Chapter 3 Networking and Internetworking Concepts Switching Routing













- Slides: 63

Chapter 3: Networking and Internetworking § § § Concepts Switching Routing (IP) End-to-End Protocols (UDP/TCP) Wireless LAN

Introduction

Building Blocks z Nodes: PC, special-purpose hardware… yhosts yswitches z Links: coax cable, optical fiber… ypoint-to-point (a) ymultiple access (b) ■■■

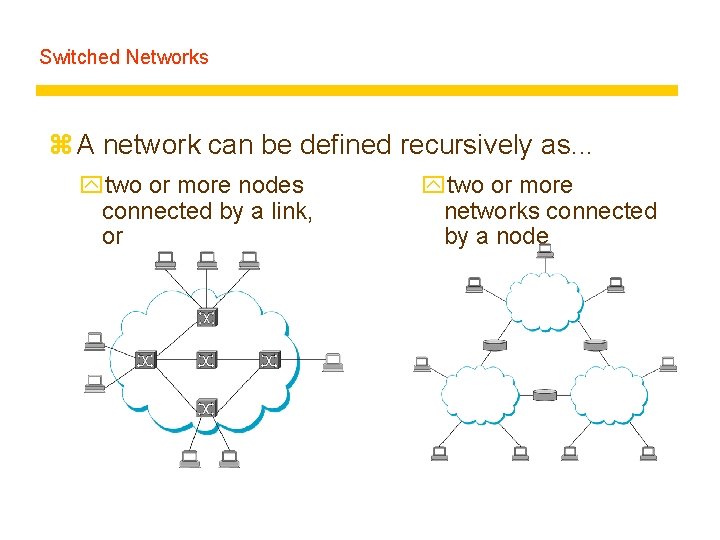
Switched Networks z A network can be defined recursively as. . . ytwo or more nodes connected by a link, or ytwo or more networks connected by a node

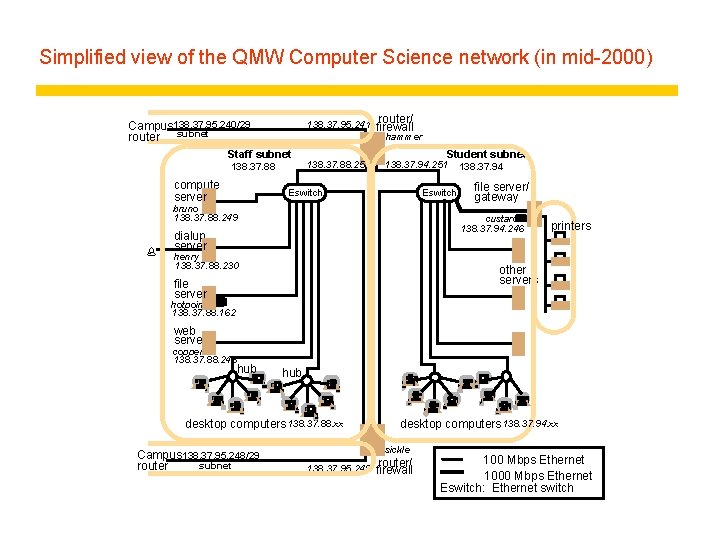
Simplified view of the QMW Computer Science network (in mid-2000) Campus 138. 37. 95. 240/29 router subnet 138. 37. 95. 241 hammer Staff subnet 138. 37. 88 compute server router/ firewall 138. 37. 88. 251 Student subnet 138. 37. 94. 251 Eswitch bruno 138. 37. 88. 249 % 138. 37. 94 file server/ gateway custard 138. 37. 94. 246 dialup server henry 138. 37. 88. 230 printers other servers file server hotpoint 138. 37. 88. 162 web server copper 138. 37. 88. 248 hub desktop computers 138. 37. 88. xx Campus 138. 37. 95. 248/29 subnet router desktop computers 138. 37. 94. xx sickle router/ 138. 37. 95. 249 firewall 100 Mbps Ethernet 1000 Mbps Ethernet Eswitch: Ethernet switch

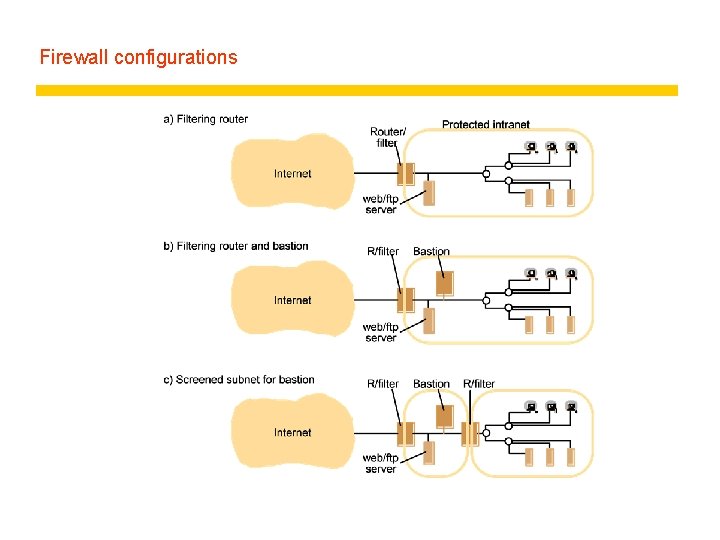
Firewall configurations

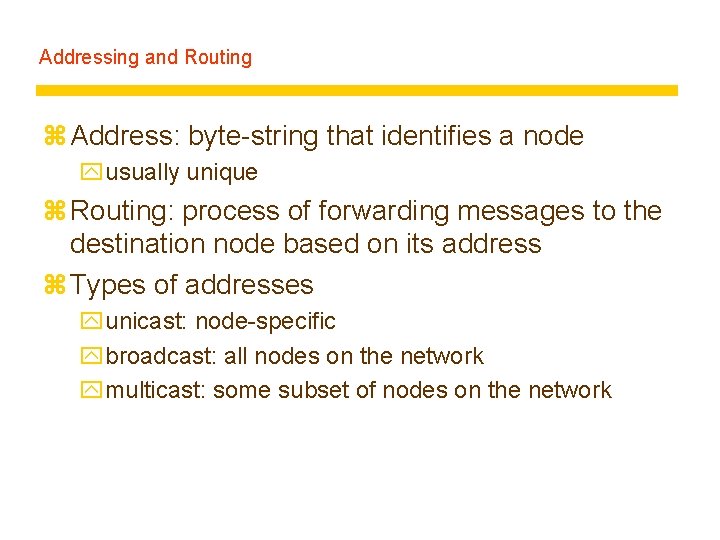
Addressing and Routing z Address: byte-string that identifies a node yusually unique z Routing: process of forwarding messages to the destination node based on its address z Types of addresses yunicast: node-specific ybroadcast: all nodes on the network ymulticast: some subset of nodes on the network

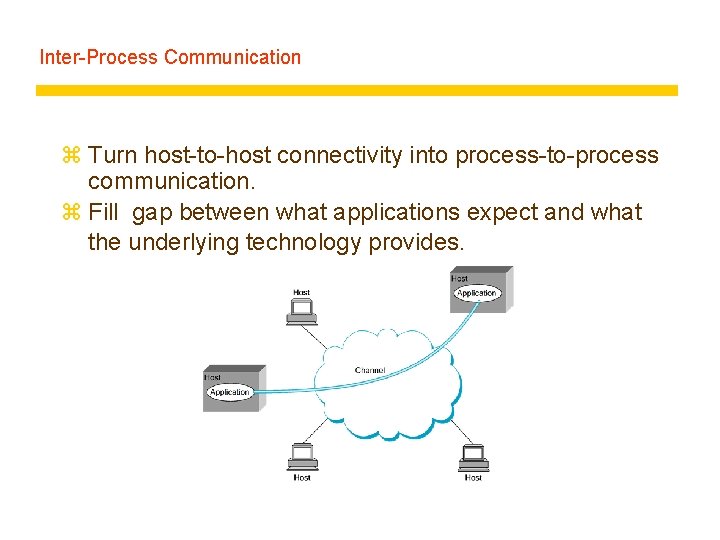
Inter-Process Communication z Turn host-to-host connectivity into process-to-process communication. z Fill gap between what applications expect and what the underlying technology provides.

