Chapter 5 2 The Network Layer Congestion Control









- Slides: 50

Chapter 5 -2 The Network Layer

Congestion Control Algorithms • • • General Principles of Congestion Control Congestion Prevention Policies Congestion Control in Virtual-Circuit Subnets Congestion Control in Datagram Subnets Load Shedding Jitter Control

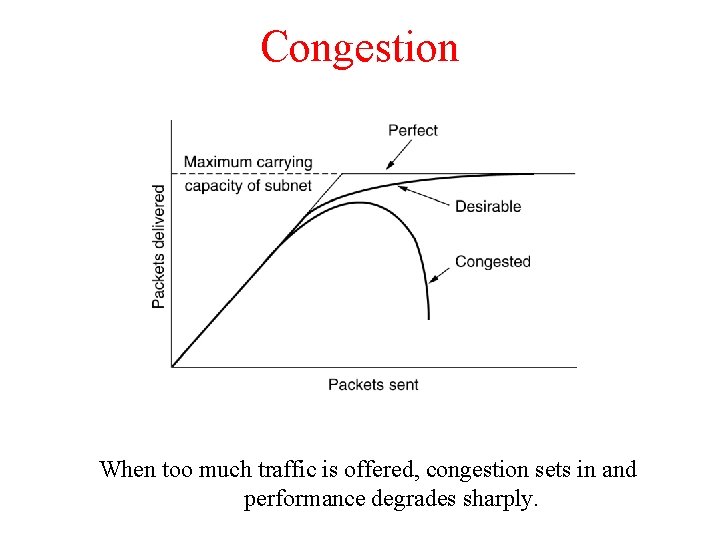
Congestion When too much traffic is offered, congestion sets in and performance degrades sharply.

General Principles of Congestion Control a) Monitor the system. – detect when and where congestion occurs. b) Pass information to where action can be taken. c) Adjust system operation to correct the problem.

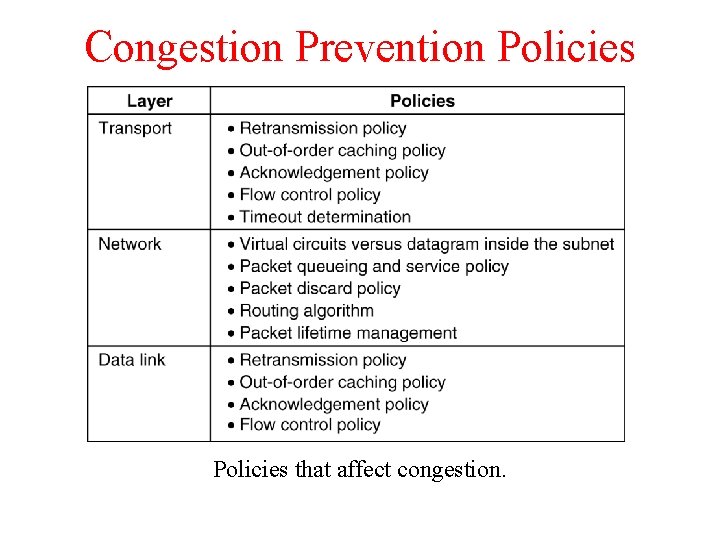
Congestion Prevention Policies 5 -26 Policies that affect congestion.

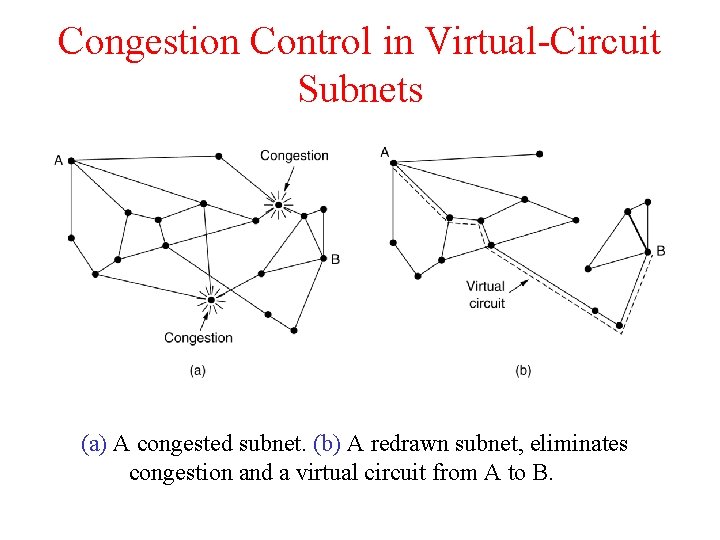
Congestion Control in Virtual-Circuit Subnets (a) A congested subnet. (b) A redrawn subnet, eliminates congestion and a virtual circuit from A to B.

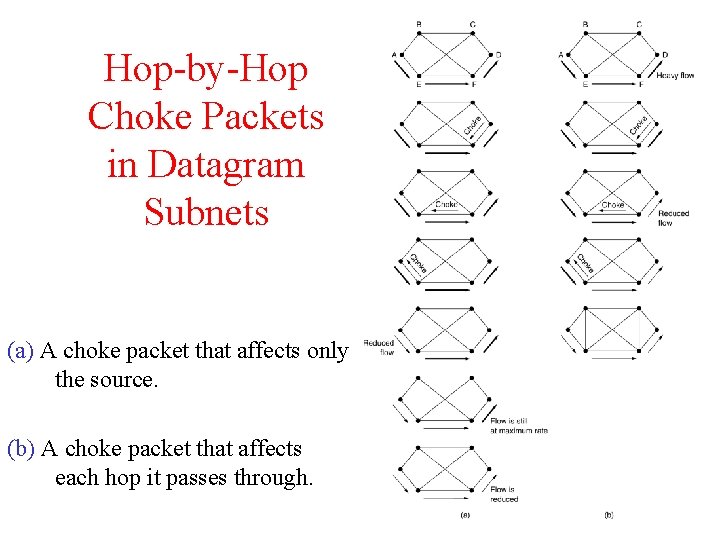
Hop-by-Hop Choke Packets in Datagram Subnets (a) A choke packet that affects only the source. (b) A choke packet that affects each hop it passes through.

Quality of Service Control • • • Requirements Techniques for Achieving Good Quality of Service Integrated Services Differentiated Services Label Switching and MPLS

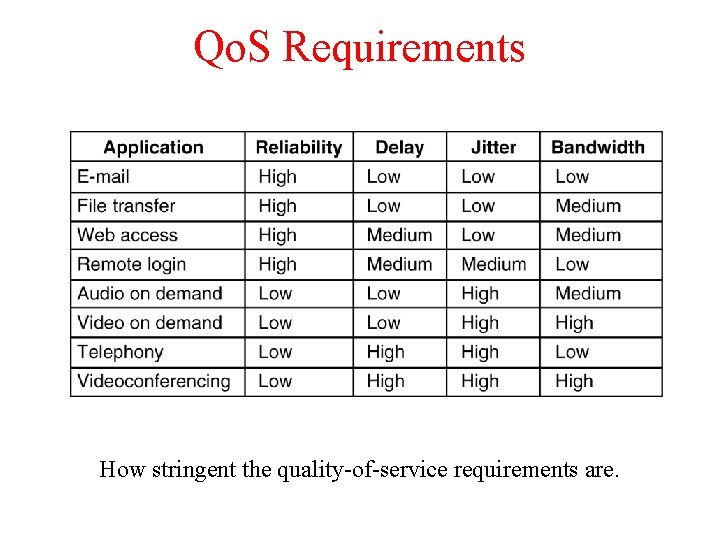
Qo. S Requirements 5 -30 How stringent the quality-of-service requirements are.

