Chapter 4 Requirements Definition User Outline Requirements Items















- Slides: 29

Chapter – 4 Requirements Definition

User Outline Requirements Items to be inventoried Requirement categories Traffic sizing Traffic characteristics Time and Delay consideration Network Delay elements Connectivity types Availability and Reliability Service Aspects Budget constraints

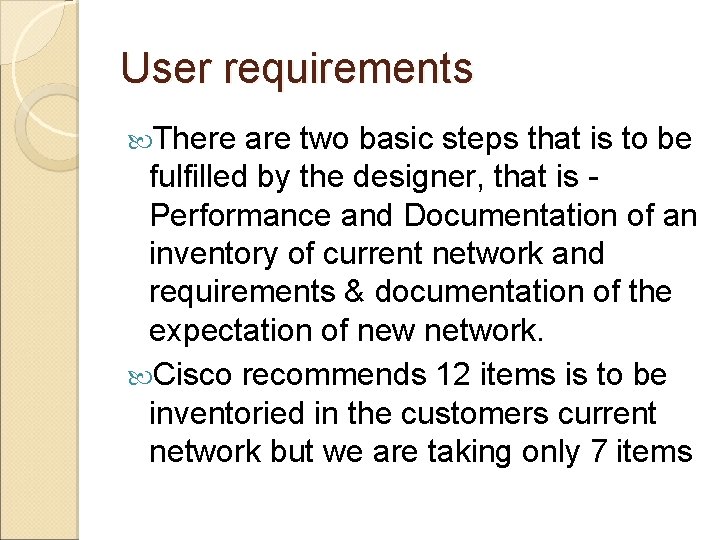
User requirements There are two basic steps that is to be fulfilled by the designer, that is Performance and Documentation of an inventory of current network and requirements & documentation of the expectation of new network. Cisco recommends 12 items is to be inventoried in the customers current network but we are taking only 7 items

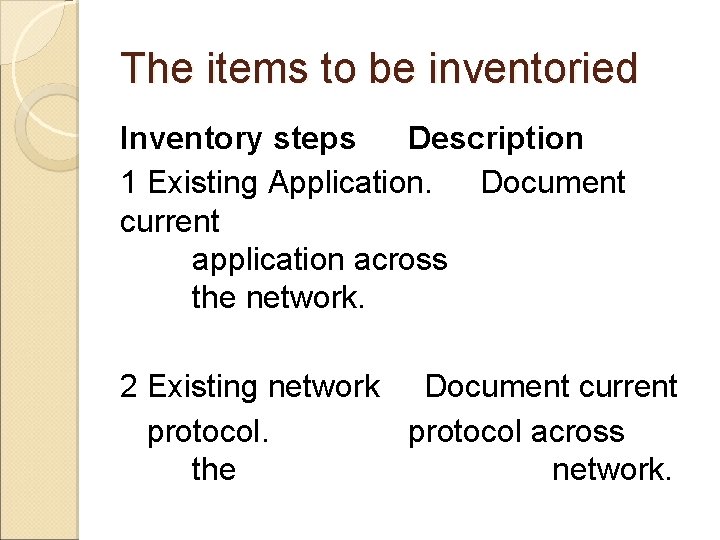
The items to be inventoried Inventory steps Description 1 Existing Application. Document current application across the network. 2 Existing network Document current protocol across the network.

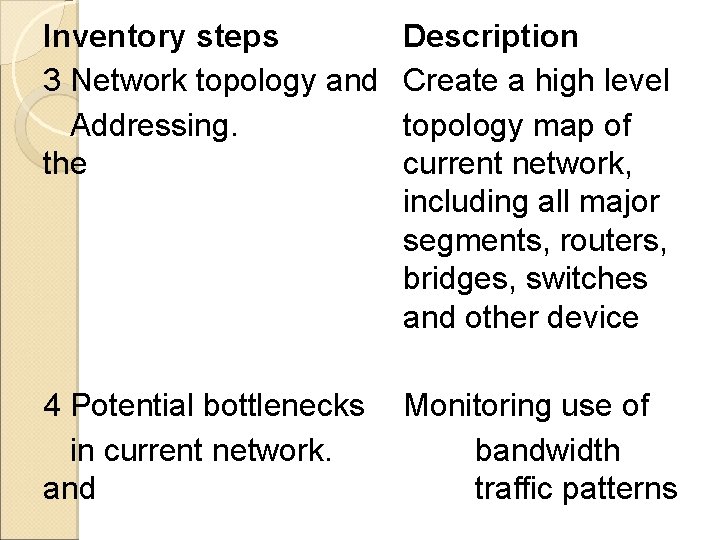
Inventory steps 3 Network topology and Addressing. the Description Create a high level topology map of current network, including all major segments, routers, bridges, switches and other device 4 Potential bottlenecks in current network. and Monitoring use of bandwidth traffic patterns