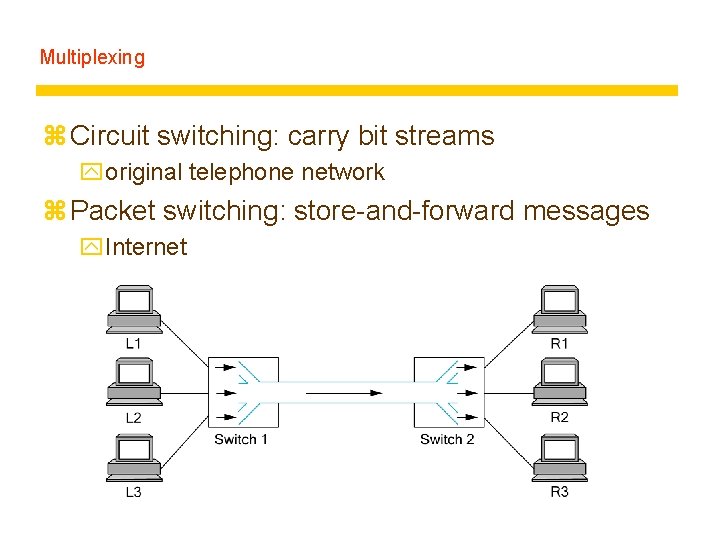
Multiplexing z Circuit switching: carry bit streams yoriginal telephone network z Packet switching: store-and-forward messages y. Internet

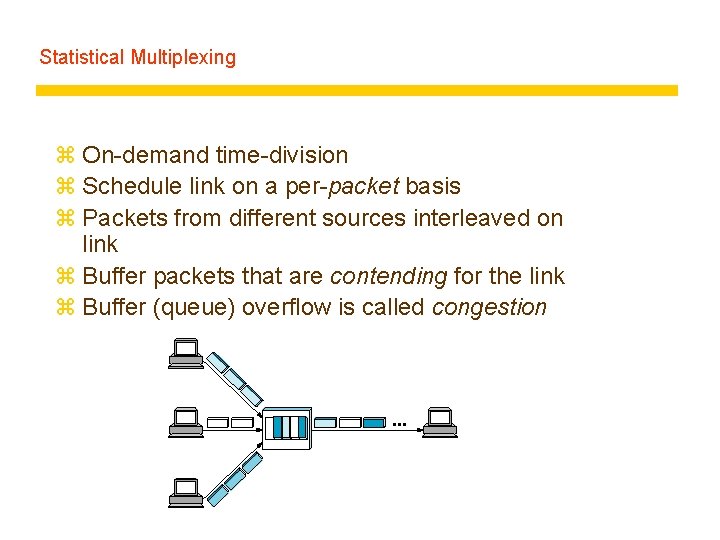
Statistical Multiplexing z On-demand time-division z Schedule link on a per-packet basis z Packets from different sources interleaved on link z Buffer packets that are contending for the link z Buffer (queue) overflow is called congestion ■■■

What Goes Wrong in the Network? z Bit-level errors (electrical interference) z Packet-level errors (congestion) z Link and node failures z Packets are delayed z Packets are deliver out-of-order z Third parties eavesdrop

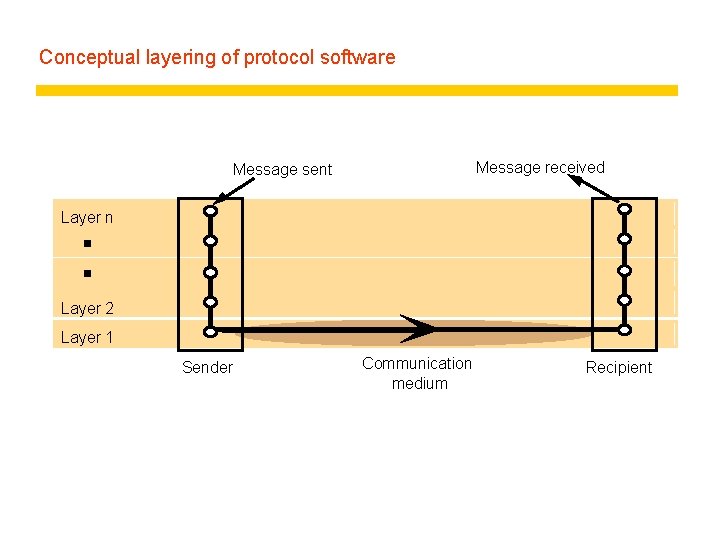
Conceptual layering of protocol software Message received Message sent Layer n Layer 2 Layer 1 Sender Communication medium Recipient

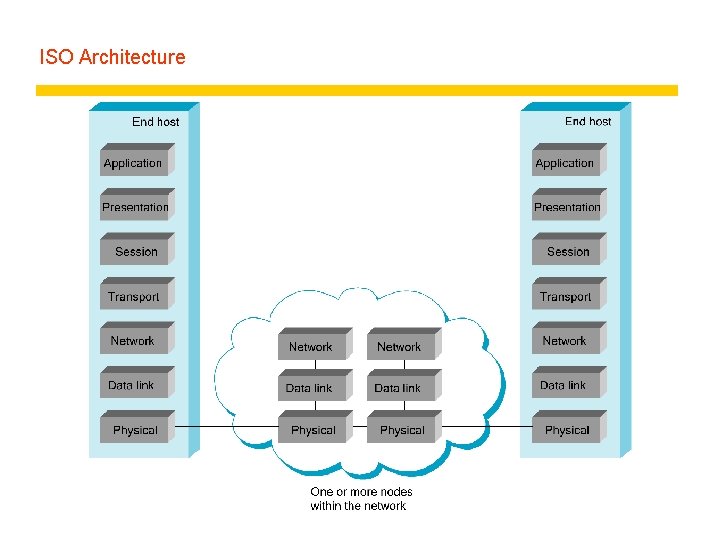
Protocol layers in the ISO Open Systems Interconnection (OSI) model z most peer-to-peer communication is indirect z peer-to-peer is direct only at hardware level

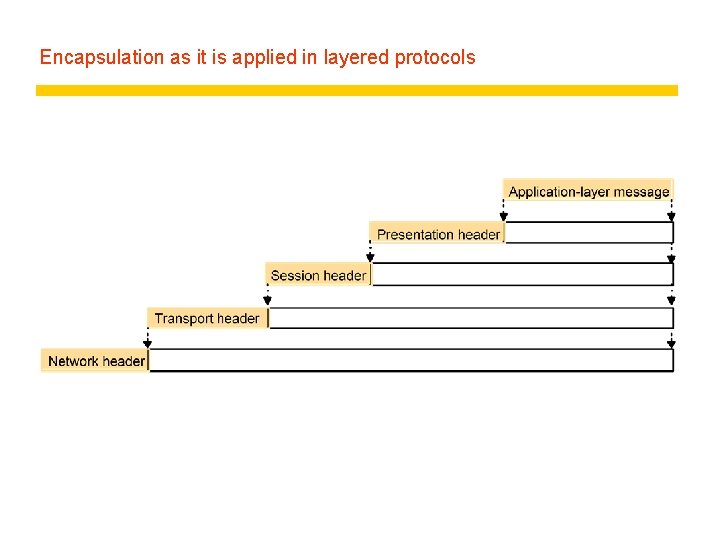
Encapsulation as it is applied in layered protocols

ISO Architecture

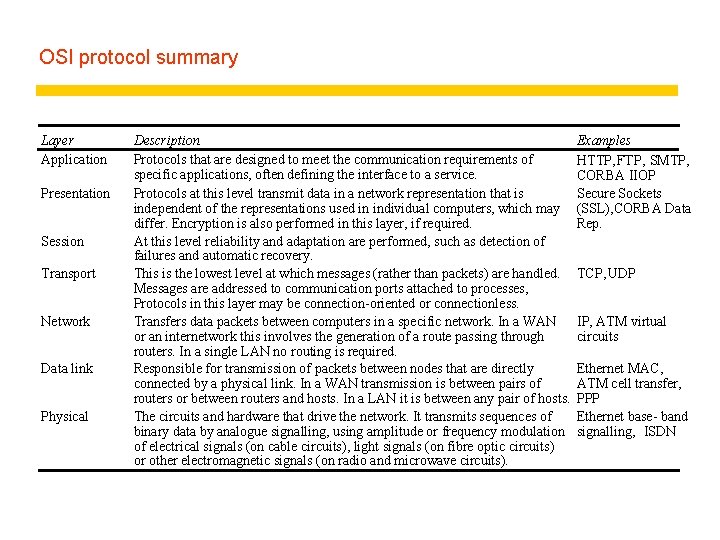
OSI protocol summary Layer Application Presentation Session Transport Network Data link Physical Description Protocols that are designed to meet the communication requirements of specific applications, often defining the interface to a service. Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports attached to processes, Protocols in this layer may be connection-oriented or connectionless. Transfers data packets between computers in a specific network. In a WAN or an internetwork this involves the generation of a route passing through routers. In a single LAN no routing is required. Responsible for transmission of packets between nodes that are directly connected by a physical link. In a WAN transmission is between pairs of routers or between routers and hosts. In a LAN it is between any pair of hosts. The circuits and hardware that drive the network. It transmits sequences of binary data by analogue signalling, using amplitude or frequency modulation of electrical signals (on cable circuits), light signals (on fibre optic circuits) or other electromagnetic signals (on radio and microwave circuits). Examples HTTP, FTP , SMTP, CORBA IIOP Secure Sockets (SSL), CORBA Data Rep. TCP, UDP IP, ATM virtual circuits Ethernet MAC, ATM cell transfer, PPP Ethernet base- band signalling, ISDN

