Chapter 21 Security Computer Center CS NCTU Free





![Computer Center, CS, NCTU setuid program q /etc/passwd zfs[~] -chiahung- ls -al /usr/bin/passwd -r-sr-xr-x Computer Center, CS, NCTU setuid program q /etc/passwd zfs[~] -chiahung- ls -al /usr/bin/passwd -r-sr-xr-x](https://slidetodoc.com/presentation_image/9e3014a05cae2e421231ba825374a69f/image-11.jpg)






- Slides: 28

Chapter 21 Security

Computer Center, CS, NCTU Free. BSD Security Advisories q http: //www. freebsd. org/security/advisors. html q Upcoming Free. BSD Security Advisory • Announced on 12/1 • Zero-day-exploit 2

Computer Center, CS, NCTU 3 Free. BSD Security Advisories q Advisory • Security information q Where to find it • freebsd-security-notifications Mailing list Ø http: //lists. freebsd. org/mailman/listinfo/freebsd-security-notifications • Web page (Security Advisories Channel) Ø http: //www. freebsd. org

Computer Center, CS, NCTU 4 Free. BSD Security Advisories q Example • rtld

Computer Center, CS, NCTU 5 Free. BSD Security Advisories (4) q Example • Description

Computer Center, CS, NCTU 6 Free. BSD Security Advisories (5) q Example • Workaround • Solution

Computer Center, CS, NCTU Common Security Problems q Unreliable wetware • Phishing site q Software bugs • Free. BSD security advisor • portaudit q Open doors • Account password • Disk share with the world 7

Computer Center, CS, NCTU Common trick q Tricks • ssh scan and hack Ø ssh guard Ø sshit Ø… • Phishing • XSS & sql injection • … q Objective • • 8 Spam Jump gateway File sharing …

Computer Center, CS, NCTU 9 Process file system - procfs q Procfs • A view of the system process table • Normally mount on /proc • mount –t procfs proc /proc

Computer Center, CS, NCTU 10 Simple SQL injection example q User/pass authentication SELECT * FROM usr. Table WHERE user = AND pass = ; q No input validation SELECT * FROM usr. Table WHERE user = ‘test’ AND pass = ‘a’ OR ‘a’ = ‘a’
![Computer Center CS NCTU setuid program q etcpasswd zfs chiahung ls al usrbinpasswd rsrxrx Computer Center, CS, NCTU setuid program q /etc/passwd zfs[~] -chiahung- ls -al /usr/bin/passwd -r-sr-xr-x](https://slidetodoc.com/presentation_image/9e3014a05cae2e421231ba825374a69f/image-11.jpg)
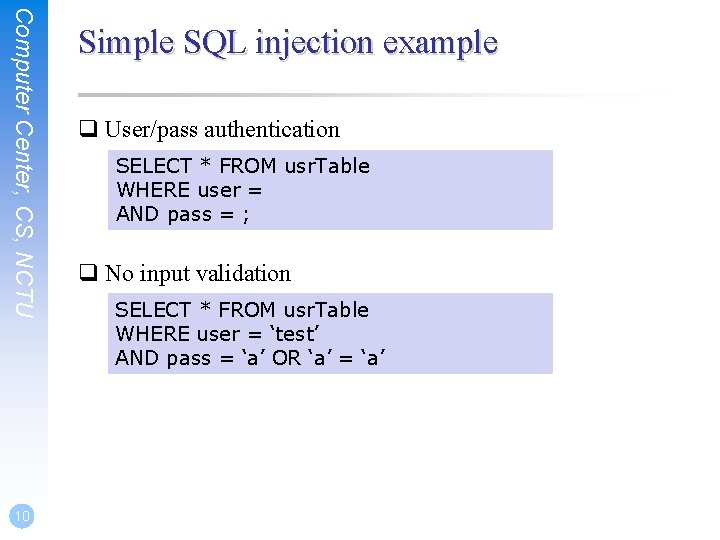
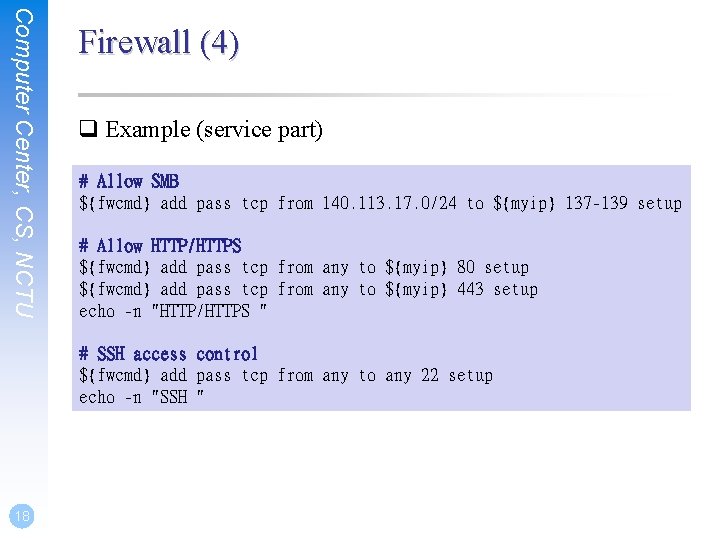
Computer Center, CS, NCTU setuid program q /etc/passwd zfs[~] -chiahung- ls -al /usr/bin/passwd -r-sr-xr-x 2 root wheel 8224 Dec 5 22: 00 /usr/bin/passwd • /etc/master. passwd is read only ! q Setuid shell scripts are especially apt to cause security problems • Minimize the number of setuid programs /usr/bin/find / -user root –perm -4000 –print | /bin/mail –s “Setuid root files” username • Disable the setuid execution on individual filesystems Ø -o nosuid 11

