Chapter 2 History Terminology of Computer Crime Investigation


























- Slides: 28

Chapter 2 History & Terminology of Computer Crime Investigation A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in Power. Point form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: q If you use these slides (e. g. , in a class) in substantially unaltered form, that you mention their source (after all, we’d like credit for our effort!) q If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Digital Evidence and Computer Crime, 2 nd edition. Eoghan Casey Elsevier Academic Press, July 2004. Thanks and enjoy! IG/DS All material copyright 2004 -2008 Isaac Ghansah, Dick Smith, All Rights Reserved History and Terminology 1

Chapter 2: Introduction Our goal: q get “feel” and terminology q more depth, detail later in course q approach: v use actual cases Overview: q what’s the history of Computer Crime Investigation q Investigative tools q Language and terminology q Different roles of computer use in crimes History and Terminology 2

Chapter 2: Introduction q 1969 and 1970 earliest computer crime was when student protestors burned computers q Unauthorized access to large time-shared computers (stealing time) not illegal at the time. q Laws have always been trying to catch up to technology ** q Florida in 1978 was first state to introduce computer crime law to address fraud and intrusion. History and Terminology 3

Chapter 2: Introduction continued q Laws were result of highly publicized incident at q q Flagler Dog Track where employees printed winning tickets. Interesting point, they also defined unauthorized access to a computer as a crime even if no maliciousness in the act. Now adopted in every state but Vermont. Canada was first country to enact laws 1983 US Federal Computer Fraud and Abuse Act passed in 1984 and amended 1986, 1988, 1989, 1990 History and Terminology 4

Chapter 2: Introduction continued q Australian Crimes Act amended in 1989 q Britain Computer Abuse Act passed 1990 q However many countries failed to enact laws against computer crime. q May 2000 a computer science student in the Philippines created a VBS virus called loveletter or Subject: I Love You. It spread over the entire Internet in one day and caused over $5. 5 Billion damage. ** q He was arrested but had to be released! ** History and Terminology 5

Chapter 2: roadmap 2. 1 Brief History of Computer Crime Investigation 2. 2 Evolution of Investigative Tools 2. 3 Language of Computer Crime Investigation 2. 3. 1 The Role of Computers in Crime 2. 3. 1. 1 Hardware as Contraband or Fruits of Crime 2. 3. 1. 2 Hardware as an Instrumentality 2. 3. 1. 3 Hardware as Evidence 2. 3. 1. 4 Information as Contraband or Fruits of Crime 2. 3. 1. 5 Information as an Instrumentality 2. 3. 1. 6 Information as Evidence 2. 4 Summary History and Terminology 6

2. 1 Brief History of Computer Crime Investigation q Growth in computer-related crime in late 1980 s and early 1990 s resulted in law enforcement agencies working together to develop training and capacity to deal with the problem. q Centers such as SEARCH, Federal Law Enforcement Center (FLETC) and National White Collar Crime Center (NW 3 C). q National level gave way to regional centers which gave way to local centers. History and Terminology 7

2. 1 Brief History of Computer Crime Investigation continued q Result in pyramid structure: v First responder basic collection & examination v Regional - handle more advanced cases v National - to assist most challenging cases q Advances in technology and computer- related crime created need specialization: Digital crime scene technicians – to collect evidence v Examiners – who process acquired evidence v Investigators – who analyze and build case v History and Terminology 8

2. 1 Brief History of Computer Crime Investigation continued q Best practice when single individual responsible for all three, to consider the tasks separately. q American Society of Crime Laboratory Directors (ASCLD) proposed requirements for digital evidence examiners in forensic laboratories. q Similar efforts in international standards (ISO 17025; ENFSI 2003) History and Terminology 9

2. 1 Brief History of Computer Crime Investigation continued q Goal to create several tiers of certification starting with general knowledge exam that everyone must pass including first responders who handle digital evidence. q Then more specialized certification for individuals who handle complex cases. History and Terminology 10

2. 2 Evolution of Investigative Tools q UNIX had a program called “dd” since the 1980 s ( “disk copy”**) q Early 1990 s Safe. Back and DIBS used to collect all data on a disk without altering. q Need for more advanced tools resulted in Encase and FTK (forensic tool kit) to make digital investigators job easier (hardware write blocker**). q Recent Linux as a platform and tools Sleuthkit and SMART History and Terminology 11

2. 2 Evolution of Investigative Tools continued q Not all examiners aware of tools and have been criticized by the court for not using “the method which would yield the most complete and accurate results”. q Network tools “tcpdump” and “Ethereal” used to capture network traffic. q “Wireshark” newest network tool ** q Carnivore, Net. Intercept, NFR Security, Net. Witness and Silent. Runner help extract information from network traffic History and Terminology 12

2. 2 Evolution of Investigative Tools continued q Often require individuals ingenuity to collect and analyze evidence. (we call it “think outside the box” i. e. be creative in your thinking **) q Tools for embedded systems ZERT, TULP and Cards 4 Labs have been developed for password protected and deleted data. q Techniques using electron microscopes are available but prohibitively expensive. History and Terminology 13

2. 2 Evolution of Investigative Tools continued q National Institute of Standards and Testing (NIST) making efforts to test some digital evidence processing tools. q Not practical to have one single group test every tool also may not be possible to create standard tests for advanced features of various tools. q Best practice: Digital Investigators must validate their own results using multiple tools. History and Terminology 14

