Chapter 4 Network Layer Chapter 4 Network Layer
































- Slides: 92

Chapter 4 Network Layer

Chapter 4: Network Layer Chapter goals: r understand principles behind network layer services: m network layer service models m forwarding versus routing m how a router works m routing (path selection) m dealing with scale m IPv 4 and IPv 6

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

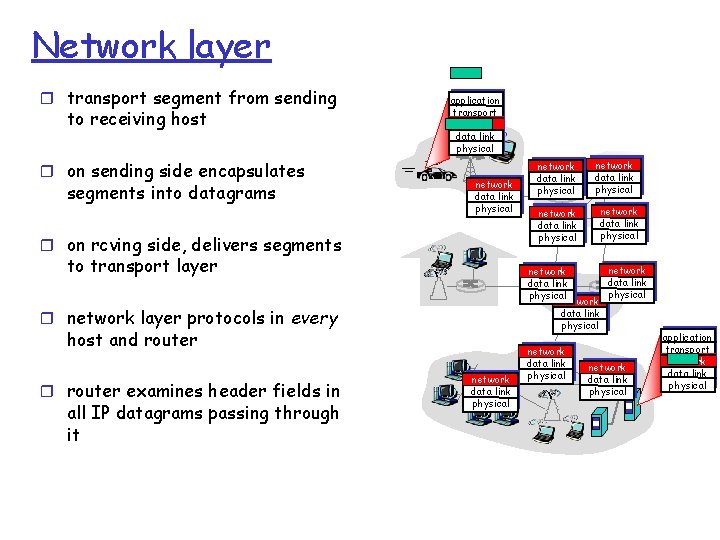
Network layer r transport segment from sending to receiving host r on sending side encapsulates segments into datagrams application transport network data link physical r on rcving side, delivers segments to transport layer host and router all IP datagrams passing through it network data link physical network data link physical r network layer protocols in every r router examines header fields in network data link physical application transport network data link physical

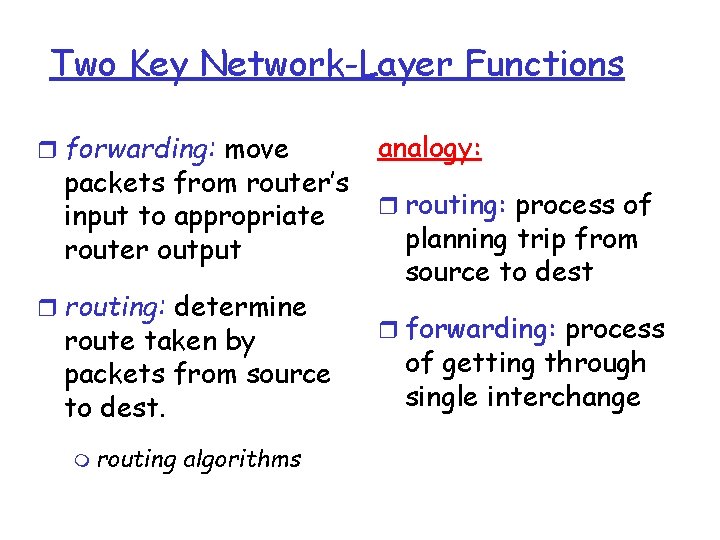
Two Key Network-Layer Functions r forwarding: move packets from router’s input to appropriate router output r routing: determine route taken by packets from source to dest. m routing algorithms analogy: r routing: process of planning trip from source to dest r forwarding: process of getting through single interchange

Interplay between routing and forwarding routing algorithm local forwarding table header value output link 0100 0101 0111 1001 3 2 2 1 value in arriving packet’s header 0111 1 3 2

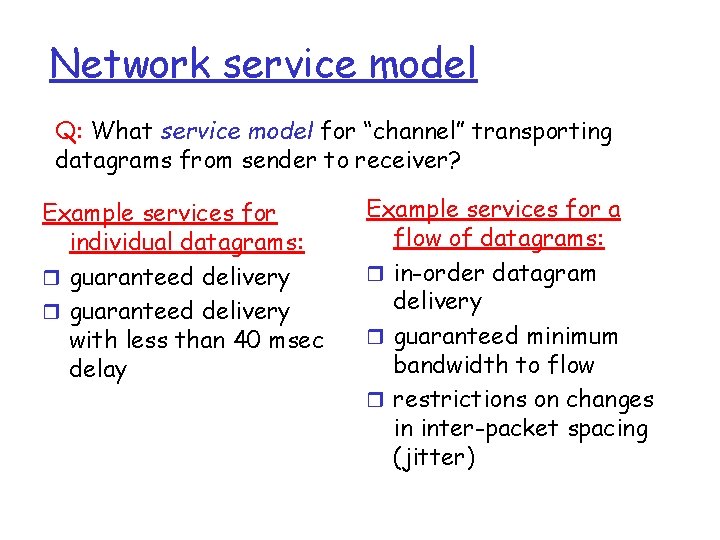
Network service model Q: What service model for “channel” transporting datagrams from sender to receiver? Example services for individual datagrams: r guaranteed delivery with less than 40 msec delay Example services for a flow of datagrams: r in-order datagram delivery r guaranteed minimum bandwidth to flow r restrictions on changes in inter-packet spacing (jitter)

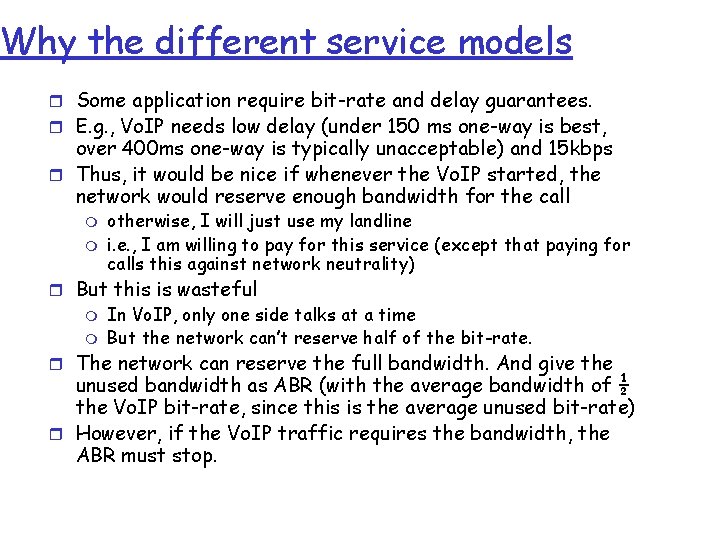
Network layer service models: Network Architecture Internet Service Model Guarantees ? Congestion Bandwidth Loss Order Timing feedback best effort none ATM CBR ATM VBR ATM ABR ATM UBR constant rate guaranteed minimum none no no no yes yes yes no no (inferred via loss) no congestion yes no no CBR = constant bit-rate (phone, not Vo. IP) VBR = variable bit-rate (e. g. , variable bit-rate video, audio) ABR = available bit-rate. Like best effort but with guaranteed minimum bit-rate, but it gets feedback from the network to adjust the sending rate UBR = unspecified bit-rate. Like best effort

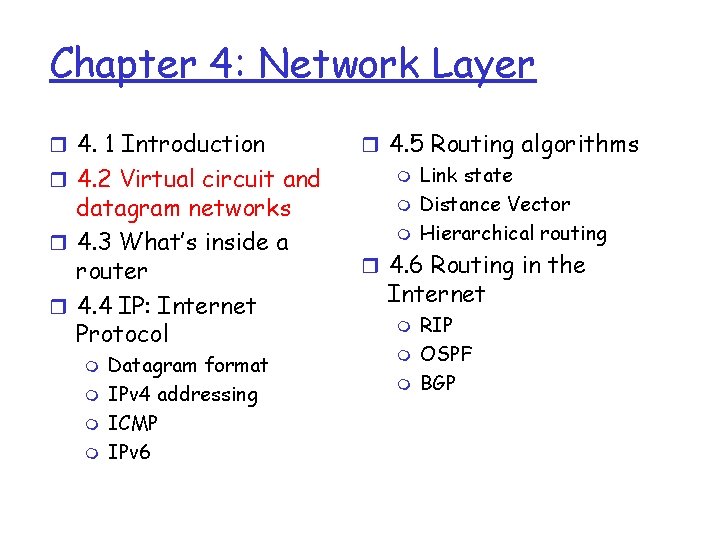
Why the different service models r Some application require bit-rate and delay guarantees. r E. g. , Vo. IP needs low delay (under 150 ms one-way is best, over 400 ms one-way is typically unacceptable) and 15 kbps r Thus, it would be nice if whenever the Vo. IP started, the network would reserve enough bandwidth for the call m m otherwise, I will just use my landline i. e. , I am willing to pay for this service (except that paying for calls this against network neutrality) r But this is wasteful m In Vo. IP, only one side talks at a time m But the network can’t reserve half of the bit-rate. r The network can reserve the full bandwidth. And give the unused bandwidth as ABR (with the average bandwidth of ½ the Vo. IP bit-rate, since this is the average unused bit-rate) r However, if the Vo. IP traffic requires the bandwidth, the ABR must stop.

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

Network layer connection and connection-less service r datagram network provides network-layer connectionless service r VC network provides network-layer connection service

Virtual circuits “source-to-dest path behaves much like telephone circuit” m m performance-wise network actions along source-to-dest path r call setup, teardown for each call before data can flow r each packet carries VC identifier (not destination host address) r every router on source-dest path maintains “state” for each passing connection r link, router resources (bandwidth, buffers) may be allocated to VC (dedicated resources = predictable service)

VC implementation a VC consists of: 1. 2. 3. path from source to destination VC numbers entries in forwarding tables in routers along path q A packet belonging to VC carries VC number (rather than dest address) q However, it is difficult to ensure that the VC number is unique across the network q Instead, the VC number is changed at each link

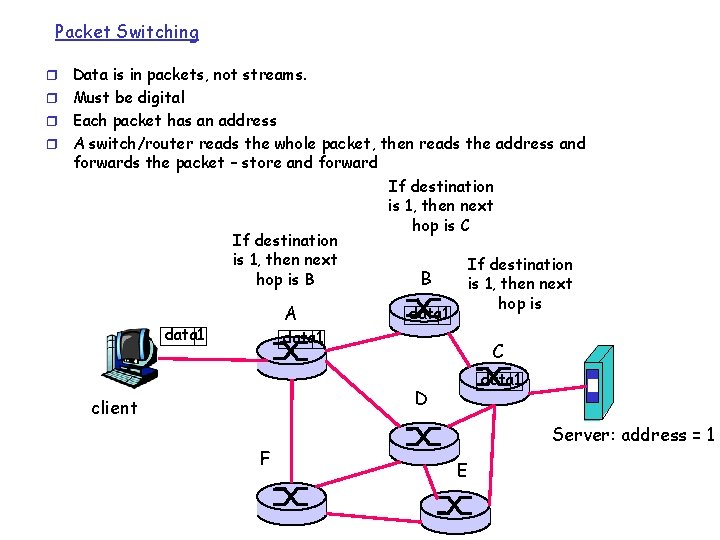
Packet Switching Data is in packets, not streams. r Must be digital r Each packet has an address r A switch/router reads the whole packet, then reads the address and forwards the packet – store and forward If destination is 1, then next hop is C If destination is 1, then next If destination hop is B B is 1, then next hop is data 1 A data 1 r C data 1 D client F Server: address = 1 E