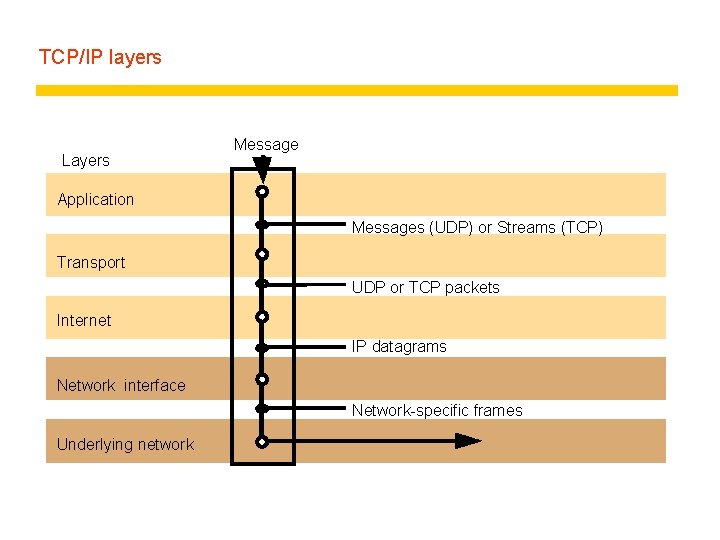
TCP/IP layers Layers Message Application Messages (UDP) or Streams (TCP) Transport UDP or TCP packets Internet IP datagrams Network interface Network-specific frames Underlying network

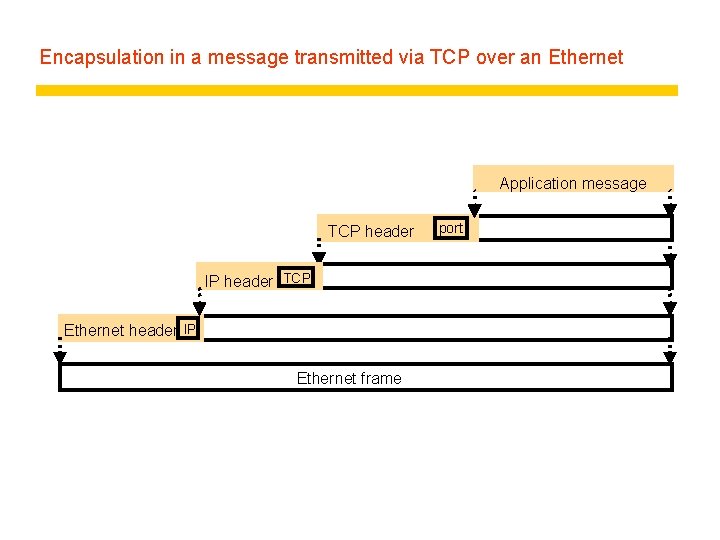
Encapsulation in a message transmitted via TCP over an Ethernet Application message TCP header IP header TCP Ethernet header IP Ethernet frame port

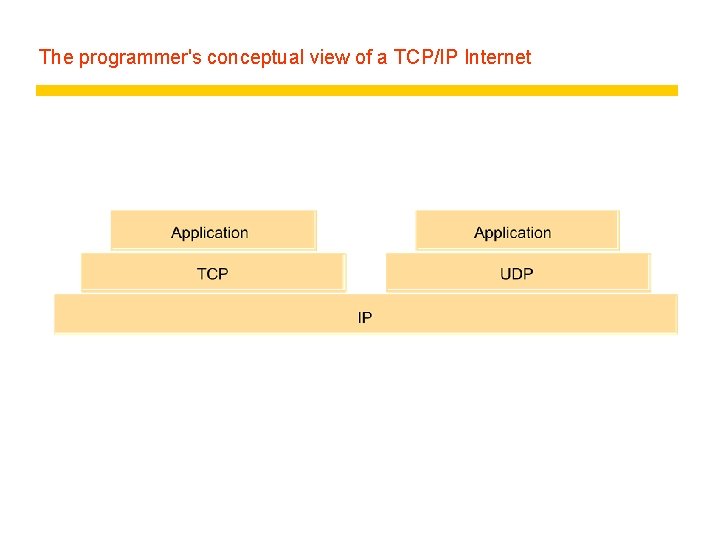
The programmer's conceptual view of a TCP/IP Internet

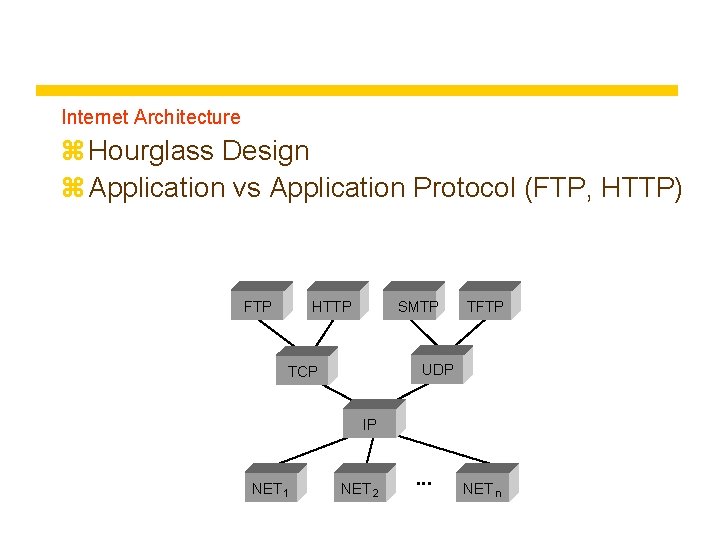
Internet Architecture z Hourglass Design z Application vs Application Protocol (FTP, HTTP) FTP HTTP SMTP TFTP UDP TCP IP NET 1 NET 2 ■■■ NET n

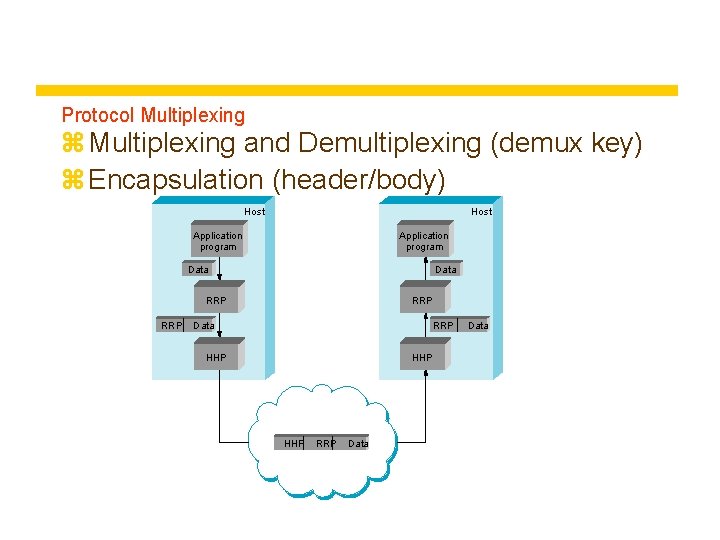
Protocol Multiplexing z Multiplexing and Demultiplexing (demux key) z Encapsulation (header/body) Host Application program Data RRP RRP Data RRP HHP HHP RRP Data

Switching

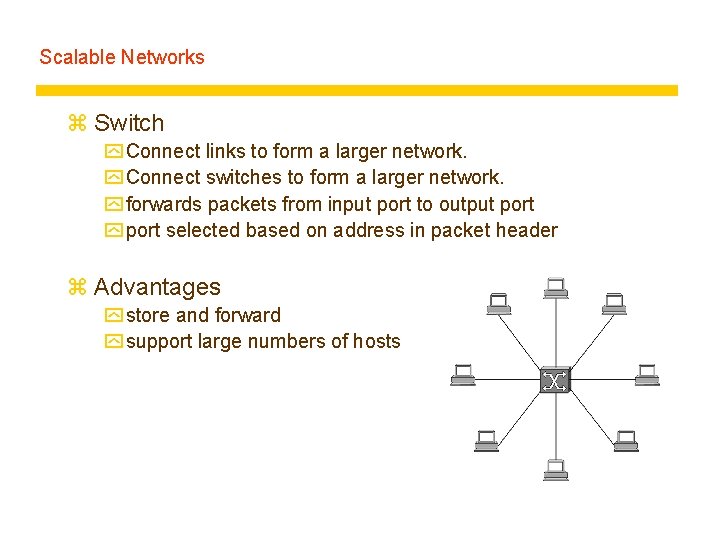
Scalable Networks z Switch y Connect links to form a larger network. y Connect switches to form a larger network. y forwards packets from input port to output port y port selected based on address in packet header z Advantages y store and forward y support large numbers of hosts

