CHAPTER 2 Elementary Cryptography 1 Objectives Define the

CHAPTER 2 Elementary Cryptography 1
Objectives Define the concept of encryption Discuss different type of cryptography algorithms Explain the difference between symmetric and asymmetric encryption Define and describe the knowledge, techniques and methods used in cryptography Write and demonstrate encryption/decryption algorithm in the form of program Define and describe the role of cryptography in security 2

Introduction Cryptography : secret writing. The strongest tool for controlling against many kind of security threats. Fortunately, it is not necessary to understand the underlying mathematics to be able to use cryptography. 3

Consider this situation… Sender S sending a message to recipient R. If S entrust the message to T who will delivers it to R, T become transmission medium. If outsider O wants to access the message (read, change, destroy), O become interceptor or intruder. So, any time after S transmits it via T, the message is vulnerable to exploitation. 4

the message is vulnerable to exploitation, and O might try to access the message in any of the following ways: Block it, by preventing its reaching R , thereby affecting the availability of the message. Intercept it, by reading or listening to the message, thereby affecting the confidentiality of the message. Modify it, by seizing the message and changing it in some way, affecting the message's integrity. Fabricate an authentic -looking message, arranging for it to be delivered as if it came from S , thereby also affecting the integrity of the message. 5

Terminology Encryption : process of encoding a message so that its meaning is not obvious. Decryption : reverse process, transforming an encrypted message back into its normal, original form. Encode, decode, encipher, decipher. A system for encryption and decryption is called cryptosystem. 6
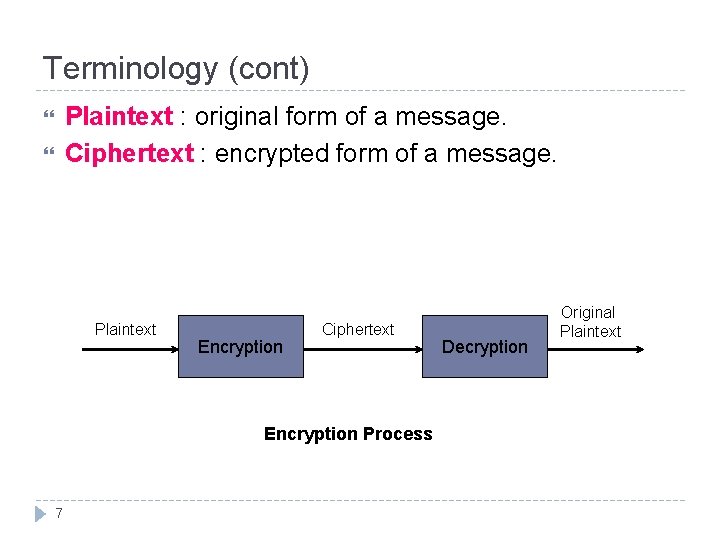
Terminology (cont) Plaintext : original form of a message. Ciphertext : encrypted form of a message. Plaintext Encryption Ciphertext Encryption Process 7 Decryption Original Plaintext
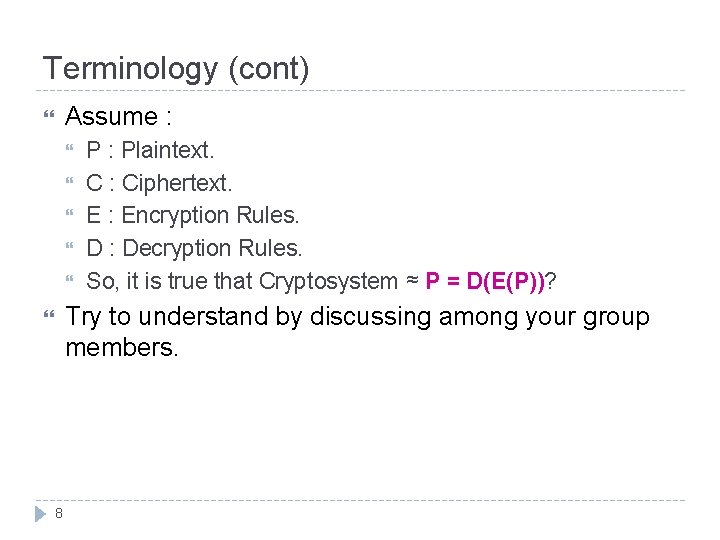
Terminology (cont) Assume : P : Plaintext. C : Ciphertext. E : Encryption Rules. D : Decryption Rules. So, it is true that Cryptosystem ≈ P = D(E(P))? Try to understand by discussing among your group members. 8
Encryption Algorithm The cryptosystem involves a set of rules for how to encrypt the plaintext and how to decrypt the ciphertext. This rules are called algorithm. Often use a device called a key, denoted by K. This create a dependency of C = E(K, P). Key K selects one specific algorithm from the E set. 9
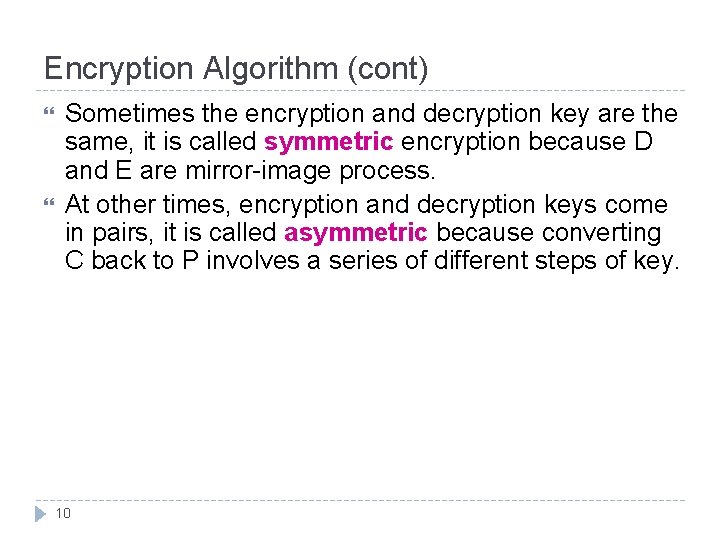
Encryption Algorithm (cont) Sometimes the encryption and decryption key are the same, it is called symmetric encryption because D and E are mirror-image process. At other times, encryption and decryption keys come in pairs, it is called asymmetric because converting C back to P involves a series of different steps of key. 10
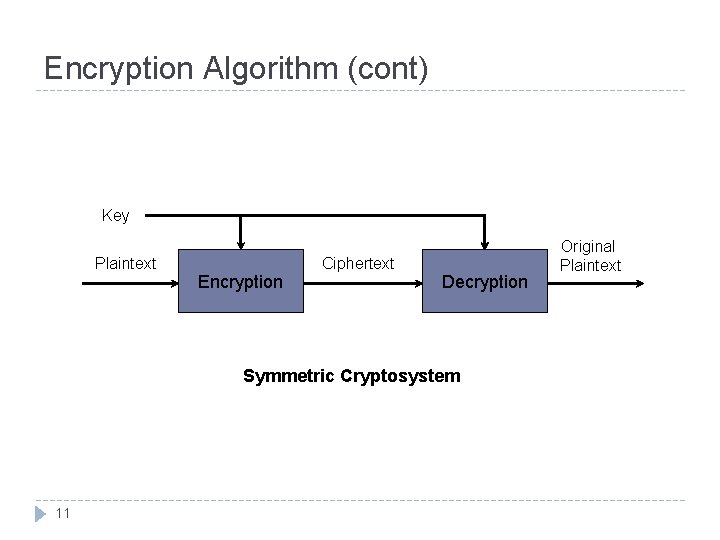
Encryption Algorithm (cont) Key Plaintext Encryption Ciphertext Decryption Symmetric Cryptosystem 11 Original Plaintext
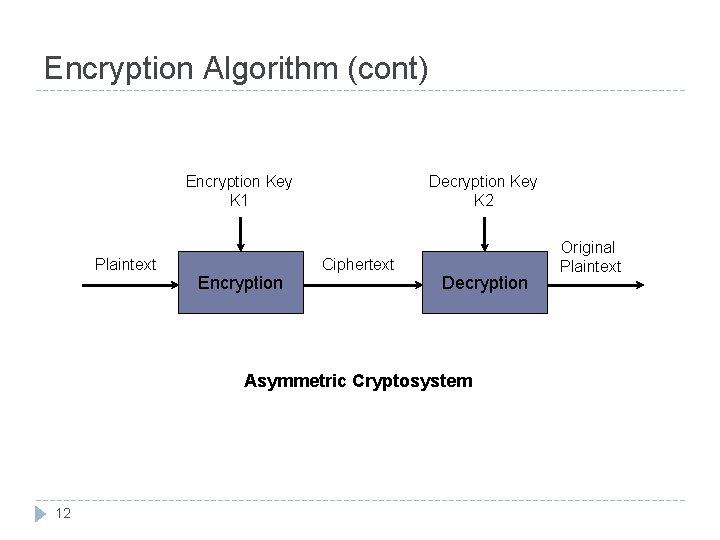
Encryption Algorithm (cont) Encryption Key K 1 Plaintext Encryption Decryption Key K 2 Ciphertext Decryption Asymmetric Cryptosystem 12 Original Plaintext
Encryption Algorithm (cont) A key gives us flexibility in using an encryption scheme. An encryption scheme that does not require the use of key is called keyless cipher. 13

