Chapter 4 Concurrency Control Algorithms 4 2 General









- Slides: 51

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned „The optimist believes we live in the best of all possible worlds. The pessimist fears this is true. “ (Robert Oppenheimer) 1/7/2022 Transactional Information Systems 1

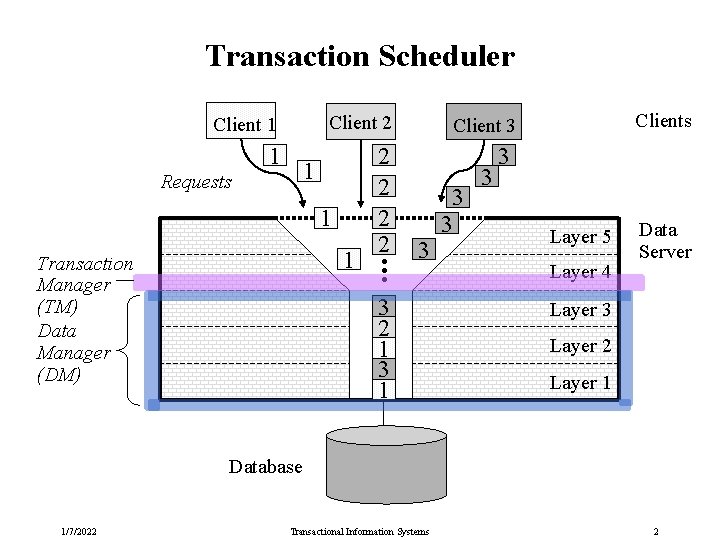
Transaction Scheduler Client 2 1 2 2 1 Requests 1 1 Transaction Manager (TM) Data Manager (DM) . . . Client 1 Clients Client 3 3 3 2 1 3 3 3 3 Layer 5 Layer 4 Data Server Layer 3 Layer 2 Layer 1 Database 1/7/2022 Transactional Information Systems 2

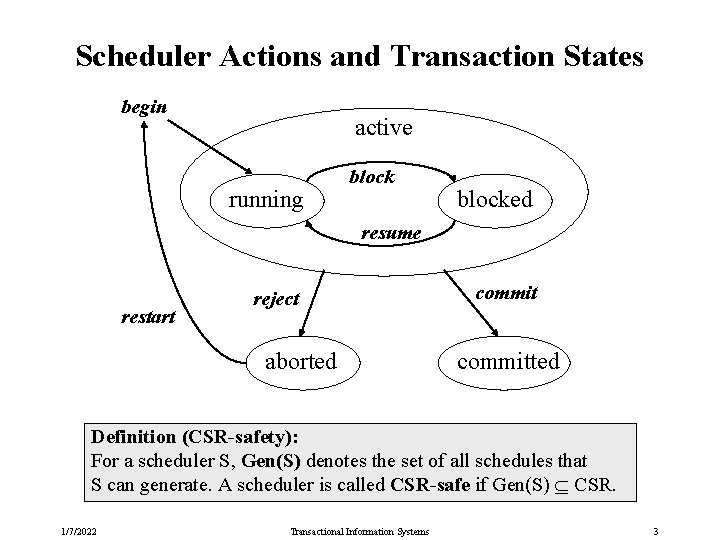
Scheduler Actions and Transaction States begin active running blocked resume restart reject aborted committed Definition (CSR-safety): For a scheduler S, Gen(S) denotes the set of all schedules that S can generate. A scheduler is called CSR-safe if Gen(S) CSR. 1/7/2022 Transactional Information Systems 3

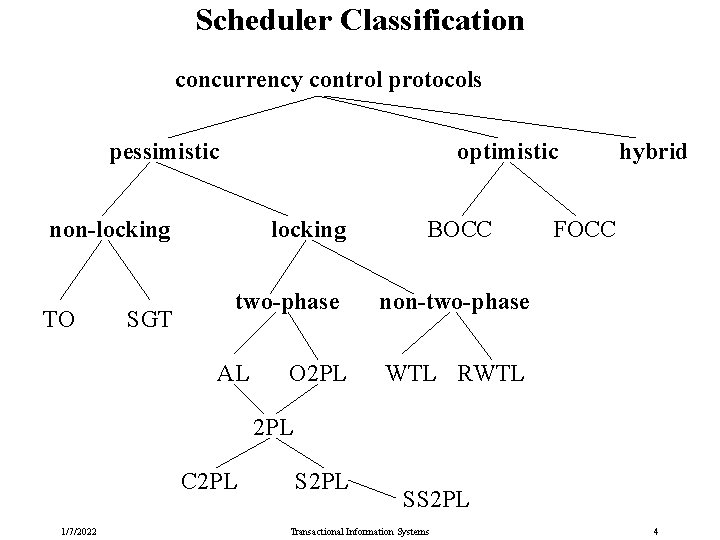
Scheduler Classification concurrency control protocols pessimistic optimistic non-locking TO SGT locking two-phase AL O 2 PL BOCC hybrid FOCC non-two-phase WTL RWTL 2 PL C 2 PL 1/7/2022 S 2 PL SS 2 PL Transactional Information Systems 4

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 5

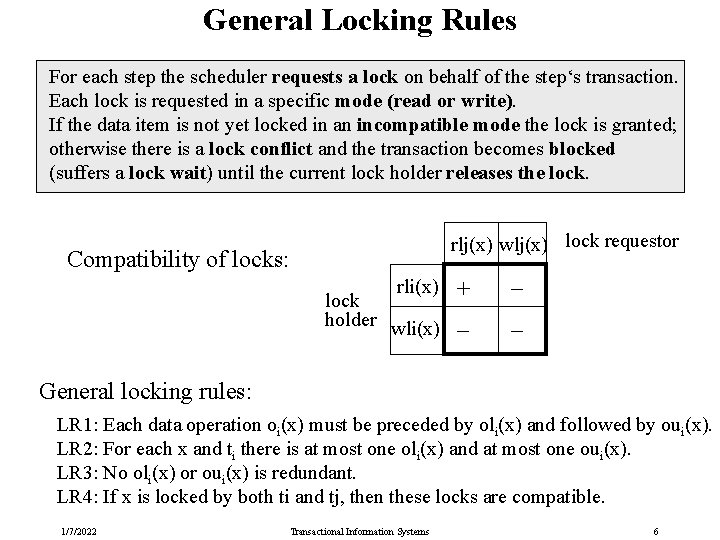
General Locking Rules For each step the scheduler requests a lock on behalf of the step‘s transaction. Each lock is requested in a specific mode (read or write). If the data item is not yet locked in an incompatible mode the lock is granted; otherwise there is a lock conflict and the transaction becomes blocked (suffers a lock wait) until the current lock holder releases the lock. rlj(x) wlj(x) lock requestor Compatibility of locks: rli(x) + lock holder wli(x) _ _ _ General locking rules: LR 1: Each data operation oi(x) must be preceded by oli(x) and followed by oui(x). LR 2: For each x and ti there is at most one oli(x) and at most one oui(x). LR 3: No oli(x) or oui(x) is redundant. LR 4: If x is locked by both ti and tj, then these locks are compatible. 1/7/2022 Transactional Information Systems 6

