Chapter 3 Symmetric Key Crypto The chief forms



![RC 4 Initialization • S[] is permutation of 0, 1, . . . , RC 4 Initialization • S[] is permutation of 0, 1, . . . ,](https://slidetodoc.com/presentation_image/1fb738a95259664e60ab9452a07e81b6/image-13.jpg)
![Byte S[256] is permutation of 0, 1, . . . , 255 Byte K[N] Byte S[256] is permutation of 0, 1, . . . , 255 Byte K[N]](https://slidetodoc.com/presentation_image/1fb738a95259664e60ab9452a07e81b6/image-15.jpg)













- Slides: 72

Chapter 3: Symmetric Key Crypto The chief forms of beauty are order and symmetry… Aristotle “You boil it in sawdust: you salt it in glue: You condense it with locusts and tape: Still keeping one principal object in view To preserve its symmetrical shape. ” Lewis Carroll, The Hunting of the Snark Part 1 Cryptography 1

Symmetric Key Crypto • Stream cipher generalize One-Time Pad (OTP) – Except that key is relatively short – Key is stretched into a long keystream – Keystream is used just like a One-Time Pad • Block cipher generalized codebook – Block cipher key determines a codebook – Each key yields a different codebook – Employs both “confusion” and “diffusion” Part 1 Cryptography 2

When & Where • For applications that require encryption/decryption of a stream of data, such as – over a data communications channel or a browser/Web link, a stream cipher might be the better alternative. • For applications that deal with blocks of data, such as – file transfer, e-mail, and database, block ciphers may be more appropriate. • However, either type of cipher can be used in virtually any application.

Stream Ciphers Processes input elements continuously Key input to a pseudorandom bit generator • Produces stream of random like numbers • Unpredictable without knowing input key • XOR keystream bits output with plaintext bytes

Stream Ciphers • Once upon a time, not so very long ago… stream ciphers were the king of crypto • Today, not as popular as block ciphers • We’ll discuss two Stream Cipher Algorithms: 1. A 5/1 • Based on shift registers (LFSR) • Used in GSM mobile phone system 2. RC 4 • Based on a changing lookup table • Used in many places (i. e. WEP, WPA) Part 1 Cryptography 5

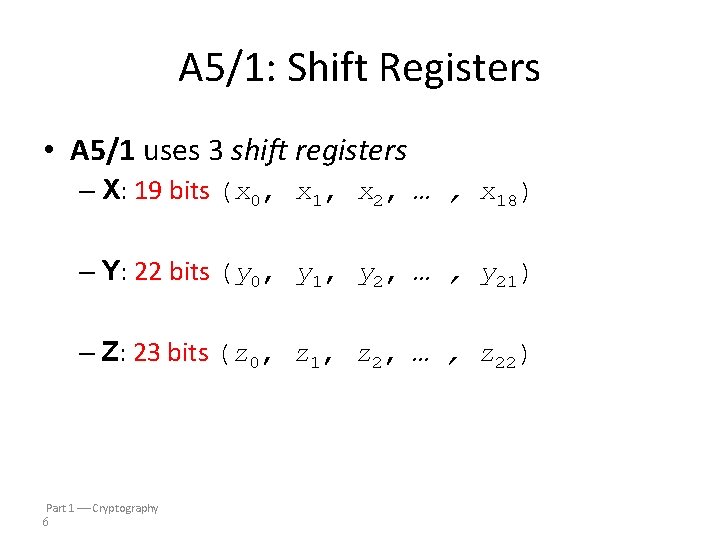
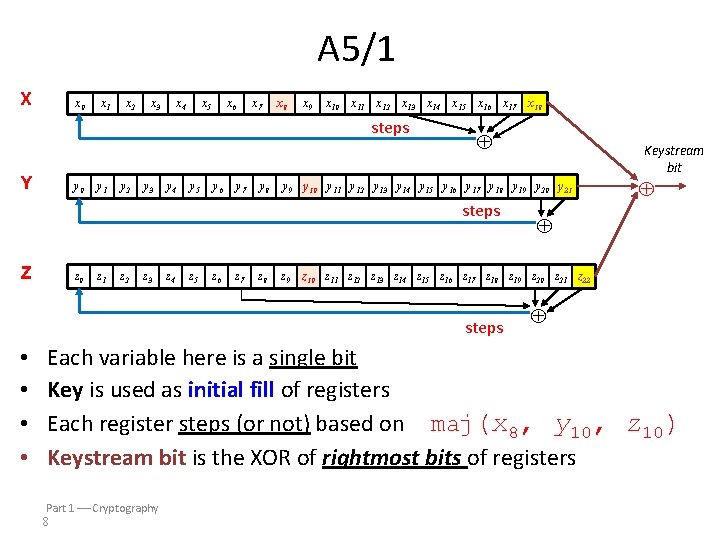
A 5/1: Shift Registers • A 5/1 uses 3 shift registers – X: 19 bits (x 0, x 1, x 2, … , x 18) – Y: 22 bits (y 0, y 1, y 2, … , y 21) – Z: 23 bits (z 0, z 1, z 2, … , z 22) Part 1 Cryptography 6

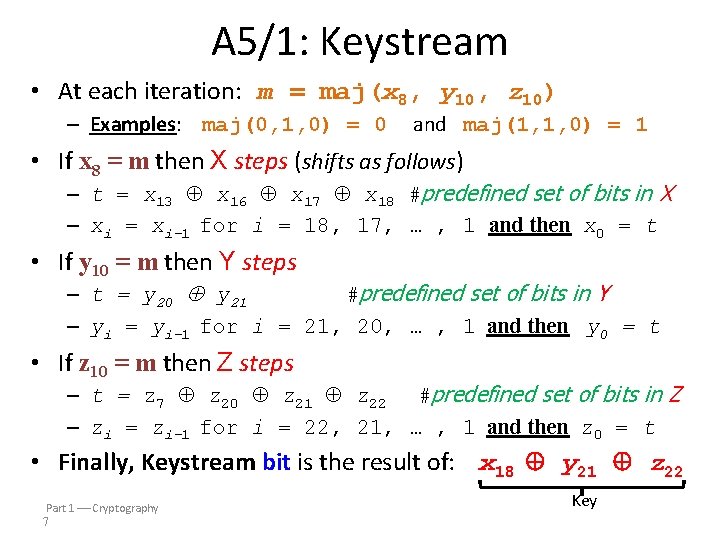
A 5/1: Keystream • At each iteration: m = maj(x 8, y 10, z 10) – Examples: maj(0, 1, 0) = 0 and maj(1, 1, 0) = 1 • If x 8 = m then X steps (shifts as follows) – t = x 13 x 16 x 17 x 18 #predefined set of bits in X – xi = xi 1 for i = 18, 17, … , 1 and then x 0 = t • If y 10 = m then Y steps – t = y 20 y 21 #predefined set of bits in Y – yi = yi 1 for i = 21, 20, … , 1 and then y 0 = t • If z 10 = m then Z steps – t = z 7 z 20 z 21 z 22 #predefined set of bits in Z – zi = zi 1 for i = 22, 21, … , 1 and then z 0 = t • Finally, Keystream bit is the result of: x 18 y 21 z 22 Part 1 Cryptography 7 Key

A 5/1 X x 0 x 1 x 2 x 3 x 4 x 5 x 6 x 7 x 8 x 9 x 10 x 11 x 12 x 13 steps Y y 0 y 1 y 2 y 3 y 4 y 5 y 6 y 7 y 8 x 14 x 15 x 16 x 17 x 18 y 9 y 10 y 11 y 12 y 13 y 14 y 15 y 16 y 17 y 18 y 19 y 20 y 21 steps Z z 0 z 1 z 2 z 3 z 4 z 5 z 6 z 7 z 8 z 9 z 10 z 11 z 12 z 13 z 14 z 15 z 16 z 17 z 18 z 19 z 20 z 21 z 22 steps • • Keystream bit Each variable here is a single bit Key is used as initial fill of registers Each register steps (or not) based on maj(x 8, y 10, z 10) Keystream bit is the XOR of rightmost bits of registers Part 1 Cryptography 8

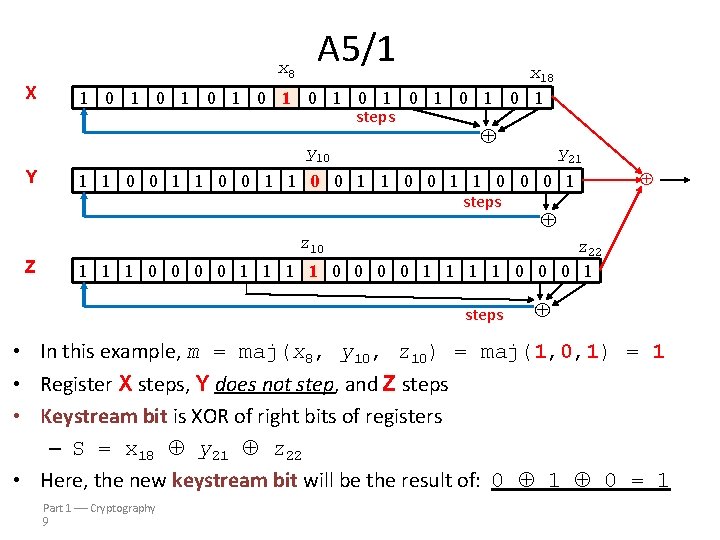
x 8 X A 5/1 x 18 1 0 1 0 1 0 1 steps y 10 Y y 21 1 1 0 0 1 1 0 0 0 1 steps z 10 Z z 22 1 1 1 0 0 0 0 1 1 1 1 0 0 0 1 steps • In this example, m = maj(x 8, y 10, z 10) = maj(1, 0, 1) = 1 • Register X steps, Y does not step, and Z steps • Keystream bit is XOR of right bits of registers – S = x 18 y 21 z 22 • Here, the new keystream bit will be the result of: 0 1 0 = 1 Part 1 Cryptography 9

