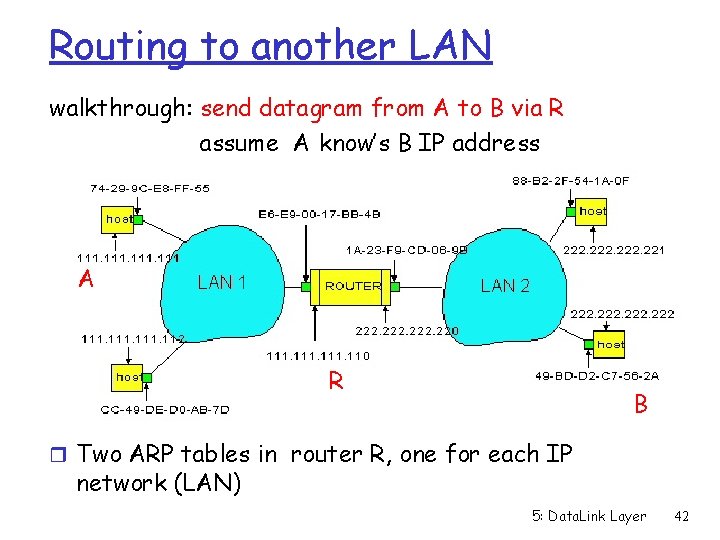
Routing to another LAN walkthrough: send datagram from A to B via R assume A know’s B IP address A R B r Two ARP tables in router R, one for each IP network (LAN) 5: Data. Link Layer 42

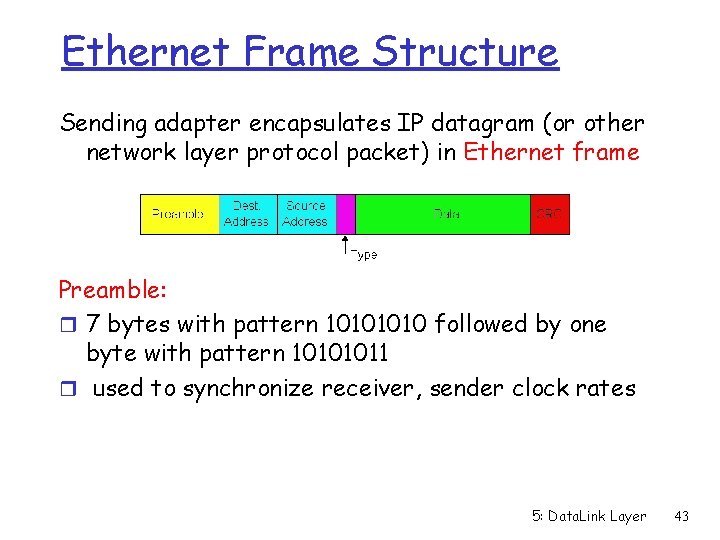
Ethernet Frame Structure Sending adapter encapsulates IP datagram (or other network layer protocol packet) in Ethernet frame Preamble: r 7 bytes with pattern 1010 followed by one byte with pattern 10101011 r used to synchronize receiver, sender clock rates 5: Data. Link Layer 43

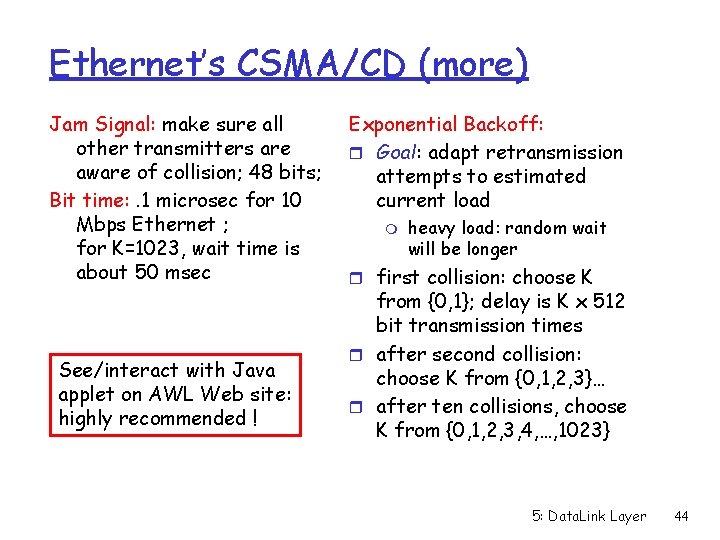
Ethernet’s CSMA/CD (more) Jam Signal: make sure all other transmitters are aware of collision; 48 bits; Bit time: . 1 microsec for 10 Mbps Ethernet ; for K=1023, wait time is about 50 msec See/interact with Java applet on AWL Web site: highly recommended ! Exponential Backoff: r Goal: adapt retransmission attempts to estimated current load m heavy load: random wait will be longer r first collision: choose K from {0, 1}; delay is K x 512 bit transmission times r after second collision: choose K from {0, 1, 2, 3}… r after ten collisions, choose K from {0, 1, 2, 3, 4, …, 1023} 5: Data. Link Layer 44

