Chapter 5 Link Layer and LANs A note



![PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram](https://slidetodoc.com/presentation_image_h2/b028dae1253f07833a3a4f14905aa18d/image-21.jpg)
- Slides: 27

Chapter 5 Link Layer and LANs A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in Power. Point form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: q If you use these slides (e. g. , in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) q If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Computer Networking: A Top Down Approach 4 th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007. Thanks and enjoy! JFK/KWR All material copyright 1996 -2007 J. F Kurose and K. W. Ross, All Rights Reserved 5: Data. Link Layer 1

Chapter 5: The Data Link Layer Our goals: r understand principles behind data link layer services: m m error detection, correction sharing a broadcast channel: multiple access link layer addressing reliable data transfer, flow control r instantiation and implementation of various link layer technologies 5: Data. Link Layer 2

Link Layer r 5. 1 Introduction and r r services 5. 2 Error detection and correction 5. 3 Multiple access protocols 5. 4 Link-layer Addressing 5. 5 Ethernet r 5. 6 Link-layer switches r 5. 7 PPP r 5. 8 Link virtualization: ATM, MPLS 5: Data. Link Layer 3

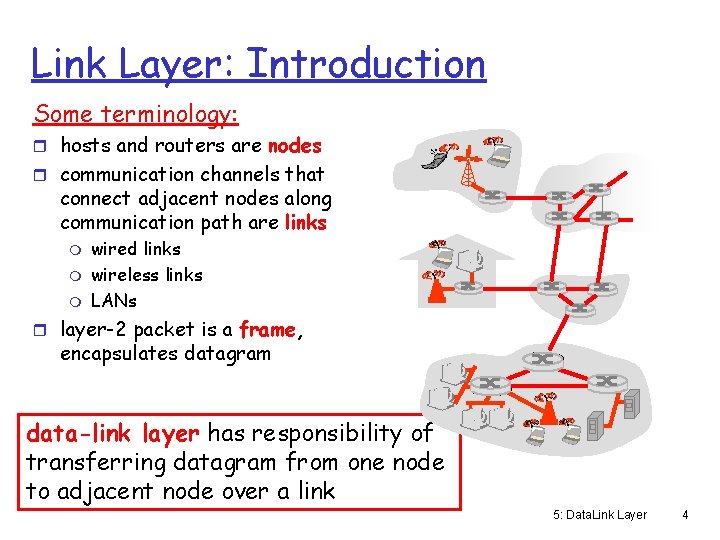
Link Layer: Introduction Some terminology: r hosts and routers are nodes r communication channels that connect adjacent nodes along communication path are links m m m wired links wireless links LANs r layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 5: Data. Link Layer 4

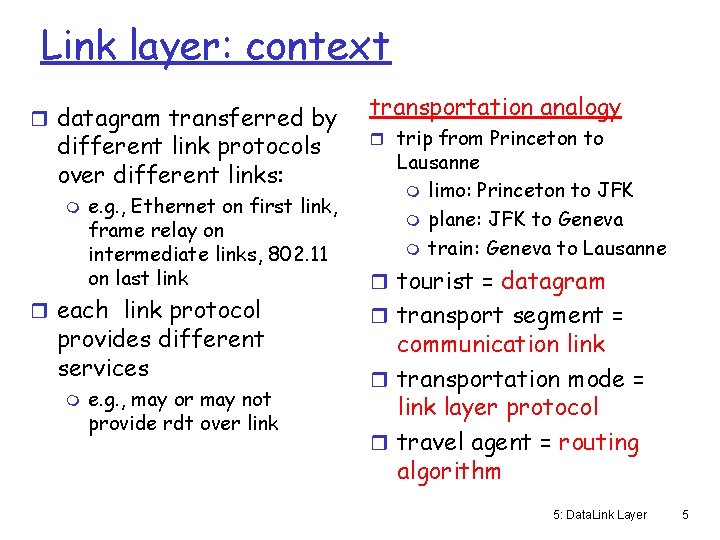
Link layer: context r datagram transferred by different link protocols over different links: m e. g. , Ethernet on first link, frame relay on intermediate links, 802. 11 on last link r each link protocol provides different services m e. g. , may or may not provide rdt over link transportation analogy r trip from Princeton to Lausanne m limo: Princeton to JFK m plane: JFK to Geneva m train: Geneva to Lausanne r tourist = datagram r transport segment = communication link r transportation mode = link layer protocol r travel agent = routing algorithm 5: Data. Link Layer 5