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 7

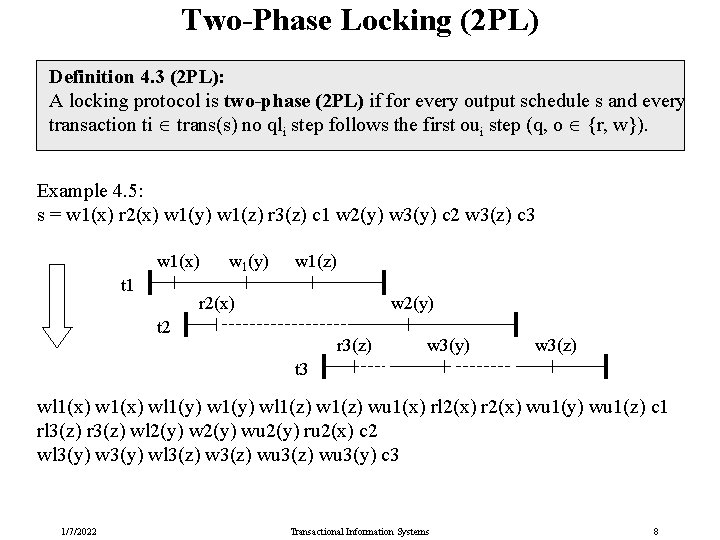
Two-Phase Locking (2 PL) Definition 4. 3 (2 PL): A locking protocol is two-phase (2 PL) if for every output schedule s and every transaction ti trans(s) no qli step follows the first oui step (q, o {r, w}). Example 4. 5: s = w 1(x) r 2(x) w 1(y) w 1(z) r 3(z) c 1 w 2(y) w 3(y) c 2 w 3(z) c 3 w 1(x) t 1 w 1(y) w 1(z) r 2(x) w 2(y) t 2 r 3(z) w 3(y) w 3(z) t 3 wl 1(x) wl 1(y) wl 1(z) wu 1(x) rl 2(x) r 2(x) wu 1(y) wu 1(z) c 1 rl 3(z) r 3(z) wl 2(y) wu 2(y) ru 2(x) c 2 wl 3(y) wl 3(z) wu 3(y) c 3 1/7/2022 Transactional Information Systems 8

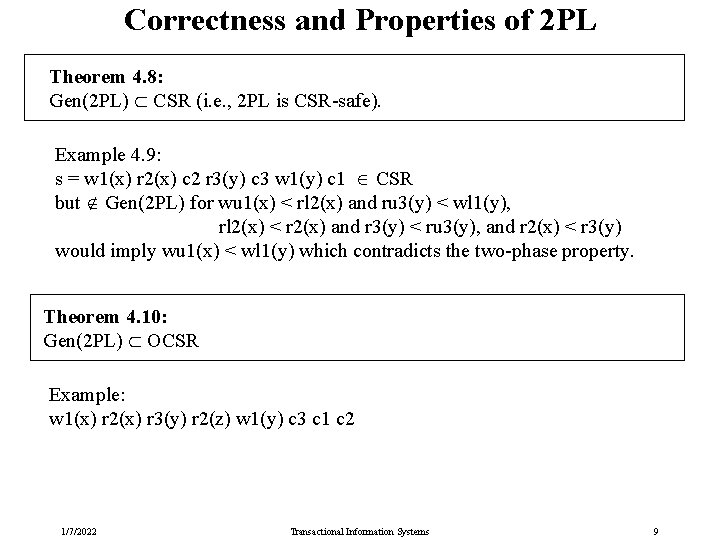
Correctness and Properties of 2 PL Theorem 4. 8: Gen(2 PL) CSR (i. e. , 2 PL is CSR-safe). Example 4. 9: s = w 1(x) r 2(x) c 2 r 3(y) c 3 w 1(y) c 1 CSR but Gen(2 PL) for wu 1(x) < rl 2(x) and ru 3(y) < wl 1(y), rl 2(x) < r 2(x) and r 3(y) < ru 3(y), and r 2(x) < r 3(y) would imply wu 1(x) < wl 1(y) which contradicts the two-phase property. Theorem 4. 10: Gen(2 PL) OCSR Example: w 1(x) r 2(x) r 3(y) r 2(z) w 1(y) c 3 c 1 c 2 1/7/2022 Transactional Information Systems 9

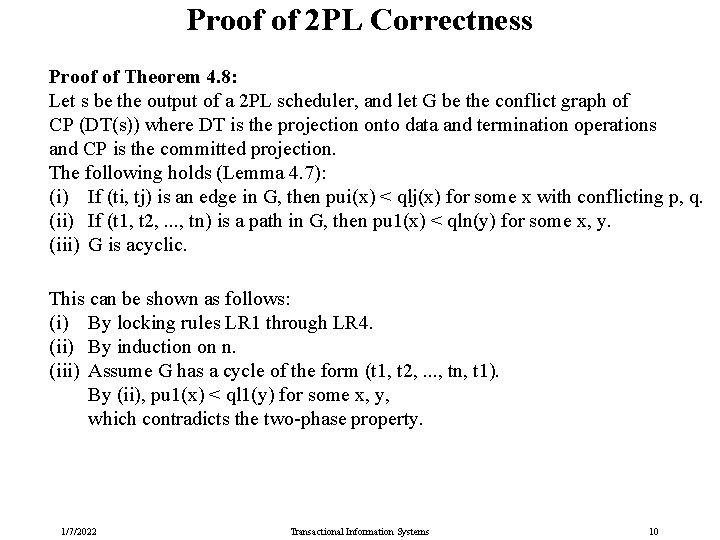
Proof of 2 PL Correctness Proof of Theorem 4. 8: Let s be the output of a 2 PL scheduler, and let G be the conflict graph of CP (DT(s)) where DT is the projection onto data and termination operations and CP is the committed projection. The following holds (Lemma 4. 7): (i) If (ti, tj) is an edge in G, then pui(x) < qlj(x) for some x with conflicting p, q. (ii) If (t 1, t 2, . . . , tn) is a path in G, then pu 1(x) < qln(y) for some x, y. (iii) G is acyclic. This can be shown as follows: (i) By locking rules LR 1 through LR 4. (ii) By induction on n. (iii) Assume G has a cycle of the form (t 1, t 2, . . . , tn, t 1). By (ii), pu 1(x) < ql 1(y) for some x, y, which contradicts the two-phase property. 1/7/2022 Transactional Information Systems 10

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 11

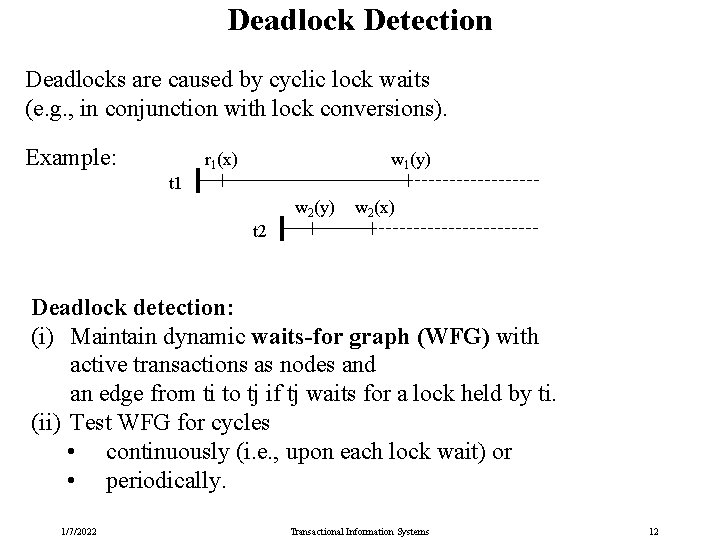
Deadlock Detection Deadlocks are caused by cyclic lock waits (e. g. , in conjunction with lock conversions). Example: r 1(x) w 1(y) t 1 w 2(y) w 2(x) t 2 Deadlock detection: (i) Maintain dynamic waits-for graph (WFG) with active transactions as nodes and an edge from ti to tj if tj waits for a lock held by ti. (ii) Test WFG for cycles • continuously (i. e. , upon each lock wait) or • periodically. 1/7/2022 Transactional Information Systems 12