Interconnecting LAN segments r Hubs r Bridges r Switches m Remark: switches are essentially multi-port bridges. m What we say about bridges also holds for switches! 5: Data. Link Layer 45

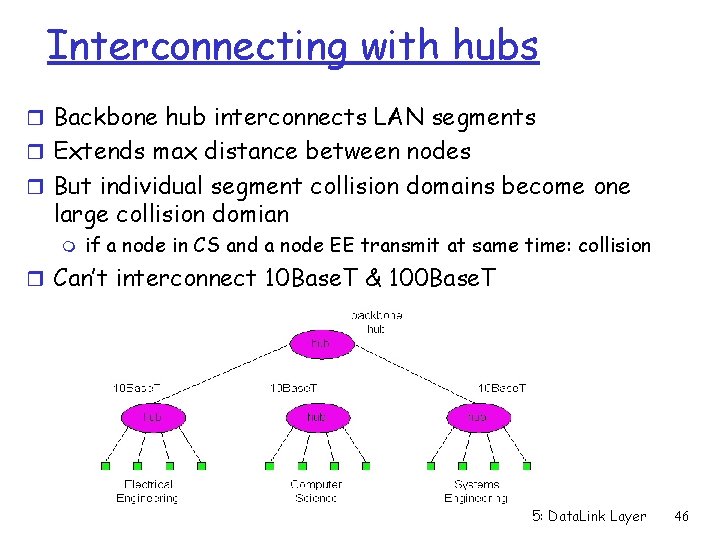
Interconnecting with hubs r Backbone hub interconnects LAN segments r Extends max distance between nodes r But individual segment collision domains become one large collision domian m if a node in CS and a node EE transmit at same time: collision r Can’t interconnect 10 Base. T & 100 Base. T 5: Data. Link Layer 46

Bridges r Link layer device m stores and forwards Ethernet frames m examines frame header and selectively forwards frame based on MAC dest address m when frame is to be forwarded on segment, uses CSMA/CD to access segment r transparent m hosts are unaware of presence of bridges r plug-and-play, self-learning m bridges do not need to be configured 5: Data. Link Layer 47

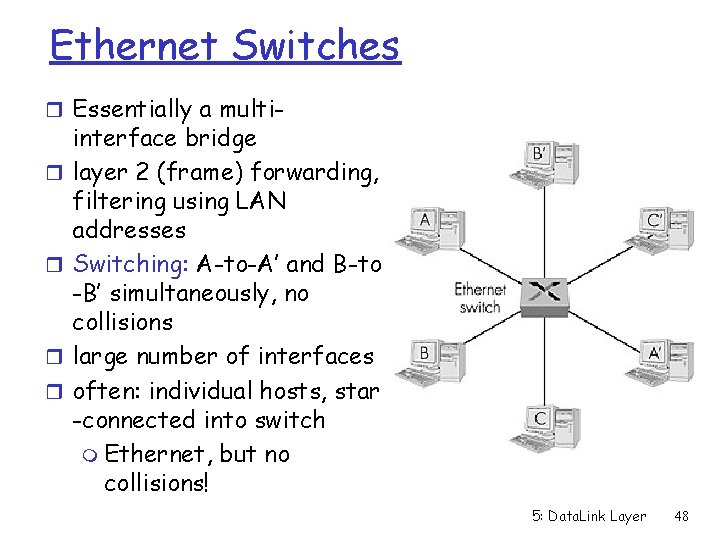
Ethernet Switches r Essentially a multir r interface bridge layer 2 (frame) forwarding, filtering using LAN addresses Switching: A-to-A’ and B-to -B’ simultaneously, no collisions large number of interfaces often: individual hosts, star -connected into switch m Ethernet, but no collisions! 5: Data. Link Layer 48