CHAPTER 30 Internet Management Albert Yifan Jianxin Huaidong

CHAPTER 30 Internet Management Albert Yifan Jianxin Huaidong Lai Yee Daniel 30. 1, 2, 3 30. 4, 5, 6, 7 30. 8 30. 9 30. 10 30. 11, 12, 13 1

Internet Management Activities in Internet management: Debug problems · Control routing · Find computer that violate protocol standard · 2
Network Management Originally, many wide area networks included management protocols as part of their link level protocols. Advantage: Managers were often able to control switches even if higher level protocols failed. 3

Internet management differs from network management A single manager can control heterogeneous devices including IP routers, bridges, modems, work-stations, and printers. · The controlled entities may not share a common link level protocol. · The set of machines a manager controls may lie at arbitrary points in an internet. · 4
Internet management operates at the application level Advantages: • One set of protocol can be used for all networks. • Same protocols can be used for all managed devices. • A manager can control the routers across an entire TCP/IP internet without having direct attached to every physical network or router. Disadvantage: • If the operating system, IP software, or transport protocol software does not work correctly, the manager may not be able to contact a router that needs managing. 5
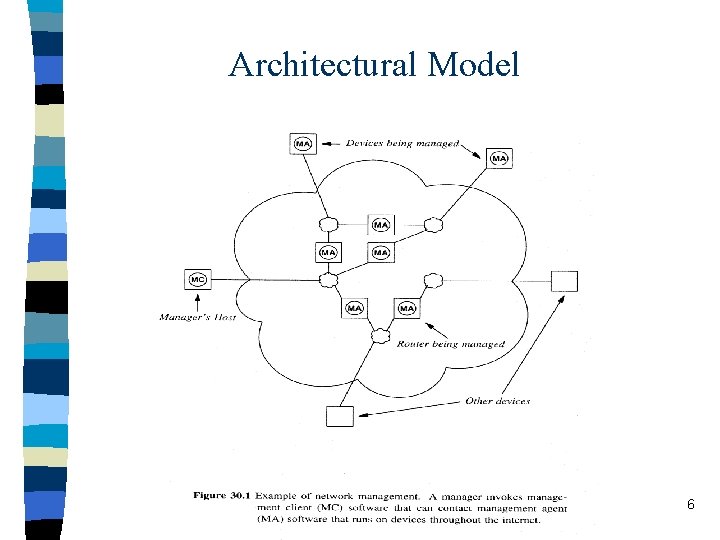
Architectural Model 6
Architectural Model • Client software usually runs on the manager’s workstation. • Each participating router or host runs a server program called management agent. • Most managers only control devices at their local sites; a large site may have multiple managers. Internet management software uses an authentication mechanism to ensure only authorized managers can access or control a particular device. 7
Protocol Framework It’s all about management information! n SNMP How to exchange? n MIB How to store and operate? n SMI How to define and identify? n ASN. 1 Formal notation used by SMI. 8
SNMP v 3 – how to communicate? n Stands for Simple Network Management Protocol version 3 n A standard Network Management Protocol n Defines: - message format, form of names and addresses - how to use transport protocol - set of operations and their meaning - approach is minimalistic 9