Shift Register Crypto • Shift register crypto efficient in hardware • Often, slow if implemented in software • In the past, very popular • Today, more is done in software due to fast processors • Shift register crypto still used in some applications – Especially in resource-constrained devices Part 1 Cryptography 10

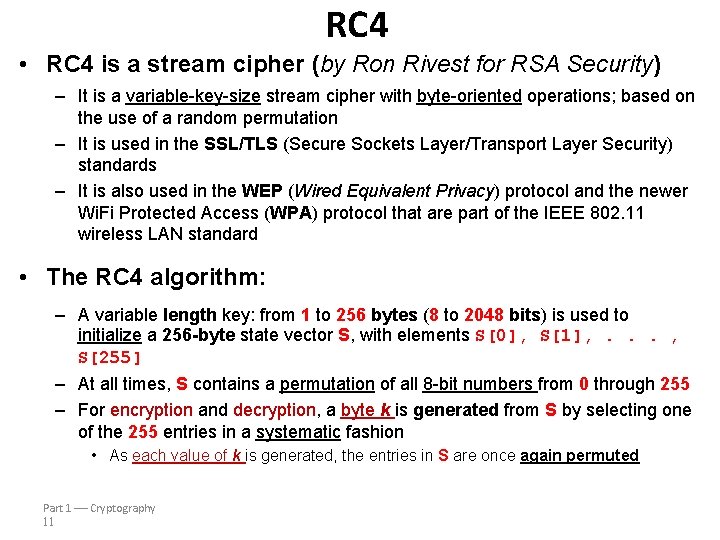
RC 4 • RC 4 is a stream cipher (by Ron Rivest for RSA Security) – It is a variable-key-size stream cipher with byte-oriented operations; based on the use of a random permutation – It is used in the SSL/TLS (Secure Sockets Layer/Transport Layer Security) standards – It is also used in the WEP (Wired Equivalent Privacy) protocol and the newer Wi. Fi Protected Access (WPA) protocol that are part of the IEEE 802. 11 wireless LAN standard • The RC 4 algorithm: – A variable length key: from 1 to 256 bytes (8 to 2048 bits) is used to initialize a 256 -byte state vector S, with elements S[0], S[1], . . . , S[255] – At all times, S contains a permutation of all 8 -bit numbers from 0 through 255 – For encryption and decryption, a byte k is generated from S by selecting one of the 255 entries in a systematic fashion • As each value of k is generated, the entries in S are once again permuted Part 1 Cryptography 11

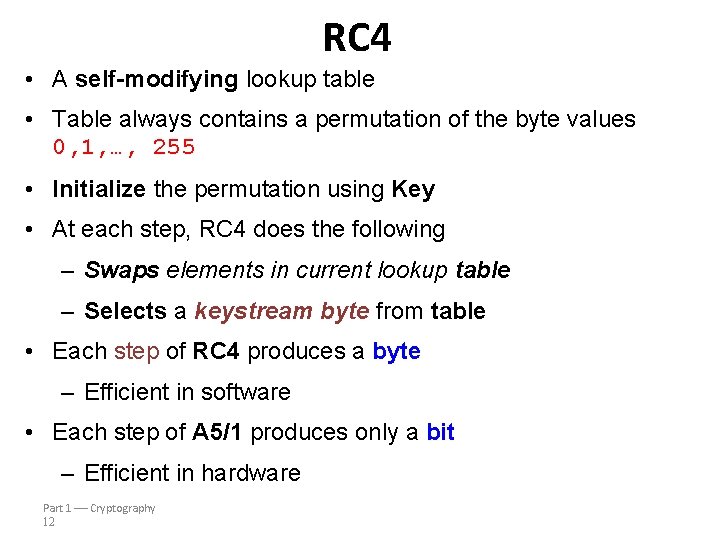
RC 4 • A self-modifying lookup table • Table always contains a permutation of the byte values 0, 1, …, 255 • Initialize the permutation using Key • At each step, RC 4 does the following – Swaps elements in current lookup table – Selects a keystream byte from table • Each step of RC 4 produces a byte – Efficient in software • Each step of A 5/1 produces only a bit – Efficient in hardware Part 1 Cryptography 12
![RC 4 Initialization S is permutation of 0 1 RC 4 Initialization • S[] is permutation of 0, 1, . . . ,](https://slidetodoc.com/presentation_image/1fb738a95259664e60ab9452a07e81b6/image-13.jpg)
RC 4 Initialization • S[] is permutation of 0, 1, . . . , 255 • K[] contains N bytes of key # Initialization forfor i = 0 ito=255 0 to 255 S[i] =i = i S[i] T[i] = K [i=mod N] mod #N is N] the #N key is length T[i] K [i the key length next i i next Initial of Permutation of S # Initial#Permutation S j =j 0 = 0 0 to 255 forfor i = 0 ito=255 j = (j + S[i] + T[i]) mod 256 swap(S[i], S[j]) next swap(S[i], i next i j = 0 i = i=j=0 Part 1 Cryptography 13

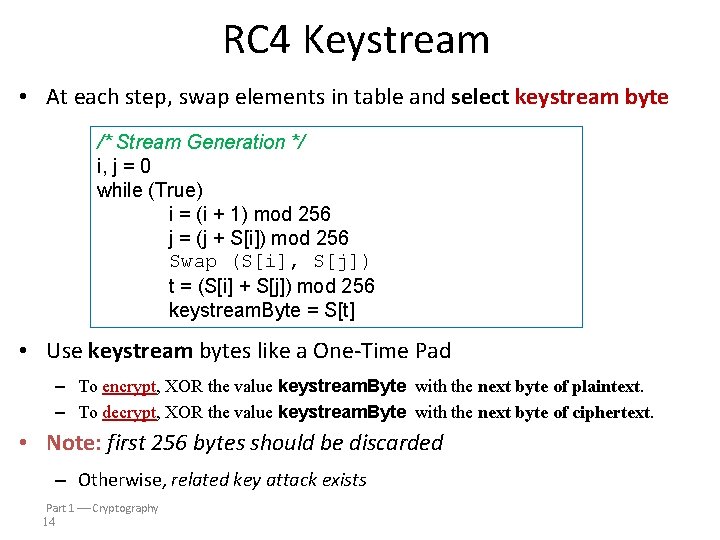
RC 4 Keystream • At each step, swap elements in table and select keystream byte i/*=Stream (i + 1)Generation mod 256 */ ji, =j =(j 0+ S[i]) mod 256 while (True) swap(S[i], i = (i. S[j]) + 1) mod 256 (j + S[i]) mod 256 t = (S[i] j += S[j]) mod 256 Swap (S[i], S[j]) keystream. Byte = S[t] t = (S[i] + S[j]) mod 256 keystream. Byte = S[t] • Use keystream bytes like a One-Time Pad – To encrypt, XOR the value keystream. Byte with the next byte of plaintext. – To decrypt, XOR the value keystream. Byte with the next byte of ciphertext. • Note: first 256 bytes should be discarded – Otherwise, related key attack exists Part 1 Cryptography 14
![Byte S256 is permutation of 0 1 255 Byte KN Byte S[256] is permutation of 0, 1, . . . , 255 Byte K[N]](https://slidetodoc.com/presentation_image/1fb738a95259664e60ab9452a07e81b6/image-15.jpg)
Byte S[256] is permutation of 0, 1, . . . , 255 Byte K[N] contains N bytes of key


Stream Ciphers: Summary • Stream ciphers were popular in the past – Efficient in hardware – Speed was needed to keep up with voice, etc. – Today, processors are fast, so software-based crypto is usually more than fast enough • Future of stream ciphers? – Shamir declared “the death of stream ciphers” – May be greatly exaggerated… Part 1 Cryptography 17