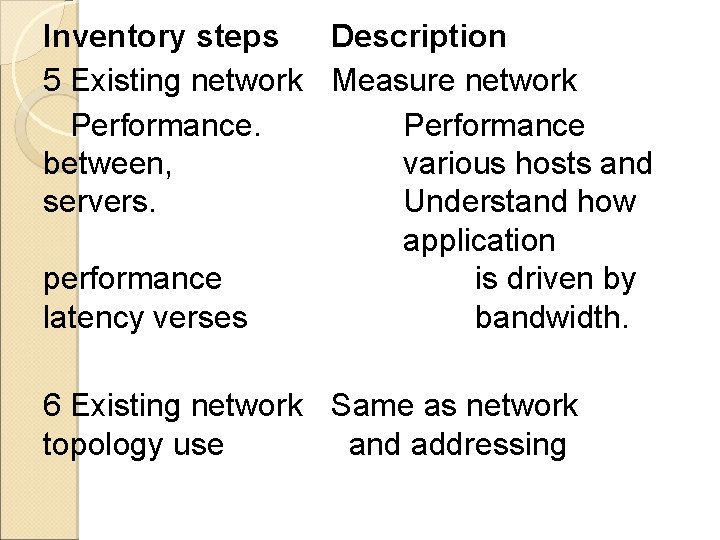
Inventory steps Description 5 Existing network Measure network Performance between, various hosts and servers. Understand how application performance is driven by latency verses bandwidth. 6 Existing network Same as network topology use and addressing

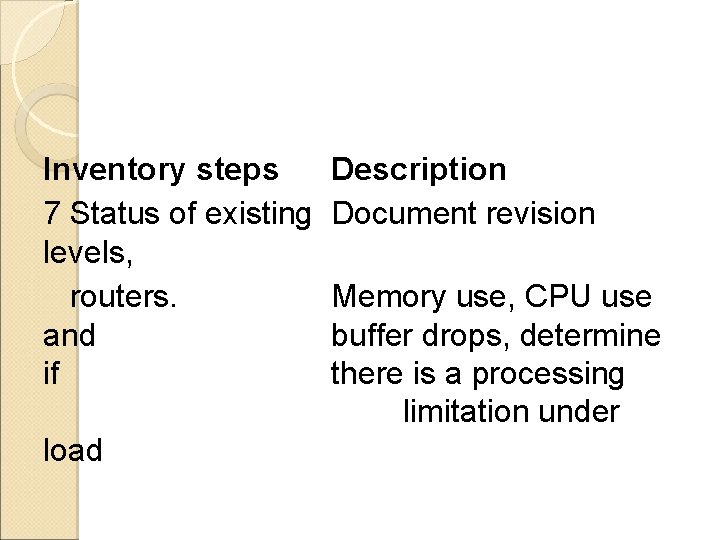
Inventory steps 7 Status of existing levels, routers. and if load Description Document revision Memory use, CPU use buffer drops, determine there is a processing limitation under

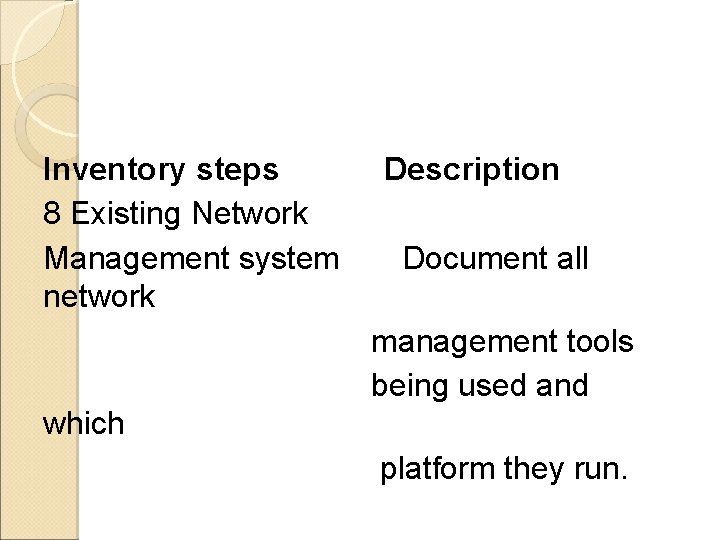
Inventory steps 8 Existing Network Management system network Description Document all management tools being used and which platform they run.