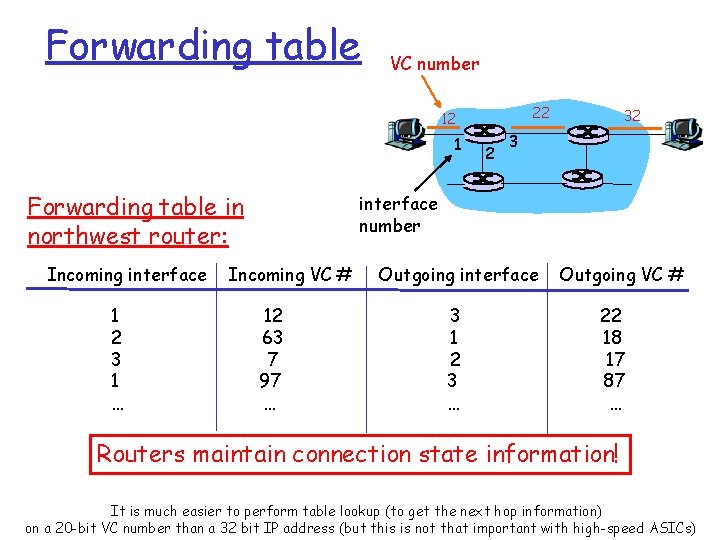
Forwarding table VC number 22 12 1 Forwarding table in northwest router: Incoming interface 1 2 3 1 … 2 32 3 interface number Incoming VC # 12 63 7 97 … Outgoing interface 3 1 2 3 … Outgoing VC # 22 18 17 87 … Routers maintain connection state information! It is much easier to perform table lookup (to get the next hop information) on a 20 -bit VC number than a 32 bit IP address (but this is not that important with high-speed ASICs)

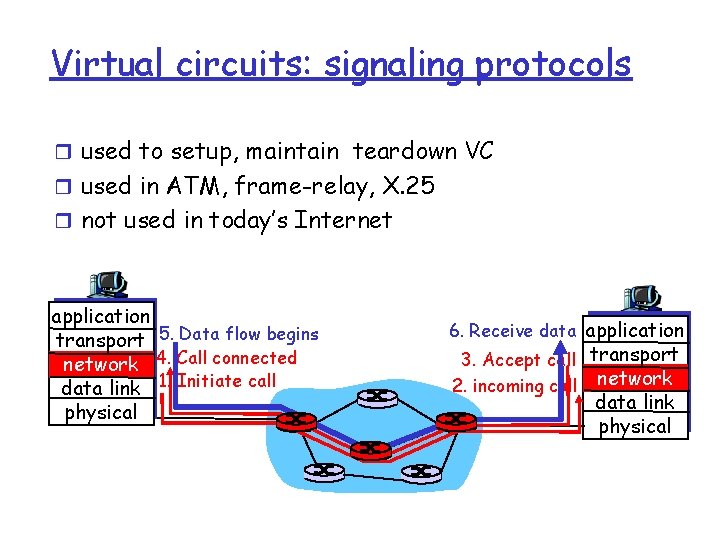
Virtual circuits: signaling protocols r used to setup, maintain teardown VC r used in ATM, frame-relay, X. 25 r not used in today’s Internet application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical 6. Receive data application 3. Accept call transport 2. incoming call network data link physical

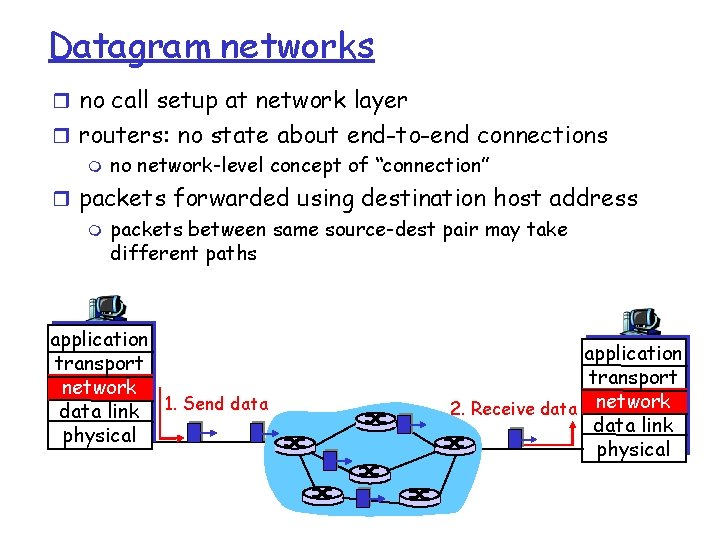
Datagram networks r no call setup at network layer r routers: no state about end-to-end connections m no network-level concept of “connection” r packets forwarded using destination host address m packets between same source-dest pair may take different paths application transport network data link 1. Send data physical application transport 2. Receive data network data link physical

MPLS (Multiprotocol Label Switching) r MPLS is widely used in large ISPs (e. g. , AT&T) r MPLS is a compromise between IP and VC. r MPLS can run over an IP network. r Today, most routers support MPLS and IP at the same time r MPLS uses label switching, which the same idea as VC number m m m Packets have a 20 -bit label When a packet arrives on an interface, the a table lookup is performed, the output interface is found, next label is found, and the current label is changed to the next label Label lookup is faster than IP address lookup. But speed isn’t really a concern

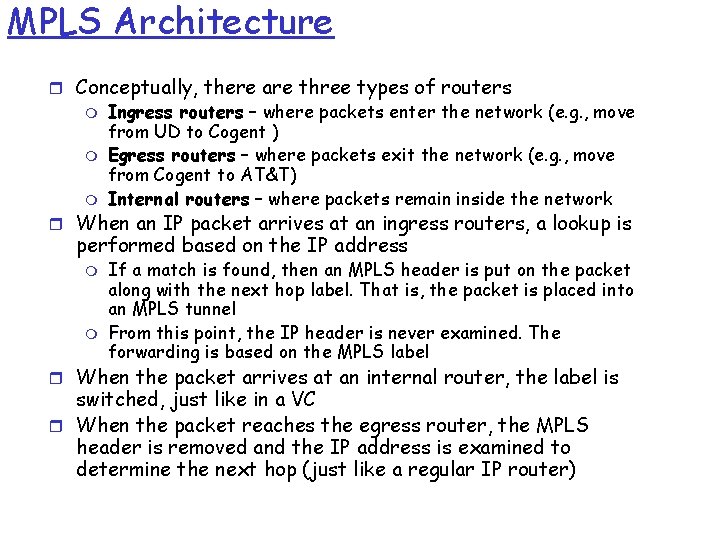
MPLS Architecture r Conceptually, there are three types of routers m Ingress routers – where packets enter the network (e. g. , move from UD to Cogent ) m Egress routers – where packets exit the network (e. g. , move from Cogent to AT&T) m Internal routers – where packets remain inside the network r When an IP packet arrives at an ingress routers, a lookup is performed based on the IP address m m If a match is found, then an MPLS header is put on the packet along with the next hop label. That is, the packet is placed into an MPLS tunnel From this point, the IP header is never examined. The forwarding is based on the MPLS label r When the packet arrives at an internal router, the label is switched, just like in a VC r When the packet reaches the egress router, the MPLS header is removed and the IP address is examined to determine the next hop (just like a regular IP router)

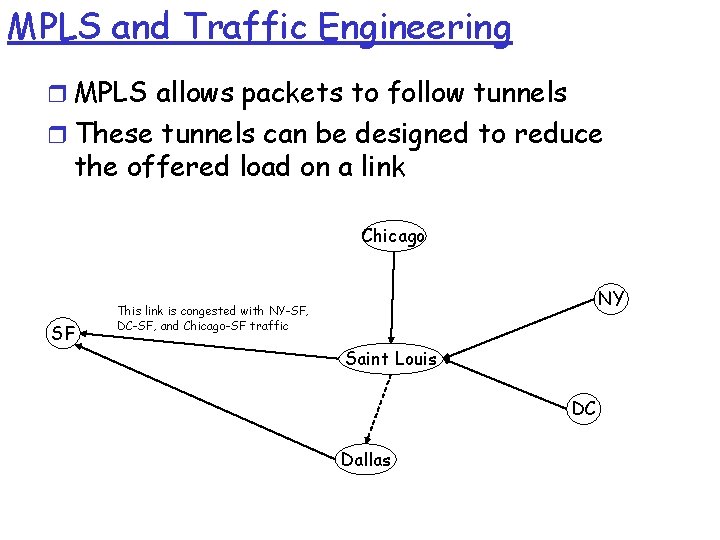
MPLS and Traffic Engineering r MPLS allows packets to follow tunnels r These tunnels can be designed to reduce the offered load on a link Chicago SF NY This link is congested with NY-SF, DC-SF, and Chicago-SF traffic Saint Louis DC Dallas

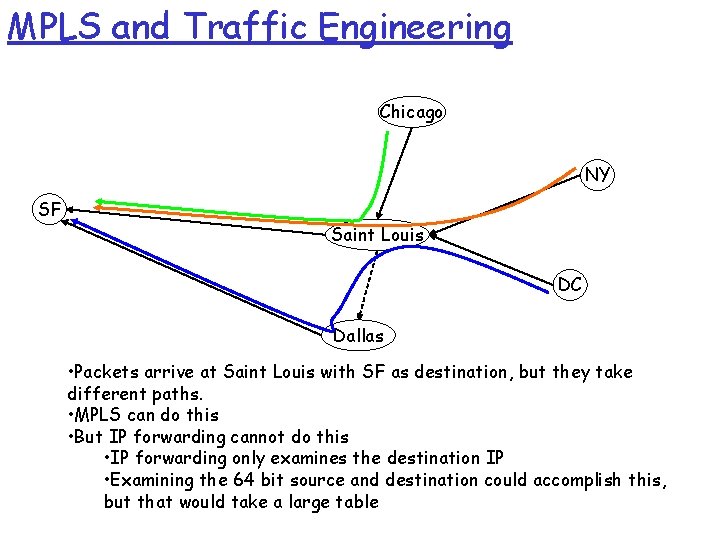
MPLS and Traffic Engineering Chicago NY SF Saint Louis DC Dallas • Packets arrive at Saint Louis with SF as destination, but they take different paths. • MPLS can do this • But IP forwarding cannot do this • IP forwarding only examines the destination IP • Examining the 64 bit source and destination could accomplish this, but that would take a large table

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

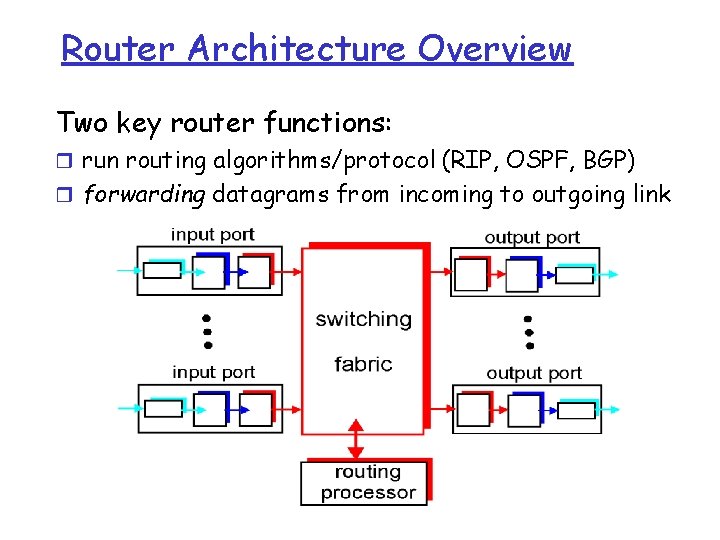
Router Architecture Overview Two key router functions: r run routing algorithms/protocol (RIP, OSPF, BGP) r forwarding datagrams from incoming to outgoing link

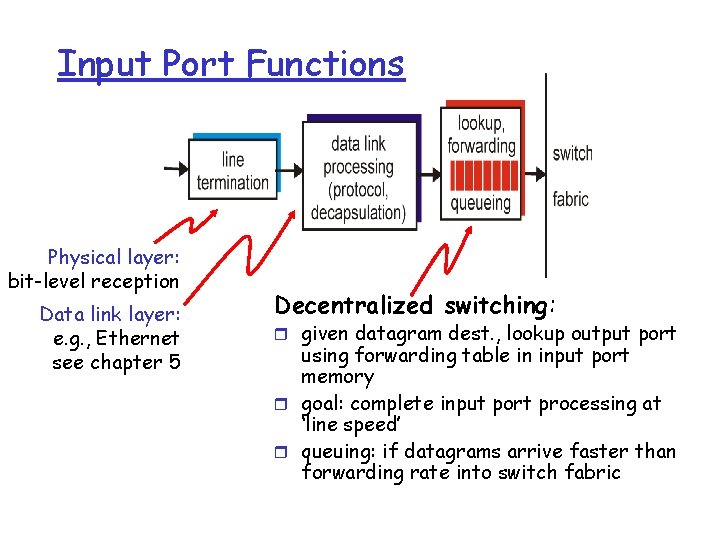
Input Port Functions Physical layer: bit-level reception Data link layer: e. g. , Ethernet see chapter 5 Decentralized switching: r given datagram dest. , lookup output port using forwarding table in input port memory r goal: complete input port processing at ‘line speed’ r queuing: if datagrams arrive faster than forwarding rate into switch fabric