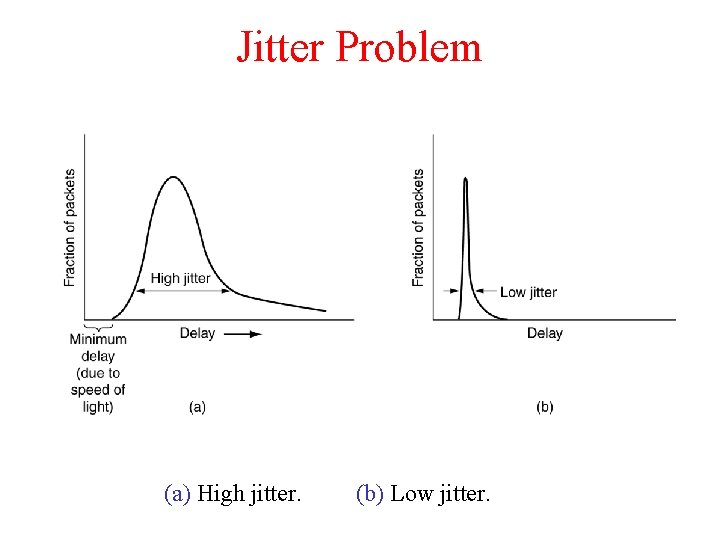
Jitter Problem (a) High jitter. (b) Low jitter.

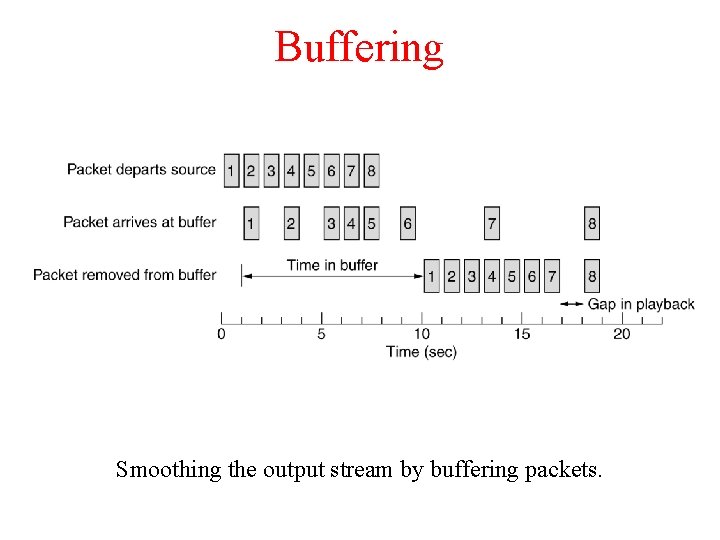
Buffering Smoothing the output stream by buffering packets.

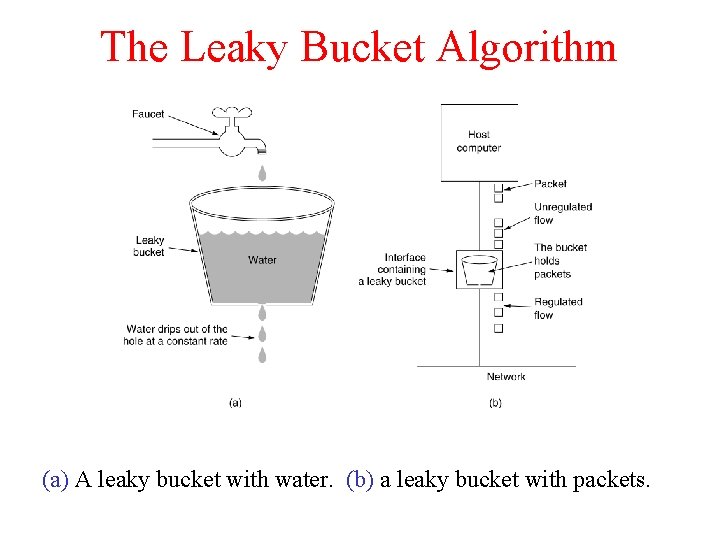
The Leaky Bucket Algorithm (a) A leaky bucket with water. (b) a leaky bucket with packets.

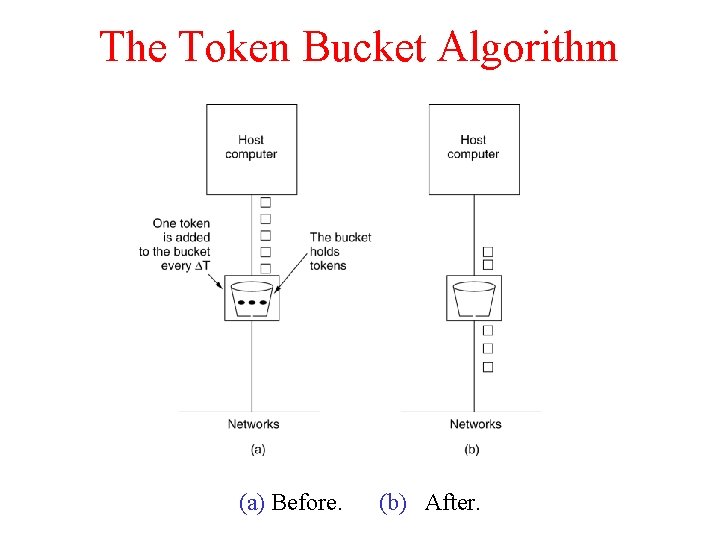
The Token Bucket Algorithm 5 -34 (a) Before. (b) After.

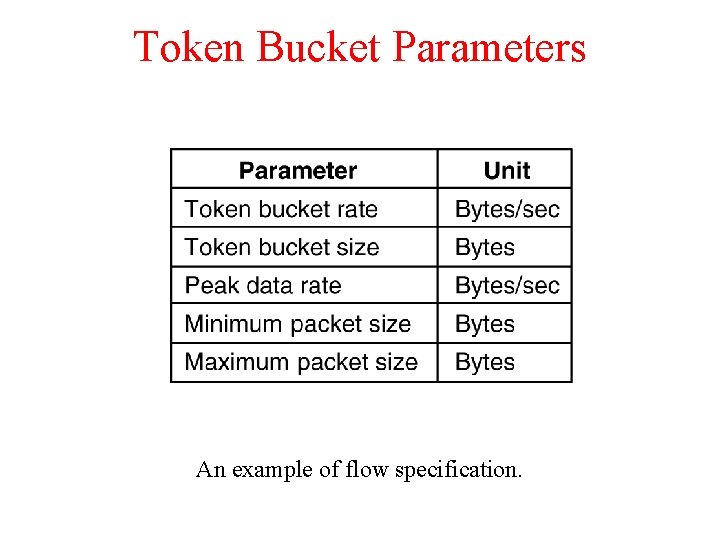
Token Bucket Parameters 5 -34 An example of flow specification.