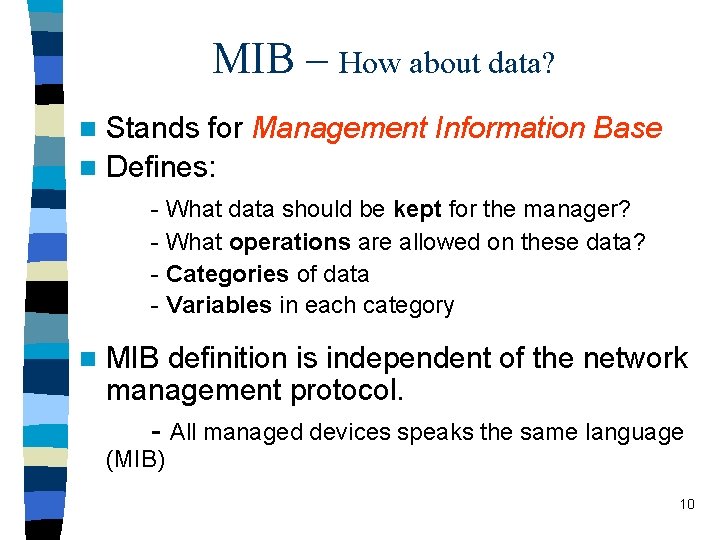
MIB – How about data? Stands for Management Information Base n Defines: n - What data should be kept for the manager? - What operations are allowed on these data? - Categories of data - Variables in each category n MIB definition is independent of the network management protocol. - All managed devices speaks the same language (MIB) 10
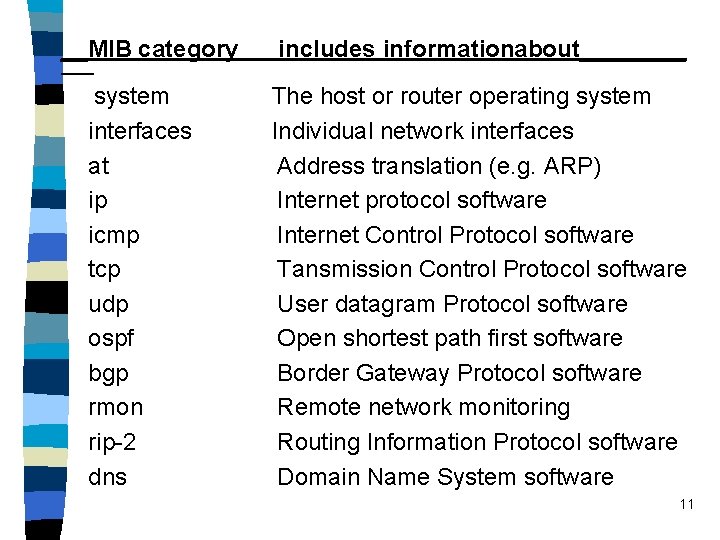
__MIB category system interfaces at ip icmp tcp udp ospf bgp rmon rip-2 dns includes informationabout____ The host or router operating system Individual network interfaces Address translation (e. g. ARP) Internet protocol software Internet Control Protocol software Tansmission Control Protocol software User datagram Protocol software Open shortest path first software Border Gateway Protocol software Remote network monitoring Routing Information Protocol software Domain Name System software 11
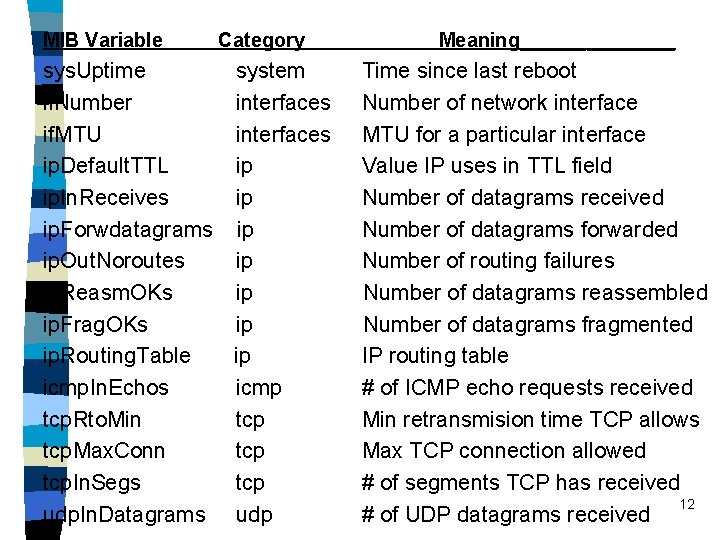
MIB Variable Category sys. Uptime system if. Number interfaces if. MTU interfaces ip. Default. TTL ip ip. In. Receives ip ip. Forwdatagrams ip ip. Out. Noroutes ip ip. Reasm. OKs ip ip. Frag. OKs ip ip. Routing. Table ip icmp. In. Echos icmp tcp. Rto. Min tcp. Max. Conn tcp. In. Segs tcp udp. In. Datagrams udp Meaning_______ Time since last reboot Number of network interface MTU for a particular interface Value IP uses in TTL field Number of datagrams received Number of datagrams forwarded Number of routing failures Number of datagrams reassembled Number of datagrams fragmented IP routing table # of ICMP echo requests received Min retransmision time TCP allows Max TCP connection allowed # of segments TCP has received 12 # of UDP datagrams received
MIB variables n Each variable can be stored as - A single integer - A complex structure e. g. , an entire Routing Table Also defines table entries. n Presentation only has logical meaning. n - Router may use different internal data structures 13
SMI – rules to define and identify variables Stands for Structure of Management Information n Specifies: - What variable types are allowed? - What naming rules should be followed? - How to refer to the tables of values? e. g. , the IP routing table n 14