Three types of switching fabrics

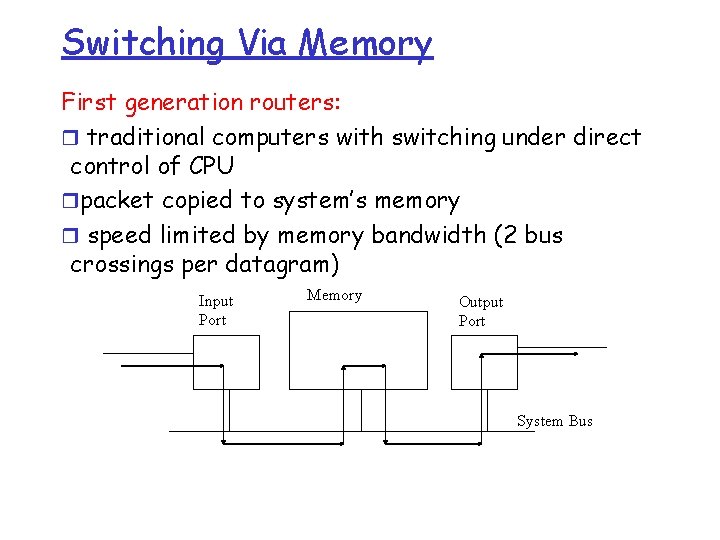
Switching Via Memory First generation routers: r traditional computers with switching under direct control of CPU rpacket copied to system’s memory r speed limited by memory bandwidth (2 bus crossings per datagram) Input Port Memory Output Port System Bus

Switching Via a Bus r datagram from input port memory to output port memory via a shared bus r bus contention: switching speed limited by bus bandwidth r 32 Gbps bus, Cisco 5600: sufficient speed for access and enterprise routers

Switching Via An Interconnection Network r overcome bus bandwidth limitations r Banyan networks, other interconnection nets initially developed to connect processors in multiprocessor r advanced design: fragmenting datagram into fixed length cells, switch cells through the fabric. r Cisco 12000: switches 60 Gbps through the interconnection network

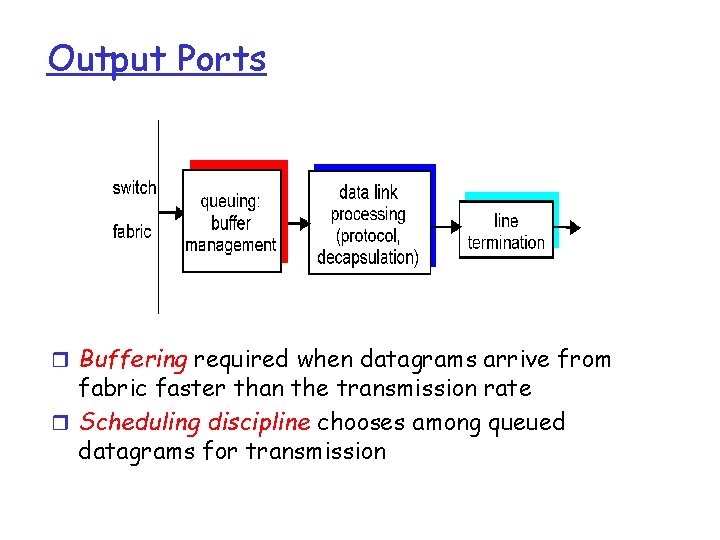
Output Ports r Buffering required when datagrams arrive from fabric faster than the transmission rate r Scheduling discipline chooses among queued datagrams for transmission

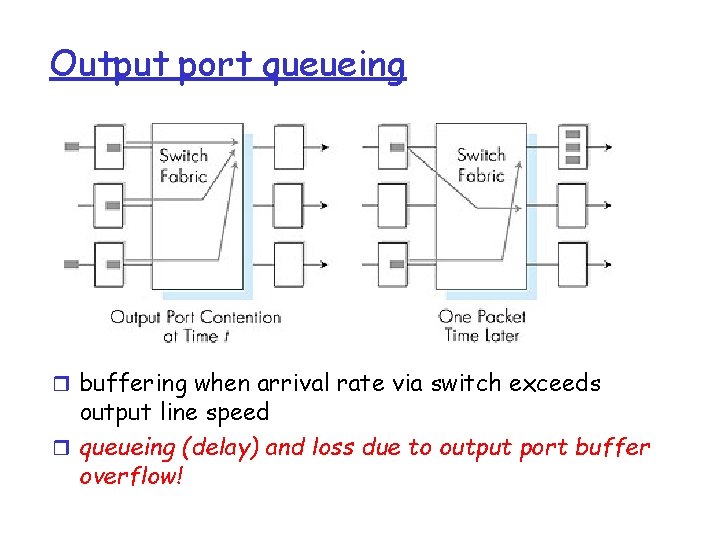
Output port queueing r buffering when arrival rate via switch exceeds output line speed r queueing (delay) and loss due to output port buffer overflow!

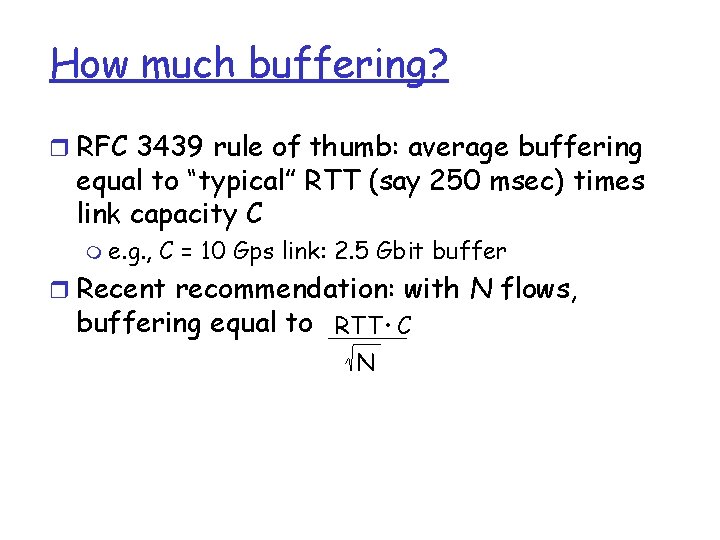
How much buffering? r RFC 3439 rule of thumb: average buffering equal to “typical” RTT (say 250 msec) times link capacity C m e. g. , C = 10 Gps link: 2. 5 Gbit buffer r Recent recommendation: with N flows, buffering equal to RTT. C N

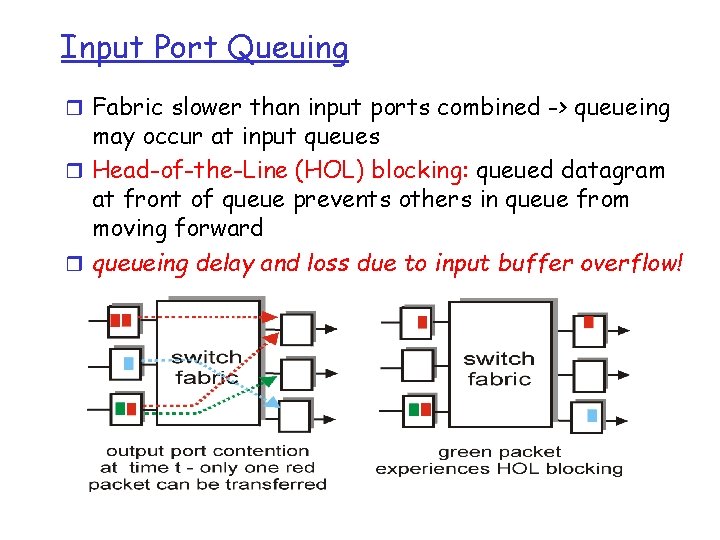
Input Port Queuing r Fabric slower than input ports combined -> queueing may occur at input queues r Head-of-the-Line (HOL) blocking: queued datagram at front of queue prevents others in queue from moving forward r queueing delay and loss due to input buffer overflow!

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

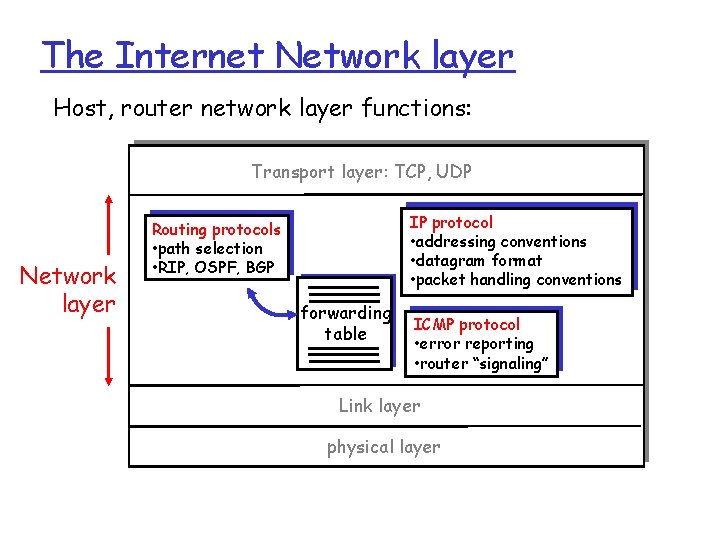
The Internet Network layer Host, router network layer functions: Transport layer: TCP, UDP Network layer IP protocol • addressing conventions • datagram format • packet handling conventions Routing protocols • path selection • RIP, OSPF, BGP forwarding table ICMP protocol • error reporting • router “signaling” Link layer physical layer

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

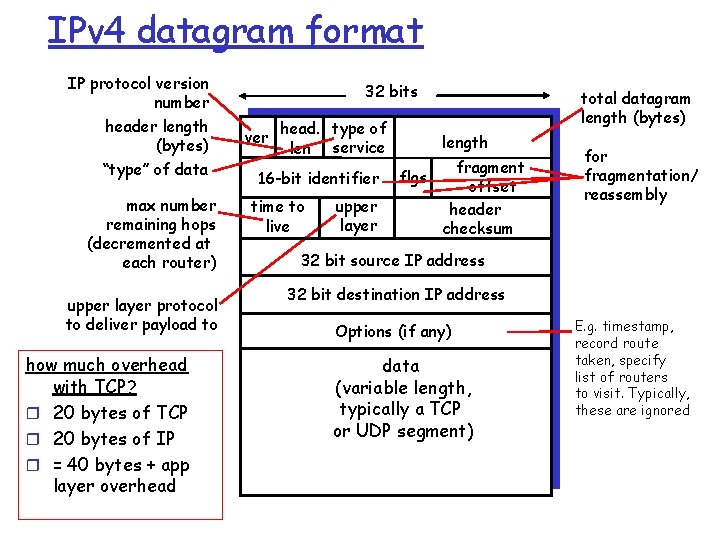
IPv 4 datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to how much overhead with TCP? r 20 bytes of TCP r 20 bytes of IP r = 40 bytes + app layer overhead 32 bits ver head. type of len service 16 -bit identifier time to live upper layer total datagram length (bytes) length fragment flgs offset header checksum for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) E. g. timestamp, record route taken, specify list of routers to visit. Typically, these are ignored