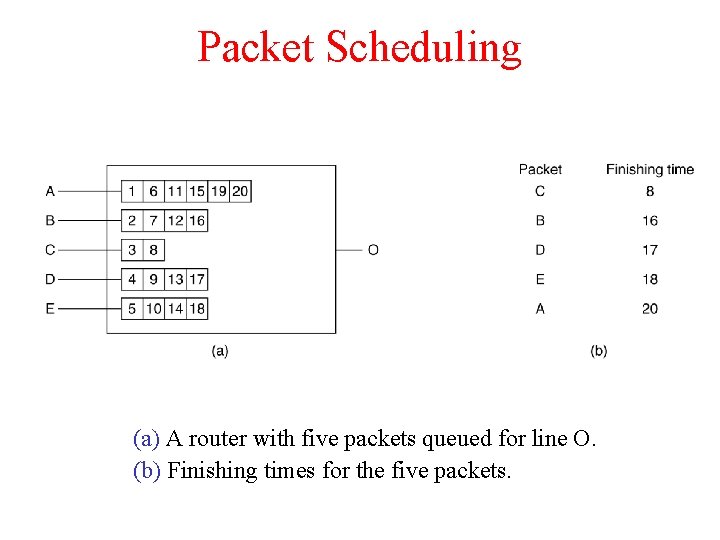
Packet Scheduling (a) A router with five packets queued for line O. (b) Finishing times for the five packets.

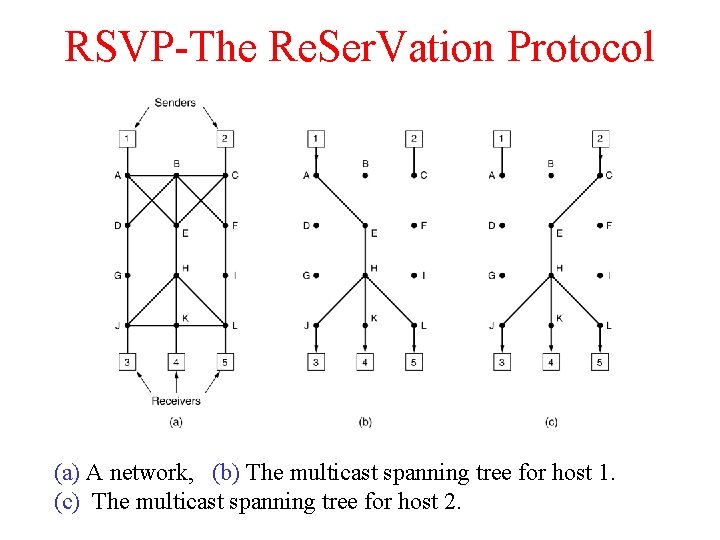
RSVP-The Re. Ser. Vation Protocol (a) A network, (b) The multicast spanning tree for host 1. (c) The multicast spanning tree for host 2.

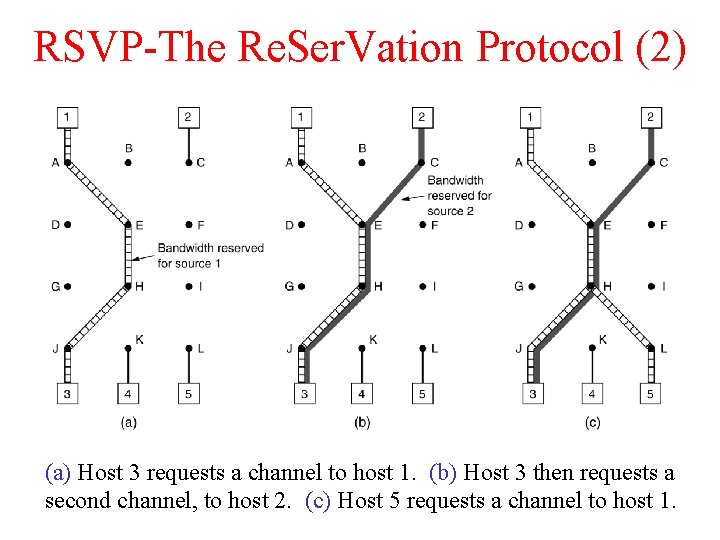
RSVP-The Re. Ser. Vation Protocol (2) (a) Host 3 requests a channel to host 1. (b) Host 3 then requests a second channel, to host 2. (c) Host 5 requests a channel to host 1.

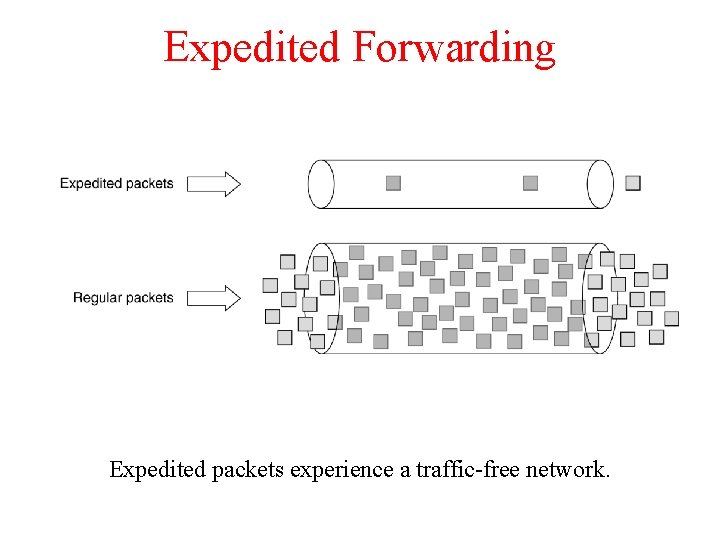
Expedited Forwarding Expedited packets experience a traffic-free network.

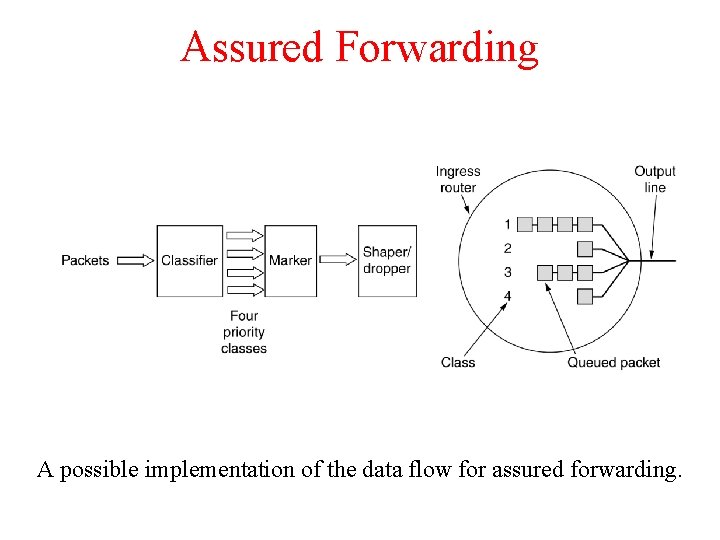
Assured Forwarding A possible implementation of the data flow for assured forwarding.