ASN. 1 – a formal notation used by SMI Stands for ISO’s Abstract Syntax Notation 1 n A formal notation of defining variable names and types n - In documents: human can read - In communication: compact encoded representation n Benefits: - Makes the form and contents of variables unambiguous. - Simplifies the implementation of protocols - guarantees interoperability 15
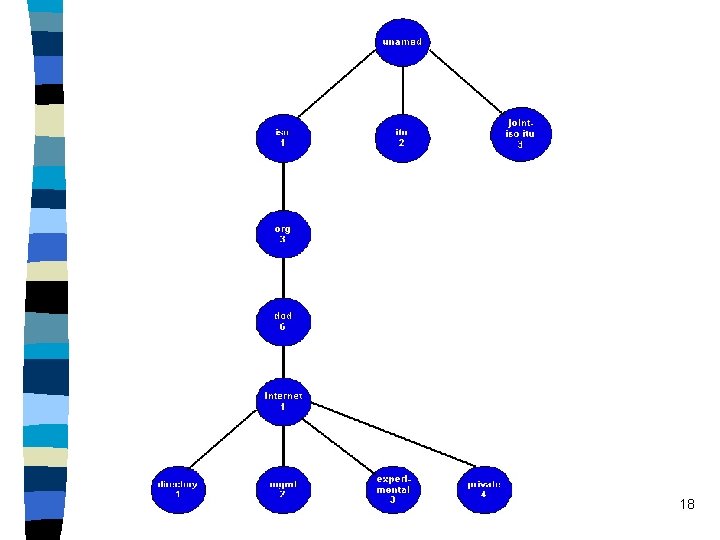
30. 8 Structure And Representation Of MIB Object Names --- Jianxin n Object Identifier Namespace: – Names used for MIB variables are taken from the object identifier namespace administered by ISO and ITU. – The object identifier namespace is absolute, meaning that names are structured to make them globally unique. 16
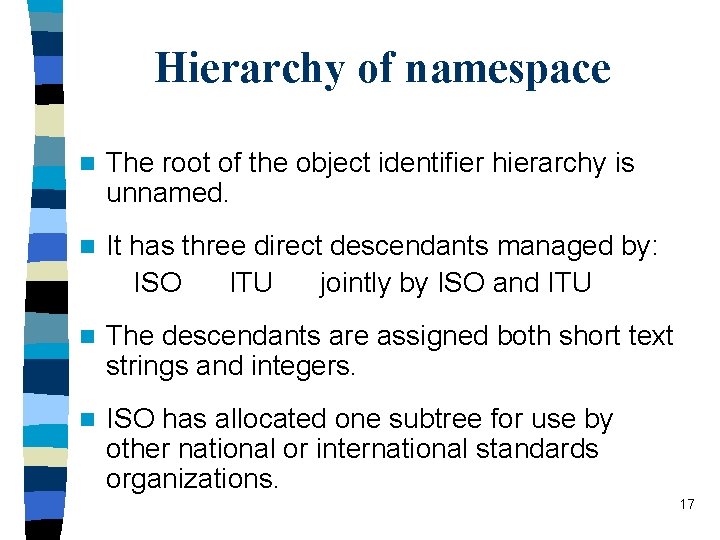
Hierarchy of namespace n The root of the object identifier hierarchy is unnamed. n It has three direct descendants managed by: ISO ITU jointly by ISO and ITU n The descendants are assigned both short text strings and integers. n ISO has allocated one subtree for use by other national or international standards organizations. 17
18
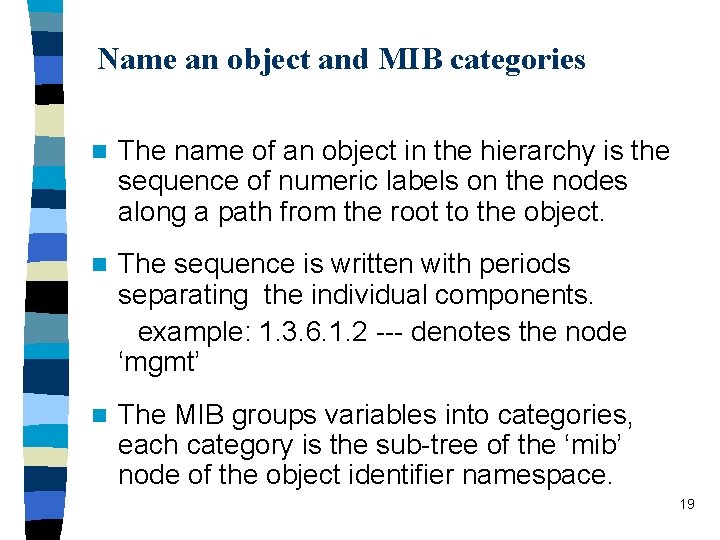
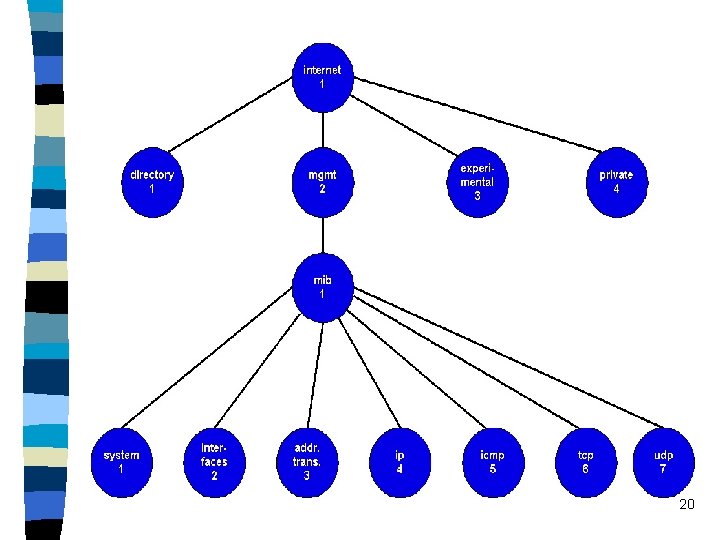
Name an object and MIB categories n The name of an object in the hierarchy is the sequence of numeric labels on the nodes along a path from the root to the object. n The sequence is written with periods separating the individual components. example: 1. 3. 6. 1. 2 --- denotes the node ‘mgmt’ n The MIB groups variables into categories, each category is the sub-tree of the ‘mib’ node of the object identifier namespace. 19
20