Link Layer Services r framing, link access: m encapsulate datagram into frame, adding header, trailer m channel access if shared medium m “MAC” addresses used in frame headers to identify source, dest • different from IP address! r reliable delivery between adjacent nodes m seldom used on low bit-error link (fiber, some twisted pair) m wireless links: high error rates • Q: why both link-level and end-end reliability? 5: Data. Link Layer 6

Link Layer Services (more) r flow control: m pacing between adjacent sending and receiving nodes r error detection: m errors caused by signal attenuation, noise. m receiver detects presence of errors: • signals sender for retransmission or drops frame r error correction: m receiver identifies and corrects bit error(s) without resorting to retransmission r half-duplex and full-duplex m with half duplex, nodes at both ends of link can transmit, but not at same time 5: Data. Link Layer 7

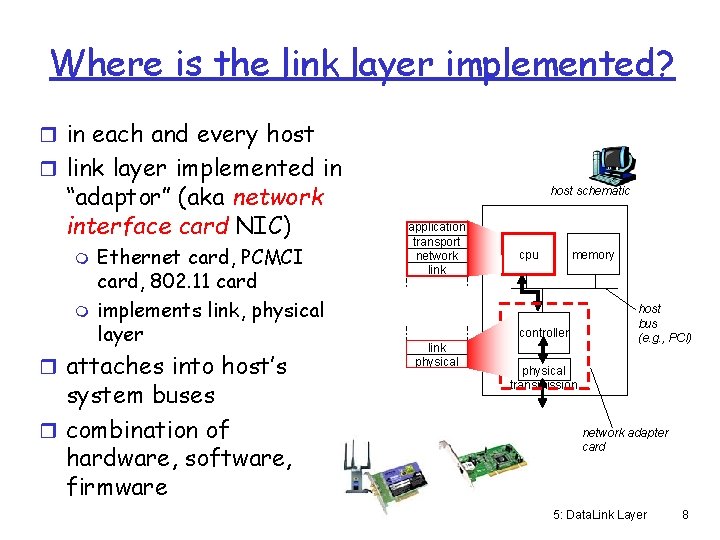
Where is the link layer implemented? r in each and every host r link layer implemented in “adaptor” (aka network interface card NIC) m m Ethernet card, PCMCI card, 802. 11 card implements link, physical layer r attaches into host’s system buses r combination of hardware, software, firmware host schematic application transport network link cpu memory controller link physical host bus (e. g. , PCI) physical transmission network adapter card 5: Data. Link Layer 8

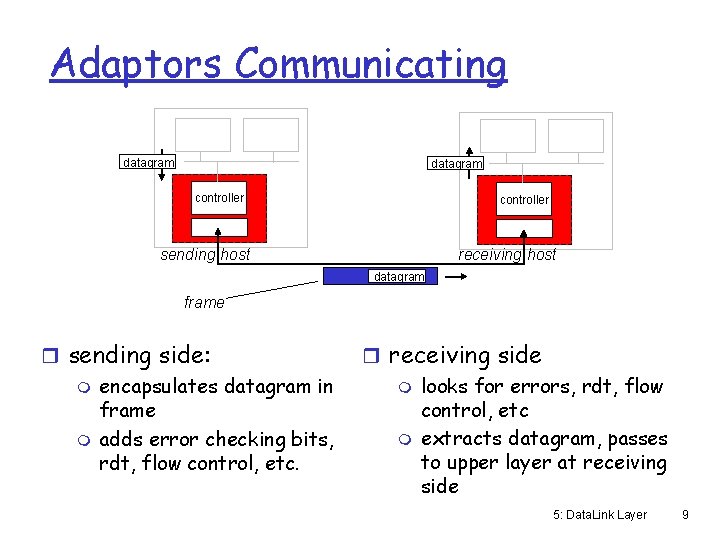
Adaptors Communicating datagram controller receiving host sending host datagram frame r sending side: m encapsulates datagram in frame m adds error checking bits, rdt, flow control, etc. r receiving side m looks for errors, rdt, flow control, etc m extracts datagram, passes to upper layer at receiving side 5: Data. Link Layer 9