Internetworking • • How Networks Differ How Networks Can Be Connected Concatenated Virtual Circuits Connectionless Internetworking Tunneling Internetwork Routing Fragmentation

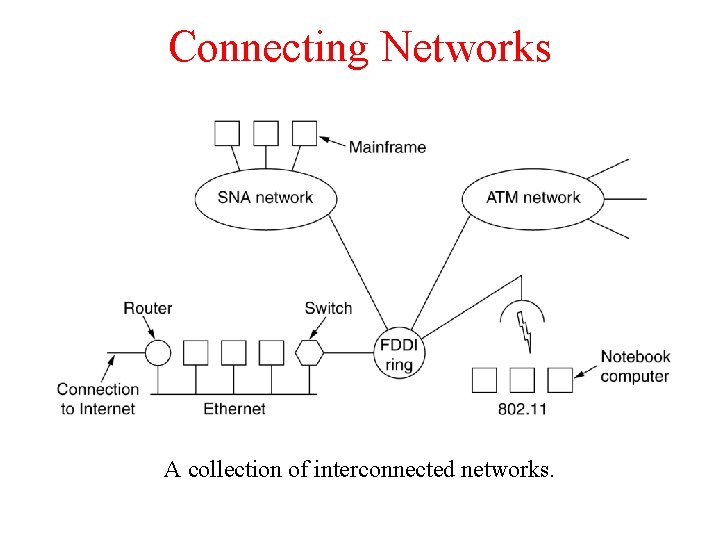
Connecting Networks A collection of interconnected networks.

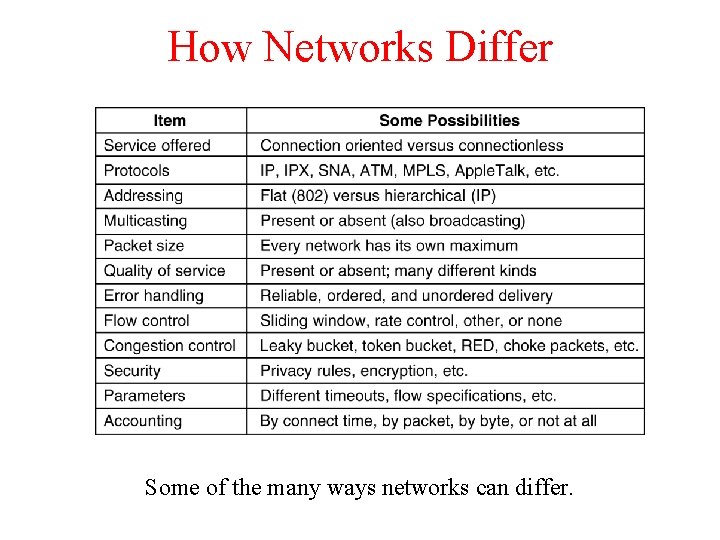
How Networks Differ 5 -43 Some of the many ways networks can differ.

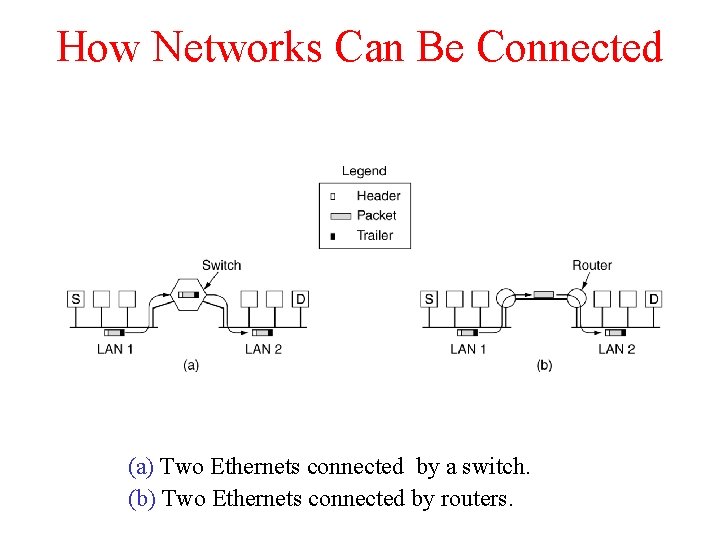
How Networks Can Be Connected (a) Two Ethernets connected by a switch. (b) Two Ethernets connected by routers.

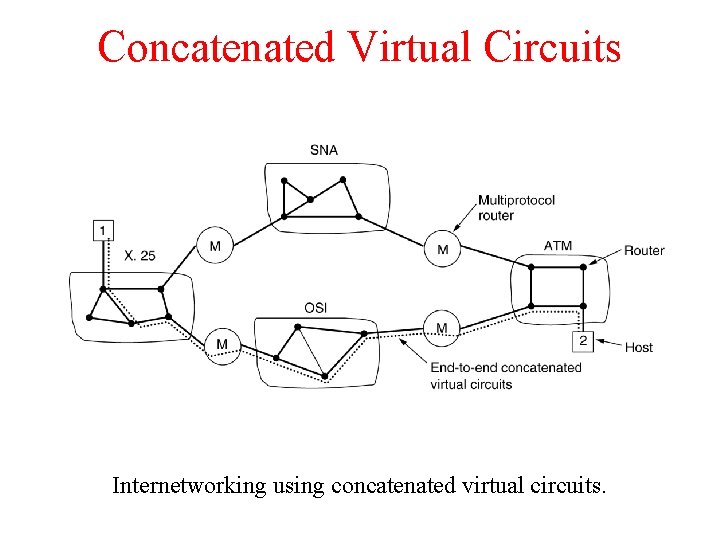
Concatenated Virtual Circuits Internetworking using concatenated virtual circuits.

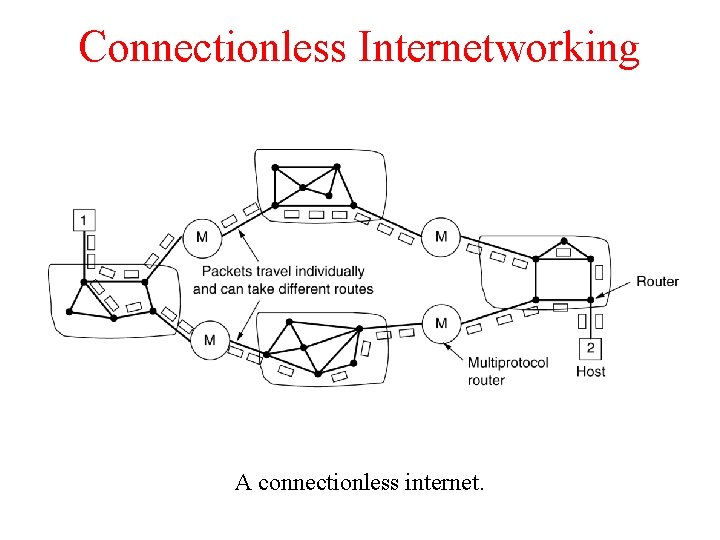
Connectionless Internetworking A connectionless internet.