Block Ciphers Part 1 Cryptography 18

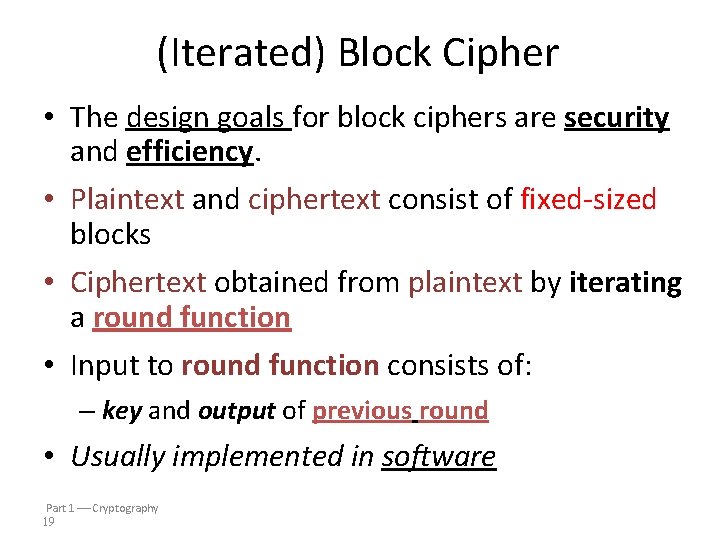
(Iterated) Block Cipher • The design goals for block ciphers are security and efficiency. • Plaintext and ciphertext consist of fixed-sized blocks • Ciphertext obtained from plaintext by iterating a round function • Input to round function consists of: – key and output of previous round • Usually implemented in software Part 1 Cryptography 19

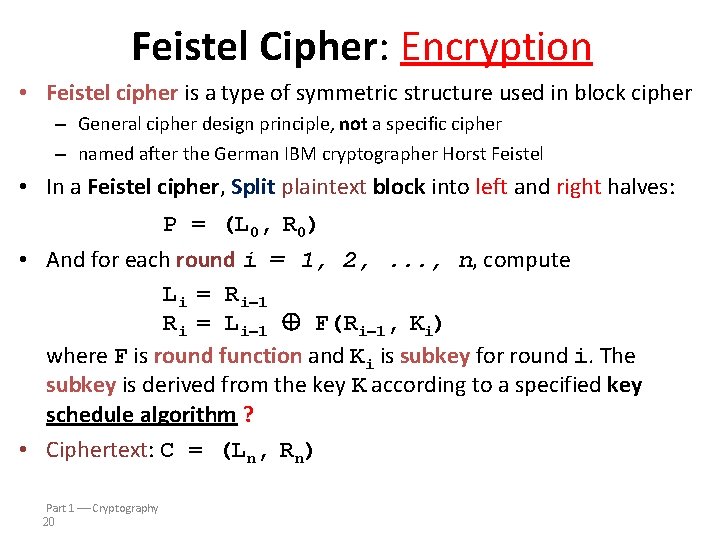
Feistel Cipher: Encryption • Feistel cipher is a type of symmetric structure used in block cipher – General cipher design principle, not a specific cipher – named after the German IBM cryptographer Horst Feistel • In a Feistel cipher, Split plaintext block into left and right halves: P = (L 0, R 0) • And for each round i = 1, 2, . . . , n, compute Li = Ri 1 Ri = Li 1 F(Ri 1, Ki) where F is round function and Ki is subkey for round i. The subkey is derived from the key K according to a specified key schedule algorithm ? • Ciphertext: C = (Ln, Rn) Part 1 Cryptography 20

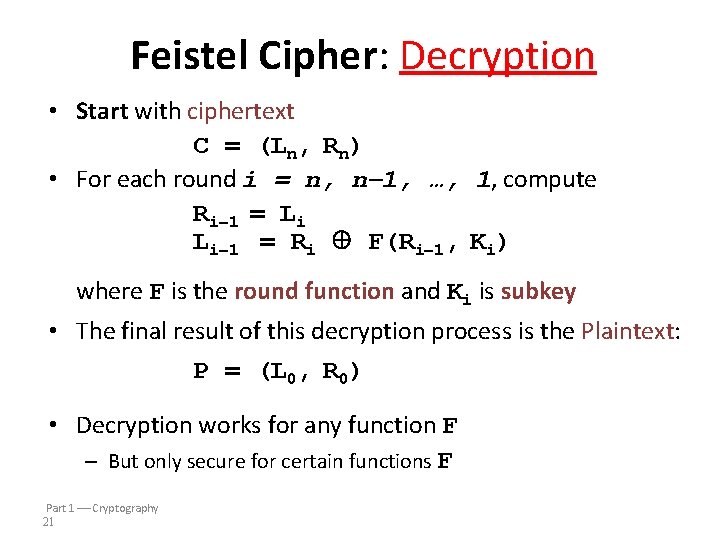
Feistel Cipher: Decryption • Start with ciphertext C = (Ln, Rn) • For each round i = n, n 1, …, 1, compute Ri 1 = Li Li 1 = Ri F(Ri 1, Ki) where F is the round function and Ki is subkey • The final result of this decryption process is the Plaintext: P = (L 0, R 0) • Decryption works for any function F – But only secure for certain functions F Part 1 Cryptography 21

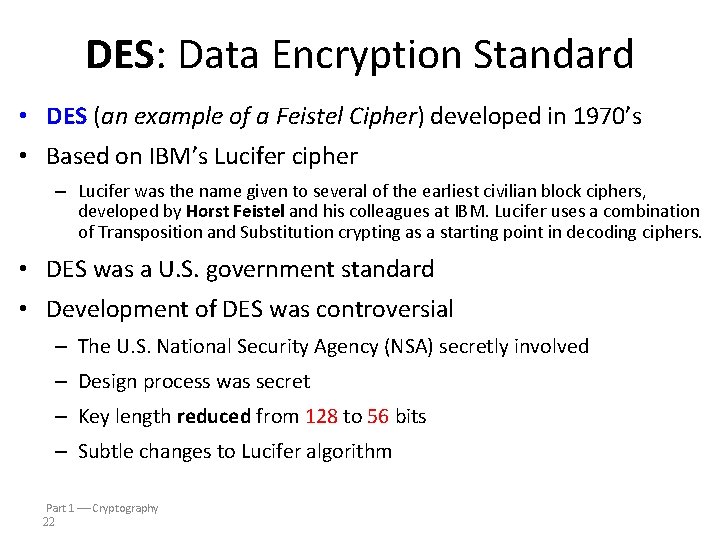
DES: Data Encryption Standard • DES (an example of a Feistel Cipher) developed in 1970’s • Based on IBM’s Lucifer cipher – Lucifer was the name given to several of the earliest civilian block ciphers, developed by Horst Feistel and his colleagues at IBM. Lucifer uses a combination of Transposition and Substitution crypting as a starting point in decoding ciphers. • DES was a U. S. government standard • Development of DES was controversial – The U. S. National Security Agency (NSA) secretly involved – Design process was secret – Key length reduced from 128 to 56 bits – Subtle changes to Lucifer algorithm Part 1 Cryptography 22

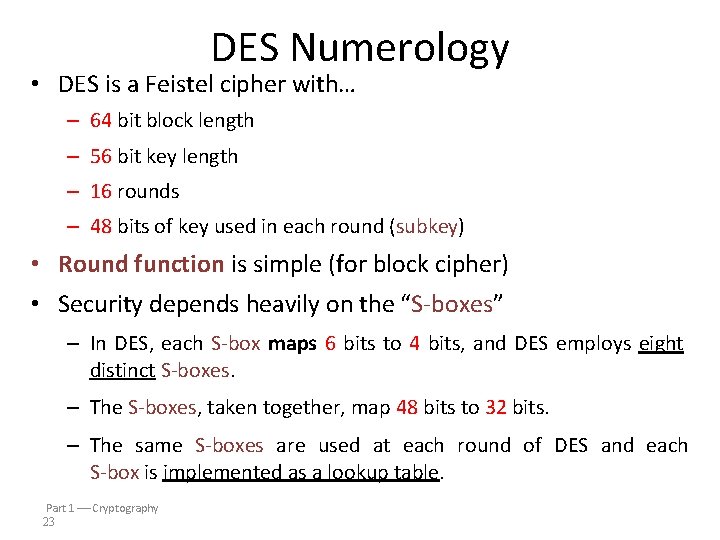
DES Numerology • DES is a Feistel cipher with… – 64 bit block length – 56 bit key length – 16 rounds – 48 bits of key used in each round (subkey) • Round function is simple (for block cipher) • Security depends heavily on the “S-boxes” – In DES, each S-box maps 6 bits to 4 bits, and DES employs eight distinct S-boxes. – The S-boxes, taken together, map 48 bits to 32 bits. – The same S-boxes are used at each round of DES and each S-box is implemented as a lookup table. Part 1 Cryptography 23

L 32 28 expand 48 32 One Round of DES key R 48 S-boxes 28 shift 28 Ki The round function F is the composition of the expansion permutation, addition (XORing) of subkey, S-boxes, and P-box 28 compress 48 28 28 32 32 P box 32 L R key F(Ri-1, Ki) = P-box(S-boxes(Expand(Ri-1) Ki))