Computer Center, CS, NCTU Security issues q /etc/hosts. equiv and ~/. rhosts q Trusted remote host and user name DB • Allow user to login (via rlogin) and copy files (rcp) between machines without passwords • Format: Ø Simple: hostname [username] Ø Complex: [+-][hostname|@netgroup] [[+-][username|@netgorup]] • Example Ø bar. com foo Ø +@adm_cs_cc -@chwong q Do not use this 12 (trust user “foo” from host “bar. com”) (trust all from amd_cs_cc group)

Computer Center, CS, NCTU 13 Security tools q nmap q jhon, crack q PGP q CA q…

Computer Center, CS, NCTU 14 Firewall q Free. BSD firewalls • ipfw -- IP firewall and traffic shaper control program Ø ipfw(8) • ipf (IP Filter) - alters packet filtering lists for IP packet input and output Ø ipf(8) • pf -- packet filter Ø pf(4)

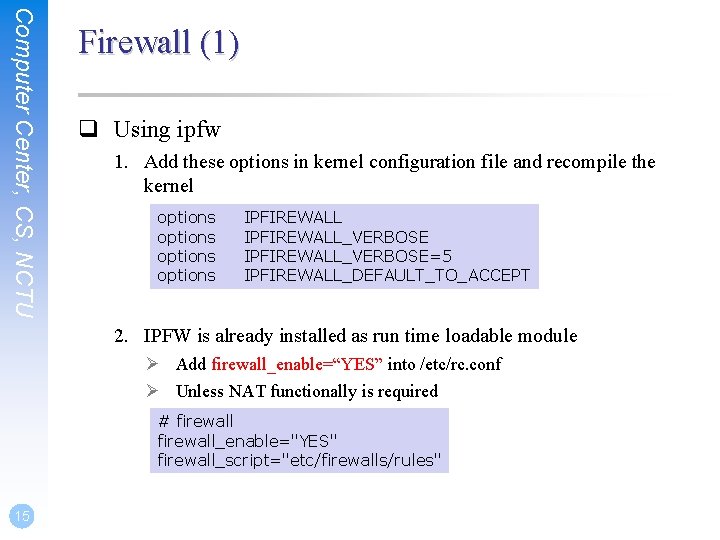
Computer Center, CS, NCTU Firewall (1) q Using ipfw 1. Add these options in kernel configuration file and recompile the kernel options IPFIREWALL_VERBOSE=5 IPFIREWALL_DEFAULT_TO_ACCEPT 2. IPFW is already installed as run time loadable module Ø Add firewall_enable=“YES” into /etc/rc. conf Ø Unless NAT functionally is required # firewall_enable="YES" firewall_script="etc/firewalls/rules" 15