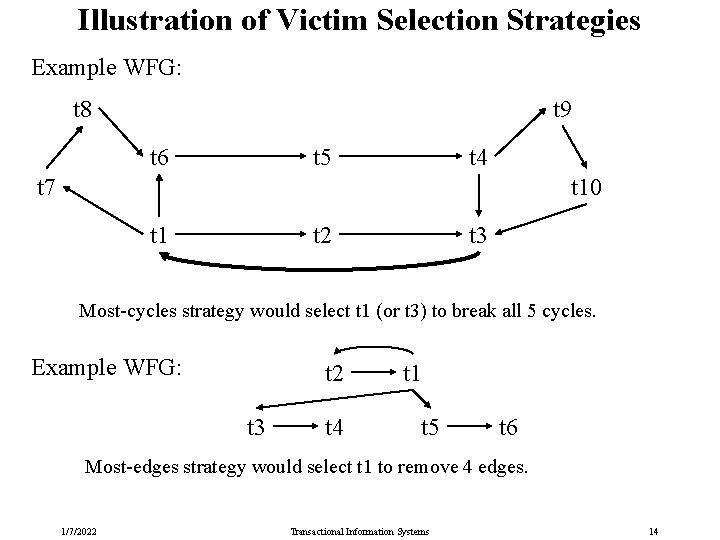
Deadlock Resolution Choose a transaction on a WFG cycle as a deadlock victim and abort this transaction, and repeat until no more cycles. Possible victim selection strategies: 1. Last blocked 2. Random 3. Youngest 4. Minimum locks 5. Minimum work 6. Most cycles 7. Most edges 1/7/2022 Transactional Information Systems 13

Illustration of Victim Selection Strategies Example WFG: t 8 t 9 t 6 t 5 t 4 t 7 t 10 t 1 t 2 t 3 Most-cycles strategy would select t 1 (or t 3) to break all 5 cycles. Example WFG: t 2 t 3 t 4 t 1 t 5 t 6 Most-edges strategy would select t 1 to remove 4 edges. 1/7/2022 Transactional Information Systems 14

Deadlock Prevention Restrict lock waits to ensure acyclic WFG at all times. Reasonable deadlock prevention strategies: 1. Wait-die: 2. upon ti blocked by tj: 3. if ti started before tj then wait else abort ti 4. 2. Wound-wait: 5. upon ti blocked by tj: 6. if ti started before tj then abort tj else wait 7. 3. Immediate restart: 8. upon ti blocked by tj: abort ti 9. 4. Running priority: 10. upon ti blocked by tj: 11. if tj is itself blocked then abort tj else wait 12. 5. Timeout: 13. abort waiting transaction when a timer expires 14. Abort entails later restart. 1/7/2022 Transactional Information Systems 15

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 16

Definition 4. 11 (Conservative 2 PL): Under static or conservative 2 PL (C 2 PL) each transaction acquires all its locks before the first data operation (preclaiming). time locks general 2 PL locks Variants of 2 PL Definition 4. 12 (Strict 2 PL): Under strict 2 PL (S 2 PL) each transaction holds all its write locks until the transaction terminates. locks time Definition 4. 13 (Strong 2 PL): Under strong 2 PL (SS 2 PL) each transaction holds all its locks (i. e. , both r and w) until the transaction terminates. 1/7/2022 Transactional Information Systems 17

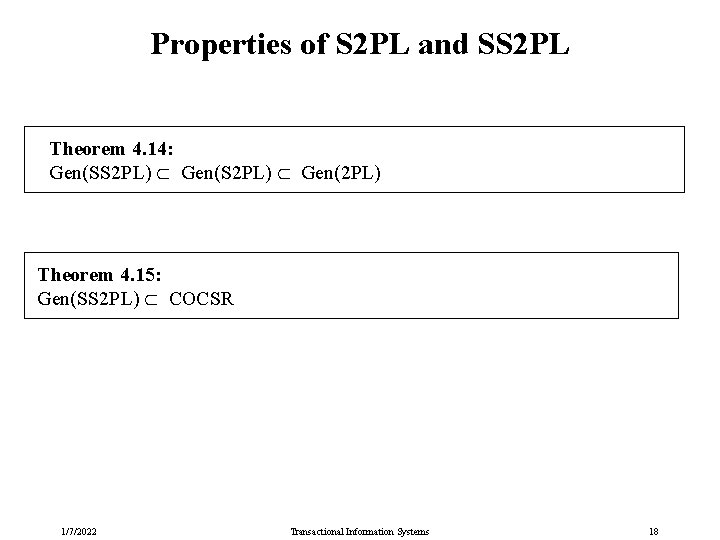
Properties of S 2 PL and SS 2 PL Theorem 4. 14: Gen(SS 2 PL) Gen(2 PL) Theorem 4. 15: Gen(SS 2 PL) COCSR 1/7/2022 Transactional Information Systems 18

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 19

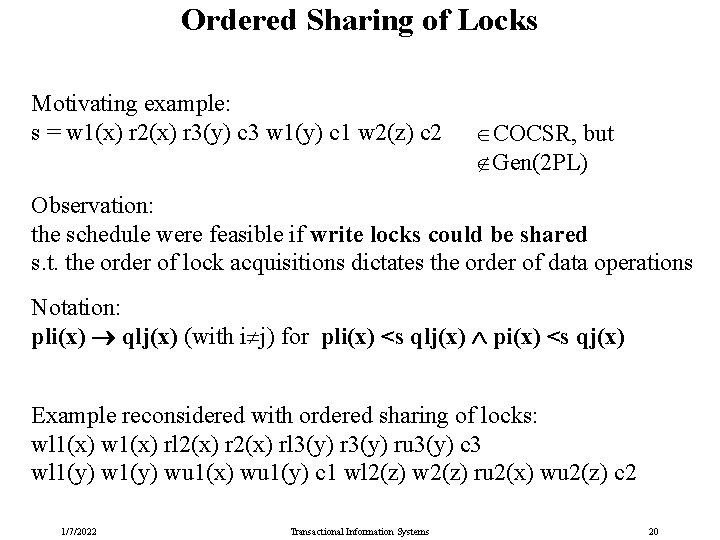
Ordered Sharing of Locks Motivating example: s = w 1(x) r 2(x) r 3(y) c 3 w 1(y) c 1 w 2(z) c 2 COCSR, but Gen(2 PL) Observation: the schedule were feasible if write locks could be shared s. t. the order of lock acquisitions dictates the order of data operations Notation: pli(x) qlj(x) (with i j) for pli(x) <s qlj(x) pi(x) <s qj(x) Example reconsidered with ordered sharing of locks: wl 1(x) w 1(x) rl 2(x) rl 3(y) ru 3(y) c 3 wl 1(y) wu 1(x) wu 1(y) c 1 wl 2(z) w 2(z) ru 2(x) wu 2(z) c 2 1/7/2022 Transactional Information Systems 20