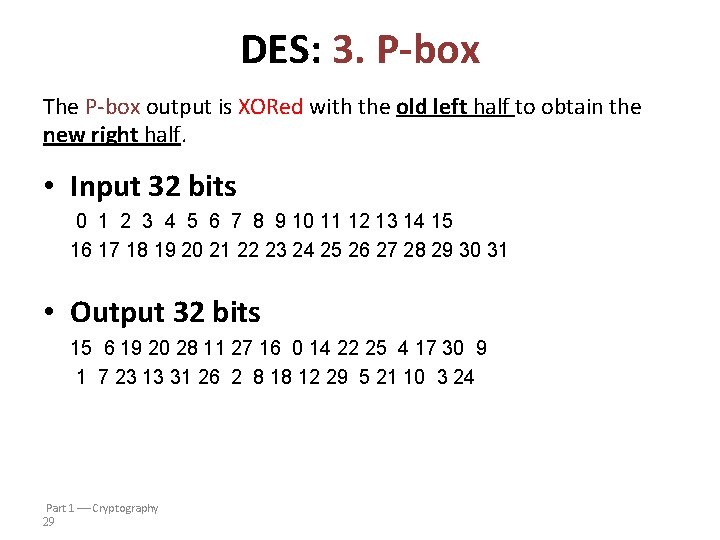
DES Example 1. The expansion permutation expands its input from 32 to 48 bits, and the subkey is XORed with the result. 2. The S-boxes then compress these 48 bits down to 32 bits before the result is passed through the P-box. 3. The P-box output is XORed with the old left half to obtain the new right half. It's important to keep in mind and realize that the overall structure of DES is actually fairly simple. – In fact, some of the DES operations are of no security benefit whatsoever, and if these were stripped away to reveal the essential security features, the algorithm becomes even simpler. Convention: bits are numbered from left to right, beginning with the index 0

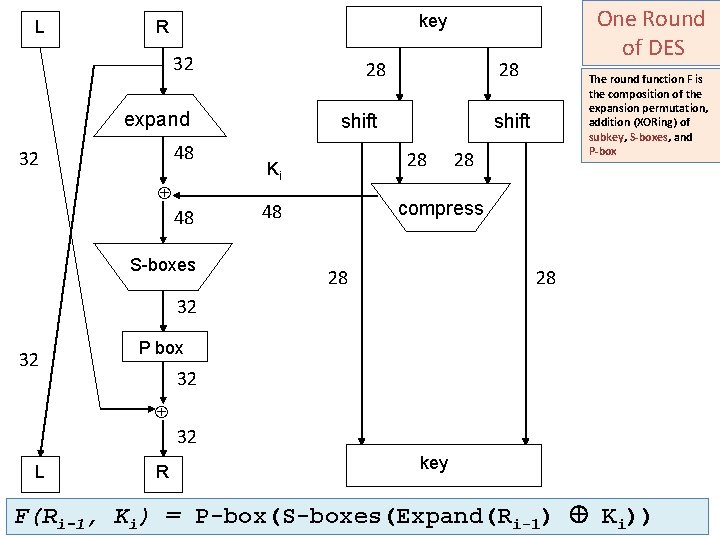
DES: 1. Expansion Permutation The expansion permutation expands its input from 32 to 48 bits, and the subkey is XORed with the result. • Input 32 bits 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 • Output 48 bits 31 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 0 Part 1 Cryptography 26

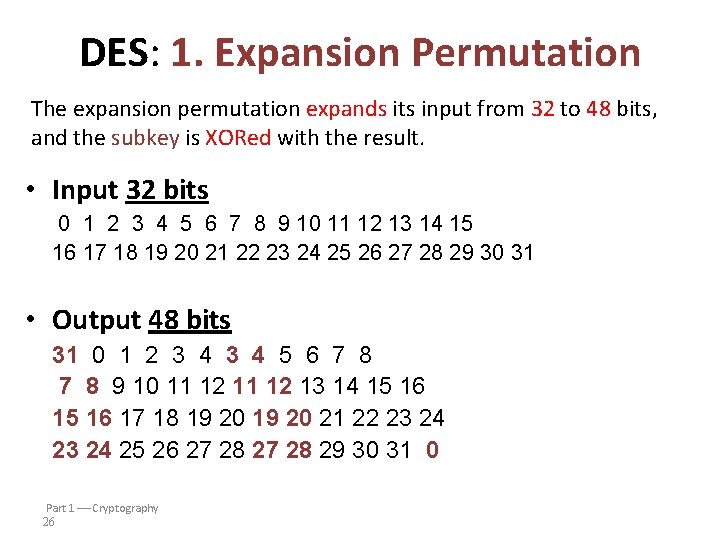
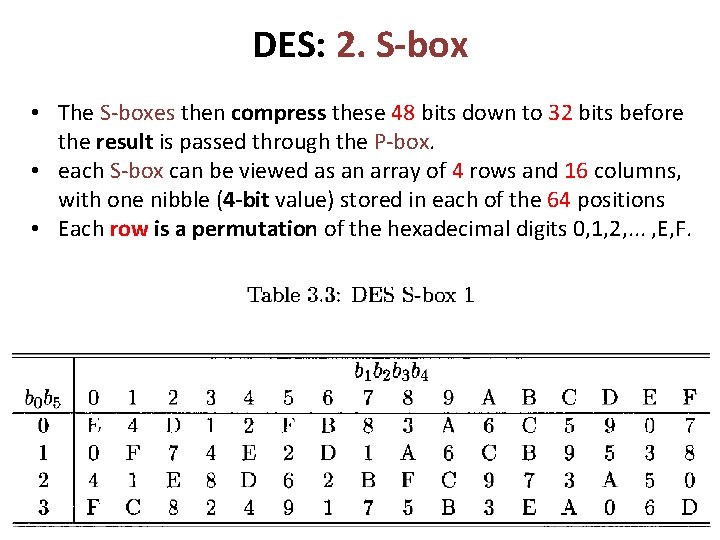
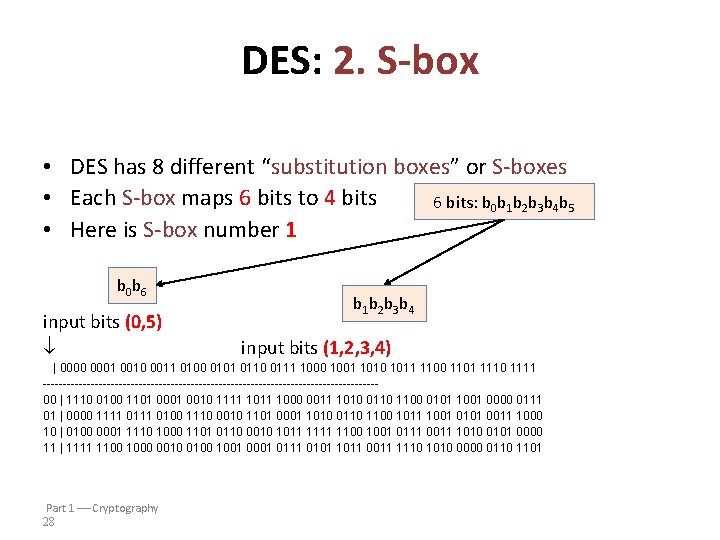
DES: 2. S-box • The S-boxes then compress these 48 bits down to 32 bits before the result is passed through the P-box. • each S-box can be viewed as an array of 4 rows and 16 columns, with one nibble (4 -bit value) stored in each of the 64 positions • Each row is a permutation of the hexadecimal digits 0, 1, 2, . . . , E, F.

DES: 2. S-box • DES has 8 different “substitution boxes” or S-boxes • Each S-box maps 6 bits to 4 bits 6 bits: b 0 b 1 b 2 b 3 b 4 b 5 • Here is S-box number 1 b 0 b 6 input bits (0, 5) b 1 b 2 b 3 b 4 input bits (1, 2, 3, 4) | 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111 ------------------------------------------00 | 1110 0100 1101 0010 1111 1000 0011 1010 0110 1100 0101 1001 0000 0111 01 | 0000 1111 0100 1110 0010 1101 0001 1010 0110 1100 1011 1001 0101 0011 1000 10 | 0100 0001 1110 1000 1101 0110 0010 1011 1100 1001 0111 0011 1010 0101 0000 11 | 1111 1100 1000 0010 0100 1001 0111 0101 1011 0011 1110 1010 0000 0110 1101 Part 1 Cryptography 28

DES: 3. P-box The P-box output is XORed with the old left half to obtain the new right half. • Input 32 bits 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 • Output 32 bits 15 6 19 20 28 11 27 16 0 14 22 25 4 17 30 9 1 7 23 13 31 26 2 8 18 12 29 5 21 10 3 24 Part 1 Cryptography 29

DES Last Word (Almost) • An initial permutation before round 1 • Halves are swapped after last round • A final permutation (inverse of initial perm) applied to (R 16, L 16) • None of this serves any security purpose Part 1 Cryptography 30

Security of DES • Security depends heavily on S-boxes (8 of them) – Everything else in DES is linear • 35+ years of intense analysis has revealed no back door • Attacks, essentially exhaustive key search – 256 possible keys ? • Inescapable Conclusions – Designers of DES knew what they were doing – Designers of DES were way ahead of their time (at least w. r. t. certain cryptanalytic techniques) Part 1 Cryptography 31

