Chapter 2 Information Security Fundamentals Certification Objectives Comp


Chapter 2 Information Security Fundamentals

Certification Objectives • Comp. TIA Security+ • 1. 1 Given a scenario, analyze indicators of compromise and determine the type of malware. • 1. 2 Compare and contrast types of attacks. • 1. 6 Explain the impact associated with types of vulnerabilities. • 2. 5 Given a scenario, deploy mobile devices securely. • 3. 1 Explain use cases and purpose for frameworks, best practices and secure configuration guides. • 5. 8 Given a scenario, carry out data security and privacy policies. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Certification Objectives (continued) • Microsoft MTA Security Fundamentals • 1. 1 Understand core security principles. • 1. 2 Understand physical security. • 1. 3 Understand Internet security. • 2. 6 Understand malware. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 1 Security Principles
Key Terms • attack surface • CIA triad • confidentiality • defense in depth • frameworks • integrity • Internet of Things (Io. T) • nonrepudiation process Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Learning Goals • Explain each of the three main security principles. • Identify business security domains. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
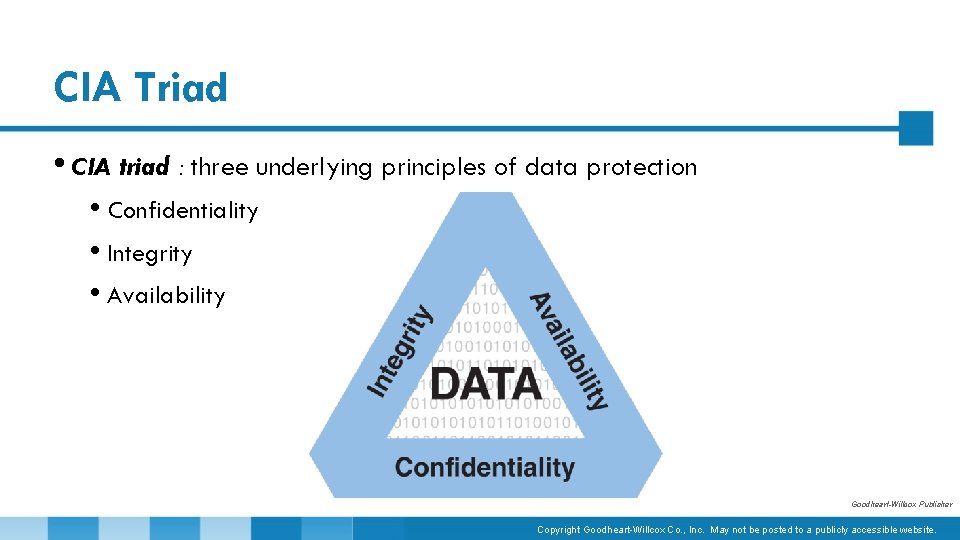
CIA Triad • CIA triad : three underlying principles of data protection • Confidentiality • Integrity • Availability Goodheart-Willcox Publisher Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

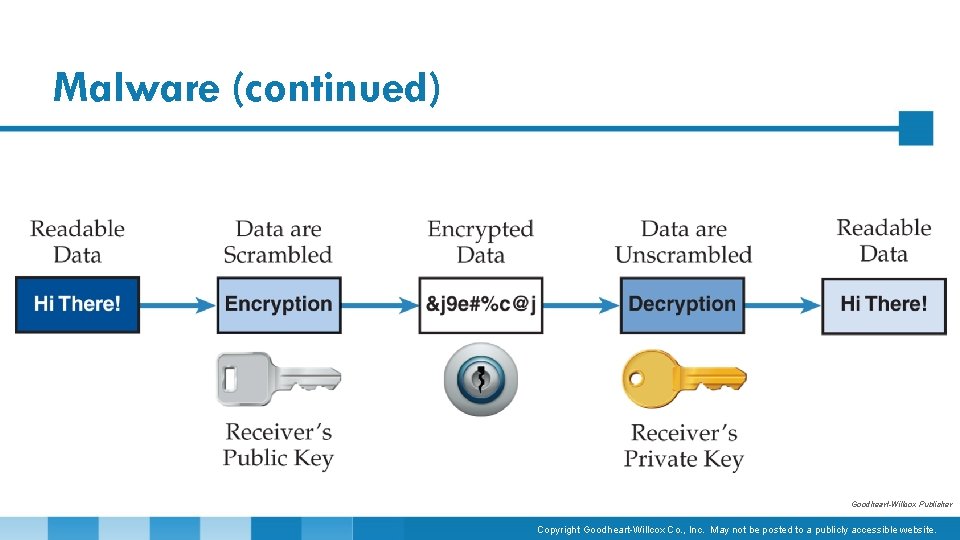
CIA Triad (continued) • Confidentiality : condition of being private or secret • Ensuring users only have access to the data they need • Implemented by the rights and privileges granted to the individual computer users • Encryption converts data into a format that can only be read by the holder of the decryption key. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
CIA Triad (continued) • Integrity : state of being complete or uncorrupted • Ensures data are not changed or altered without permission to do so • Folder or file permissions can ensure integrity. • Nonrepudiation process : changes are tracked by which user account made them Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

CIA Triad (continued) • Availability • Data can be accessed when needed • Solutions for problems like hardware failure or hacking are needed so data can always be accessed Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Security Domains • To protect data and assets, areas of business are broken down into information technology security domains. • users • workstations • LAN • WAN • remote access • system Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Security Domains (continued) • Attack surface : all the locations and methods that could constitute a security risk • Defense in depth : having multiple levels of protection • Frameworks : help break down the aspects of a business and security domains into manageable task areas and tasks Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Security Domains (continued) • Users • Includes staff, vendors, contractors, guests • Weakest link in security chain • Workstation • Issues surrounding workstations or other devices used by people • Internet of Things (Io. T) : describes the connection of nontraditional