Chapter 3 3 4 The Integers and Division






- Slides: 13

Chapter 3 – – – 3. 4 The Integers and Division The Division Algorithm Modular Arithmetic Applications of Congruences Cryptology 1

Division • Definition 1: if a and b are integers with a≠ 0, we say that a divides b if there is an integer c such that b=ac. When a divides b we say that a is a factor of b and that b is a multiple of a. the notation a|b denotes that a divides b. we write a /| b when a does not divide b. • Example 1: Determine whether 3|7 and whether 3|12. • Example: Determine whether 3|0. 2

• Theorem 1: let a, b, and c be integers. Then 1. If a|b and a|c, then a|(b+c) 2. If a|b and a|bc for all integer c 3. If a|b and b|c, then a|c • Corollary 1: If a, b, c are integers such that a|b and a|c , then a| mb + nc whenever m and n are integers. 3

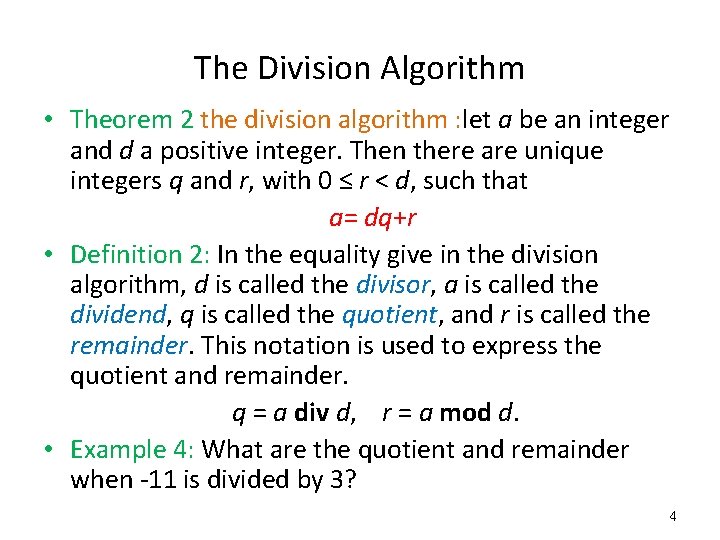
The Division Algorithm • Theorem 2 the division algorithm : let a be an integer and d a positive integer. Then there are unique integers q and r, with 0 ≤ r < d, such that a= dq+r • Definition 2: In the equality give in the division algorithm, d is called the divisor, a is called the dividend, q is called the quotient, and r is called the remainder. This notation is used to express the quotient and remainder. q = a div d, r = a mod d. • Example 4: What are the quotient and remainder when -11 is divided by 3? 4

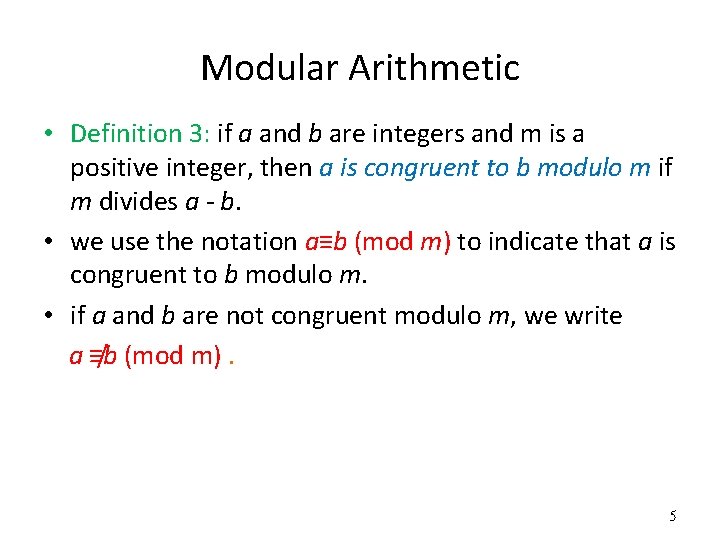
Modular Arithmetic • Definition 3: if a and b are integers and m is a positive integer, then a is congruent to b modulo m if m divides a - b. • we use the notation a≡b (mod m) to indicate that a is congruent to b modulo m. • if a and b are not congruent modulo m, we write / (mod m). a ≡b 5

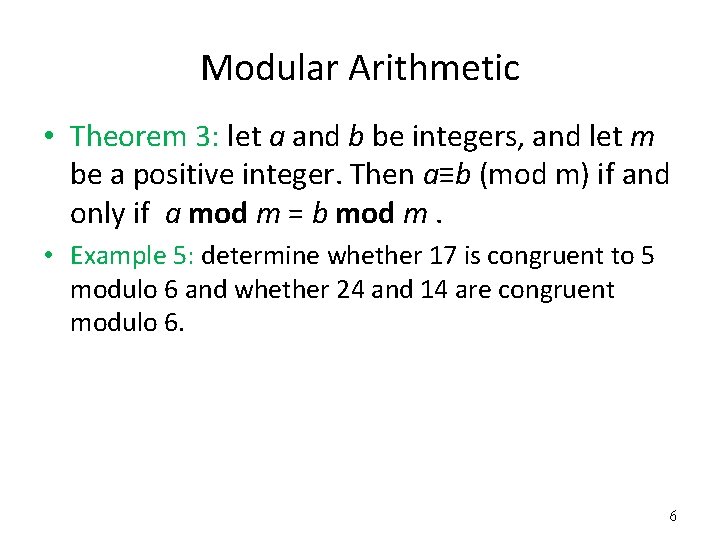
Modular Arithmetic • Theorem 3: let a and b be integers, and let m be a positive integer. Then a≡b (mod m) if and only if a mod m = b mod m. • Example 5: determine whether 17 is congruent to 5 modulo 6 and whether 24 and 14 are congruent modulo 6. 6