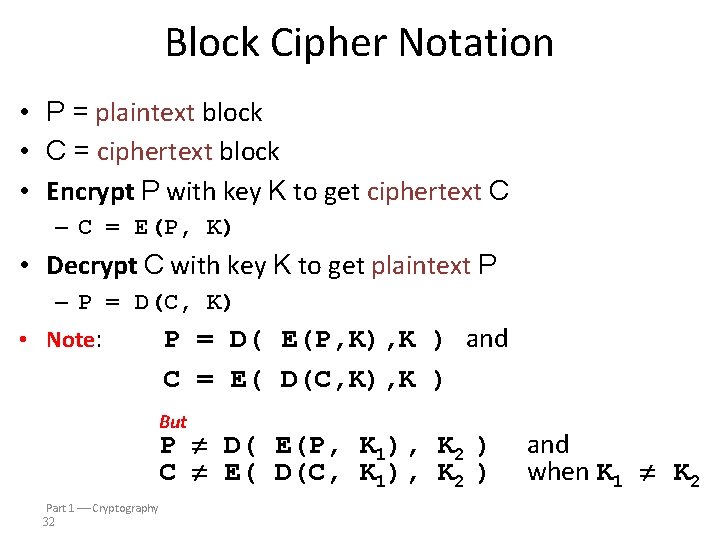
Block Cipher Notation • P = plaintext block • C = ciphertext block • Encrypt P with key K to get ciphertext C – C = E(P, K) • Decrypt C with key K to get plaintext P – P = D(C, K) • Note: P = D( E(P, K), K ) and C = E( D(C, K), K ) But P D( E(P, K 1), K 2 ) C E( D(C, K 1), K 2 ) Part 1 Cryptography 32 and when K 1 K 2

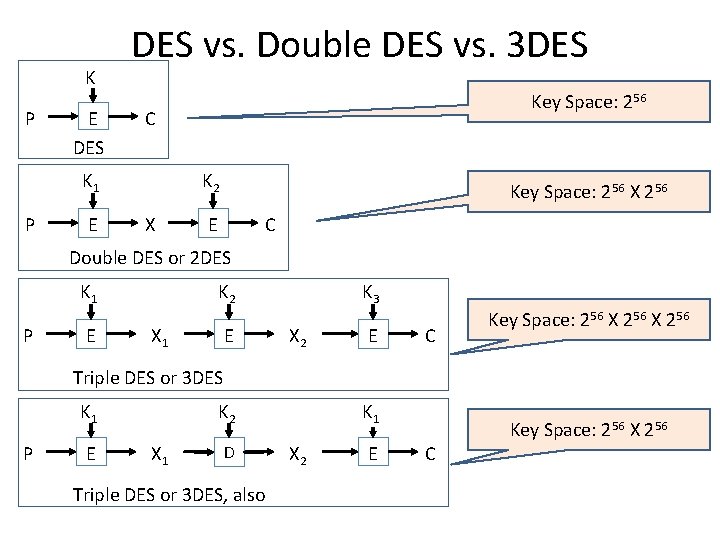
K P E DES vs. Double DES vs. 3 DES C K 1 P E Key Space: 256 K 2 X Key Space: 256 X 256 E C Double DES or 2 DES K 1 P E K 2 X 1 E K 3 X 2 E C Key Space: 256 X 256 Triple DES or 3 DES K 1 P E K 1 K 2 X 1 D Triple DES or 3 DES, also X 2 E C Key Space: 256 X 256

Meet In The Middle (MITM) Attack • Double DES (2 DES) is supposed to give 112 -bit key length. – E( E(P, K 1), K 2 ) and D( D(P, K 1), K 2 ) K 1 P E K 2 X E Double DES: Encryption K 2 C C D K 1 X D P Double DES: Decryption – 256 * 256 = 2112, key space (possible keys) – Instead, attackers may end up trying 257, how come? • Thus, double encryption is not that significant in terms of added security, but why?

2 DES • Why not C = E( E(P, K), K ) instead? – Trick question still just 56 bit key • Why not C = E( E(P, K 1), K 2 ) instead? • A (semi-practical) known plaintext attack (MITM) – Pre-compute table of X 1 = E(P, K 1) for every possible key K 1 (resulting table has 256 entries, storage? ) – Then for each possible K 2 compute X 2 = D(C, K 2) until a match in table is found • Find when X 1 == X 2 and use it to infer the keys – When match is found, have E(P, K 1) = D(C, K 2) – Result gives us keys: C = E( E(P, K 1), K 2) Part 1 Cryptography 35

Triple DES • Today, 56 -bit DES key is too small – Exhaustive key search is feasible • 2 DES is not secure enough (almost similar to Single DES) • But DES is everywhere, so what to do? • Triple DES or 3 DES (112 -bit key or 168 -bit, large enough) – C = E( D( E(P, K 1), K 2), K 1) – P = D( E( D(C, K 1), K 2), K 1) • Why Encrypt-Decrypt-Encrypt with 2 keys? – Backward compatible: E( D( E(P, K), K) = E(P, K) – and 112 is a lot of bits Part 1 Cryptography 36

AES: Advanced Encryption Standard • Replacement for DES • AES competition (late 90’s) – U. S. NSA openly involved – Transparent selection process – Many strong algorithms proposed – Rijndael Algorithm ultimately selected (pronounced like “Rain Doll” or “Rhine Doll”) • Iterated block cipher (like DES) • Not a Feistel cipher (unlike DES) Part 1 Cryptography 37

AES: Executive Summary • Block size: 128 bits (others in Rijndael) • Key length: 128, 192 or 256 bits – independent of block size in Rijndael • 10 to 14 rounds (depends on key length) • Each round uses 4 functions (3 “layers”) 1. Byte. Sub : nonlinear layer 2. Shift. Row : linear mixing layer 3. Mix. Column : nonlinear layer 4. Add. Round. Key : key addition layer Part 1 Cryptography 38

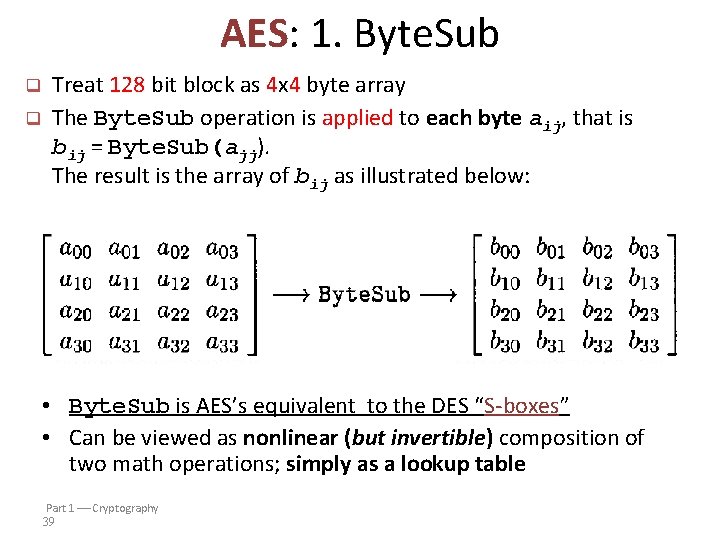
AES: 1. Byte. Sub q q Treat 128 bit block as 4 x 4 byte array The Byte. Sub operation is applied to each byte aij, that is bij = Byte. Sub(ajj). The result is the array of bij as illustrated below: • Byte. Sub is AES’s equivalent to the DES “S-boxes” • Can be viewed as nonlinear (but invertible) composition of two math operations; simply as a lookup table Part 1 Cryptography 39

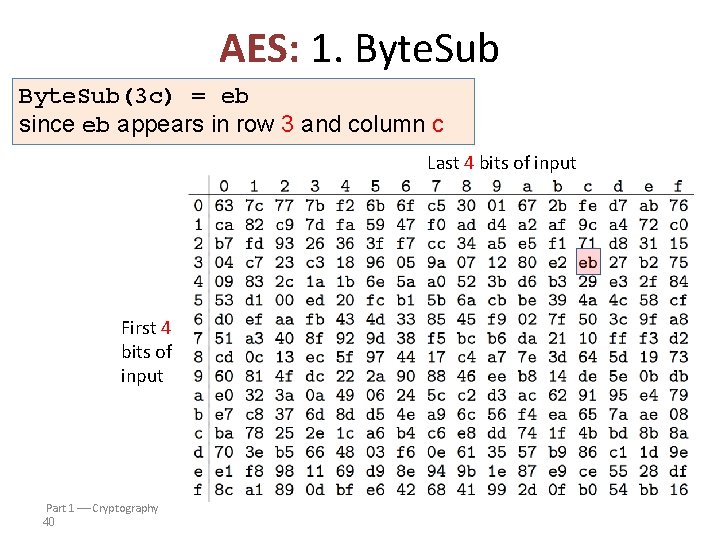
AES: 1. Byte. Sub(3 c) = eb since eb appears in row 3 and column c Last 4 bits of input First 4 bits of input Part 1 Cryptography 40