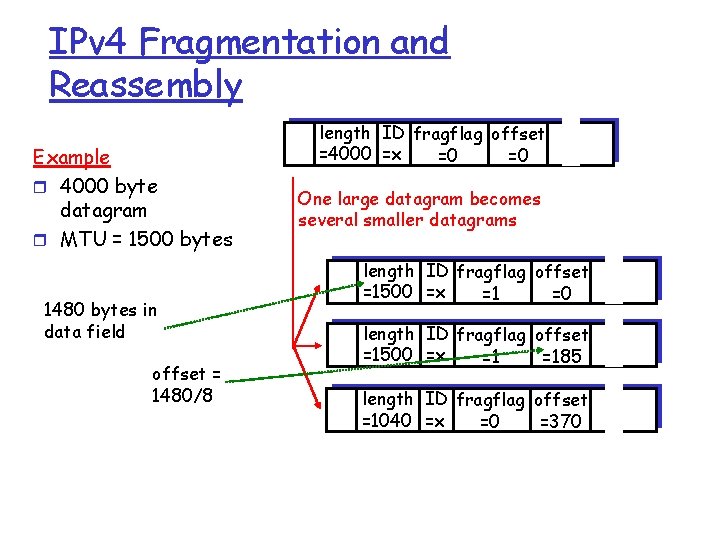
IPv 4 Fragmentation & Reassembly r r network links have MTU (max. transfer size) - largest possible link-level frame. m different link types, different MTUs m E. g. , ethernet allows 1500 B frames m 802. 11 allows 2346 B frames It would be very difficult for the end host to know the correct packet size m r fragmentation: in: one large datagram out: 3 smaller datagrams Note that larger packets are more efficient (less bandwidth is consumed by the header) Large IP datagram divided (“fragmented”) within the network m one datagram becomes several datagrams m “reassembled” only at final destination m IP header bits used to identify, order related fragments reassembly

IPv 4 Fragmentation and Reassembly Example r 4000 byte datagram r MTU = 1500 bytes 1480 bytes in data field offset = 1480/8 length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =185 length ID fragflag offset =1040 =x =0 =370

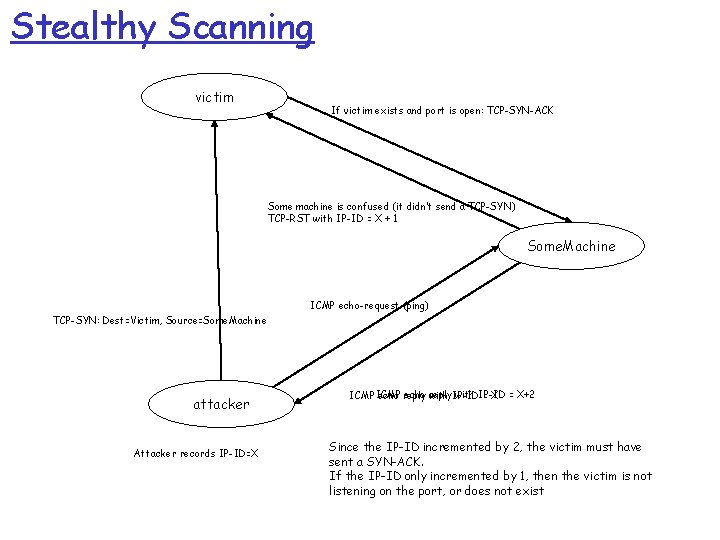
Stealthy Scanning r Before attacking a network, one must learn which hosts are present. m That is, which IP addresses have host that are running various services (e. g. , listening on various TCP ports) r This is done by scanning. For example, sending an ICMP ping message to random IP address or sending TCP-SYN messages m m What happens if a host receives an TCP-SYN on a port that is not listening It depends on the OS, but the typically, a TCP-RST packet is generated r ISPs (e. g. , UD) will look for scanners and take action (e. g. , disconnect them) r So what is an attacker to do?

Stealthy Scanning victim If victim exists and port is open: TCP-SYN-ACK Some machine is confused (it didn’t send a TCP-SYN) TCP-RST with IP-ID = X + 1 Some. Machine ICMP echo-request (ping) TCP-SYN: Dest=Victim, Source=Some. Machine attacker Attacker records IP-ID=X echo reply with IP-ID ICMP echo reply with IP-ID = X+2 Since the IP-ID incremented by 2, the victim must have sent a SYN-ACK. If the IP-ID only incremented by 1, then the victim is not listening on the port, or does not exist

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

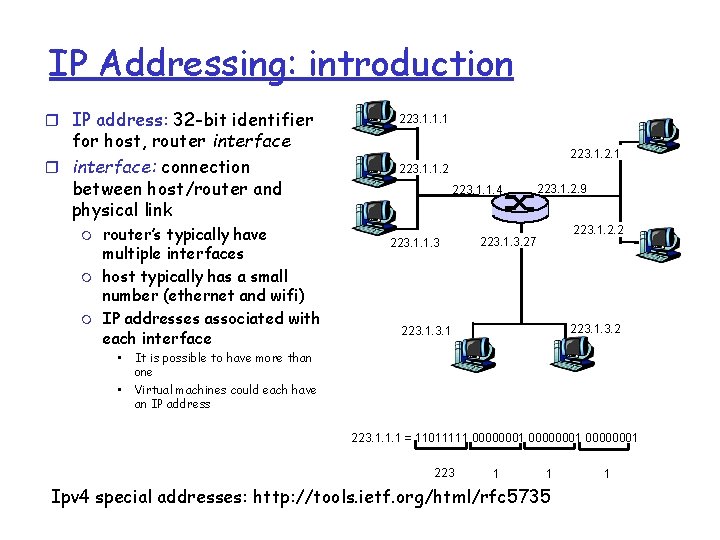
IP Addressing: introduction r IP address: 32 -bit identifier for host, router interface: connection between host/router and physical link m m m router’s typically have multiple interfaces host typically has a small number (ethernet and wifi) IP addresses associated with each interface • • 223. 1. 1. 1 223. 1. 2. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 9 223. 1. 2. 2 223. 1. 3. 27 223. 1. 3. 2 223. 1 It is possible to have more than one Virtual machines could each have an IP address 223. 1. 1. 1 = 11011111 00000001 223 1 1 Ipv 4 special addresses: http: //tools. ietf. org/html/rfc 5735 1

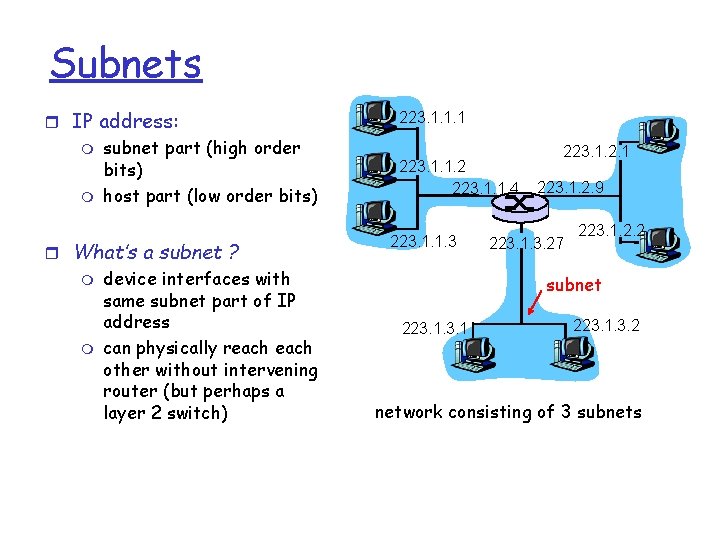
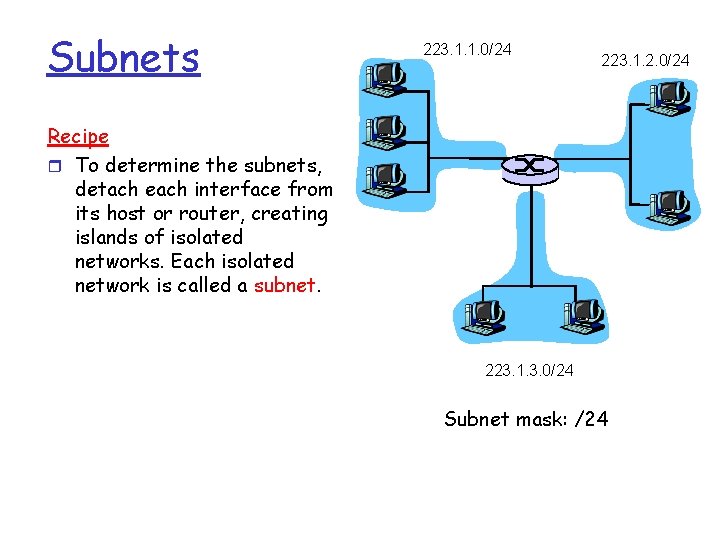
Subnets r IP address: m m subnet part (high order bits) host part (low order bits) r What’s a subnet ? m m device interfaces with same subnet part of IP address can physically reach other without intervening router (but perhaps a layer 2 switch) 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 subnet 223. 1. 3. 2 network consisting of 3 subnets

Subnets 223. 1. 1. 0/24 223. 1. 2. 0/24 Recipe r To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. 223. 1. 3. 0/24 Subnet mask: /24

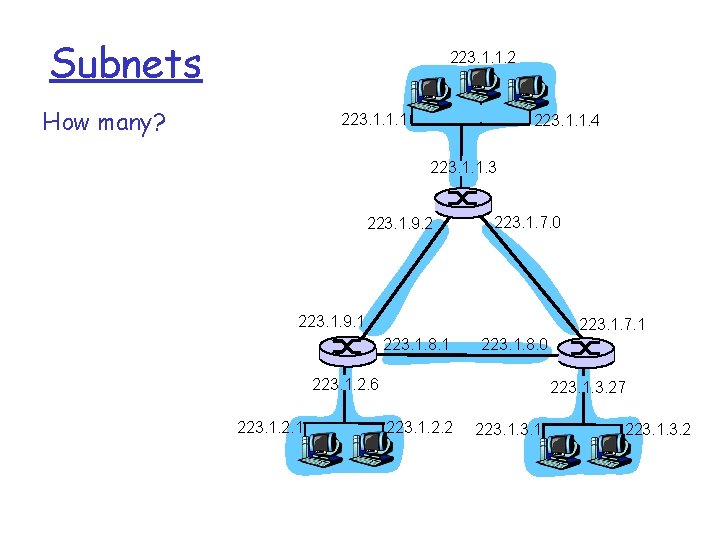
Subnets 223. 1. 1. 2 How many? 223. 1. 1. 1 223. 1. 1. 4 223. 1. 1. 3 223. 1. 9. 2 223. 1. 7. 0 223. 1. 9. 1 223. 1. 7. 1 223. 1. 8. 0 223. 1. 2. 6 223. 1. 2. 1 223. 1. 3. 27 223. 1. 2. 2 223. 1. 3. 2

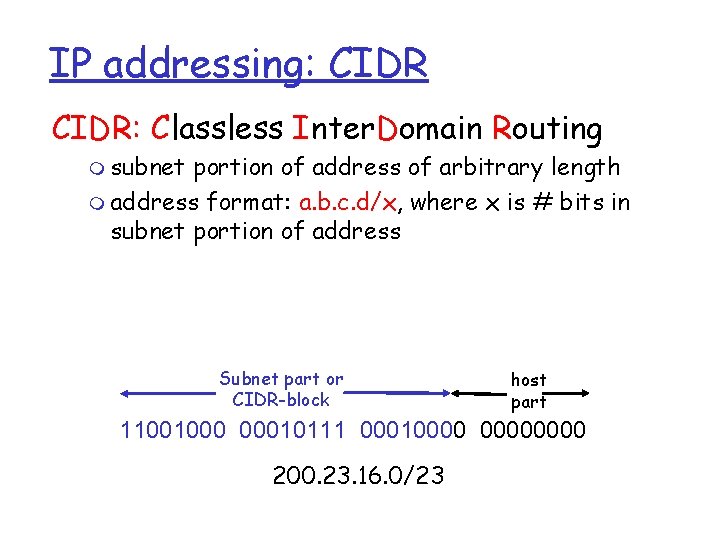
IP addressing: CIDR: Classless Inter. Domain Routing m subnet portion of address of arbitrary length m address format: a. b. c. d/x, where x is # bits in subnet portion of address Subnet part or CIDR-block host part 11001000 00010111 00010000 200. 23. 16. 0/23