The Wonderful of Cryptography : hidden writing, practice of using encryption to conceal text. Cryptanalyst : people studies encryption and encrypted messages, hoping to find hidden meanings, works for unauthorized interceptor. Cryptographer : same people but works on behalf of a legitimate sender / receiver. Cryptology : research or studies of E & D. 14

Cryptanalysis A cryptanalyst’s chore is to break an encryption. What cryptanalyst’s do are : 15 Attempt to break a single message. Attempt to recognize patterns in encrypted message Attempt to infer without breaking the encryption Attempt to deduce the key Attempt to find the weaknesses in implementation or environment Attempt to find the general weaknesses without necessarily having intercept any messages
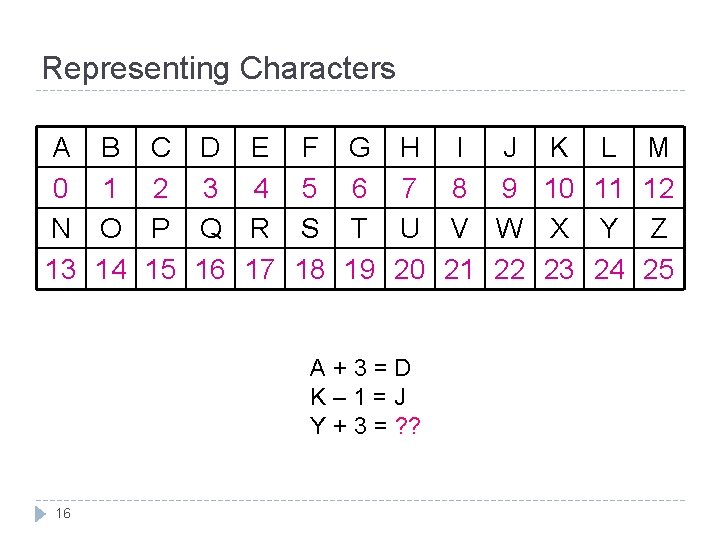
Representing Characters A 0 N 13 B 1 O 14 C 2 P 15 D 3 Q 16 E 4 R 17 F 5 S 18 G 6 T 19 H I J 7 8 9 U V W 20 21 22 A+3=D K– 1=J Y + 3 = ? ? 16 K 10 X 23 L 11 Y 24 M 12 Z 25
Representing Characters (cont) There is many types of encryption. Two simple form of encryption : 17 Substitution : one letter is exchange to the another. Transposition : the order of the letters is rearranged.

Substitution Cipher Children sometimes devise “secret codes” that a correspondence table with which to substitute a character or symbol for each character of the original message. This technique is called a manoalphabetic cipher or simple substitution. Caesar Cipher, Permutation and One-Time Pads (Vernam and Book Cipher). 18

Caesar Cipher The Caesar Cipher has an important place in history. Each letter is translated to a letter a fixed number of places after it in alphabet. Algorithm : c = E(p) = p + n Caesar used a shift of 3. c = E(p) = p + 3 19
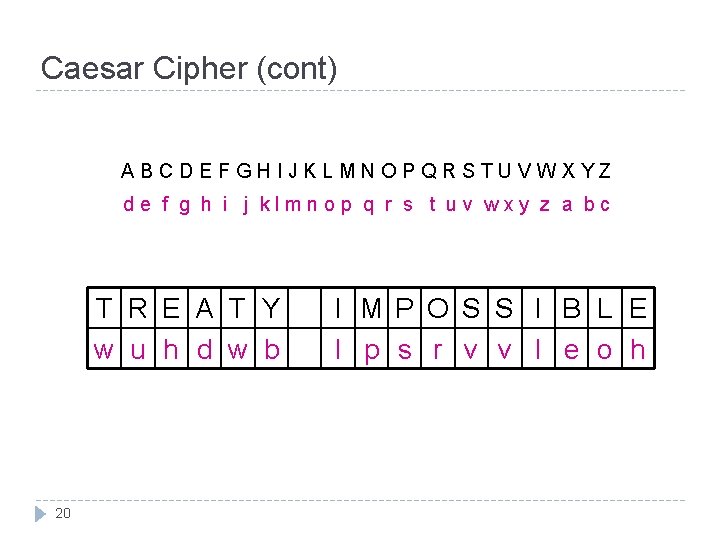
Caesar Cipher (cont) ABCDEFGHIJKLMNOPQRSTUVWXYZ de f g h i j klmnop q r s t uv wxy z a bc T R E A T Y w u h d w b 20 I M P O S S I B L E l p s r v v l e o h
Caesar Cipher (cont) Advantages : Early one, most easy to perform in the field. Quite simple, pattern formula was easy to memorize and implement. Disadvantages : 21 Dangerous to perform for soldiers or spies. Obvious pattern is major weakness
Permutation : Reordering of the elements of a sequence. One way to scramble an alphabet is to use a key, a word that controls the permutation. Sender and receiver need to remember the ‘key’ to ensure encryption and decryption successful. 22

Permutation Key : word ABCDEFGHIJKLMNOPQRSTUVWXYZ wor d a bc efgh i j k l mnp qs t u v x yz Security : qartpfsy Key : professional ABCDEFGHIJKLMNOPQRSTUVWXYZ pr o f es i n al bcd g h j k mqt u v wx yz Security : qeoumaty Key : count by threes ABCDEFGHIJKLMNOPQRSTUVWXYZ a d gjmp svybeh k n qt w z c f i l o r ux Security : cmgizyfu 23