Link Layer r 5. 1 Introduction and r r services 5. 2 Error detection and correction 5. 3 Multiple access protocols 5. 4 Link-layer Addressing 5. 5 Ethernet r 5. 6 Link-layer switches r 5. 7 PPP r 5. 8 Link Virtualization: ATM. MPLS 5: Data. Link Layer 10

Error Detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction otherwise 5: Data. Link Layer 11

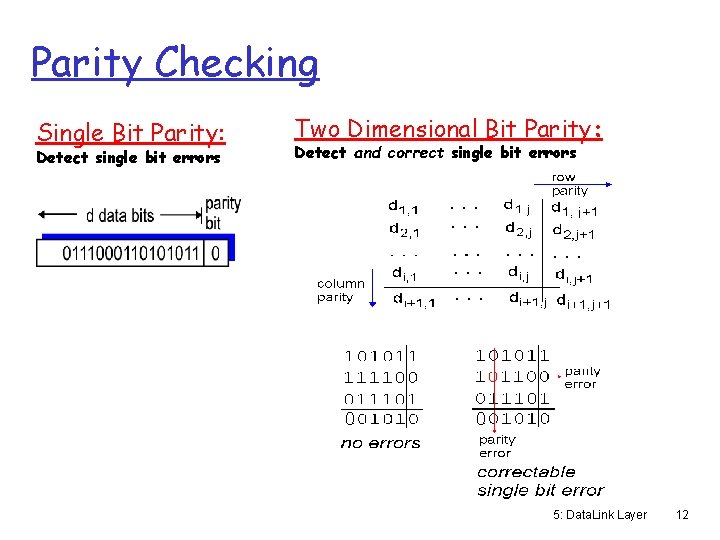
Parity Checking Single Bit Parity: Detect single bit errors Two Dimensional Bit Parity: Detect and correct single bit errors 0 0 5: Data. Link Layer 12

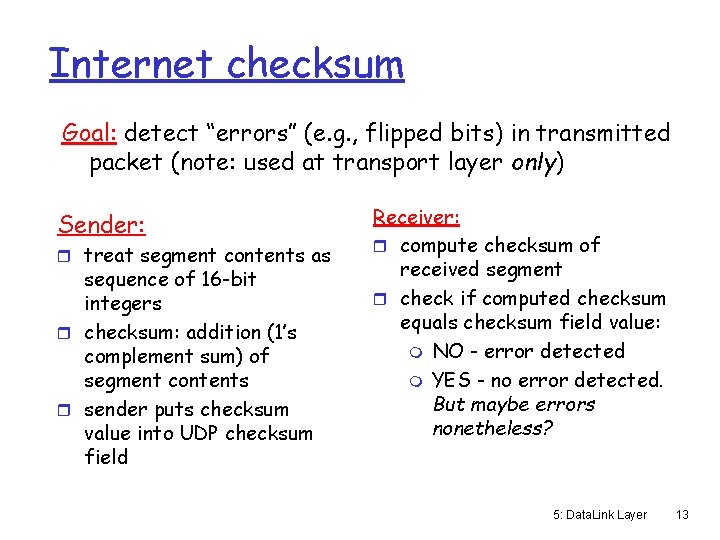
Internet checksum Goal: detect “errors” (e. g. , flipped bits) in transmitted packet (note: used at transport layer only) Sender: r treat segment contents as sequence of 16 -bit integers r checksum: addition (1’s complement sum) of segment contents r sender puts checksum value into UDP checksum field Receiver: r compute checksum of received segment r check if computed checksum equals checksum field value: m NO - error detected m YES - no error detected. But maybe errors nonetheless? 5: Data. Link Layer 13