IP addresses: how to get one? Q: How does network get subnet part of IP addr? A: gets allocated portion of its provider ISP’s address space ISP's block 11001000 00010111 00010000 200. 23. 16. 0/20 Organization 1 Organization 2. . . 11001000 00010111 00010000 11001000 00010111 00010010 0000 11001000 00010111 00010100 0000 …. 200. 23. 16. 0/23 200. 23. 18. 0/23 200. 23. 20. 0/23 …. Organization 7 11001000 00010111 00011110 0000 200. 23. 30. 0/23

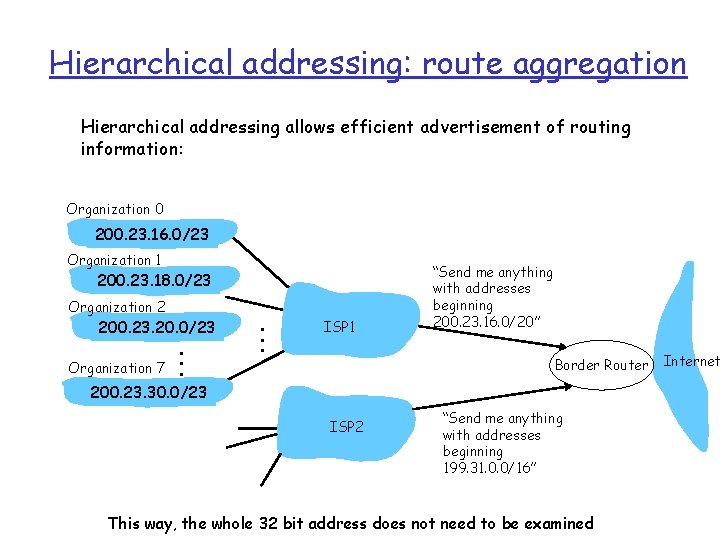
Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . ISP 1 “Send me anything with addresses beginning 200. 23. 16. 0/20” Border Router 200. 23. 30. 0/23 ISP 2 “Send me anything with addresses beginning 199. 31. 0. 0/16” This way, the whole 32 bit address does not need to be examined Internet

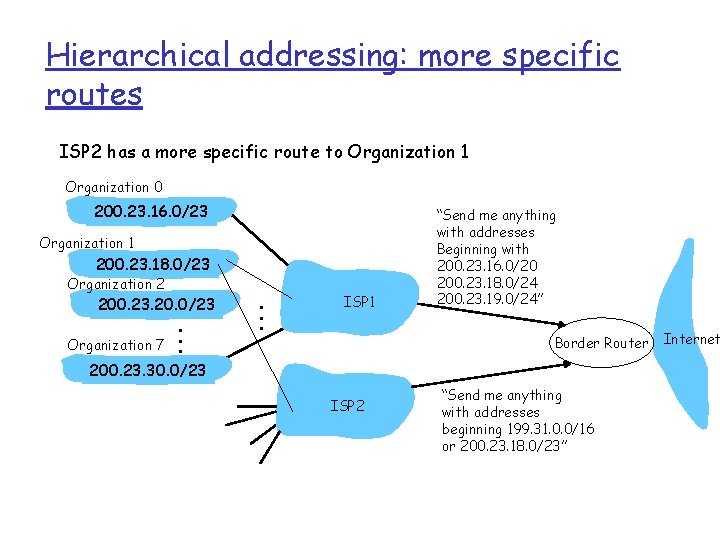
Hierarchical addressing: more specific routes ISP 2 has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . ISP 1 “Send me anything with addresses Beginning with 200. 23. 16. 0/20” Border Router 200. 23. 30. 0/23 ISP 2 Organization 1 200. 23. 18. 0/23 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” Internet

Longest prefix matching Border Router Forwarding Table Prefix Match 200. 23. 16. 0/20 200. 23. 18. 0/23 199. 31. 0. 0/16 otherwise Link Interface 0 1 1 2 If a packet with destination address 200. 23. 18. 12 arrives at the boarder router, then is it forwarding to interface 0 or 1? Since interface 1 has a longer match, it goes to interface 1

Hierarchical addressing: more specific routes ISP 2 has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . ISP 1 “Send me anything with addresses Beginning with 200. 23. 16. 0/20 ” Border Router 200. 23. 30. 0/23 ISP 2 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” Internet

Hierarchical addressing: more specific routes ISP 2 has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . ISP 1 “Send me anything with addresses Beginning with 200. 23. 16. 0/20 200. 23. 18. 0/24 200. 23. 19. 0/24” Border Router 200. 23. 30. 0/23 ISP 2 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” Internet

IP addressing: the last word. . . Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned Names and Numbers m allocates addresses m manages DNS m assigns domain names, resolves disputes m ICANN allocates chunks of addresses to Regional Internet Registry (RIR), which allocate them to organizations in their region

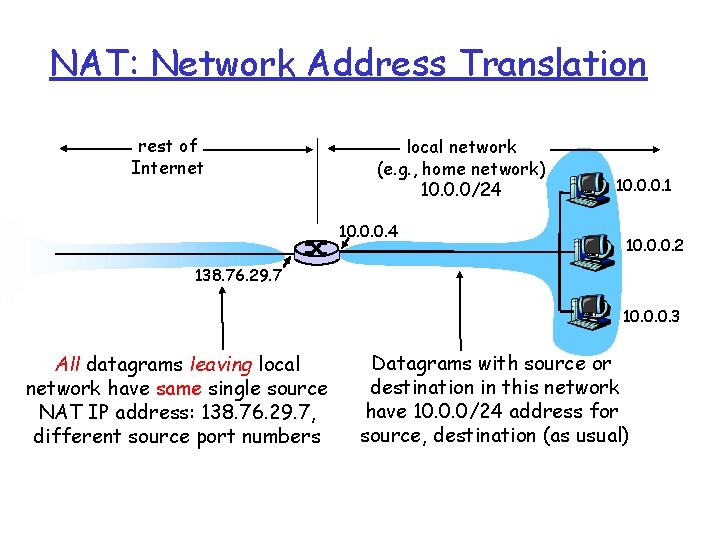
NAT: Network Address Translation rest of Internet local network (e. g. , home network) 10. 0. 0/24 10. 0. 0. 1 10. 0. 0. 2 138. 76. 29. 7 10. 0. 0. 3 All datagrams leaving local network have same single source NAT IP address: 138. 76. 29. 7, different source port numbers Datagrams with source or destination in this network have 10. 0. 0/24 address for source, destination (as usual)

NAT: Network Address Translation r Motivation: local network uses just one IP address as far as outside world is concerned: m range of addresses not needed from ISP: just one IP address for all devices m can change addresses of devices in local network without notifying outside world m can change ISP without changing addresses of devices in local network m devices inside local net not explicitly addressable, visible by outside world (a security plus).

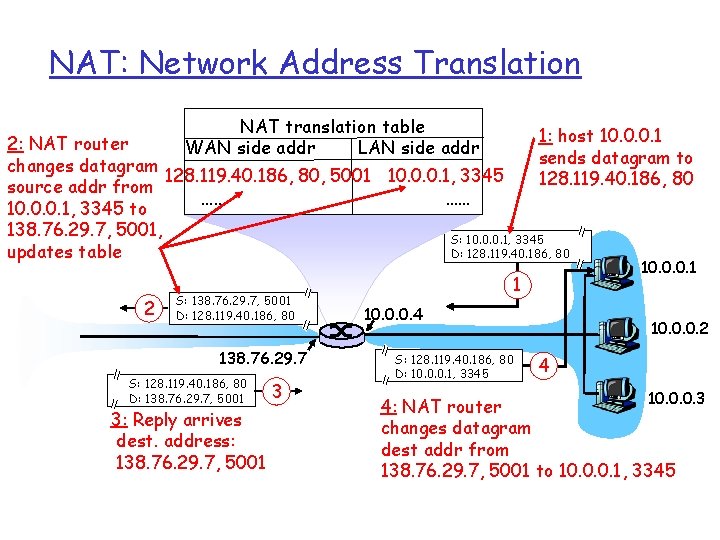
NAT: Network Address Translation Implementation: NAT router must: m outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #). . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. m remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair m incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table

NAT: Network Address Translation NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 2: NAT router sends datagram to changes datagram 128. 119. 40. 186, 80, 5001 10. 0. 0. 1, 3345 128. 119. 40. 186, 80 source addr from …… …… 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 updates table 2 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 10. 0. 0. 1 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345

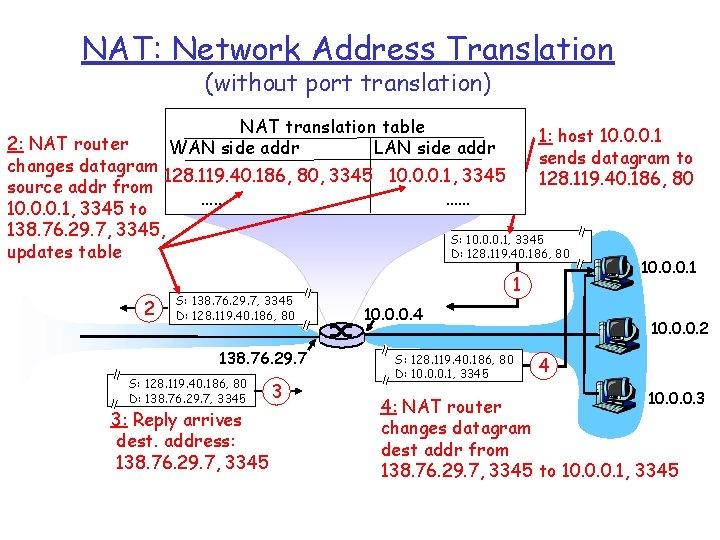
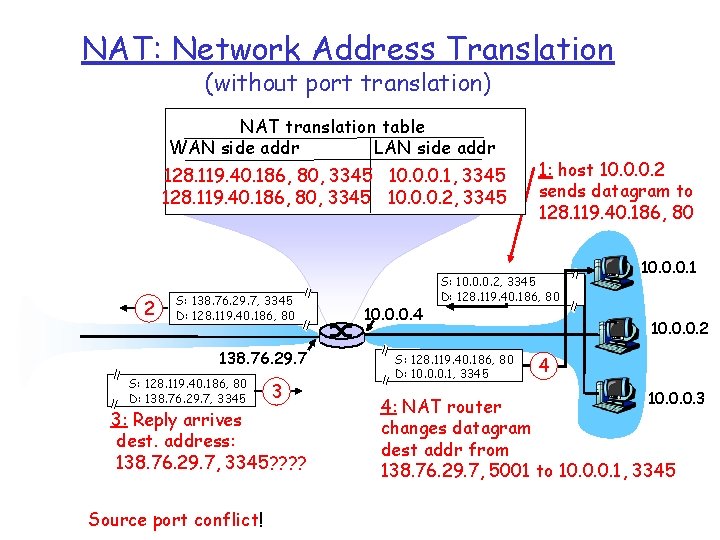
NAT: Network Address Translation (without port translation) NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 2: NAT router sends datagram to changes datagram 128. 119. 40. 186, 80, 3345 10. 0. 0. 1, 3345 128. 119. 40. 186, 80 source addr from …… …… 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 3345, S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 updates table 2 S: 138. 76. 29. 7, 3345 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 3345 3: Reply arrives dest. address: 138. 76. 29. 7, 3345 3 10. 0. 0. 1 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 3345 to 10. 0. 0. 1, 3345

NAT: Network Address Translation (without port translation) NAT translation table WAN side addr LAN side addr 128. 119. 40. 186, 80, 3345 10. 0. 0. 1, 3345 128. 119. 40. 186, 80, 3345 10. 0. 0. 2, 3345 2 S: 138. 76. 29. 7, 3345 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 3345 3 3: Reply arrives dest. address: 138. 76. 29. 7, 3345? ? Source port conflict! 10. 0. 0. 4 1: host 10. 0. 0. 2 sends datagram to 128. 119. 40. 186, 80 S: 10. 0. 0. 2, 3345 D: 128. 119. 40. 186, 80 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 1 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345