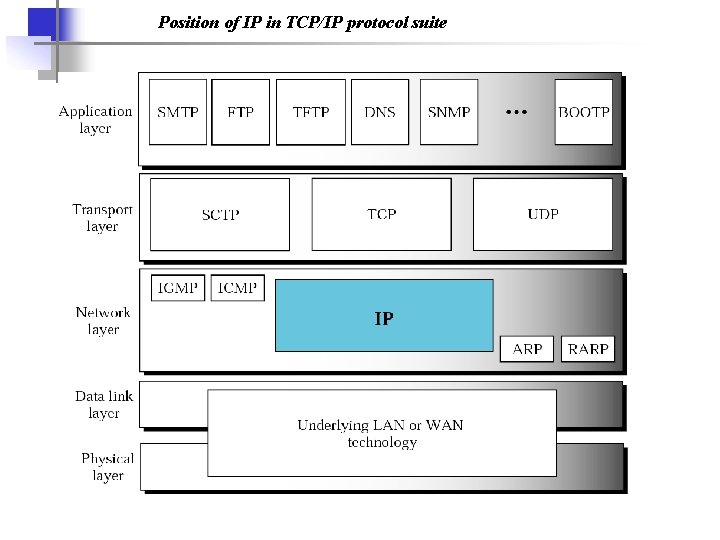
The Network Layer in the Internet • • • The IP Protocol IP Addressing Internet Control Message Protocols

Position of IP in TCP/IP protocol suite

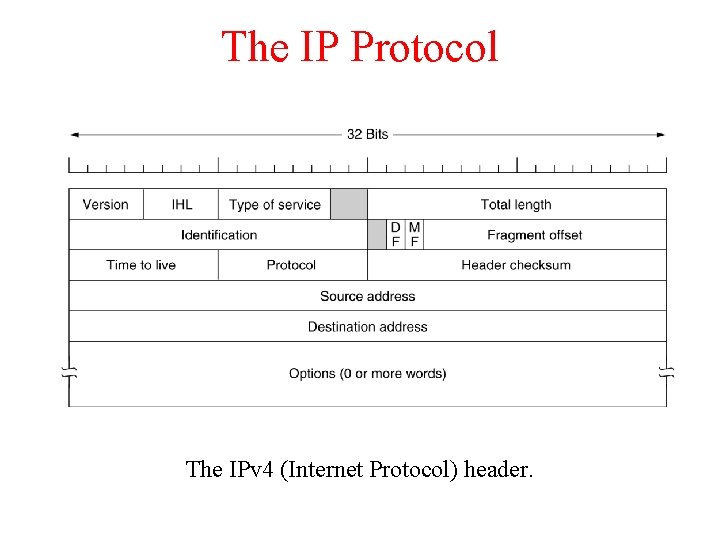
The IP Protocol The IPv 4 (Internet Protocol) header.

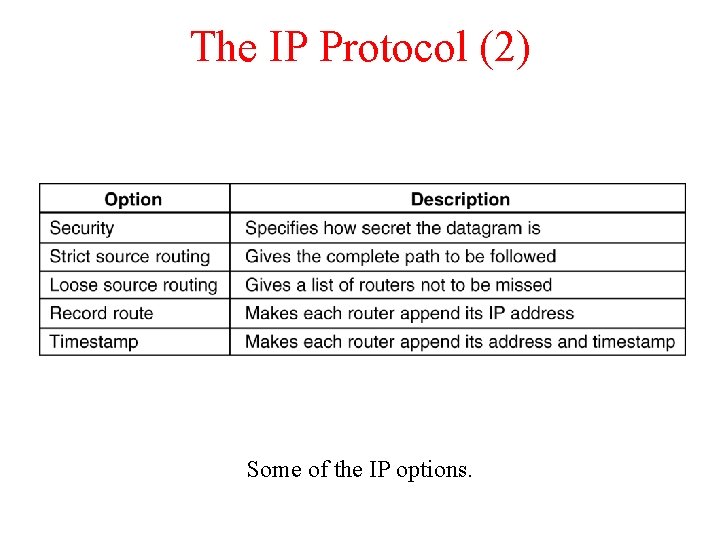
The IP Protocol (2) 5 -54 Some of the IP options.

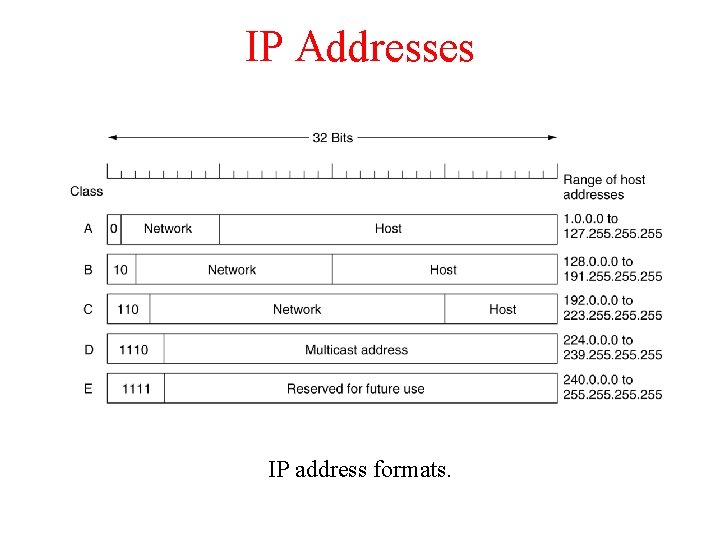
IP Addresses IP address formats.

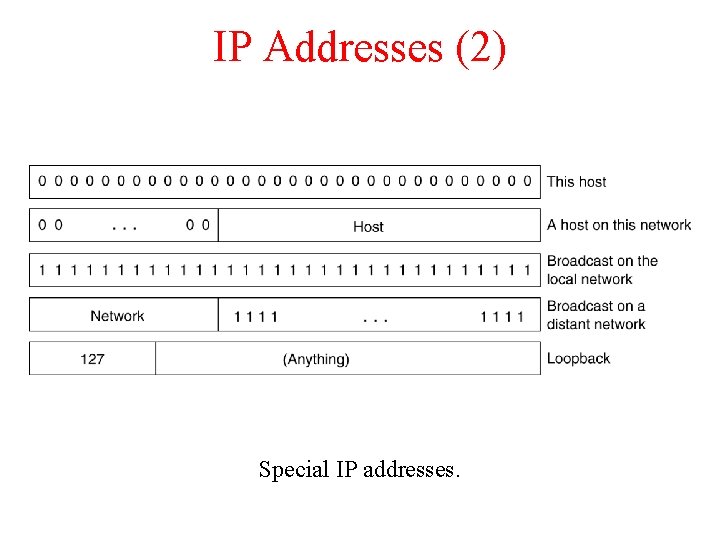
IP Addresses (2) Special IP addresses.