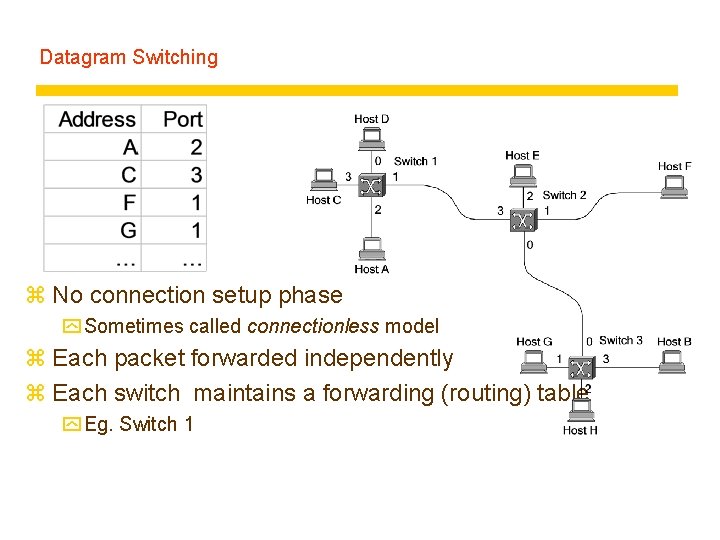
Datagram Switching z No connection setup phase y Sometimes called connectionless model z Each packet forwarded independently z Each switch maintains a forwarding (routing) table y Eg. Switch 1

Datagram Model z Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. y No Qo. S z Since packets are treated independently, it is possible to route around link and node failures. z Since every packet must carry the full address of the destination, the overhead per packet is higher than for the connection-oriented model.

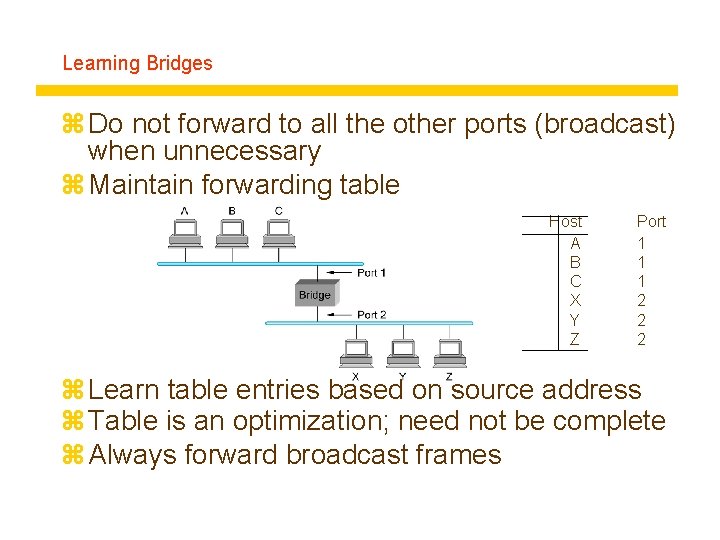
Learning Bridges z Do not forward to all the other ports (broadcast) when unnecessary z Maintain forwarding table Host A B C X Y Z Port 1 1 1 2 2 2 z Learn table entries based on source address z Table is an optimization; need not be complete z Always forward broadcast frames

Routing (IP)

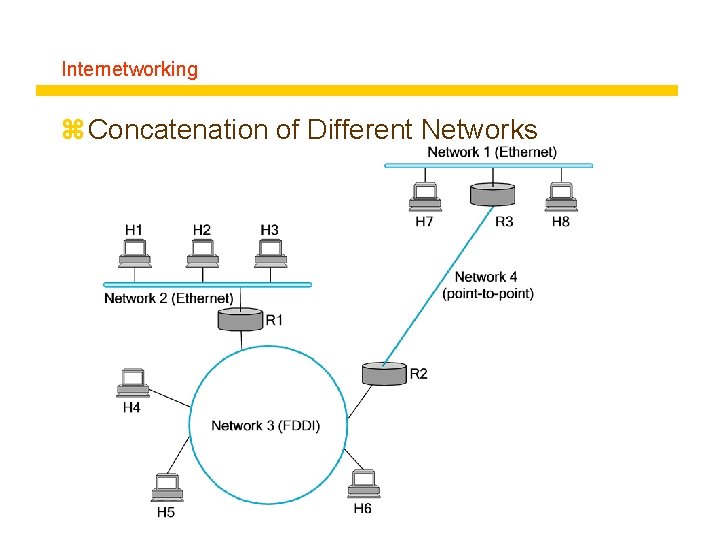
Internetworking z Concatenation of Different Networks

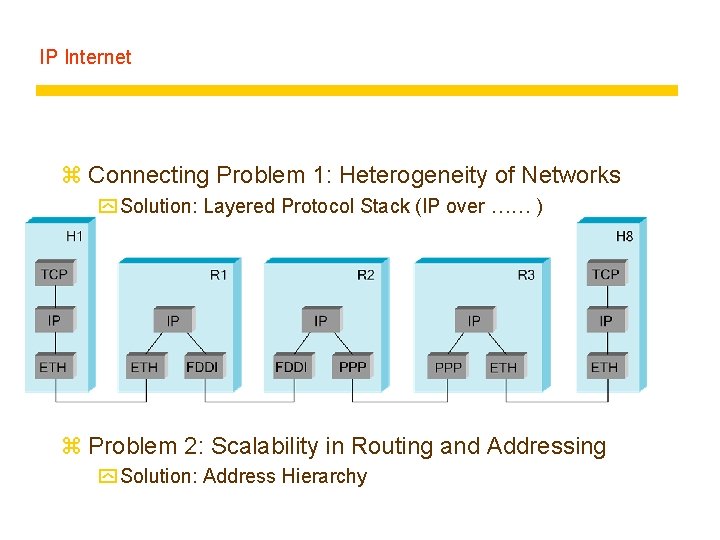
IP Internet z Connecting Problem 1: Heterogeneity of Networks y Solution: Layered Protocol Stack (IP over …… ) z Problem 2: Scalability in Routing and Addressing y Solution: Address Hierarchy

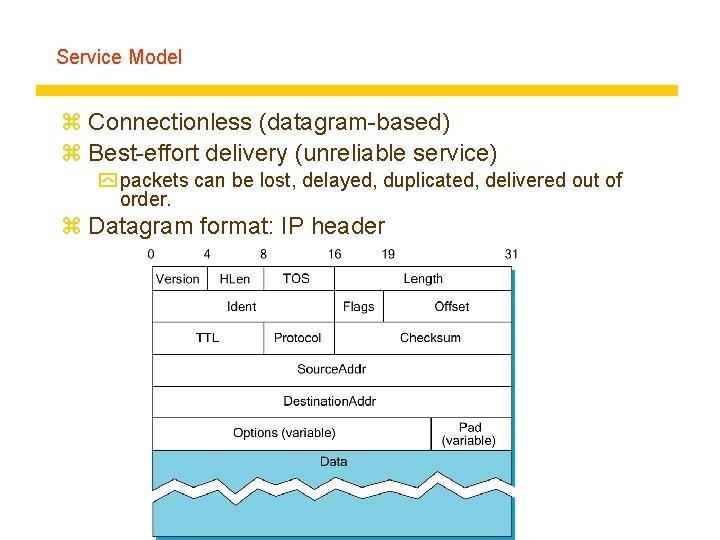
Service Model z Connectionless (datagram-based) z Best-effort delivery (unreliable service) y packets can be lost, delayed, duplicated, delivered out of order. z Datagram format: IP header

IP Header z Version (always set to the value 4 for IP v 4) z IP Header Length (number of 32 -bit words forming the header, usually five) z Size of Datagram (in bytes, header + data) z Flags 3 bits: R (reserved bit set to 0) DF (Don't fragment ) MF (More fragments) z Time To Live (Number of hops /links which the packet may be routed over, decremented by most routers - used to prevent accidental routing loops) z Protocol (the type of transport packet being carried (e. g. 1 = ICMP; 6 = TCP; 17= UDP). z Header Checksum (A 1's complement checksum of IP header, updated whenever the packet header is modified by a node. Packets with an invalid checksum are discarded by all nodes in an IP network) z Source Address / Destination Address