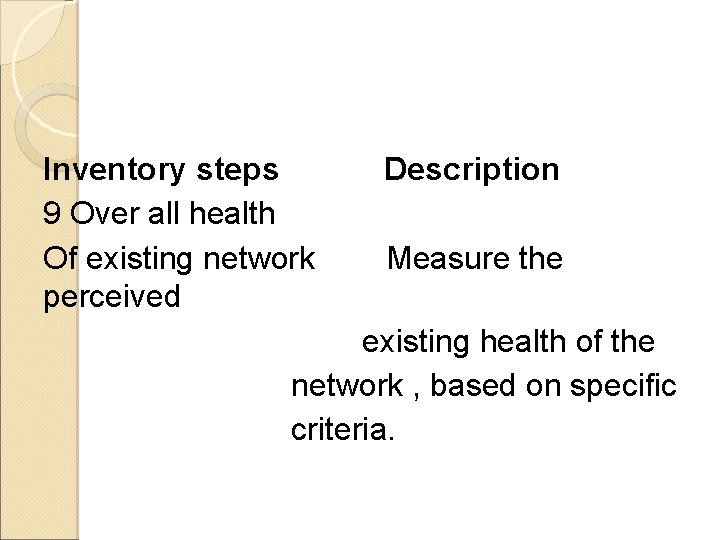
Inventory steps 9 Over all health Of existing network perceived Description Measure the existing health of the network , based on specific criteria.

Requirement categories Requirement are classified into three different categories, they are as follows Business Requirements Security Requirements Manageability Requirements

Business Requirements Business requirements includes the following items. Timeline Staffing Training Budgets and Project approval

Security Requirements Security requirements are very critical to most business, it includes the following. Who can access the network? Each resource. What can be accessed and when? Determine the appropriate security level for the resources and network you are trying to protect.

Manageability Requirements can vary across the board from simple PING program documentation that each device in the network is alive to full blown network management system.

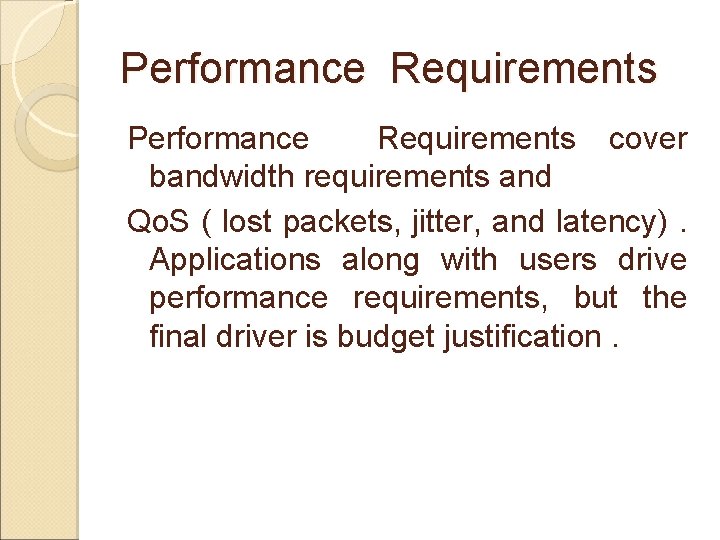
Performance Requirements cover bandwidth requirements and Qo. S ( lost packets, jitter, and latency). Applications along with users drive performance requirements, but the final driver is budget justification.

Traffic sizing Traffic comes in many sizes in many shapes and sizes. Which is having many protocols and formats. It travels in many types and patterns. It requires special methods of processing and handling. The traffic is measured in two common formats ◦ 1. Units of measure and ◦ 2. Packaging of these units 1. Units of measure means, bits, bytes message block. 2. Packaging of these units means, file, packets, frames or cell.

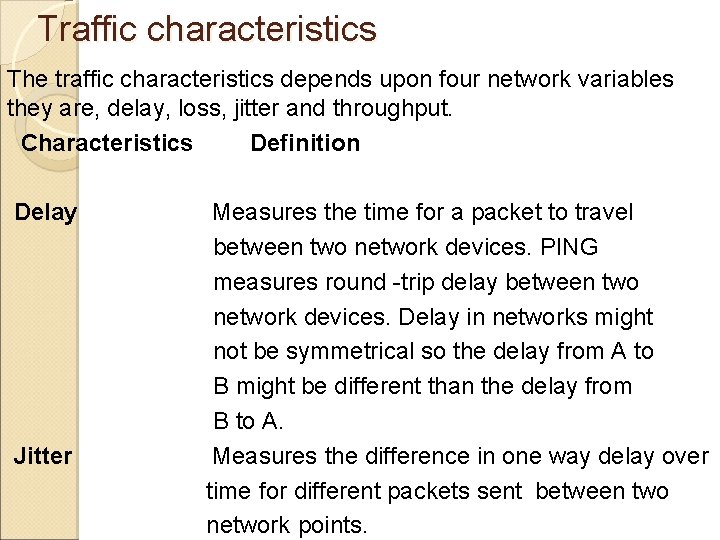
Traffic characteristics The traffic characteristics depends upon four network variables they are, delay, loss, jitter and throughput. Characteristics Definition Delay Jitter Measures the time for a packet to travel between two network devices. PING measures round -trip delay between two network devices. Delay in networks might not be symmetrical so the delay from A to B might be different than the delay from B to A. Measures the difference in one way delay over time for different packets sent between two network points.