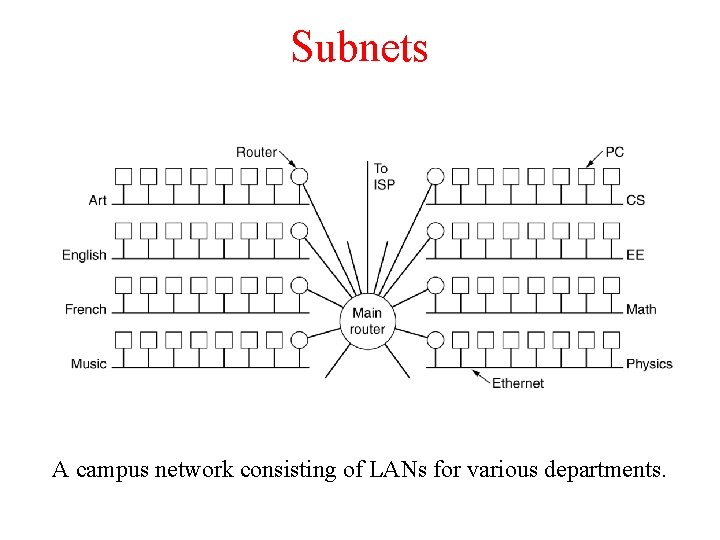
Subnets A campus network consisting of LANs for various departments.

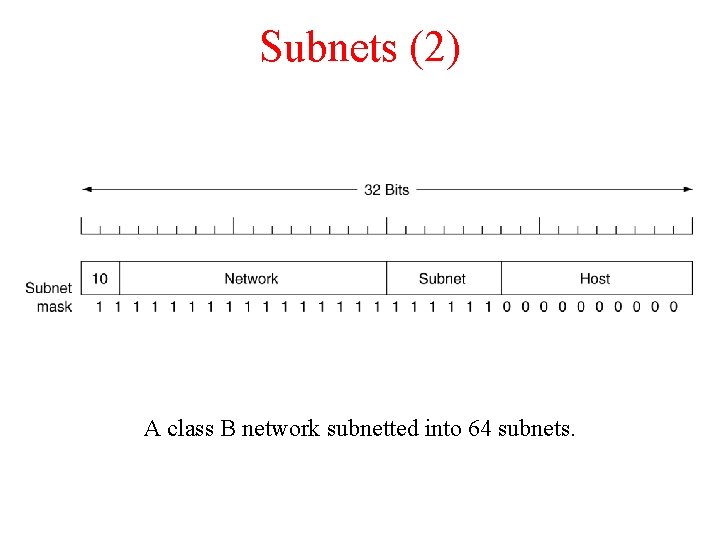
Subnets (2) A class B network subnetted into 64 subnets.

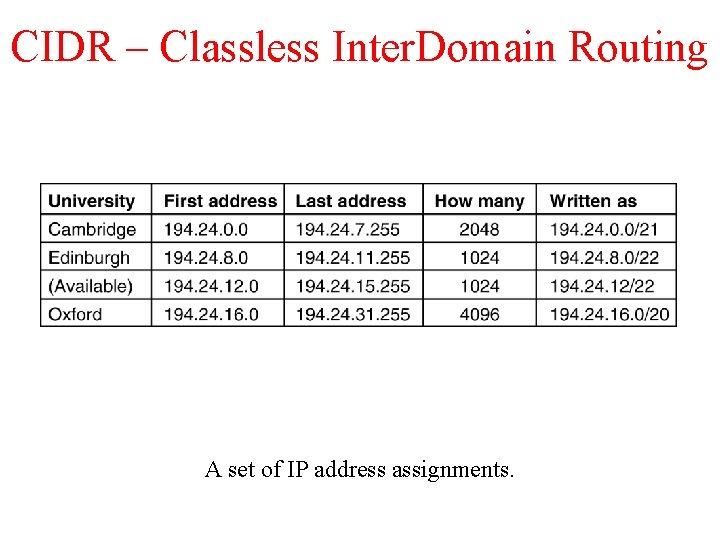
CIDR – Classless Inter. Domain Routing 5 -59 A set of IP address assignments.

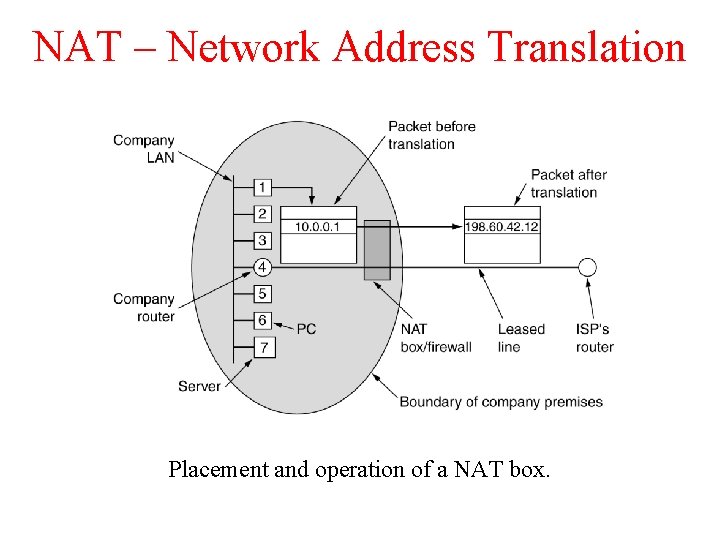
NAT – Network Address Translation Placement and operation of a NAT box.

FRAGMENTATION The format and size of a frame depend on the protocol used by the physical network. A datagram may have to be fragmented to fit the protocol regulations. The topics discussed in this section include: Maximum Transfer Unit (MTU) Fields Related to Fragmentation