computing devices to the Internet Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Security Domains (continued) • LAN • Network infrastructure within a small area • Issues related to servers, switches, routers, and media • WAN • Network infrastructure for more than one geographic location • Internet Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Security Domains (continued) • Remote Access • Employees can connect to the computer network remotely • Challenges include securing data, verification of users, security of remote system • System • Services and software used to provide access to data and resources • Covers web servers, database servers, etc. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Section 2. 1 Review 1. Which security principle relates to protecting data against unauthorized changes? Integrity 2. What is the practice of having multiple layers of security to protect against intruders? Defense in depth 3. Briefly describe frameworks. Guidelines for designing security policies Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 1 Review 4. Nontraditional computing devices with Internet access describes _____. Internet of Things (Io. T) 5. What is the weakest link in an organization’s security policy and plan? Users Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 2 Vulnerabilities and Threats
Key Terms • adware • armored virus • backdoor • cookie policy • cryptomalware • digital footprint • drive-by-download • dumpster diving • firmware • heuristic methodology • keylogger • logic bomb • macro virus • malware Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Key Terms • payload • persistent cookie • polymorphic virus • pretexting • ransomware • remote access Trojan (RAT) • rootkit • secure cookie • session cookie • social engineering • third-party cookie • threat • time bomb Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Key Terms • Trojan horse • vulnerability • zero-day vulnerability Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Learning Goals • Compare and contrast forms of malware. • Explain vulnerabilities that exist in software. • Identify cybersecurity threats outside of malware. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Malware • Malware : computer code intentionally written to cause some form of harm • Malicious software • Harm ranges from stealing or destroying data to collecting information of allowing remote access to a system • Exploits vulnerabilities • Vulnerability : flaw or potential for harm Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Malware (continued) • Threat : something that takes a vulnerability to a level where it can be exploited • Purpose of malware is found in its payload • Payload : actions of the malicious code • Many kinds of malware Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Malware (continued) • Trojan Horse • Malware hidden inside other software that appears to be harmless • Remote access Trojan (RAT) : form of malware that allows the hacker to use an embedded backdoor to gain administrative control of the victim’s computer Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Malware (continued) • Worm • Form of malware that infects systems with its payload • Moves and spreads from one computer to another through open network ports • Sasser worm caused computers to slow or shut down • My. Doom worm is the