One-Time Pads Sometime considered the perfect cipher. Encipher the plaintext with a prearrange chart called a Vigenère tableau. Two problems of one-time pad : The need for absolute synchronization between sender and receiver. The need for an unlimited number of keys. Vernam Cipher and Book Cipher. 24
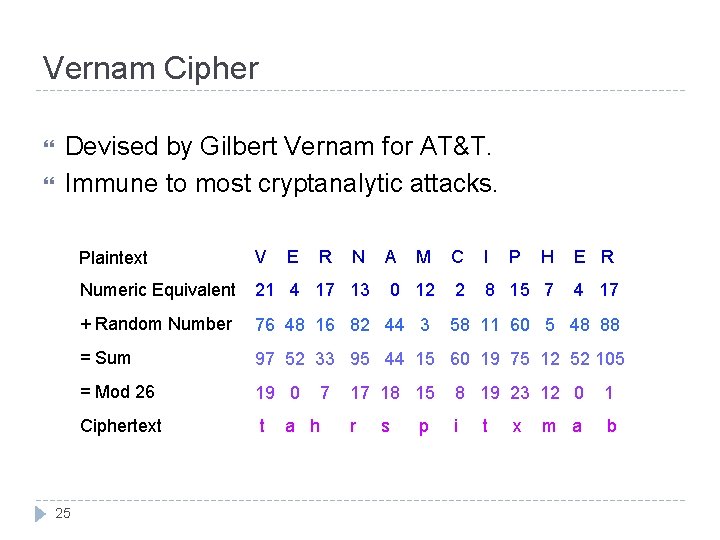
Vernam Cipher Devised by Gilbert Vernam for AT&T. Immune to most cryptanalytic attacks. 25 Plaintext V E R Numeric Equivalent 21 4 17 13 + Random Number 76 48 16 82 44 3 = Sum 97 52 33 95 44 15 60 19 75 12 52 105 = Mod 26 19 0 Ciphertext t a h 7 N A M C I P H E R 0 12 2 8 15 7 4 17 58 11 60 5 48 88 17 18 15 8 19 23 12 0 1 r i b s p t x m a

Book Cipher Randomly take a key from any book, piece of music or other object with which the structure can be analyzed. Any book can provide a key. This key is formed from the letters of the text, in order. 26
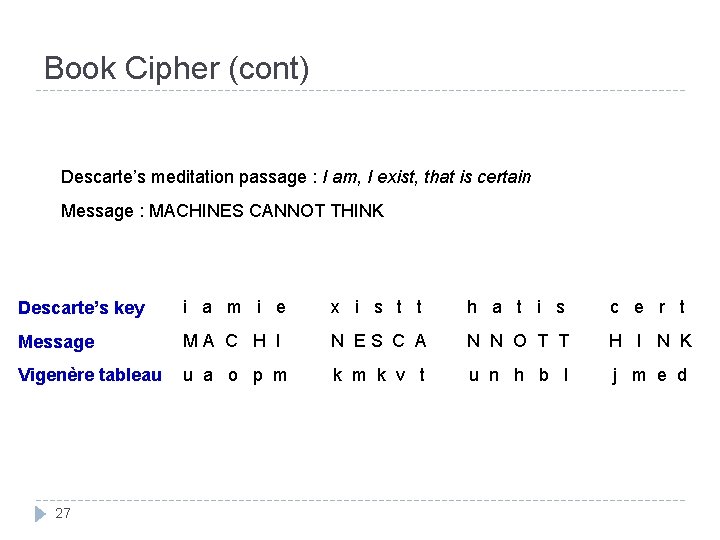
Book Cipher (cont) Descarte’s meditation passage : I am, I exist, that is certain Message : MACHINES CANNOT THINK Descarte’s key i a m i e x i s t t h a t i s c e r t Message MA C H I N ES C A N N O T T H I N K Vigenère tableau u a o p m k v t u n h b l j m e d 27
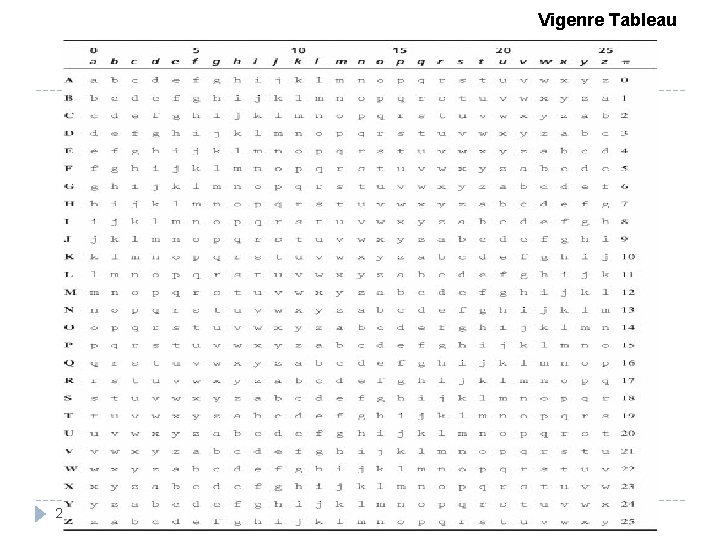
Vigenre Tableau 28
Transpositions The goal of substitution is confusion. Transposition : an encryption in which the letters of the message are rearranged. Aims for diffusion. DES Algorithm and AES Algorithm. 29
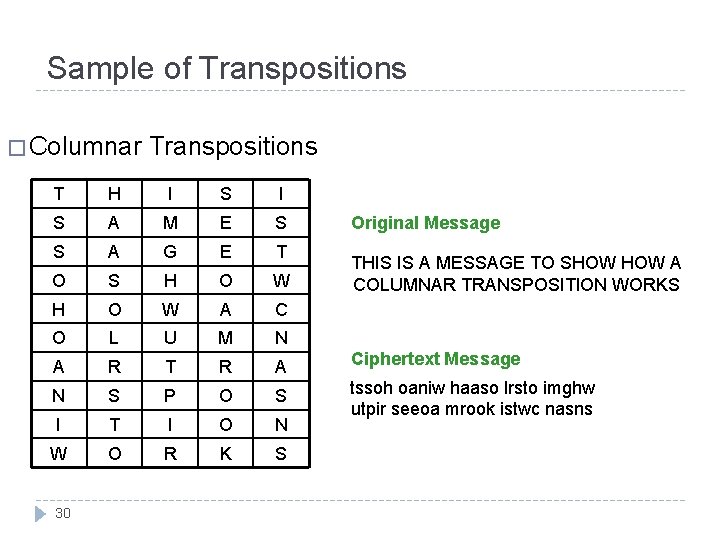
Sample of Transpositions � Columnar Transpositions T H I S A M E S S A G E T O S H O W A C O L U M N A R T R A Ciphertext Message N S P O S I T I O N tssoh oaniw haaso lrsto imghw utpir seeoa mrook istwc nasns W O R K S 30 Original Message THIS IS A MESSAGE TO SHOW A COLUMNAR TRANSPOSITION WORKS
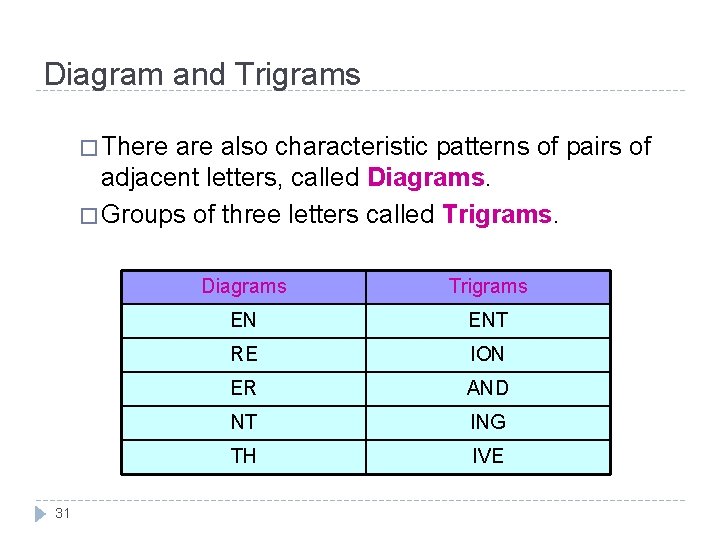
Diagram and Trigrams � There also characteristic patterns of pairs of adjacent letters, called Diagrams. � Groups of three letters called Trigrams. 31 Diagrams Trigrams EN ENT RE ION ER AND NT ING TH IVE
Combinations of Approaches Substitution and transposition can be considered as building blocks for encryption. A combination of two ciphers is called a product cipher. A formula can be conclude as E 2(E 1(P, k 1), k 2) 32
Making “Good” Encryption Algorithm Claude Shannon’s (1949) 33 The amount of secrecy needed should determine the amount of labor appropriate for the encryption and decryption. The set of keys and the enciphering algorithm should be free from complexity. The implementation of the process should be as simple as possible.
Making “Good” Encryption Algorithm (cont) 34 Errors in ciphering should not propagate and cause corruption of further information in the message. The size of the enciphered text should be no larger than the text of the original message.