Simple category naming examples The category labeled ip has been assigned the value 4. n The names of all MIB variables corresponding to ip have an identifier that begins with the prefix: 1. 3. 6. 1. 2. 1. 4 The textual label would be: iso. org. dod. internet. mgmt. mib. ip n When network management protocols use names of MIB variables in messages, each name has a suffix appended. For simple variables, the suffix is 0. n 21
Complex example How about the variable ip. Addr. Table n A list of the IP addresses for each network interface n It’s a sub-tree under ip node, with prefix: n iso. org. dod. internet. mgmt. mib. ip. Addr. Table How to represent such data structures. n MIB defines a uniform, virtual interface to access data n 22
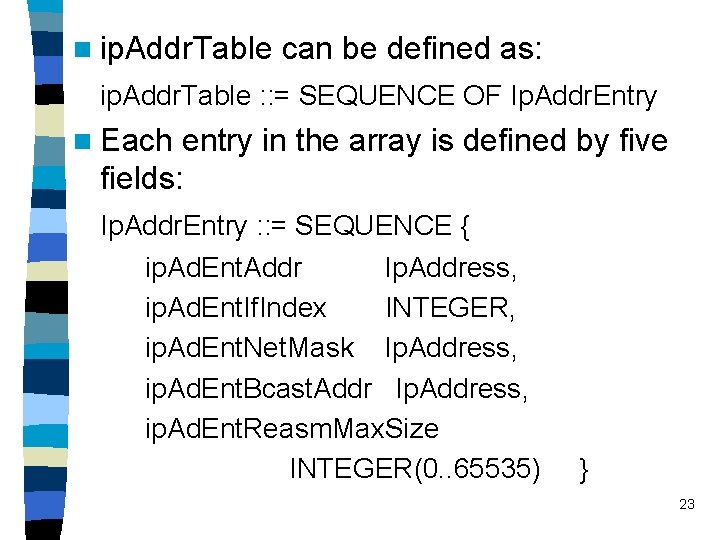
n ip. Addr. Table can be defined as: ip. Addr. Table : : = SEQUENCE OF Ip. Addr. Entry n Each entry in the array is defined by five fields: Ip. Addr. Entry : : = SEQUENCE { ip. Ad. Ent. Addr Ip. Address, ip. Ad. Ent. If. Index INTEGER, ip. Ad. Ent. Net. Mask Ip. Address, ip. Ad. Ent. Bcast. Addr Ip. Address, ip. Ad. Ent. Reasm. Max. Size INTEGER(0. . 65535) } 23
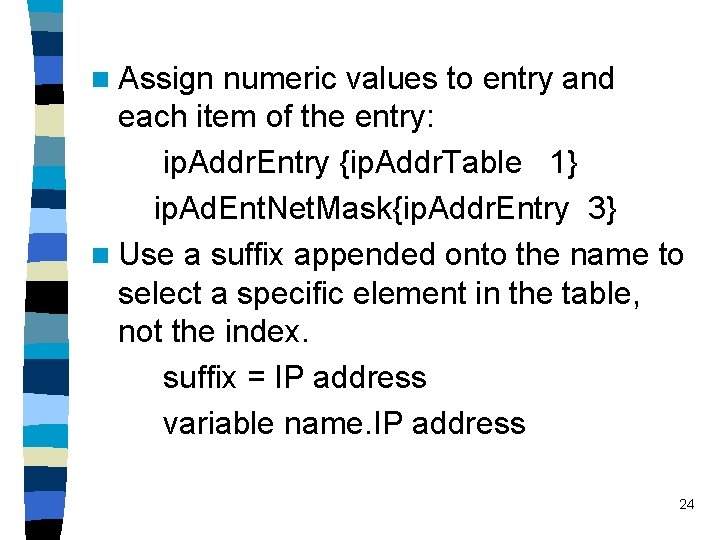
n Assign numeric values to entry and each item of the entry: ip. Addr. Entry {ip. Addr. Table 1} ip. Ad. Ent. Net. Mask{ip. Addr. Entry 3} n Use a suffix appended onto the name to select a specific element in the table, not the index. suffix = IP address variable name. IP address 24