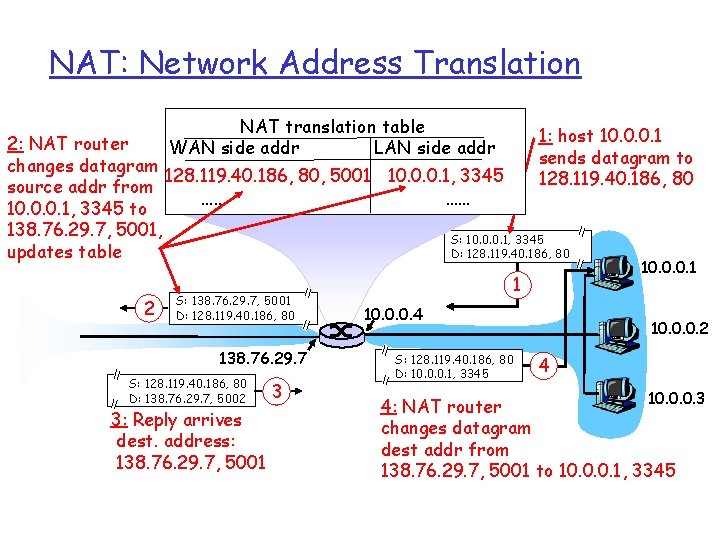
NAT: Network Address Translation NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 2: NAT router sends datagram to changes datagram 128. 119. 40. 186, 80, 5001 10. 0. 0. 1, 3345 128. 119. 40. 186, 80 source addr from …… …… 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 updates table 2 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5002 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 10. 0. 0. 1 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345

NAT: Network Address Translation NAT translation table WAN side addr LAN side addr 128. 119. 40. 186, 80, 5001 10. 0. 0. 1, 3345 128. 119. 40. 186, 80, 5002 10. 0. 0. 2, 3345 2 S: 138. 76. 29. 7, 5002 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5002 3: Reply arrives dest. address: 138. 76. 29. 7: 5002 3 10. 0. 0. 4 1: host 10. 0. 0. 2 sends datagram to 128. 119. 40. 186, 80 S: 10. 0. 0. 2, 3345 D: 128. 119. 40. 186, 80 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 1 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5002 to 10. 0. 0. 2, 3345

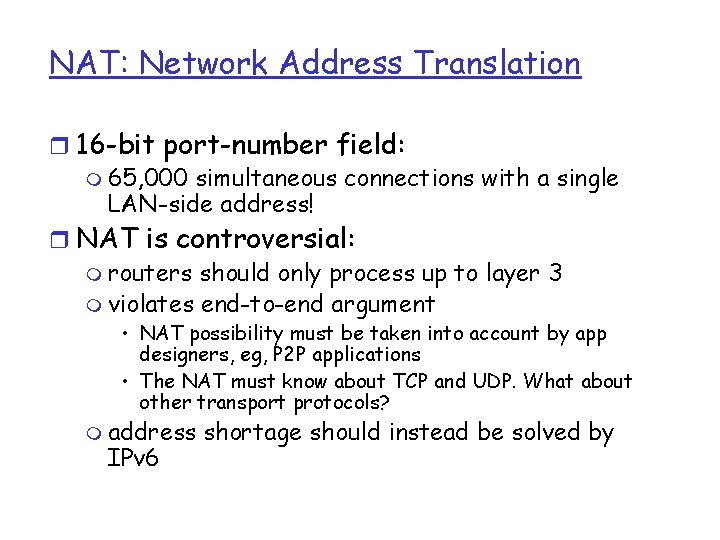
NAT: Network Address Translation r 16 -bit port-number field: m 65, 000 simultaneous connections with a single LAN-side address! r NAT is controversial: m routers should only process up to layer 3 m violates end-to-end argument • NAT possibility must be taken into account by app designers, eg, P 2 P applications • The NAT must know about TCP and UDP. What about other transport protocols? m address IPv 6 shortage should instead be solved by

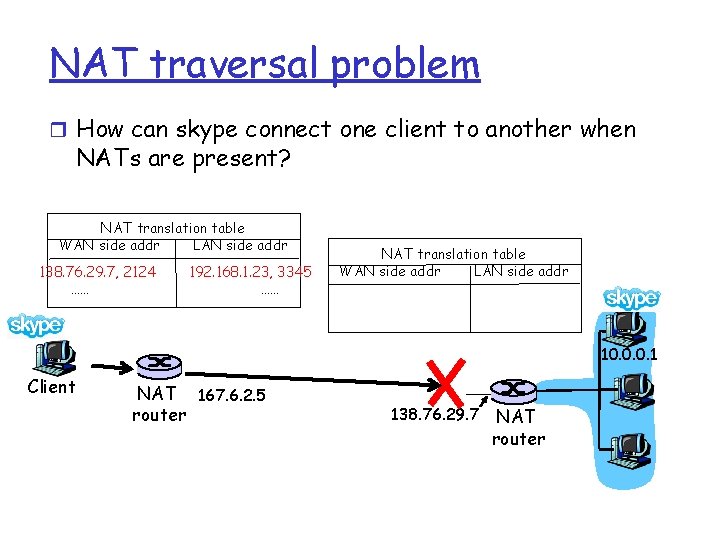
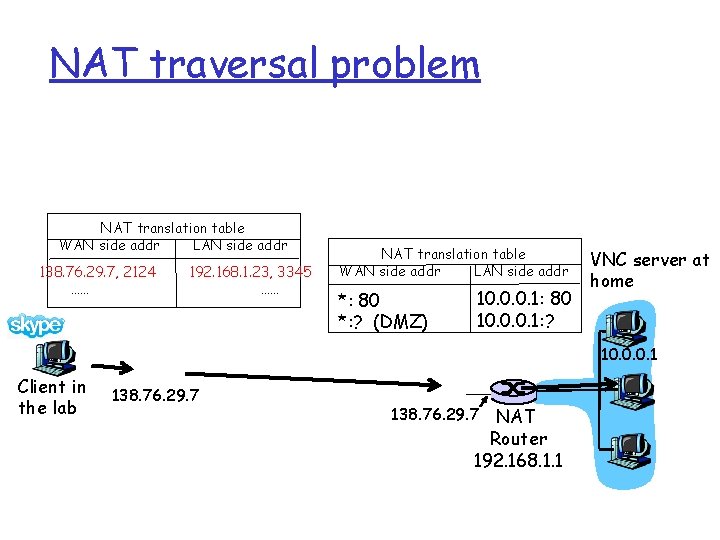
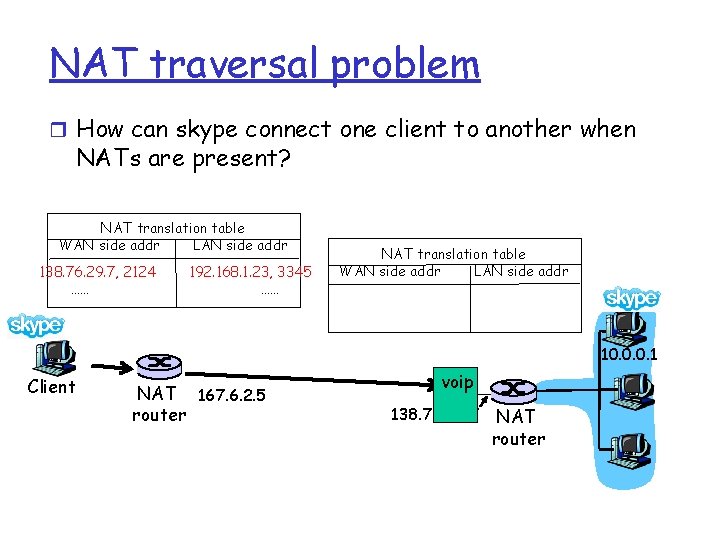
NAT traversal problem r How can skype connect one client to another when NATs are present? NAT translation table WAN side addr LAN side addr 138. 76. 29. 7, 2124 …… 192. 168. 1. 23, 3345 …… NAT translation table WAN side addr LAN side addr 10. 0. 0. 1 Client NAT 167. 6. 2. 5 router 138. 76. 29. 7 NAT router

NAT traversal problem r How can skype connect one client to another when NATs are present? NAT translation table WAN side addr LAN side addr 138. 76. 29. 7, 2124 …… 192. 168. 1. 23, 3345 …… NAT translation table WAN side addr LAN side addr *: 80 *: ? (DMZ) 10. 0. 0. 1: 80 10. 0. 0. 2: ? 10. 0. 0. 1 Client NAT 167. 6. 2. 5 router 138. 76. 29. 7 NAT router

NAT traversal problem NAT translation table WAN side addr LAN side addr 138. 76. 29. 7, 2124 …… 192. 168. 1. 23, 3345 …… NAT translation table WAN side addr LAN side addr *: 80 *: ? (DMZ) 10. 0. 0. 1: 80 10. 0. 0. 1: ? VNC server at home 10. 0. 0. 1 Client in the lab 138. 76. 29. 7 NAT Router 192. 168. 1. 1

NAT traversal problem r How can skype connect one client to another when NATs are present? NAT translation table WAN side addr LAN side addr 138. 76. 29. 7, 2124 …… 192. 168. 1. 23, 3345 …… NAT translation table WAN side addr LAN side addr 10. 0. 0. 1 Client NAT 167. 6. 2. 5 router voip 138. 76. 29. 7 NAT router

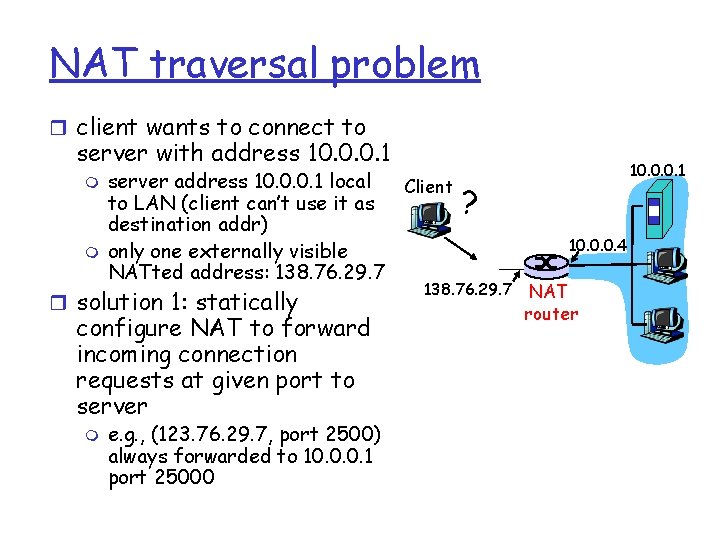
NAT traversal problem r client wants to connect to server with address 10. 0. 0. 1 m m server address 10. 0. 0. 1 local Client to LAN (client can’t use it as destination addr) only one externally visible NATted address: 138. 76. 29. 7 r solution 1: statically configure NAT to forward incoming connection requests at given port to server m e. g. , (123. 76. 29. 7, port 2500) always forwarded to 10. 0. 0. 1 port 25000 10. 0. 0. 1 ? 138. 76. 29. 7 10. 0. 0. 4 NAT router

NAT traversal problem r solution 2: Universal Plug and Play (UPn. P) Internet Gateway Device (IGD) Protocol. Allows NATted host to: v learn public IP address (138. 76. 29. 7) v add/remove port mappings (with lease times) i. e. , automate static NAT port map configuration 10. 0. 0. 1 IGD 10. 0. 0. 4 138. 76. 29. 7 NAT router