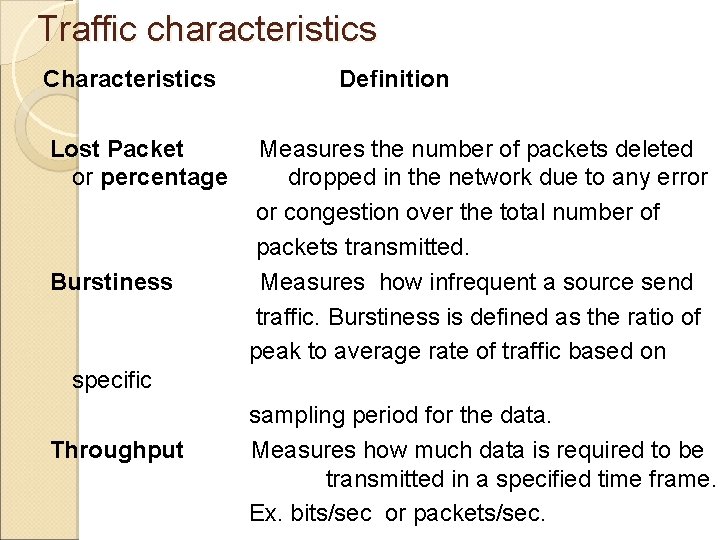
Traffic characteristics Characteristics Lost Packet or percentage Burstiness Definition Measures the number of packets deleted dropped in the network due to any error or congestion over the total number of packets transmitted. Measures how infrequent a source send traffic. Burstiness is defined as the ratio of peak to average rate of traffic based on specific Throughput sampling period for the data. Measures how much data is required to be transmitted in a specified time frame. Ex. bits/sec or packets/sec.

Protocol The full suit of user protocols must be defined for both existing and planned applications. This include all protocols serving all seven layers of OSI reference model Which protocol is used on both side the application side and the network side. This is because the network devices like routers, switches or bridges heavily depends on protocols.

Time and Delay considerations is most important aspects of data communications networking and How applications and protocols manage delay. Response time : It is defined as the round trip delay from source to destination, or the time required it takes a user to send a request until he or she receives a reply.

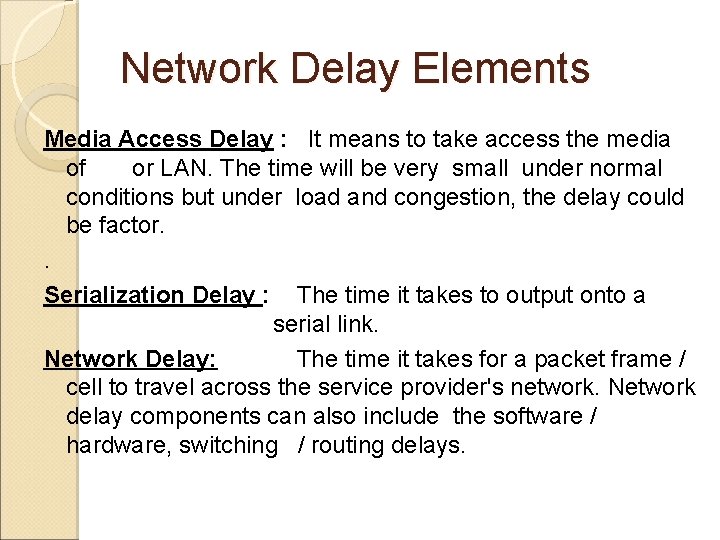
Time and Delay considerations There are three elements of delay. ◦ Media access delay ◦ Serialization delay ◦ Network delay They are explained in the picture on next slide.