Properties of “Trustworthy” Encryption Systems It is based on sound mathematics. It has been analyzed by competent experts and found to be sound. Good cryptographic are not just invented but they are derived from solid principles. Experts can think of only so many possible attacks. It has stood the “test of time”. 35 Successful use and analysis is not a guarantee of a good algorithm!!!
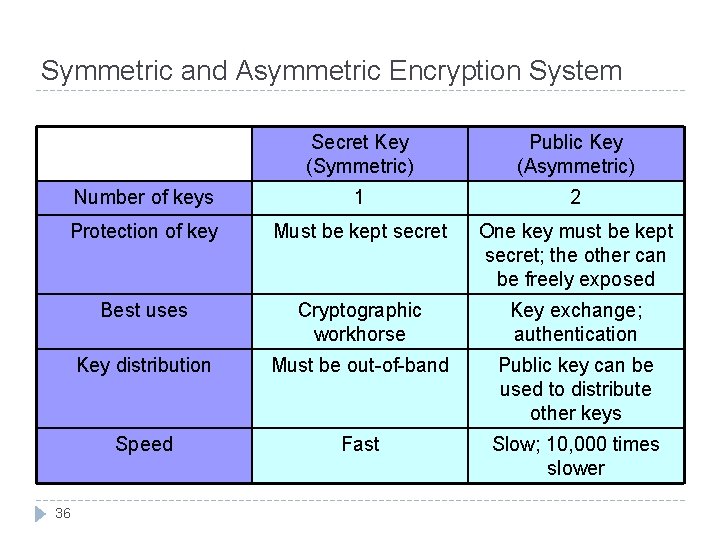
Symmetric and Asymmetric Encryption System Secret Key (Symmetric) Public Key (Asymmetric) Number of keys 1 2 Protection of key Must be kept secret One key must be kept secret; the other can be freely exposed Best uses Cryptographic workhorse Key exchange; authentication Key distribution Must be out-of-band Public key can be used to distribute other keys Speed Fast Slow; 10, 000 times slower 36
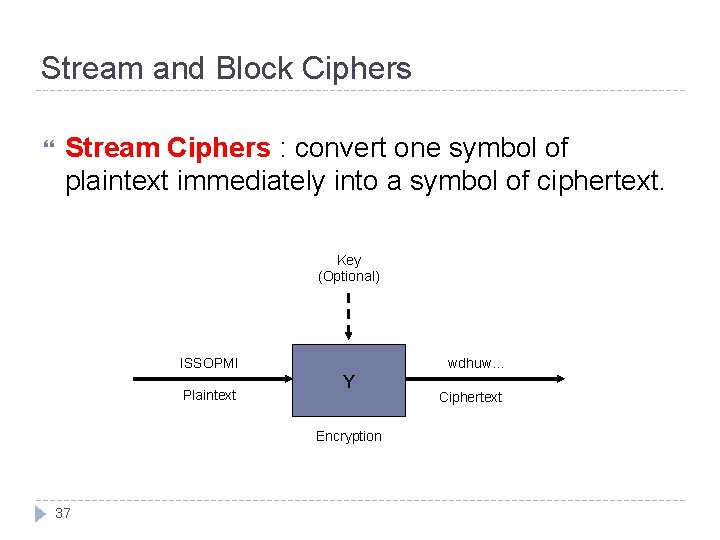
Stream and Block Ciphers Stream Ciphers : convert one symbol of plaintext immediately into a symbol of ciphertext. Key (Optional) ISSOPMI Plaintext wdhuw… Y Encryption 37 Ciphertext
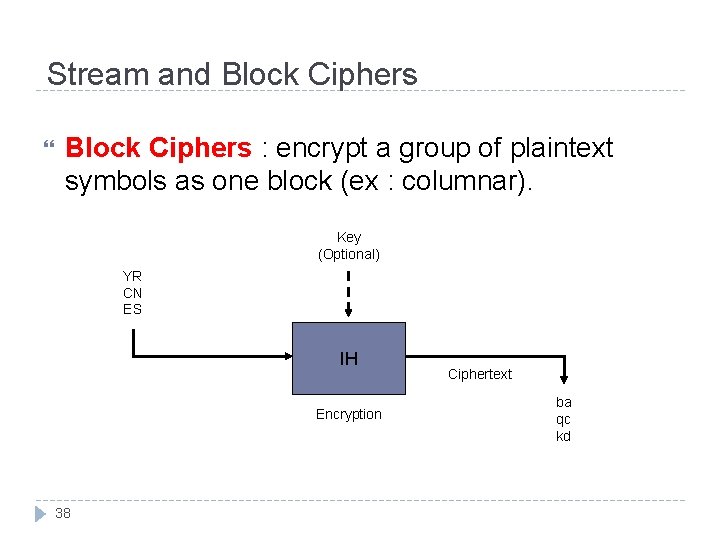
Stream and Block Ciphers : encrypt a group of plaintext symbols as one block (ex : columnar). Key (Optional) YR CN ES IH Encryption 38 Ciphertext ba qc kd
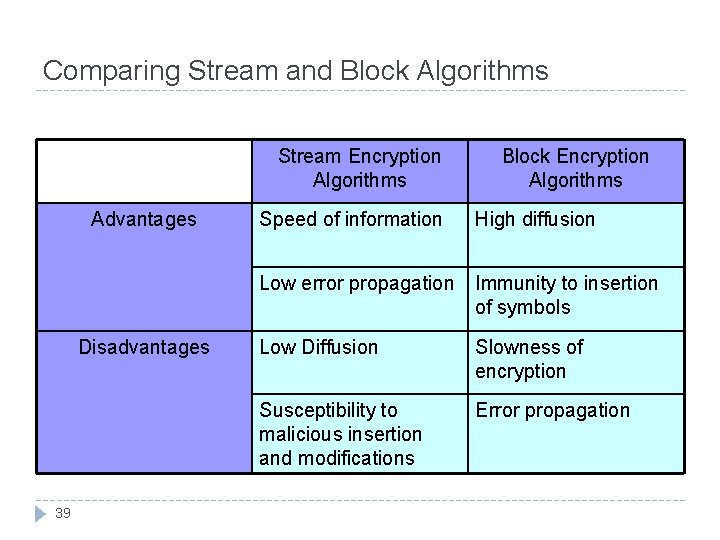
Comparing Stream and Block Algorithms Stream Encryption Algorithms Advantages Disadvantages 39 Block Encryption Algorithms Speed of information High diffusion Low error propagation Immunity to insertion of symbols Low Diffusion Slowness of encryption Susceptibility to malicious insertion and modifications Error propagation
Weaknesses A cryptanalyst works against human. Not only are people fallible, but so are hardware and software implementations. The only rule that applies to the attacker is that there are no rules. That why we need to know about widely encryption scheme such as DES, AES and RSA. 40