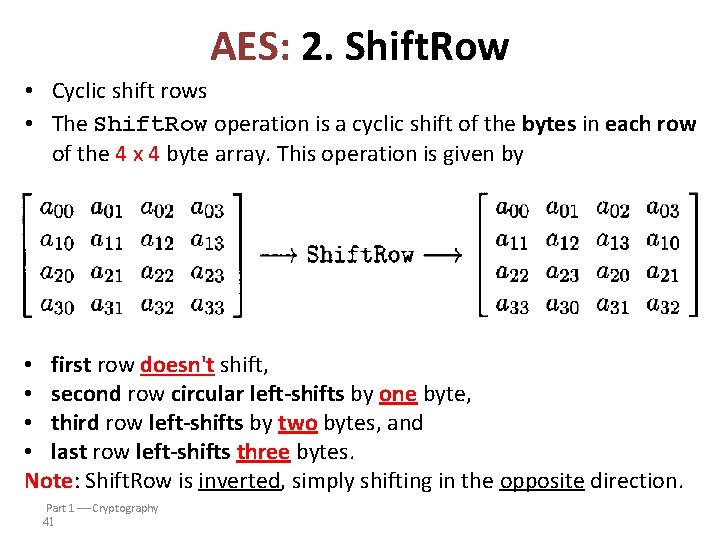
AES: 2. Shift. Row • Cyclic shift rows • The Shift. Row operation is a cyclic shift of the bytes in each row of the 4 x 4 byte array. This operation is given by • first row doesn't shift, • second row circular left-shifts by one byte, • third row left-shifts by two bytes, and • last row left-shifts three bytes. Note: Shift. Row is inverted, simply shifting in the opposite direction. Part 1 Cryptography 41

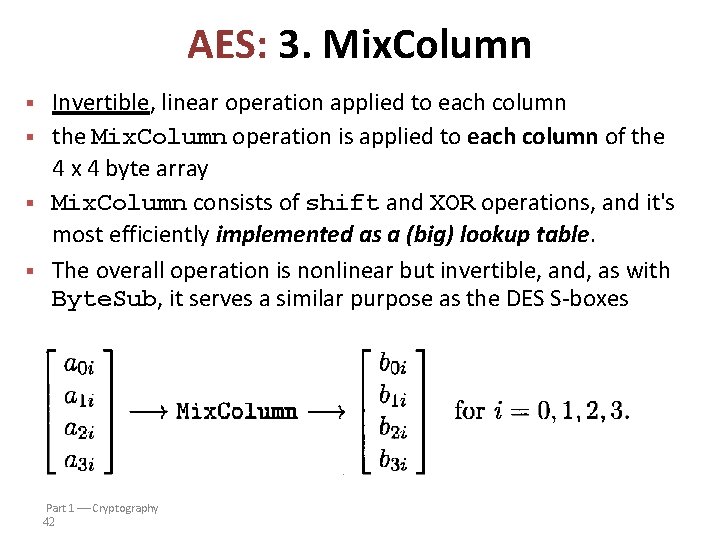
AES: 3. Mix. Column § § Invertible, linear operation applied to each column the Mix. Column operation is applied to each column of the 4 x 4 byte array Mix. Column consists of shift and XOR operations, and it's most efficiently implemented as a (big) lookup table. The overall operation is nonlinear but invertible, and, as with Byte. Sub, it serves a similar purpose as the DES S-boxes Part 1 Cryptography 42

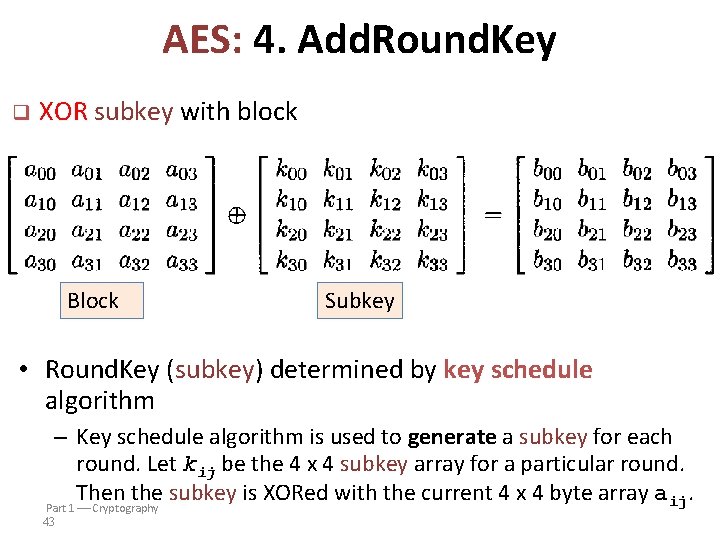
AES: 4. Add. Round. Key q XOR subkey with block Block Subkey • Round. Key (subkey) determined by key schedule algorithm – Key schedule algorithm is used to generate a subkey for each round. Let kij be the 4 x 4 subkey array for a particular round. Then the subkey is XORed with the current 4 x 4 byte array aij. Part 1 Cryptography 43

AES: Decryption • To decrypt, process must be invertible • Inverse of Mix. Add. Round. Key is easy, since “ ” is its own inverse • Mix. Column is invertible (inverse is also implemented as a lookup table) • Inverse of Shift. Row is easy (cyclic shift the other direction) • Byte. Sub is invertible (inverse is also implemented as a lookup table) Part 1 Cryptography 44

AES Summary • AES has both excellent confusion and diffusion • Look-up tables: non-linear, good at destroying patterns (confusion) • Diffusion stage spreads every part of the input to the output: – changing one bit of input changes half the output bits on average – The Mix. Columns operation along with the Shift. Rows step, is the primary source of diffusion • Both confusion and diffusion are repeated multiple times for each input to increase the amount of scrambling • The secret key is mixed at every stage so that an attacker cannot pre-calculate what the cipher does. • None of this would happen if you used a simple one-stage scramble based on a key.

A Few Other Block Ciphers • Briefly… – IDEA – Blowfish – RC 6 • More detailed… – TEA Part 1 Cryptography 46

Block Cipher Modes • Using a stream cipher is easy—you generate a keystream that is the same length as the plaintext (or ciphertext) and XOR. • Using a block cipher is also easy, provided that you have exactly one block to encrypt. • But how should multiple blocks be encrypted with a block cipher? • It turns out that the answer is not as straightforward as it might seem. Part 1 Cryptography 47

Multiple Blocks • How to encrypt multiple blocks? • Do we need a new key for each block? – If so, as impractical as a One-Time Pad! • Encrypt each block independently? • Is there any analog of codebook “additive”? • What about partial blocks, how to handle them? – What about Padding or CFC Part 1 Cryptography 48

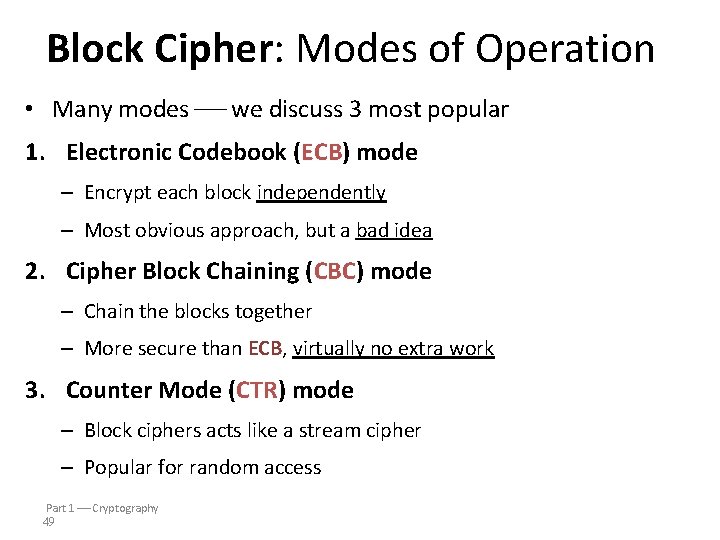
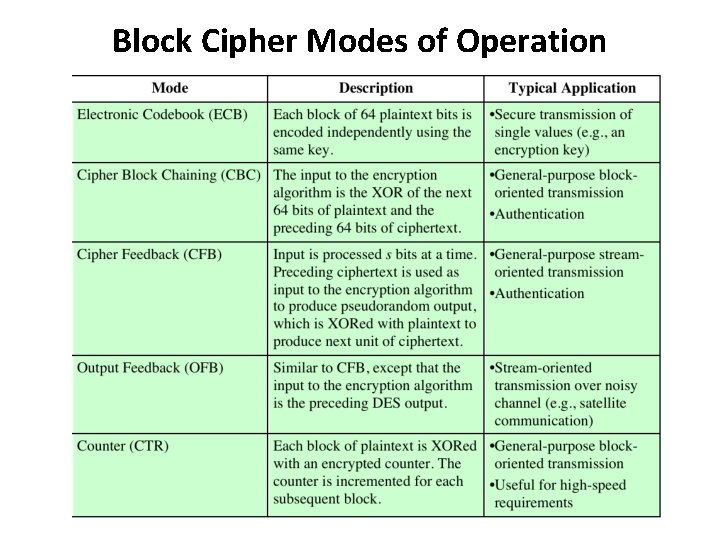
Block Cipher: Modes of Operation • Many modes we discuss 3 most popular 1. Electronic Codebook (ECB) mode – Encrypt each block independently – Most obvious approach, but a bad idea 2. Cipher Block Chaining (CBC) mode – Chain the blocks together – More secure than ECB, virtually no extra work 3. Counter Mode (CTR) mode – Block ciphers acts like a stream cipher – Popular for random access Part 1 Cryptography 49