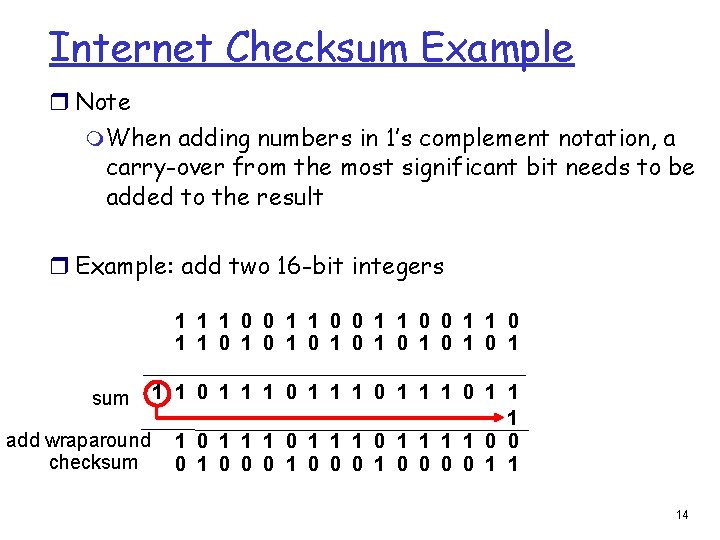
Internet Checksum Example r Note m When adding numbers in 1’s complement notation, a carry-over from the most significant bit needs to be added to the result r Example: add two 16 -bit integers 1 1 0 0 1 1 1 0 1 0 1 1 1 0 1 1 1 add wraparound 1 1 0 1 1 0 0 checksum 1 0 0 0 0 1 1 sum 14

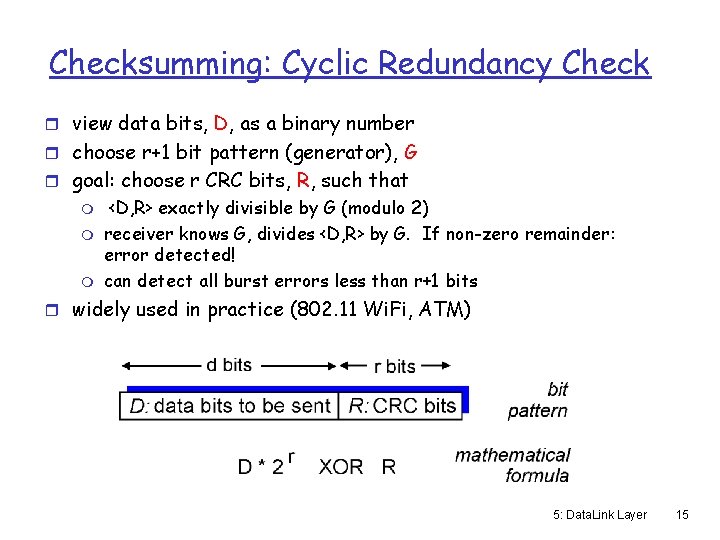
Checksumming: Cyclic Redundancy Check r view data bits, D, as a binary number r choose r+1 bit pattern (generator), G r goal: choose r CRC bits, R, such that m m m <D, R> exactly divisible by G (modulo 2) receiver knows G, divides <D, R> by G. If non-zero remainder: error detected! can detect all burst errors less than r+1 bits r widely used in practice (802. 11 Wi. Fi, ATM) 5: Data. Link Layer 15

Checksumming: Cyclic Redundancy Check r Sender has data D, which is d bits long. r Sender computes R, an r-bit CRC of those d bits mr is usually 8, 12, 16, or 32 r Sender sends D followed by R to the receiver r Receiver computes the CRC of the received data m If no match, there were certainly errors m If match, no error detected 16

Checksumming: Cyclic Redundancy Check r Better at detecting errors than other methods we've seen m Can detect all burst errors up to r bits m But much more complicated to compute r Since the link layer is handled semi-autonomously in adapter hardware, CRCs are more appropriate for the link layer than for higher layers in the protocol stack. r The mathematical details are in the text. 17