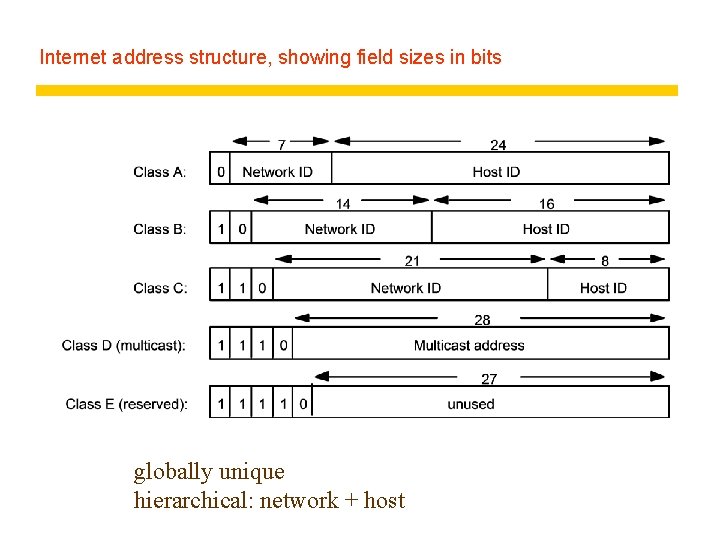
Internet address structure, showing field sizes in bits globally unique hierarchical: network + host

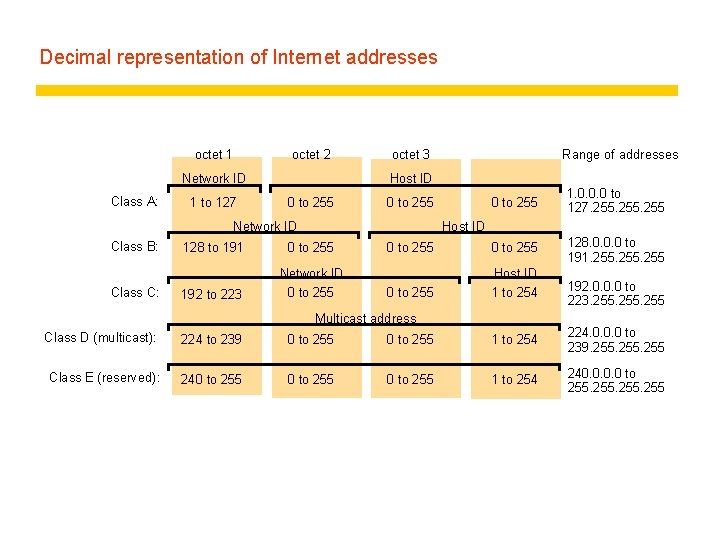
Decimal representation of Internet addresses octet 1 octet 2 Network ID Class A: 1 to 127 octet 3 Host ID 0 to 255 1. 0. 0. 0 to 127. 255 0 to 255 128. 0. 0. 0 to 191. 255 0 to 255 Host ID 1 to 254 0 to 255 Network ID Class B: Class C: Range of addresses Host ID 128 to 191 0 to 255 192 to 223 Network ID 0 to 255 Multicast address 192. 0. 0. 0 to 223. 255 Class D (multicast): 224 to 239 0 to 255 1 to 254 224. 0. 0. 0 to 239. 255 Class E (reserved): 240 to 255 1 to 254 240. 0 to 255

Datagram Forwarding Strategy z Every datagram contains destination’s address z if connected to destination network, then forward to the host in LAN y. If network number of destination IP == my network number z if not directly connected, then forward to the host’s default router z Each router maintains a forwarding table yforwarding table maps network number (rather than host address) into next hop or interface number (if directly connected)

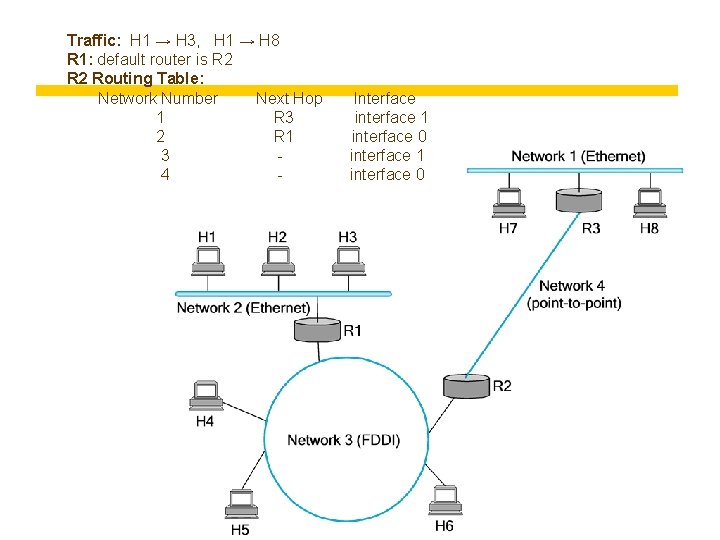
Traffic: H 1 → H 3, H 1 → H 8 R 1: default router is R 2 Routing Table: Network Number Next Hop 1 R 3 2 R 1 3 4 - Interface interface 1 interface 0

Address Translation in LAN z Map IP addresses into physical addresses of the destination host (if connected directly) or the next hop router z ARP y Each host caches its table of IP to physical address bindings y table entries are discarded if not refreshed x timeout in about 10 minutes y broadcast request if IP address not in table y target machine send its physical address to the sender y target machine also updates add entry of the source in its table x It is likely that the target will send IP packets to the source later on. y Other hosts (who receives the broadcasted request) update table if already have an entry

End-to-End Protocols z Underlying best-effort network y drop messages y re-orders messages y delivers duplicate copies of a given message y limits packet (not message) to some finite size y delivers messages after an arbitrarily long delay z Common end-to-end services y guarantee message delivery y deliver messages in the same order they are sent y deliver at most one copy of each message y support arbitrarily large messages y support synchronization between sender and receiver y allow the receiver to flow control the sender y support multiple application processes on each host

End-to-End Protocols (UDP/TCP)

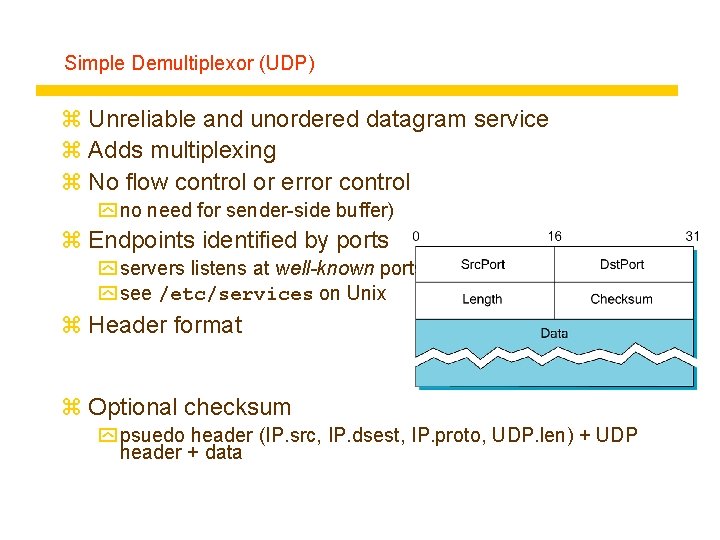
Simple Demultiplexor (UDP) z Unreliable and unordered datagram service z Adds multiplexing z No flow control or error control y no need for sender-side buffer) z Endpoints identified by ports y servers listens at well-known ports! y see /etc/services on Unix z Header format z Optional checksum y psuedo header (IP. src, IP. dsest, IP. proto, UDP. len) + UDP header + data

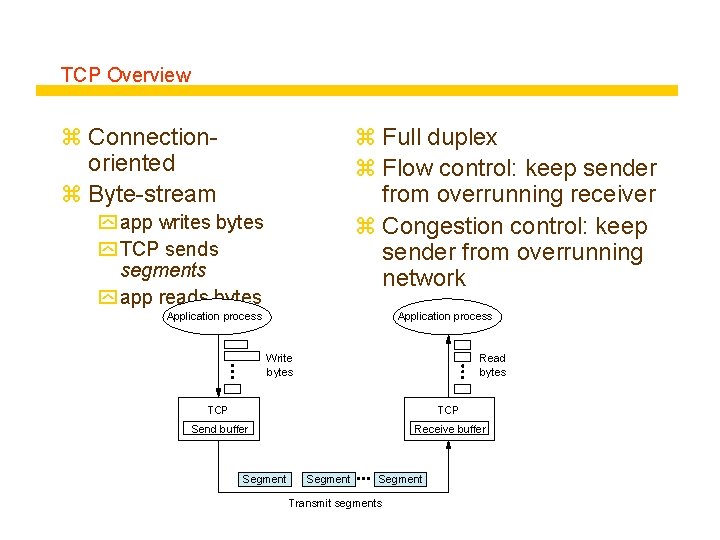
TCP Overview z Connectionoriented z Byte-stream z Full duplex z Flow control: keep sender from overrunning receiver z Congestion control: keep sender from overrunning network y app writes bytes y TCP sends segments y app reads bytes Application process Read bytes Write bytes TCP Send buffer Receive buffer Segment ■■■ Segment Transmit segments