quickest-spreading worm via e-mail Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Malware (continued) • Time or Logic Bomb • Time bomb : deploys its payload when a date or time occurs • Logic bomb : deploys when conditions exist that the malware is seeking • Armored Virus : designed to prevent security analysts from reading the source code by attempting to prevent access to or disassembly of the code itself Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Malware (continued) • Ransomware • Does not steal or destroy data, • Encrypts data so user cannot access it until a fee is paid to the hacker • Cryptomalware : malware that encrypts the user’s data • Drive-by-download : ransomware automatically downloaded when a user visits a web page that is infected Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Malware (continued) Goodheart-Willcox Publisher Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
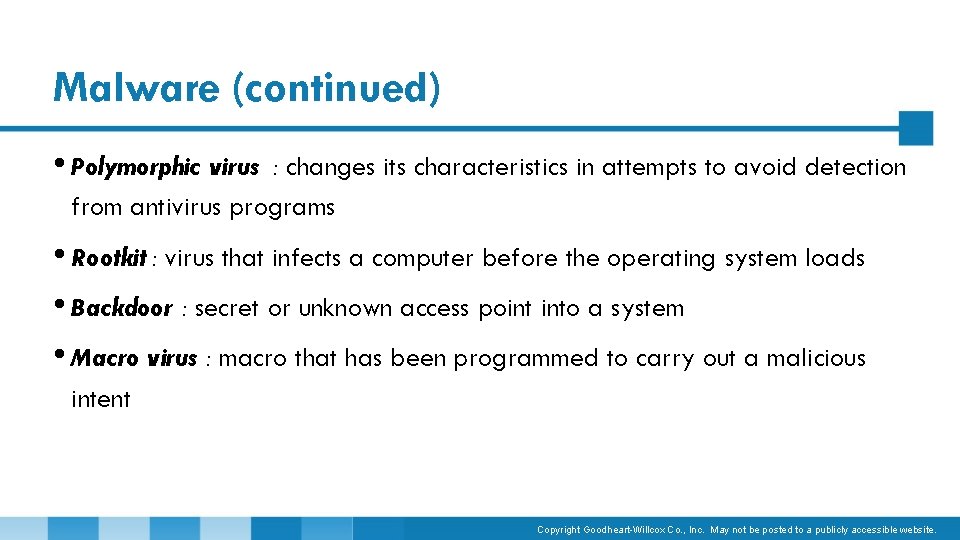
Malware (continued) • Polymorphic virus : changes its characteristics in attempts to avoid detection from antivirus programs • Rootkit : virus that infects a computer before the operating system loads • Backdoor : secret or unknown access point into a system • Macro virus : macro that has been programmed to carry out a malicious intent Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Malware (continued) • Defending Against Malware • Prevention is best defense • Using antimalware software program is critical to catch threats that may have been installed without your knowledge. • Keep the operating system fully patched • Be careful of Internet downloads • Heuristic methodology : approach to finding previously undetected unwanted programs or variants of known viruses Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Software Vulnerabilities • Zero-Day Vulnerability : exists in software when it was released and remains unknown until it is exploited by hackers • No immediate fix or patch usually available • Best defense is to keep system and software patched • Firmware : software that is embedded in hardware Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Other Security Threats • Keylogger : technology that tracks a user’s keystrokes on the keyboard • Adware : software installed on a computer that collects data on the user and then redirects advertising sites to the web browser Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Other Security Threats (continued) • Cookies • Small text files saved on the computer for web browsers and websites • Cookie policy : states if the site uses cookies and how they are used • Session cookie : exists only as long as the web browser is open • Persistent cookie : stays on your computer until an expiration date is met Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Other Security Threats (continued) • Cookies • Secure cookie : can only be sent using an encrypted session • Third-party cookie : originates from a visit to a website, but references a different website Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Other Security Threats (continued) • Social Engineering • Hacker using social tools and techniques to obtain information • Once data is obtained the hacker can use it to gain access to systems • Digital footprint : information about a person left behind by his or her actions on the Internet Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Other Security Threats (continued) • Pretexting : using a lie or scam to obtain private information • Other ways to obtain information: • Convincing people to reveal information • Social media platforms • Public records • Advanced Internet searches • Dumpster diving : digging through the trash for useful information Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