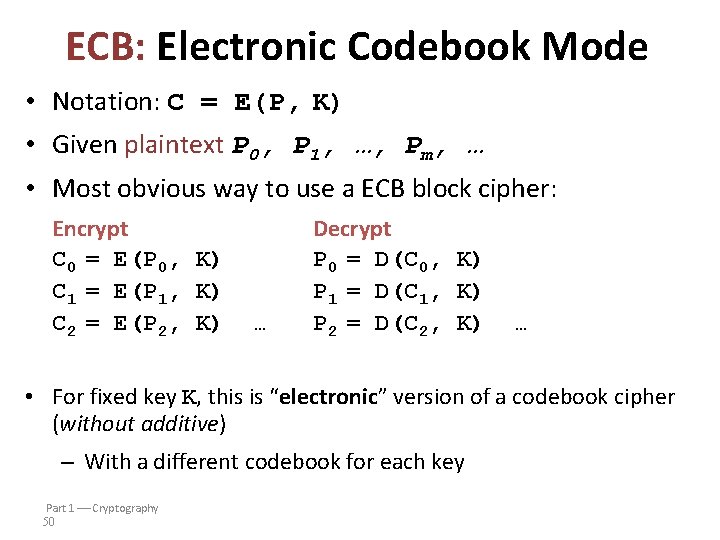
ECB: Electronic Codebook Mode • Notation: C = E(P, K) • Given plaintext P 0, P 1, …, Pm, … • Most obvious way to use a ECB block cipher: Encrypt C 0 = E(P 0, K) C 1 = E(P 1, K) C 2 = E(P 2, K) … Decrypt P 0 = D(C 0, K) P 1 = D(C 1, K) P 2 = D(C 2, K) … • For fixed key K, this is “electronic” version of a codebook cipher (without additive) – With a different codebook for each key Part 1 Cryptography 50

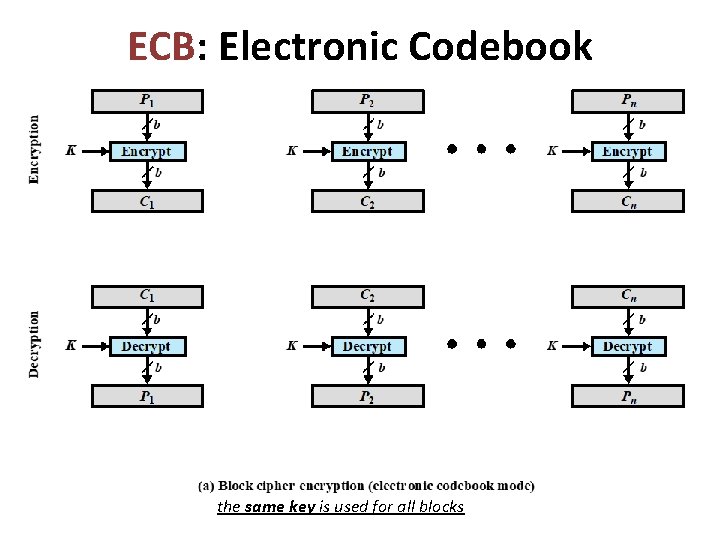
ECB: Electronic Codebook the same key is used for all blocks

ECB: Electronic Codebook • • Simplest mode • “Codebook” is used because there is an unique ciphertext for every b-bit block of plaintext Plaintext is handled b-bit (block) at a time and each block is encrypted using the same key • Not secure for long messages • since repeated plaintext is seen in repeated ciphertext • this is a serious security issues and it should never be used in practice. • To overcome security deficiencies: • you need a technique where the same plaintext block, if repeated, produces different ciphertext blocks ? ?

ECB Weakness • Suppose Pi = Pj • Then Ci = Cj and then Trudy will know that Pi = Pj • This gives Trudy some information, even if she does not know Pi or Pj • Trudy might know Pi. Then now she knows Pj • Is this a serious issue? And when it will become one? Part 1 Cryptography 53

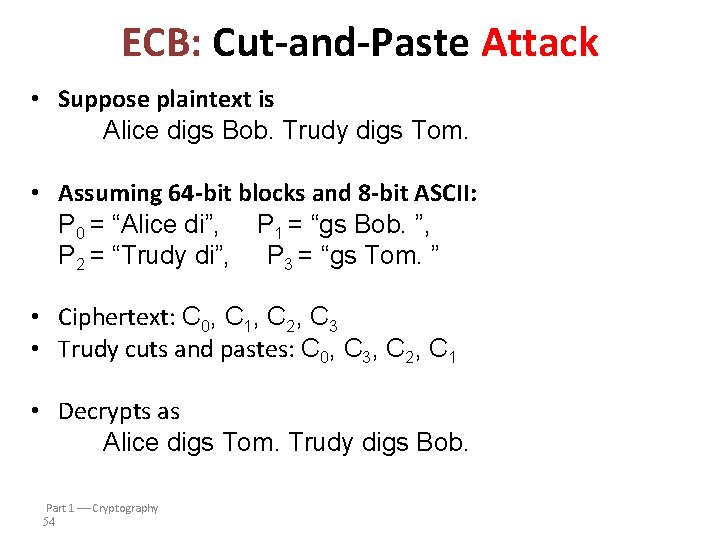
ECB: Cut-and-Paste Attack • Suppose plaintext is Alice digs Bob. Trudy digs Tom. • Assuming 64 -bit blocks and 8 -bit ASCII: P 0 = “Alice di”, P 1 = “gs Bob. ”, P 2 = “Trudy di”, P 3 = “gs Tom. ” • Ciphertext: C 0, C 1, C 2, C 3 • Trudy cuts and pastes: C 0, C 3, C 2, C 1 • Decrypts as Alice digs Tom. Trudy digs Bob. Part 1 Cryptography 54

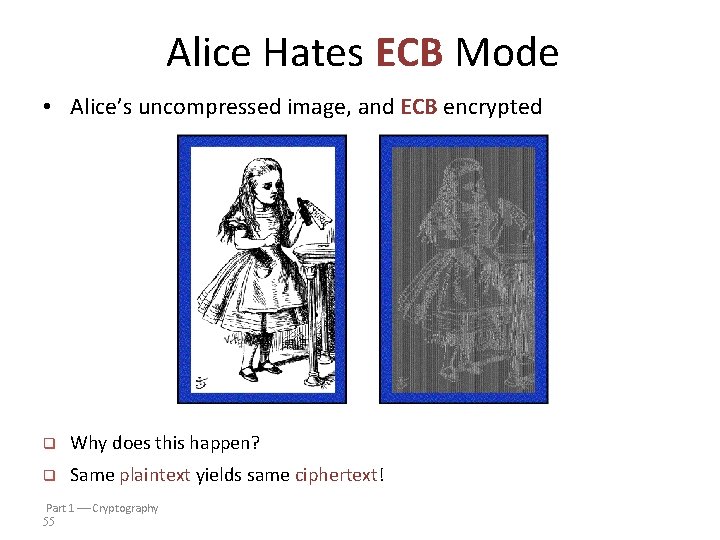
Alice Hates ECB Mode • Alice’s uncompressed image, and ECB encrypted q Why does this happen? q Same plaintext yields same ciphertext! Part 1 Cryptography 55

CBC: Cipher Block Chaining Mode • Blocks are “chained” together • A random Initialization Vector (IV) is required to start with the CBC mode • IV is random, but not secret Encryption Decryption C 0 = E(IV P 0, K), C 1 = E(C 0 P 1, K), C 2 = E(C 1 P 2, K), … P 0 = IV D(C 0, K), P 1 = C 0 D(C 1, K), P 2 = C 1 D(C 2, K), … • Analogous to classic codebook with additive Part 1 Cryptography 56


CBC: Cipher Block Chaining Mode • Pros: Using the CBC, identical plaintext blocks yield different ciphertext blocks this is very good! • But what about errors in transmission (error propagation)? – Suppose the ciphertext block Ci is garbled to, say, G Ci. Then Pi D(G, K) Ci-1 and Pi+1 D(Ci+1, K) G – But Pi+2 = D(Ci+2, K) Ci+1, … • However, all subsequent blocks are decrypted correctly. – That is, each plaintext block only depends on two consecutive ciphertext blocks, so errors do not propagate beyond two blocks. But, the fact that a single-bit error can cause two entire blocks to be garbled is a serious concern in high error-rate environments such as wireless. – Stream ciphers do not have this problem—a single garbled ciphertext bit results in a single garbled plaintext bit—and that is one reason why stream ciphers are often preferred in wireless applications Part 1 Cryptography 58

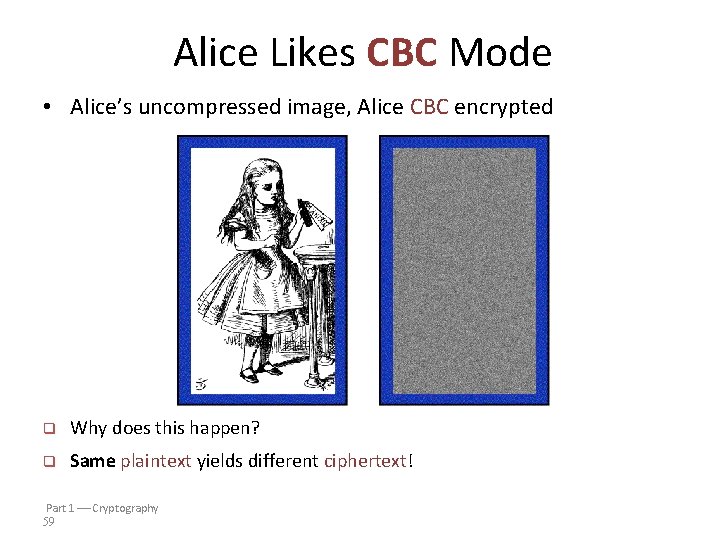
Alice Likes CBC Mode • Alice’s uncompressed image, Alice CBC encrypted q Why does this happen? q Same plaintext yields different ciphertext! Part 1 Cryptography 59