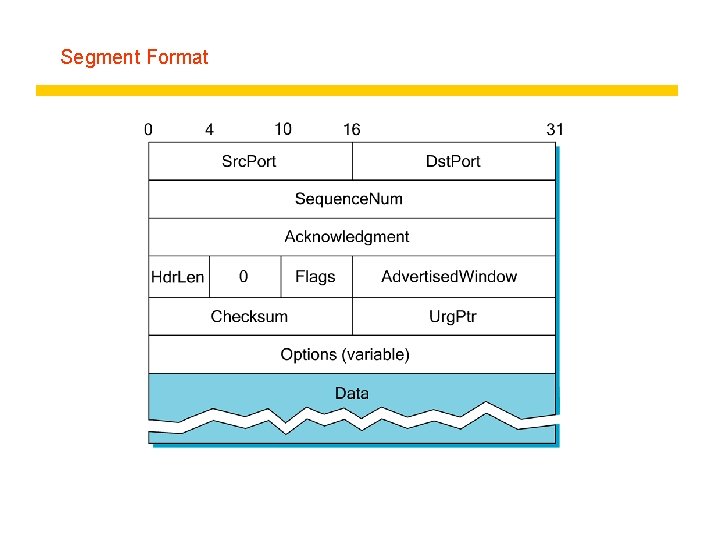
Segment Format

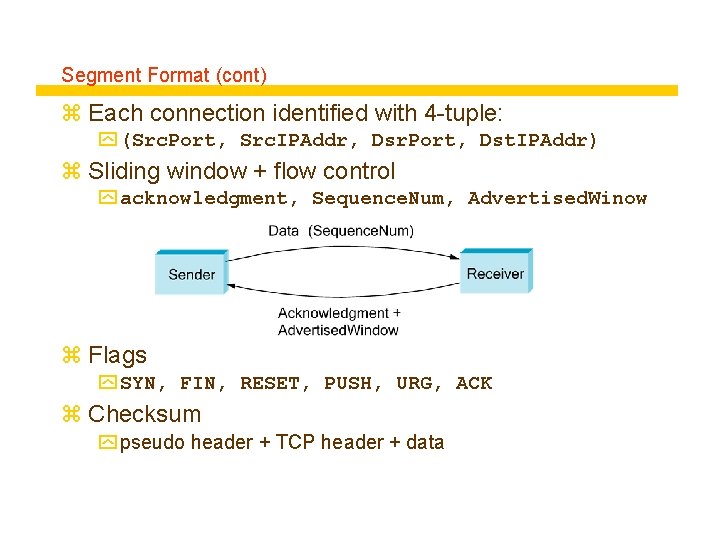
Segment Format (cont) z Each connection identified with 4 -tuple: y (Src. Port, Src. IPAddr, Dsr. Port, Dst. IPAddr) z Sliding window + flow control y acknowledgment, Sequence. Num, Advertised. Winow z Flags y SYN, FIN, RESET, PUSH, URG, ACK z Checksum y pseudo header + TCP header + data

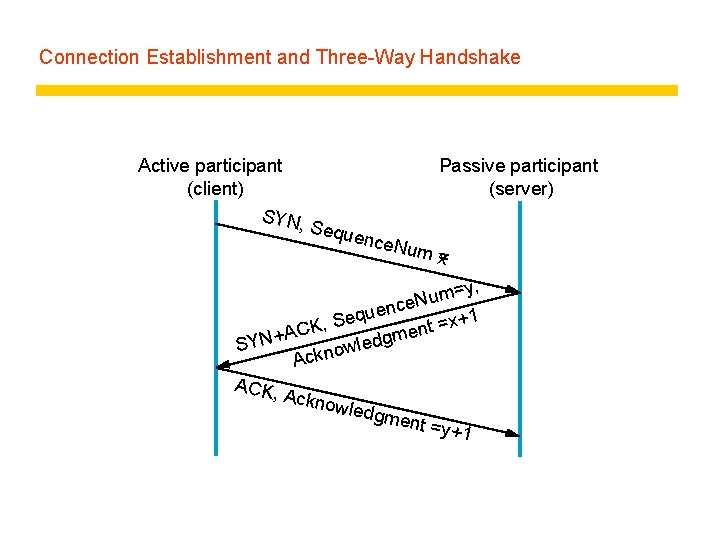
Connection Establishment and Three-Way Handshake Active participant (client) SYN, Passive participant (server) Sequ e nce. N um = x =y, m u N nce e u q e +1 S x , = t K AC men + g N d Y e l S ow Ackn ACK, Ackno wledg ment =y+1

Reliability and Flow Control z The receiver’s buffer has two purposes y. Reorder segments received out of order y. Hold data unread by the application z The sender cannot send more than Advertised. Window bytes of unacknowledged data at any given time (Flow Control). z The sender retransmits after timeout y. Adaptive RTT measurement.

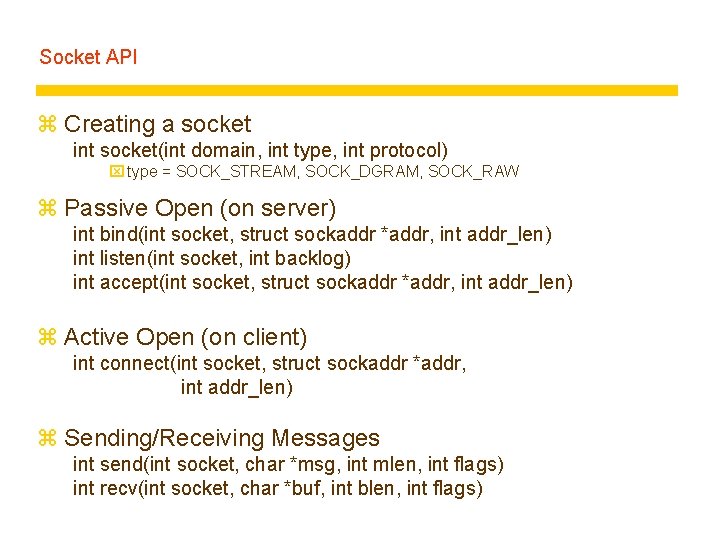
Socket API z Creating a socket int socket(int domain, int type, int protocol) x type = SOCK_STREAM, SOCK_DGRAM, SOCK_RAW z Passive Open (on server) int bind(int socket, struct sockaddr *addr, int addr_len) int listen(int socket, int backlog) int accept(int socket, struct sockaddr *addr, int addr_len) z Active Open (on client) int connect(int socket, struct sockaddr *addr, int addr_len) z Sending/Receiving Messages int send(int socket, char *msg, int mlen, int flags) int recv(int socket, char *buf, int blen, int flags)

Wireless LAN

Ethernet Overview z The most successful Local Area Networks z Bandwidth: 10 Mbps, 100 Mbps (Fast), 1 Gbps z Avoid Simultaneous on a Shared Line: CSMA/CD ymultiple access ycarrier sense: xlisten before transmitting. xdistinguish an idle and busy link. ycollision detection xlisten while transmitting. x. Collision: What you hear is different from what you listen

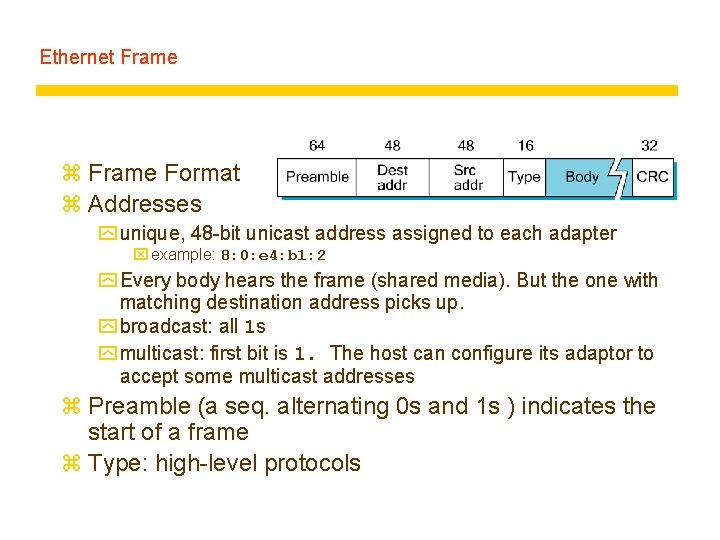
Ethernet Frame z Frame Format z Addresses y unique, 48 -bit unicast address assigned to each adapter x example: 8: 0: e 4: b 1: 2 y Every body hears the frame (shared media). But the one with matching destination address picks up. y broadcast: all 1 s y multicast: first bit is 1. The host can configure its adaptor to accept some multicast addresses z Preamble (a seq. alternating 0 s and 1 s ) indicates the start of a frame z Type: high-level protocols

