Chapter 4 PRIVACY PRIVACY PROTECTION THE LAW n
























- Slides: 26

Chapter 4 PRIVACY

PRIVACY PROTECTION & THE LAW n Information about people is gathered, stored, analyzed and reported because organizations can use it to make better decisions. - n Job hiring, approve a loan, offer a scholarship Knowing consumers purchasing habits and financial condition. - Know who will buy their products and services

n n Adoption of the United States Constitution – 1789 Several amendments where made, 10 of this where known as the Bill of Right n 4 th amendment states: The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized. n The US supreme court has ruled that the

n Privacy Protection Study Commission noted in 1977 n “The real danger is the gradual erosion of individual liberties through the automation, integration, and interconnection of many small, separate record-keeping systems, each of which alone may seen innocuous, even benevolent, and wholly justifiable.

INFORMATION PRIVACY Information privacy is the combination of communications privacy ( the ability to communicate with others without those communications being monitors by other persons or organizations) and data privacy (the ability to limit access to one’s personal data by other individuals and organizations in order to exercise a substantial degree of control over that data and its use).

PRIVACY LAWS, APPLICATION AND COURT RULINGS Financial data n Health Information n Children’s personal data n Electronic surveillance n Export of Personal data n Access to government records n

FINANCIAL DATA n Financial products and services, including credit cards, savings and checking accounts, loans, payroll direct deposit and brokerage accounts n • To access this financial products – logon name, password, account number or PIN - high risk of loss of privacy and potential financial loss Fair Credit Reporting Act of 1970 regulates the operations of credit-reporting bureaus, including how to collect, store and use credit information. - an act designed to promote accuracy, fairness, and privacy of information in the files of credit-reporting companies.

HEALTH INFORMATION n The use of electronic medical records and the subsequent interlinking and transferring of this electronic information * Health Insurance Portability and Accountability Act of 1996 was designed to improve the portability and continuity of health insurance coverage; to reduce fraud, waste, and abuse in health insurance and healthcare delivery; and to simplify the administration of health insurance.

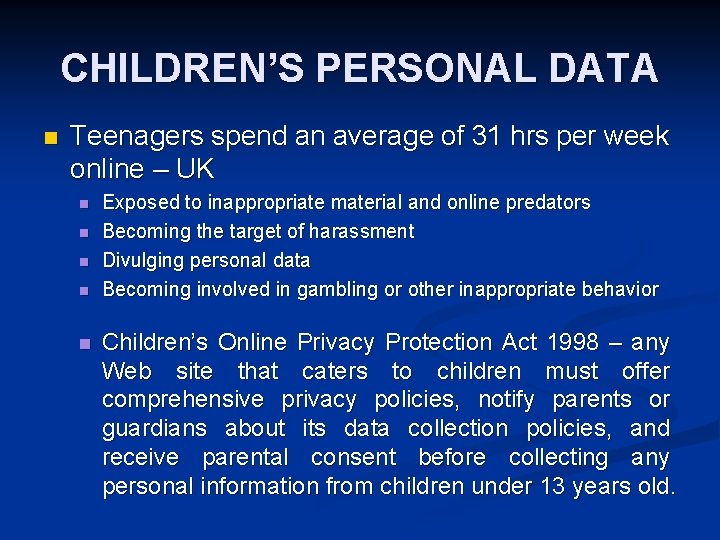
CHILDREN’S PERSONAL DATA n Teenagers spend an average of 31 hrs per week online – UK n n n Exposed to inappropriate material and online predators Becoming the target of harassment Divulging personal data Becoming involved in gambling or other inappropriate behavior Children’s Online Privacy Protection Act 1998 – any Web site that caters to children must offer comprehensive privacy policies, notify parents or guardians about its data collection policies, and receive parental consent before collecting any personal information from children under 13 years old.

ELECTRONIC SURVEILLANCE n Government surveillance, including other forms of electronic surveillance. n • • Reaction of worldwide terrorist activities and the development of new communication technologies Communications Act of 1934 – regulating all nonfederal government use of radio and television broadcasting and all international communications that originate or terminate in the United States. The act also restricted the government’s ability to secretly intercept communications. Title III of the Omnibus Crime Control and Safe Streets Act – Wiretap Act, regulates the interception of wire (telephone) and oral communications. It allows state and federal law enforcement officials to use wiretapping and electronic eavesdropping, but only under strict limitaitons.

* Foreign intelligence Surveillance Act 1978 – describes procedures for the electronic surveillance and collection of foreign intelligence information in communications between foreign powers and the agents of foreign powers. Foreign intelligence is information relating to the capabilities, intentions, or activities of foreign governments or agents of foreign governments or foreign organizations.

* The Electronic Communications Privacy Act of 1986 - The protection of communications while in transfer from sender to receiver - The protection of communications held in electronic storage - The prohibition of devices to record dialing, routing, addressing, and signaling information without a search warrant Pen registry – a device that records electronic impulses to identify the numbers dialed for outgoing calls Trap and trace – a device that records the originating number of incoming calls for

The USA Patriot Act (Uniting And Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism) 0 f 2001 - it was passed after the September 11, 2001 terrorist attacks. - It gave sweeping new powers both to domestic law enforcement and international intelligence agencies, including increasing the ability of law enforcement agencies to search telephone, email, medical, financial, and other records. - It was passed into law in just 5 weeks after it was introduced.