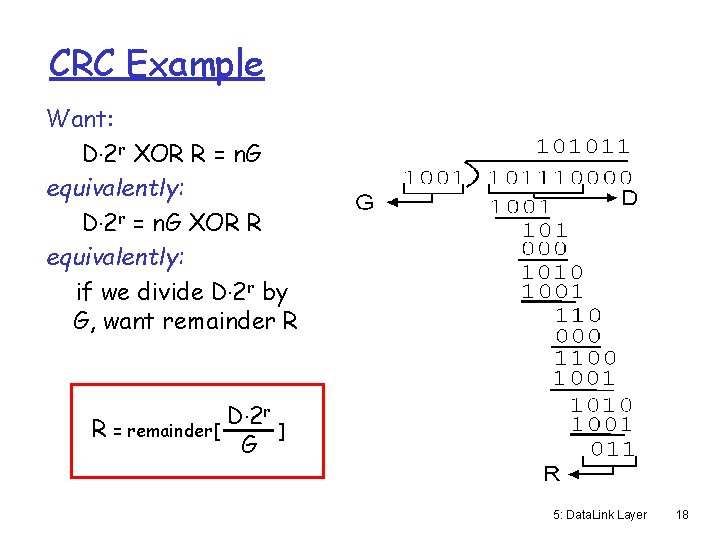
CRC Example Want: D. 2 r XOR R = n. G equivalently: D. 2 r = n. G XOR R equivalently: if we divide D. 2 r by G, want remainder R R = remainder[ D. 2 r G ] 5: Data. Link Layer 18

Link Layer r 5. 1 Introduction and r r services 5. 2 Error detection and correction 5. 3 Multiple access protocols 5. 4 Link-Layer Addressing 5. 5 Ethernet r 5. 6 Hubs and switches r 5. 7 PPP r 5. 8 Link Virtualization: ATM 5: Data. Link Layer 19

Point to Point Data Link Control r one sender, one receiver, one link: easier than broadcast link: m no Media Access Control m no need for explicit MAC addressing m e. g. , dialup link, ISDN line r most popular point-to-point DLC protocol: m PPP (point-to-point protocol) m probably use this at home: • Dailup : Plain PPP • ADSL : PPP over Ethernet (PPPo. E) 5: Data. Link Layer 20
![PPP Design Requirements RFC 1557 r packet framing encapsulation of networklayer r r datagram PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram](https://slidetodoc.com/presentation_image_h2/b028dae1253f07833a3a4f14905aa18d/image-21.jpg)
PPP Design Requirements [RFC 1557] r packet framing: encapsulation of network-layer r r datagram in data link frame m carry network layer data of any network layer protocol (not just IP) at same time m ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer address negotiation: endpoint can learn/configure each other’s network address 5: Data. Link Layer 21

PPP non-requirements r no error correction/recovery r no flow control r out of order delivery OK r no need to support multipoint links (e. g. , polling) Error recovery, flow control, data re-ordering all relegated to higher layers! 5: Data. Link Layer 22

PPP Data Control Protocol Before exchanging networklayer data, data link peers must r configure PPP link (max. frame length, authentication) r learn/configure network layer information m for IP: carry IP Control Protocol (IPCP) msgs (protocol field: 8021) to configure/learn IP address 5: Data. Link Layer 23

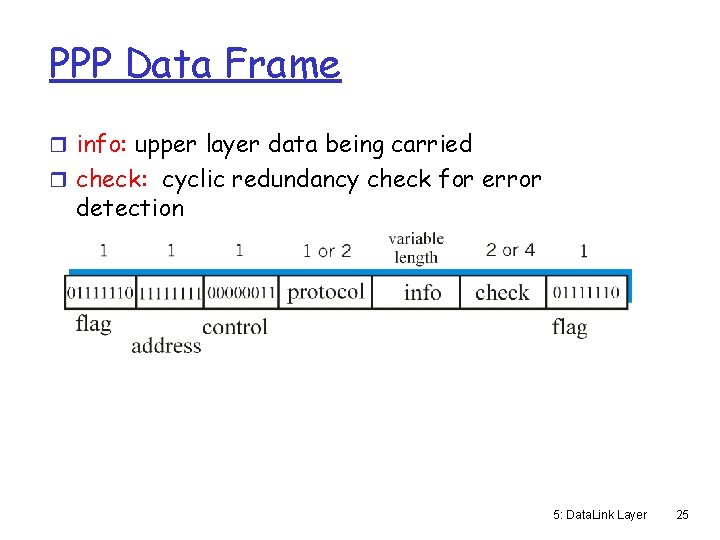
PPP Data Frame r Flag: delimiter (framing) r Address: does nothing (only one option) r Control: does nothing; in the future possible multiple control fields r Protocol: upper layer protocol to which frame delivered (eg, PPP-LCP, IPCP, etc) 5: Data. Link Layer 24