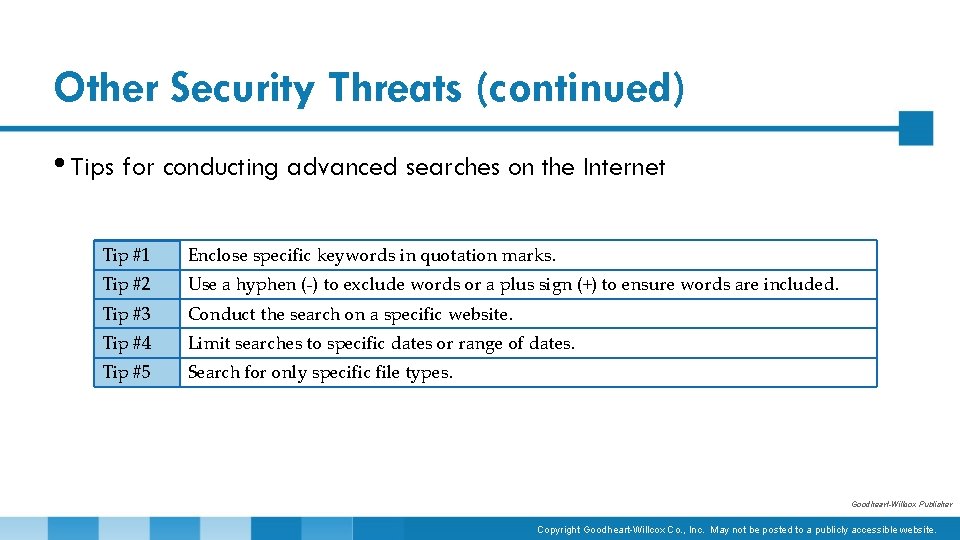
Other Security Threats (continued) • Tips for conducting advanced searches on the Internet Tip #1 Enclose specific keywords in quotation marks. Tip #2 Use a hyphen (-) to exclude words or a plus sign (+) to ensure words are included. Tip #3 Conduct the search on a specific website. Tip #4 Limit searches to specific dates or range of dates. Tip #5 Search for only specific file types. Goodheart-Willcox Publisher Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Section 2. 2 Review 1. What is a Trojan or Trojan horse? Malware that hides inside a legitimate program. 2. Software that is preinstalled or embedded in hardware is known as _____. firmware 3. Which type of cookie remains on the computer after the browser is closed until it reaches its expiration date? Persistent Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 2 Review 4. What is the social engineering technique in which the hacker lies to get information? Pretexting 5. If you are digging through a trash can for information, what is this hacking technique called? Dumpster diving Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 3 Legal Requirements
Key Terms • compliance • Computer Fraud and Abuse Act (CFAA) • Electronic Communication Privacy Act (ECPA) • electronic health record (EHR) • Gramm-Leach-Bliley Act (GLBA) • Health Insurance Portability and Accounting Act (HIPAA) • Payment Card Industry Data Security Standard (PCI DSS) • protected health information (PHI) • Sarbanes-Oxley Act (SOX) Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Learning Goals • Define compliance. • Identify laws and standards related to digital security. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Compliance • Compliance : following the rules or standards that have been established • Laws are established to ensure data and privacy are protected • Most are federal • States have their own laws • Companies with business outside the country must abide by the laws in the other country where they operate, too. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Laws and Standards • Computer Fraud and Abuse Act (CFAA) • Deals with unauthorized access of computers • Covers primarily protected computers located on US governmental systems, financial institutions, and interstate or foreign communication • Theoretically, most computers and cell phones are covered Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Laws and Standards (continued) • Electronic Communication Privacy Act (ECPA) • Protects wire and electronic transmissions of data • Covers communication such as e-mail, telephone conversations, and data stored electronically • Wiretap Act: prohibits the intentional interception, use, disclosure, or procurement of any communication Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Laws and Standards (continued) • Electronic Communication Privacy Act (ECPA) • Stored Communications Act (SCA): protects the privacy of the content