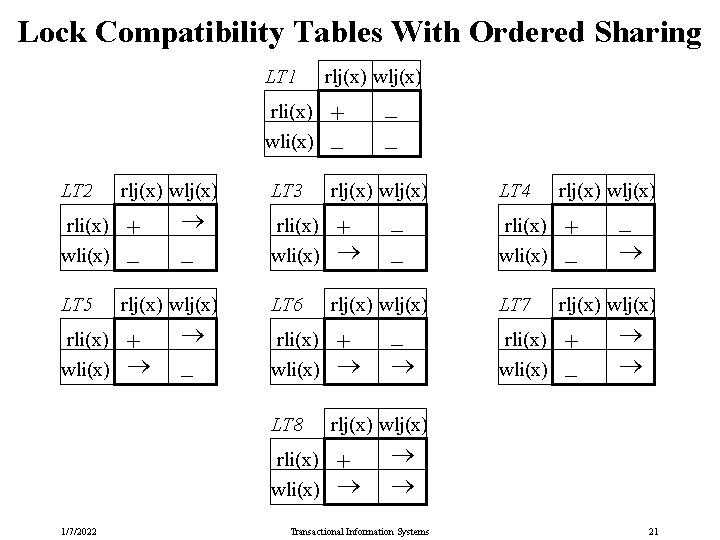
Lock Compatibility Tables With Ordered Sharing LT 1 rlj(x) wlj(x) rli(x) + wli(x) _ LT 2 rlj(x) wlj(x) rli(x) + wli(x) _ LT 5 rli(x) _ rlj(x) wlj(x) + wli(x) _ LT 3 rlj(x) wlj(x) rli(x) + wli(x) LT 6 + wli(x) rli(x) _ LT 4 rlj(x) wlj(x) rli(x) + wli(x) _ LT 7 rli(x) _ rlj(x) wlj(x) + wli(x) 1/7/2022 _ _ rlj(x) wlj(x) rli(x) LT 8 _ _ Transactional Information Systems 21

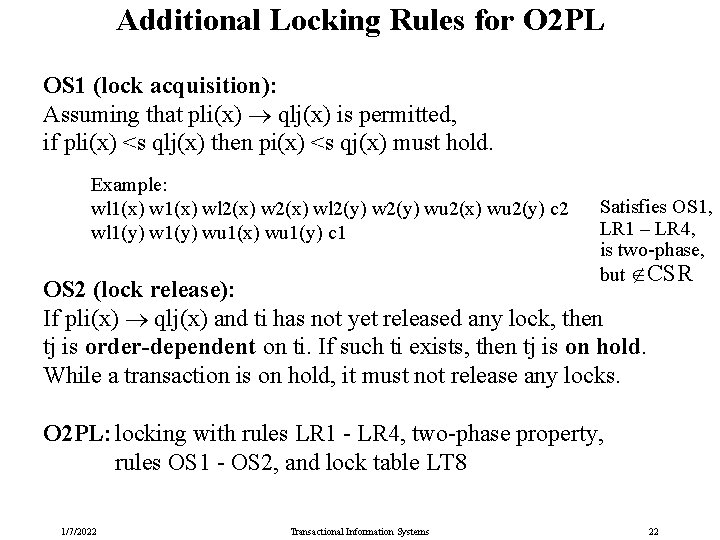
Additional Locking Rules for O 2 PL OS 1 (lock acquisition): Assuming that pli(x) qlj(x) is permitted, if pli(x) <s qlj(x) then pi(x) <s qj(x) must hold. Example: wl 1(x) wl 2(x) wl 2(y) wu 2(x) wu 2(y) c 2 wl 1(y) wu 1(x) wu 1(y) c 1 Satisfies OS 1, LR 1 – LR 4, is two-phase, but CSR OS 2 (lock release): If pli(x) qlj(x) and ti has not yet released any lock, then tj is order-dependent on ti. If such ti exists, then tj is on hold. While a transaction is on hold, it must not release any locks. O 2 PL: locking with rules LR 1 - LR 4, two-phase property, rules OS 1 - OS 2, and lock table LT 8 1/7/2022 Transactional Information Systems 22

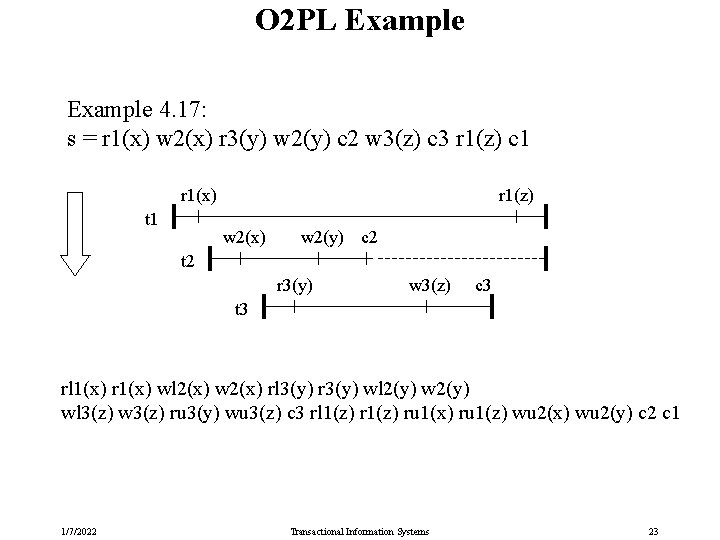
O 2 PL Example 4. 17: s = r 1(x) w 2(x) r 3(y) w 2(y) c 2 w 3(z) c 3 r 1(z) c 1 r 1(x) t 1 r 1(z) w 2(x) w 2(y) c 2 t 2 r 3(y) w 3(z) c 3 t 3 rl 1(x) r 1(x) wl 2(x) w 2(x) rl 3(y) r 3(y) wl 2(y) wl 3(z) w 3(z) ru 3(y) wu 3(z) c 3 rl 1(z) ru 1(x) ru 1(z) wu 2(x) wu 2(y) c 2 c 1 1/7/2022 Transactional Information Systems 23

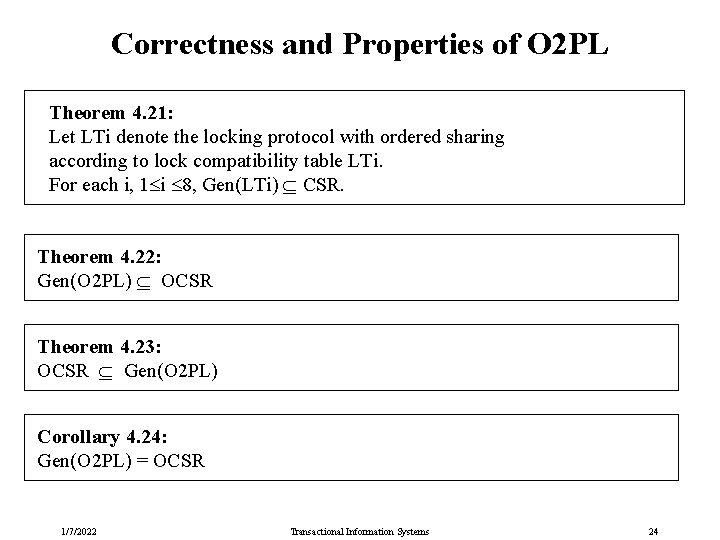
Correctness and Properties of O 2 PL Theorem 4. 21: Let LTi denote the locking protocol with ordered sharing according to lock compatibility table LTi. For each i, 1 i 8, Gen(LTi) CSR. Theorem 4. 22: Gen(O 2 PL) OCSR Theorem 4. 23: OCSR Gen(O 2 PL) Corollary 4. 24: Gen(O 2 PL) = OCSR 1/7/2022 Transactional Information Systems 24