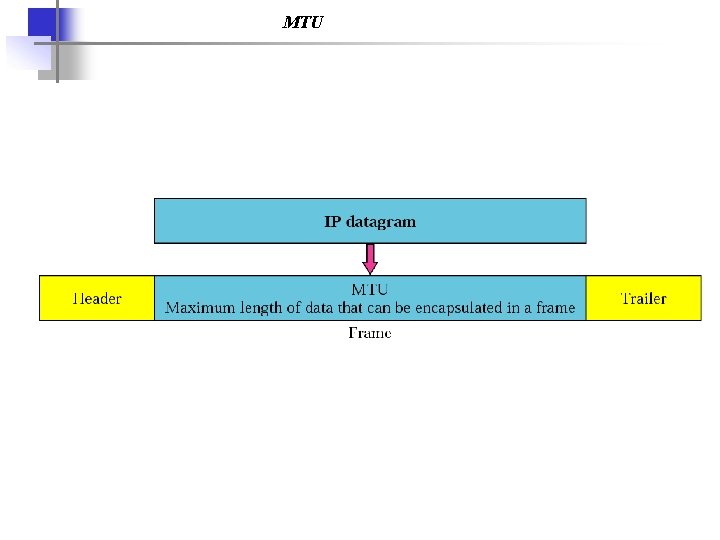
MTU

MTUs for some networks

Flags field

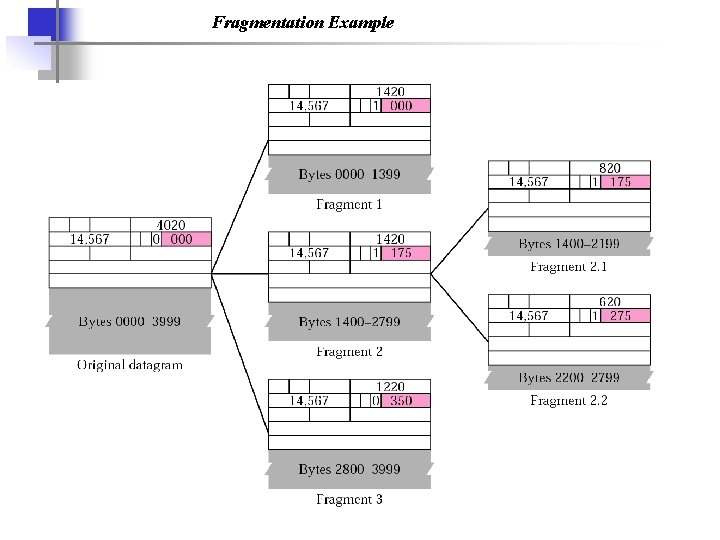
Fragmentation Example

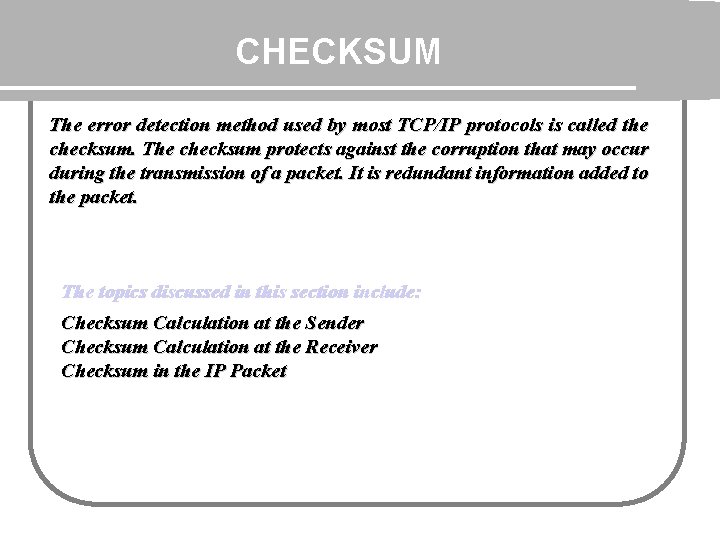
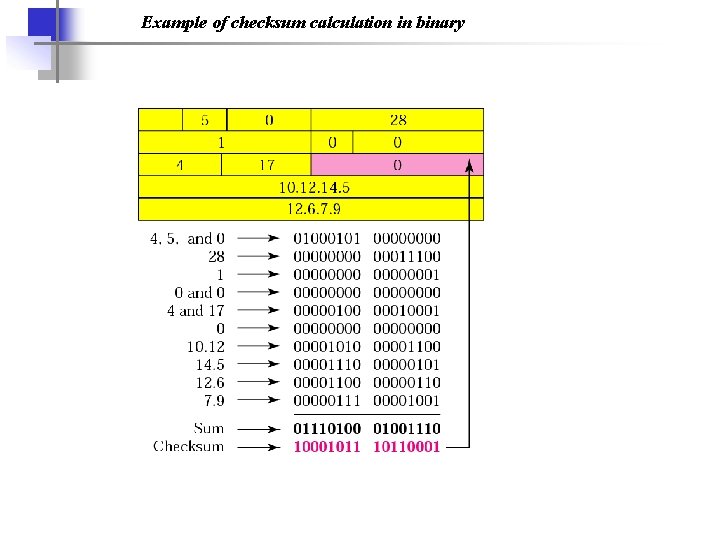
CHECKSUM The error detection method used by most TCP/IP protocols is called the checksum. The checksum protects against the corruption that may occur during the transmission of a packet. It is redundant information added to the packet. The topics discussed in this section include: Checksum Calculation at the Sender Checksum Calculation at the Receiver Checksum in the IP Packet

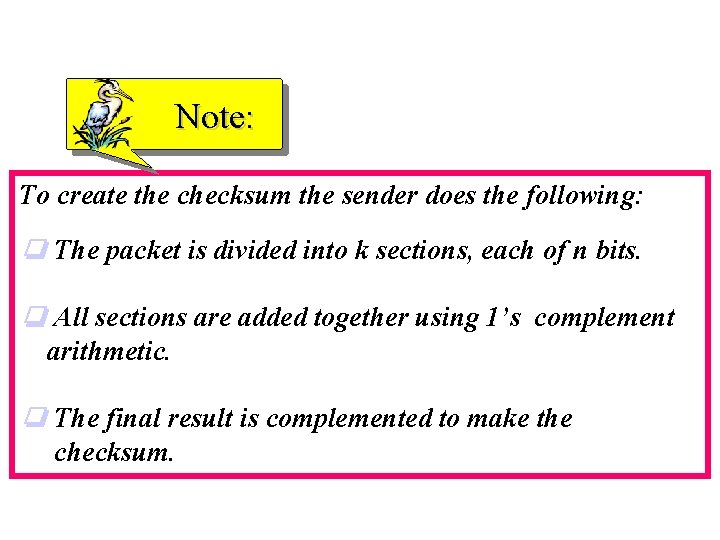
Note: To create the checksum the sender does the following: ❏ The packet is divided into k sections, each of n bits. ❏ All sections are added together using 1’s complement arithmetic. ❏ The final result is complemented to make the checksum.