EXPORT OF PERSONAL DATA • Organization for Economic Co-operation and Development Fair Information Practices 1980 – its goal is to set policy and come to agreement on topics for which multilateral consensus, and peer pressure are essential to make these policies and agreements stick. • The 1980 privacy guidelines is also know as Fair Information Practices

ACCESS TO GOVERNMENT RECORDS n The Freedom of Information Act (FOIA) 1966, amended 1974 – enables the public to gain access to certain government records n The Privacy Act – prohibits the government from concealing the existence of any personal data record-keeping systems.

CURRENT AND IMPORATNT PRIVACY ISSUES Identity theft occurs when someone steals key pieces of personal information to impersonate a person. (name, address, date of birth, social security number, mother’s maiden name) - apply for a new credit card, rent an apartment, set up utility or phone service, and register for college course – all in someone else’s name.

DATA BREACHES Identity theft involves breaches of large databases to gain personal information. n It may be caused by hackers breaking into the database or more often than one would suspect, by carelessness or failure to follow proper security procedures. Ex. A laptop computer containing the encrypted SSS number of 26. 5 million U. S. veterans was stolen from home of a Veterans Affairs analyst. n

PURCHASE OF PERSONAL DATA Phishing is the attempt to steal personal identity data by tricking users into entering information on a counterfeit Web site. Spyware is keystroke-logging software downloaded to user’s computer without the knowledge or consent of the user. - - Also called spouse monitor, child monitor or surveillance tool It creates a record of the keystrokes entered on the computer, enabling the capture of account usernames, password and credit card numbers and other sensitive information It can view the Web sites visited as well as transcript of chat logs

CONSUMER PROFILING Companies openly collect personal information about internet users through: registering at Web sites, complete surveys, fill out forms, enter contest online Companies obtain information through the use of cookies, text files that a Web sit can download to visitor’s hard drives so that it can identify visitors on subsequent visits. Companies also use tracking software to allow their Web site to analyze browsing habits and deduce personal interest and preferences. - Personal information about the consumer may be sold or shared with third parties.

Collecting Data from Web Site Visits - Marketers use cookies to recognize return visitors tot heir sites and store useful information about them. - Cookies allow marketers to collect clickstream data – information gathered by monitoring a consumer’s online activity.

Personalization Software - use to optimize the number, frequency, and mixture of their ad placements, and to evaluate how visitors react to new ads. Types of personalization software a. Rules-based personalization software Uses business rules tied to customer-supplied preferences or on-line behavior to determine the most appropriate page views and product information to display when a user visit a web site. Ex. If you use a Web site to book airline tickets to a popular vacation spots, might ensure that you are shown ads for rental cars.

b. Collaborative filtering Offers consumer recommendations based on the types of products purchased by other people with similar buying habits. Ex. If you bought a book by Dean Koontz, a company may recommend Stephen King books to you, based on the fact that a significant percentage of other customers bought books by both authors. c. Demographic filtering It augments click-stream data and usersupplied data with demographic information associated with user zip codes to make product suggestions. Ex. you read a story about white-water rafting, you may be offered a

Consumer Data Privacy - Personal data is being gathered and sold to other companies without the permission of consumers who provide the data. Platform for Privacy Preferences (P 3 P) is a screening technology which helps shield the users from sites that do not provide the level of privacy protection they desire. * The World Wide Web Consortium – an international industry group whose member include Apple, Ericson and Microsoft – created P 3 P and is supporting its development.

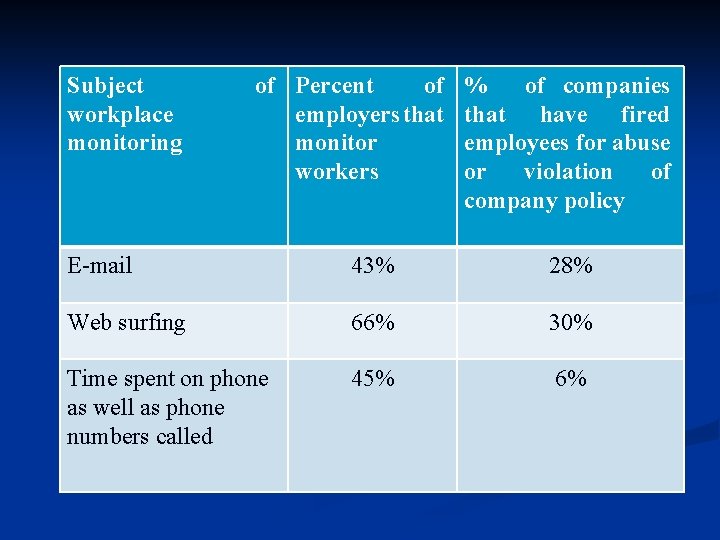
WORKPLACE MONITORING Companies have developed a policy on the use of IT in the workplace in order to protect against employee abuses that reduce worker productivity or expose the employer to harassment lawsuits.

Subject workplace monitoring of Percent of employers that monitor workers % of companies that have fired employees for abuse or violation of company policy E-mail 43% 28% Web surfing 66% 30% Time spent on phone as well as phone numbers called 45% 6%

ADVANCED SURVEILLANCE TECHNOLOGY n n n Surveillance camera - Smart Surveillance system – singles out people who are acting suspiciously is under development in Australia Facial recognition software - to help identify criminal suspects, with mixed results Global Positioning System (GPS) Chips - Are being placed in many devices to precisely locate users.