2. 3 Language of Computer Crime Investigation q Even though movement to standardization there lack of agreement on basic terminology. i. e. meaning “computer crime”. q If computer played no role in the crime but contains digital evidence relevant to the investigation it is called computer-related. q US Department of Justice and Council of Europe use “cybercrime”. History and Terminology 15

2. 3 Language of Computer Crime Investigation continued q Computer forensics also has different meanings to different people. q To make matters worst the Information Security people use the term to describe a wide range of activities to protect computer systems rather than gathering evidence. q Digital forensic science to describe the field as a whole History and Terminology 16

2. 3 Language of Computer Crime Investigation continued q Additionally the terms forensic computer analysis and forensic computing are widely used. q The author states he will use the term digital evidence examination in the text to standardize. History and Terminology 17

2. 3. 1 The Role of Computers in Crime q Need arises to describe the role of computers in a crime. q Investigating computer intrusion requires one approach while investigating a homicide requires a completely different approach. q When a computer contains only a few small pieces of digital evidence the investigators might not be authorized to collect the entire computer. History and Terminology 18

2. 3. 1 The Role of Computers in Crime continued q If computer is key or contains large amount of evidence then easier to obtain a warrant to search and seize the entire computer. q Don Parker - one of the first to perceive that computer crime as a serious problem in the 1970 s. He was instrumental in enacting Florida’s Computer Crime Act and wrote several books on the subject. History and Terminology 19

2. 3. 1 The Role of Computers in Crime continued q He proposed 4 categories: v Computer as object (e. g. when stolen or destroyed) v Computer as subject (e. g. infected with virus or denial of service Do. S) v Computer as tool (e. g. forge documents or used to break into other computers) v Symbol of computer (e. g. Con artist claim to a secret program that could make a fortune on the stock market) History and Terminology 20

2. 3. 1. 1 Hardware as Contraband or Fruits of Crime q Contraband – property that a private citizen is not permitted to possess. q Illegal to possess hardware that will intercept electronic communications. q Fruits of crime are equipment that was stolen or purchased with stolen credit cards. q Main reason to seize contraband is to prevent and deter future crimes. History and Terminology 21

2. 3. 1. 2 Hardware as an Instrumentality q Computer that is specially manufactured, equipped and/or configured to commit a specific crime. q Key word to remember is “significant” in definition of instrumentality. q Virginia decision that computer with related accessories was an instrumentality because it contained detailed file “growing characteristics of marijuana plants”. History and Terminology 22

2. 3. 1. 3 Hardware as Evidence q Now acceptable to search for and seize any property that constitutes evidence of commission of criminal offense. q This separate category is necessary to cover hardware that is neither contraband nor the instrumentality of a crime. q For example a scanner that digitizes child pornography has unique scanning characteristics that link the hardware to the digitized images, it could be seized as evidence. History and Terminology 23

2. 3. 1. 4 Information as Contraband or Fruits of Crime q Common form contraband is encryption software. q Another form of contraband is child pornography. q Fruits of crime include illegal copies of computer programs, stolen trade secrets and passwords, and any other information that was obtained by criminal activity. History and Terminology 24

2. 3. 1. 5 Information as an Instrumentality q Programs that computer intruders use to break into computer systems are the instrumentality of a crime. q These programs are commonly called “exploits”. q Computer programs that record people’s passwords when they log into a computer can be an instrumentality, and programs that crack passwords (John the Ripper, L 0 phtcrack **) often play a role in a crime. q Is it a crime for a system administrator to crack his/her organizations password file? ** History and Terminology 25

2. 3. 1. 6 Information as Evidence q Telephone companies, ISPs, banks, credit institutions keep information on customers. q These records can reveal a wealth of information about an individuals daily life. q Although laws cover how long companies must keep records/logs it can vary on what information must be saved. q US Computer Assistance Law Enforcement Act (CALEA) in 2000 compels telephone companies to keep detailed records of customer calls for an indefinite period. History and Terminology 26

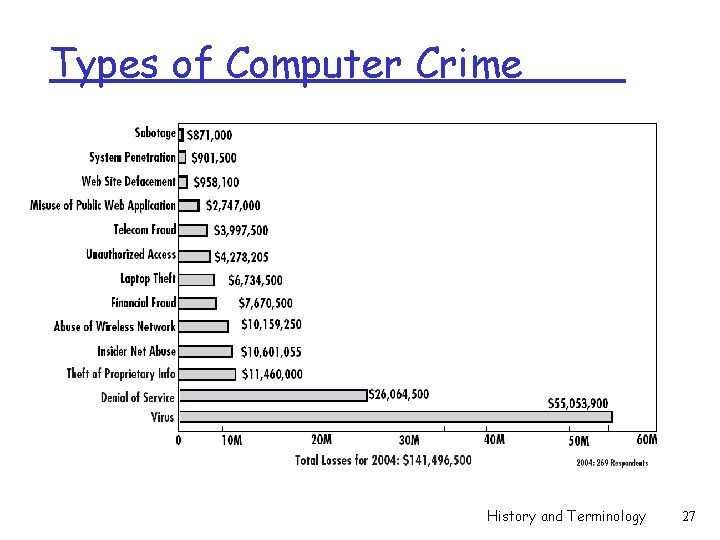
Types of Computer Crime History and Terminology 27

Chapter 2: Summary Covered a “ton” of material! q Terminology q History You now have: q context, overview, “feel” of Computer Crime Investigation q more depth, detail to follow! History and Terminology 28