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 25

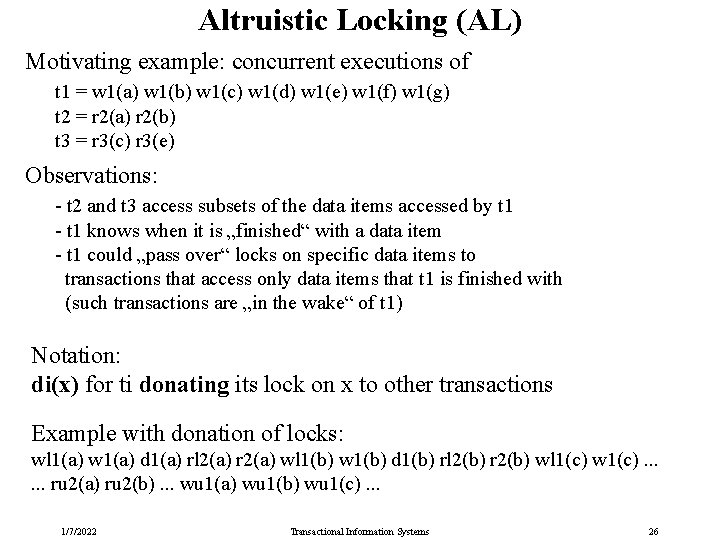
Altruistic Locking (AL) Motivating example: concurrent executions of t 1 = w 1(a) w 1(b) w 1(c) w 1(d) w 1(e) w 1(f) w 1(g) t 2 = r 2(a) r 2(b) t 3 = r 3(c) r 3(e) Observations: - t 2 and t 3 access subsets of the data items accessed by t 1 - t 1 knows when it is „finished“ with a data item - t 1 could „pass over“ locks on specific data items to transactions that access only data items that t 1 is finished with (such transactions are „in the wake“ of t 1) Notation: di(x) for ti donating its lock on x to other transactions Example with donation of locks: wl 1(a) w 1(a) d 1(a) rl 2(a) r 2(a) wl 1(b) w 1(b) d 1(b) rl 2(b) r 2(b) wl 1(c) w 1(c). . . ru 2(a) ru 2(b). . . wu 1(a) wu 1(b) wu 1(c). . . 1/7/2022 Transactional Information Systems 26

Additional Locking Rules for AL AL 1: Once ti has donated a lock on x, it can no longer access x. AL 2: After ti has donated a lock x, ti must eventually unlock x. AL 3: ti and tj can simultaneously hold conflicting locks only if ti has donated its lock on x. Definition 4. 27: (i) pj(x) is in the wake of ti (i j) in s if di(x) <s pj(x) <s oui(x). (ii) tj is in the wake of ti if some operation of tj is in the wake of ti. tj is completely in the wake of ti if all its operations are in the wake of ti. (iii) tj is indebted to ti in s if there are steps oi(x), di(x), pj(x) s. t. pj(x) is in the wake of ti and ( pj(x) and oi(x) are in conflict or there is qk(x) conflicting with both pj(x) and oi(x) <s qk(x) <s pj(x). AL 4: When tj is indebted to ti, tj must remain completely in the wake of ti. AL: 1/7/2022 locking with rules LR 1 - LR 4, two-phase property, donations, and rules AL 1 - AL 4. Transactional Information Systems 27

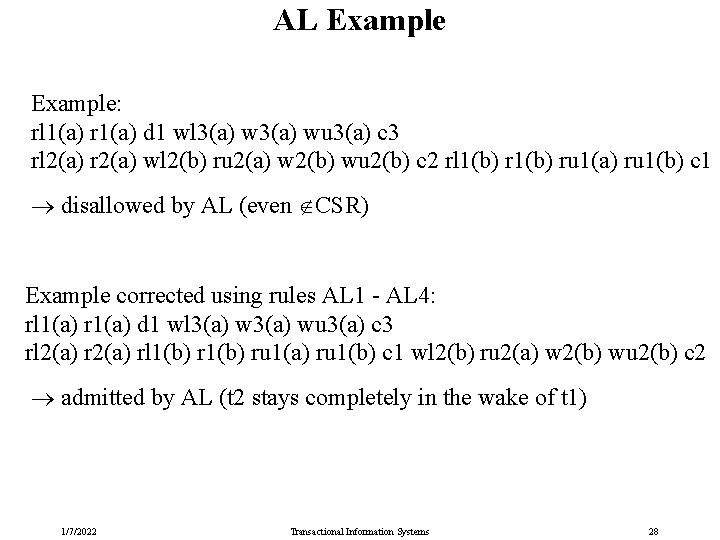
AL Example: rl 1(a) r 1(a) d 1 wl 3(a) wu 3(a) c 3 rl 2(a) r 2(a) wl 2(b) ru 2(a) w 2(b) wu 2(b) c 2 rl 1(b) ru 1(a) ru 1(b) c 1 disallowed by AL (even CSR) Example corrected using rules AL 1 - AL 4: rl 1(a) r 1(a) d 1 wl 3(a) wu 3(a) c 3 rl 2(a) rl 1(b) ru 1(a) ru 1(b) c 1 wl 2(b) ru 2(a) w 2(b) wu 2(b) c 2 admitted by AL (t 2 stays completely in the wake of t 1) 1/7/2022 Transactional Information Systems 28

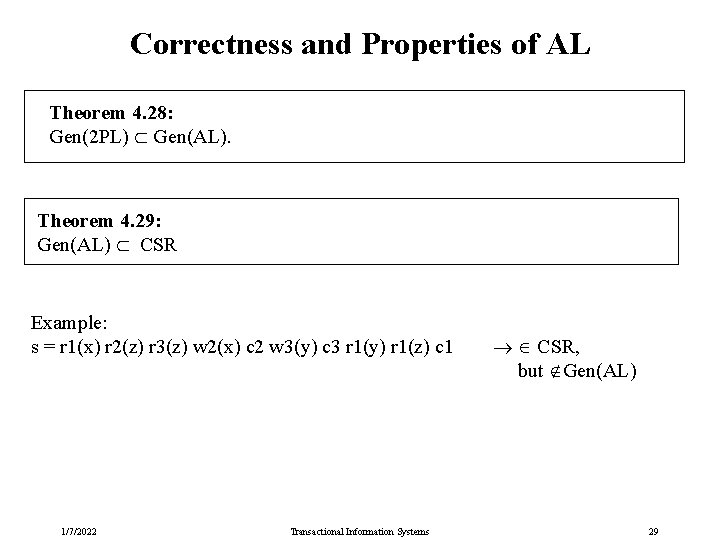
Correctness and Properties of AL Theorem 4. 28: Gen(2 PL) Gen(AL). Theorem 4. 29: Gen(AL) CSR Example: s = r 1(x) r 2(z) r 3(z) w 2(x) c 2 w 3(y) c 3 r 1(y) r 1(z) c 1 1/7/2022 Transactional Information Systems CSR, but Gen(AL) 29

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 3. 1 Introduction • 4. 3. 2 Two-Phase Locking (2 PL) • 4. 3. 3 Deadlock Handling • 4. 3. 4 Variants of 2 PL • 4. 3. 5 Ordered Sharing of Locks (O 2 PL) • 4. 3. 6 Altruistic Locking (AL) • 4. 3. 7 Non-Two-Phase Locking (WTL, RWTL) • 4. 3. 8 Geometry of Locking • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 30