The Data Encryption Standard (DES) The DES, a system developed for the U. S government. Intended for use by the general public. Many hardware and software systems have been designed with the DES. Recently, its adequacy has been questioned. 41

The Data Encryption Standard (DES) (cont) Desirable criteria : 42 Able to provide high level of security. Specified and easy to understand. Available to all users. Adaptable for use in diverse application. Economical to implement in electronic devices. Efficient to use. Able to be validate. Exportable.
The Data Encryption Standard (DES) (cont) Overview : 43 Careful and complex combination of : substitution and transposition. Derives its strength from repeated application of these two techniques for 16 cycles. The algorithm begin with encrypting plaintext as block of 64 bits. (but in fact it can be any 56 -bit number- The extra 8 bits are often used as check digits and do not affect encryption in normal implementations ) It is suitable for implementation in software on most computers.

Double DES Researcher suggest using a double encryption for greater secrecy. Take two keys and perform two encryption, one on top of the other. Assumption is FALSE : two encryptions are no better than one. The double encryption only double the work for the attacker. 44
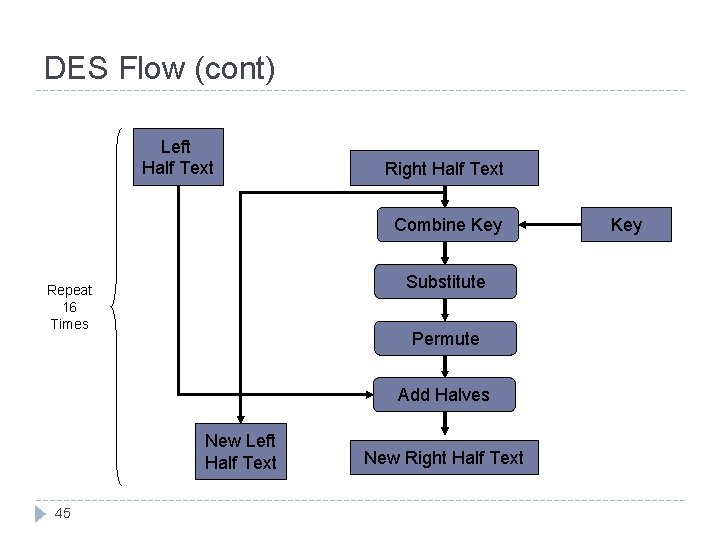
DES Flow (cont) Left Half Text Right Half Text Combine Key Substitute Repeat 16 Times Permute Add Halves New Left Half Text 45 New Right Half Text Key

Triple DES Using two keys and applying them into three operations adds apparent strength. Encrypt with one key, decrypt with the second, and encrypt with the first again. So that 112 bits effective key length is quite strong and it is effective against all feasible known attacks. 46