Computer Center, CS, NCTU 16 Firewall (2) 3. Edit ipfw command script that you specify in rc. conf Ø Ex: /etc/firewall/rules 4. ipfw command Ø % sudo ipfw list Ø % sudo ipfw flush (show current firewall rules) (delete all firewall rules) Ø % ipfw add {pass|deny} {udp|tcp|all} from where to where

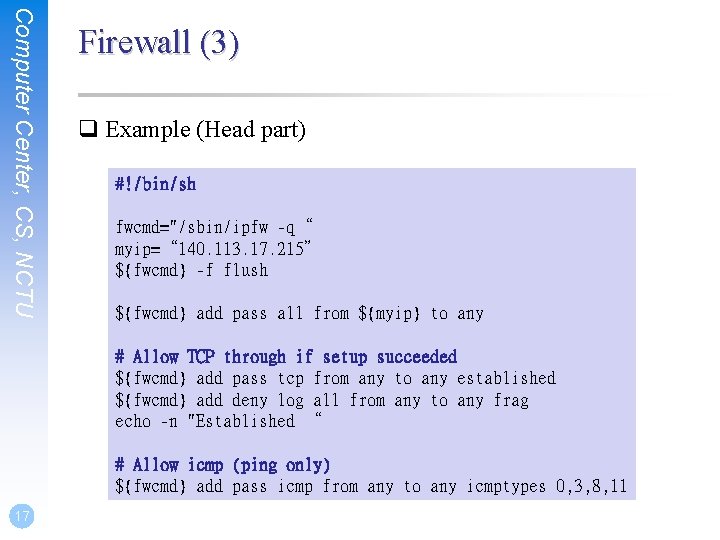
Computer Center, CS, NCTU Firewall (3) q Example (Head part) #!/bin/sh fwcmd="/sbin/ipfw -q“ myip=“ 140. 113. 17. 215” ${fwcmd} -f flush ${fwcmd} add pass all from ${myip} to any # Allow TCP through if setup succeeded ${fwcmd} add pass tcp from any to any established ${fwcmd} add deny log all from any to any frag echo -n "Established “ # Allow icmp (ping only) ${fwcmd} add pass icmp from any to any icmptypes 0, 3, 8, 11 17

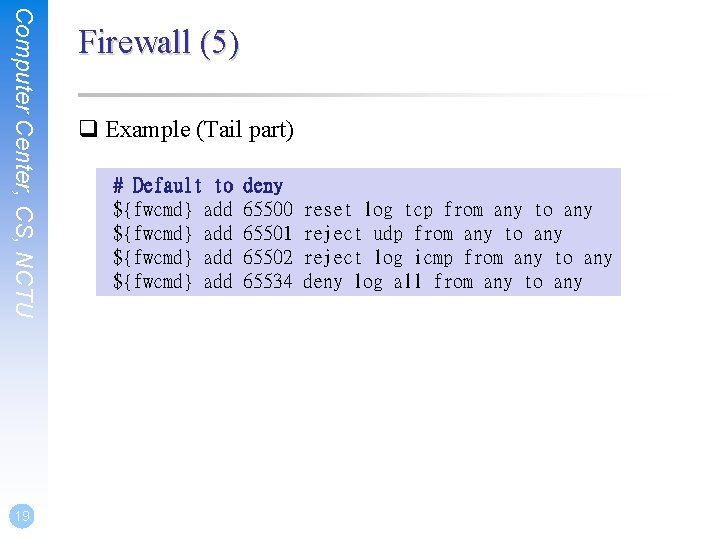
Computer Center, CS, NCTU Firewall (4) q Example (service part) # Allow SMB ${fwcmd} add pass tcp from 140. 113. 17. 0/24 to ${myip} 137 -139 setup # Allow HTTP/HTTPS ${fwcmd} add pass tcp from any to ${myip} 80 setup ${fwcmd} add pass tcp from any to ${myip} 443 setup echo -n "HTTP/HTTPS " # SSH access control ${fwcmd} add pass tcp from any to any 22 setup echo -n "SSH " 18