(Write-only) Tree Locking a b Motivating example: concurrent executions of transactions with access patterns that comply with organizing data items into a virtual tree t 1 = w 1(a) w 1(b) w 1(d) w 1(e) w 1(i) w 1(k) t 2 = w 2(a) w 2(b) w 2(c) w 2(d) w 2(h) c f g d e h i j k Definition 4. 30 (write-only tree locking (WTL)): Under the write-only tree locking protocol (WTL) lock requests and releases must obey LR 1 - LR 4 and the following additional rules: WTL 1: A lock on a node x other than the tree root can be acquired only if the transaction already holds a lock on the parent of x. WTL 2: After a wui(x) no further wli(x) is allowed (on the same x). Example: wl 1(a) wl 1(b) wu 1(a) w 1(b) wl 2(a) wl 1(d) wu 1(d) wl 1(e) wu 1(b) w 1(e) wl 2(b) wu 2(a) w 2(b). . . 1/7/2022 Transactional Information Systems 31

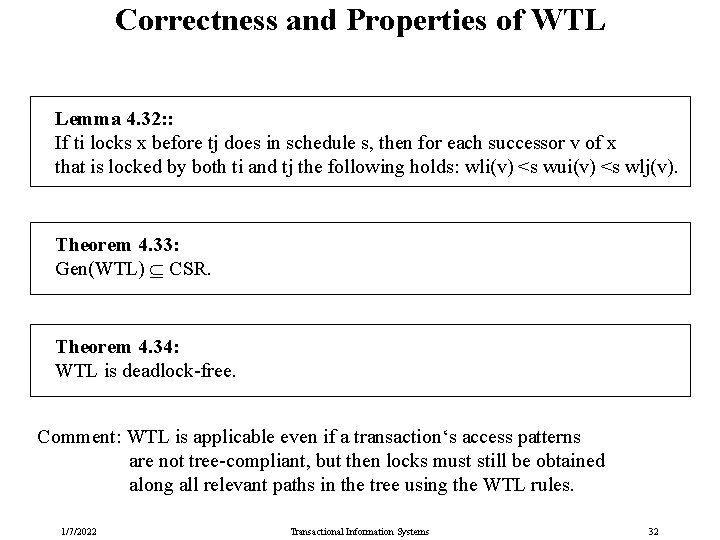
Correctness and Properties of WTL Lemma 4. 32: : If ti locks x before tj does in schedule s, then for each successor v of x that is locked by both ti and tj the following holds: wli(v) <s wui(v) <s wlj(v). Theorem 4. 33: Gen(WTL) CSR. Theorem 4. 34: WTL is deadlock-free. Comment: WTL is applicable even if a transaction‘s access patterns are not tree-compliant, but then locks must still be obtained along all relevant paths in the tree using the WTL rules. 1/7/2022 Transactional Information Systems 32

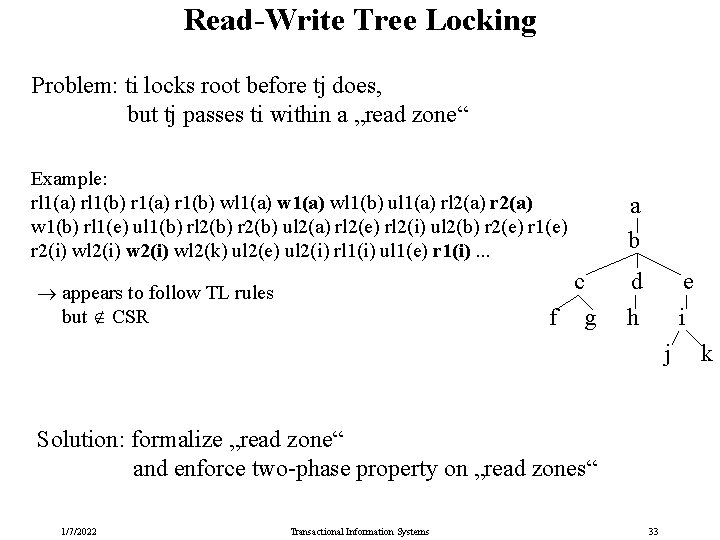
Read-Write Tree Locking Problem: ti locks root before tj does, but tj passes ti within a „read zone“ Example: rl 1(a) rl 1(b) r 1(a) r 1(b) wl 1(a) wl 1(b) ul 1(a) rl 2(a) r 2(a) w 1(b) rl 1(e) ul 1(b) rl 2(b) r 2(b) ul 2(a) rl 2(e) rl 2(i) ul 2(b) r 2(e) r 1(e) r 2(i) wl 2(k) ul 2(e) ul 2(i) rl 1(i) ul 1(e) r 1(i). . . a b c appears to follow TL rules but CSR f g d e h i j Solution: formalize „read zone“ and enforce two-phase property on „read zones“ 1/7/2022 Transactional Information Systems 33 k

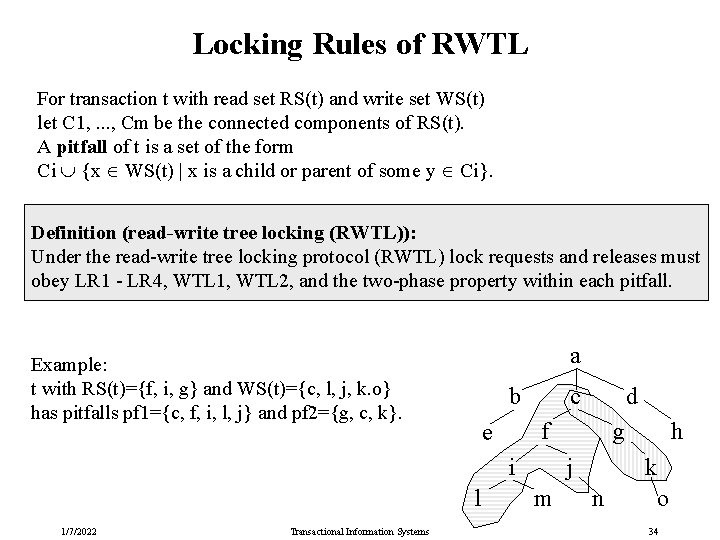
Locking Rules of RWTL For transaction t with read set RS(t) and write set WS(t) let C 1, . . . , Cm be the connected components of RS(t). A pitfall of t is a set of the form Ci {x WS(t) | x is a child or parent of some y Ci}. Definition (read-write tree locking (RWTL)): Under the read-write tree locking protocol (RWTL) lock requests and releases must obey LR 1 - LR 4, WTL 1, WTL 2, and the two-phase property within each pitfall. Example: t with RS(t)={f, i, g} and WS(t)={c, l, j, k. o} has pitfalls pf 1={c, f, i, l, j} and pf 2={g, c, k}. a b c f e i l 1/7/2022 Transactional Information Systems d g j m n h k o 34

Correctness and Generalization of RWTL Theorem 4. 37: Gen (RWTL) CSR. RWTL can be generalized for a DAG organization of data items into a DAG locking protocol with the following additional rule: ti is allowed to lock data item x only if holds locks on a majority of the predecessors of x. 1/7/2022 Transactional Information Systems 35