The Advanced Encryption Standard (AES) Desirable criteria : 47 Unclassified. Publicly disclosed. Available royalty-free for use worldwide. Symmetric block cipher algorithm for blocks of 128 bits Usable with key sizes of 128, 192 and 256 bits.
Overview of Rijndael Implemented easily on simple processors. Uses substitution, transposition, shift, exclusive OR and addition operations. Use 9, 11 or 13 cycle (round) for keys of 128, 192 and 256 bits. 48
Overview of Rijndael (cont) Each cycle consist of : 49 Byte substitution. Shift row. Mix column. Add sub key.
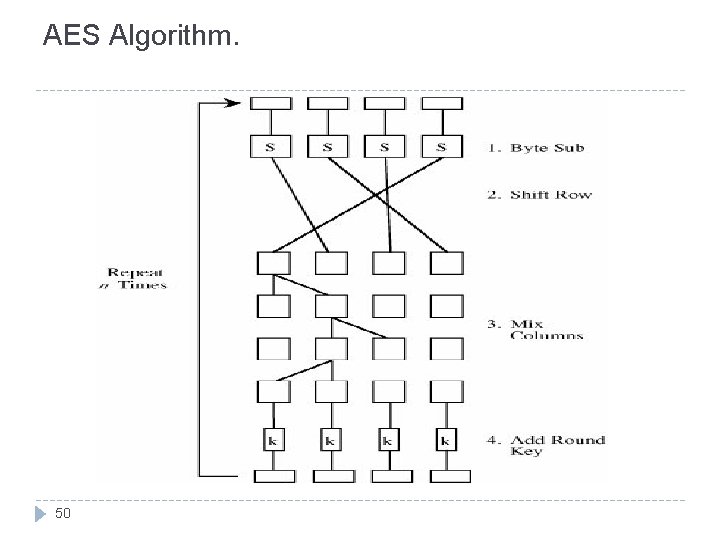
AES Algorithm. 50
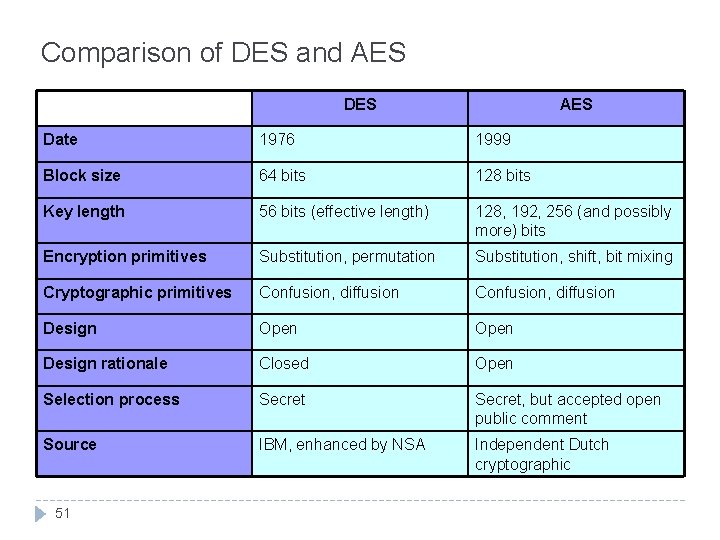
Comparison of DES and AES DES AES Date 1976 1999 Block size 64 bits 128 bits Key length 56 bits (effective length) 128, 192, 256 (and possibly more) bits Encryption primitives Substitution, permutation Substitution, shift, bit mixing Cryptographic primitives Confusion, diffusion Design Open Design rationale Closed Open Selection process Secret, but accepted open public comment Source IBM, enhanced by NSA Independent Dutch cryptographic 51
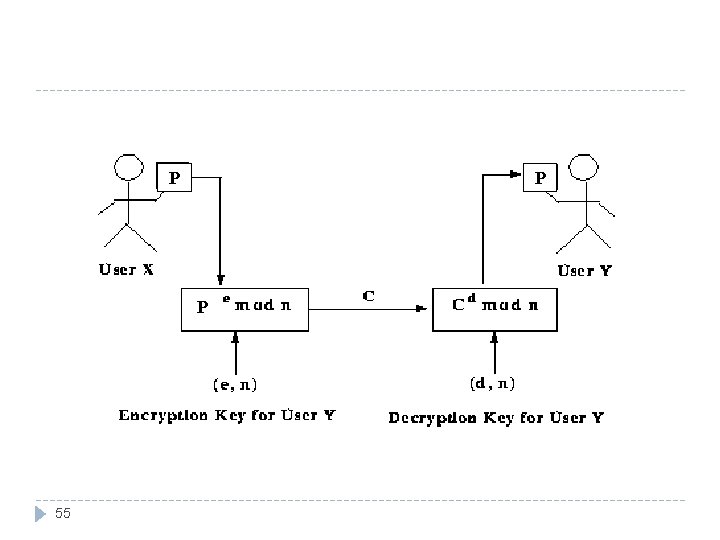
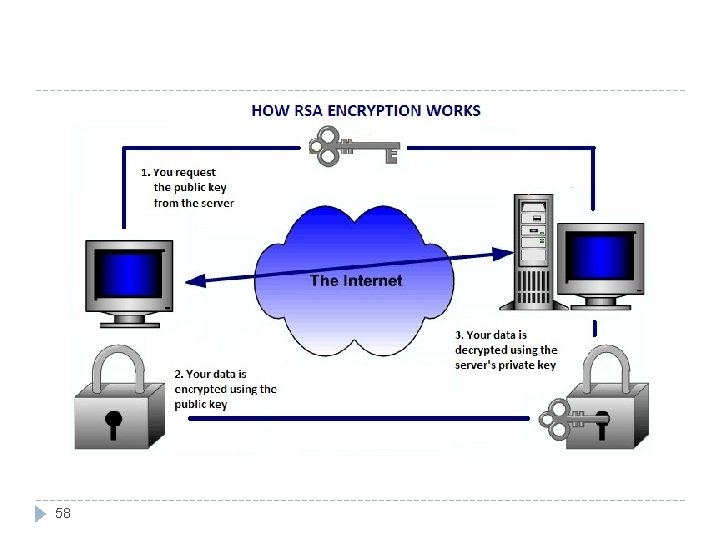
Rivest-Shamir-Adelman (RSA) Encryption RSA cryptosystem is a public key system. RSA has been the subject of extensive cryptanalysis, and no serious flaws have yet been found. Confidence in the method grows as time passes without discovery of a flaw. 52
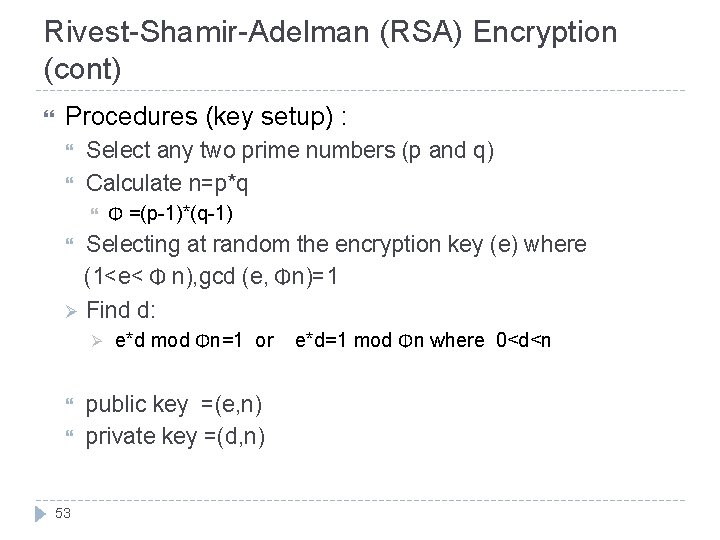
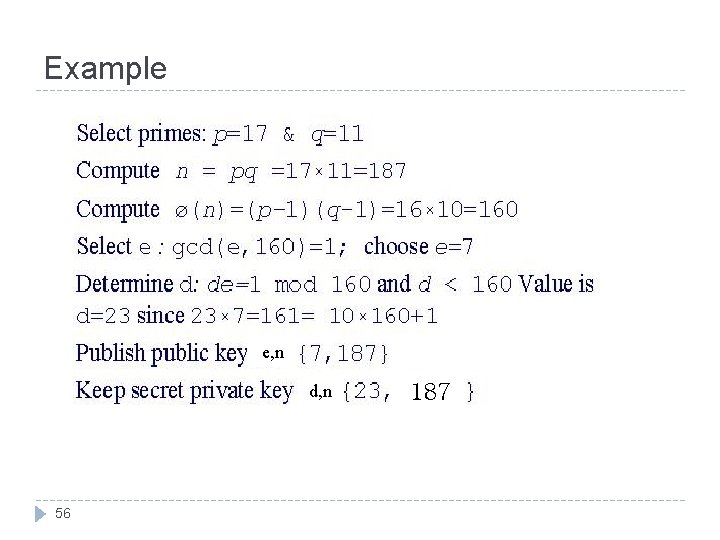
Rivest-Shamir-Adelman (RSA) Encryption (cont) Procedures (key setup) : Select any two prime numbers (p and q) Calculate n=p*q Φ =(p-1)*(q-1) Selecting at random the encryption key (e) where (1<e< Φ n), gcd (e, Φn)=1 Ø Find d: Ø 53 e*d mod Φn=1 or public key =(e, n) private key =(d, n) e*d=1 mod Φn where 0<d<n
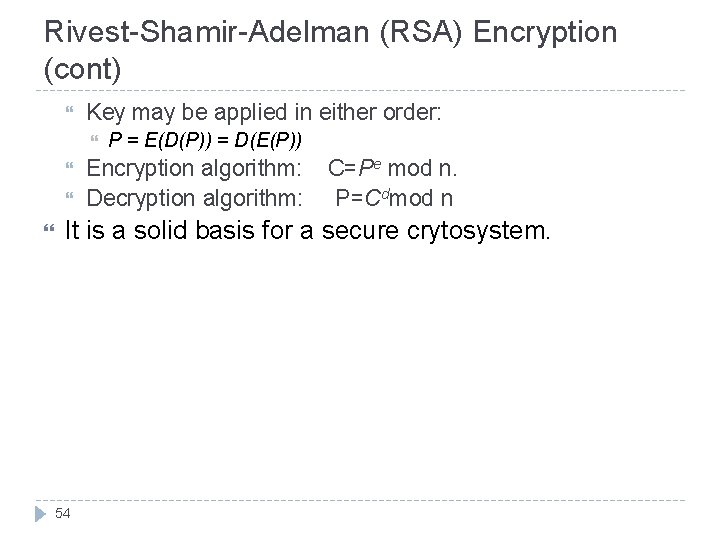
Rivest-Shamir-Adelman (RSA) Encryption (cont) Key may be applied in either order: P = E(D(P)) = D(E(P)) Encryption algorithm: Decryption algorithm: C=Pe mod n. P=Cdmod n It is a solid basis for a secure crytosystem. 54
P P P 55
Example e, n d, n 56 187