Transmit Algorithm z If line is idle… ysend immediately yupper bound message size of 1500 bytes x. Limited occupancy on the line. ymust wait 9. 6 us between back-to-back frames x. To allow other hosts to send. z If line is busy… ywait until idle and transmit immediately

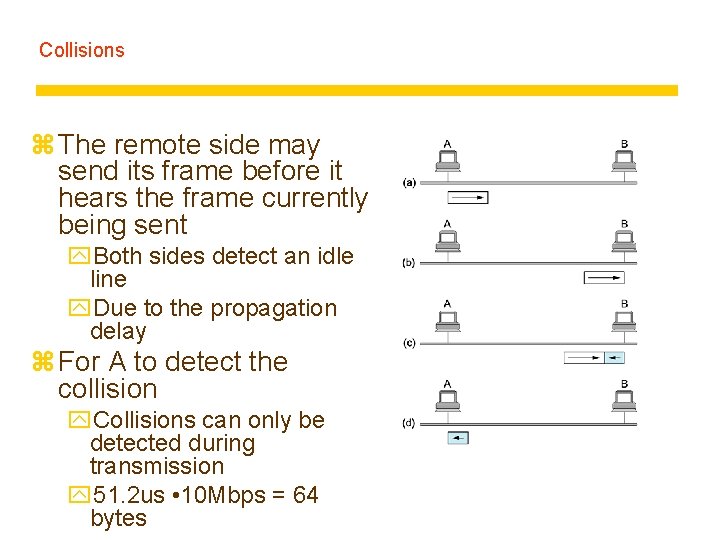
Collisions z The remote side may send its frame before it hears the frame currently being sent y. Both sides detect an idle line y. Due to the propagation delay z For A to detect the collision y. Collisions can only be detected during transmission y 51. 2 us • 10 Mbps = 64 bytes

Upon Collision z Send 32 jam bits, then stop transmitting frame y. To ensure other hosts to detect conllision z minimum frame is 64 bytes (header + 46 bytes of data) z delay and try again: exponential backoff y 1 st time: 0 or 51. 2 us selected at random y 2 nd time: 0, 51. 2, or 102. 4 us ynth time: k x 51. 2 us, for randomly selected k=0. . 2 n - 1 ygive up after several tries (usually 16)

Wireless LANs z IEEE 802. 11 z Bandwidth: 1 - 11 Mbps z Physical Media ydiffused infrared (10 m) x. Diffused: the sender do not need a clear line of sight. yspread spectrum radio (2. 4 GHz): 11 Mbps 54 Mbps

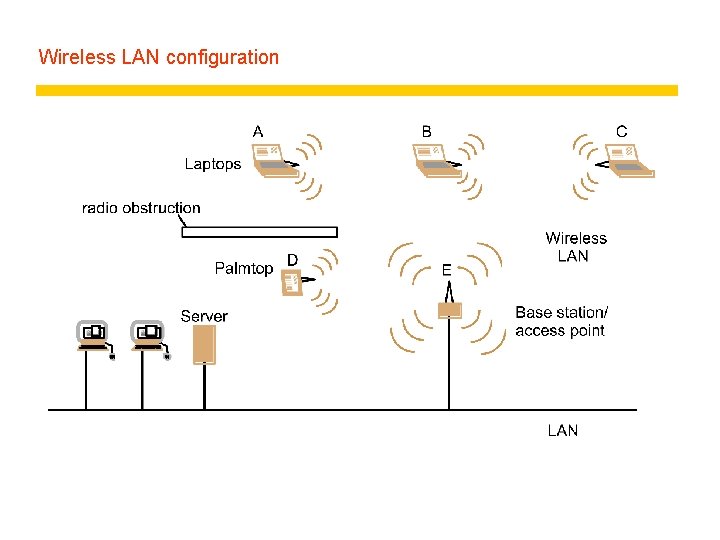
Wireless LAN configuration

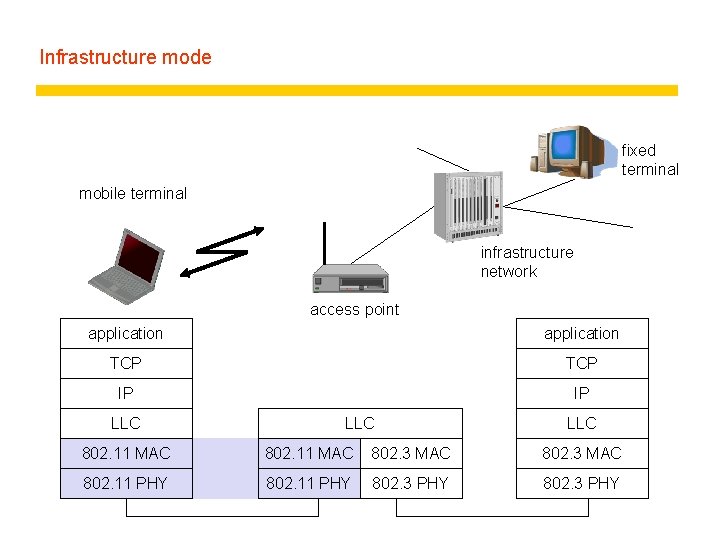
Infrastructure mode fixed terminal mobile terminal infrastructure network access point application TCP IP IP LLC LLC 802. 11 MAC 802. 3 MAC 802. 11 PHY 802. 3 PHY

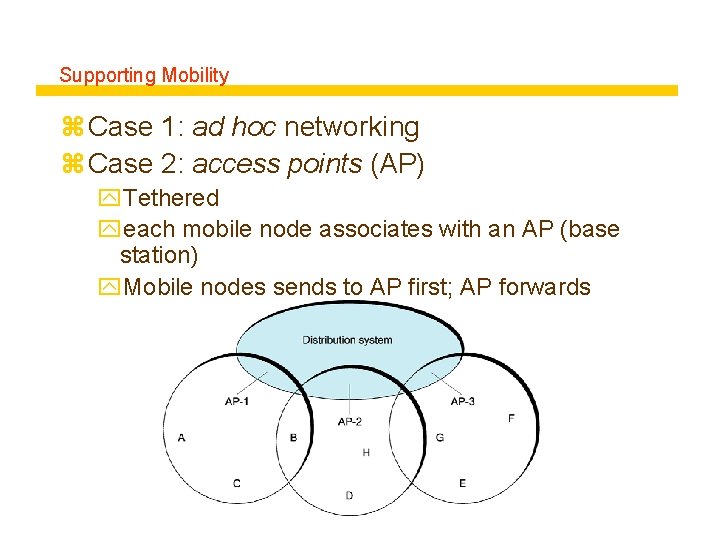
Supporting Mobility z Case 1: ad hoc networking z Case 2: access points (AP) y. Tethered yeach mobile node associates with an AP (base station) y. Mobile nodes sends to AP first; AP forwards

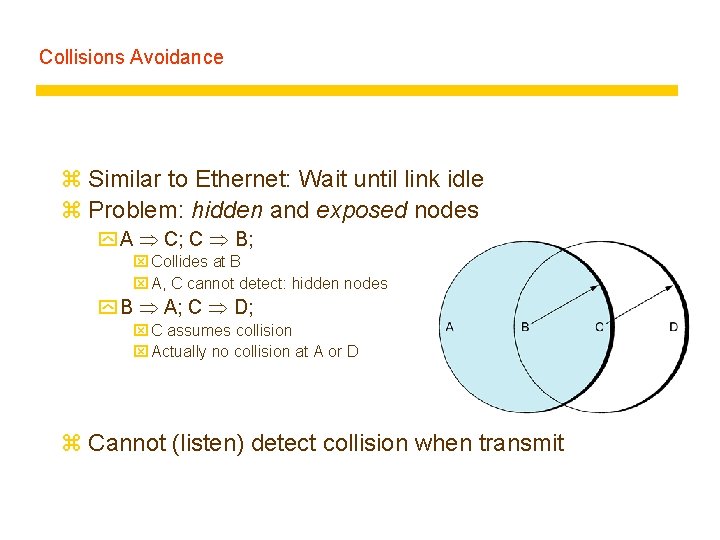
Collisions Avoidance z Similar to Ethernet: Wait until link idle z Problem: hidden and exposed nodes y A C; C B; x Collides at B x A, C cannot detect: hidden nodes y B A; C D; x C assumes collision x Actually no collision at A or D z Cannot (listen) detect collision when transmit