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 4 Non-Locking Schedulers • 4. 4. 1 Timestamp Ordering • 4. 4. 2 Serialization-Graph Testing • 4. 4. 3 Optimistic Protocols • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 36

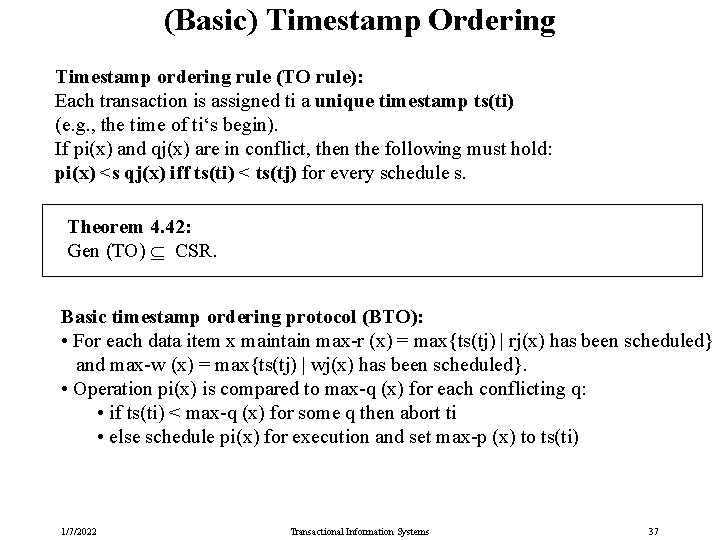
(Basic) Timestamp Ordering Timestamp ordering rule (TO rule): Each transaction is assigned ti a unique timestamp ts(ti) (e. g. , the time of ti‘s begin). If pi(x) and qj(x) are in conflict, then the following must hold: pi(x) <s qj(x) iff ts(ti) < ts(tj) for every schedule s. Theorem 4. 42: Gen (TO) CSR. Basic timestamp ordering protocol (BTO): • For each data item x maintain max-r (x) = max{ts(tj) | rj(x) has been scheduled} and max-w (x) = max{ts(tj) | wj(x) has been scheduled}. • Operation pi(x) is compared to max-q (x) for each conflicting q: • if ts(ti) < max-q (x) for some q then abort ti • else schedule pi(x) for execution and set max-p (x) to ts(ti) 1/7/2022 Transactional Information Systems 37

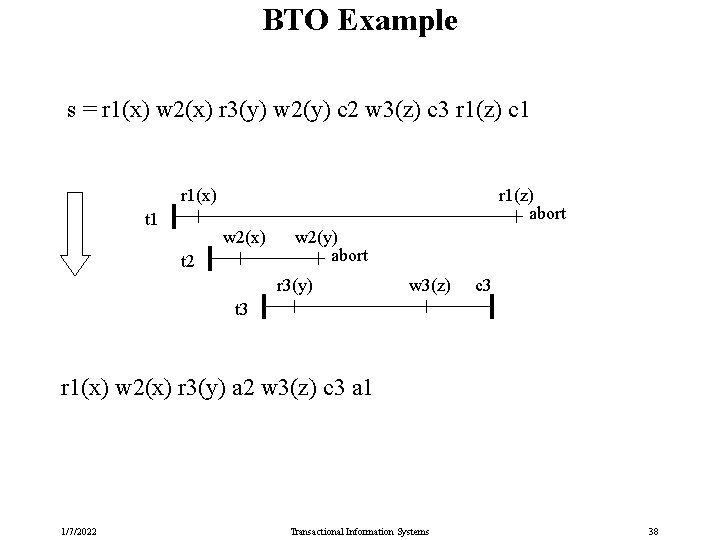
BTO Example s = r 1(x) w 2(x) r 3(y) w 2(y) c 2 w 3(z) c 3 r 1(z) c 1 r 1(x) t 1 r 1(z) abort w 2(x) t 2 w 2(y) abort r 3(y) w 3(z) c 3 t 3 r 1(x) w 2(x) r 3(y) a 2 w 3(z) c 3 a 1 1/7/2022 Transactional Information Systems 38

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 4 Non-Locking Schedulers • 4. 4. 1 Timestamp Ordering • 4. 4. 2 Serialization-Graph Testing • 4. 4. 3 Optimistic Protocols • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 39

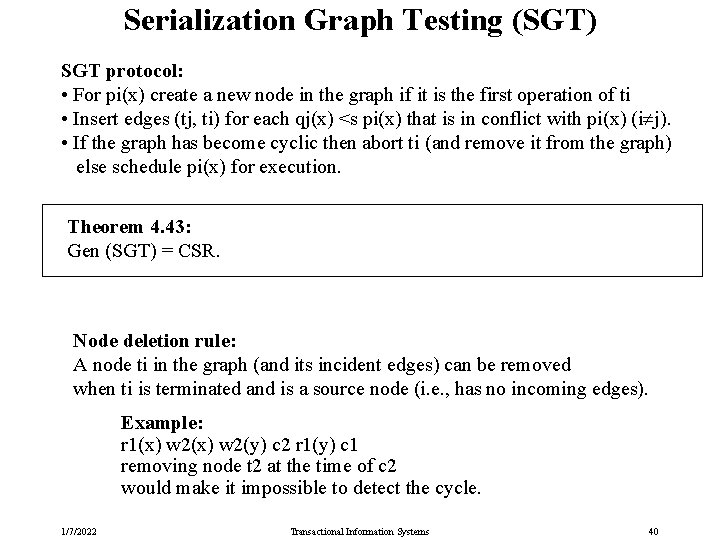
Serialization Graph Testing (SGT) SGT protocol: • For pi(x) create a new node in the graph if it is the first operation of ti • Insert edges (tj, ti) for each qj(x) <s pi(x) that is in conflict with pi(x) (i j). • If the graph has become cyclic then abort ti (and remove it from the graph) else schedule pi(x) for execution. Theorem 4. 43: Gen (SGT) = CSR. Node deletion rule: A node ti in the graph (and its incident edges) can be removed when ti is terminated and is a source node (i. e. , has no incoming edges). Example: r 1(x) w 2(y) c 2 r 1(y) c 1 removing node t 2 at the time of c 2 would make it impossible to detect the cycle. 1/7/2022 Transactional Information Systems 40

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 4 Non-Locking Schedulers • 4. 4. 1 Timestamp Ordering • 4. 4. 2 Serialization-Graph Testing • 4. 4. 3 Optimistic Protocols • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 41

Optimistic Protocols Motivation: conflicts are infrequent Approach: divide each transaction t into three phases: read phase: execute transaction with writes into private workspace validation phase (certifier): upon t‘s commit request test if schedule remains CSR if t is committed now based on t‘s read set RS(t) and write set WS(t) write phase: upon successful validation transfer the workspace contents into the database (deferred writes) otherwise abort t (i. e. , discard workspace) 1/7/2022 Transactional Information Systems 42