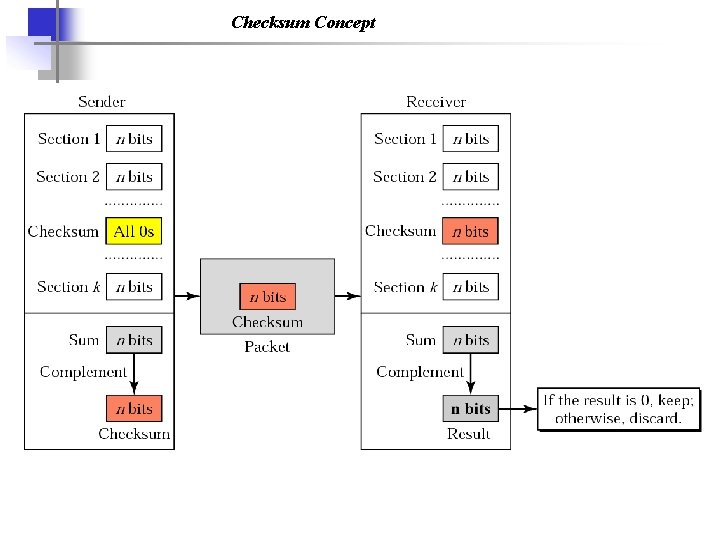
Checksum Concept

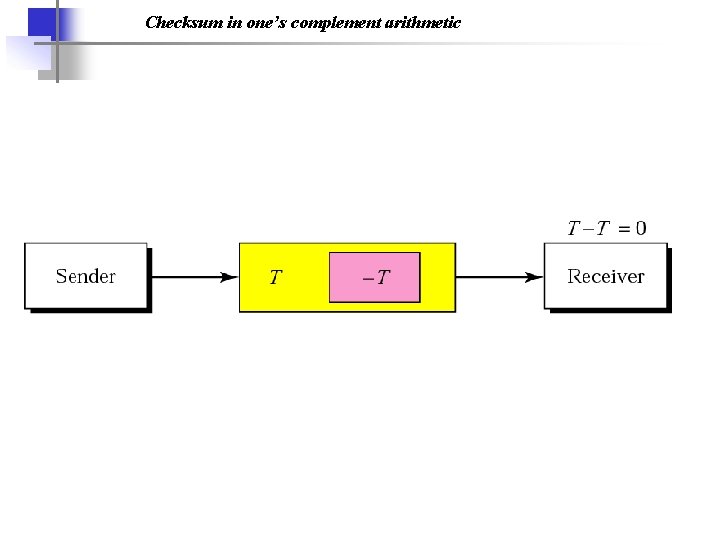
Checksum in one’s complement arithmetic

Example of checksum calculation in binary

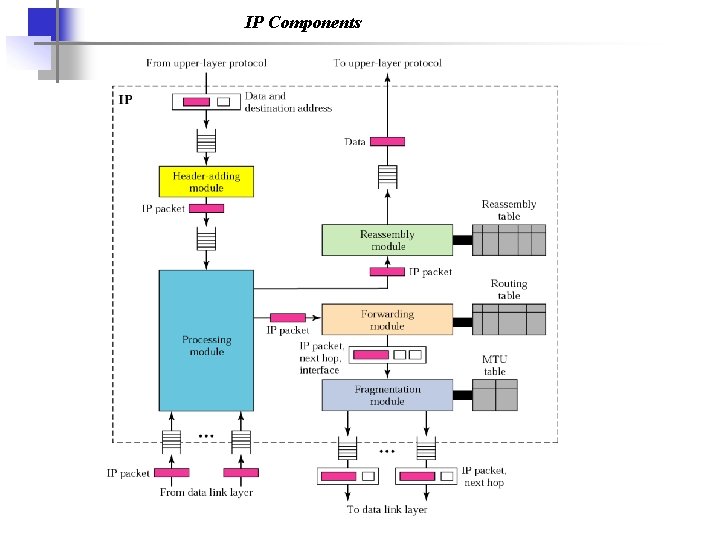
IP PACKAGE We give an example of a simplified IP software package to show its components and the relationships between the components. This IP package involves eight modules. The topics discussed in this section include: Header-Adding Module Processing Module Queues Routing Table Forwarding Module MTU Table Fragmentation Module Reassembly Table Reassembly Module

IP Components

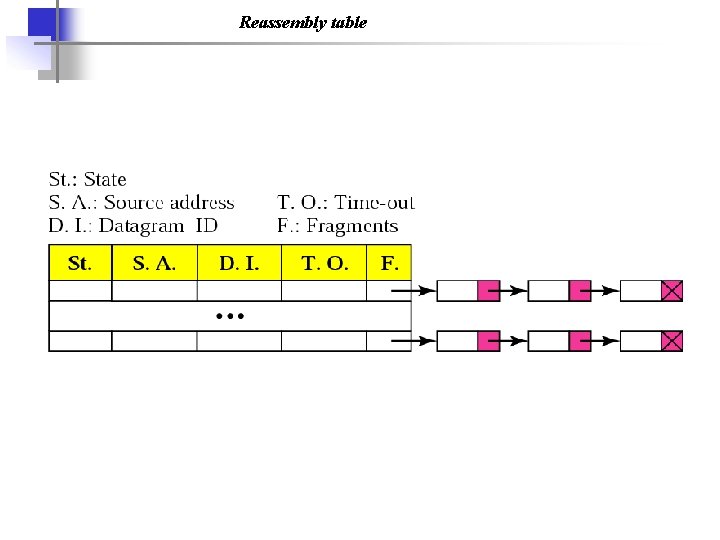
Reassembly table

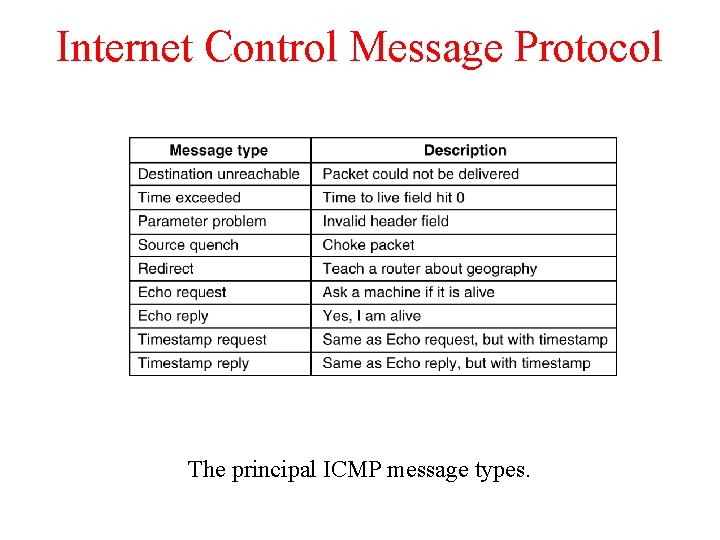
Internet Control Message Protocol 5 -61 The principal ICMP message types.

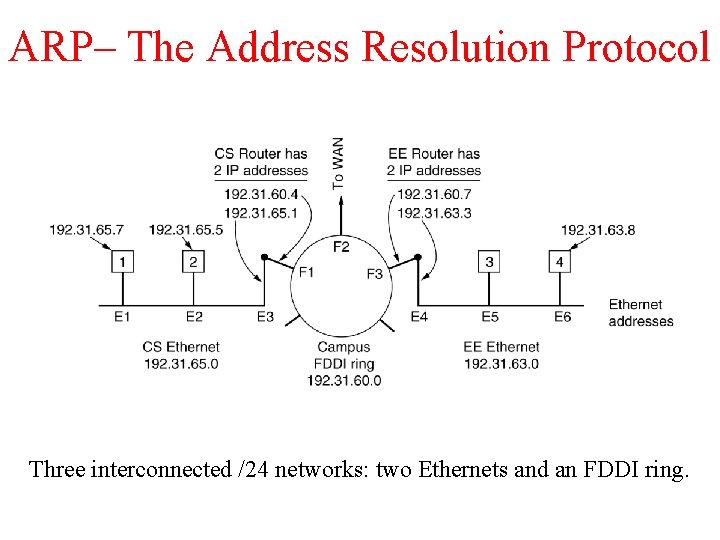
ARP– The Address Resolution Protocol Three interconnected /24 networks: two Ethernets and an FDDI ring.