57
58

The Uses of Encryption Cryptographic Hash Function Key Exchange Digital Signature Certificates 59
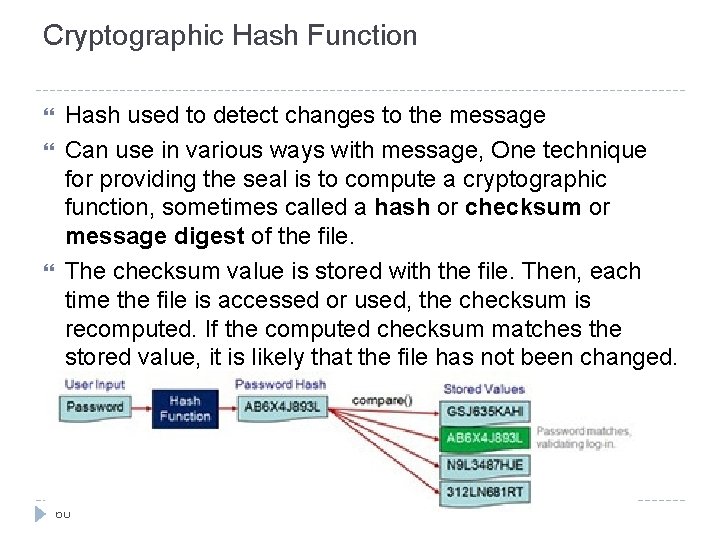
Cryptographic Hash Function Hash used to detect changes to the message Can use in various ways with message, One technique for providing the seal is to compute a cryptographic function, sometimes called a hash or checksum or message digest of the file. The checksum value is stored with the file. Then, each time the file is accessed or used, the checksum is recomputed. If the computed checksum matches the stored value, it is likely that the file has not been changed. 60

• Hash Function guarantee a message's integrity (address the nonalterability and nonreusability) • A change or reuse will be flagged by the checksum, so the recipient can know something is amiss and the recipient can make sure the message was not altered (intentionally or by chance) during the communication. • The most widely used cryptographic hash functions are MD 4, MD 5 (where MD stands for Message Digest), and SHA/SHS (Secure Hash Algorithm or Standard). • the hash can be said to represent the document's fingerprint 61
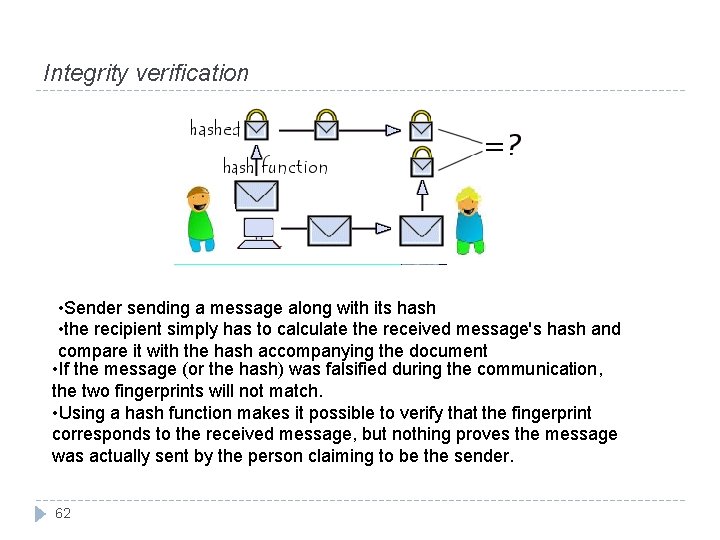
Integrity verification • Sender sending a message along with its hash • the recipient simply has to calculate the received message's hash and compare it with the hash accompanying the document • If the message (or the hash) was falsified during the communication, the two fingerprints will not match. • Using a hash function makes it possible to verify that the fingerprint corresponds to the received message, but nothing proves the message was actually sent by the person claiming to be the sender. 62
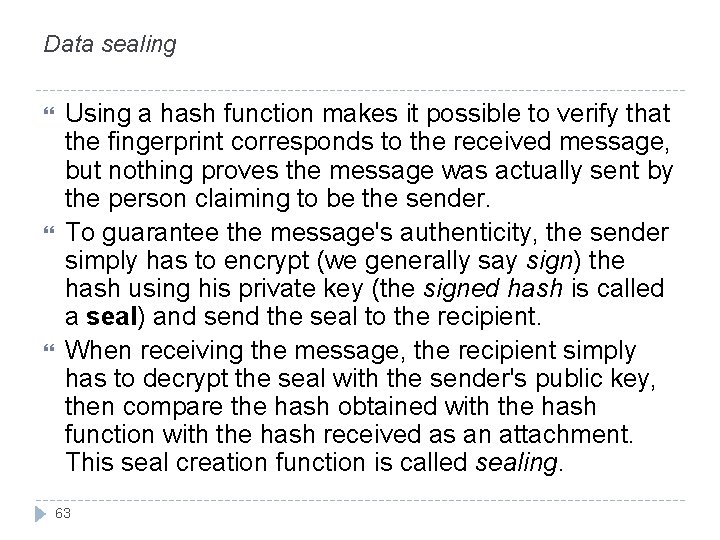
Data sealing Using a hash function makes it possible to verify that the fingerprint corresponds to the received message, but nothing proves the message was actually sent by the person claiming to be the sender. To guarantee the message's authenticity, the sender simply has to encrypt (we generally say sign) the hash using his private key (the signed hash is called a seal) and send the seal to the recipient. When receiving the message, the recipient simply has to decrypt the seal with the sender's public key, then compare the hash obtained with the hash function with the hash received as an attachment. This seal creation function is called sealing. 63
64
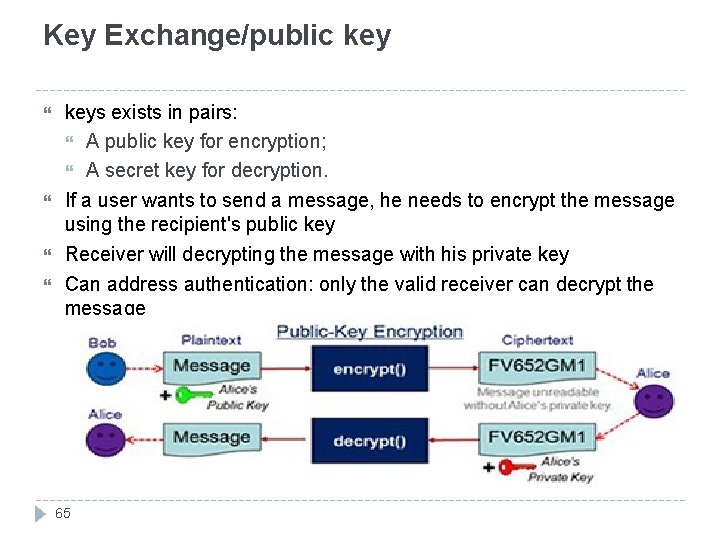
Key Exchange/public keys exists in pairs: A public key for encryption; A secret key for decryption. If a user wants to send a message, he needs to encrypt the message using the recipient's public key Receiver will decrypting the message with his private key Can address authentication: only the valid receiver can decrypt the message 65
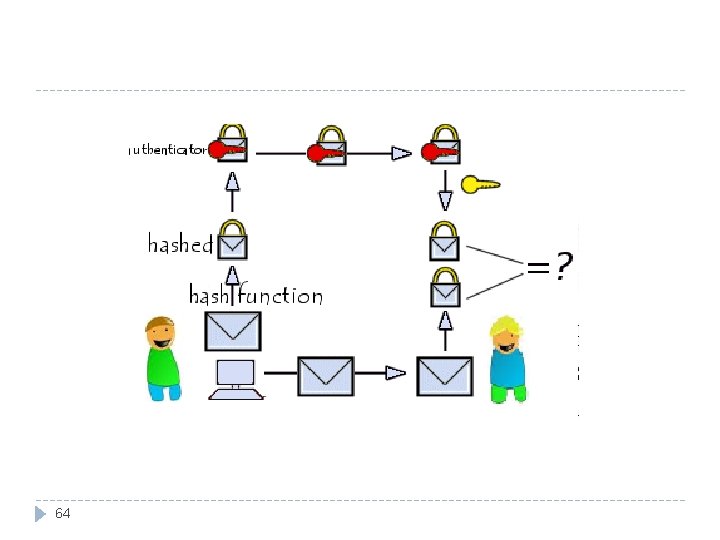
Digital Signatures Used to demonstrating the authenticity of a digital message or document Electronic signatures address non-repudiation , that is, they make it possible to ensure the sender really sent the message (sender cannot deny having sent the message). A digital signature must : 66 It must be unforgeable. It must be authentic It is not alterable. It is not reusable.
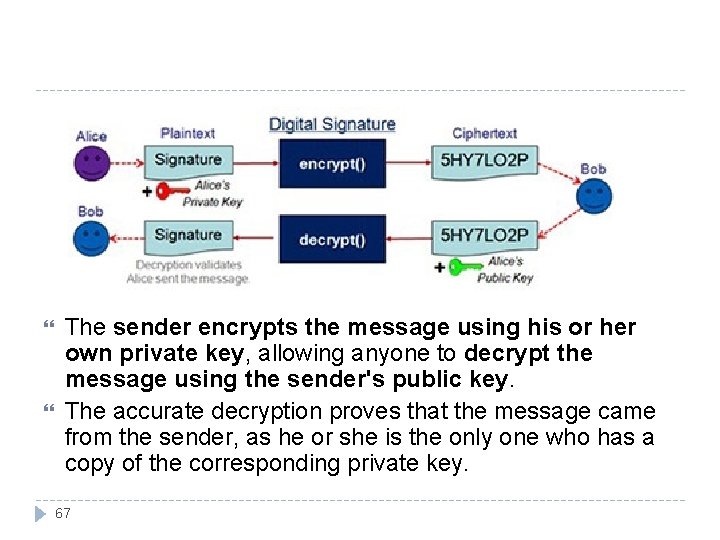
The sender encrypts the message using his or her own private key, allowing anyone to decrypt the message using the sender's public key. The accurate decryption proves that the message came from the sender, as he or she is the only one who has a copy of the corresponding private key. 67
Digital certificates A digital certificate is an electronic "credit card" that establishes your credentials when doing business or other transactions on the Web. Certificates are small files that are divided into two parts: The part containing information The part containing the certification authority's signature It is issued by a certification authority (CA). Digital certificates can be kept in registries so that authenticating users can look up other users' public keys 68