Simple Network Management Protocol (SNMP) Huaidong Meng Instructor: Dr. Sharon Hall 25
Simple Network Management protocol n Network Management protocol: – specify communication between client program a network manager invoked and server program executing on a host or router. – which defines the form and meaning of message exchanged – representation of names and values of message – define administrative relationships among routers between managed. 26
Network Management Protocol n Allow the manager – – n Reboot the system Add or delete the router Disable or enable a particular network interface Remove cached address binding The main disadvantage: the resulting complexity – For example, the command to delete a routing table entry differs from the command to disable an interface. 27
SNMP takes an interesting alternative approach to network management n casts all operations in a fetch-store paradigm, instead of defining a large set of commands: – Stability • Its definition remains fixed. – Simple to implement, understand, and debug • It avoids the complexity of having special cases for each command. – Flexible • Accommodate arbitrary commands in an elegant framework 28

SNMP commands n get-request fetch a value from a specific variable n get-next-request fetch a value without knowing its exact name n get bulk-request n Response fetch a large volume of data n set-request store a value in a specific variable n inform-request reference to a third-party data n snmpv 2 -trap reply triggered by an event n Report undefined at present a response to any of above request 29

Searching Table Using Names n get-next-request – Allows a client to iterate through a table by supplies a prefix of a valid object identifier, without knowing how many items the table contains. – The server returns a network mask field of the first entry in ip. Addr. Table, and the client uses the full object identifier returned by the server to request the next item in the table. – See page 566 for the example 30