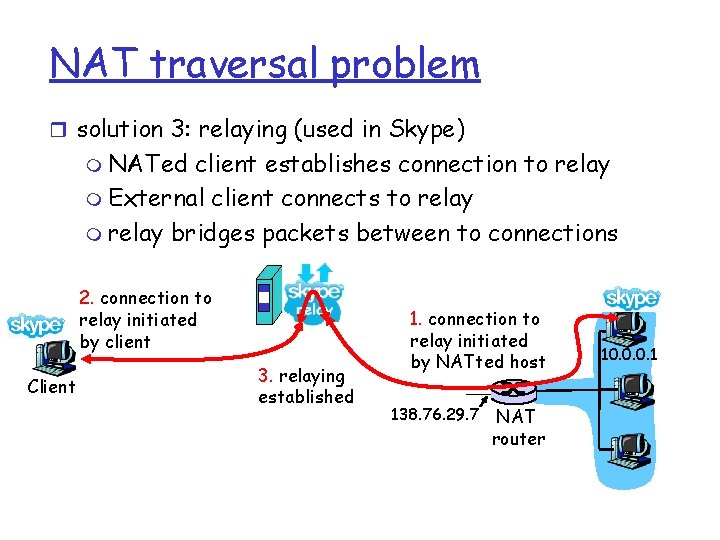
NAT traversal problem r solution 3: relaying (used in Skype) m NATed client establishes connection to relay m External client connects to relay m relay bridges packets between to connections 2. connection to relay initiated by client Client 3. relaying established 1. connection to relay initiated by NATted host 138. 76. 29. 7 NAT router 10. 0. 0. 1

IP addresses: how to get one? Q: How does a host get IP address? r hard-coded by system admin in a file m Windows: control-panel->network->configuration>tcp/ip->properties m UNIX: /etc/rc. config r DHCP: Dynamic Host Configuration Protocol: dynamically get address from as server m “plug-and-play”

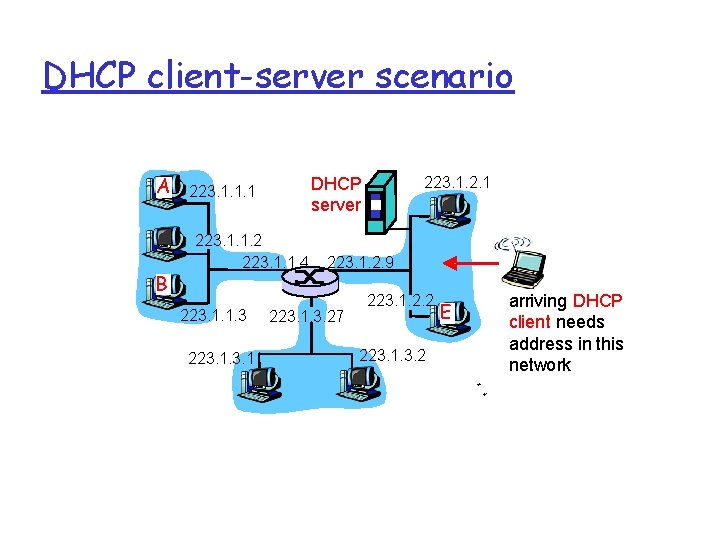
DHCP: Dynamic Host Configuration Protocol Goal: allow host to dynamically obtain its IP address from network server when it joins network Can renew its lease on address in use Allows reuse of addresses (only hold address while connected an “on”) Support for mobile users who want to join network (more shortly) DHCP overview: m host broadcasts “DHCP discover” msg m DHCP server responds with “DHCP offer” msg m host requests IP address: “DHCP request” msg m DHCP server sends address: “DHCP ack” msg

DHCP client-server scenario A B 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 DHCP server 223. 1. 1. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 223. 1. 3. 2 E arriving DHCP client needs address in this network

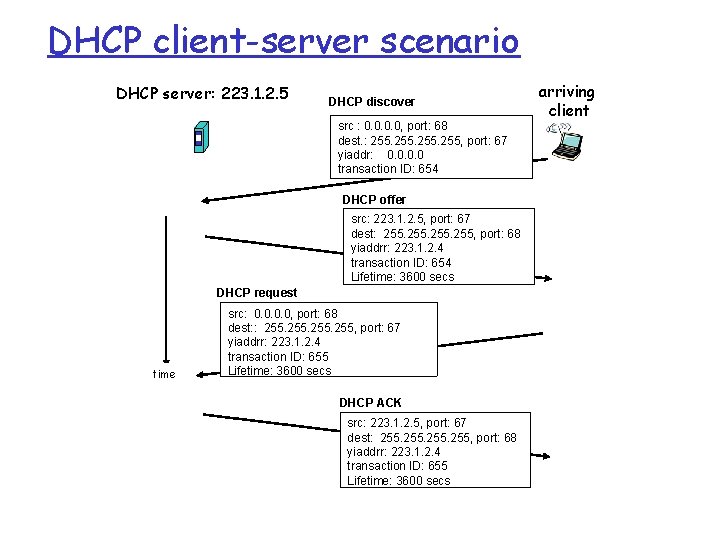
DHCP client-server scenario DHCP server: 223. 1. 2. 5 DHCP discover src : 0. 0, port: 68 dest. : 255, port: 67 yiaddr: 0. 0 transaction ID: 654 DHCP offer src: 223. 1. 2. 5, port: 67 dest: 255, port: 68 yiaddrr: 223. 1. 2. 4 transaction ID: 654 Lifetime: 3600 secs DHCP request time src: 0. 0, port: 68 dest: : 255, port: 67 yiaddrr: 223. 1. 2. 4 transaction ID: 655 Lifetime: 3600 secs DHCP ACK src: 223. 1. 2. 5, port: 67 dest: 255, port: 68 yiaddrr: 223. 1. 2. 4 transaction ID: 655 Lifetime: 3600 secs arriving client

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

ICMP: Internet Control Message Protocol r used by hosts & routers to communicate network-level information m error reporting: unreachable host, network, port, protocol m echo request/reply (used by ping) r network-layer “above” IP: m ICMP msgs carried in IP datagrams r ICMP message: type, code plus first 8 bytes of IP datagram causing error Type 0 3 3 3 4 Code 0 0 1 2 3 6 7 0 8 9 10 11 12 0 0 0 description echo reply (ping) dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) echo request (ping) route advertisement router discovery TTL expired bad IP header

Traceroute and ICMP r Source sends series of UDP or ICMP segments to dest m m m First has TTL =1 Second has TTL=2, etc. Unlikely port number r When nth datagram arrives to nth router: m m m Router discards datagram And (might) send to source an ICMP message (type 11, code 0) Message includes name of router& IP address r When ICMP message arrives, source calculates RTT r Traceroute does this 3 times Stopping criterion r UDP or ICMP segment eventually arrives at destination host r Destination (might) return ICMP “host unreachable” packet (type 3, code 3) r When source gets this ICMP, stops.

ICMP ping flood r Send many ICMP ping messages to a web server r The server will not be able to respond fast enough, and hence not be able to provide is primary service m Denial of service attack (Do. S) r DDo. S (distributed Do. S). Many hosts send ICMP ping messages to a web server r One defense is to filter out messages from hosts that send too many ICMP messages r So, attackers send ICMP messages, but with a random source address. r Or attackers can send ICMP messages to random hosts but with the source address of the victim r One defense is to filter all ICMP messages

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP

IPv 6 r Initial motivation: 32 -bit address space soon to be completely allocated. r Additional motivation: m header format helps speed processing/forwarding m “header changes to facilitate Qo. S and built-in security” IPv 6 datagram format: m fixed-length 40 byte header m no fragmentation allowed

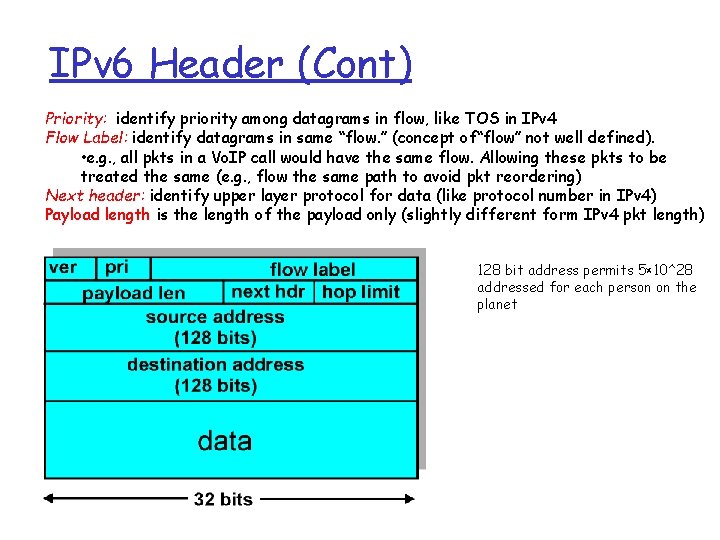
IPv 6 Header (Cont) Priority: identify priority among datagrams in flow, like TOS in IPv 4 Flow Label: identify datagrams in same “flow. ” (concept of“flow” not well defined). • e. g. , all pkts in a Vo. IP call would have the same flow. Allowing these pkts to be treated the same (e. g. , flow the same path to avoid pkt reordering) Next header: identify upper layer protocol for data (like protocol number in IPv 4) Payload length is the length of the payload only (slightly different form IPv 4 pkt length) 128 bit address permits 5× 10^28 addressed for each person on the planet

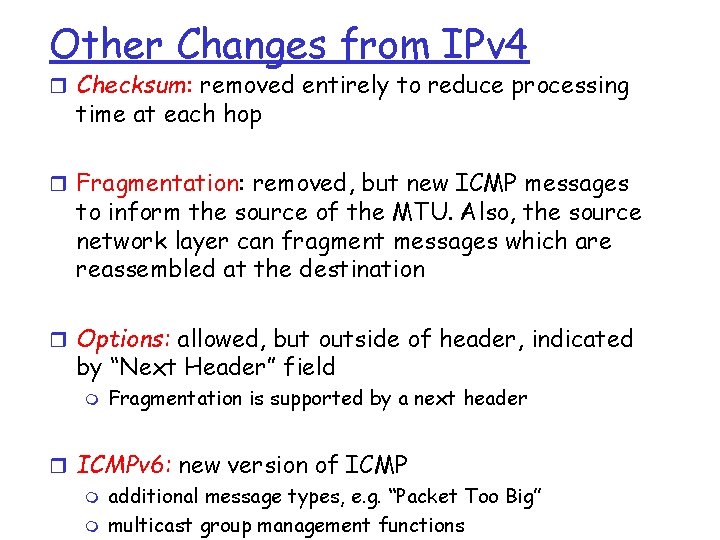
Other Changes from IPv 4 r Checksum: removed entirely to reduce processing time at each hop r Fragmentation: removed, but new ICMP messages to inform the source of the MTU. Also, the source network layer can fragment messages which are reassembled at the destination r Options: allowed, but outside of header, indicated by “Next Header” field m Fragmentation is supported by a next header r ICMPv 6: new version of ICMP m additional message types, e. g. “Packet Too Big” m multicast group management functions

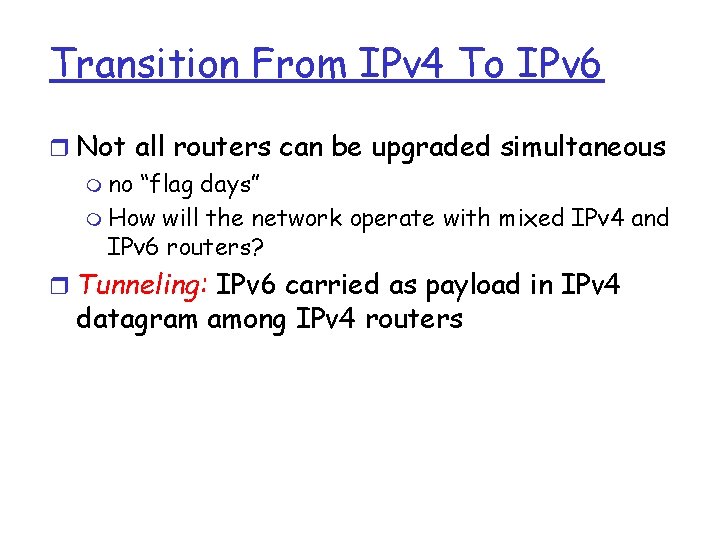
Transition From IPv 4 To IPv 6 r Not all routers can be upgraded simultaneous m no “flag days” m How will the network operate with mixed IPv 4 and IPv 6 routers? r Tunneling: IPv 6 carried as payload in IPv 4 datagram among IPv 4 routers