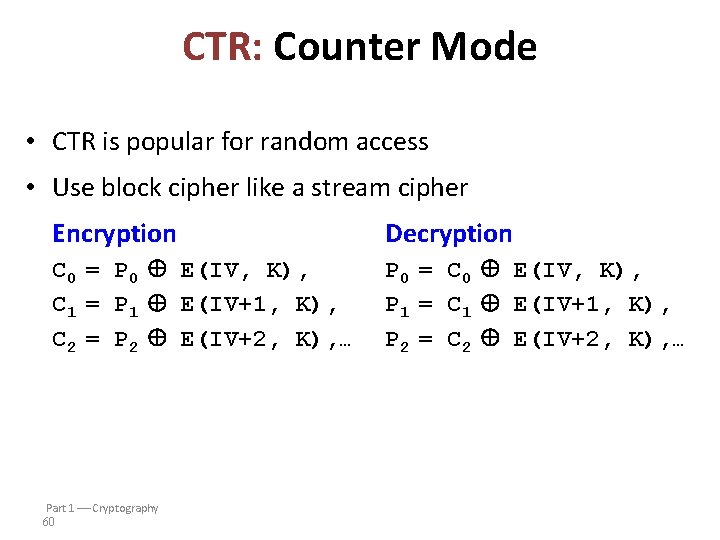
CTR: Counter Mode • CTR is popular for random access • Use block cipher like a stream cipher Encryption Decryption C 0 = P 0 E(IV, K), C 1 = P 1 E(IV+1, K), C 2 = P 2 E(IV+2, K), … P 0 = C 0 E(IV, K), P 1 = C 1 E(IV+1, K), P 2 = C 2 E(IV+2, K), … Part 1 Cryptography 60


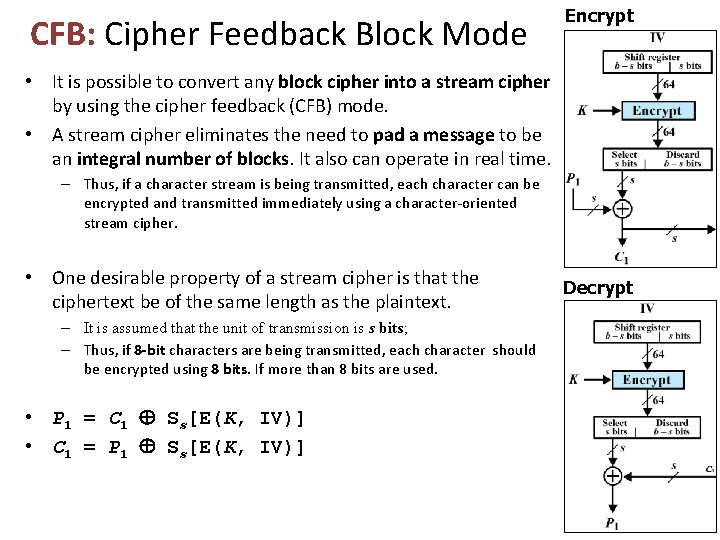
CFB: Cipher Feedback Block Mode Encrypt • It is possible to convert any block cipher into a stream cipher by using the cipher feedback (CFB) mode. • A stream cipher eliminates the need to pad a message to be an integral number of blocks. It also can operate in real time. – Thus, if a character stream is being transmitted, each character can be encrypted and transmitted immediately using a character-oriented stream cipher. • One desirable property of a stream cipher is that the ciphertext be of the same length as the plaintext. – It is assumed that the unit of transmission is s bits; – Thus, if 8 -bit characters are being transmitted, each character should be encrypted using 8 bits. If more than 8 bits are used. • P 1 = C 1 Ss[E(K, IV)] • C 1 = P 1 Ss[E(K, IV)] Decrypt


Block Cipher Modes of Operation

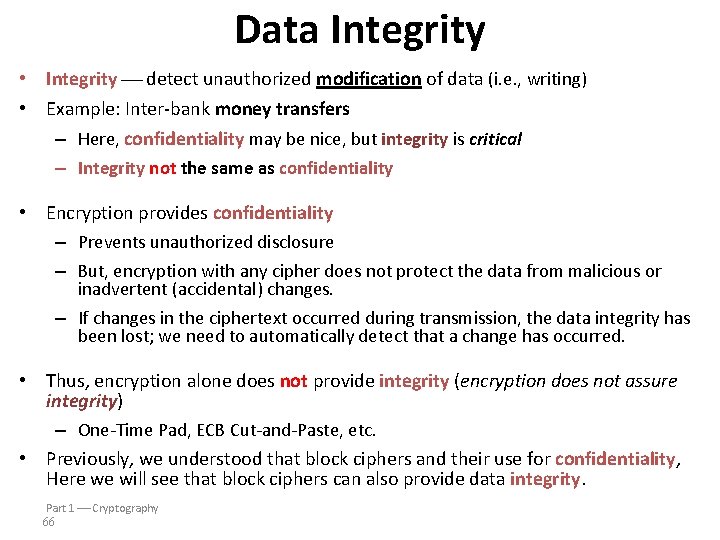
Integrity Part 1 Cryptography 65

Data Integrity • Integrity detect unauthorized modification of data (i. e. , writing) • Example: Inter-bank money transfers – Here, confidentiality may be nice, but integrity is critical – Integrity not the same as confidentiality • Encryption provides confidentiality – Prevents unauthorized disclosure – But, encryption with any cipher does not protect the data from malicious or inadvertent (accidental) changes. – If changes in the ciphertext occurred during transmission, the data integrity has been lost; we need to automatically detect that a change has occurred. • Thus, encryption alone does not provide integrity (encryption does not assure integrity) – One-Time Pad, ECB Cut-and-Paste, etc. • Previously, we understood that block ciphers and their use for confidentiality, Here we will see that block ciphers can also provide data integrity. Part 1 Cryptography 66

MAC: Message Authentication Code • MAC: uses a block cipher to ensure data integrity – The procedure is simple: • Encrypt the data in CBC mode • Discard all ciphertext blocks except the final one • Save only the final ciphertext block (the MAC) – This final ciphertext block is known as the CBC residue or remainder, serves as the MAC; (CBC-MAC). – This MAC serves as a cryptographic checksum for data – An Initialization Vector (IV) is needed, and the shared symmetric key required. Part 1 Cryptography 67

MAC Computation • MAC computation (assuming N blocks) C 0 = E(IV P 0, K), C 1 = E(C 0 P 1, K), C 2 = E(C 1 P 2, K), … CN 1 = E(CN 2 PN 1, K) = MAC • Send IV, P 0, P 1, …, PN 1 and MAC • Receiver does the same computation and verifies that result agrees with MAC • Both sender and receiver must know K Part 1 Cryptography 68

• • Does a MAC work? Suppose Alice has 4 plaintext blocks Alice computes C 0 C 1 C 2 C 3 • = = E(IV E(C 0 E(C 1 E(C 2 P 0, P 1, P 2, P 3, K), K), K) = MAC Alice computes the MAC and sends the plaintext, the IV, and the MAC to Bob – Alice sends IV, P 0, P 1, P 2, P 3 and MAC • Bob computes the MAC using the key and received IV and plaintext. If his computed "MAC" matches the received MAC, then he is satisfied with the integrity of the data. • Suppose Trudy changes P 1 to X • Bob computes C 0 C 1 C 2 C 3 • • = = E(IV E(C 0 E(C 1 E(C 2 P 0, X, P 2, P 3, K), K), K) = MAC It works since error propagates into MAC Trudy can’t make MAC == MAC without K

Confidentiality and Integrity • Often confidentiality and integrity are both required. Thus, we could – Encrypt data with one key – Encrypt MAC with another key • Why not use the same key? – Send last encrypted block (MAC) twice? – This cannot add any security! • Using different keys to encrypt and compute MAC works, even if keys are related – But, twice as much needed for either confidentiality or integrity alone – it would be better to do both confidentiality and integrity with single CBC – Can do a little better ? ? ” • Computing a MAC based on CBC encryption is not the only way to provide integrity. – A hashed MAC, or HMAC, is another standard approach to integrity – digital signature is yet another option.

Uses for Symmetric Crypto • Confidentiality – Transmitting data over insecure channel – Secure storage on insecure media • Integrity (MAC) • Authentication protocols (later…) • Anything you can do with a hash function (upcoming chapter…) Part 1 Cryptography 71

Summary: Block vs. Stream Ciphers Block Cipher • • Processes the input one block of elements at a time Produces an output block for each input block Can reuse keys More common Stream Cipher • Processes the input elements continuously • Produces output one element at a time • Primary advantage is that they are almost always faster and use far less code • Encrypts plaintext one bit or byte at a time • Pseudorandom stream is one that is unpredictable without knowledge of the input key