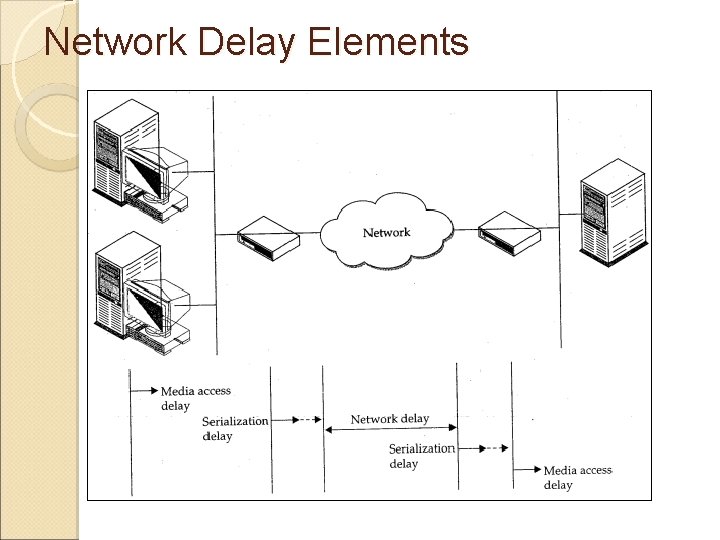
Network Delay Elements

Network Delay Elements Media Access Delay : It means to take access the media of or LAN. The time will be very small under normal conditions but under load and congestion, the delay could be factor. . Serialization Delay : The time it takes to output onto a serial link. Network Delay: The time it takes for a packet frame / cell to travel across the service provider's network. Network delay components can also include the software / hardware, switching / routing delays.

Connectivity User connectivity will be defined by existing or available connectivity methods. For, example some remote locations might have only dial, x. DSL, or cable access.

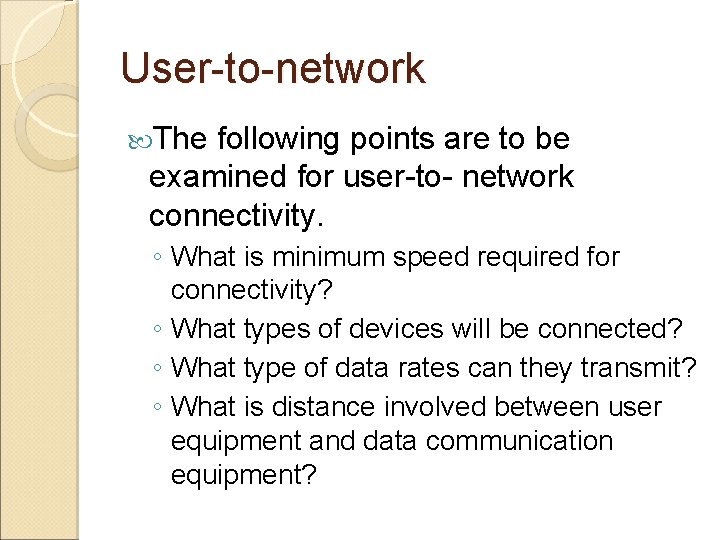
User-to-network The following points are to be examined for user-to- network connectivity. ◦ What is minimum speed required for connectivity? ◦ What types of devices will be connected? ◦ What type of data rates can they transmit? ◦ What is distance involved between user equipment and data communication equipment?

◦ What are the vendors software and hardware vendor specifics? ◦ What mode of addressing is required for access? ◦ What are protocols required for basic connectivity?

NETWORK-TO-NETWORK CONNECTIVITY Once the user-to-network interface has been defined, any network-tonetwork connectivity requirements for new or existing networks can also be defined To what extent is everywhere connectivity required? Will the connectivity be homogenous or heterogeneous? Will private, public or hybrid network access be required? What type of technology will be used for network interfaces and internetworking? Some examples are: Multipoint or point-to-point. Multiplexing or concentration Switched (Circuit, Packet or Cell) Bridge or routed Hybrid.

SERVICE ASPECTS Service aspects such as network management, billing, security, user support and disaster recovery are important topic with range of standard and proprietary solutions. Network designer must understand the capabilities offered by each technology and protocol.

BUDGET CONSTRAINTS It means the limitations of budget: The designer must design the network within a given budget, accommodating the largest number of users and applications within the available budget. This becomes a balance between cost, capabilities and connectivity. A network becomes cost justified if it improves operating efficiency, helps users meet corporate objectives. There are two things who controls the network budget, the network manager and the users, but most often it is the network manager. When user have budgetary control the question is, what is placed on the network? When network manager has control and the user is a customer, the user tries to place everything possible over the network.

VIDEOS https: //www. youtube. com/watch? v=qp. Kg. VTCm 06 c