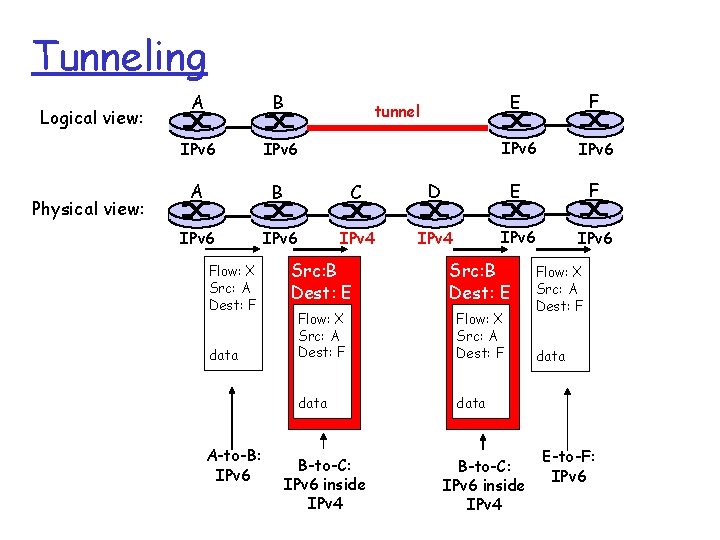
Tunneling Logical view: Physical view: E F IPv 6 IPv 6 A B IPv 6 tunnel IPv 4

Tunneling Logical view: Physical view: A B IPv 6 A B C IPv 6 IPv 4 Flow: X Src: A Dest: F data A-to-B: IPv 6 E F IPv 6 D E F IPv 4 IPv 6 tunnel Src: B Dest: E Flow: X Src: A Dest: F data B-to-C: IPv 6 inside IPv 4 Flow: X Src: A Dest: F data E-to-F: IPv 6

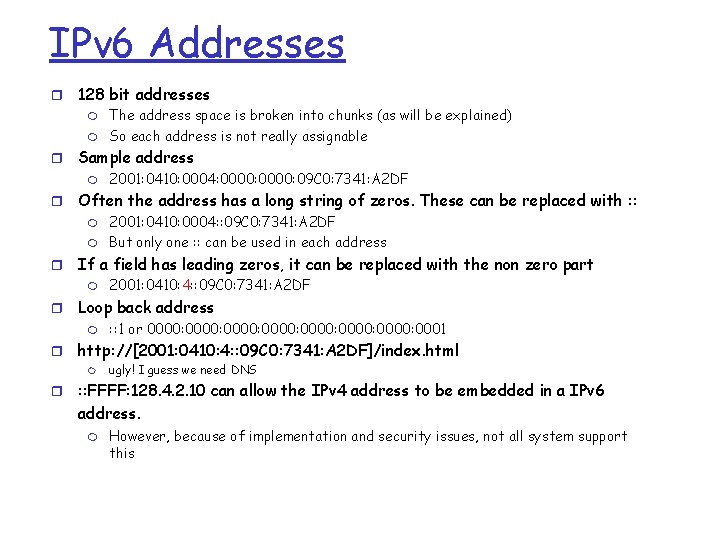
IPv 6 Addresses r 128 bit addresses m m r Sample address m r m : : 1 or 0000: 0000: 0001 http: //[2001: 0410: 4: : 09 C 0: 7341: A 2 DF]/index. html m r 2001: 0410: 4: : 09 C 0: 7341: A 2 DF Loop back address m r 2001: 0410: 0004: : 09 C 0: 7341: A 2 DF But only one : : can be used in each address If a field has leading zeros, it can be replaced with the non zero part m r 2001: 0410: 0004: 0000: 09 C 0: 7341: A 2 DF Often the address has a long string of zeros. These can be replaced with : : m r The address space is broken into chunks (as will be explained) So each address is not really assignable ugly! I guess we need DNS : : FFFF: 128. 4. 2. 10 can allow the IPv 4 address to be embedded in a IPv 6 address. m However, because of implementation and security issues, not all system support this

IPv 6 broadcast r IPv 4 allows broadcast – where all hosts on the subnet receive the message m m 255 is the broadcast address On the subnet 128. 4. 2/24, the broadcast address is 128. 4. 2. 255 r IPv 6 does not really have broadcast. r Instead, it has local multicast, where every host in a subnet gets the message m m (well, this seems to be the same thing that IPv 4 did. IPv 4 does really let you broadcast over the entire internet) FF 02: : 1 is the local broadcast address

IPv 6 Address Scope r In IPv 6, the address has scope, i. e. , the address is valid in some region r FE 80: : /10 is a link local addresses. m m These addresses are only used inside a subnet (customer network) Routers do not forward these r FF 00: : /8 are multicast address (global scope) r Everything else are global unicast addresses (global scope)

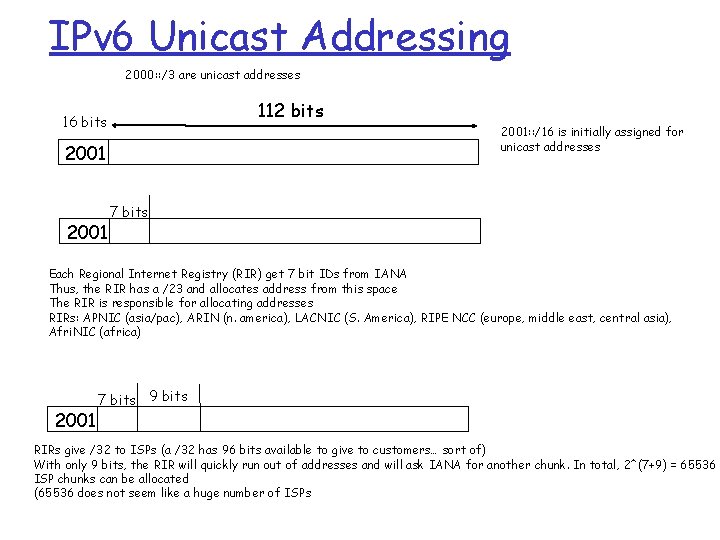
IPv 6 Unicast Addressing 2000: : /3 are unicast addresses 112 bits 16 bits 2001: : /16 is initially assigned for unicast addresses 2001 7 bits Each Regional Internet Registry (RIR) get 7 bit IDs from IANA Thus, the RIR has a /23 and allocates address from this space The RIR is responsible for allocating addresses RIRs: APNIC (asia/pac), ARIN (n. america), LACNIC (S. America), RIPE NCC (europe, middle east, central asia), Afri. NIC (africa) 2001 7 bits 9 bits RIRs give /32 to ISPs (a /32 has 96 bits available to give to customers… sort of) With only 9 bits, the RIR will quickly run out of addresses and will ask IANA for another chunk. In total, 2^(7+9) = 65536 ISP chunks can be allocated (65536 does not seem like a huge number of ISPs

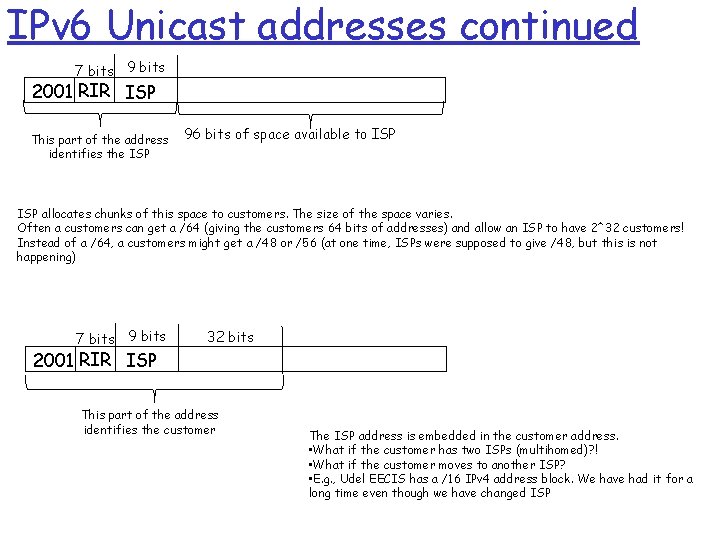
IPv 6 Unicast addresses continued 7 bits 9 bits 2001 RIR ISP This part of the address identifies the ISP 96 bits of space available to ISP allocates chunks of this space to customers. The size of the space varies. Often a customers can get a /64 (giving the customers 64 bits of addresses) and allow an ISP to have 2^32 customers! Instead of a /64, a customers might get a /48 or /56 (at one time, ISPs were supposed to give /48, but this is not happening) 7 bits 9 bits 32 bits 2001 RIR ISP This part of the address identifies the customer The ISP address is embedded in the customer address. • What if the customer has two ISPs (multihomed)? ! • What if the customer moves to another ISP? • E. g. , Udel EECIS has a /16 IPv 4 address block. We have had it for a long time even though we have changed ISP

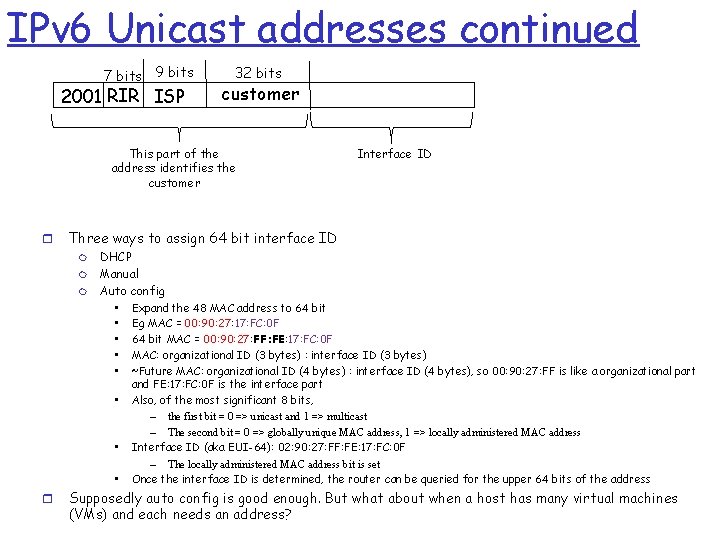
IPv 6 Unicast addresses continued 7 bits 9 bits 2001 RIR ISP 32 bits customer This part of the address identifies the customer r Three ways to assign 64 bit interface ID m m m DHCP Manual Auto config • Expand the 48 MAC address to 64 bit • Eg MAC = 00: 90: 27: 17: FC: 0 F • 64 bit MAC = 00: 90: 27: FF: FE: 17: FC: 0 F • MAC: organizational ID (3 bytes) : interface ID (3 bytes) • ~Future MAC: organizational ID (4 bytes) : interface ID (4 bytes), so 00: 90: 27: FF is like a organizational part • • • r Interface ID and FE: 17: FC: 0 F is the interface part Also, of the most significant 8 bits, – the first bit = 0 => unicast and 1 => multicast – The second bit = 0 => globally unique MAC address, 1 => locally administered MAC address Interface ID (aka EUI-64): 02: 90: 27: FF: FE: 17: FC: 0 F – The locally administered MAC address bit is set Once the interface ID is determined, the router can be queried for the upper 64 bits of the address Supposedly auto config is good enough. But what about when a host has many virtual machines (VMs) and each needs an address?

IPv 6 Interface ID r The interface ID is the same as the MAC r Thus, a web site can examine the IPv 6 address to determine r r your MAC and hence identify the end-host This is a significant privacy problem Also, MAC addresses can be guessed (e. g. , I know Apple’s organizational part and can guess the lower 3 bytes. In this way I can find MACs) Using random interface IDs solves these problems, but might also result in address collision DHCP is another solution m DHCP is needed anyway to set the DNS server

Chapter 4: Network Layer r 4. 1 Introduction r 4. 2 Virtual circuit and datagram networks r 4. 3 What’s inside a router r 4. 4 IP: Internet Protocol m m Datagram format IPv 4 addressing ICMP IPv 6 r 4. 5 Routing algorithms m Link state m Distance Vector m Hierarchical routing r 4. 6 Routing in the Internet m m m RIP OSPF BGP r 4. 7 Broadcast and multicast routing