he structure of certificates is standardized by the ITU's X. 509 standard (more precisely X. 509 v 3), which defines the information contained in the certificate: 69 The version of X. 509 the certificate corresponds to; The certificate's serial number; The encryption algorithm used to sign the certificate; The name (DN, for Distinguished Name) of the issuing certification authority; The certificate's starting validity date; The certificate's ending validity date; The public key's subject; The public key of the certificate's owner; The certificate issuer's signature (thumbprint).
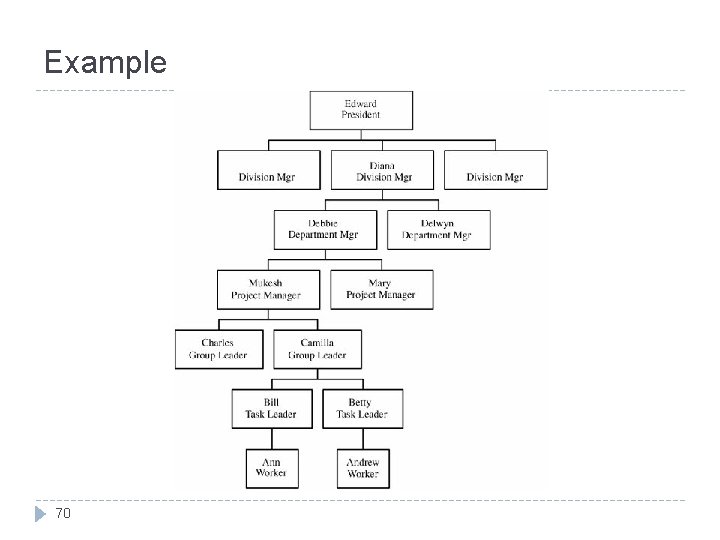
Example 70
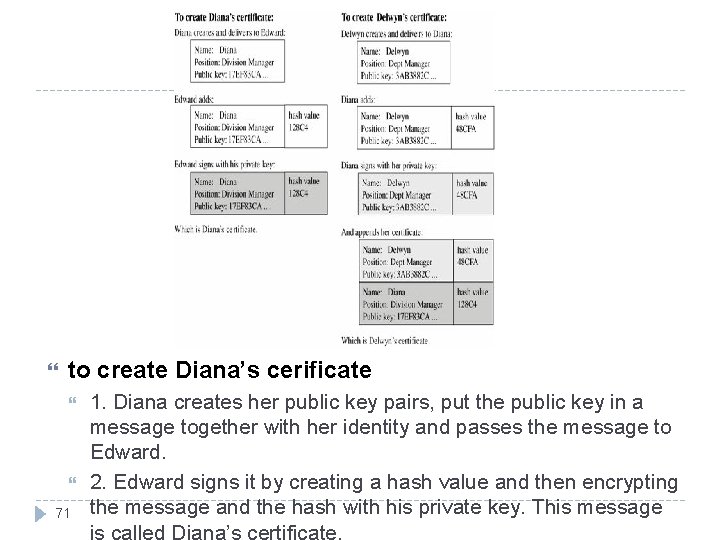
to create Diana’s cerificate 71 1. Diana creates her public key pairs, put the public key in a message together with her identity and passes the message to Edward. 2. Edward signs it by creating a hash value and then encrypting the message and the hash with his private key. This message is called Diana’s certificate.

Certificates are mainly used in three types of contexts: 72 Client certificates, stored on the user's workstation or embedded in a container such as a chip card, make it possible to identify a user and associate him with rights. In most cases, they are transmitted to the server when a connection is made, and the server assigns rights in function of the user's accreditation. They are real digital ID cards that use an asymmetric key pair ranging from 512 to 1024 bits long. Server certificates, installed on a web server, make it possible to connect a service with the service's owner. In the case of a website, they make it possible to guarantee that the web page's URL and particularly its domain really belong to such or such a company. They also make it possible to protect transactions with users. VPN certificates are a type of certificate installed in network equipment that make it possible to encrypt communication flows from start to finish between two points (for example, two company sites). In this type of scenario, the users have a client certificate, the servers apply a server certificate and the communication equipment uses a special certificate (generally an IPSec certificate.
- Slides: 72