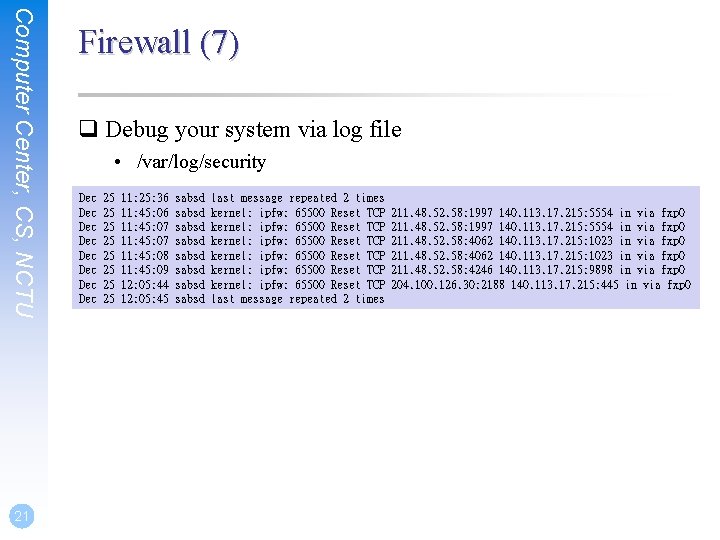
Computer Center, CS, NCTU 19 Firewall (5) q Example (Tail part) # Default to ${fwcmd} add deny 65500 65501 65502 65534 reset log tcp from any to any reject udp from any to any reject log icmp from any to any deny log all from any to any

Computer Center, CS, NCTU 20 Firewall (6) q Manual reset firewall rules • Edit the script and • % sudo sh /etc/firewall/rules q When you install new service and wondering why it can not use… • % sudo ipfw flush • Delete all firewall rules to remove problems caused by firewall

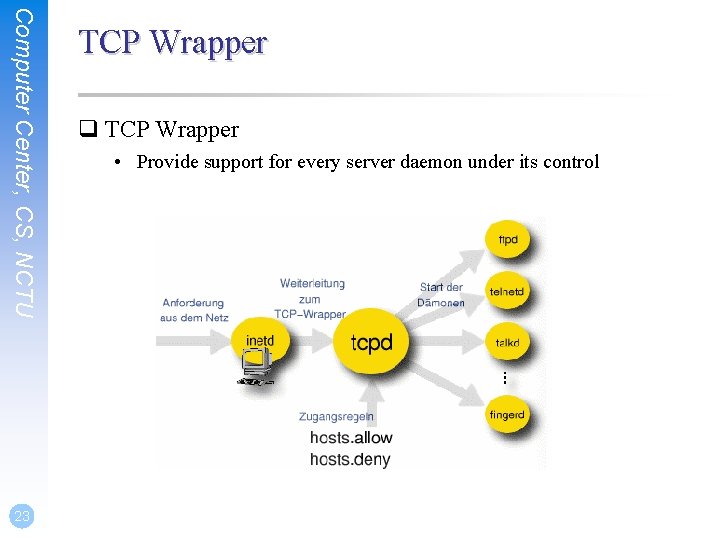
Computer Center, CS, NCTU 21 Firewall (7) q Debug your system via log file • /var/log/security Dec Dec 25 25 11: 25: 36 11: 45: 07 11: 45: 08 11: 45: 09 12: 05: 44 12: 05: 45 sabsd sabsd last message repeated 2 times kernel: ipfw: 65500 Reset TCP kernel: ipfw: 65500 Reset TCP last message repeated 2 times 211. 48. 52. 58: 1997 140. 113. 17. 215: 5554 in via fxp 0 211. 48. 52. 58: 4062 140. 113. 17. 215: 1023 in via fxp 0 211. 48. 52. 58: 4246 140. 113. 17. 215: 9898 in via fxp 0 204. 100. 126. 30: 2188 140. 113. 17. 215: 445 in via fxp 0