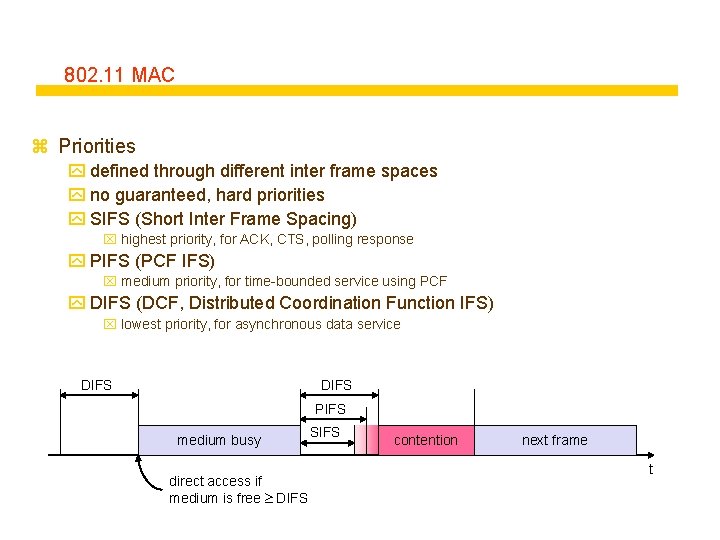
802. 11 MAC z Priorities y defined through different inter frame spaces y no guaranteed, hard priorities y SIFS (Short Inter Frame Spacing) x highest priority, for ACK, CTS, polling response y PIFS (PCF IFS) x medium priority, for time-bounded service using PCF y DIFS (DCF, Distributed Coordination Function IFS) x lowest priority, for asynchronous data service DIFS PIFS medium busy direct access if medium is free DIFS SIFS contention next frame t

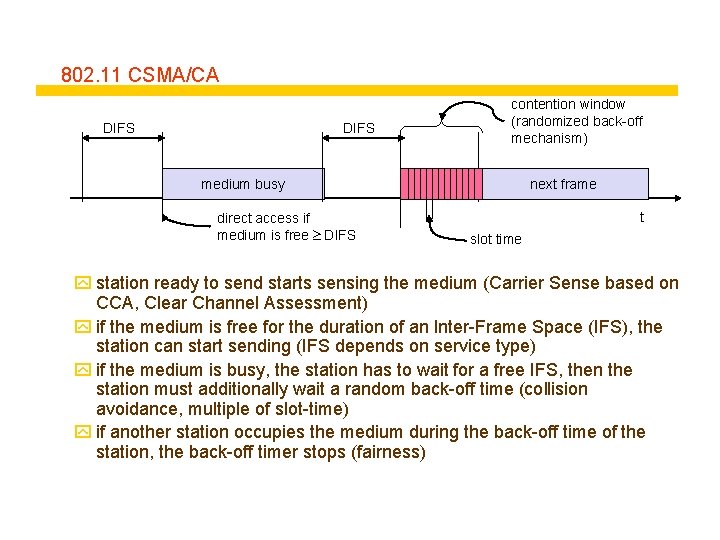
802. 11 CSMA/CA DIFS contention window (randomized back-off mechanism) medium busy direct access if medium is free DIFS next frame t slot time y station ready to send starts sensing the medium (Carrier Sense based on CCA, Clear Channel Assessment) y if the medium is free for the duration of an Inter-Frame Space (IFS), the station can start sending (IFS depends on service type) y if the medium is busy, the station has to wait for a free IFS, then the station must additionally wait a random back-off time (collision avoidance, multiple of slot-time) y if another station occupies the medium during the back-off time of the station, the back-off timer stops (fairness)

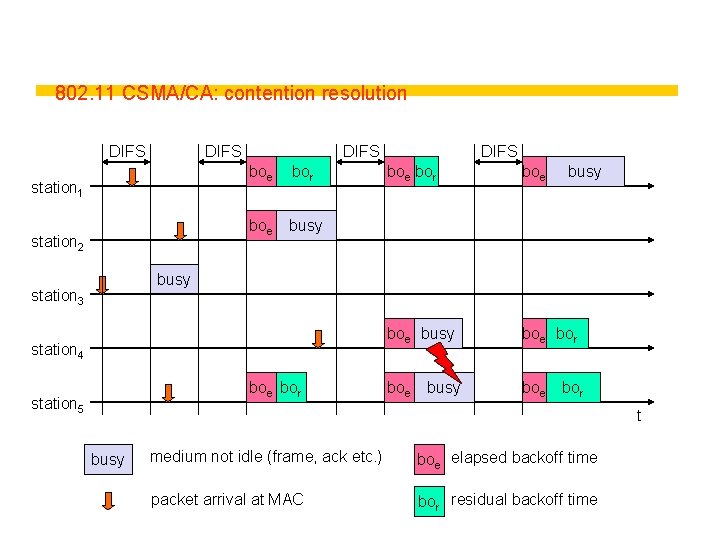
802. 11 CSMA/CA: contention resolution DIFS station 1 station 2 DIFS boe bor boe busy boe bor boe busy station 3 station 4 boe bor station 5 busy bor t busy medium not idle (frame, ack etc. ) boe elapsed backoff time packet arrival at MAC bor residual backoff time

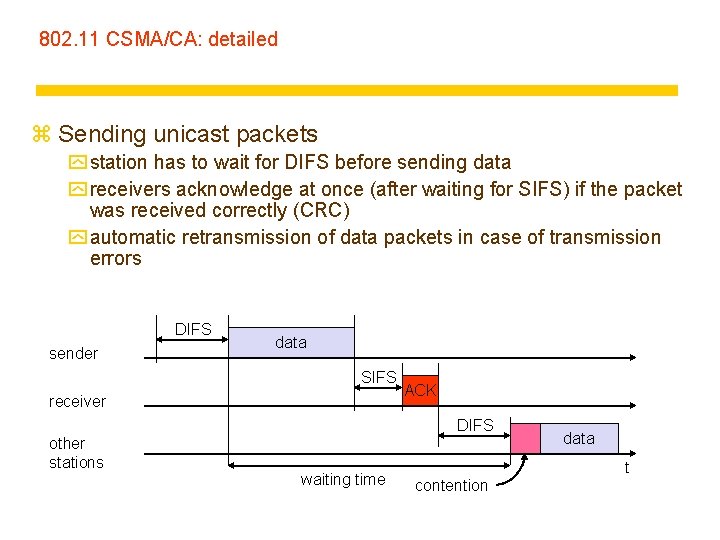
802. 11 CSMA/CA: detailed z Sending unicast packets y station has to wait for DIFS before sending data y receivers acknowledge at once (after waiting for SIFS) if the packet was received correctly (CRC) y automatic retransmission of data packets in case of transmission errors DIFS sender data SIFS receiver ACK DIFS other stations waiting time data t contention

Multiple Access with Collision Avoidance (MACA) z Sender transmits Request. To. Send (RTS) frame y Specifying how long to hold the medium z Receiver replies with Clear. To. Send (CTS) frame z Neighbors… y see CTS: keep quiet y see RTS but not CTS: receiver cannot hear me, ok to transmit z Receive sends ACK when has frame y neighbors silent until see ACK z Collisions y no collisions detection y known when don’t receive CTS or ACK x The cost of collision with RTS/CTS is much smaller y exponential backoff

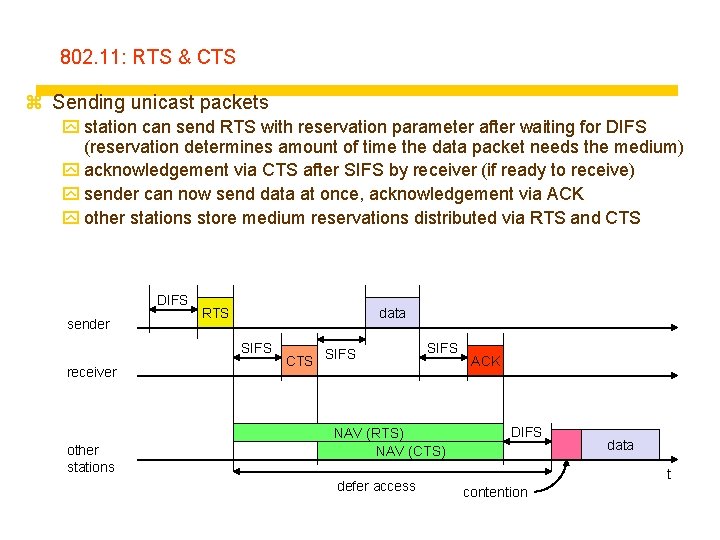
802. 11: RTS & CTS z Sending unicast packets y station can send RTS with reservation parameter after waiting for DIFS (reservation determines amount of time the data packet needs the medium) y acknowledgement via CTS after SIFS by receiver (if ready to receive) y sender can now send data at once, acknowledgement via ACK y other stations store medium reservations distributed via RTS and CTS DIFS sender RTS data SIFS receiver other stations CTS SIFS NAV (RTS) NAV (CTS) defer access ACK DIFS data t contention

Mobility (cont) z Scanning (selecting an AP) ynode sends Probe frame yall AP’s w/in reach reply with Probe. Response frame ynode selects one AP; sends it Associate. Request frame y. AP replies with Association. Response frame z When yactive: when join or move x. Signal with old AP weakened xnew AP informs old AP via tethered network ypassive: AP periodically sends Beacon frame