PPP Data Frame r info: upper layer data being carried r check: cyclic redundancy check for error detection 5: Data. Link Layer 25

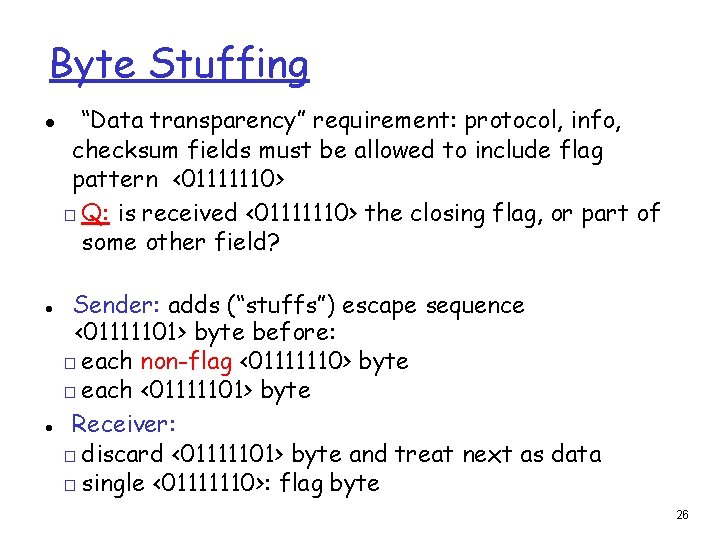
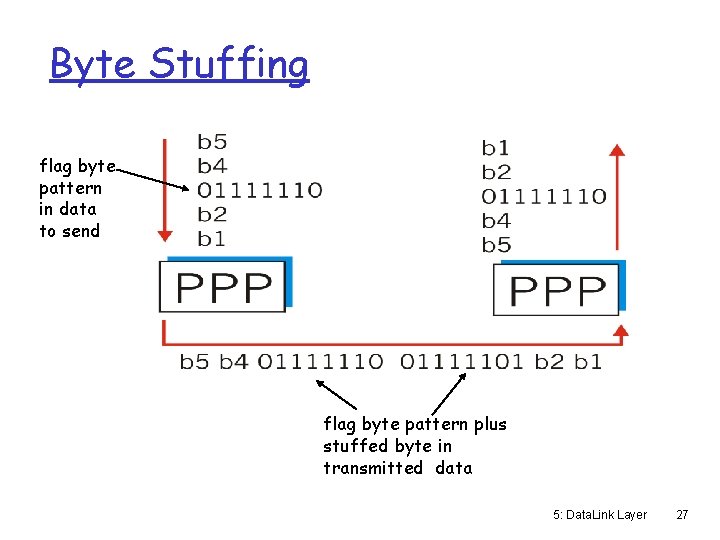
Byte Stuffing “Data transparency” requirement: protocol, info, checksum fields must be allowed to include flag pattern <01111110> □ Q: is received <01111110> the closing flag, or part of some other field? Sender: adds (“stuffs”) escape sequence <01111101> byte before: □ each non-flag <01111110> byte □ each <01111101> byte Receiver: □ discard <01111101> byte and treat next as data □ single <01111110>: flag byte 26

Byte Stuffing flag byte pattern in data to send flag byte pattern plus stuffed byte in transmitted data 5: Data. Link Layer 27