Computer Center, CS, NCTU 22 TCP Wrapper q There are something that a firewall will not handle • Sending text back to the source q TCP wrapper • Extend the abilities of inetd Ø Provide support for every server daemon under its control • Logging support • Return message • Permit a daemon to only accept internal connetions

Computer Center, CS, NCTU 23 TCP Wrapper q TCP Wrapper • Provide support for every server daemon under its control

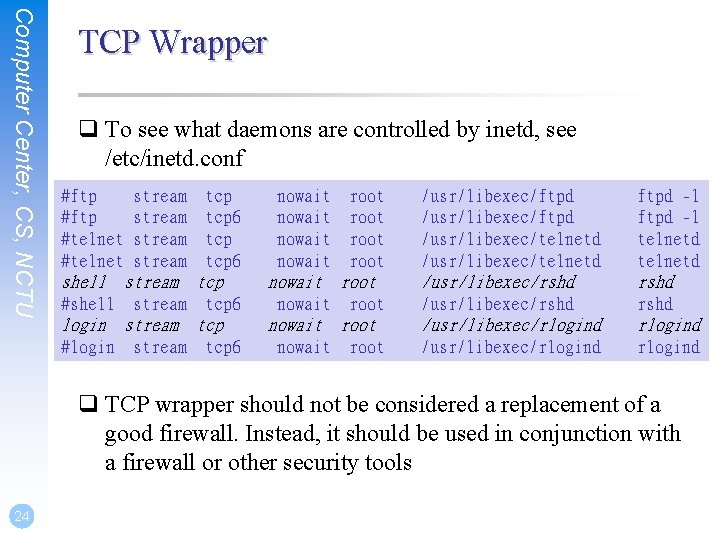
Computer Center, CS, NCTU TCP Wrapper q To see what daemons are controlled by inetd, see /etc/inetd. conf #ftp #telnet stream tcp tcp 6 shell stream tcp #shell stream tcp 6 login stream tcp #login stream tcp 6 nowait root nowait root /usr/libexec/ftpd /usr/libexec/telnetd ftpd -l telnetd /usr/libexec/rshd /usr/libexec/rlogind q TCP wrapper should not be considered a replacement of a good firewall. Instead, it should be used in conjunction with a firewall or other security tools 24

Computer Center, CS, NCTU TCP Wrapper q To use TCP wrapper 1. inetd daemon must start up with “-Ww” option (default) Or edit /etc/rc. conf inetd_enable="YES" inetd_flags="-w. W" • Edit /etc/hosts. allow Ø Format: daemon: address: action – daemon is the daemon name which inetd started – address can be hostname, IPv 4 addr, IPv 6 addr – action can be “allow” or “deny” – Keyword “ALL” can be used in daemon and address fields to means everything 25

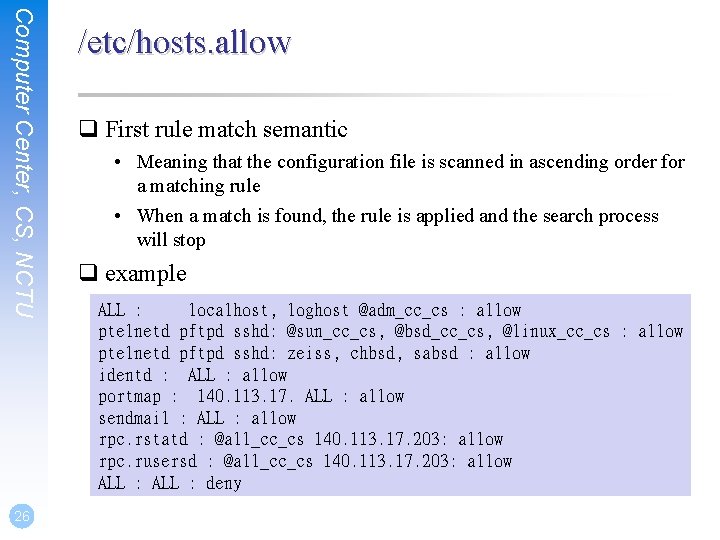
Computer Center, CS, NCTU 26 /etc/hosts. allow q First rule match semantic • Meaning that the configuration file is scanned in ascending order for a matching rule • When a match is found, the rule is applied and the search process will stop q example ALL : localhost, loghost @adm_cc_cs : allow ptelnetd pftpd sshd: @sun_cc_cs, @bsd_cc_cs, @linux_cc_cs : allow ptelnetd pftpd sshd: zeiss, chbsd, sabsd : allow identd : ALL : allow portmap : 140. 113. 17. ALL : allow sendmail : ALL : allow rpc. rstatd : @all_cc_cs 140. 113. 17. 203: allow rpc. rusersd : @all_cc_cs 140. 113. 17. 203: allow ALL : deny