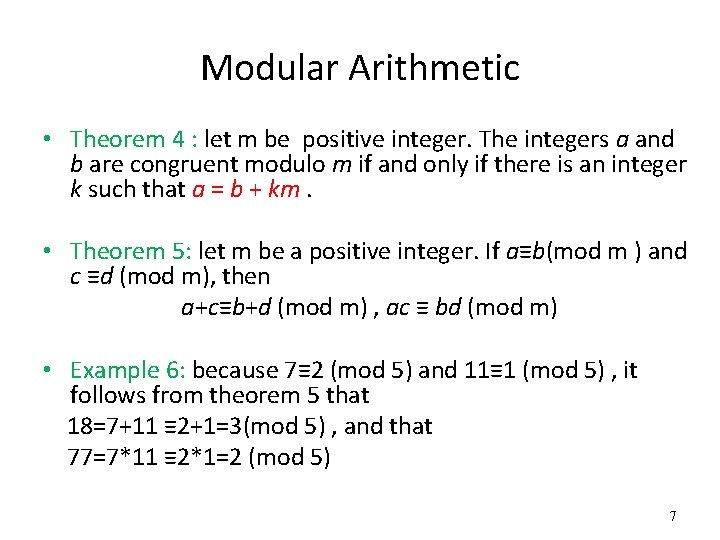
Modular Arithmetic • Theorem 4 : let m be positive integer. The integers a and b are congruent modulo m if and only if there is an integer k such that a = b + km. • Theorem 5: let m be a positive integer. If a≡b(mod m ) and c ≡d (mod m), then a+c≡b+d (mod m) , ac ≡ bd (mod m) • Example 6: because 7≡ 2 (mod 5) and 11≡ 1 (mod 5) , it follows from theorem 5 that 18=7+11 ≡ 2+1=3(mod 5) , and that 77=7*11 ≡ 2*1=2 (mod 5) 7

• Corollary 2: let m be a positive integer and let a and b be integers. Then (a+b) mod m = ((a mod m)+(b mod m)) mod m And ab mod m =((a mod m)(b mod m)) mod m. 8

Applications of Congruences • Hashing Functions • Pseudorandom Numbers • Cryptology 9

Hashing Functions • How can memory locations be assigned so that customer records can be retrieved quickly? • Hashing function and key • h(k) = k mod m; m is the number of available memory locations. • Collision: one way to re solve a collision is to assign the first free location. 10

Pseudorandom Numbers • The numbers generated by systematic method are not truly random, they are called pseudorandom numbers. • Linear Congruential Method(m, a, c, x 0 : integers): • Modulus m • Multiplier a, 2 a < m • Increment c, 0 c < m • Seed x 0 , 0 x 0 < m • xn+1= (axn+c) mod m • For example: m=9, a=7, c=4, x 0 =3, then (x 1, x 2, x 3, x 4, x 5, x 6, x 7, x 8, x 9)=(7, 8, 6, 1, 2, 0, 4, 5, 3) x 10=x 1 11

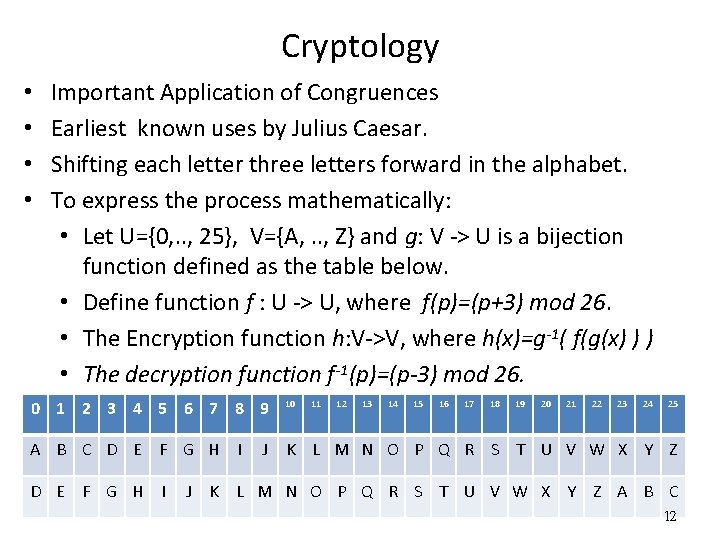
Cryptology • • Important Application of Congruences Earliest known uses by Julius Caesar. Shifting each letter three letters forward in the alphabet. To express the process mathematically: • Let U={0, . . , 25}, V={A, . . , Z} and g: V -> U is a bijection function defined as the table below. • Define function f : U -> U, where f(p)=(p+3) mod 26. • The Encryption function h: V->V, where h(x)=g-1( f(g(x) ) ) • The decryption function f-1(p)=(p-3) mod 26. 0 1 2 3 4 5 6 7 8 9 A B C D E F G H I 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 J K L M N O P Q R S T U V W X Y Z A B C 12

Applications of Congruences • Example 9: • What is the secret message produced from the message “MEET YOU IN THE PARK” using the Caesar cipher. • HW: Example 10, p 208 13