SNMP Message Format SNMPv 3 Message : : = SEQUENCE { msg. Version INTEGER (0. . 2147483647), msg. Global. Data Header. Data, msg. Security. Parameters OCTET STRING, msg. Data Scoped. Pdu. Data } 31
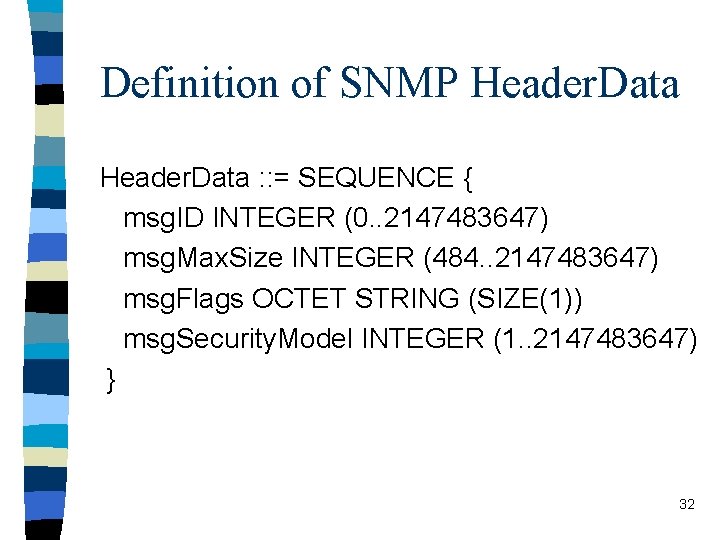
Definition of SNMP Header. Data : : = SEQUENCE { msg. ID INTEGER (0. . 2147483647) msg. Max. Size INTEGER (484. . 2147483647) msg. Flags OCTET STRING (SIZE(1)) msg. Security. Model INTEGER (1. . 2147483647) } 32
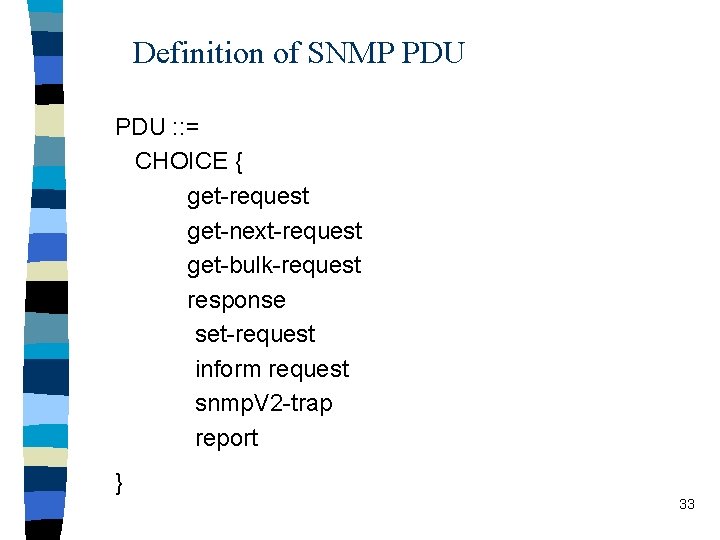
Definition of SNMP PDU : : = CHOICE { get-request get-next-request get-bulk-request response set-request inform request snmp. V 2 -trap report } 33
Internet Management -Example Encoded SNMP Message Figure 30. 11 contains an encoded get-request message for data item sys. Descr n Each term used is further defined until it can be defined by primitive data type, e. g. integer, string. -Let’s compare the message with the n specified format n Hence, the encoded items have variablelength fields 34

Internet Management -New Features In SNMPv 3 Scope: Security and administration n Goal: generality, flexibility and ease of admin. n Example new features n – – Message Authentication Privacy Authorization & View-based Access Control Remote Configuration 35
Internet Management -Summary An application level client program accesses and controls agents running on devices n SNMP is the standard TCP/IP network management protocol that uses 2 conceptual operation, fetch and store n A companion standard, MIB, defines the variables that are maintained by the agents n MIB variables are described by ASN. 1, which uses a hierarchical namespace to ensure global uniqueness n 36

THANK YOU
- Slides: 37