of files stored by service providers • Pen Register Act: requires governmental entities obtain a court order on a pen register, which is a device that captures the numbers and related information of outgoing calls Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Laws and Standards (continued) • Gramm-Leach-Bliley Act (GLBA) • Ensures that financial businesses are protecting your private data • Safeguards Rule: businesses must develop, implement, and maintain a comprehensive information security program • Financial Privacy Rule: regulates the collection and disclosure of a consumer’s nonpublic personal information (NPI) Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Laws and Standards (continued) • Sarbanes-Oxley Act (SOX) • Prevents company executives from hiding or destroying electronic records for a minimum of five years • Designed to crack down on corporate fraud Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Laws and Standards (continued) • Health Insurance Portability and Accounting Act (HIPAA) • Protects electronic medical records and personal health information • Privacy Rule: establishes a set of national standards for the protection of all “individually identifiable health information” Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Laws and Standards (continued) • Health Insurance Portability and Accounting Act (HIPAA) • Protected health information (PHI) : individually identifiable health information in the form of electronic data, paper records, or spoken conversation • Electronic health record (EHR) : digital or electronic platform for health records Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Laws and Standards (continued) • Security Rule: establishes a set of national standards to protect personal health information in electronic form • Standards help organizations understand the safeguards they must undertake Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
Laws and Standards (continued) • Payment Card Industry Data Security Standard (PCI DSS) • Set of regulations from credit card vendors that apply to businesses using their services • Industry standard, not law • Applies to any organization, regardless of size or number of transactions • Four levels of compliance based on merchant levels, which are determined by number of transactions per year Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
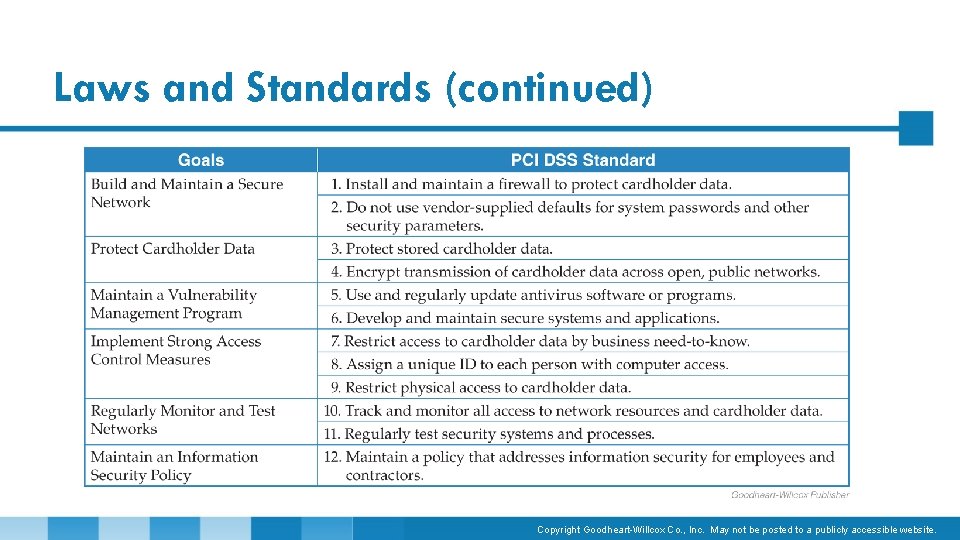
Laws and Standards (continued) Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 3 Review 1. What is meant by compliance? Following rules and regulations by which an organization must abide. 2. Which law covers unauthorized access to computers? Electronic Communication Privacy Act (ECPA) 3. What is the basic purpose of the Gramm-Leach-Bliley Act (GLBA)? It ensures financial businesses, such as banks, protect private personal data. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.

Section 2. 3 Review 4. What governmental agency monitors issues related to the SOX rules? Securities and Exchange Commission (SEC) 5. What is the minimum number of credit card transactions for the PCI DSS regulations to apply? It applies to any organization that collects, transmits, or stores credit card data regardless of the number of transactions. Copyright Goodheart-Willcox Co. , Inc. May not be posted to a publicly accessible website.
- Slides: 57