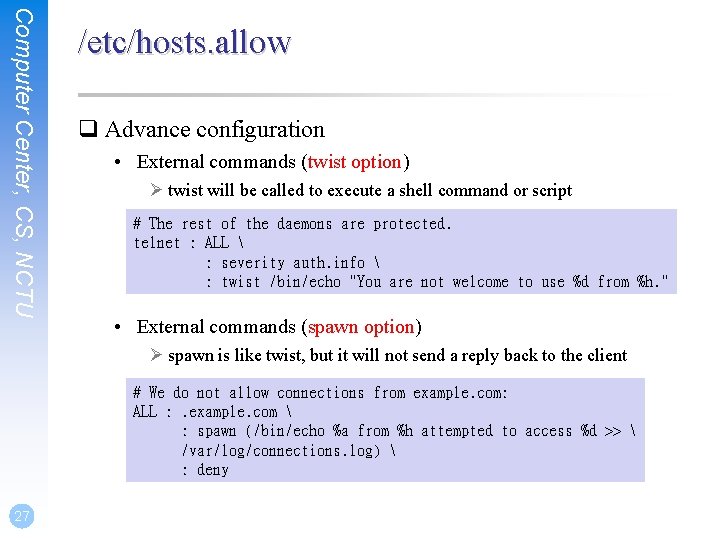
Computer Center, CS, NCTU /etc/hosts. allow q Advance configuration • External commands (twist option) Ø twist will be called to execute a shell command or script # The rest of the daemons are protected. telnet : ALL : severity auth. info : twist /bin/echo "You are not welcome to use %d from %h. " • External commands (spawn option) Ø spawn is like twist, but it will not send a reply back to the client # We do not allow connections from example. com: ALL : . example. com : spawn (/bin/echo %a from %h attempted to access %d >> /var/log/connections. log) : deny 27

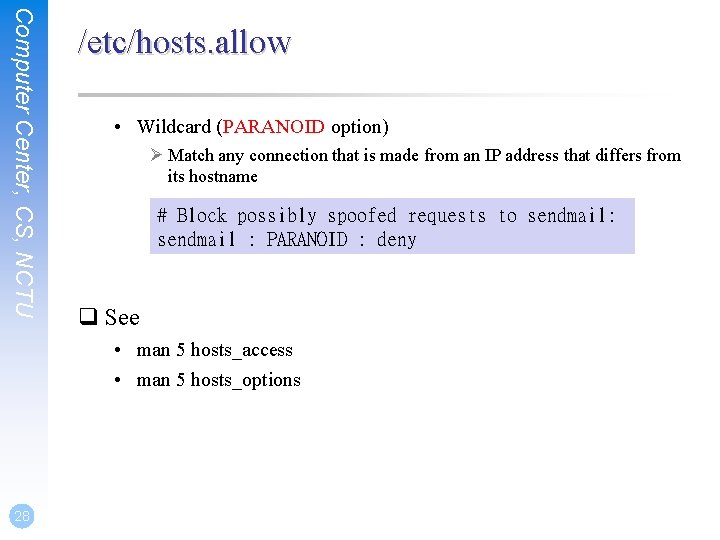
Computer Center, CS, NCTU /etc/hosts. allow • Wildcard (PARANOID option) Ø Match any connection that is made from an IP address that differs from its hostname # Block possibly spoofed requests to sendmail: sendmail : PARANOID : deny q See • man 5 hosts_access • man 5 hosts_options 28