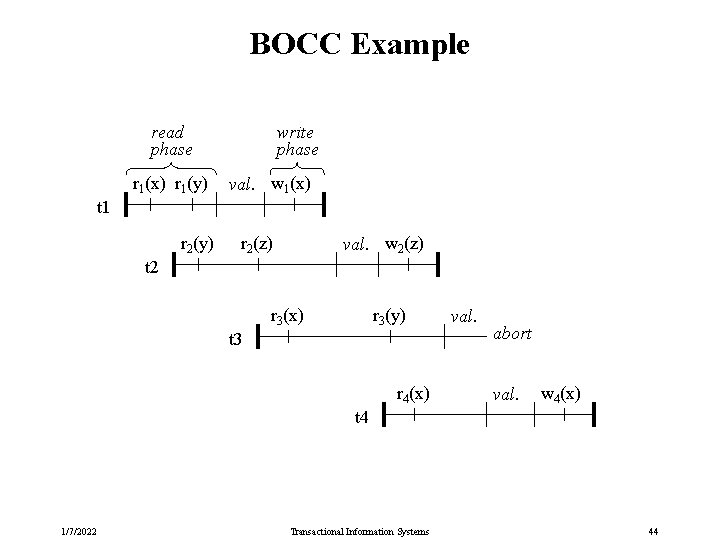
Backward-oriented Optimistic CC (BOCC) Execute a transaction‘s validation and write phase together as a critical section: while ti being in the val-write phase, no other tk can enter its val-write phase BOCC validation of tj: compare tj to all previously committed ti accept tj if one of the following holds • ti has ended before tj has started, or • RS(tj) WS(ti) = and ti has validated before tj Theorem 4. 46: Gen (BOCC) CSR. Proof: Assume that G(s) is acyclic. Adding a newly validated transaction can insert only edges into the new node, but no outgoing edges (i. e. , the new node is last in the serialization order). 1/7/2022 Transactional Information Systems 43

BOCC Example read phase r 1(x) r 1(y) write phase val. w 1(x) t 1 r 2(y) r 2(z) val. w 2(z) t 2 r 3(x) r 3(y) t 3 r 4(x) val. abort val. w 4(x) t 4 1/7/2022 Transactional Information Systems 44

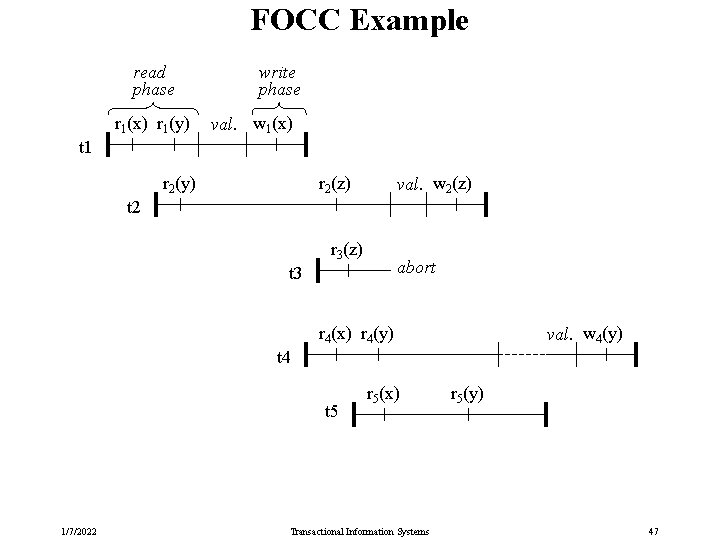
Forward-oriented Optimistic CC (FOCC) Execute a transaction‘s val-write phase as a strong critical section: while ti being in the val-write phase, no other tk can perform any steps. FOCC validation of tj: compare tj to all concurrently active ti (which must be in their read phase) accept tj if WS(tj) RS*(ti) = where RS*(ti) is the current read set of ti Remarks: • FOCC is much more flexible than BOCC: upon unsuccessful validation of tj it has three options: • abort tj • abort one of the active ti for which RS*(ti) and WS(tj) intersect • wait and retry the validation of tj later (after the commit of the intersecting ti) • Read-only transactions do not need to validate at all. 1/7/2022 Transactional Information Systems 45

Correctness of FOCC Theorem 4. 47: Gen (FOCC) CSR. Proof: Assume that G(s) has been acyclic and that validating tj would create a cycle. So tj would have to have an outgoing edge to an already committed tk. However, for all previously committed tk the following holds: 1. If tk was committed before tj started, then no edge (tj, tk) is possible. 2. If tj was in its read phase when tk validated, then WS(tk) must be disjoint with RS*(tj) and all later reads of tj and all writes of tj must follow tk (because of the strong critical section); so neither a wr nor a ww/rw edge (tj, tk) is possible. 1/7/2022 Transactional Information Systems 46

FOCC Example read phase r 1(x) r 1(y) write phase val. w 1(x) t 1 r 2(y) r 2(z) val. w 2(z) t 2 r 3(z) abort t 3 r 4(x) r 4(y) val. w 4(y) t 4 t 5 1/7/2022 r 5(x) Transactional Information Systems r 5(y) 47

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 48

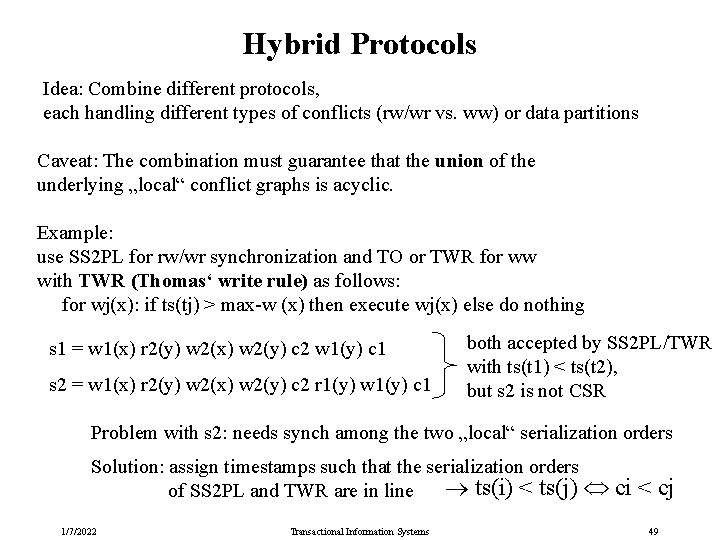
Hybrid Protocols Idea: Combine different protocols, each handling different types of conflicts (rw/wr vs. ww) or data partitions Caveat: The combination must guarantee that the union of the underlying „local“ conflict graphs is acyclic. Example: use SS 2 PL for rw/wr synchronization and TO or TWR for ww with TWR (Thomas‘ write rule) as follows: for wj(x): if ts(tj) > max-w (x) then execute wj(x) else do nothing s 1 = w 1(x) r 2(y) w 2(x) w 2(y) c 2 w 1(y) c 1 s 2 = w 1(x) r 2(y) w 2(x) w 2(y) c 2 r 1(y) w 1(y) c 1 both accepted by SS 2 PL/TWR with ts(t 1) < ts(t 2), but s 2 is not CSR Problem with s 2: needs synch among the two „local“ serialization orders Solution: assign timestamps such that the serialization orders ts(i) < ts(j) of SS 2 PL and TWR are in line 1/7/2022 Transactional Information Systems ci < cj 49

Chapter 4: Concurrency Control Algorithms • 4. 2 General Scheduler Design • 4. 3 Locking Schedulers • 4. 4 Non-Locking Schedulers • 4. 5 Hybrid Protocols • 4. 6 Lessons Learned 1/7/2022 Transactional Information Systems 50

Lessons Learned • S 2 PL is the most versatile and robust protocol and widely used in practice • Knowledge about specifically restricted access patterns facilitates non-two-phase locking protocols (e. g. , TL, AL) • O 2 PL and SGT are more powerful but have more overhead • FOCC can be attractive for specific workloads • Hybrid protocols are conceivable but non-trivial 1/7/2022 Transactional Information Systems 51